Technology in Organizations: Cloud Computing, Security at Amazon
VerifiedAdded on 2023/06/08
|17
|4088
|293
Report
AI Summary
This report explores the role of technology in organizations, focusing on cloud computing, security, and privacy, with Amazon as a case study. It discusses the benefits of cloud computing, including improved productivity, flexibility, and cost savings. The report also highlights essential security requirements like integrity, authentication, and confidentiality, and examines IT security frameworks such as ISO 27000 series and NIST SP 800-53. Furthermore, the document covers the importance of telecommunications and spreadsheets in networking infrastructure for business operations. Desklib provides access to similar solved assignments and past papers for students.

TECHNOLOGY IN
ORGANIZATION
ORGANIZATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
QUESTION 1 — Case study...........................................................................................................3
QUESTION 2 — Security and Privacy...........................................................................................5
QUESTION — 3 Telecommunication and spreadsheets.................................................................8
a)..................................................................................................................................................8
B)..................................................................................................................................................9
........................................................................................................................................................16
CONCLUSION..............................................................................................................................16
REFERENCES................................................................................................................................1
INTRODUCTION...........................................................................................................................3
QUESTION 1 — Case study...........................................................................................................3
QUESTION 2 — Security and Privacy...........................................................................................5
QUESTION — 3 Telecommunication and spreadsheets.................................................................8
a)..................................................................................................................................................8
B)..................................................................................................................................................9
........................................................................................................................................................16
CONCLUSION..............................................................................................................................16
REFERENCES................................................................................................................................1

INTRODUCTION
Technology in organization are most important in business to keep business fully organized
and technology consist the cloud computing, track process of products and services, auto mobile
technology, etc. Technology helps in enhance the efficiency of company and its products and
services. this helps in manage the data flows and employees record within the organization and
help operation to reduce cost. the technology in business helps business to enhance their growth
and developments rapidly. technologies also demand task for workers and new skills which are
required using technology. Amazon company is the American international technology company
This includes the cloud computing, e-commerce, artificial intelligence and digital streaming, etc.
the report will discuss the role of cloud computing and its benefits to amazon company to adopt
this technology as well as security and privacy which must implement by organization. this
report will also elaborate the telecommunication and spreadsheets a networking infrastructure for
business operations.
QUESTION 1 — Case study
Amazon company is the multinational company and largest online retailer. It is the internet
based business enterprise that focus on the digital streaming, artificial intelligence services, cloud
computing and e-commerce services. company offer many products range such as books,
jewellery, electronics, clothing, beauty suppliers, toys, etc. (Dastin, 2018). Amazon have its
software developments centres, websites, customers service centres and data centres around the
world. it also offers the expanding platform of products and services in retail such as Amazon
marketplace, woot, merch by Amazon, etc. In the context of consumer technology, it provides
the Amazon kindle, Amazon fire TV, Amazon, Echo, etc.
Cloud computing is the provision of computer services that includes the storage, servers,
networking, analytics, software, servers, intelligence, etc. over the internet to offer flexible
resources, faster innovation and economics scale. It is not the trendy application that people used
it for they share their videos and photos. The cloud computing is the part of business model. It
not only helps in assess data and business stores but it also helps in operate business. Cloud
Technology in organization are most important in business to keep business fully organized
and technology consist the cloud computing, track process of products and services, auto mobile
technology, etc. Technology helps in enhance the efficiency of company and its products and
services. this helps in manage the data flows and employees record within the organization and
help operation to reduce cost. the technology in business helps business to enhance their growth
and developments rapidly. technologies also demand task for workers and new skills which are
required using technology. Amazon company is the American international technology company
This includes the cloud computing, e-commerce, artificial intelligence and digital streaming, etc.
the report will discuss the role of cloud computing and its benefits to amazon company to adopt
this technology as well as security and privacy which must implement by organization. this
report will also elaborate the telecommunication and spreadsheets a networking infrastructure for
business operations.
QUESTION 1 — Case study
Amazon company is the multinational company and largest online retailer. It is the internet
based business enterprise that focus on the digital streaming, artificial intelligence services, cloud
computing and e-commerce services. company offer many products range such as books,
jewellery, electronics, clothing, beauty suppliers, toys, etc. (Dastin, 2018). Amazon have its
software developments centres, websites, customers service centres and data centres around the
world. it also offers the expanding platform of products and services in retail such as Amazon
marketplace, woot, merch by Amazon, etc. In the context of consumer technology, it provides
the Amazon kindle, Amazon fire TV, Amazon, Echo, etc.
