Technology in Organisations: Cloud Computing, Security & Networking
VerifiedAdded on 2023/06/08
|12
|3916
|249
Report
AI Summary
This report examines the crucial role of technology in modern organizations, focusing on cloud computing, security, and networking infrastructure. It analyzes the benefits of cloud adoption, including security, cost reduction, and quality control, using Amazon as a case study. The report also details essential security requirements, such as training policies, change management, and password management, to protect organizational data. Furthermore, it explores key networking infrastructure components like cabling, wireless connectivity, and network security devices that support daily business operations. The document provides a comprehensive overview of how technology drives efficiency and security in organizational contexts, contributed by a student and available on Desklib.

Technology In
Organisations
Organisations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
QUESTION 1...................................................................................................................................3
A. Role of Cloud-Computing in business from the Cloud Computing Model point of view.....3
B. Benefits of adopting Cloud Computing:- ..............................................................................4
QUESTION 2...................................................................................................................................5
Security requirements and their frameworks that must be implemented by organisations for
security and control over information :-......................................................................................5
QUESTION 3...................................................................................................................................7
A. Key Networking Infrastructure in organisation that used in business operations daily:-......7
B. Spreadsheet from the Sales department of All Tech Group .......10
CONCLUSION..............................................................................................................................10
REFERENCES .............................................................................................................................12
INTRODUCTION...........................................................................................................................3
QUESTION 1...................................................................................................................................3
A. Role of Cloud-Computing in business from the Cloud Computing Model point of view.....3
B. Benefits of adopting Cloud Computing:- ..............................................................................4
QUESTION 2...................................................................................................................................5
Security requirements and their frameworks that must be implemented by organisations for
security and control over information :-......................................................................................5
QUESTION 3...................................................................................................................................7
A. Key Networking Infrastructure in organisation that used in business operations daily:-......7
B. Spreadsheet from the Sales department of All Tech Group .......10
CONCLUSION..............................................................................................................................10
REFERENCES .............................................................................................................................12

INTRODUCTION
Technology plays a very essential role in businesses, technology role is speedy going to
increases with the time. Now days technology is not separated from the business world. In
business the role of technology caused excellent growth. Now in the field of technology old and
outdated technology were replaced with the modern technology tools such as cloud computing,
big data, artificial intelligence, and internet of things. Introduction of new technology give a
revolutionized result in business models and concepts, and this happens only because technology
gave a effective approach and plan on how the business can go efficiently and effectively.
Technology provides efficient, faster and convenient way for performing all the activities,
operations in business. In this case based on Amazon which is a multinational company and the
world's high valuable brand. It was founded by Jeff Bezos in Washington in 1995, on 5 July. In
this case we analyse about the role of cloud-computing in an organisation and also the
requirement of securities which helps the organisation to create a effective framework for the
security of data. Networking infrastructure that helps business in their day-to-day operations
(Alizadeh and Hassan, 2019).
QUESTION 1
A. Role of Cloud-Computing in business from the Cloud Computing Model point of view
Cloud-computing is a process of offering various services through the internet for
processing, managing, and storing the data. It gives various services, tools such as software,
servers, and data storage for companies so that they can increase their economy scale, operations,
and efficiently use resources. Cloud computing helps business for virtually access their business,
and also make a flexible way of operating their data, at any time and at any place. In order to
utilize resources, software, amazon uses various competitive advantages, and this help them in
connecting with their suppliers, stakeholder, creditors, investors (Chandra and Borah, 2021).
Below are the three types of cloud computing which Amazon utilize in their day-to-day
operations:-
Platform as a Services:- This type of cloud computing indicates the delivering of on-
demand tools for managing, testing and developing the software applications. PAAS
majorly offers a framework which provides a platform or a medium through which
consumers can develop, and manage the applications. This helps the Amazon in
Technology plays a very essential role in businesses, technology role is speedy going to
increases with the time. Now days technology is not separated from the business world. In
business the role of technology caused excellent growth. Now in the field of technology old and
outdated technology were replaced with the modern technology tools such as cloud computing,
big data, artificial intelligence, and internet of things. Introduction of new technology give a
revolutionized result in business models and concepts, and this happens only because technology
gave a effective approach and plan on how the business can go efficiently and effectively.
Technology provides efficient, faster and convenient way for performing all the activities,
operations in business. In this case based on Amazon which is a multinational company and the
world's high valuable brand. It was founded by Jeff Bezos in Washington in 1995, on 5 July. In
this case we analyse about the role of cloud-computing in an organisation and also the
requirement of securities which helps the organisation to create a effective framework for the
security of data. Networking infrastructure that helps business in their day-to-day operations
(Alizadeh and Hassan, 2019).
