ACCT6001: Database Application and Security Report - Butler Financing
VerifiedAdded on 2023/03/21
|9
|1933
|54
Report
AI Summary
This report details the creation of a database for Butler Financing Company to address data inconsistency issues arising from spreadsheet use. It justifies the use of a database management system (DBMS) and outlines its advantages, including data redundancy control, improved consistency, and enhanced security. The report identifies entities such as BORROWER, LENDER, and MORTGAGE_REQUEST, and presents an ER diagram illustrating their relationships. It then demonstrates the implementation using Microsoft Access, including table structures for BORROWER, LENDER, PROPERTY_APPRAISER, and MORTGAGE_REQUEST, along with example queries, forms, and reports. Furthermore, the report addresses IT security and privacy concerns, detailing potential database risks like data tampering, unauthorized access, and lack of accountability. It also specifies data security requirements, including confidentiality, privacy of communications, secure data storage, and authentication methods to ensure data integrity and protection. The conclusion summarizes the benefits of the database approach and emphasizes the importance of security measures.

Table of Contents
Introduction......................................................................................................................................2
Justification of the use of database..................................................................................................2
ER diagram......................................................................................................................................3
Microsoft Access.............................................................................................................................4
BORROWER table..................................................................................................................................4
LENDER table........................................................................................................................................4
PROPERTY_APPRAISR table...............................................................................................................5
MORTGAGE_REQUEST table..............................................................................................................5
Queries....................................................................................................................................................5
Forms......................................................................................................................................................6
Reports....................................................................................................................................................7
IT security and Privacy............................................................................................................................7
Database risks..........................................................................................................................................7
Data Tampering......................................................................................................................................................7
Unauthorized Access to Tables and Columns........................................................................................................7
Unauthorized Access to Data Rows.......................................................................................................................8
Lack of Accountability...........................................................................................................................................8
Data Security Requirements....................................................................................................................8
Confidentiality.......................................................................................................................................................8
Privacy of Communications...................................................................................................................................8
Secure Storage of Sensitive Data...........................................................................................................................8
Authentication........................................................................................................................................................8
Conclusion.......................................................................................................................................9
References........................................................................................................................................9
Introduction......................................................................................................................................2
Justification of the use of database..................................................................................................2
ER diagram......................................................................................................................................3
Microsoft Access.............................................................................................................................4
BORROWER table..................................................................................................................................4
LENDER table........................................................................................................................................4
PROPERTY_APPRAISR table...............................................................................................................5
MORTGAGE_REQUEST table..............................................................................................................5
Queries....................................................................................................................................................5
Forms......................................................................................................................................................6
Reports....................................................................................................................................................7
IT security and Privacy............................................................................................................................7
Database risks..........................................................................................................................................7
Data Tampering......................................................................................................................................................7
Unauthorized Access to Tables and Columns........................................................................................................7
Unauthorized Access to Data Rows.......................................................................................................................8
Lack of Accountability...........................................................................................................................................8
Data Security Requirements....................................................................................................................8
Confidentiality.......................................................................................................................................................8
Privacy of Communications...................................................................................................................................8
Secure Storage of Sensitive Data...........................................................................................................................8
Authentication........................................................................................................................................................8
Conclusion.......................................................................................................................................9
References........................................................................................................................................9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The report aims at creating a database for Butler Financing Company which provides mortgages
to the borrowers by matching their requests with the lending capacity of lenders. The entire
storing of data has been done in spreadsheet up till now. But due to increase in the customer
base, there has been a rise in the issues of data consistency. The manual feeding of data in the
spreadsheet has led to cancellation of various mortgages, over or unpaid mortgages to the
lenders. Other inconsistencies include double entry of mortgages, borrowers and lenders. Along
with this, there are various data security risks in the current spreadsheet data storage mechanism
i.e. illegal access to users, unauthenticated entry of data or modifying/adding columns in the
spreadsheet. As a result of these data issues and inconsistencies, it has been proposed to transfer
data from spreadsheet to a database management system. The database for the Butler company
has been decided to be made using Microsoft Access.
Justification of the use of database
The use of database for the company would bring in several business advantages. Some of the
advantages may be realized sooner and some over time. Following are the key advantages from
using the database system.
Control of data redundancy
The database approach would ultimately help to reduce any redundancy that will brought in by
using other methods. As mentioned, the database will not completely remove the redundancies
but controls the amount of redundancy being introduced in the database.
