Desklib - Online Library for Study Material and Solved Assignments
VerifiedAdded on 2023/04/21
|12
|2697
|384
AI Summary
Desklib is an online library that offers study material, solved assignments, essays, dissertations, and more. It provides a wide range of content for various subjects and courses. Whether you need help with your assignments or want to explore additional study material, Desklib has you covered. Find relevant content for your courses and subjects, and enhance your learning experience.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Question 2.............................................................................................................................................3
Question 3.............................................................................................................................................3
Question 4.............................................................................................................................................4
Question 5.............................................................................................................................................4
Question 6.............................................................................................................................................5
Question 7.............................................................................................................................................5
Question 8.............................................................................................................................................5
References.............................................................................................................................................6
Question 2.............................................................................................................................................3
Question 3.............................................................................................................................................3
Question 4.............................................................................................................................................4
Question 5.............................................................................................................................................4
Question 6.............................................................................................................................................5
Question 7.............................................................................................................................................5
Question 8.............................................................................................................................................5
References.............................................................................................................................................6

Question 2
2a. Amazon performs extraordinarily productively estimated against income per guest, which
is one of the key measures for any business site, regardless of whether it's a media site, web
crawler, informal community or an exchange retailer or offers travel or budgetary
administrations
ii. Merits of cloud storage
Usability: The user can directly access the data of the Cloud storage service, which
can be used for accessing the desktop folders of the macs and PCs.
Accessibility is used on accessing the stored files which can be used from anywhere
via an internet connection(NT, 2014).
Demerits of cloud storage
Usability refers to accessing the data of loss storage folders. This will permanently
move your documents from its original folder to the location of the cloud storage.
In the cloud storage, the data cannot be accessed without using the internet
connection(Sullivan, 2017).
Question 3
a. Assume the company temperature of the entire parameters, then calculate the
population of the standard deviations.
i. To check the all items count towards the length all rundowns are allowable, in
light of the fact that the issue is characterized notwithstanding for the vacant
rundown of the length to be consider as zero. The vacant rundown isn't an
allowable information, in light of the fact that figuring the mean would require
a division by zero, as there are no number in the rundown.
ii. To find the 75% milliseconds as a percentage of the target repose time we are
calculate the assumable values is,
6
8 X 100 = 75%
2a. Amazon performs extraordinarily productively estimated against income per guest, which
is one of the key measures for any business site, regardless of whether it's a media site, web
crawler, informal community or an exchange retailer or offers travel or budgetary
administrations
ii. Merits of cloud storage
Usability: The user can directly access the data of the Cloud storage service, which
can be used for accessing the desktop folders of the macs and PCs.
Accessibility is used on accessing the stored files which can be used from anywhere
via an internet connection(NT, 2014).
Demerits of cloud storage
Usability refers to accessing the data of loss storage folders. This will permanently
move your documents from its original folder to the location of the cloud storage.
In the cloud storage, the data cannot be accessed without using the internet
connection(Sullivan, 2017).
Question 3
a. Assume the company temperature of the entire parameters, then calculate the
population of the standard deviations.
i. To check the all items count towards the length all rundowns are allowable, in
light of the fact that the issue is characterized notwithstanding for the vacant
rundown of the length to be consider as zero. The vacant rundown isn't an
allowable information, in light of the fact that figuring the mean would require
a division by zero, as there are no number in the rundown.
ii. To find the 75% milliseconds as a percentage of the target repose time we are
calculate the assumable values is,
6
8 X 100 = 75%
Hence a 25% decrease in latency results in a 75% increase in the time.
Available to process the response.
b. let as consider the values of the borderline temperature can be find the everyday
temperature hot or not) of the input list, and of the output list can be find below table,
Temperature days Comments
[] [] Smallest input: empty list
[14,15,16,17] [] Smallest output: no hot days
[18,19,20] [18.19,20] Largest output: all days are hot
[14,15,16,17,18,19,20] [20,20,21] Borderline temperatures
c. Subproblems to be consider as,Compute the module of list and tuple values (user
inputs). Compute the mean of the list and tuple best aggregation values. Computer the
sum of list and tuple values of aggregation. Subtract the lowest values. Divide the
result on the problems values by 3. Compute the case analysis of mean values of the
list and tuple values.
