Technology in Organization
VerifiedAdded on 2022/11/30
|16
|4290
|430
AI Summary
This article discusses the role of technology in organizations, focusing on the use of big data, IT security, and data privacy. It explores how technology helps in managing data flow, tracking processes, and maintaining employee records. The article also highlights the role of big data in education and human resources, as well as the benefits it brings to organizations. Additionally, it covers IT security measures and the key provisions of GDPR.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Technology in
organization
organization
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Contents
Introduction................................................................................................................................................3
Main body..................................................................................................................................................3
Identify and discussing Big Data and its role of Arden University......................................................3
IT security and data privacy....................................................................................................................6
Cellular network, components and benefits..........................................................................................9
Conclusion...............................................................................................................................................12
References..............................................................................................................................................14
Introduction................................................................................................................................................3
Main body..................................................................................................................................................3
Identify and discussing Big Data and its role of Arden University......................................................3
IT security and data privacy....................................................................................................................6
Cellular network, components and benefits..........................................................................................9
Conclusion...............................................................................................................................................12
References..............................................................................................................................................14

Introduction
Businesses are growing with the use of advance technology. For the companies
sustainability it is necessary to adopt innovation which is created by technology. The
use of technology provides the advantage to the organization for operating in fast pace.
The role of technology is essential as it provides new approaches o mange the business
activities efficiently and effectively with minimum manpower and reduces the cost of
doing business. The use of technology in the organization is very important as it helps in
maintain the data flow, track processes and maintains employee records (Breheny and
et. al., 2018). The term technology refers to the skills, techniques, methods and process
used in the business for production and involving scientific investigation. It is a branch of
scientific knowledge deal with engineering and applied science. With the use of
technology in the organization it brings growth, improves business communication,
production and helps in keeping the record related to employees, financial, and
inventory etc. It helps the governments, individuals in increasing their efficiency by
having a vast knowledge of information technology. The report is done on the case of
Arden University of united Kingdom which has done expansion of its business in
Germany. The discussed topic includes the big data, security and privacy,
telecommunication of cellular network.
Main body
Identify and discussing Big Data and its role of Arden University
Arden University was recognized in 1990 by resource development international.
It is a private profit teaching firm in the UK which provides distance learning with various
undergraduates and post graduates program. The term big data was used by John
Mashey in 1990. Big data refer to a field where data which are too complex or large are
analyzed systematically for extracting information and dealing with data sets. It involves
data processing application. It offers statistical power. The analysis of Big data involves
data capturing, data analysis, data search, sharing, storing, and transferring,
Businesses are growing with the use of advance technology. For the companies
sustainability it is necessary to adopt innovation which is created by technology. The
use of technology provides the advantage to the organization for operating in fast pace.
The role of technology is essential as it provides new approaches o mange the business
activities efficiently and effectively with minimum manpower and reduces the cost of
doing business. The use of technology in the organization is very important as it helps in
maintain the data flow, track processes and maintains employee records (Breheny and
et. al., 2018). The term technology refers to the skills, techniques, methods and process
used in the business for production and involving scientific investigation. It is a branch of
scientific knowledge deal with engineering and applied science. With the use of
technology in the organization it brings growth, improves business communication,
production and helps in keeping the record related to employees, financial, and
inventory etc. It helps the governments, individuals in increasing their efficiency by
having a vast knowledge of information technology. The report is done on the case of
Arden University of united Kingdom which has done expansion of its business in
Germany. The discussed topic includes the big data, security and privacy,
telecommunication of cellular network.
Main body
Identify and discussing Big Data and its role of Arden University
Arden University was recognized in 1990 by resource development international.
It is a private profit teaching firm in the UK which provides distance learning with various
undergraduates and post graduates program. The term big data was used by John
Mashey in 1990. Big data refer to a field where data which are too complex or large are
analyzed systematically for extracting information and dealing with data sets. It involves
data processing application. It offers statistical power. The analysis of Big data involves
data capturing, data analysis, data search, sharing, storing, and transferring,

visualization, querying regarding data, updating, information, privacy, and data source.
The big data involves the data with their sizes of capacity in software for processing in
accepted time, and value. To extract the value and particular size of data set from big
data it applies the predictive, behavior and advance data analytics. It requires the
collection of enormous volume data. The companies’ get opportunities from big data in
creating new goods and services, by combining and analyzing industry data that have
sufficient information about the buyers suppliers, and consumer preferences. Big data is
connected with three basic elements: volume, variety, and velocity (Campeau 2019).
