Technology for Detecting & Preventing Financial Statement Fraud in UAE
VerifiedAdded on 2023/05/28
|35
|6198
|385
Project
AI Summary
This project investigates the impact of technology on the detection and prevention of financial statement fraud within organizations in the UAE. Data was collected from 125 managerial employees across various UAE organizations through questionnaires and analyzed using regression analysis in SPSS. The study identifies different types of financial statement fraud, evaluates technological improvements in accounting, investigates techniques used for fraud detection, assesses challenges in implementing fraud detection technologies, and analyzes measures to improve fraud detection performance. The findings indicate a significant positive relationship between fraud prevention techniques and the detection of financial statement fraud, supporting the alternative hypothesis that technology has a significant impact on preventing and detecting financial statement fraud in the UAE. The research also references fraud theories such as the fraud triangle and fraud diamond to provide a theoretical underpinning to the practical applications of technology.

1
Technology and Financial Statement Fraud
Technology and Financial Statement Fraud
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Abstract
The aim of the study is to evaluate the effect of technology in the detection and prevention of
financial statement fraud in organizations of UAE. For this purpose, 125 respondents have been
selected from different organizations that consist of managerial position employees. The data has
been collected by the use of desk research method and survey through questionnaire method to
attain valid and credible results for the research study. In addition to this, regression analysis has
been conducted on the data collected through survey through questionnaire method by the help
of SPSS. It is found out that there is an acceptance of alternative hypothesis as there is a presence
of significant relationship among prevention techniques and detect of financial statement fraud in
organizations of UAE. It is also found out that there is a presence of positive correlation between
the dependent and independent variable that is there is a significant impact of technology on
detection and prevention of financial statement fraud.
Abstract
The aim of the study is to evaluate the effect of technology in the detection and prevention of
financial statement fraud in organizations of UAE. For this purpose, 125 respondents have been
selected from different organizations that consist of managerial position employees. The data has
been collected by the use of desk research method and survey through questionnaire method to
attain valid and credible results for the research study. In addition to this, regression analysis has
been conducted on the data collected through survey through questionnaire method by the help
of SPSS. It is found out that there is an acceptance of alternative hypothesis as there is a presence
of significant relationship among prevention techniques and detect of financial statement fraud in
organizations of UAE. It is also found out that there is a presence of positive correlation between
the dependent and independent variable that is there is a significant impact of technology on
detection and prevention of financial statement fraud.

3
Table of Contents
Abstract............................................................................................................................................2
Introduction......................................................................................................................................4
Aim and Objectives.....................................................................................................................4
Hypothesis with Theory...............................................................................................................5
Research Questions......................................................................................................................5
Research Rationale......................................................................................................................5
Literature review..............................................................................................................................6
To identify different types of frauds that occurs in financial statements....................................6
To evaluate various technological improvements in accounting.................................................7
Investigation of different techniques which are being used to detect financial statement fraud. 8
To evaluate the challenges faced by the organizations in implementation of the technologies
for the detection of the financial statement fraud........................................................................8
To analyze different measures taken to improve the performance of the detection of the
financial statement fraud..............................................................................................................9
Literature gap.............................................................................................................................10
Conceptual framework...............................................................................................................11
Research Methodology..................................................................................................................12
Research Limitation...................................................................................................................13
Data analysis and Discussion.........................................................................................................14
Conclusion.....................................................................................................................................28
References......................................................................................................................................29
Appendix........................................................................................................................................31
Questionnaire.............................................................................................................................31
Table of Contents
Abstract............................................................................................................................................2
Introduction......................................................................................................................................4
Aim and Objectives.....................................................................................................................4
Hypothesis with Theory...............................................................................................................5
Research Questions......................................................................................................................5
Research Rationale......................................................................................................................5
Literature review..............................................................................................................................6
To identify different types of frauds that occurs in financial statements....................................6
To evaluate various technological improvements in accounting.................................................7
Investigation of different techniques which are being used to detect financial statement fraud. 8
To evaluate the challenges faced by the organizations in implementation of the technologies
for the detection of the financial statement fraud........................................................................8
To analyze different measures taken to improve the performance of the detection of the
financial statement fraud..............................................................................................................9
Literature gap.............................................................................................................................10
Conceptual framework...............................................................................................................11
Research Methodology..................................................................................................................12
Research Limitation...................................................................................................................13
Data analysis and Discussion.........................................................................................................14
Conclusion.....................................................................................................................................28
References......................................................................................................................................29
Appendix........................................................................................................................................31
Questionnaire.............................................................................................................................31
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
Introduction
Financial statement fraud refers to making modifications in the financial statements of the
companies by the way of addition or omission of the data related to it for the purpose of
projecting a desired financial strength of the company to its stakeholders which is false in nature.