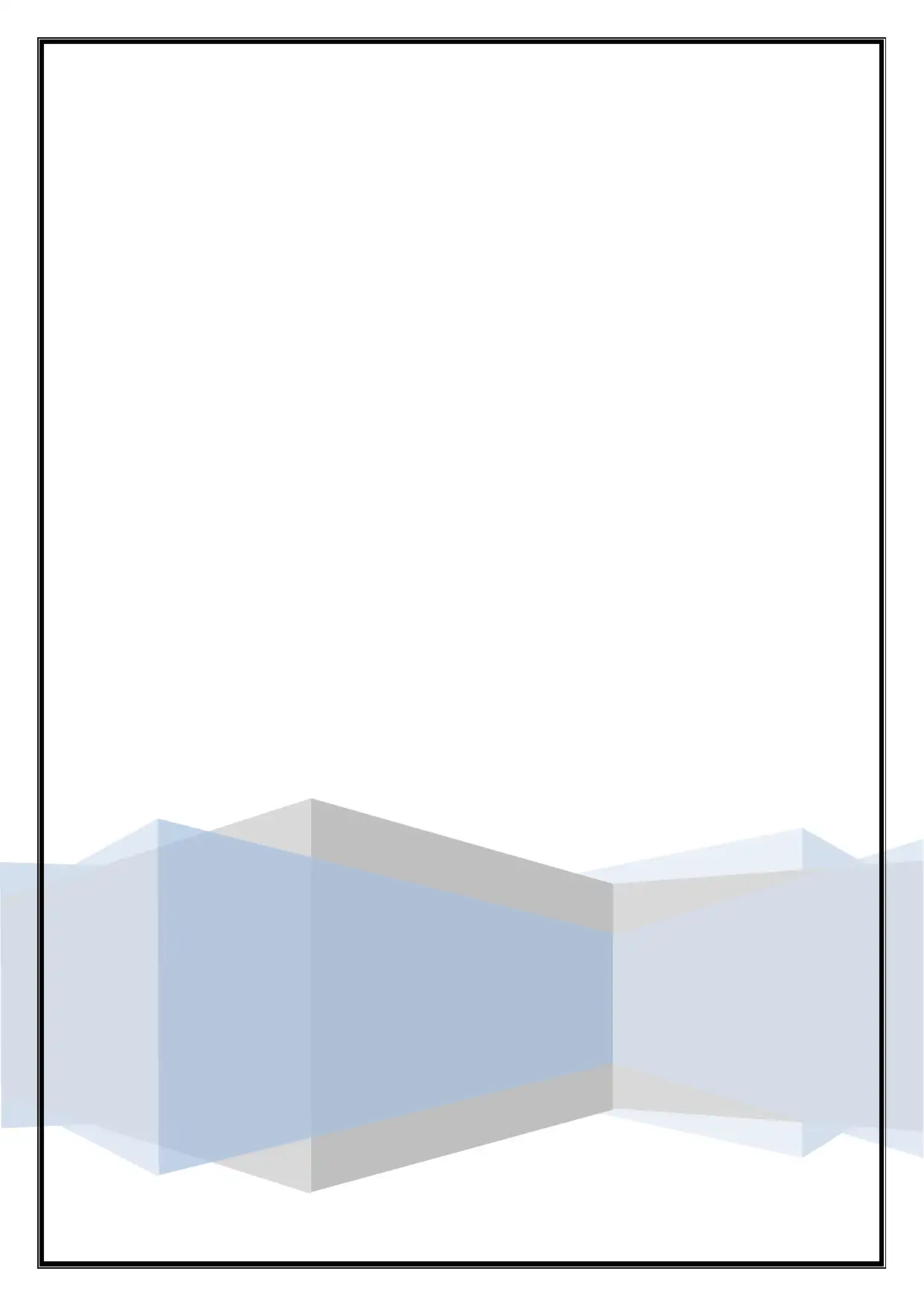
d.
Question 4
a.
Public transport environment
While waiting in a queue environment
At a cinema, or similar place where other are usually quiet.
At church or a worship service
Available to process the response.
b. let as consider the values of the borderline temperature can be find the everyday
temperature hot or not) of the input list, and of the output list can be find below table,
Temperature days Comments
[] [] Smallest input: empty list
[14,15,16,17] [] Smallest output: no hot days
[18,19,20] [18.19,20] Largest output: all days are hot
[14,15,16,17,18,19,20] [20,20,21] Borderline temperatures
c. Subproblems to be consider as,Compute the module of list and tuple values (user
inputs). Compute the mean of the list and tuple best aggregation values. Computer the
sum of list and tuple values of aggregation. Subtract the lowest values. Divide the
result on the problems values by 3. Compute the case analysis of mean values of the
list and tuple values.
d.
Question 4
a.
Public transport environment
While waiting in a queue environment
At a cinema, or similar place where other are usually quiet.
At church or a worship service
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

b) i).
Security and privacy concerns
Manufacturer Defects and No Fault Found
Battery Mortality Issues
iii. Progressively productive utilization of power can be utilized for One
straightforward approach to make the battery last longer is to diminish
pointless control utilization of the cell phone. This can be accomplished by
consequently killing or decreasing the intensity of high-depleting parts of the
versatile phone. High-control batteries is use for enhance its vitality putting
away capacity. Right now, practically all cell phones use lithium-particle
batteries, which have one of the most noteworthy vitality densities of battery
types, implying that they have more vitality for indistinguishable size from
most different sorts. Short charging time is utilized for the One method to
accomplish this is to go through an impetus to speed the compound responses
inside the battery. In any case, impetuses are normally made of valuable
metals, thus they are expensive. Harvest vitality from the earth can be utilized
for the cell phones with vitality reaped from the earth or the individual
conveying it. This incorporates delivering vitality from sunlight based, sound,
water dew and contact. In any case, the measure of vitality gathered with
current innovations is too little to even think about replenishing the power
utilized.
iv. The number of pixels is given by 3888 × 5184 =20155392.
For Convenience, this value is usually rounded down to 10 megapixels.
The aspect ratio is the ratio between the width and height of the image
Sensor. Therefore:
Aspect ratio is width: height
= 3888:5158.
The aspect ratio can be cancelled down by dividing both sides by 1296 (Although,
like me, you may have had to cancel down several times by Smaller numbers) to give an
aspect ratio of 4:2.
iv.
Touch screen, an increasingly natural GUI can be actualized on a portable telephone.
This enables clients to control the two designs and content.