Volume- The term volume defines the size which is huge in shaping value out of
data. Volume is a characteristic which is measured when dealing with big data.
The university collects data from several of sources, involving social media and
information from sensor, business transactions, or machine-to-machine data.
Variety- It defines to assorted source including structured and unstructured data.
The data applications are analyzed in the form of emails, monitoring devices,
photos, videos, PDFs, audio, etc. The variety of unstructured data has issues for
mining and analyzing data, storage of data. In earlier times spreadsheets and
database are used (Cure 2019).
Velocity- It is related to generating speed of data. The big data of velocity
examines the speediness of data how it meets the demand and data potential by
processing and generating quickly. The data flows in various sources like
business processes, social media sites, sensors, application logs, networks and
Mobile devices, etc. The data flow is enormous and continuous.
Value- By analyzing the data it defines the profitability of the information in terms
of valuable. It is a measurement of the quality in big data.
Variability- It defines the change in characteristic of format, structure and
sources in big data. It is a combination of structure and unstructured data
integrating and transforming raw data from manifold sources.
Veracity- It defines the reliability by having the combination of data value and
data quality which is required to achieve value. The capturing of data quality is
great providing accurate analysis.
The big data involves the data with their sizes of capacity in software for processing in
accepted time, and value. To extract the value and particular size of data set from big
data it applies the predictive, behavior and advance data analytics. It requires the
collection of enormous volume data. The companies’ get opportunities from big data in
creating new goods and services, by combining and analyzing industry data that have
sufficient information about the buyers suppliers, and consumer preferences. Big data is
connected with three basic elements: volume, variety, and velocity (Campeau 2019).
Volume- The term volume defines the size which is huge in shaping value out of
data. Volume is a characteristic which is measured when dealing with big data.
The university collects data from several of sources, involving social media and
information from sensor, business transactions, or machine-to-machine data.
Variety- It defines to assorted source including structured and unstructured data.
The data applications are analyzed in the form of emails, monitoring devices,
photos, videos, PDFs, audio, etc. The variety of unstructured data has issues for
mining and analyzing data, storage of data. In earlier times spreadsheets and
database are used (Cure 2019).
Velocity- It is related to generating speed of data. The big data of velocity
examines the speediness of data how it meets the demand and data potential by
processing and generating quickly. The data flows in various sources like
business processes, social media sites, sensors, application logs, networks and
Mobile devices, etc. The data flow is enormous and continuous.
Value- By analyzing the data it defines the profitability of the information in terms
of valuable. It is a measurement of the quality in big data.
Variability- It defines the change in characteristic of format, structure and
sources in big data. It is a combination of structure and unstructured data
integrating and transforming raw data from manifold sources.
Veracity- It defines the reliability by having the combination of data value and
data quality which is required to achieve value. The capturing of data quality is
great providing accurate analysis.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Examples-1- The use of big data in Government increases the efficiency,
productivity and innovation by reducing the cost. It collaborates the working of
local to central by creating new innovative process for delivering better outcome.
The national security administration makes the use of big data by monitoring the
activities of internet in search of illegal activities (Holmwood 2018).
2. The use of big data in Healthcare provides personalized medicine and
prescriptive analytics, automated external and internal reporting of patient data.
The volume of data has increased by adopting mHealth, eHealth and wearable
technologies. It involves the electronic health record, sensor data, imaging data
etc.
Role of big data
The Big data has vast role in education department as It provides the choices
between the colleges, universities as they utilize the big data in various interesting way
which increase their profit margin and attendance of the school through students and
teachers. The big data helps the universities in finding g the new development in terms
of teaching, organizing students and college work, infrastructure. The big data collects a
lot of information which is stored at one place for reducing the time and cost. Predictive
analytics is used for retention of student by tracking their progress. It also identifies the
non-academic factors in the universities. In education the big data has a important role
as it incorporates the education experience for students betterment. It also improves the
learning style and benefits target enrollment. The use of big data in universities helps in
targeting student scholarships by identifying quality students who helps in contribution
for the betterment of the institutions. An institution uses big data for judging past
performance of a student no matter which school or college he/she was enrolled in. The
use of big data in university creates customized programs for the individual students as
all data is collected and stored. The right use of big data cuts the energy and save
operating cost and programs can be modified. The role of big data in human resource
department helps in informing and improving various areas related to training,
recruitment, development, performance. It helps the HR mangers to make smart
decisions for achieving their organizational goals. With the use of big data the HR
productivity and innovation by reducing the cost. It collaborates the working of
local to central by creating new innovative process for delivering better outcome.