This fraudulent practice has been carried out by the firms to gain the interest of the investors
from whom they appeal to gain a credit. The Forensic accounting Dubai offer services to detect
and avoid such kind of fraud in the organizations as it has huge repercussions at the time of
detected by the authorities (Van Akkeren and Buckby, 2017). There are several firms that offer
forensic accounting Dubai services in UAE. It is also found out that there are several techniques
and technology that has been used by the firms to detect financial statement fraud such as
password protection, digital analysis and firewall protection and so on. It is found out that
emergence and growth of e-commerce and internet has resulted in increasing the exposure to
fraud.
It is essential for the accountants to ensure that the information or computer network should be
accessible by only legitimate users. Passwords are considered as the oldest technique of
computer defense. Technological advancement has helped in the creation of new forms of
password protection such as use of biological features of the user like retina patterns, fingerprints
and voiceprints to prevent the fraudulent practices carried out in terms of financial statements.
Apart from this, the establishment of firewalls has helped in controlling the unauthorized access
of the financial information related to the organizations in UAE (Rahman and Anwar, 2014).
Aim and Objectives
The main aim of the research is to analyze the effect of technology used to detect and prevent
financial statement fraud in UAE. For the purpose of the attainment of this aim, there is a
requirement to attain the following objectives.
To identify different types of frauds that occurs in financial statements
To evaluate various technological improvements in accounting
Investigation of different techniques which are being used to detect financial statement
fraud
Introduction
Financial statement fraud refers to making modifications in the financial statements of the
companies by the way of addition or omission of the data related to it for the purpose of
projecting a desired financial strength of the company to its stakeholders which is false in nature.
This fraudulent practice has been carried out by the firms to gain the interest of the investors
from whom they appeal to gain a credit. The Forensic accounting Dubai offer services to detect
and avoid such kind of fraud in the organizations as it has huge repercussions at the time of
detected by the authorities (Van Akkeren and Buckby, 2017). There are several firms that offer
forensic accounting Dubai services in UAE. It is also found out that there are several techniques
and technology that has been used by the firms to detect financial statement fraud such as
password protection, digital analysis and firewall protection and so on. It is found out that
emergence and growth of e-commerce and internet has resulted in increasing the exposure to
fraud.
It is essential for the accountants to ensure that the information or computer network should be
accessible by only legitimate users. Passwords are considered as the oldest technique of
computer defense. Technological advancement has helped in the creation of new forms of
password protection such as use of biological features of the user like retina patterns, fingerprints
and voiceprints to prevent the fraudulent practices carried out in terms of financial statements.
Apart from this, the establishment of firewalls has helped in controlling the unauthorized access
of the financial information related to the organizations in UAE (Rahman and Anwar, 2014).
Aim and Objectives
The main aim of the research is to analyze the effect of technology used to detect and prevent
financial statement fraud in UAE. For the purpose of the attainment of this aim, there is a
requirement to attain the following objectives.
To identify different types of frauds that occurs in financial statements
To evaluate various technological improvements in accounting
Investigation of different techniques which are being used to detect financial statement
fraud
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
To evaluate the challenges faced by the organizations in the implementation of the
technologies for the detection of the financial statement fraud
To analyze different measures taken to improve the performance of the detection of the
financial statement fraud
Hypothesis with Theory
The hypothesis for the research study is as follows:
H0: There is no existence of significant relationship between prevention techniques and detect of
financial statement fraud in organizations of UAE.