QUESTION 1
A. Role of Cloud-Computing in business from the Cloud Computing Model point of view
Cloud-computing is a process of offering various services through the internet for
processing, managing, and storing the data. It gives various services, tools such as software,
servers, and data storage for companies so that they can increase their economy scale, operations,
and efficiently use resources. Cloud computing helps business for virtually access their business,
and also make a flexible way of operating their data, at any time and at any place. In order to
utilize resources, software, amazon uses various competitive advantages, and this help them in
connecting with their suppliers, stakeholder, creditors, investors (Chandra and Borah, 2021).
Below are the three types of cloud computing which Amazon utilize in their day-to-day
operations:-
Platform as a Services:- This type of cloud computing indicates the delivering of on-
demand tools for managing, testing and developing the software applications. PAAS
majorly offers a framework which provides a platform or a medium through which
consumers can develop, and manage the applications. This helps the Amazon in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

decreases the use of costly and complex process of purchasing and managing software
licensing. Applications which developers are make related 5to the application of life
cycle providers majorly focuses on that.
Infrastructure as a Services:- It indicates that providers of the cloud services arrange
the infrastructure for the organisation which involves the data storage, actual servers,
virtualisation and networks, with the help of the providers Amazon access the cloud-
services API and dashboards. They manage various operations and activities like
operating system, apps which supports the amazon in efficient functioning of operations.
The infrastructure providers as a service manages the hardware, servers, hard drives and
data storage in an effective and efficient way. If there is any mistake or technical error
arises then the providers manage and repair the problem. This helps the amazon in
managing, and storing the project, files and data in effective and efficient way so that
they can not see any kind of difficulties controlling and managing the confidential data
(Sharma, Gupta and Acharya, 2020).
Software as a service:- This software as a services involves the providers of software
and hosts lease software and lease on the basis of subscription to the organisation. It
helps in avoid the procedure which are lengthy like software installation, that the
administrators of IT install in organisation. Amazon can use huge different software in
addition of emails, collaboration and calendering Amazon can also utilize this model
Software as a service because that helps in the application accessing, with help of web
browsers which they use with the help of username and login password.
B. Benefits of adopting Cloud Computing:-
In modern days business cloud-computing is most essential, cloud computing has been
from two decades despite the data pointing to the cost-benefits , business competitive advantages
it holds and maintain a huge portion of business community which going to operate without it.
Cloud Computing gives various benefits to the users, that because they manage their operations
in an effective and efficient way (Yuvaraj, 2020).
There are various benefits of Cloud Computing which Amazon enjoys:-
Security:- Most of the business have concern about the security, by adopting cloud
computing, cloud computing gives security related to the data, files, software and all
types of essential information. It helps in measuring and monitoring all the activities and
licensing. Applications which developers are make related 5to the application of life
cycle providers majorly focuses on that.
Infrastructure as a Services:- It indicates that providers of the cloud services arrange
the infrastructure for the organisation which involves the data storage, actual servers,
virtualisation and networks, with the help of the providers Amazon access the cloud-
services API and dashboards. They manage various operations and activities like
operating system, apps which supports the amazon in efficient functioning of operations.
The infrastructure providers as a service manages the hardware, servers, hard drives and
data storage in an effective and efficient way. If there is any mistake or technical error
arises then the providers manage and repair the problem. This helps the amazon in
managing, and storing the project, files and data in effective and efficient way so that
they can not see any kind of difficulties controlling and managing the confidential data
(Sharma, Gupta and Acharya, 2020).
Software as a service:- This software as a services involves the providers of software
and hosts lease software and lease on the basis of subscription to the organisation. It
helps in avoid the procedure which are lengthy like software installation, that the
administrators of IT install in organisation. Amazon can use huge different software in
addition of emails, collaboration and calendering Amazon can also utilize this model
Software as a service because that helps in the application accessing, with help of web
browsers which they use with the help of username and login password.
B. Benefits of adopting Cloud Computing:-
In modern days business cloud-computing is most essential, cloud computing has been
from two decades despite the data pointing to the cost-benefits , business competitive advantages
it holds and maintain a huge portion of business community which going to operate without it.
Cloud Computing gives various benefits to the users, that because they manage their operations
in an effective and efficient way (Yuvaraj, 2020).
There are various benefits of Cloud Computing which Amazon enjoys:-
Security:- Most of the business have concern about the security, by adopting cloud
computing, cloud computing gives security related to the data, files, software and all
types of essential information. It helps in measuring and monitoring all the activities and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

operations in an effective way. Amazon utilize the cloud computing as it is high secure
and safe in comparison with other infrastructure, with the secure storage in database
cloud computing allows the encryption of data. with the help of cloud computing they
can measure and control access, implementation of authentication procedure and also
there is a measure of bespoke security which ensures that the data is secure and protected.
Lower Cost:- Cloud computing provides simpler and easier access to the information.