Physical catches are expensive and should be physically planned into the cell phone
and electrically associated
Security and privacy concerns
Manufacturer Defects and No Fault Found
Battery Mortality Issues
iii. Progressively productive utilization of power can be utilized for One
straightforward approach to make the battery last longer is to diminish
pointless control utilization of the cell phone. This can be accomplished by
consequently killing or decreasing the intensity of high-depleting parts of the
versatile phone. High-control batteries is use for enhance its vitality putting
away capacity. Right now, practically all cell phones use lithium-particle
batteries, which have one of the most noteworthy vitality densities of battery
types, implying that they have more vitality for indistinguishable size from
most different sorts. Short charging time is utilized for the One method to
accomplish this is to go through an impetus to speed the compound responses
inside the battery. In any case, impetuses are normally made of valuable
metals, thus they are expensive. Harvest vitality from the earth can be utilized
for the cell phones with vitality reaped from the earth or the individual
conveying it. This incorporates delivering vitality from sunlight based, sound,
water dew and contact. In any case, the measure of vitality gathered with
current innovations is too little to even think about replenishing the power
utilized.
iv. The number of pixels is given by 3888 × 5184 =20155392.
For Convenience, this value is usually rounded down to 10 megapixels.
The aspect ratio is the ratio between the width and height of the image
Sensor. Therefore:
Aspect ratio is width: height
= 3888:5158.
The aspect ratio can be cancelled down by dividing both sides by 1296 (Although,
like me, you may have had to cancel down several times by Smaller numbers) to give an
aspect ratio of 4:2.
iv.
Touch screen, an increasingly natural GUI can be actualized on a portable telephone.
This enables clients to control the two designs and content.
Physical catches are expensive and should be physically planned into the cell phone
and electrically associated

Question 5
a. Creating the two drawings can consist the values of nobbies1 and hobbies 2.
Nobbies 1= {‘football’, ballet, kickboxing}
Nobbies 2=’judo ’the implementing object values can find each values and finally
draw the graph in python.
i).You should actualize and compile (not execute) the class definition for each class in the
python code. The reason and interface for the class is reported as python doc remarks and
should be utilized for the football class name. A Class Header Is defined as recognizing
information: Class name, football, artful dance, kickboxing, and so on. Strategy headers is
used for Strategy (Operation) name - must compare precisely with the name appeared on the