H1: There is a presence of significant relationship between prevention techniques and detect of
financial statement fraud in organizations of UAE.
The theory of fraud triangle entails the reasoning behind the decision of an employee to commit
fraud. This theory considers three elements that contribute towards the occurrence of fraud such
as pressure, opportunity and rationalization. The pressure on individual in the form of debt
problem, shortfall in revenue and so on encourages employees to commit fraud. The second
stage is the opportunity to commit fraud where the employee considers the clear course of action
through which their position can be abused to solve their aim of committing the fraud (Mansor,
2015). In the last stage, i.e. rationalization, an employee should have an ability to rationalize the
crime in a manner that the employee has a justification for the crime that is acceptable to their
internal and moral compass. In addition to this, Fraud Diamond theory is an extension of Fraud
Triangle theory and include one more element i.e. capability which emphasizes on the fact that
an employee should have the capability to carry out fraud which is considered as a criminal
activity.
Research Questions
The research question for this study is ‘How technology helps in detection and prevention of the
occurrence of financial statement fraud in UAE organizations?’
Research Rationale
This research study is significant for the accounting professionals as it provides the information
related to the different digital technologies that can be implemented or used by the organizations
to detect financial statements fraud in an effective manner. Along with this, it is also important
for the students as it helps them to gather knowledge regarding the emergence of a separate
industry to detect financial statement fraud occurred in different firms in UAE (Anand, Dacin
To evaluate the challenges faced by the organizations in the implementation of the
technologies for the detection of the financial statement fraud
To analyze different measures taken to improve the performance of the detection of the
financial statement fraud
Hypothesis with Theory
The hypothesis for the research study is as follows:
H0: There is no existence of significant relationship between prevention techniques and detect of
financial statement fraud in organizations of UAE.
H1: There is a presence of significant relationship between prevention techniques and detect of
financial statement fraud in organizations of UAE.
The theory of fraud triangle entails the reasoning behind the decision of an employee to commit
fraud. This theory considers three elements that contribute towards the occurrence of fraud such
as pressure, opportunity and rationalization. The pressure on individual in the form of debt
problem, shortfall in revenue and so on encourages employees to commit fraud. The second
stage is the opportunity to commit fraud where the employee considers the clear course of action
through which their position can be abused to solve their aim of committing the fraud (Mansor,
2015). In the last stage, i.e. rationalization, an employee should have an ability to rationalize the
crime in a manner that the employee has a justification for the crime that is acceptable to their
internal and moral compass. In addition to this, Fraud Diamond theory is an extension of Fraud
Triangle theory and include one more element i.e. capability which emphasizes on the fact that
an employee should have the capability to carry out fraud which is considered as a criminal
activity.
Research Questions
The research question for this study is ‘How technology helps in detection and prevention of the
occurrence of financial statement fraud in UAE organizations?’
Research Rationale
This research study is significant for the accounting professionals as it provides the information
related to the different digital technologies that can be implemented or used by the organizations
to detect financial statements fraud in an effective manner. Along with this, it is also important
for the students as it helps them to gather knowledge regarding the emergence of a separate
industry to detect financial statement fraud occurred in different firms in UAE (Anand, Dacin

6
and Murphy, 2015). Apart from this, it is also significant for future researchers as it helps in
creation of the background for the future researches.
Literature review
The literature review has been developed in order to carry out the in-depth analysis of research
issue as effect and use of technology over detecting and preventing the fraud in UAE
organizations.
To identify different types of frauds that occurs in financial statements
In this modern era of technological advancement, technologies have been developed in order to
make the operational process faster and efficient but in limited and the misuse of technology has
emerged. In context to this, the UAE organizations are also found to indulge into the fraudulent
financial statement as they misstate the financial information for its external and internal users
which left a dirty image of country and organizations over the global people and corporate
governance (Narendra, et al., 2016). In recent years, financial scandals have increased as issue
for the corporate governance and the fraudulent activities in presenting financial information has
wiped out the billions of dollars of the values of stakeholders. On the other hand, financial
statement frauds have also resulted into the erosion of confidence of investors in this rapidly
developing financial market. Narendra, et al., (2016) determined that the State Audit Association
has also reported that the liable authorities of UAE have also engaged into the recovery of AED
1 billion due to the fraudulent activities. On the other hand, UAE has also ranked as 21th country
out of the 175 countries that also signs that it has also high level corruption country in the global
level market.