Cloud computing is the provision of computer services that includes the storage, servers,
networking, analytics, software, servers, intelligence, etc. over the internet to offer flexible
resources, faster innovation and economics scale. It is not the trendy application that people used
it for they share their videos and photos. The cloud computing is the part of business model. It
not only helps in assess data and business stores but it also helps in operate business. Cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

computing are mostly used by the large and medium business as well as they are work with the
major cloud providers. It is most important for business because it helps in provide the data
recovery, flexibility, easy access, maintenance and high level of security. Cloud computing is
more affordable for business rather to invest on another machines. There are various roles of
cloud computing in business such as it helps in improve business productivity, performance its
organization speeds and it’s also helps in the better security (Risse, 2019). There are various
roles of cloud computing which involved in the cloud computing arrangements such as
regulators, cloud broker, cloud customers, cloud service providers and cloud broker.
With the help of cloud computing service providers, that helps business in hold
networking, software’s, infrastructure, etc. this helps in manage the employees and also helps in
provide security to employees within the business. In the cloud customers, it seeks the more
cloud services form the cloud service providers. In the context of cloud broke, the organization
get the many changes within the organization and that helps in migrate their essential to
organization (Deng, Wang and Song, 2021). The cloud computing also helps in access the
security brokers to business and it is most important for business to improve is securing and
protect business data and its information. This provides the encrypting to sensitive data and helps
in preventing the misuse of data.
There are various roles of cloud computing in business which are beneficial for the
company that helps in reduce the IT cost, provide flexibility, access automatics updates,
collaborate efficiency and protect business data and information (Wang, 2018).
There are various benefits of cloud computing in business if they are adopting it within
the organization. Benefits such as security, flexibility, cost savings, mobility, insight, quality
control, loss prevention, increase collaboration, provide competitive edge, automatic software
updates, sustainability, disaster recovery, etc. the cloud computing helps in save the business cost
and its investments (Saini, Upadhyaya and Khandelwal, 2019). The cloud computing helps in
easy access the business data and also helps in save money and its time in project beginning. In
the organization, the pay-as-you-go systems also used in the data storage to provide services to
clients and stakeholders. Company not require charging with space. It is more beneficial for
business because that leads in lower cost and higher returns.
major cloud providers. It is most important for business because it helps in provide the data
recovery, flexibility, easy access, maintenance and high level of security. Cloud computing is
more affordable for business rather to invest on another machines. There are various roles of
cloud computing in business such as it helps in improve business productivity, performance its
organization speeds and it’s also helps in the better security (Risse, 2019). There are various
roles of cloud computing which involved in the cloud computing arrangements such as
regulators, cloud broker, cloud customers, cloud service providers and cloud broker.
With the help of cloud computing service providers, that helps business in hold
networking, software’s, infrastructure, etc. this helps in manage the employees and also helps in
provide security to employees within the business. In the cloud customers, it seeks the more
cloud services form the cloud service providers. In the context of cloud broke, the organization
get the many changes within the organization and that helps in migrate their essential to
organization (Deng, Wang and Song, 2021). The cloud computing also helps in access the
security brokers to business and it is most important for business to improve is securing and
protect business data and its information. This provides the encrypting to sensitive data and helps
in preventing the misuse of data.
There are various roles of cloud computing in business which are beneficial for the
company that helps in reduce the IT cost, provide flexibility, access automatics updates,
collaborate efficiency and protect business data and information (Wang, 2018).
There are various benefits of cloud computing in business if they are adopting it within
the organization. Benefits such as security, flexibility, cost savings, mobility, insight, quality
control, loss prevention, increase collaboration, provide competitive edge, automatic software
updates, sustainability, disaster recovery, etc. the cloud computing helps in save the business cost
and its investments (Saini, Upadhyaya and Khandelwal, 2019). The cloud computing helps in
easy access the business data and also helps in save money and its time in project beginning. In
the organization, the pay-as-you-go systems also used in the data storage to provide services to
clients and stakeholders. Company not require charging with space. It is more beneficial for
business because that leads in lower cost and higher returns.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The company adopted the cloud computing then it helps in secure the data. It also helps
business to easily remote the data at anywhere and any place. Data and information of business is
encryption and less accessible for the hackers and thefts. It also helps in provide the flexibility
and the cloud computes services can easily access and meet the demands of business. This helps
in improve the business infrastructure and provide efficiency to overall business (Widyastuti and
Irwansyah, 2018). It also helps in provide the mobile access to business such as devices and
smartphones. Cloud computing also helps in improve the customer services which are most
important fir business to enhance the productivity and profitability. This also allow that
customers can easily connect with employees of business to resolve the feedback and queries.
This is beneficial for the better documents control and business can exchange the large volume
of information in the production loop and also helps in create the lots of conflicting files in the
various titles ad formats.
The cloud computing also helps in offer the various application to business through the
services such as platform as a service, software as a service, infrastructure as a service. The
customers of business also have an option to create a public, private and hybrid network access.