class outline. Reason - Describe the motivation behind this task. Must be a succinct, clear
English sentence utilizing terms from the issue python space. Parameters and return types -
name, type, and depiction. Special cases thrown\ can be pursues as (Design by Contract
groups) Pre-and Post-conditions (with the exception of getter/setter strategies). Suggested:
utilize custom labels (Error-Checking groups).
B i).
Draw rundown and move the situation of the tuples on second rundown after that
move the situation of the third rundown. The code is shorter and therefore increasingly
discernible. They are less demanding to change, making it more uncertain that blunders are
presented. The expressly reflects the deterioration of an issue and subsequently is less
demanding to get it.
ii.A movement that begins with an issue and results inaprogram, by means of disintegration,
designs what's more, calculations. You will adapt new examples for producing and handling
data that is put away in records. Bundle code that tackles a sub-issue.
Numeracy
Critical thinking
Correspondence
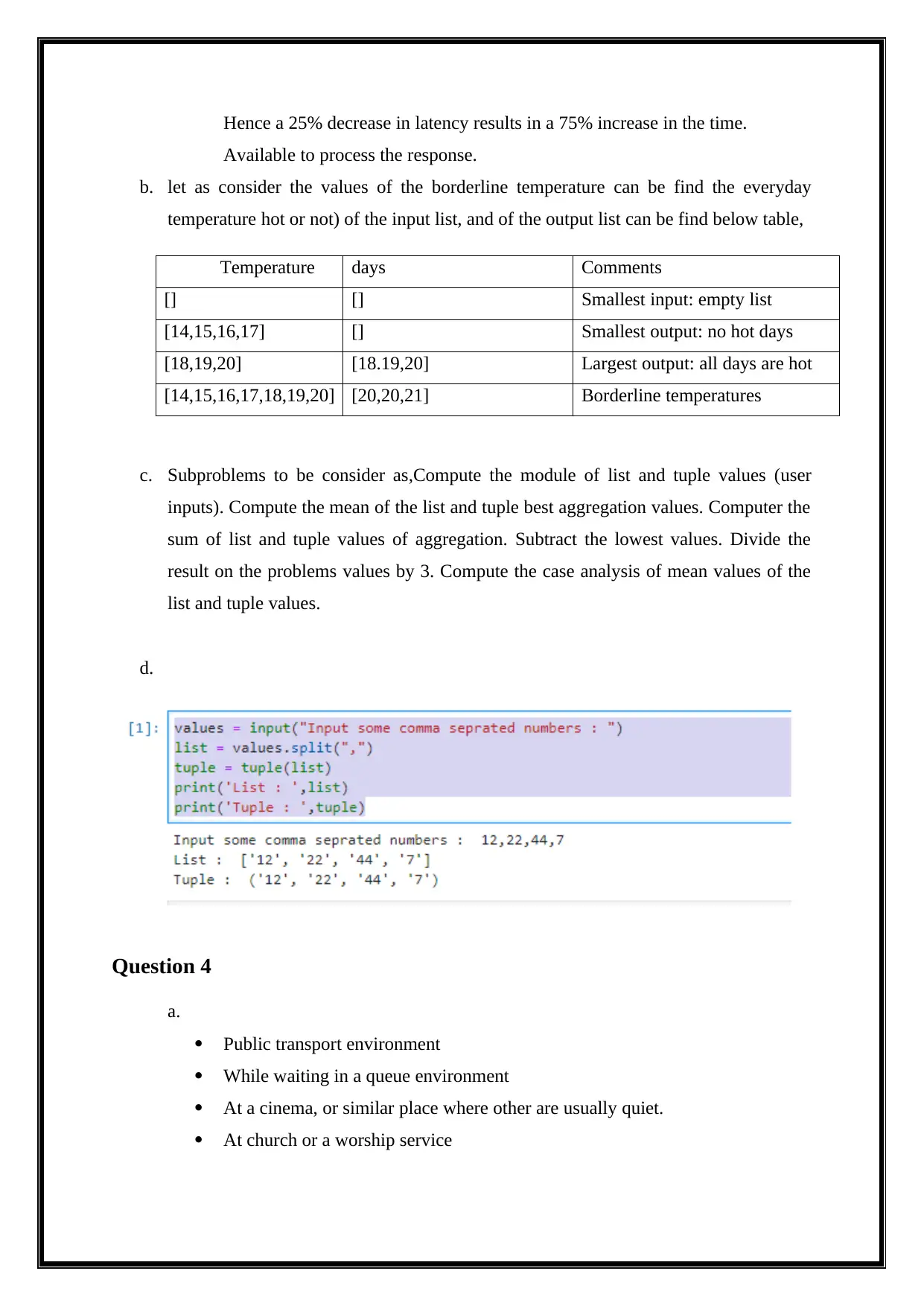
iii. Height = float(input(‘Height: '))
Radian = float(input(‘Radius: '))
a. Creating the two drawings can consist the values of nobbies1 and hobbies 2.
Nobbies 1= {‘football’, ballet, kickboxing}
Nobbies 2=’judo ’the implementing object values can find each values and finally
draw the graph in python.
i).You should actualize and compile (not execute) the class definition for each class in the
python code. The reason and interface for the class is reported as python doc remarks and
should be utilized for the football class name. A Class Header Is defined as recognizing
information: Class name, football, artful dance, kickboxing, and so on. Strategy headers is
used for Strategy (Operation) name - must compare precisely with the name appeared on the
class outline. Reason - Describe the motivation behind this task. Must be a succinct, clear
English sentence utilizing terms from the issue python space. Parameters and return types -
name, type, and depiction. Special cases thrown\ can be pursues as (Design by Contract
groups) Pre-and Post-conditions (with the exception of getter/setter strategies). Suggested:
utilize custom labels (Error-Checking groups).
B i).
Draw rundown and move the situation of the tuples on second rundown after that
move the situation of the third rundown. The code is shorter and therefore increasingly
discernible. They are less demanding to change, making it more uncertain that blunders are
presented. The expressly reflects the deterioration of an issue and subsequently is less
demanding to get it.
ii.A movement that begins with an issue and results inaprogram, by means of disintegration,
designs what's more, calculations. You will adapt new examples for producing and handling