According to the Chen, (2016), in presenting the financial statement, there are several frauds
have been detected with its different nature and consequences. In context to this, it is perceived
that misinterpretation of financial information is one of the major fraud in which the wrong data
and Murphy, 2015). Apart from this, it is also significant for future researchers as it helps in
creation of the background for the future researches.
Literature review
The literature review has been developed in order to carry out the in-depth analysis of research
issue as effect and use of technology over detecting and preventing the fraud in UAE
organizations.
To identify different types of frauds that occurs in financial statements
In this modern era of technological advancement, technologies have been developed in order to
make the operational process faster and efficient but in limited and the misuse of technology has
emerged. In context to this, the UAE organizations are also found to indulge into the fraudulent
financial statement as they misstate the financial information for its external and internal users
which left a dirty image of country and organizations over the global people and corporate
governance (Narendra, et al., 2016). In recent years, financial scandals have increased as issue
for the corporate governance and the fraudulent activities in presenting financial information has
wiped out the billions of dollars of the values of stakeholders. On the other hand, financial
statement frauds have also resulted into the erosion of confidence of investors in this rapidly
developing financial market. Narendra, et al., (2016) determined that the State Audit Association
has also reported that the liable authorities of UAE have also engaged into the recovery of AED
1 billion due to the fraudulent activities. On the other hand, UAE has also ranked as 21th country
out of the 175 countries that also signs that it has also high level corruption country in the global
level market.
According to the Chen, (2016), in presenting the financial statement, there are several frauds
have been detected with its different nature and consequences. In context to this, it is perceived
that misinterpretation of financial information is one of the major fraud in which the wrong data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
are published by the accounting managers and the colleagues as well. It is also found out that
theft of intellectual property is also a fraud in the financial fraud. It is also revealed that stealing
the financial information from the organizational source is also termed as major challenge for the
modern edge business in UAE. On the other hand, the intentional omission has also occurred as a
financial fraud issue and its main aim to provide benefits to one stakeholder or a single investor.
With this, manipulation with the accounting records is also identified as a fraudulent bustle in the
financial statement.
To evaluate various technological improvements in accounting
Gupta and Gill, (2012), observed that the accounting profession is transforming from traditional
to modern era business because of the optimization of productivity with the emergence of newer
and innovative technologies. The technologies has enable the accountant to prepare the financial
information too quickly and drawn results for effective decision making. It is also described that
accounting technology has sharpen the efficiency and effective data presentation. It is assessed
that artificial intelligence has also developed in advance manner which is valuable carry out the
accurate recording, decreasing operating cost and enhance efficiency as well. With this, cloud
computing is also a technological advancement which assists the accountant to work from any
location of any time along with this, the information can also be delivered through cloud
technology is also easy. Furthermore, the innovation in the tax software has also emerged as the
valuable improvement in the financial presentation and management that is also supportive for
business to reduce the errors of margin which is ultimately resulted into the avoiding tax
penalties that leads to preventing the issues for its stakeholders. Moreover, the Collins, A. and
Halverson, (2018), mobile accounting is also an impulsive technological advancement in which
the accountant can use and share the information. The mobile technology has also bridge the gap
are published by the accounting managers and the colleagues as well. It is also found out that
theft of intellectual property is also a fraud in the financial fraud. It is also revealed that stealing
the financial information from the organizational source is also termed as major challenge for the
modern edge business in UAE. On the other hand, the intentional omission has also occurred as a
financial fraud issue and its main aim to provide benefits to one stakeholder or a single investor.
With this, manipulation with the accounting records is also identified as a fraudulent bustle in the
financial statement.