Cloud computing technology also helps in provide the environmental benefits to business and
helps in reduce the carbon footprints (Oke, 2021). Cloud computing helps in enhance the
productivity of business and also helps in improve the profitability of organization and it also
rapidly involve in the business environments. The technology is the successful implementation
strategy for the organization and also helps in monitor business at very stage. This helps in
access to automatic updates for the business IT requirements and it helps in provide regular
update system with the latest technology and offer up to date version.
QUESTION 2 — Security and Privacy
The security requirements are referred as the statements of require for the security
functionality that helps in ensures many securities properties of software that has been satisfied.
The security requirements help in business to prepared for the security threats that company a
face and endangering business (Kumar and Goyal, 2019). There are various types of security
requirements in information technology such as secure functional requirements, non-functional
requirements, functional requirements and secure developments requirements.
business to easily remote the data at anywhere and any place. Data and information of business is
encryption and less accessible for the hackers and thefts. It also helps in provide the flexibility
and the cloud computes services can easily access and meet the demands of business. This helps
in improve the business infrastructure and provide efficiency to overall business (Widyastuti and
Irwansyah, 2018). It also helps in provide the mobile access to business such as devices and
smartphones. Cloud computing also helps in improve the customer services which are most
important fir business to enhance the productivity and profitability. This also allow that
customers can easily connect with employees of business to resolve the feedback and queries.
This is beneficial for the better documents control and business can exchange the large volume
of information in the production loop and also helps in create the lots of conflicting files in the
various titles ad formats.
The cloud computing also helps in offer the various application to business through the
services such as platform as a service, software as a service, infrastructure as a service. The
customers of business also have an option to create a public, private and hybrid network access.
Cloud computing technology also helps in provide the environmental benefits to business and
helps in reduce the carbon footprints (Oke, 2021). Cloud computing helps in enhance the
productivity of business and also helps in improve the profitability of organization and it also
rapidly involve in the business environments. The technology is the successful implementation
strategy for the organization and also helps in monitor business at very stage. This helps in
access to automatic updates for the business IT requirements and it helps in provide regular
update system with the latest technology and offer up to date version.
QUESTION 2 — Security and Privacy
The security requirements are referred as the statements of require for the security
functionality that helps in ensures many securities properties of software that has been satisfied.
The security requirements help in business to prepared for the security threats that company a
face and endangering business (Kumar and Goyal, 2019). There are various types of security
requirements in information technology such as secure functional requirements, non-functional
requirements, functional requirements and secure developments requirements.

There are three security requirements which must be implemented by the organization to
secure the data and information of business. The three major security requirements are integrity,
authentication and confidentiality. There are the security policies which are responding to the
requirements for the integrity, authentication and confidentiality. In the context of integrity, it
helps in determines that what type of data must be validated and protected. The company
software must be protected with the subversion that they include the destruction, insertion,
tampering, corruption. The integrity helps in preserved the software developments. In the context
of confidentiality, it is also known as privacy (Abdel Hakeem, Hussein and Kim, 2022). It helps
in protect the company private information to prevent the unauthorized access. The
authentication is helps in protect the business user logon information and data and manage the
restricted area of business. The authentication includes the storage of passwords, encryption,
transmittal and spoofing. Authentication are most important for business to secure the data and
information as well as sensitive data of company from the hackers and thefts.
The security requirements cover the various areas such as network and security data, data
validation and sanitization, authentication and password management, cryptography and key
management, etc. authentication and password management are most important for business to
manage and control the data from the frauds and hackers. The business data are always sensitive
and mots important for survive business for the long term assess. The security requirements is
consisted the associated security measures. The confidentiality consists the physical control,
security policy and access control that all are most important for the business security. The
integrity assess control, physical protection, attack detection.
The IT security framework is the series of documentation process that helps in defines the
procedures, policies around the management of information and implement security control. That
type of frameworks are blueprints of reducing vulnerabilities and helps in managing risk of
business. Information security frameworks are requiring to manage the business security and this
framework required so regulation and standards. The business organization can customize
frameworks to solve the specific information security problems such as various regulatory
compliance goals, and industry specific requirements (Makhdoom, 2020). The security
frameworks are most important for business because that effectively control and support
compliance, operational and audit requirements. The frameworks help in provide the
administrative activities and policies for the business information security managements.
secure the data and information of business. The three major security requirements are integrity,
authentication and confidentiality. There are the security policies which are responding to the
requirements for the integrity, authentication and confidentiality. In the context of integrity, it
helps in determines that what type of data must be validated and protected. The company
software must be protected with the subversion that they include the destruction, insertion,
tampering, corruption. The integrity helps in preserved the software developments. In the context
of confidentiality, it is also known as privacy (Abdel Hakeem, Hussein and Kim, 2022). It helps
in protect the company private information to prevent the unauthorized access. The
authentication is helps in protect the business user logon information and data and manage the
restricted area of business. The authentication includes the storage of passwords, encryption,
transmittal and spoofing. Authentication are most important for business to secure the data and
information as well as sensitive data of company from the hackers and thefts.