Cloud computing managed differently from other servers and it prove that cloud is more
efficient. In cloud computing the return on investment is higher as it offers various
benefits such as time saving, cost saving. It helps in providing ease in data storing
without investing in the space for the data and information.
Quality Control:- Cloud computing helps in maintaining the efficient high quality of
activities and operations in a effective and consistent way like all the major documents,
files are placed in a single and secure format which maintain and take care about the
consistency and efficiency in storing information and data (Dečman and Vintar, 2019).
QUESTION 2
Security requirements and their frameworks that must be implemented by organisations for
security and control over information :-
For each and every organisation it is very crucial to frame their operational activities in such a
way so that, functioning of these activities can be smoothly. Security is the main source in
maintaining data secrecy and accuracy for preventing management of an organisation from
hazardous threats and data leakage risk from unauthorised sources. Amazon as a international
organisation maintains a variety of data from their clients and suppliers. In order to retain their
whole data with safety and security they uses advanced techniques of IT (Kaur and Kinger,
2018). The main three security requirements which are must be implemented by Amazon are as
follows:-
Training policy regarding security awareness:- These policies provides assistance to
all individuals of organisation towards effective working with proper safety of
information within the company. Amazon arranges timely training and development
programs for their employees development and also for their enhancement in knowledge
regarding these different information technology systems that organisation install to
and safe in comparison with other infrastructure, with the secure storage in database
cloud computing allows the encryption of data. with the help of cloud computing they
can measure and control access, implementation of authentication procedure and also
there is a measure of bespoke security which ensures that the data is secure and protected.
Lower Cost:- Cloud computing provides simpler and easier access to the information.
Cloud computing managed differently from other servers and it prove that cloud is more
efficient. In cloud computing the return on investment is higher as it offers various
benefits such as time saving, cost saving. It helps in providing ease in data storing
without investing in the space for the data and information.
Quality Control:- Cloud computing helps in maintaining the efficient high quality of
activities and operations in a effective and consistent way like all the major documents,
files are placed in a single and secure format which maintain and take care about the
consistency and efficiency in storing information and data (Dečman and Vintar, 2019).
QUESTION 2
Security requirements and their frameworks that must be implemented by organisations for
security and control over information :-
For each and every organisation it is very crucial to frame their operational activities in such a
way so that, functioning of these activities can be smoothly. Security is the main source in
maintaining data secrecy and accuracy for preventing management of an organisation from
hazardous threats and data leakage risk from unauthorised sources. Amazon as a international
organisation maintains a variety of data from their clients and suppliers. In order to retain their
whole data with safety and security they uses advanced techniques of IT (Kaur and Kinger,
2018). The main three security requirements which are must be implemented by Amazon are as
follows:-
Training policy regarding security awareness:- These policies provides assistance to
all individuals of organisation towards effective working with proper safety of
information within the company. Amazon arranges timely training and development
programs for their employees development and also for their enhancement in knowledge
regarding these different information technology systems that organisation install to

protect their data. In these training programs employees of Amazon are entitled to sign an
agreement that they would keep their information and data confidential and complete the
whole training program. Amazon's employees plays a very crucial role in maintaining
secrecy and security of data, they are very dedicated towards their organisation. Security
awareness programs help employees and management in understanding the importance
of data security which assist them working with care and ensures task completion in
proper manner. These training programs are always conducted in updated manner in
order to meet market requirement regarding use of information technology and data
security as well because leaking of any confidential data of organisation leads in
declination of the organisation (Kalpana and Singaraju, 2022). That's why Amazon have
their main focus on security of information so that they are able to retain their position in
market and can achieve continuous growth. Their development and training programs
covers all relevant fields such as ensuring proper maintenance of workstations, security
policies regarding access of internet, responsibility of employees towards using
company's systems and other relevant things.
Change Management Policy:- Management should effectively manages the changes in
organisation which are related with the information system, which mainly supports in the
proper function of operations. Main aim of this policy is to manage, control or improve
the operations for the effective management. If security and operations of the
management effected because of any reasons than the systems and software can be
replaced or changed. With the help of this policy Amazon eliminates the sudden and
unexpected changes which can effect the system security negatively. It is the
responsibility of manager to work on the correct policies and planning so that it helps in
maintaining the control and consistency in the flexible environment, and also changes
which are effects the IT sector must follow effective and proper structure which helps the
organisation to maintain consistency in their operations. The changes which the
organisation do should be in a effective and positive manner which results in huge safety
and security of the data (Singh and Malhotra, 2021).