To evaluate various technological improvements in accounting
Gupta and Gill, (2012), observed that the accounting profession is transforming from traditional
to modern era business because of the optimization of productivity with the emergence of newer
and innovative technologies. The technologies has enable the accountant to prepare the financial
information too quickly and drawn results for effective decision making. It is also described that
accounting technology has sharpen the efficiency and effective data presentation. It is assessed
that artificial intelligence has also developed in advance manner which is valuable carry out the
accurate recording, decreasing operating cost and enhance efficiency as well. With this, cloud
computing is also a technological advancement which assists the accountant to work from any
location of any time along with this, the information can also be delivered through cloud
technology is also easy. Furthermore, the innovation in the tax software has also emerged as the
valuable improvement in the financial presentation and management that is also supportive for
business to reduce the errors of margin which is ultimately resulted into the avoiding tax
penalties that leads to preventing the issues for its stakeholders. Moreover, the Collins, A. and
Halverson, (2018), mobile accounting is also an impulsive technological advancement in which
the accountant can use and share the information. The mobile technology has also bridge the gap
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
in between the accountant and client that helps the accountant to manage the business while on
the move. It is approached that the specialized accounting software are going to be introduced by
the modern age companies which away the accountant from ledge, pen and desk calculator and
the process has also improved.
Investigation of different techniques which are being used to detect financial statement
fraud
In the words of Agathee and Ramen, (2017), the advancement of technology is supportive for the
accounting development and carrying out the process in efficient manner. In addition to this,
there are several techniques have been emerged in order to detect and prevent the fraud which
occurred in the financial statement of organizations. In addition to this, it is also assessed that
the major techniques have been investigated as continual audit of through technical software the
wrong interpreted information can be identified and corrected in effective manner. Wells, (2017),
assessed that the computer aided techniques can be used to assess the risk automatically. It is
also determined that the data mining is also good option for the management or technology to
catch the mistakes in the financial statement presented by the UAE based organizations. Data
mining is useful for detecting the false information from the large size data of financial
information. Along with this, Akkeren and Buckby, (2017), also stated that the audit support
system are also considered as major technological tools which are also useful for the firms in
order to carry out the audit operations efficiently .
To evaluate the challenges faced by the organizations in implementation of the technologies
for the detection of the financial statement fraud
Sadaf, et al., (2018), determined that the fraud detection is a major issue in which it needs proper
tools and efforts and adopting the fraud detection is also an issue because of its different
in between the accountant and client that helps the accountant to manage the business while on
the move. It is approached that the specialized accounting software are going to be introduced by
the modern age companies which away the accountant from ledge, pen and desk calculator and
the process has also improved.
Investigation of different techniques which are being used to detect financial statement
fraud
In the words of Agathee and Ramen, (2017), the advancement of technology is supportive for the
accounting development and carrying out the process in efficient manner. In addition to this,
there are several techniques have been emerged in order to detect and prevent the fraud which
occurred in the financial statement of organizations. In addition to this, it is also assessed that
the major techniques have been investigated as continual audit of through technical software the
wrong interpreted information can be identified and corrected in effective manner. Wells, (2017),
assessed that the computer aided techniques can be used to assess the risk automatically. It is
also determined that the data mining is also good option for the management or technology to
catch the mistakes in the financial statement presented by the UAE based organizations. Data
mining is useful for detecting the false information from the large size data of financial
information. Along with this, Akkeren and Buckby, (2017), also stated that the audit support
system are also considered as major technological tools which are also useful for the firms in
order to carry out the audit operations efficiently .
To evaluate the challenges faced by the organizations in implementation of the technologies
for the detection of the financial statement fraud
Sadaf, et al., (2018), determined that the fraud detection is a major issue in which it needs proper
tools and efforts and adopting the fraud detection is also an issue because of its different

9
consequences of identification and controlling the fraud detection process. It is observed that the
organization faces the challenge of disparate transaction systems in which the data cannot be
shared and transferred in easy manner so it is critical issue for the organization while
implementing the fraud detection technologies. Barghathi, et al., (2018), reviewed that this
system might also not be able to interact with other system this technological system has been
designed in order to operate for the management of large data size. In relation to the fraud
detection technology, piecemeal fraud detection system is also developed but the organization
faces the problems in implementing this fraud identification system by the organization. In
addition to this, up -gradation of this system is also problematic for the organization to get it in
advance manner. On the other hand, there is also need for training and education about the newly
installed system in the organization which has also become a challenge to conduct the training
and development session. It is also revealed that the cost is also a challenge for the organization
because the expenses occur in order to operate the high techno –efficient computer system for
detecting the fraud detection in the financial statement of business (Bammi, et al., 2018).