The security requirements cover the various areas such as network and security data, data
validation and sanitization, authentication and password management, cryptography and key
management, etc. authentication and password management are most important for business to
manage and control the data from the frauds and hackers. The business data are always sensitive
and mots important for survive business for the long term assess. The security requirements is
consisted the associated security measures. The confidentiality consists the physical control,
security policy and access control that all are most important for the business security. The
integrity assess control, physical protection, attack detection.
The IT security framework is the series of documentation process that helps in defines the
procedures, policies around the management of information and implement security control. That
type of frameworks are blueprints of reducing vulnerabilities and helps in managing risk of
business. Information security frameworks are requiring to manage the business security and this
framework required so regulation and standards. The business organization can customize
frameworks to solve the specific information security problems such as various regulatory
compliance goals, and industry specific requirements (Makhdoom, 2020). The security
frameworks are most important for business because that effectively control and support
compliance, operational and audit requirements. The frameworks help in provide the
administrative activities and policies for the business information security managements.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The frameworks can be applied according to the compliance requirements and industry.
There are various types of security frameworks which helps in security professionals manage and
organize an information security programs. The organizations can use the frameworks for control
the data and security according to the industry type. The security frameworks such as discussed
below.
ISO 27000 series is the frameworks and IT security standards and that was developed by
the international organization for standardization. The ISO is the flexible security frameworks
from the others frameworks and mostly organization used this framework for the security and
data control. There are two primary standards in these frameworks such as 27001 and 27002
because it establishes the procedure and requirements for built an information security
management (Abraham, Schneider and Vom Brocke, 2019). The ISO also address the cloud
computing and provide guidelines related to the disaster recover programs, provide storage
security and protection and collection of digital evidence. This mostly used in the public and
private sectors organization.
In the context of NIST SP 800-53, it is mainly focused on the information security virtually and
also focus on the increasing the cloud security. This security also used by business to improve
the security within the organization with the data policies. This framework is mostly used in the
private sectors and it’s also includes the cyber security frameworks.
The NIST CSF frameworks helps in improve the critical infrastructure of cyber security.
The infrastructures such as energy production, food suppliers, healthcare transportations and
delivery, communication, water supplies etc. this is mainly focused on the risk management and
risk analysis of security and control data. The security control is based on the various phases
such as detect, respond, recover, identify, protect. It can be sued by the both private and public
organization.
The critical security control frameworks can also be used by business to manage the
operation control and technical security which are most important for business. This is basically
focused on increase the technical infrastructure of the data control and that includes the data
protection, audit log management, inventory and control of business assets (Janssen, 2020). It is
most useful for the business IT departments and that can be used by companies lacking the
technical information security experience.
There are various types of security frameworks which helps in security professionals manage and
organize an information security programs. The organizations can use the frameworks for control
the data and security according to the industry type. The security frameworks such as discussed
below.
ISO 27000 series is the frameworks and IT security standards and that was developed by
the international organization for standardization. The ISO is the flexible security frameworks
from the others frameworks and mostly organization used this framework for the security and
data control. There are two primary standards in these frameworks such as 27001 and 27002
because it establishes the procedure and requirements for built an information security
management (Abraham, Schneider and Vom Brocke, 2019). The ISO also address the cloud
computing and provide guidelines related to the disaster recover programs, provide storage
security and protection and collection of digital evidence. This mostly used in the public and
private sectors organization.
In the context of NIST SP 800-53, it is mainly focused on the information security virtually and
also focus on the increasing the cloud security. This security also used by business to improve
the security within the organization with the data policies. This framework is mostly used in the
private sectors and it’s also includes the cyber security frameworks.
The NIST CSF frameworks helps in improve the critical infrastructure of cyber security.
The infrastructures such as energy production, food suppliers, healthcare transportations and
delivery, communication, water supplies etc. this is mainly focused on the risk management and
risk analysis of security and control data. The security control is based on the various phases
such as detect, respond, recover, identify, protect. It can be sued by the both private and public
organization.
The critical security control frameworks can also be used by business to manage the
operation control and technical security which are most important for business. This is basically
focused on increase the technical infrastructure of the data control and that includes the data
protection, audit log management, inventory and control of business assets (Janssen, 2020). It is
most useful for the business IT departments and that can be used by companies lacking the
technical information security experience.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

HITTRUST common security frameworks are includes the risk managements and risk
analysis frameworks with the business operational requirements. It is mostly considering by the
healthcare sectors and business.