Management Policies and Creation Of Password:- For the proper and Efficient
procedure of documentation this policy helps guides the organisation about how the
operations and functions should be making, executing and reviewing, for the protection
agreement that they would keep their information and data confidential and complete the
whole training program. Amazon's employees plays a very crucial role in maintaining
secrecy and security of data, they are very dedicated towards their organisation. Security
awareness programs help employees and management in understanding the importance
of data security which assist them working with care and ensures task completion in
proper manner. These training programs are always conducted in updated manner in
order to meet market requirement regarding use of information technology and data
security as well because leaking of any confidential data of organisation leads in
declination of the organisation (Kalpana and Singaraju, 2022). That's why Amazon have
their main focus on security of information so that they are able to retain their position in
market and can achieve continuous growth. Their development and training programs
covers all relevant fields such as ensuring proper maintenance of workstations, security
policies regarding access of internet, responsibility of employees towards using
company's systems and other relevant things.
Change Management Policy:- Management should effectively manages the changes in
organisation which are related with the information system, which mainly supports in the
proper function of operations. Main aim of this policy is to manage, control or improve
the operations for the effective management. If security and operations of the
management effected because of any reasons than the systems and software can be
replaced or changed. With the help of this policy Amazon eliminates the sudden and
unexpected changes which can effect the system security negatively. It is the
responsibility of manager to work on the correct policies and planning so that it helps in
maintaining the control and consistency in the flexible environment, and also changes
which are effects the IT sector must follow effective and proper structure which helps the
organisation to maintain consistency in their operations. The changes which the
organisation do should be in a effective and positive manner which results in huge safety
and security of the data (Singh and Malhotra, 2021).
Management Policies and Creation Of Password:- For the proper and Efficient
procedure of documentation this policy helps guides the organisation about how the
operations and functions should be making, executing and reviewing, for the protection
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

of data from any risk organisation should create necessary login and password in order to
protect the informations, data , and files. Amazon can change the temporary passwords or
formulates the regulations and rules, this helps the employees to protect the data in an
effective and ethical manner. Amazon should provide training to their all employees for
how to generate or use password. Changing of password on a regular basis helps the
organisations to maintain security and privacy in the organisation. For maintaining the
effective password complexity, in password specific length with the various characters
are required which supports in eliminating the excess of data which is unauthorised.
There should be differentiated passwords in all software and applications because that
became difficult for tracking the passwords (EL AMRANI and GIBET TANI, 2018). For
the security of information Amazon should create a mandatory policy for all employees
in which the effective and proper logout option available in respect of prescribed session
time limit. This indicates that the framework of this security helps the organisation in
eliminating and reducing the access of unethical risks access which can result in the theft
of information and data, with this policy Amazon can analyse and track their ongoing
operations, can detect capabilities, access the cyber programs and can detect the
capabilities. This policy is highly helpful in protecting the infrastructure and critical
framework of the organisation which is important for the cybersecurity. This policy also
helps in maintaining the efficient and appropriate consistency in the functions and
operations which highly supports the Amazon in offering the services which are high and
rich in quality to the clients. It also decreases the high cost from the functions and
operations in relation to data management by executing the various alternatives which are
easier in handling. This policy helps the whole organisation to perform effectively and
efficiently (Paul and Dangwal, 2018).
QUESTION 3
A. Key Networking Infrastructure in organisation that used in business operations daily:-
Network infrastructure are available in both forms software as well as hardware that
helps in day to day operations of management. There are numerous kinds of network
infrastructure such as facilities, services, hardware and software. Hardware network
infrastructure includes cable lines, smart phones and computers that help a business at all levels
protect the informations, data , and files. Amazon can change the temporary passwords or
formulates the regulations and rules, this helps the employees to protect the data in an
effective and ethical manner. Amazon should provide training to their all employees for
how to generate or use password. Changing of password on a regular basis helps the
organisations to maintain security and privacy in the organisation. For maintaining the
effective password complexity, in password specific length with the various characters
are required which supports in eliminating the excess of data which is unauthorised.
There should be differentiated passwords in all software and applications because that
became difficult for tracking the passwords (EL AMRANI and GIBET TANI, 2018). For
the security of information Amazon should create a mandatory policy for all employees
in which the effective and proper logout option available in respect of prescribed session
time limit. This indicates that the framework of this security helps the organisation in
eliminating and reducing the access of unethical risks access which can result in the theft
of information and data, with this policy Amazon can analyse and track their ongoing
operations, can detect capabilities, access the cyber programs and can detect the
capabilities. This policy is highly helpful in protecting the infrastructure and critical
framework of the organisation which is important for the cybersecurity. This policy also
helps in maintaining the efficient and appropriate consistency in the functions and
operations which highly supports the Amazon in offering the services which are high and
rich in quality to the clients. It also decreases the high cost from the functions and
operations in relation to data management by executing the various alternatives which are
easier in handling. This policy helps the whole organisation to perform effectively and
efficiently (Paul and Dangwal, 2018).