Control of data consistency
The database approach would ultimately help to reduce any inconsistency that will brought in by
using other methods. As mentioned, the database will not completely remove the inconsistencies
but controls the amount of inconsistency being introduced in the database.
More information
It may be possible to extract additional data and results by integration of database with analytics
and intelligence tools to derive additional information using the same data.
Employing a database system makes the data virtually available to all people in the organization
as well as remote employees (Date, Kannan and Swamynathan, 2006).
Employing a database system improves the data integrity of the database because of inbuilt
consistency and validity mechanisms built in. The database is not permitted to violate any
constraints as defined by the administrator.
The report aims at creating a database for Butler Financing Company which provides mortgages
to the borrowers by matching their requests with the lending capacity of lenders. The entire
storing of data has been done in spreadsheet up till now. But due to increase in the customer
base, there has been a rise in the issues of data consistency. The manual feeding of data in the
spreadsheet has led to cancellation of various mortgages, over or unpaid mortgages to the
lenders. Other inconsistencies include double entry of mortgages, borrowers and lenders. Along
with this, there are various data security risks in the current spreadsheet data storage mechanism
i.e. illegal access to users, unauthenticated entry of data or modifying/adding columns in the
spreadsheet. As a result of these data issues and inconsistencies, it has been proposed to transfer
data from spreadsheet to a database management system. The database for the Butler company
has been decided to be made using Microsoft Access.
Justification of the use of database
The use of database for the company would bring in several business advantages. Some of the
advantages may be realized sooner and some over time. Following are the key advantages from
using the database system.
Control of data redundancy
The database approach would ultimately help to reduce any redundancy that will brought in by
using other methods. As mentioned, the database will not completely remove the redundancies
but controls the amount of redundancy being introduced in the database.
Control of data consistency
The database approach would ultimately help to reduce any inconsistency that will brought in by
using other methods. As mentioned, the database will not completely remove the inconsistencies
but controls the amount of inconsistency being introduced in the database.
More information
It may be possible to extract additional data and results by integration of database with analytics
and intelligence tools to derive additional information using the same data.
Employing a database system makes the data virtually available to all people in the organization
as well as remote employees (Date, Kannan and Swamynathan, 2006).
Employing a database system improves the data integrity of the database because of inbuilt
consistency and validity mechanisms built in. The database is not permitted to violate any
constraints as defined by the administrator.

The security of the database can also be increased by simply employing the use of a database
system. This is because, the database can be prevented from unathorized use by simply
employing the use of usernames and passwords.
The database can also include enforcement of standards such as documentation standards, data
formats, update procedures, naming conventions and so on.
Economies of scale can be enforced by combining all organizational data into one place and
streamlining the administrator and usage of database systems.
Improvement of responsiveness and data accessibility can be achieved. This is because an
optimized database management system can prove to be extremely fast and efficient at retrieving
queries and performing data operations.
The database approach is able to provide a low-level file handling-based routine. These kinds of
provisions allow operators to focus their energy on a specific functionality rather than the whole.
By employing a centralized database system, various different conflicts and differences between
departments and users could be resolved. Decisions would then be based on the use of resources
for organization rather than a single entity.
Database system also brings in about a change in the maintenance of data. Through the use of a
database system, systematic maintenance of database can be greatly improved (Middleton,
2012).
The database system can inherently be encrypted by different levels of encryption apart from
also having tier-based access. This increases the security of database and enforces strong
protection mechanisms for it.
Database system also allows for concurrent user-based access. This means that multiple people
can use the database without having to interfere other’s work or restrict other’s work.
The database would be continuously backed up to on-site and off-site storage. This adds another
layer of protection as the database remains safe at all times. In the event of any disaster or
breach, the data can be restored promptly.
ER diagram
Following entities have been identified for the proposed Butler Financing company:
Entity Description / Attributes
BORROWER This entity represents a person who requests for mortgage from
company.
system. This is because, the database can be prevented from unathorized use by simply
employing the use of usernames and passwords.
The database can also include enforcement of standards such as documentation standards, data
formats, update procedures, naming conventions and so on.
Economies of scale can be enforced by combining all organizational data into one place and
streamlining the administrator and usage of database systems.
Improvement of responsiveness and data accessibility can be achieved. This is because an
optimized database management system can prove to be extremely fast and efficient at retrieving
queries and performing data operations.