The national security administration makes the use of big data by monitoring the
activities of internet in search of illegal activities (Holmwood 2018).
2. The use of big data in Healthcare provides personalized medicine and
prescriptive analytics, automated external and internal reporting of patient data.
The volume of data has increased by adopting mHealth, eHealth and wearable
technologies. It involves the electronic health record, sensor data, imaging data
etc.
Role of big data
The Big data has vast role in education department as It provides the choices
between the colleges, universities as they utilize the big data in various interesting way
which increase their profit margin and attendance of the school through students and
teachers. The big data helps the universities in finding g the new development in terms
of teaching, organizing students and college work, infrastructure. The big data collects a
lot of information which is stored at one place for reducing the time and cost. Predictive
analytics is used for retention of student by tracking their progress. It also identifies the
non-academic factors in the universities. In education the big data has a important role
as it incorporates the education experience for students betterment. It also improves the
learning style and benefits target enrollment. The use of big data in universities helps in
targeting student scholarships by identifying quality students who helps in contribution
for the betterment of the institutions. An institution uses big data for judging past
performance of a student no matter which school or college he/she was enrolled in. The
use of big data in university creates customized programs for the individual students as
all data is collected and stored. The right use of big data cuts the energy and save
operating cost and programs can be modified. The role of big data in human resource
department helps in informing and improving various areas related to training,
recruitment, development, performance. It helps the HR mangers to make smart
decisions for achieving their organizational goals. With the use of big data the HR

managers have the ability to track and monitor the recruitment efficiency of the ideal
candidates. It makes the hiring process easy by narrowing down large group of
candidates. The big data also provides the chance of improving loyalty and reducing
turnover. (Jaiswal and et. al., 2017).
Benefits of big data
The Arden University adopted management program of big data analytics for
educators, decision makers and shareholder for identifying the problem and
opportunities for causing the positive change. The big data provided various benefits –
Cost saving – in education resources should be allocated properly for keeping the
efficiency of data. The cloud- based system reduces the potential of data storage
cost and remove pressure from IT department. the use of digital information
computerizes a lot of monotonous work quickly and easily which saves the funds in
the long run. The big data helps in recruitment that maximizes the ROI on each
student by saving cost (Jarvis 2017).
Quick in decision making- The universities and college information is stored at one
centralized location, which saves time by the use of big data as it helps in finding
one specific report or information about a particular student. It helps in making quick
decision which improves the stability of enrollments.
Improvement in student performance- the big data analytics helps the students to
stay on course of having better grades. It tracks and compares academic results and
test performance with the earlier performance. It also provides the guidance through
teacher notes and social media which gives an insight to student behavior for
increasing performance (Kajornbun and et. al., 2019).
IT security and data privacy
IT security defines a cyber security set which is a strategy used for stopping the
unauthorized access of organizational assets such as computers, networks, and data.
The computer system and network are protected from the damage of hardware,
software and electronic data. It also protects from disclosure of information. The
reliability and privacy of susceptible information is maintained by blocking the
candidates. It makes the hiring process easy by narrowing down large group of
candidates. The big data also provides the chance of improving loyalty and reducing
turnover. (Jaiswal and et. al., 2017).
Benefits of big data
The Arden University adopted management program of big data analytics for
educators, decision makers and shareholder for identifying the problem and
opportunities for causing the positive change. The big data provided various benefits –
Cost saving – in education resources should be allocated properly for keeping the
efficiency of data. The cloud- based system reduces the potential of data storage
cost and remove pressure from IT department. the use of digital information
computerizes a lot of monotonous work quickly and easily which saves the funds in
the long run. The big data helps in recruitment that maximizes the ROI on each
student by saving cost (Jarvis 2017).
Quick in decision making- The universities and college information is stored at one
centralized location, which saves time by the use of big data as it helps in finding
one specific report or information about a particular student. It helps in making quick
decision which improves the stability of enrollments.