QUESTION 3
A. Key Networking Infrastructure in organisation that used in business operations daily:-
Network infrastructure are available in both forms software as well as hardware that
helps in day to day operations of management. There are numerous kinds of network
infrastructure such as facilities, services, hardware and software. Hardware network
infrastructure includes cable lines, smart phones and computers that help a business at all levels
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

whether it is a small business or at large level as well. Some of key network infrastructure are
described below that helps management in their daily operations:-
1. Cabling:- Cabling is the foremost and common type of network infrastructure. It
provide various channels for connecting to share data's and information, also for better
communication in all direction of business management internally and externally as well.
Cabling supports in expanding the business and in making changes in management or general
activities that are technological. Cabling in telecommunication can be merged with other
operations of management, that allow business in covering a wide range with only single cable
installation, with purpose of saving money and time both. Cabling differs from business to
business and can be modified according to the nature and size of company. Like Amazon is a
very international company so its require for cabling are vast. Cabling is called efficient and
effective when it is cost effective and is easy to operate for business, simplicity in cabling also
decreases risk of technological problems. It is a hardware network infrastructure that performs as
a mediator through that information is transferred from one network to another network device
(Ghosh and Arce, 2019). Different kinds of networking cables that support business operations
are described below:-
Coaxial cable:- The installation of this cable can be difficult due to its nature of being
greater resistance towards signal obstruction. It is able in managing high lengths of cables
between twisted pair of cables and networking devices.
Fibre optic cable:- It have glass centre that is surrounded by many layers made up of
protective materials. Electric obstruction are avoided by fibre optic cables though
transmission of light in place of electrical intervention.
Shield twisted pair cable:- A specific copper telecom wiring is used in installation of
STP especially in case of business operations. STP cables also provide support in
expanding the deviation between different cables (Ibrahim, Nilashi and Alzurqa, 2019).
Unshielded twisted pair cable:- These types of cables are widely used by system
industries such as telecommunication sector. In installation of UTP cables, conductors are
covered through each other surroundings maintaining only one circuit so that, they can
prevent intervention from any electromagnetic force.
2. Routers:- Router is a very useful network infrastructure in exchange of data as well as
in communication directly within management. It works without any interference due to their
described below that helps management in their daily operations:-
1. Cabling:- Cabling is the foremost and common type of network infrastructure. It
provide various channels for connecting to share data's and information, also for better
communication in all direction of business management internally and externally as well.
Cabling supports in expanding the business and in making changes in management or general
activities that are technological. Cabling in telecommunication can be merged with other
operations of management, that allow business in covering a wide range with only single cable
installation, with purpose of saving money and time both. Cabling differs from business to
business and can be modified according to the nature and size of company. Like Amazon is a
very international company so its require for cabling are vast. Cabling is called efficient and
effective when it is cost effective and is easy to operate for business, simplicity in cabling also
decreases risk of technological problems. It is a hardware network infrastructure that performs as
a mediator through that information is transferred from one network to another network device
(Ghosh and Arce, 2019). Different kinds of networking cables that support business operations
are described below:-
Coaxial cable:- The installation of this cable can be difficult due to its nature of being
greater resistance towards signal obstruction. It is able in managing high lengths of cables
between twisted pair of cables and networking devices.
Fibre optic cable:- It have glass centre that is surrounded by many layers made up of
protective materials. Electric obstruction are avoided by fibre optic cables though
transmission of light in place of electrical intervention.
Shield twisted pair cable:- A specific copper telecom wiring is used in installation of
STP especially in case of business operations. STP cables also provide support in
expanding the deviation between different cables (Ibrahim, Nilashi and Alzurqa, 2019).
Unshielded twisted pair cable:- These types of cables are widely used by system
industries such as telecommunication sector. In installation of UTP cables, conductors are
covered through each other surroundings maintaining only one circuit so that, they can
prevent intervention from any electromagnetic force.
2. Routers:- Router is a very useful network infrastructure in exchange of data as well as
in communication directly within management. It works without any interference due to their

right route through internal networking. They analyses the incoming information and data in
appropriate manner and then transfer it to accurate place between different networks. Alike
cabling, there also available a wide range of routers to handle the continuous changing needs of
management. The installation of router is totally dependent on requirements and size of business.
Wireless router are also called Wi-Fi routers, that have a combination of some function as a
router and some as a wireless access point. These wireless routers are suitable for small size
businesses or branches of companies that have small networking area and also used for in home
offices. Edging routing platforms and routers, together presents strategy for pursuing most
suitable way for the achievement of greater quality applications from one source to its desired
position. Routers and wireless routers plays a crucial role in maintaining security in data policies.
So that, data only transmitted in areas in which it is permitted and can prevent malicious threats.
Wired router used Ethernet cable likewise wireless routers for connecting with modem.
Afterwards, wired routers uses different cables that are already separated for connecting with one
or more networking devices through creating LAN, then linked all network devices with internet.
Core routers is commonly used by companies that have large workplace for transmitting high
amount of data into their own network (Kazim and Zhu, 2021).