To analyze different measures taken to improve the performance of the detection of the
financial statement fraud
Chan and Vasarhelyi, (2018), stated that the recent era of fast moving technology, it is essential
and important for the UAE organizations to enable them in efficient manner so the fraud and
financial misstatement can easily be detected in easy manner. The fraud detection is reliable for
organization and stakeholders both as well because it gives the real picture about the
organization. In context to this, organizations need to implement the advanced technology based
system so that the rate of fraud occurrence can be reduced in significant manner. In relation to
this, fraud monitoring can be developed with the support of artificial techniques in the system. It
consequences of identification and controlling the fraud detection process. It is observed that the
organization faces the challenge of disparate transaction systems in which the data cannot be
shared and transferred in easy manner so it is critical issue for the organization while
implementing the fraud detection technologies. Barghathi, et al., (2018), reviewed that this
system might also not be able to interact with other system this technological system has been
designed in order to operate for the management of large data size. In relation to the fraud
detection technology, piecemeal fraud detection system is also developed but the organization
faces the problems in implementing this fraud identification system by the organization. In
addition to this, up -gradation of this system is also problematic for the organization to get it in
advance manner. On the other hand, there is also need for training and education about the newly
installed system in the organization which has also become a challenge to conduct the training
and development session. It is also revealed that the cost is also a challenge for the organization
because the expenses occur in order to operate the high techno –efficient computer system for
detecting the fraud detection in the financial statement of business (Bammi, et al., 2018).
To analyze different measures taken to improve the performance of the detection of the
financial statement fraud
Chan and Vasarhelyi, (2018), stated that the recent era of fast moving technology, it is essential
and important for the UAE organizations to enable them in efficient manner so the fraud and
financial misstatement can easily be detected in easy manner. The fraud detection is reliable for
organization and stakeholders both as well because it gives the real picture about the
organization. In context to this, organizations need to implement the advanced technology based
system so that the rate of fraud occurrence can be reduced in significant manner. In relation to
this, fraud monitoring can be developed with the support of artificial techniques in the system. It
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
is also observed that organization can set up a model of fraud detection at different level as
internal and external parties. In relation to the customer aspects, Huang, et al., (2017), stated that
the transaction monitoring system can be implemented to control the fraud in the customer
solution. On the other hand, it can also be suggested that the organization can also develop its big
data analytics technology in proper manner so that it can improve the fraud detection process. In
addition to this, the data mining techniques can also be developed for the improvement of
performance of technology for identifying the fraud in the financial statements.
Literature gap
This research has been taken into the investigation of effect of technology in order to prevent and
detect the financial statement frauds in the UAE organization. In this study research
methodology has been adopted with the sample size and location. In this literature there is a gap
because the particular organization has not been chosen so that the specific study might not be
leaded in efficient manner (Rose, et al., 2014).
is also observed that organization can set up a model of fraud detection at different level as
internal and external parties. In relation to the customer aspects, Huang, et al., (2017), stated that
the transaction monitoring system can be implemented to control the fraud in the customer
solution. On the other hand, it can also be suggested that the organization can also develop its big
data analytics technology in proper manner so that it can improve the fraud detection process. In
addition to this, the data mining techniques can also be developed for the improvement of
performance of technology for identifying the fraud in the financial statements.
