Systems Documentation and Internal Controls: Revenue Cycle Review
VerifiedAdded on 2020/04/01
|9
|1536
|111
Report
AI Summary
This report, prepared for the CFO of Motherboards and More Pty Ltd, analyzes the company's accounting system, specifically its revenue cycle, in light of a recent ransomware outbreak in May 2017. The report provides a detailed overview of the revenue cycle, identifies internal control weaknesses and potential threats, and explains the mechanics of the ransomware attack. It reviews appropriate controls to mitigate risks and offers recommendations, such as implementing RFID tags for inventory tracking and deploying ransomware antivirus software, to strengthen the company's defenses. The report concludes by emphasizing the importance of these measures in preventing financial losses and protecting sensitive data from future cyberattacks. The study also highlights the impact of outdated software and the need for regular updates and data backups.

Running head: SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Systems Documentation and Internal Controls
Name of the Student
Name of the University
Author Note
Systems Documentation and Internal Controls
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Executive summary
This report deals with recent outbreak of the ransom ware attack. The report is for the
CFO of Motherboards and More Pty Ltd. He has also requested for completing a task with
the reviewing of the Revenue cycle and providing advice to management regarding the recent
‘Ransomware Outbreak’ in May 2017.The report has a detailed description of the revenue
cycle that the organization follows, identification of the threats which the currect system has,
overview of the working of the ransom ware attack, and recommendation for the organization
on how to combat the drawbacks in their system.
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Executive summary
This report deals with recent outbreak of the ransom ware attack. The report is for the
CFO of Motherboards and More Pty Ltd. He has also requested for completing a task with
the reviewing of the Revenue cycle and providing advice to management regarding the recent
‘Ransomware Outbreak’ in May 2017.The report has a detailed description of the revenue
cycle that the organization follows, identification of the threats which the currect system has,
overview of the working of the ransom ware attack, and recommendation for the organization
on how to combat the drawbacks in their system.

2
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Table of Contents
Introduction................................................................................................................................3
Overview of the Revenue Cycle................................................................................................3
Identification of threats..............................................................................................................5
Overview of the Ransom ware attack........................................................................................5
Review of appropriate controls..................................................................................................6
Recommendations......................................................................................................................6
Conclusion..................................................................................................................................7
References..................................................................................................................................8
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Table of Contents
Introduction................................................................................................................................3
Overview of the Revenue Cycle................................................................................................3
Identification of threats..............................................................................................................5
Overview of the Ransom ware attack........................................................................................5
Review of appropriate controls..................................................................................................6
Recommendations......................................................................................................................6
Conclusion..................................................................................................................................7
References..................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Introduction
A recent outbreak of the ransomware attack.The following report discusses about the
accounting system of the Motherboards and More Pty Ltd.The report has a detailed
description of the revenue cycle that the organization follows, identification of the threats
which the currect system has, overview of the working of the ransom ware attack, and
recommendation for the organization on how to combat the drawbacks in their system.
Overview of the Revenue Cycle
The revenue system, which is being followed by the Motherboards, and More Pty Ltd.
the company is a medium sized and is privately owned company. The company is a
manufacturer of motherboard, graphics cardsandmicrochipsand repairers across
Australia.Theofficesare in a central city building and the other departments are located on the
outskirts(Wells &Bravender, 2016).
The customer is allowed to place an order on the website of the company. All sale
procedures are made on credit payment. The orders are invoiced and sent to the warehouse
for the packing of the items. This is done in order of alphabetical naming of the customers.
The number of sources are almost twenty in number and the number of incoming deliveries
going out are much more than that. The large number of orders that are coming in makes the
delivery of the products wrong(Harris & Kaplan, 2015). When an item goes missing in the
warehouse the workers logs the item into the log book along with the tag so that the inventory
record can be updated.
After the item has been packed and sent out for delivery the item can then be tracked
by the customer. This would help in knowing the location of the item being delivered. After
the item has been delivered the feedback is taken form the customer and the reviews can be
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Introduction
A recent outbreak of the ransomware attack.The following report discusses about the
accounting system of the Motherboards and More Pty Ltd.The report has a detailed
description of the revenue cycle that the organization follows, identification of the threats
which the currect system has, overview of the working of the ransom ware attack, and
recommendation for the organization on how to combat the drawbacks in their system.