Improvement in student performance- the big data analytics helps the students to
stay on course of having better grades. It tracks and compares academic results and
test performance with the earlier performance. It also provides the guidance through
teacher notes and social media which gives an insight to student behavior for
increasing performance (Kajornbun and et. al., 2019).
IT security and data privacy
IT security defines a cyber security set which is a strategy used for stopping the
unauthorized access of organizational assets such as computers, networks, and data.
The computer system and network are protected from the damage of hardware,
software and electronic data. It also protects from disclosure of information. The
reliability and privacy of susceptible information is maintained by blocking the

sophisticated hackers. The IT security has a threat from malware which includes
ransom ware, spyware and viruses. The field of IT security has increased in many ways
with the introduction of internet providing wireless network of Bluetooth and WI-FI. The
IT security has gained the growth in smart devices of smart phone, television etc.
Data privacy is the practice which determines the sharing of data by customers is
for some intention. Data privacy is a division of data security related with the proper
managing of data including notice, consent, and regulatory obligations. The data privacy
is also known as information privacy where an individual has a right to control its
personal information of knowing how it’s being used and utilized. It is a important part
for consumer protection. Data protection is a division of privacy which keeps the used
data private. The laws of US data and information privacy are regulated at federal level.
The various types of information technology security include network security, internet
security, end point security, and application and cloud security. Data privacy builds the
trust and accountability with customers, investors and partners by managing and
keeping their information in privacy. The healthy implementation of data privacy involve
principles, policies and procedures governing for accessing of data for reduceing
security incidents that result in privacy breaches (McSweeney and et. al., 2019).
Businesses should use different IT security and data privacy measures to keep
their business data, cash flow and safe their customers online. The measure of IT
security and data privacy that should be implemented in organization includes-
(Narimani and et. al., 2020).
Use of strong password- The Strong passwords is critical for online security.
The combination of capital and lower-case letters, numbers and symbols is used
for creating password between eight and 12 characters long. It avoids the use of
personal data which should be changed regularly. The password provides the
benefit of two factor authentication and never used for multiple accounts again. A
password policy is created for the organization to help staff by using security in
best practices (Pedler and et. al., 2019).
ransom ware, spyware and viruses. The field of IT security has increased in many ways
with the introduction of internet providing wireless network of Bluetooth and WI-FI. The
IT security has gained the growth in smart devices of smart phone, television etc.
Data privacy is the practice which determines the sharing of data by customers is
for some intention. Data privacy is a division of data security related with the proper
managing of data including notice, consent, and regulatory obligations. The data privacy
is also known as information privacy where an individual has a right to control its
personal information of knowing how it’s being used and utilized. It is a important part
for consumer protection. Data protection is a division of privacy which keeps the used
data private. The laws of US data and information privacy are regulated at federal level.
The various types of information technology security include network security, internet
security, end point security, and application and cloud security. Data privacy builds the
trust and accountability with customers, investors and partners by managing and
keeping their information in privacy. The healthy implementation of data privacy involve
principles, policies and procedures governing for accessing of data for reduceing
security incidents that result in privacy breaches (McSweeney and et. al., 2019).
Businesses should use different IT security and data privacy measures to keep
their business data, cash flow and safe their customers online. The measure of IT
security and data privacy that should be implemented in organization includes-
(Narimani and et. al., 2020).
Use of strong password- The Strong passwords is critical for online security.
The combination of capital and lower-case letters, numbers and symbols is used
for creating password between eight and 12 characters long. It avoids the use of
personal data which should be changed regularly. The password provides the
benefit of two factor authentication and never used for multiple accounts again. A
password policy is created for the organization to help staff by using security in
best practices (Pedler and et. al., 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Firewall- Firewalls are effective gatekeepers between the computer and internet
which helps in preventing the increase of cyber threats such as viruses and
malware. The firewall devices should be properly set up in the organization to
ensure they have the updated software/firmware installed by keep checking
regularly.
Install Reliable Antivirus Software- A good and reliable antivirus program, anti-
malware software is crucial for cyber security system which helps in defending
unwanted attacks on the security network. It helps in detecting and removing
virus and malware, adware and spyware from the computer network and
provides scanning, harmful downloads and emails are filter.