Literature gap
This research has been taken into the investigation of effect of technology in order to prevent and
detect the financial statement frauds in the UAE organization. In this study research
methodology has been adopted with the sample size and location. In this literature there is a gap
because the particular organization has not been chosen so that the specific study might not be
leaded in efficient manner (Rose, et al., 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
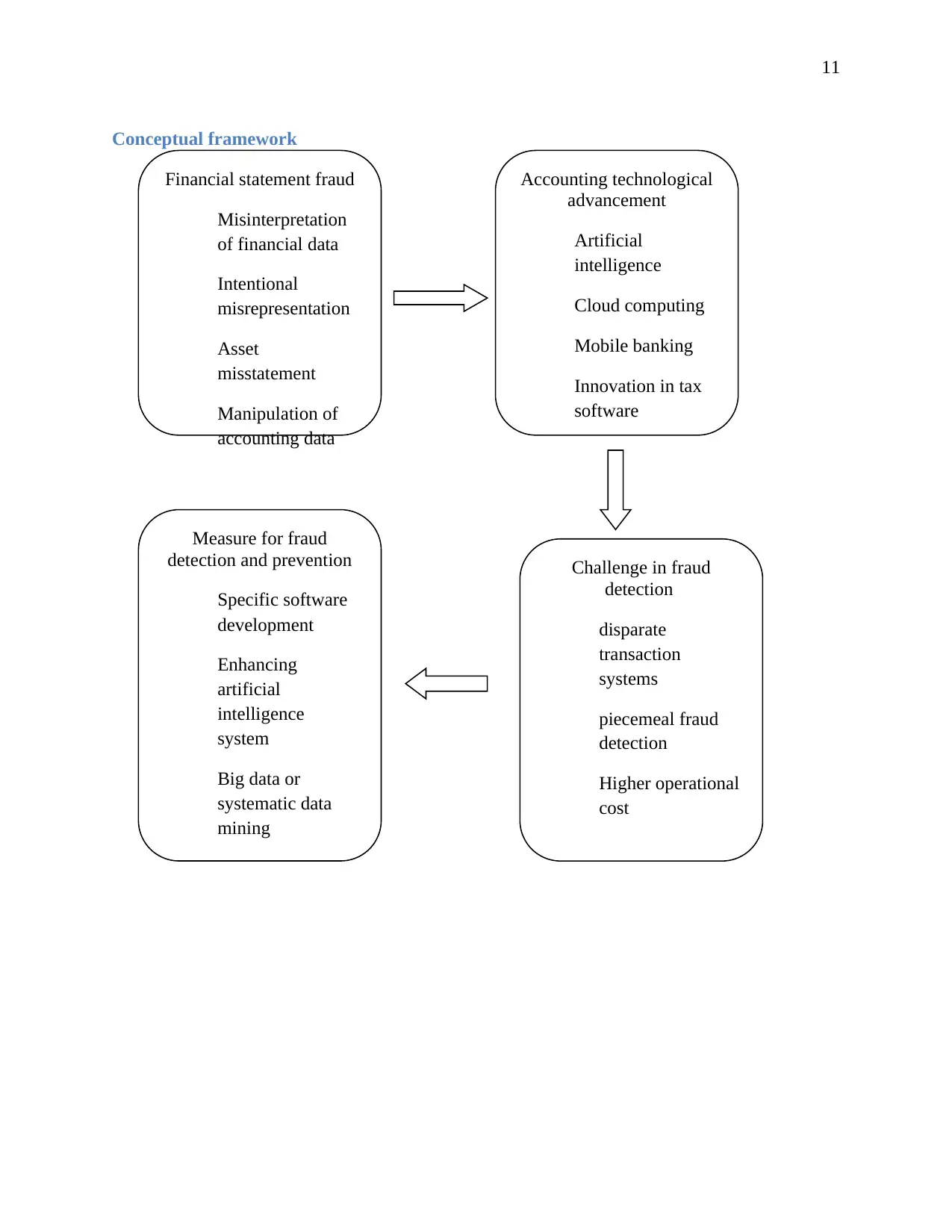
Conceptual framework
Financial statement fraud
Misinterpretation
of financial data
Intentional
misrepresentation
Asset
misstatement
Manipulation of
accounting data
Accounting technological
advancement
Artificial
intelligence
Cloud computing
Mobile banking
Innovation in tax
software
Challenge in fraud
detection
disparate
transaction
systems
piecemeal fraud
detection
Higher operational
cost
Measure for fraud
detection and prevention
Specific software
development
Enhancing
artificial
intelligence
system
Big data or
systematic data
mining
Conceptual framework
Financial statement fraud
Misinterpretation
of financial data
Intentional
misrepresentation
Asset
misstatement
Manipulation of
accounting data
Accounting technological
advancement
Artificial
intelligence
Cloud computing
Mobile banking
Innovation in tax
software
Challenge in fraud
detection
disparate
transaction
systems
piecemeal fraud
detection
Higher operational
cost
Measure for fraud
detection and prevention
Specific software
development
Enhancing
artificial
intelligence
system
Big data or
systematic data
mining

12
Research Methodology
Exploratory and descriptive are two types of research designs that are being used to carry out
most of the research studies. Exploratory research design provides insights related to different
aspects of the research topic by providing the researcher an opportunity to explore the
information related to the research topic. Along with this, descriptive research design as the
name suggests provides the results of the research study in a detailed and comprehensive
manner. Exploratory research design is appropriate for this research study as it facilitates in
gaining information related to the impact of the use of technology on the detection and
prevention of the financial statement fraud in the organizations of UAE (Bell, Bryman and
Harley, 2018).