Overview of the Revenue Cycle
The revenue system, which is being followed by the Motherboards, and More Pty Ltd.
the company is a medium sized and is privately owned company. The company is a
manufacturer of motherboard, graphics cardsandmicrochipsand repairers across
Australia.Theofficesare in a central city building and the other departments are located on the
outskirts(Wells &Bravender, 2016).
The customer is allowed to place an order on the website of the company. All sale
procedures are made on credit payment. The orders are invoiced and sent to the warehouse
for the packing of the items. This is done in order of alphabetical naming of the customers.
The number of sources are almost twenty in number and the number of incoming deliveries
going out are much more than that. The large number of orders that are coming in makes the
delivery of the products wrong(Harris & Kaplan, 2015). When an item goes missing in the
warehouse the workers logs the item into the log book along with the tag so that the inventory
record can be updated.
After the item has been packed and sent out for delivery the item can then be tracked
by the customer. This would help in knowing the location of the item being delivered. After
the item has been delivered the feedback is taken form the customer and the reviews can be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
uploaded on the company’s website for the future customers to help them buy the best
product (Sittig& Singh, 2016).
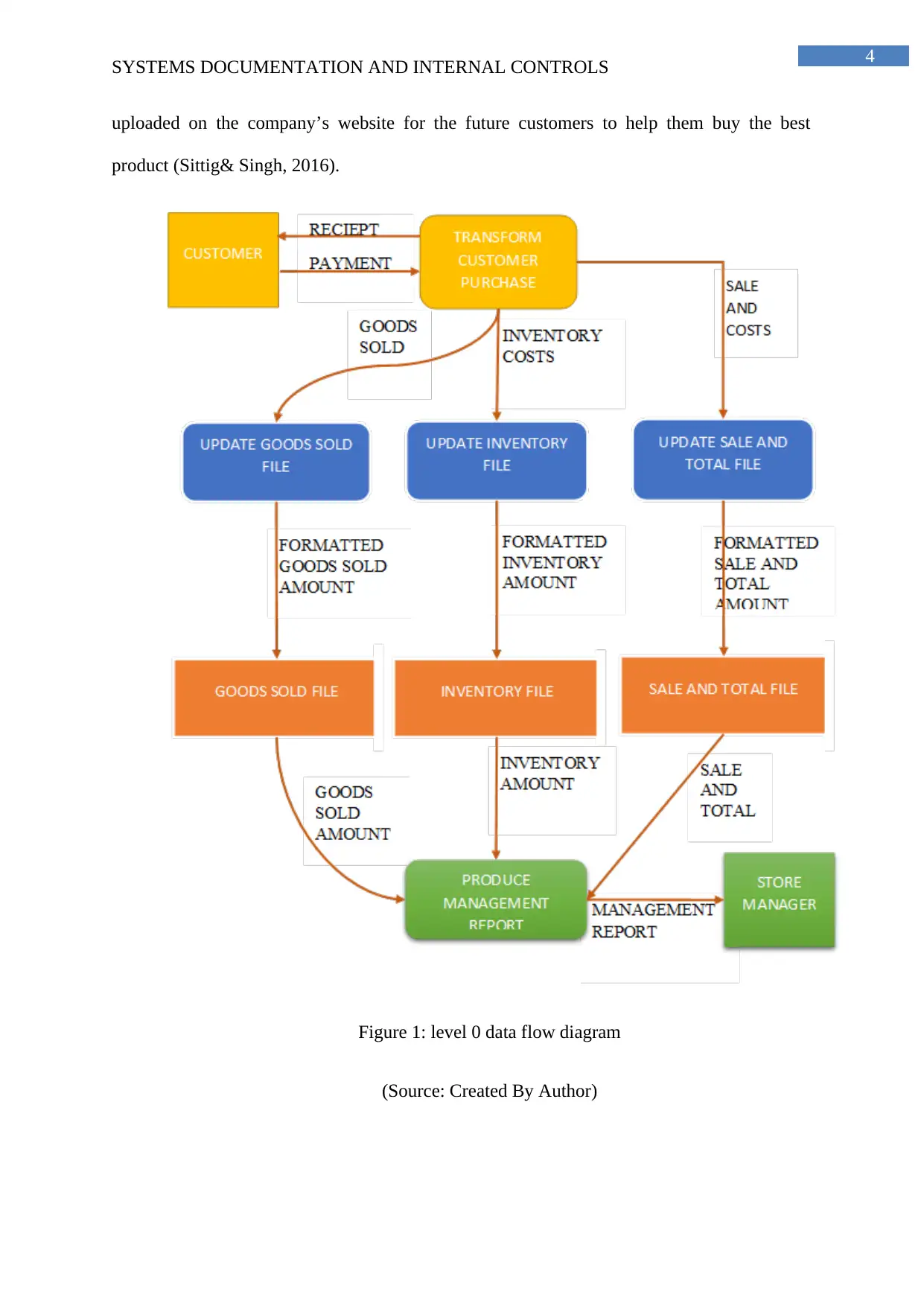
Figure 1: level 0 data flow diagram
(Source: Created By Author)
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
uploaded on the company’s website for the future customers to help them buy the best
product (Sittig& Singh, 2016).