3. Switches:- Switches and routers both networking infrastructure cab be confusing but it
is already defined that these are two different entities and have their different functions. It can be
differentiated as routers are used in connecting with networks and switches are used to create
them. Switches transmitted connections between numerous components and layers of technology
with gathering devices like smart phones, servers, computers and screens as well. Switch is the
only network infrastructure that provide path for interaction with each one to different elements
of network, that makes a communication system in the same network. Likewise, routers and
cables, switches are also available in different forms and chooses on the basis of the requirement
and size of business. The three main functions that are performed by switches are Learning,
Forwarding and preventing layers 2 switching loops (Jou and Wang, 2018).
Learning:- The procedure of generating MAC address for connecting different devices is
called learning. In the process of data transmission, when frames get into switch ports,
then switch observes MAC address of sourcing device with the frame of Ethernet. If
switch is not able in observing compatible MAC address, it will summed address with the
table to the number of port through Ethernet frame.
appropriate manner and then transfer it to accurate place between different networks. Alike
cabling, there also available a wide range of routers to handle the continuous changing needs of
management. The installation of router is totally dependent on requirements and size of business.
Wireless router are also called Wi-Fi routers, that have a combination of some function as a
router and some as a wireless access point. These wireless routers are suitable for small size
businesses or branches of companies that have small networking area and also used for in home
offices. Edging routing platforms and routers, together presents strategy for pursuing most
suitable way for the achievement of greater quality applications from one source to its desired
position. Routers and wireless routers plays a crucial role in maintaining security in data policies.
So that, data only transmitted in areas in which it is permitted and can prevent malicious threats.
Wired router used Ethernet cable likewise wireless routers for connecting with modem.
Afterwards, wired routers uses different cables that are already separated for connecting with one
or more networking devices through creating LAN, then linked all network devices with internet.
Core routers is commonly used by companies that have large workplace for transmitting high
amount of data into their own network (Kazim and Zhu, 2021).
3. Switches:- Switches and routers both networking infrastructure cab be confusing but it
is already defined that these are two different entities and have their different functions. It can be
differentiated as routers are used in connecting with networks and switches are used to create
them. Switches transmitted connections between numerous components and layers of technology
with gathering devices like smart phones, servers, computers and screens as well. Switch is the
only network infrastructure that provide path for interaction with each one to different elements
of network, that makes a communication system in the same network. Likewise, routers and
cables, switches are also available in different forms and chooses on the basis of the requirement
and size of business. The three main functions that are performed by switches are Learning,
Forwarding and preventing layers 2 switching loops (Jou and Wang, 2018).
Learning:- The procedure of generating MAC address for connecting different devices is
called learning. In the process of data transmission, when frames get into switch ports,