The company must keep in mid while they are selecting the security framework that there
are requirements of regulatory compliance requirements, industry, it and security and customers’
expectations for the organization. Adopted the security frameworks by organization can help in
security programs and company must be conscious when that selecting the frameworks. While
selecting the frameworks can result in wasted time, security gap, overload team and wasted
money. The company main consideration is compliance requirements from a contractual
perspectives and regulatory. With the compliance requirements the frameworks can be developed
for the specific industry and regulations.
QUESTION — 3 Telecommunication and spreadsheets
a)
The chosen organization is the sage group plc company and its is knowns as the sage. It is
the British multinational software company in United kingdom. Its is the second largest company
in united kingdom. The networking infrastructure is referred as the mix of software applications,
hardware devices and network services. The software infrastructure includes the operating
systems, managements tools and monitoring (Malawade, 2021.). The hardware infrastructure
includes the hubs, repeaters, bridges, gateways, routers, etc. there are three components of
networking infrastructures such as services, media and devices that helps in run, build, and
maintain the IT network. Its is the mots important part of the technology organization. It operates
the business operations with the network infrastructure which must be safe, reliable, scalable and
robust is crucial.
The network infrastructure management of sage company is focus on the various aspects
of networking such as configuration management, network infrastructure monitoring,
performance management, security management and fault management for business. The
security management in business helps in secure the sage company to protect the data and
information from the various network based and also this network is safe for business. The fault
management helps in identify the business problems and helps in fix the problems and improve
the business efficiency.
analysis frameworks with the business operational requirements. It is mostly considering by the
healthcare sectors and business.
The company must keep in mid while they are selecting the security framework that there
are requirements of regulatory compliance requirements, industry, it and security and customers’
expectations for the organization. Adopted the security frameworks by organization can help in
security programs and company must be conscious when that selecting the frameworks. While
selecting the frameworks can result in wasted time, security gap, overload team and wasted
money. The company main consideration is compliance requirements from a contractual
perspectives and regulatory. With the compliance requirements the frameworks can be developed
for the specific industry and regulations.
QUESTION — 3 Telecommunication and spreadsheets
a)
The chosen organization is the sage group plc company and its is knowns as the sage. It is
the British multinational software company in United kingdom. Its is the second largest company
in united kingdom. The networking infrastructure is referred as the mix of software applications,
hardware devices and network services. The software infrastructure includes the operating
systems, managements tools and monitoring (Malawade, 2021.). The hardware infrastructure
includes the hubs, repeaters, bridges, gateways, routers, etc. there are three components of
networking infrastructures such as services, media and devices that helps in run, build, and
maintain the IT network. Its is the mots important part of the technology organization. It operates
the business operations with the network infrastructure which must be safe, reliable, scalable and
robust is crucial.
The network infrastructure management of sage company is focus on the various aspects
of networking such as configuration management, network infrastructure monitoring,
performance management, security management and fault management for business. The
security management in business helps in secure the sage company to protect the data and
information from the various network based and also this network is safe for business. The fault
management helps in identify the business problems and helps in fix the problems and improve
the business efficiency.

The company used the wireless infrastructure of the growth of internet and technology
and consider the network management and security as well as client consideration for business.
The wireless design to integrate the telecommunication infrastructure of business ans it helps in
save time and money both.
The wireless infrastructure are mostly used in the business and sage used the wireless
infrastructure because it is the technology and software company so, it runs its business
operation in effective and effectiveness way. There are various types of wireless infrastructure
which used by the sage plc such as LAN, WAN and MAN. The wireless LAN technology helps
business to provide the internet access in the limited areas fir business operations. This also
encrypted with strong passwords so, outside of people not able to connect with the WLAN.
The wireless MAN is refer as the metropolitan are networks and that provide the access
of internet to people who are outside if sage business and employees of company. The wireless
personal area networks are comes under the limited areas (Pathan, 2018). This includes the
devices which can be connected maximum of 100 meters like Zigbee and Bluetooth. This
technology helps in increase the range of technologies in the wireless infrastructure.
This network infrastructure helps in business operation because it is more flexible for
company, ease of installations, it helps in increase the business efficiency, helps in save time and
money, remote the network management. It helps in improved the data communication of sage
business result in transfer the information business with the customers and parters of company.
This helps in provide the multi device capacity to connect the laptop, phone, Tablets and other
wireless device network which can easily assess by their employees and clients of company and
helps in accomplish the task, goals and objectives of company in effective and efficient ways
throughout the day. The business use this types of networking infrastructure in the technology
and software organization for effectively and efficiency business operations.
B)
Quarter total- In this segment, the total of all quarters was enumerated using excel tool.
Command= Sum (range of all quarters)
and consider the network management and security as well as client consideration for business.
The wireless design to integrate the telecommunication infrastructure of business ans it helps in
save time and money both.