The database approach is able to provide a low-level file handling-based routine. These kinds of
provisions allow operators to focus their energy on a specific functionality rather than the whole.
By employing a centralized database system, various different conflicts and differences between
departments and users could be resolved. Decisions would then be based on the use of resources
for organization rather than a single entity.
Database system also brings in about a change in the maintenance of data. Through the use of a
database system, systematic maintenance of database can be greatly improved (Middleton,
2012).
The database system can inherently be encrypted by different levels of encryption apart from
also having tier-based access. This increases the security of database and enforces strong
protection mechanisms for it.
Database system also allows for concurrent user-based access. This means that multiple people
can use the database without having to interfere other’s work or restrict other’s work.
The database would be continuously backed up to on-site and off-site storage. This adds another
layer of protection as the database remains safe at all times. In the event of any disaster or
breach, the data can be restored promptly.
ER diagram
Following entities have been identified for the proposed Butler Financing company:
Entity Description / Attributes
BORROWER This entity represents a person who requests for mortgage from
company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
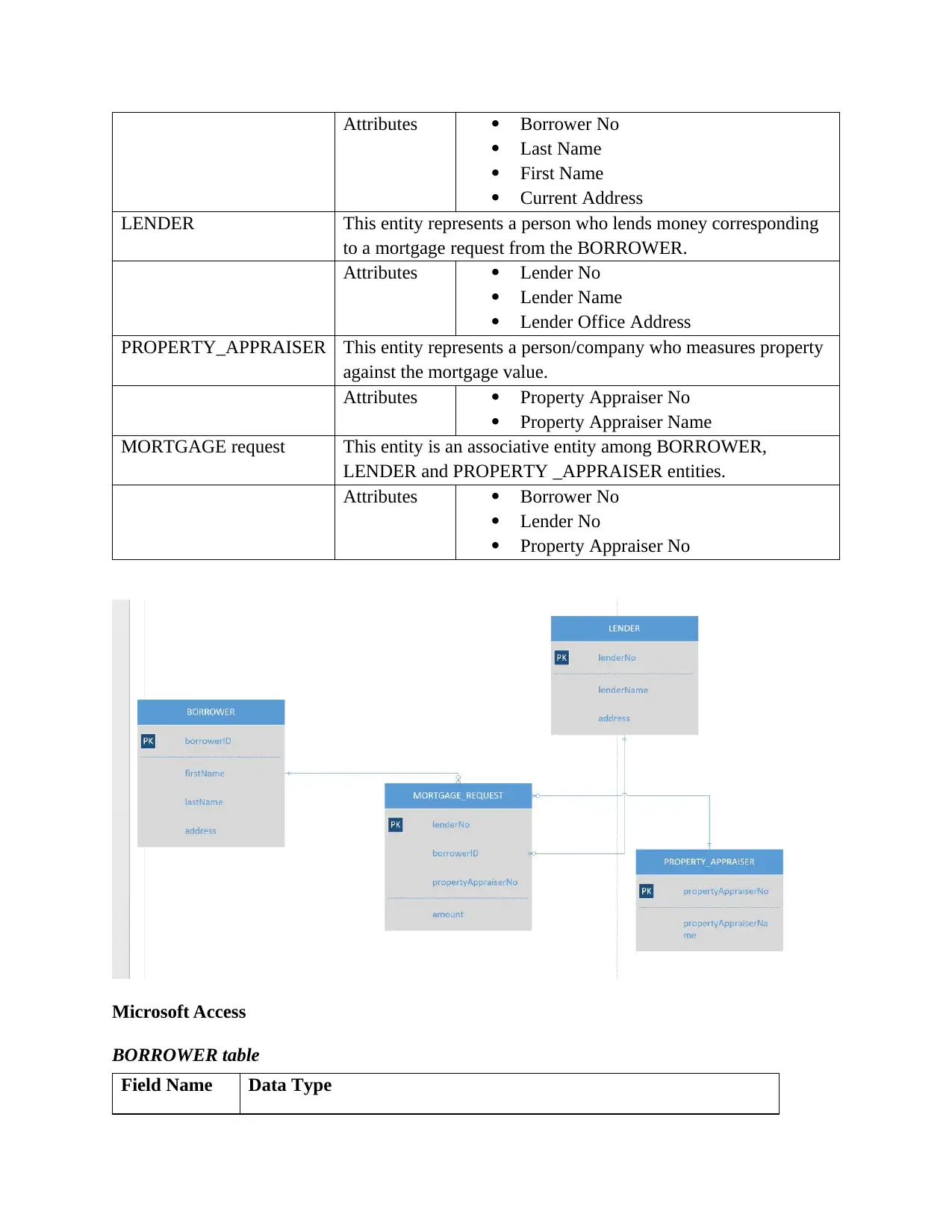
Attributes Borrower No
Last Name
First Name
Current Address
LENDER This entity represents a person who lends money corresponding
to a mortgage request from the BORROWER.