VPN- It defines to virtual private network a series of virtual connections route
over the internet which encrypts data. It involves the use of internet resources
such as web servers. The end points for the VPN connections are PCs,
Smartphone’s, tablets etc. the data is transmitted to client machine through the
use of VPN network. It protects the data of the organization and make contacts
easy.
Key provisions of GDPR
GDPR known as general data protection regulation which was established on
25th may in UK and EU in 2018. It replaced the rules of data protection act with the
purpose of providing great control to individual on their data where earlier personal
information was collected by the businesses. It is a regulation for protecting the data
and privacy of European member in connection with business within the state of EU.
The organizations are abided for following the new rules and regulation of GDPR. For
protecting consumer rights new standards has been set by GDPR concerning their
information but organization face challenge of putting system and process in place for
maintaining compliance (Phung and et. al., 2019).
European Parliament adopted GDPR in 2016. Outdated data protection directive
was replaced by GDPR in 1995. GDPR regulates exportation of personal data outside
the European Union. It provides individual control over the personal data for simplifying
the regulatory environment of international business. The enterprises are impacted with
which helps in preventing the increase of cyber threats such as viruses and
malware. The firewall devices should be properly set up in the organization to
ensure they have the updated software/firmware installed by keep checking
regularly.
Install Reliable Antivirus Software- A good and reliable antivirus program, anti-
malware software is crucial for cyber security system which helps in defending
unwanted attacks on the security network. It helps in detecting and removing
virus and malware, adware and spyware from the computer network and
provides scanning, harmful downloads and emails are filter.
VPN- It defines to virtual private network a series of virtual connections route
over the internet which encrypts data. It involves the use of internet resources
such as web servers. The end points for the VPN connections are PCs,
Smartphone’s, tablets etc. the data is transmitted to client machine through the
use of VPN network. It protects the data of the organization and make contacts
easy.
Key provisions of GDPR
GDPR known as general data protection regulation which was established on
25th may in UK and EU in 2018. It replaced the rules of data protection act with the
purpose of providing great control to individual on their data where earlier personal
information was collected by the businesses. It is a regulation for protecting the data
and privacy of European member in connection with business within the state of EU.
The organizations are abided for following the new rules and regulation of GDPR. For
protecting consumer rights new standards has been set by GDPR concerning their
information but organization face challenge of putting system and process in place for
maintaining compliance (Phung and et. al., 2019).
European Parliament adopted GDPR in 2016. Outdated data protection directive
was replaced by GDPR in 1995. GDPR regulates exportation of personal data outside
the European Union. It provides individual control over the personal data for simplifying
the regulatory environment of international business. The enterprises are impacted with

GDPR where enterprise refers to any natural or legal person irrespective of its legal
form engaged in an economic activity, including partnership or associations. The new
provisions also involve the protection of data of children’s. it also introduced the
guidelines for data breaches which results in loss, alteration and access of personal
information.
Provisions are-
Data protection officer- When personal data is processed in organization a
DPO is appointed which is responsible for providing advice to the company that
how to comply with EU GDPR requirements. The DPO is appointed by the
several entities such as public authorities, large scale businesses who are
engaged in systematic monitoring of individuals regularly, large scale business
involved in processing of personal data of special category or related to criminal
convictions/ offences. The DPO can be organization person or can be hired from
outside who have expert knowledge of data protection law and practices.
Training and awareness- The Company is responsible to provide training and
awareness to employees regarding their responsibilities and how to protect
personal data and identifying breaches. It also provides the knowledge regarding
the general data protection regulation act (Rai 2018).
Data processor- It is an organization there is a data controller which process the
personal data on behalf of another organization. It does not involve statutory
obligation and liability. To protect the data technical and organization security is
implemented and keeping a register data for activity process.
Data transfer- The controller has accountability of personal data for ensuring
that personal information is confined and GDPR requirements if processes by
third party. When the data moves outside the company or to third party the
controller is under the obligation in protecting of data.
Right to Compensation for individuals- Due to infringement a individual suffer
the damages which provides a right to GDPR for obtaining compensation
regarding the damages suffered from the organization. An individual in court can
form engaged in an economic activity, including partnership or associations. The new
provisions also involve the protection of data of children’s. it also introduced the
guidelines for data breaches which results in loss, alteration and access of personal
information.