Figure 1: level 0 data flow diagram
(Source: Created By Author)
5
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Identification of threats
The following table discusses about the different threats which is being faced by
Motherboards and More Revenue Cycle:
Internal Control Weaknesses There is no physical counting of the inventory
items.
Impact These Weaknesses If the items are not kept a track of then if
something gets lost then it will not be found
Specific Internal Controls Tagging the items in the inventory and then
keeping a track of the location the item was last
stored can help in the tracking of the lost items.
Also keeping an active connective closed circuit
camera would help in looking after the
warehouse floor.
Overview of the Ransom ware attack
The ransom ware attack which broke out in May 2017 had locked out users from their
computers and encrypted their files. The files would be decrypted only after the user agreed
to pay the hackers for a ransom amount of money. The attack was of self replicating format
which would use the vulnerability of the older windows versions (Kharraz et al., 2015). The
initial ransom amount asked was US$300. The amount increased after some hours. The virus
spread from one computer to another using the vulnerability of the windows. The security
holes of the windows versions were already published and let known to the world long before
the virus attacked (Collier, 2017). After the virus attacked the computers Microsoft
announced that they had already looked after and essential patches had been delivered for the
windows versions. The problem was that the users of windows always kept their windows
updates switched off. Many of the windows versions in use by the users have already become
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Identification of threats
The following table discusses about the different threats which is being faced by
Motherboards and More Revenue Cycle:
Internal Control Weaknesses There is no physical counting of the inventory
items.
Impact These Weaknesses If the items are not kept a track of then if
something gets lost then it will not be found
Specific Internal Controls Tagging the items in the inventory and then
keeping a track of the location the item was last
stored can help in the tracking of the lost items.
Also keeping an active connective closed circuit
camera would help in looking after the
warehouse floor.
Overview of the Ransom ware attack
The ransom ware attack which broke out in May 2017 had locked out users from their
computers and encrypted their files. The files would be decrypted only after the user agreed
to pay the hackers for a ransom amount of money. The attack was of self replicating format
which would use the vulnerability of the older windows versions (Kharraz et al., 2015). The
initial ransom amount asked was US$300. The amount increased after some hours. The virus
spread from one computer to another using the vulnerability of the windows. The security
holes of the windows versions were already published and let known to the world long before
the virus attacked (Collier, 2017). After the virus attacked the computers Microsoft
announced that they had already looked after and essential patches had been delivered for the
windows versions. The problem was that the users of windows always kept their windows
updates switched off. Many of the windows versions in use by the users have already become
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
obsolete. The most effective attack was done on the hospitals and clinics in England
(Mohurle&Patil, 2017). The exorcists forced the users to open an infected mail, which
activated the malicious virus on their system. The researchers found that there was a total
amount of 57,000 from over 99 countries.
Review of appropriate controls
The appropriate measures, which needs to be taken by the organization ti safeguard
them from the attacks of the ransom ware virus, is to install a ransom ware antivirus. This
will be able to determine the attacks of a ransom ware virus and stop the working of the
procedure as soon as it starts executing the programming script on the computer (Gupta
&Tripathi, 2017). Always keeping a backup of the files and a copy of the data server. This
would help in keeping all the dataa and the connected devices safe from the virus. They
should also check the mail that has been received by them (Pope, 2016). Opening of the mail
as soon as it is received can force a ransom ware virus to start its execution procedure. The
major problem due to which the ransom virus attacked the computers was due to the absence
of the latest updates on the system. Moreover never aping the ransom amount is also an
intelligent way of combatting the virus.