Attributes Lender No
Lender Name
Lender Office Address
PROPERTY_APPRAISER This entity represents a person/company who measures property
against the mortgage value.
Attributes Property Appraiser No
Property Appraiser Name
MORTGAGE request This entity is an associative entity among BORROWER,
LENDER and PROPERTY _APPRAISER entities.
Attributes Borrower No
Lender No
Property Appraiser No
Microsoft Access
BORROWER table
Field Name Data Type
Last Name
First Name
Current Address
LENDER This entity represents a person who lends money corresponding
to a mortgage request from the BORROWER.
Attributes Lender No
Lender Name
Lender Office Address
PROPERTY_APPRAISER This entity represents a person/company who measures property
against the mortgage value.
Attributes Property Appraiser No
Property Appraiser Name
MORTGAGE request This entity is an associative entity among BORROWER,
LENDER and PROPERTY _APPRAISER entities.
Attributes Borrower No
Lender No
Property Appraiser No
Microsoft Access
BORROWER table
Field Name Data Type
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
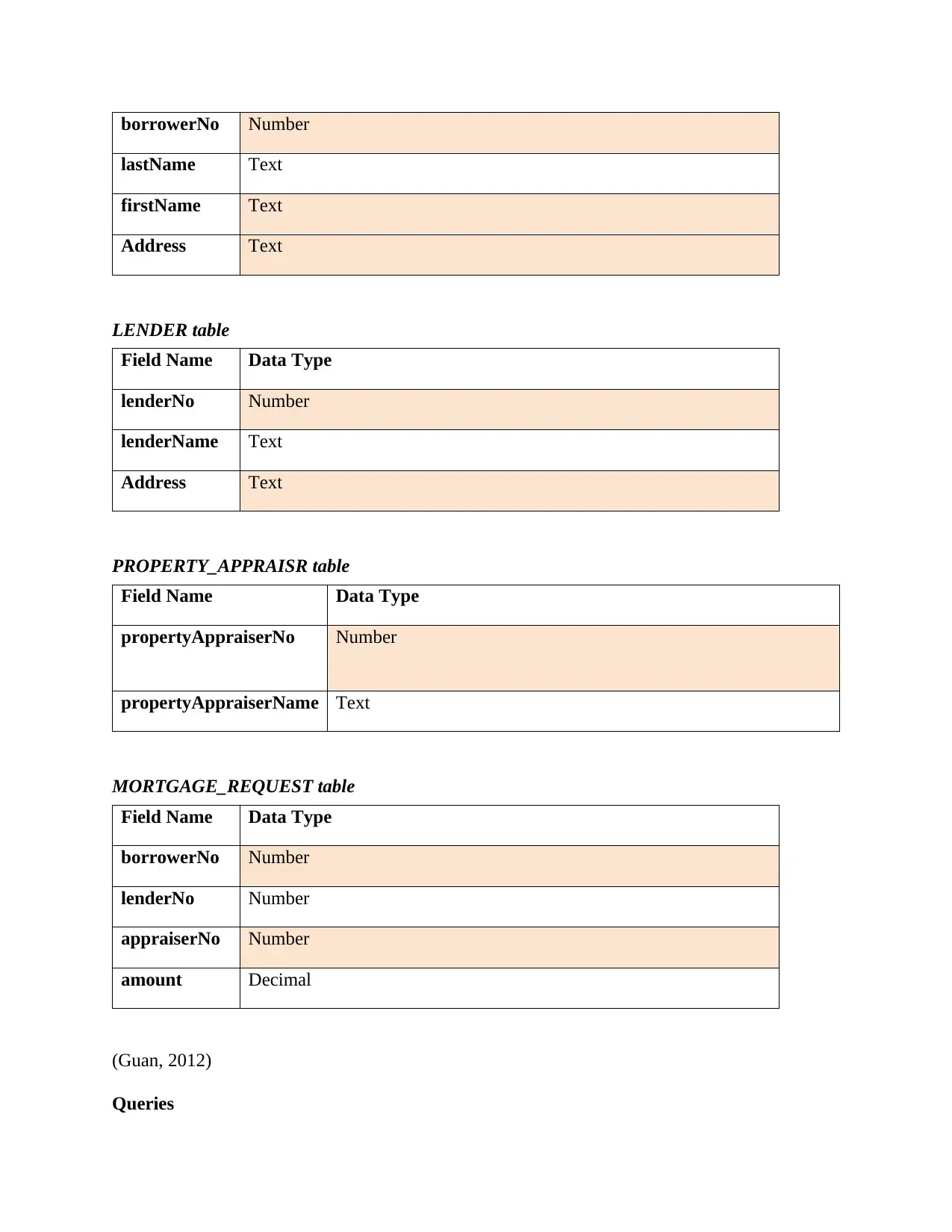
borrowerNo Number
lastName Text
firstName Text
Address Text
LENDER table
Field Name Data Type
lenderNo Number
lenderName Text
Address Text
PROPERTY_APPRAISR table
Field Name Data Type
propertyAppraiserNo Number
propertyAppraiserName Text
MORTGAGE_REQUEST table
Field Name Data Type
borrowerNo Number
lenderNo Number
appraiserNo Number
amount Decimal
(Guan, 2012)
Queries
lastName Text
firstName Text
Address Text
LENDER table
Field Name Data Type
lenderNo Number
lenderName Text
Address Text
PROPERTY_APPRAISR table
Field Name Data Type