The wireless infrastructure are mostly used in the business and sage used the wireless
infrastructure because it is the technology and software company so, it runs its business
operation in effective and effectiveness way. There are various types of wireless infrastructure
which used by the sage plc such as LAN, WAN and MAN. The wireless LAN technology helps
business to provide the internet access in the limited areas fir business operations. This also
encrypted with strong passwords so, outside of people not able to connect with the WLAN.
The wireless MAN is refer as the metropolitan are networks and that provide the access
of internet to people who are outside if sage business and employees of company. The wireless
personal area networks are comes under the limited areas (Pathan, 2018). This includes the
devices which can be connected maximum of 100 meters like Zigbee and Bluetooth. This
technology helps in increase the range of technologies in the wireless infrastructure.
This network infrastructure helps in business operation because it is more flexible for
company, ease of installations, it helps in increase the business efficiency, helps in save time and
money, remote the network management. It helps in improved the data communication of sage
business result in transfer the information business with the customers and parters of company.
This helps in provide the multi device capacity to connect the laptop, phone, Tablets and other
wireless device network which can easily assess by their employees and clients of company and
helps in accomplish the task, goals and objectives of company in effective and efficient ways
throughout the day. The business use this types of networking infrastructure in the technology
and software organization for effectively and efficiency business operations.
B)
Quarter total- In this segment, the total of all quarters was enumerated using excel tool.
Command= Sum (range of all quarters)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
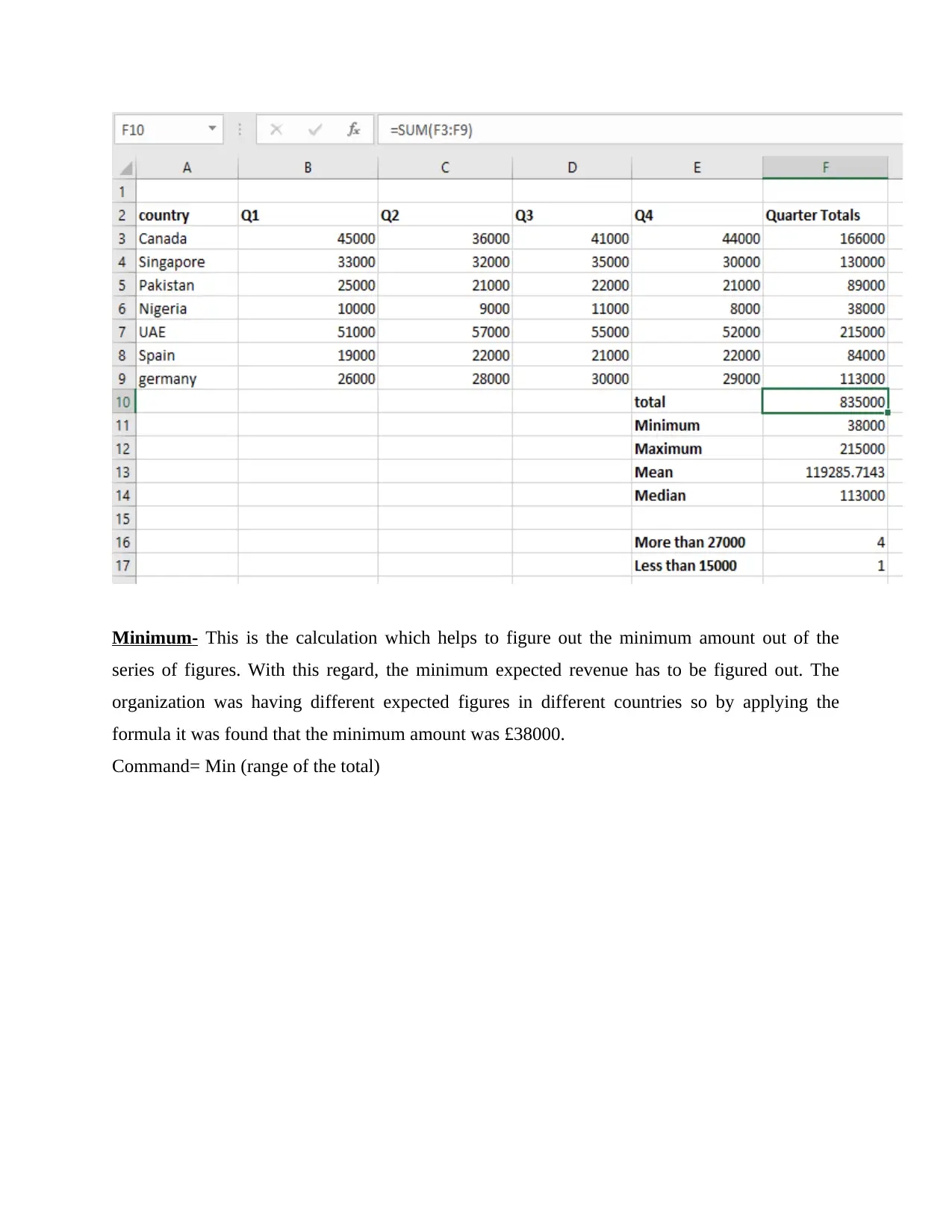
Minimum- This is the calculation which helps to figure out the minimum amount out of the
series of figures. With this regard, the minimum expected revenue has to be figured out. The
organization was having different expected figures in different countries so by applying the
formula it was found that the minimum amount was £38000.