Provisions are-
Data protection officer- When personal data is processed in organization a
DPO is appointed which is responsible for providing advice to the company that
how to comply with EU GDPR requirements. The DPO is appointed by the
several entities such as public authorities, large scale businesses who are
engaged in systematic monitoring of individuals regularly, large scale business
involved in processing of personal data of special category or related to criminal
convictions/ offences. The DPO can be organization person or can be hired from
outside who have expert knowledge of data protection law and practices.
Training and awareness- The Company is responsible to provide training and
awareness to employees regarding their responsibilities and how to protect
personal data and identifying breaches. It also provides the knowledge regarding
the general data protection regulation act (Rai 2018).
Data processor- It is an organization there is a data controller which process the
personal data on behalf of another organization. It does not involve statutory
obligation and liability. To protect the data technical and organization security is
implemented and keeping a register data for activity process.
Data transfer- The controller has accountability of personal data for ensuring
that personal information is confined and GDPR requirements if processes by
third party. When the data moves outside the company or to third party the
controller is under the obligation in protecting of data.
Right to Compensation for individuals- Due to infringement a individual suffer
the damages which provides a right to GDPR for obtaining compensation
regarding the damages suffered from the organization. An individual in court can

make an application appealing the decisions and acts of DPA (Selden and et. al.,
2018).
Cellular network, components and benefits
Nippon Telegraph and Telephone introduced the first commercial cellular
network, in 1979 in Japan. A cellular network is also known as mobile network which
refers to communication network having a wireless link. It is spread over the land
through cells served by fixed-location transceiver called as cell site or base station. In a
cellular network, each cell has a different set of frequencies from neighboring cells for
avoiding interference and provides guaranteed bandwidth within each cell. The link is
connected to end nodes in form of wireless.
The subscribers of cellular network have the advance feature on alternative
solution which increases the capacity with small battery power usage covering large
geographic area by reducing interference from other signals. The mobile network is
connected to towers having a packet of signal involving data, text messaging and voice
which brings signals in mobile devices such as phones or laptops, tablets. The cellular
network system provides equipped details of channels for signals in the cellular devices.
The channels are strong dedicated control channel it is used where digital data is
transform in to cellular mobile phone through base station. Strong paging channel it
tracks the mobile phone through MSC when call is routed. A mobile network is
complexes web of connected various cell phones which are made of cells having area
of land in hexagonal form (Stone and et. al., 2021).
Components
The components of cellular network are –
Public switched telephone network (PSTN)- The PSTN is composition of local
networks, area networks, and the long-haul network that are inter connected with
each other providing communication on telephones and other devices worldwide
basis. it is a collection of circuit- switched network comprises of telephone
lines, fiber optic cables, microwave transmission links, cellular networks, and
2018).
Cellular network, components and benefits
Nippon Telegraph and Telephone introduced the first commercial cellular
network, in 1979 in Japan. A cellular network is also known as mobile network which
refers to communication network having a wireless link. It is spread over the land
through cells served by fixed-location transceiver called as cell site or base station. In a
cellular network, each cell has a different set of frequencies from neighboring cells for
avoiding interference and provides guaranteed bandwidth within each cell. The link is
connected to end nodes in form of wireless.
The subscribers of cellular network have the advance feature on alternative
solution which increases the capacity with small battery power usage covering large
geographic area by reducing interference from other signals. The mobile network is
connected to towers having a packet of signal involving data, text messaging and voice
which brings signals in mobile devices such as phones or laptops, tablets. The cellular
network system provides equipped details of channels for signals in the cellular devices.
The channels are strong dedicated control channel it is used where digital data is
transform in to cellular mobile phone through base station. Strong paging channel it
tracks the mobile phone through MSC when call is routed. A mobile network is
complexes web of connected various cell phones which are made of cells having area
of land in hexagonal form (Stone and et. al., 2021).
Components
The components of cellular network are –
Public switched telephone network (PSTN)- The PSTN is composition of local
networks, area networks, and the long-haul network that are inter connected with
each other providing communication on telephones and other devices worldwide
basis. it is a collection of circuit- switched network comprises of telephone
lines, fiber optic cables, microwave transmission links, cellular networks, and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

communications satellites interconnected by switching centers allow telephones
for communication with each other.