data that is put away in records. Bundle code that tackles a sub-issue.
Numeracy
Critical thinking
Correspondence
iii. Height = float(input(‘Height: '))
Radian = float(input(‘Radius: '))
volume = radian * radian * 3.14158 * height
Print ("number of cookies is: ", volume)
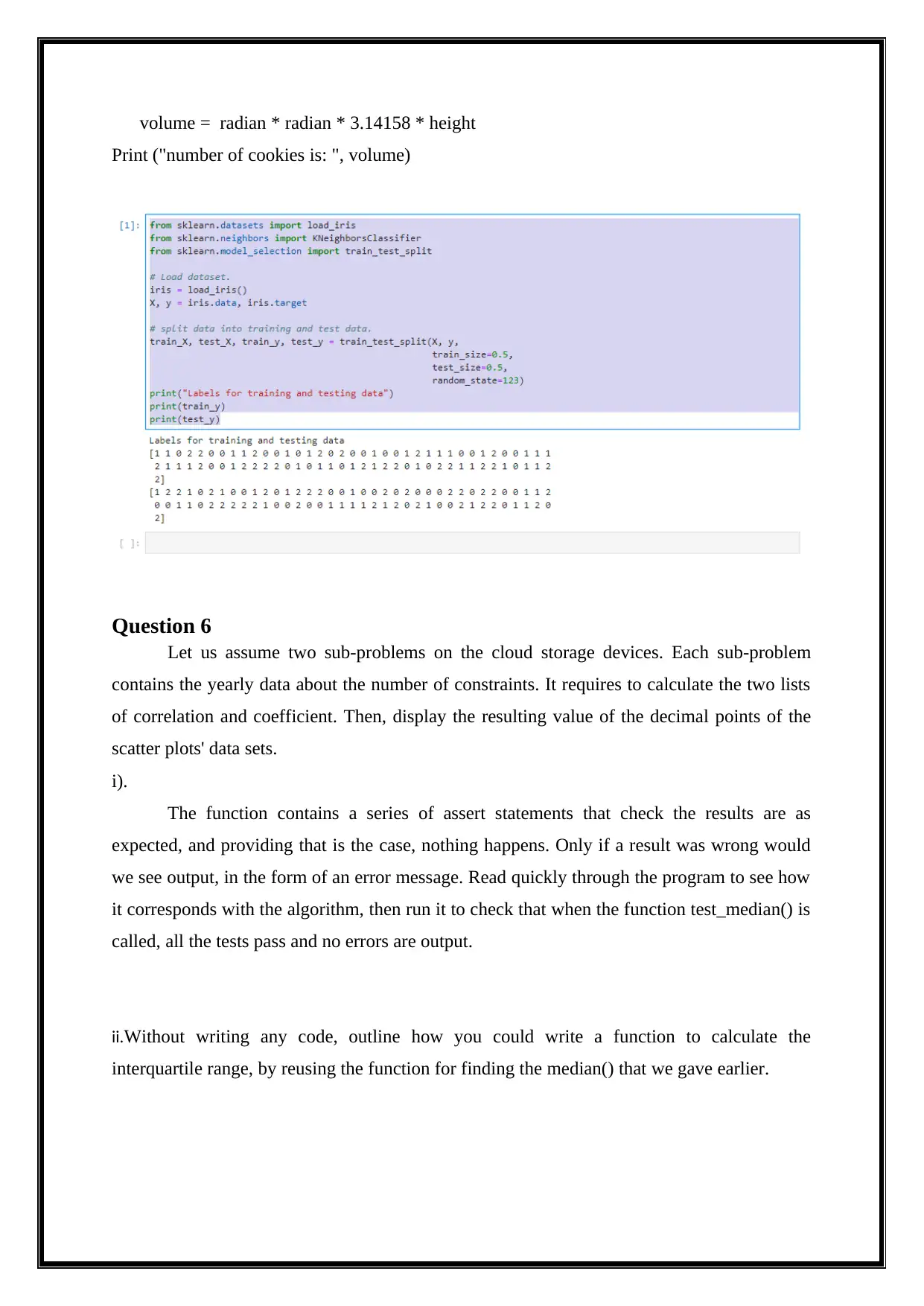
Question 6
Let us assume two sub-problems on the cloud storage devices. Each sub-problem
contains the yearly data about the number of constraints. It requires to calculate the two lists
of correlation and coefficient. Then, display the resulting value of the decimal points of the
scatter plots' data sets.
i).
The function contains a series of assert statements that check the results are as
expected, and providing that is the case, nothing happens. Only if a result was wrong would
we see output, in the form of an error message. Read quickly through the program to see how
it corresponds with the algorithm, then run it to check that when the function test_median() is
called, all the tests pass and no errors are output.
ii.Without writing any code, outline how you could write a function to calculate the
interquartile range, by reusing the function for finding the median() that we gave earlier.
Print ("number of cookies is: ", volume)
Question 6
Let us assume two sub-problems on the cloud storage devices. Each sub-problem
contains the yearly data about the number of constraints. It requires to calculate the two lists
of correlation and coefficient. Then, display the resulting value of the decimal points of the
scatter plots' data sets.
i).
The function contains a series of assert statements that check the results are as
expected, and providing that is the case, nothing happens. Only if a result was wrong would
we see output, in the form of an error message. Read quickly through the program to see how
it corresponds with the algorithm, then run it to check that when the function test_median() is
called, all the tests pass and no errors are output.
ii.Without writing any code, outline how you could write a function to calculate the
interquartile range, by reusing the function for finding the median() that we gave earlier.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
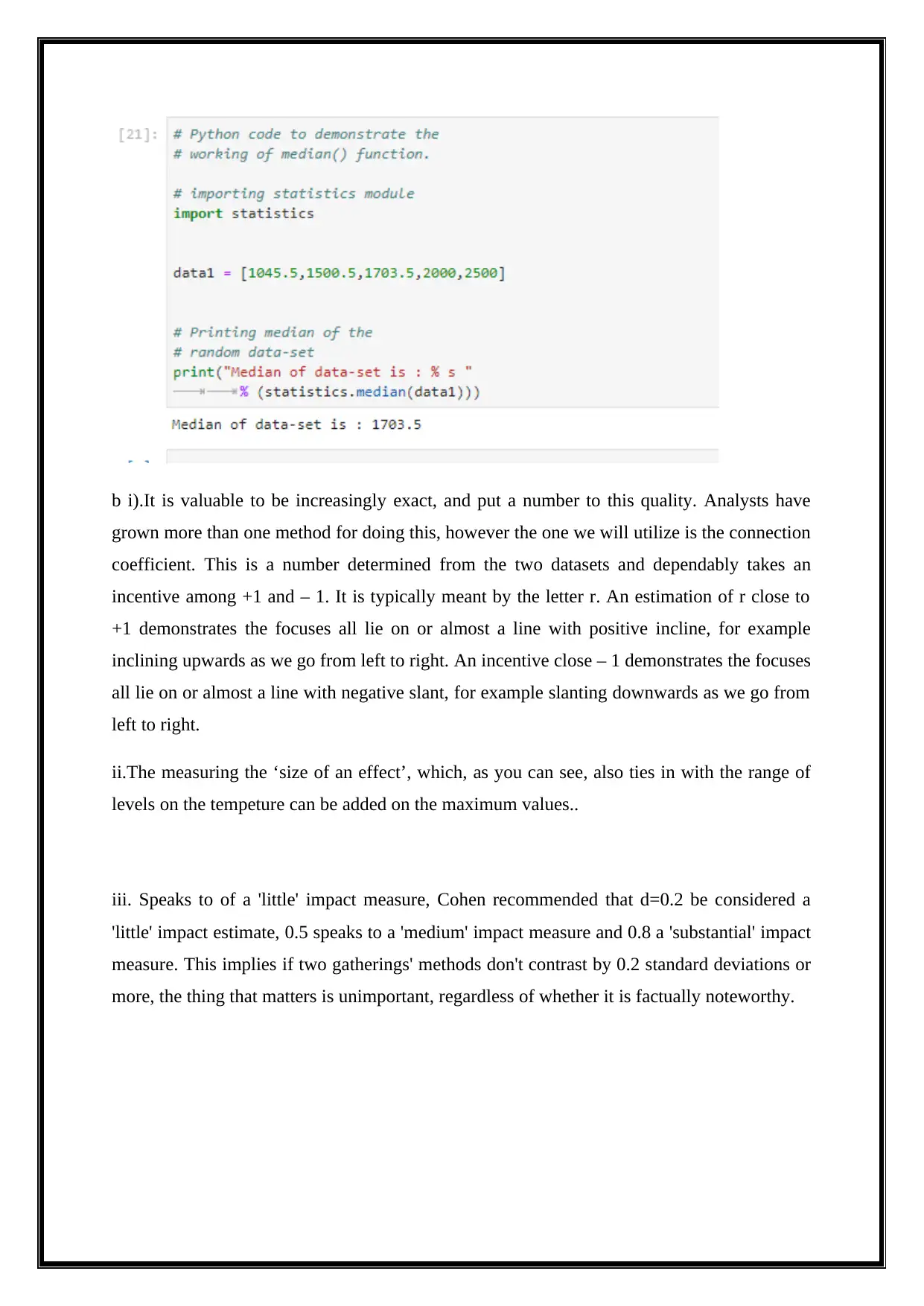
b i).It is valuable to be increasingly exact, and put a number to this quality. Analysts have
grown more than one method for doing this, however the one we will utilize is the connection
coefficient. This is a number determined from the two datasets and dependably takes an
incentive among +1 and – 1. It is typically meant by the letter r. An estimation of r close to
+1 demonstrates the focuses all lie on or almost a line with positive incline, for example
inclining upwards as we go from left to right. An incentive close – 1 demonstrates the focuses
all lie on or almost a line with negative slant, for example slanting downwards as we go from