propertyAppraiserNo Number
propertyAppraiserName Text
MORTGAGE_REQUEST table
Field Name Data Type
borrowerNo Number
lenderNo Number
appraiserNo Number
amount Decimal
(Guan, 2012)
Queries
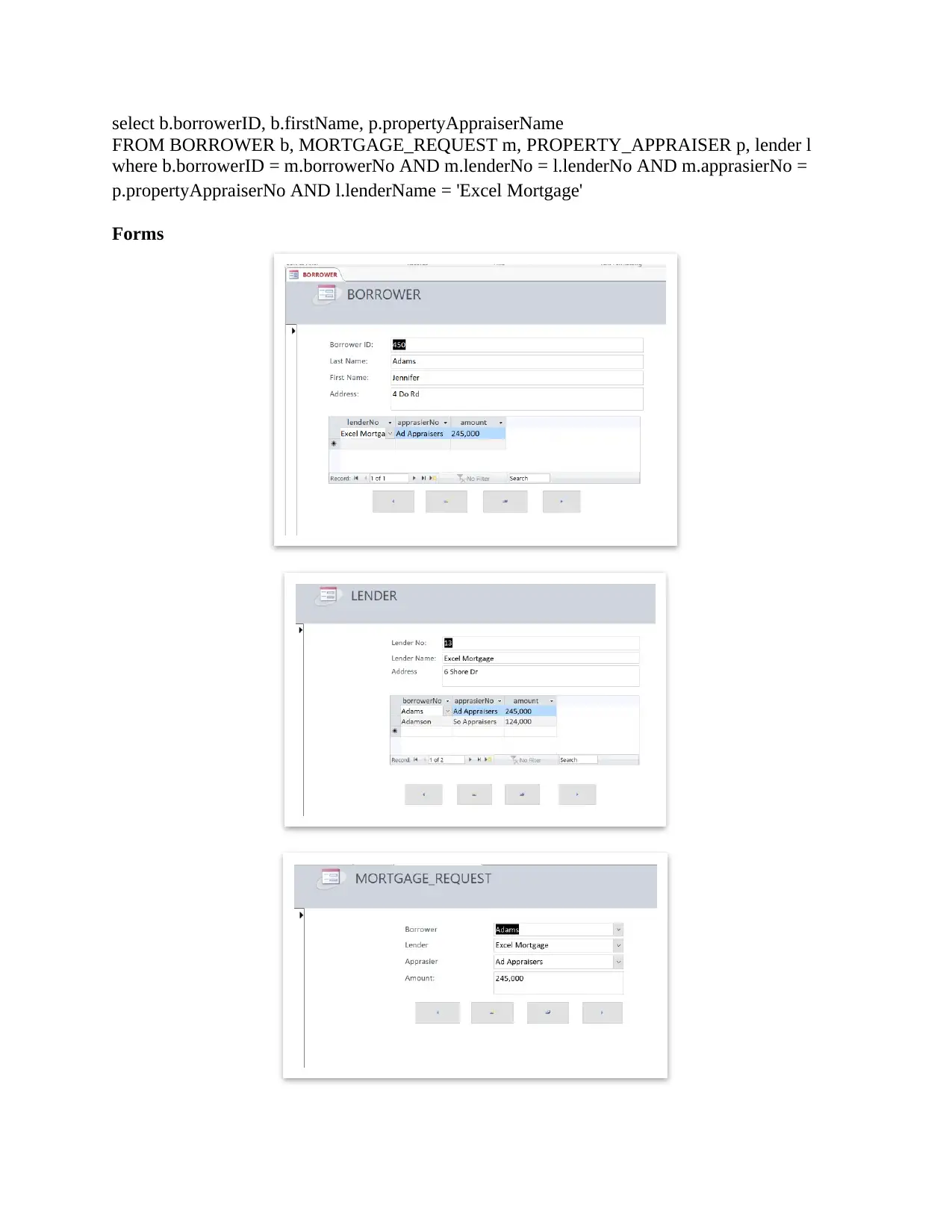
select b.borrowerID, b.firstName, p.propertyAppraiserName
FROM BORROWER b, MORTGAGE_REQUEST m, PROPERTY_APPRAISER p, lender l
where b.borrowerID = m.borrowerNo AND m.lenderNo = l.lenderNo AND m.apprasierNo =
p.propertyAppraiserNo AND l.lenderName = 'Excel Mortgage'
Forms
FROM BORROWER b, MORTGAGE_REQUEST m, PROPERTY_APPRAISER p, lender l
where b.borrowerID = m.borrowerNo AND m.lenderNo = l.lenderNo AND m.apprasierNo =
p.propertyAppraiserNo AND l.lenderName = 'Excel Mortgage'
Forms
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
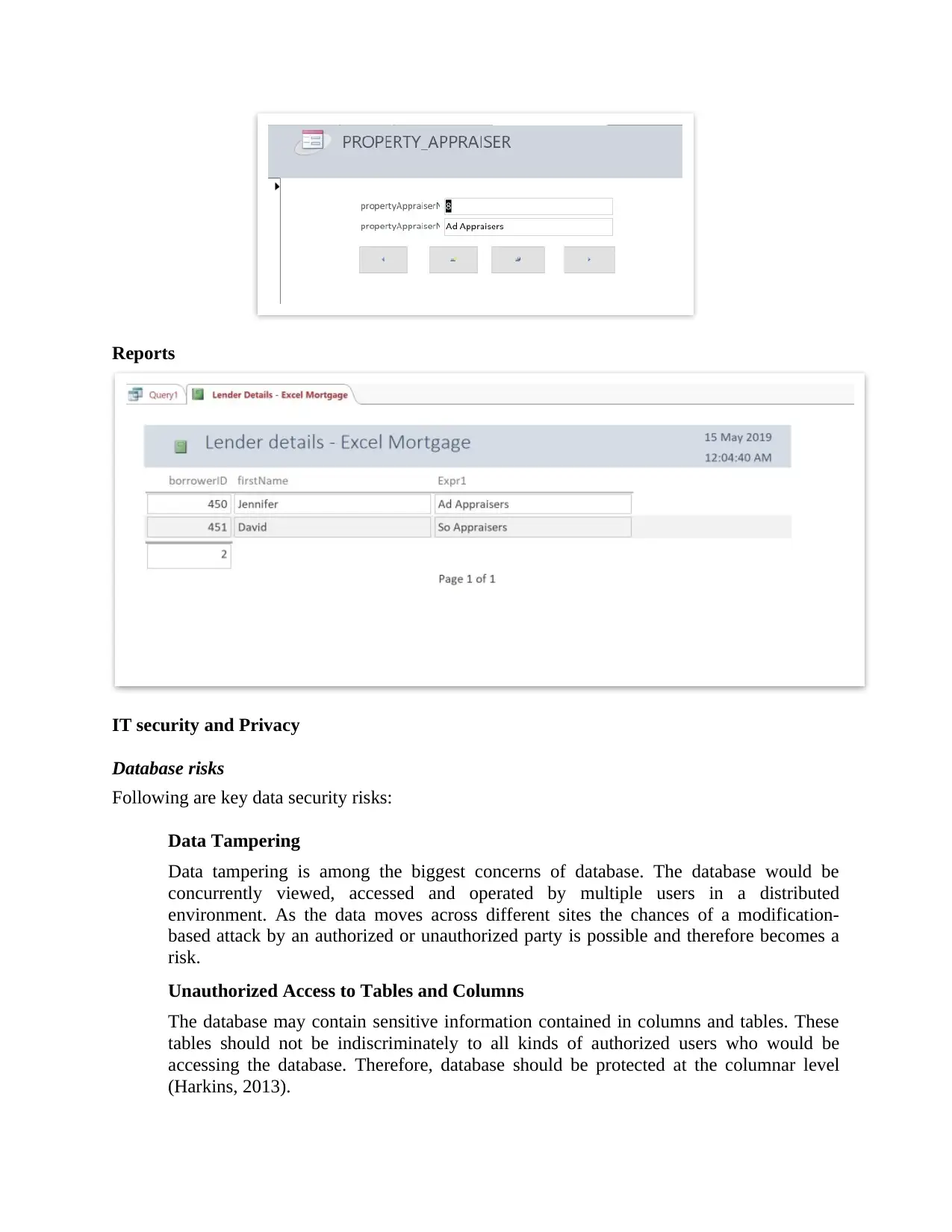
Reports
IT security and Privacy
Database risks
Following are key data security risks:
Data Tampering
Data tampering is among the biggest concerns of database. The database would be
concurrently viewed, accessed and operated by multiple users in a distributed
environment. As the data moves across different sites the chances of a modification-
based attack by an authorized or unauthorized party is possible and therefore becomes a
risk.
Unauthorized Access to Tables and Columns
The database may contain sensitive information contained in columns and tables. These
tables should not be indiscriminately to all kinds of authorized users who would be
accessing the database. Therefore, database should be protected at the columnar level
(Harkins, 2013).
IT security and Privacy
Database risks
Following are key data security risks:
Data Tampering