Command= Min (range of the total)
series of figures. With this regard, the minimum expected revenue has to be figured out. The
organization was having different expected figures in different countries so by applying the
formula it was found that the minimum amount was £38000.
Command= Min (range of the total)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
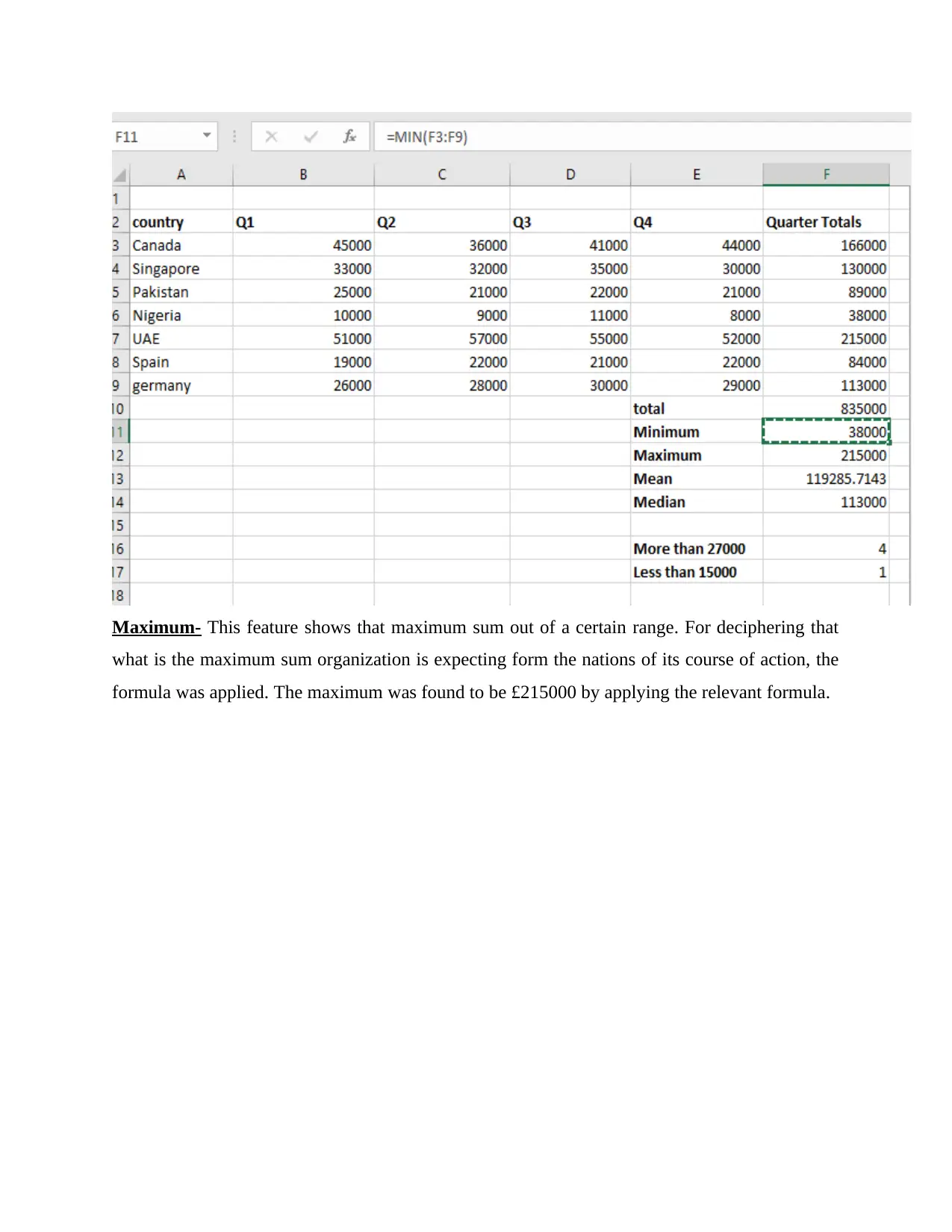
Maximum- This feature shows that maximum sum out of a certain range. For deciphering that
what is the maximum sum organization is expecting form the nations of its course of action, the
formula was applied. The maximum was found to be £215000 by applying the relevant formula.
what is the maximum sum organization is expecting form the nations of its course of action, the
formula was applied. The maximum was found to be £215000 by applying the relevant formula.