left to right.
ii.The measuring the ‘size of an effect’, which, as you can see, also ties in with the range of
levels on the tempeture can be added on the maximum values..
iii. Speaks to of a 'little' impact measure, Cohen recommended that d=0.2 be considered a
'little' impact estimate, 0.5 speaks to a 'medium' impact measure and 0.8 a 'substantial' impact
measure. This implies if two gatherings' methods don't contrast by 0.2 standard deviations or
more, the thing that matters is unimportant, regardless of whether it is factually noteworthy.
grown more than one method for doing this, however the one we will utilize is the connection
coefficient. This is a number determined from the two datasets and dependably takes an
incentive among +1 and – 1. It is typically meant by the letter r. An estimation of r close to
+1 demonstrates the focuses all lie on or almost a line with positive incline, for example
inclining upwards as we go from left to right. An incentive close – 1 demonstrates the focuses
all lie on or almost a line with negative slant, for example slanting downwards as we go from
left to right.
ii.The measuring the ‘size of an effect’, which, as you can see, also ties in with the range of
levels on the tempeture can be added on the maximum values..
iii. Speaks to of a 'little' impact measure, Cohen recommended that d=0.2 be considered a
'little' impact estimate, 0.5 speaks to a 'medium' impact measure and 0.8 a 'substantial' impact
measure. This implies if two gatherings' methods don't contrast by 0.2 standard deviations or
more, the thing that matters is unimportant, regardless of whether it is factually noteworthy.
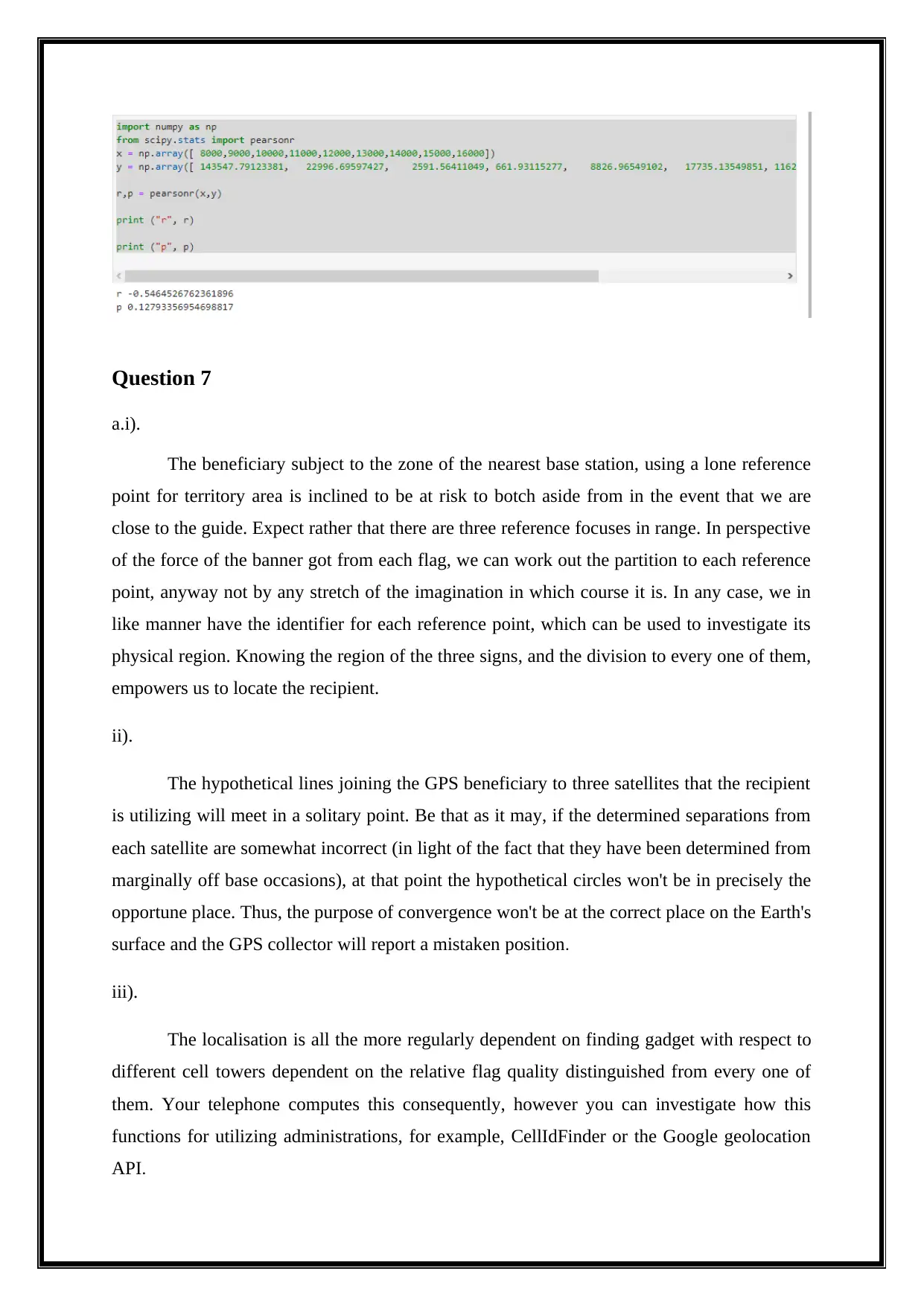
Question 7
a.i).
The beneficiary subject to the zone of the nearest base station, using a lone reference
point for territory area is inclined to be at risk to botch aside from in the event that we are
close to the guide. Expect rather that there are three reference focuses in range. In perspective
of the force of the banner got from each flag, we can work out the partition to each reference
point, anyway not by any stretch of the imagination in which course it is. In any case, we in
like manner have the identifier for each reference point, which can be used to investigate its
physical region. Knowing the region of the three signs, and the division to every one of them,
empowers us to locate the recipient.
ii).
The hypothetical lines joining the GPS beneficiary to three satellites that the recipient
is utilizing will meet in a solitary point. Be that as it may, if the determined separations from
each satellite are somewhat incorrect (in light of the fact that they have been determined from
marginally off base occasions), at that point the hypothetical circles won't be in precisely the