Data tampering is among the biggest concerns of database. The database would be
concurrently viewed, accessed and operated by multiple users in a distributed
environment. As the data moves across different sites the chances of a modification-
based attack by an authorized or unauthorized party is possible and therefore becomes a
risk.
Unauthorized Access to Tables and Columns
The database may contain sensitive information contained in columns and tables. These
tables should not be indiscriminately to all kinds of authorized users who would be
accessing the database. Therefore, database should be protected at the columnar level
(Harkins, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Unauthorized Access to Data Rows
Certain data rows could contain highly confidential information and therefore being
available to indiscriminate users makes it highly risk. For instance, in shared database
environment, the business should only have access to their own data and not be allowed
to viewed data of customers such as their passwords of transaction details.
Lack of Accountability
Another major risk with database system arises out of a poorly setup database which
makes it difficult to track user’s activities. If they cannot track the user’s activities then
would not be able to monitor their wrongdoing and hence, they cannot be held
accountable.
Data Security Requirements
Confidentiality
A secure system would ensure data confidentiality. This typically means that only the
individuals meant to are able to see the data they are supposed to. Confidentiality has
many aspects such as privacy for communications, storage of sensitive data, authorization
of users, authenticated users and so on.
Privacy of Communications
The database system needs to be in control of confidential information being stored in the
database. These includes datasets such as employment records, credit information and
health records. It also needs to keep copyright, patent and other corporate information
such as trade secrets about processes and products, marketing plans, ideas and product
launches a secret from unauthorized people.
Secure Storage of Sensitive Data
Once the data has been entered, then the data’s privacy, integrity and confidentiality must
be protected wherever the data resides.
Authentication
One of the simplest concepts in database security is their authentication, which is nothing
but a process on how the system verifies the identity of the user. A user would respond to
such request by providing a proof of identity or a token for authentication.
A user could have several different kinds of authorization on parts of their database.
Following are the authorization rights.
o Read authorization – This allows for reading, but does not permit modification of
data.
o Insert authorization – This allows for insertion of a new data, but does not permit
modification of data.
o Update authorization – This allows for data modification but does not permit data
deletion
o Delete authorization – This permits data deletion
Certain data rows could contain highly confidential information and therefore being
available to indiscriminate users makes it highly risk. For instance, in shared database
environment, the business should only have access to their own data and not be allowed
to viewed data of customers such as their passwords of transaction details.
