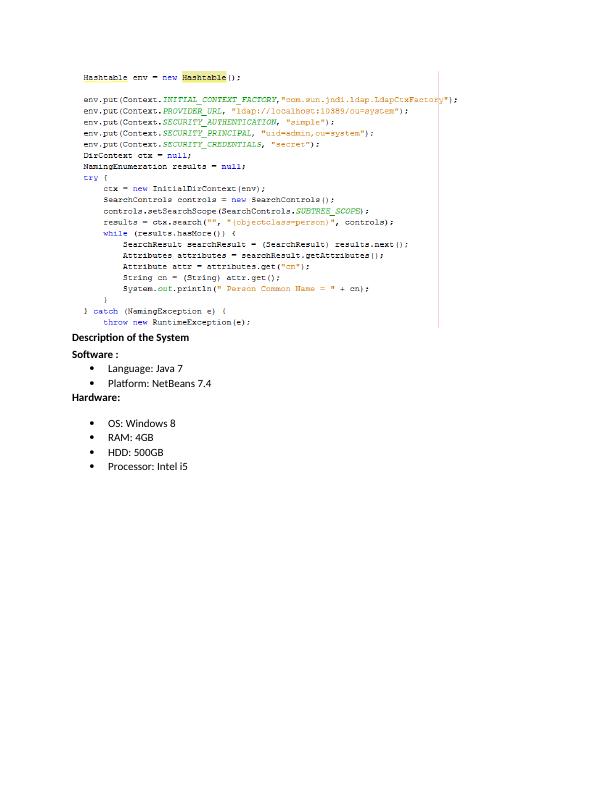
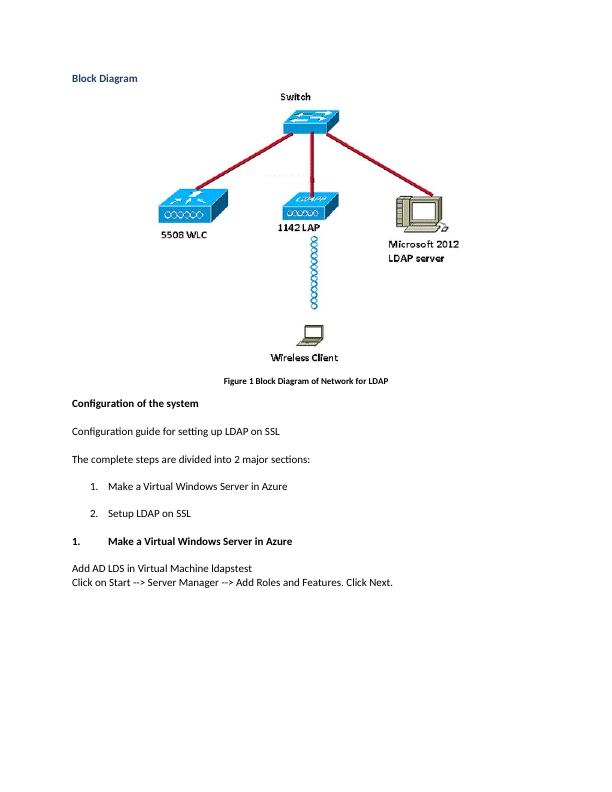
Ask a question from expert
Technology Implementation of Security Controls for FNU's Online Learning Network
20 Pages762 Words412 Views
Added on 2019-09-13
About This Document
FNU is a long distance learning organization that requires a high-performance network infrastructure to provide quality services to its users. This article discusses the network requirements and security measures needed for FNU's online learning network, including centralized authentication, cryptography, and device fingerprinting.
Technology Implementation of Security Controls for FNU's Online Learning Network
Added on 2019-09-13
BookmarkShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Technology Implementation of Security Controls for FNU's Online Learning Network
|36
|1961
|312
Technology Implementation of Security Controls : Assignment
|36
|1961
|258
Network Redesign for FNU
|20
|8038
|110
Network Redesign for FNU
|6
|2800
|359
Higher Educational Organization for Long Distance Learning | FNU
|9
|4373
|365
Network Redesign for FNU: Assignment
|20
|8038
|343