opportune place. Thus, the purpose of convergence won't be at the correct place on the Earth's
surface and the GPS collector will report a mistaken position.
iii).
The localisation is all the more regularly dependent on finding gadget with respect to
different cell towers dependent on the relative flag quality distinguished from every one of
them. Your telephone computes this consequently, however you can investigate how this
functions for utilizing administrations, for example, CellIdFinder or the Google geolocation
API.
a.i).
The beneficiary subject to the zone of the nearest base station, using a lone reference
point for territory area is inclined to be at risk to botch aside from in the event that we are
close to the guide. Expect rather that there are three reference focuses in range. In perspective
of the force of the banner got from each flag, we can work out the partition to each reference
point, anyway not by any stretch of the imagination in which course it is. In any case, we in
like manner have the identifier for each reference point, which can be used to investigate its
physical region. Knowing the region of the three signs, and the division to every one of them,
empowers us to locate the recipient.
ii).
The hypothetical lines joining the GPS beneficiary to three satellites that the recipient
is utilizing will meet in a solitary point. Be that as it may, if the determined separations from
each satellite are somewhat incorrect (in light of the fact that they have been determined from
marginally off base occasions), at that point the hypothetical circles won't be in precisely the
opportune place. Thus, the purpose of convergence won't be at the correct place on the Earth's
surface and the GPS collector will report a mistaken position.
iii).
The localisation is all the more regularly dependent on finding gadget with respect to
different cell towers dependent on the relative flag quality distinguished from every one of
them. Your telephone computes this consequently, however you can investigate how this
functions for utilizing administrations, for example, CellIdFinder or the Google geolocation
API.

B.i. The single direction beneficiary recognized the area of the vehicle in which it was
introduced and rendered its area on an advanced guide. A client would enter the location of a
goal, or a halfway location, for example, a postcode, and the PC would geocode it to a
relating physical area, recognized as a lot of scope and longitude directions of two method for
the GPS area.
ii.The two route correspondence of uninformed the area of recipients, cell-tower localisation
may uncover the area of the beneficiary back to the system, through the cell towers.
Likewise, correspondence specialist organizations may hold this data and connect it with you,
which implies that cell-tower localisation may have suggestions for individual security.