then switch observes MAC address of sourcing device with the frame of Ethernet. If
switch is not able in observing compatible MAC address, it will summed address with the
table to the number of port through Ethernet frame.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Forwarding:- It is a process through which network passes data through device which is
connected to a network port switch to another connected device with other switches port.
Preventing layering 2 switching loops:- In LAN, redundant links were generated for
avoiding whole network failure. It is one of the function of switch to prevent broadcast
storms (Morgado and Schmidt, 2019).
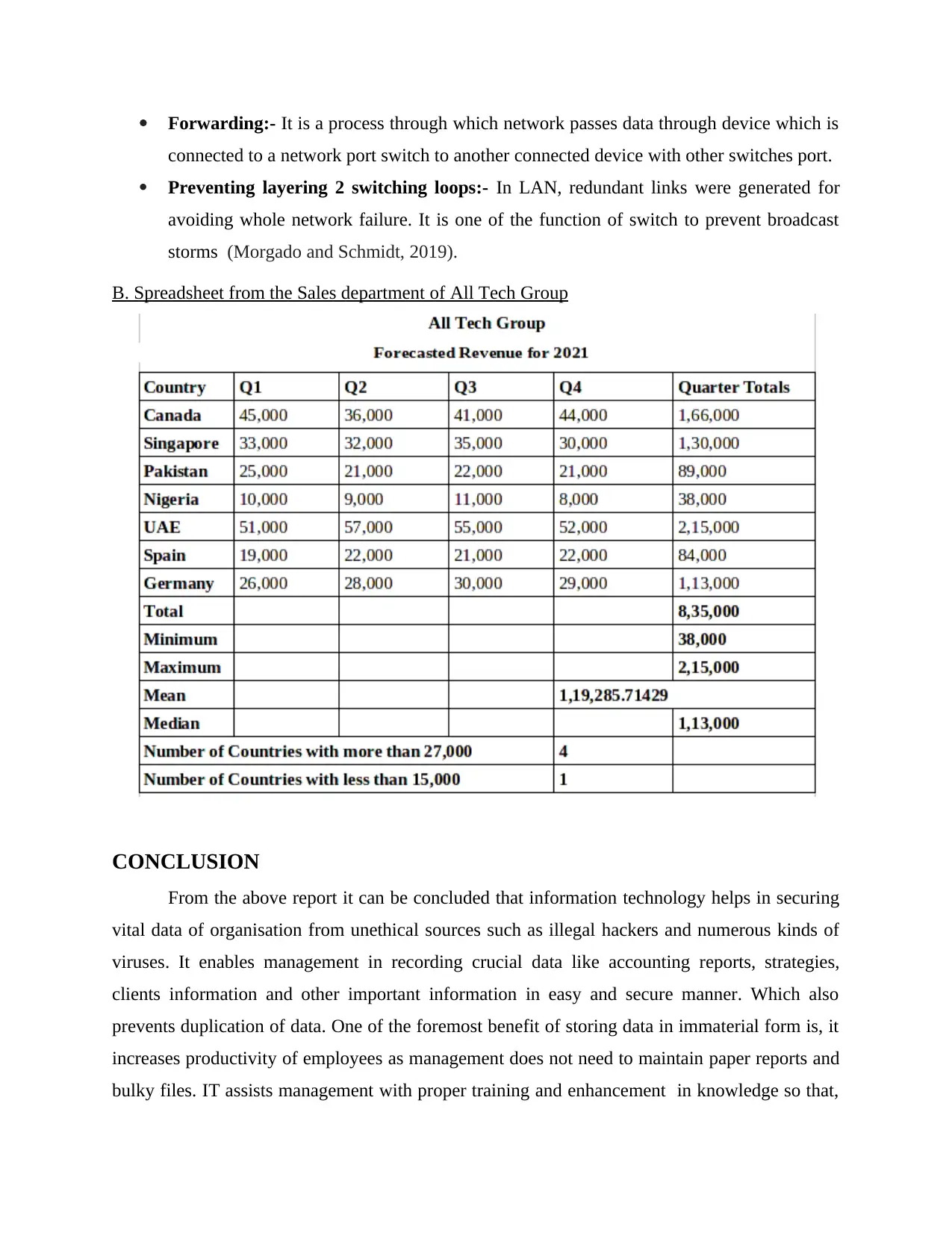
B. Spreadsheet from the Sales department of All Tech Group
CONCLUSION
From the above report it can be concluded that information technology helps in securing
vital data of organisation from unethical sources such as illegal hackers and numerous kinds of
viruses. It enables management in recording crucial data like accounting reports, strategies,
clients information and other important information in easy and secure manner. Which also
prevents duplication of data. One of the foremost benefit of storing data in immaterial form is, it
increases productivity of employees as management does not need to maintain paper reports and
bulky files. IT assists management with proper training and enhancement in knowledge so that,
connected to a network port switch to another connected device with other switches port.
Preventing layering 2 switching loops:- In LAN, redundant links were generated for
avoiding whole network failure. It is one of the function of switch to prevent broadcast
storms (Morgado and Schmidt, 2019).
B. Spreadsheet from the Sales department of All Tech Group
CONCLUSION
From the above report it can be concluded that information technology helps in securing
vital data of organisation from unethical sources such as illegal hackers and numerous kinds of
viruses. It enables management in recording crucial data like accounting reports, strategies,
clients information and other important information in easy and secure manner. Which also
prevents duplication of data. One of the foremost benefit of storing data in immaterial form is, it
increases productivity of employees as management does not need to maintain paper reports and
bulky files. IT assists management with proper training and enhancement in knowledge so that,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

organisational operations can match with time and new trends in market., this update leads in
producing creative ideas which raise organisation's profit and market share. Report highlights
various pros of cloud computing in operational activities of companies. Few security frameworks
are described above through which management can secure data and have control over data.
producing creative ideas which raise organisation's profit and market share. Report highlights
various pros of cloud computing in operational activities of companies. Few security frameworks
are described above through which management can secure data and have control over data.

REFERENCES
(Books and journals)
Kaur, R. and Kinger, S., 2018. Analysis of security algorithms in cloud computing. International
Journal of Application or Innovation in Engineering & Management (IJAIEM), 3(3),
pp.171-176.
EL AMRANI, C. and GIBET TANI, H., 2018. Smarter round robin scheduling algorithm for
cloud computing and big data. Journal of Data Mining & Digital Humanities.
Kalpana, P. and Singaraju, S., 2022. Data security in cloud computing using RSA
algorithm. International Journal of research in computer and communication
technology, IJRCCT, ISSN, pp.2278-5841.
Ghosh, A. and Arce, I., 2019. Guest editors' introduction: In cloud computing we trust-But
should we?. IEEE security & privacy, 8(6), pp.14-16.