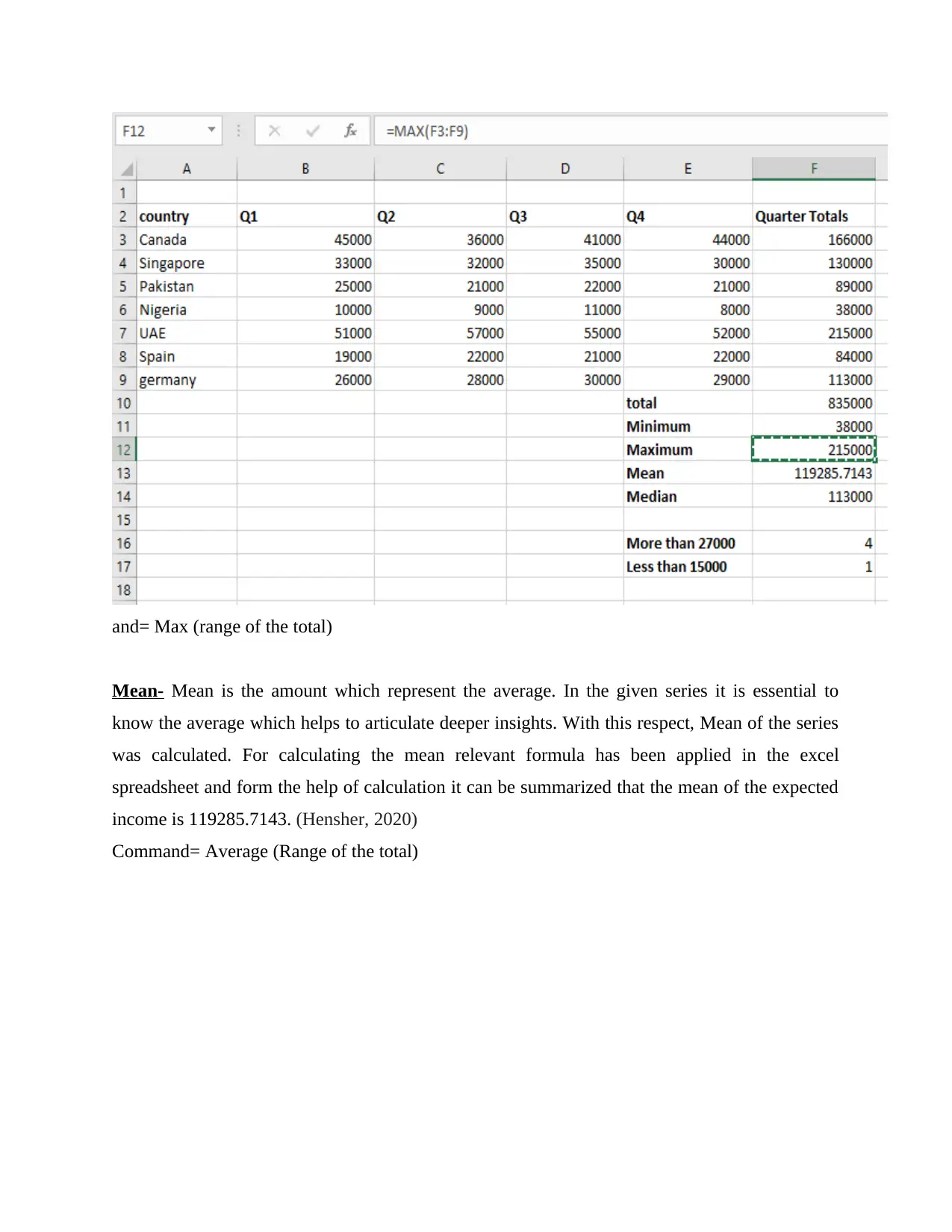
and= Max (range of the total)
Mean- Mean is the amount which represent the average. In the given series it is essential to
know the average which helps to articulate deeper insights. With this respect, Mean of the series
was calculated. For calculating the mean relevant formula has been applied in the excel
spreadsheet and form the help of calculation it can be summarized that the mean of the expected
income is 119285.7143. (Hensher, 2020)
Command= Average (Range of the total)
Mean- Mean is the amount which represent the average. In the given series it is essential to
know the average which helps to articulate deeper insights. With this respect, Mean of the series
was calculated. For calculating the mean relevant formula has been applied in the excel
spreadsheet and form the help of calculation it can be summarized that the mean of the expected
income is 119285.7143. (Hensher, 2020)
Command= Average (Range of the total)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