Positivism and interpretivism are different types of philosophies which are being used to carry
out the research. Interpretivism is a philosophy which takes into consideration the views and
opinions of researcher along with the elements of the research to attain reliable results for the
research study. Positivism is a structured approach that takes into consideration the elements of
the research such as hypothesis, aims and objectives, and research questions to attain valid and
reliable results for the research study (Hair, et.al, 2015).
Positivism philosophy is being used in this research study as for attaining valid and reliable
results, researcher would consider only the elements of the research such as research question,
background, hypothesis, aims and objectives. Besides this, there are two approaches which are
being used by the researchers to carry out the research such as deductive and inductive approach.
Inductive approach refers to the approach in which consideration is being given to specific
information to derive generalized results for the research study (Walliman, 2017). Apart from
this, in deductive approach deductions have been made in the general or broad information
related to the research topic in order to reach to a precise outcome of the research. In relation to
this research study, deductive approach is being used as it helps in attaining the specific outcome
i.e. use of technology to detect and prevent only financial statement fraud by considering general
information i.e. use of technology to detect and prevent different types of frauds.
It is necessary for the researcher to collect relevant data related to the research topic as it helps in
the creation of the foundation for the attainment of the results of the research study. For this
Research Methodology
Exploratory and descriptive are two types of research designs that are being used to carry out
most of the research studies. Exploratory research design provides insights related to different
aspects of the research topic by providing the researcher an opportunity to explore the
information related to the research topic. Along with this, descriptive research design as the
name suggests provides the results of the research study in a detailed and comprehensive
manner. Exploratory research design is appropriate for this research study as it facilitates in
gaining information related to the impact of the use of technology on the detection and
prevention of the financial statement fraud in the organizations of UAE (Bell, Bryman and
Harley, 2018).
Positivism and interpretivism are different types of philosophies which are being used to carry
out the research. Interpretivism is a philosophy which takes into consideration the views and
opinions of researcher along with the elements of the research to attain reliable results for the
research study. Positivism is a structured approach that takes into consideration the elements of
the research such as hypothesis, aims and objectives, and research questions to attain valid and
reliable results for the research study (Hair, et.al, 2015).
Positivism philosophy is being used in this research study as for attaining valid and reliable
results, researcher would consider only the elements of the research such as research question,
background, hypothesis, aims and objectives. Besides this, there are two approaches which are
being used by the researchers to carry out the research such as deductive and inductive approach.
Inductive approach refers to the approach in which consideration is being given to specific
information to derive generalized results for the research study (Walliman, 2017). Apart from
this, in deductive approach deductions have been made in the general or broad information
related to the research topic in order to reach to a precise outcome of the research. In relation to
this research study, deductive approach is being used as it helps in attaining the specific outcome
i.e. use of technology to detect and prevent only financial statement fraud by considering general
information i.e. use of technology to detect and prevent different types of frauds.
It is necessary for the researcher to collect relevant data related to the research topic as it helps in
the creation of the foundation for the attainment of the results of the research study. For this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 35
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