Paul, P.K. and Dangwal, K.L., 2018. Cloud based educational systems and its challenges and
opportunities and Issues. Turkish Online Journal of Distance Education, 15(1), pp.89-
98.
Ibrahim, O., Nilashi, M. and Alzurqa, E., 2019. Cloud computing adoption model for e-
government implementation. Information Development, 33(3), pp.303-323.
Kazim, M. and Zhu, S.Y., 2021. A survey on top security threats in cloud computing.
Jou, M. and Wang, J., 2018. Observations of achievement and motivation in using cloud
computing driven CAD: Comparison of college students with high school and
vocational high school backgrounds. Computers in Human Behavior, 29(2), pp.364-
369.
Morgado, E.M. and Schmidt, R., 2019, June. Increasing Moodle resources through cloud
computing. In 7th Iberian Conference on Information Systems and Technologies (CISTI
2012) (pp. 1-4). IEEE.
Alizadeh, M. and Hassan, W.H., 2019, July. Challenges and opportunities of mobile cloud
computing. In 2013 9th International Wireless Communications and Mobile Computing
Conference (IWCMC) (pp. 660-666). ieee.
Chandra, D.G. and Borah, M.D., 2021, February. Cost benefit analysis of cloud computing in
education. In 2012 International Conference on Computing, Communication and
Applications (pp. 1-6). IEEE.
Yuvaraj, M., 2020. Cloud computing applications in Indian Central University libraries: A study
of librariansuse. Library Philosophy and Practice (e-journal), 992.
Sharma, M., Gupta, R. and Acharya, P., 2020. Analysing the adoption of cloud computing
service: A systematic literature review. Global Knowledge, Memory and
Communication.
Dečman, M. and Vintar, M., 2019, April. A possible solution for digital preservation of e‐
government: A centralised repository within a cloud computing framework. In Aslib
Proceedings. Emerald Group Publishing Limited.
Singh, A. and Malhotra, M., 2021. Security concerns at various levels of cloud computing
paradigm: A review. International journal of computer networks and applications, 2(2),
pp.41-45.
(Books and journals)
Kaur, R. and Kinger, S., 2018. Analysis of security algorithms in cloud computing. International
Journal of Application or Innovation in Engineering & Management (IJAIEM), 3(3),
pp.171-176.
EL AMRANI, C. and GIBET TANI, H., 2018. Smarter round robin scheduling algorithm for
cloud computing and big data. Journal of Data Mining & Digital Humanities.
Kalpana, P. and Singaraju, S., 2022. Data security in cloud computing using RSA
algorithm. International Journal of research in computer and communication
technology, IJRCCT, ISSN, pp.2278-5841.
Ghosh, A. and Arce, I., 2019. Guest editors' introduction: In cloud computing we trust-But
should we?. IEEE security & privacy, 8(6), pp.14-16.
Paul, P.K. and Dangwal, K.L., 2018. Cloud based educational systems and its challenges and
opportunities and Issues. Turkish Online Journal of Distance Education, 15(1), pp.89-
98.
Ibrahim, O., Nilashi, M. and Alzurqa, E., 2019. Cloud computing adoption model for e-
government implementation. Information Development, 33(3), pp.303-323.
Kazim, M. and Zhu, S.Y., 2021. A survey on top security threats in cloud computing.
Jou, M. and Wang, J., 2018. Observations of achievement and motivation in using cloud
computing driven CAD: Comparison of college students with high school and
vocational high school backgrounds. Computers in Human Behavior, 29(2), pp.364-
369.
Morgado, E.M. and Schmidt, R., 2019, June. Increasing Moodle resources through cloud
computing. In 7th Iberian Conference on Information Systems and Technologies (CISTI
2012) (pp. 1-4). IEEE.
Alizadeh, M. and Hassan, W.H., 2019, July. Challenges and opportunities of mobile cloud
computing. In 2013 9th International Wireless Communications and Mobile Computing
Conference (IWCMC) (pp. 660-666). ieee.
Chandra, D.G. and Borah, M.D., 2021, February. Cost benefit analysis of cloud computing in
education. In 2012 International Conference on Computing, Communication and
Applications (pp. 1-6). IEEE.
Yuvaraj, M., 2020. Cloud computing applications in Indian Central University libraries: A study
of librariansuse. Library Philosophy and Practice (e-journal), 992.
Sharma, M., Gupta, R. and Acharya, P., 2020. Analysing the adoption of cloud computing
service: A systematic literature review. Global Knowledge, Memory and
Communication.
Dečman, M. and Vintar, M., 2019, April. A possible solution for digital preservation of e‐
government: A centralised repository within a cloud computing framework. In Aslib
Proceedings. Emerald Group Publishing Limited.
Singh, A. and Malhotra, M., 2021. Security concerns at various levels of cloud computing
paradigm: A review. International journal of computer networks and applications, 2(2),
pp.41-45.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