Lack of Accountability
Another major risk with database system arises out of a poorly setup database which
makes it difficult to track user’s activities. If they cannot track the user’s activities then
would not be able to monitor their wrongdoing and hence, they cannot be held
accountable.
Data Security Requirements
Confidentiality
A secure system would ensure data confidentiality. This typically means that only the
individuals meant to are able to see the data they are supposed to. Confidentiality has
many aspects such as privacy for communications, storage of sensitive data, authorization
of users, authenticated users and so on.
Privacy of Communications
The database system needs to be in control of confidential information being stored in the
database. These includes datasets such as employment records, credit information and
health records. It also needs to keep copyright, patent and other corporate information
such as trade secrets about processes and products, marketing plans, ideas and product
launches a secret from unauthorized people.
Secure Storage of Sensitive Data
Once the data has been entered, then the data’s privacy, integrity and confidentiality must
be protected wherever the data resides.
Authentication
One of the simplest concepts in database security is their authentication, which is nothing
but a process on how the system verifies the identity of the user. A user would respond to
such request by providing a proof of identity or a token for authentication.
A user could have several different kinds of authorization on parts of their database.
Following are the authorization rights.
o Read authorization – This allows for reading, but does not permit modification of
data.
o Insert authorization – This allows for insertion of a new data, but does not permit
modification of data.
o Update authorization – This allows for data modification but does not permit data
deletion
o Delete authorization – This permits data deletion

A user could be assigned to all, none or even a combination of the authorization types mentioned
above. There are other forms of authorization given to a user too, these related to the
modification of database schema:
Index authorization allows for deletion and creation of indexes.
Resource authorization allows for creation of new relations.
Alteration authorization allows for deletion or addition of relation attributes.
Drop authorization allows for deletion of any relations (Hutchinson and Coulthard,
2013).
Conclusion
This report has provided an overview of justification of using a database instead of a spreadsheet
by detailing the benefits of a database. Along with this, the report provides a normalized
structure of the database which is the base of any database. In order to provide the usefulness of
proposed database, various entry forms and reports are built using MS Access which proves that
database implementation is a wise decision. It minimizes any kind of data inconsistency and
redundancy. The report provides an insight over the database security and how it can be
implemented in the database to prevent database breach or authorized data access.
References
Date, C., Kannan, A. and Swamynathan, S. (2006). An introduction to database systems. 1st ed.
Noida: Dorling Kindersley, pp.12-14.
Guan, K. (2012). Microsoft Access. 1st ed. Sandgate, Qld.: Knowledge Books and Software,
pp.12-14.
Harkins, S. (2013). Using Microsoft Access 97. 1st ed. Indianapolis, IN: Que, pp.14-19.
Hutchinson, S. and Coulthard, G. (2013). Microsoft Access 2000. 1st ed. Boston, Mass.:
Irwin/McGraw-Hill, pp.45-47.
Middleton, J. (2012). Microsoft Access. 1st ed. London: Pitman, pp.34-36.
above. There are other forms of authorization given to a user too, these related to the
modification of database schema:
Index authorization allows for deletion and creation of indexes.
Resource authorization allows for creation of new relations.
Alteration authorization allows for deletion or addition of relation attributes.
Drop authorization allows for deletion of any relations (Hutchinson and Coulthard,
2013).
Conclusion
This report has provided an overview of justification of using a database instead of a spreadsheet
by detailing the benefits of a database. Along with this, the report provides a normalized
structure of the database which is the base of any database. In order to provide the usefulness of
proposed database, various entry forms and reports are built using MS Access which proves that
database implementation is a wise decision. It minimizes any kind of data inconsistency and
redundancy. The report provides an insight over the database security and how it can be
implemented in the database to prevent database breach or authorized data access.
References
Date, C., Kannan, A. and Swamynathan, S. (2006). An introduction to database systems. 1st ed.
Noida: Dorling Kindersley, pp.12-14.
Guan, K. (2012). Microsoft Access. 1st ed. Sandgate, Qld.: Knowledge Books and Software,
pp.12-14.
Harkins, S. (2013). Using Microsoft Access 97. 1st ed. Indianapolis, IN: Que, pp.14-19.
Hutchinson, S. and Coulthard, G. (2013). Microsoft Access 2000. 1st ed. Boston, Mass.:
Irwin/McGraw-Hill, pp.45-47.
Middleton, J. (2012). Microsoft Access. 1st ed. London: Pitman, pp.34-36.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