Recommendations
From the above report discussion, it can be said the most important problem that, the
Motherboards and More Pty Ltd faces is the difficulty in keeping a tr4ack of the items that is
there in the warehouse. The items has been tagged and kept in the shelf. The items should be
tagged and number with the help of a radio frequency identification tags (RFID).This would
help in knowing the location of the product and if an unauthorized way were taken up to take
the item out of the warehouse then the tags would help in informing the authorities about the
item being taking out of the warehouse.
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
obsolete. The most effective attack was done on the hospitals and clinics in England
(Mohurle&Patil, 2017). The exorcists forced the users to open an infected mail, which
activated the malicious virus on their system. The researchers found that there was a total
amount of 57,000 from over 99 countries.
Review of appropriate controls
The appropriate measures, which needs to be taken by the organization ti safeguard
them from the attacks of the ransom ware virus, is to install a ransom ware antivirus. This
will be able to determine the attacks of a ransom ware virus and stop the working of the
procedure as soon as it starts executing the programming script on the computer (Gupta
&Tripathi, 2017). Always keeping a backup of the files and a copy of the data server. This
would help in keeping all the dataa and the connected devices safe from the virus. They
should also check the mail that has been received by them (Pope, 2016). Opening of the mail
as soon as it is received can force a ransom ware virus to start its execution procedure. The
major problem due to which the ransom virus attacked the computers was due to the absence
of the latest updates on the system. Moreover never aping the ransom amount is also an
intelligent way of combatting the virus.
Recommendations
From the above report discussion, it can be said the most important problem that, the
Motherboards and More Pty Ltd faces is the difficulty in keeping a tr4ack of the items that is
there in the warehouse. The items has been tagged and kept in the shelf. The items should be
tagged and number with the help of a radio frequency identification tags (RFID).This would
help in knowing the location of the product and if an unauthorized way were taken up to take
the item out of the warehouse then the tags would help in informing the authorities about the
item being taking out of the warehouse.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Conclusion
From the above report, it can be determined that the ransom ware attack on the
international organizations has made a lot of loss in the financial situations and a lot of data
of the company. The detailed study of the case study on the Motherboards and More Pty Ltd
has produced the details based on the technical drawbacks of the warehouse. The drawback
can be removed by following the recommendation provided in the report.
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
Conclusion
From the above report, it can be determined that the ransom ware attack on the
international organizations has made a lot of loss in the financial situations and a lot of data
of the company. The detailed study of the case study on the Motherboards and More Pty Ltd
has produced the details based on the technical drawbacks of the warehouse. The drawback
can be removed by following the recommendation provided in the report.

8
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
References
Collier, R. (2017). NHS ransomware attack spreads worldwide.
Gupta, G., &Tripathi, K. (2017). STUDY ON RANSOMWARE ATTACK AND ITS
PREVENTION. International Education and Research Journal, 3(5).
Harris, M. T., & Kaplan, D. (2015). The Revenue Cycle. In The Complete Business Guide for
a Successful Medical Practice (pp. 107-119). Springer International Publishing.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., &Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mohurle, S., &Patil, M. (2017). A brief study of Wannacry Threat: Ransomware Attack
2017. International Journal, 8(5).
Pope, J. (2016). Ransomware: Minimizing the Risks. Innovations in clinical
neuroscience, 13(11-12), 37.
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransomware attacks. Applied clinical informatics, 7(2), 624.
Wells, S. T., &Bravender, R. (2016). Improving employee engagement in the revenue
cycle. Healthcare Financial Management, 70(10), 36-39.
SYSTEMS DOCUMENTATION AND INTERNAL CONTROLS
References
Collier, R. (2017). NHS ransomware attack spreads worldwide.
Gupta, G., &Tripathi, K. (2017). STUDY ON RANSOMWARE ATTACK AND ITS
PREVENTION. International Education and Research Journal, 3(5).
Harris, M. T., & Kaplan, D. (2015). The Revenue Cycle. In The Complete Business Guide for
a Successful Medical Practice (pp. 107-119). Springer International Publishing.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., &Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mohurle, S., &Patil, M. (2017). A brief study of Wannacry Threat: Ransomware Attack
2017. International Journal, 8(5).
Pope, J. (2016). Ransomware: Minimizing the Risks. Innovations in clinical
neuroscience, 13(11-12), 37.
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransomware attacks. Applied clinical informatics, 7(2), 624.
Wells, S. T., &Bravender, R. (2016). Improving employee engagement in the revenue
cycle. Healthcare Financial Management, 70(10), 36-39.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