Question 8
ii.The 16 years old student, whose name was not released because he's minor, was arrested
following an investigation launched by local law enforcement, with assistance from a
colonial country task force and the US secret server of the KTVU reported. The reports can
be mention on the first started to trickles into police two weeks ago, when teachers in the
mount Diablo unified schools district started receiving suspicious emails in their inbox, as it
turns out, they were part of a phishing attempt launched of the student. The colonial was
police has been reported on at least one teacher did enter their information, which allowed the
student to access the mount Diablo unified schools District IT networks and in trun the
schools grading system.
Ii.The high school student can be hacked on the emails on targeting teacher emails and
attempt the change in grade to the portal. The university have provides for the username and
password on the one portal and can be access on the anytime so can be easy to change the
grade and not secure on the information. Protect the networks on the IT system
B i).
The punishing attacks on the teenager student can be used for law enforcement caught wind
of the scheme; they obtained search warrants for IP addresses associated with the site in the
phishing email. After that, it was a matter of what Concord Police Financial Crimes
Supervisor Sgt. Carl Cruz described as “good old-fashioned police detective work” to trace it
to the student’s address.
introduced and rendered its area on an advanced guide. A client would enter the location of a
goal, or a halfway location, for example, a postcode, and the PC would geocode it to a
relating physical area, recognized as a lot of scope and longitude directions of two method for
the GPS area.
ii.The two route correspondence of uninformed the area of recipients, cell-tower localisation
may uncover the area of the beneficiary back to the system, through the cell towers.
Likewise, correspondence specialist organizations may hold this data and connect it with you,
which implies that cell-tower localisation may have suggestions for individual security.
Question 8
ii.The 16 years old student, whose name was not released because he's minor, was arrested
following an investigation launched by local law enforcement, with assistance from a
colonial country task force and the US secret server of the KTVU reported. The reports can
be mention on the first started to trickles into police two weeks ago, when teachers in the
mount Diablo unified schools district started receiving suspicious emails in their inbox, as it
turns out, they were part of a phishing attempt launched of the student. The colonial was
police has been reported on at least one teacher did enter their information, which allowed the
student to access the mount Diablo unified schools District IT networks and in trun the
schools grading system.
Ii.The high school student can be hacked on the emails on targeting teacher emails and
attempt the change in grade to the portal. The university have provides for the username and
password on the one portal and can be access on the anytime so can be easy to change the
grade and not secure on the information. Protect the networks on the IT system
B i).
The punishing attacks on the teenager student can be used for law enforcement caught wind
of the scheme; they obtained search warrants for IP addresses associated with the site in the
phishing email. After that, it was a matter of what Concord Police Financial Crimes
Supervisor Sgt. Carl Cruz described as “good old-fashioned police detective work” to trace it
to the student’s address.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ii. The punishing attacks on the California police has arrest the teenage student and record
Police say a student at Ignacio Valley High School targeted teachers with a phishing scam
and hacked into the Mount Diablo Unified School District computer system in order to
change his grades as well as those of other students.
Concord police say they called in the U.S. Secret Service and a Contra Costa
County task force when they first got the report two weeks ago. The student, whose name is
not being released because he's a juvenile, was arrested Wednesday on 14 felony counts, after
investigators say they tracked down the hacking attack to the student's home.
"We wrote numerous search warrants to get the IP addresses of the possible phishing site
email.
References
Doc.ic.ac.uk. (2019). The CIA principle. [online] Available at:
https://www.doc.ic.ac.uk/~ajs300/security/CIA.htm [Accessed 5 Jan. 2019].
Police say a student at Ignacio Valley High School targeted teachers with a phishing scam
and hacked into the Mount Diablo Unified School District computer system in order to
change his grades as well as those of other students.
Concord police say they called in the U.S. Secret Service and a Contra Costa
County task force when they first got the report two weeks ago. The student, whose name is
not being released because he's a juvenile, was arrested Wednesday on 14 felony counts, after
investigators say they tracked down the hacking attack to the student's home.
"We wrote numerous search warrants to get the IP addresses of the possible phishing site
email.
References
Doc.ic.ac.uk. (2019). The CIA principle. [online] Available at:
https://www.doc.ic.ac.uk/~ajs300/security/CIA.htm [Accessed 5 Jan. 2019].

NT, B. (2014). 5 advantages and disadvantages of Cloud Storage. [online] Big Data Made
Simple. Available at: https://bigdata-madesimple.com/5-advantages-and-disadvantages-of-
cloud-storage/ [Accessed 5 Jan. 2019].
Rouse, M. (2019). What is confidentiality, integrity, and availability (CIA triad)?. [online]
WhatIs.com. Available at: https://whatis.techtarget.com/definition/Confidentiality-integrity-
and-availability-CIA [Accessed 5 Jan. 2019].
Sullivan, D. (2017). The Risks and Benefits of Cloud Storage. [online] Cloudwards. Available
at: https://www.cloudwards.net/the-risks-and-benefits-of-cloud-storage/ [Accessed 5 Jan.
2019].
Simple. Available at: https://bigdata-madesimple.com/5-advantages-and-disadvantages-of-
cloud-storage/ [Accessed 5 Jan. 2019].
Rouse, M. (2019). What is confidentiality, integrity, and availability (CIA triad)?. [online]
WhatIs.com. Available at: https://whatis.techtarget.com/definition/Confidentiality-integrity-
and-availability-CIA [Accessed 5 Jan. 2019].
Sullivan, D. (2017). The Risks and Benefits of Cloud Storage. [online] Cloudwards. Available
at: https://www.cloudwards.net/the-risks-and-benefits-of-cloud-storage/ [Accessed 5 Jan.
2019].
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.