Mobile telephone switching office (MTSO) – For mobile switching it is a central
office for transferring call from cell sites to PSTN involving mobile switching
center, field monitoring and relay stations. The system operation is controlled by
MSC in analog cellular network such as calls, track of bills and local subscribers.
The local and long distance landline telephone are interconnected through
mobile telephone switching office for compiling billing information and data.
BSC/RNC are the subordinate responsible for assigning and reassigning
frequencies to each call, controlling handoffs of lead mobile phone leaving one
cell (formally known as BTS)'s coverage area, that is switched automatically in
a channel to the next cell. It provides the interface and connectivity to PSTN.
The cell site- It defines the physical location of radio equipment having coverage
within a cell. In cell site power sources, interface equipment, transmitter and
antenna system are the components of hardware which are located. It transmits
the signals of cell phone in mobile back to receiver which is known as antenna
equipment.
Mobile subscriber units (MSU) – It comprise of control unit and transceiver for
transmitting and receiving radio transmission from a cell site. The MSU types are
mobile telephone, portable, and transportable. The MSU network uses wireless
and wired network providing access to the internet and university resources
available on campus as well as many common outdoor areas (Valença and et.
al., 2020).
Principles of cellular network
The cell site communicates with many mobiles by using one channel per mobile.
Through electronically different cell frequency is switched to one cell frequency
without having any disturbance.
The cellular network has a large capacity of frequency is used for numerous links
in different cells rather than a particular large transmitter.
for communication with each other.
Mobile telephone switching office (MTSO) – For mobile switching it is a central
office for transferring call from cell sites to PSTN involving mobile switching
center, field monitoring and relay stations. The system operation is controlled by
MSC in analog cellular network such as calls, track of bills and local subscribers.
The local and long distance landline telephone are interconnected through
mobile telephone switching office for compiling billing information and data.
BSC/RNC are the subordinate responsible for assigning and reassigning
frequencies to each call, controlling handoffs of lead mobile phone leaving one
cell (formally known as BTS)'s coverage area, that is switched automatically in
a channel to the next cell. It provides the interface and connectivity to PSTN.
The cell site- It defines the physical location of radio equipment having coverage
within a cell. In cell site power sources, interface equipment, transmitter and
antenna system are the components of hardware which are located. It transmits
the signals of cell phone in mobile back to receiver which is known as antenna
equipment.
Mobile subscriber units (MSU) – It comprise of control unit and transceiver for
transmitting and receiving radio transmission from a cell site. The MSU types are
mobile telephone, portable, and transportable. The MSU network uses wireless
and wired network providing access to the internet and university resources
available on campus as well as many common outdoor areas (Valença and et.
al., 2020).
Principles of cellular network
The cell site communicates with many mobiles by using one channel per mobile.
Through electronically different cell frequency is switched to one cell frequency
without having any disturbance.
The cellular network has a large capacity of frequency is used for numerous links
in different cells rather than a particular large transmitter.

The towers of cell are nearer in cellular network which require less power with a
single transmitter or satellite in mobile devices.
The cellular network is urbanized for mobile radio telephone using low power.
Benefits
It provides in roaming voice and data service.
It connects fixed and wireless telephone user.
The cellular network is easy in marinating and upgrades the equipments.
With the cellular network the mobile and fixed subscriber have an immediate
connection as the mobile is switched on.
It provides a higher capacity.
The cellular network consumes less power.
It helps in reducing the interference from other signals.
The cellular network is spread to large coverage area
The Payroll department of Weaning Entertainment Ltd has spreadsheet providing
information regarding the mean, median, maximum and minimum value of gross salary,
net salary and taxes that has to be calculated
single transmitter or satellite in mobile devices.
The cellular network is urbanized for mobile radio telephone using low power.
Benefits
It provides in roaming voice and data service.
It connects fixed and wireless telephone user.
The cellular network is easy in marinating and upgrades the equipments.
With the cellular network the mobile and fixed subscriber have an immediate
connection as the mobile is switched on.
It provides a higher capacity.
The cellular network consumes less power.
It helps in reducing the interference from other signals.
The cellular network is spread to large coverage area
The Payroll department of Weaning Entertainment Ltd has spreadsheet providing
information regarding the mean, median, maximum and minimum value of gross salary,
net salary and taxes that has to be calculated
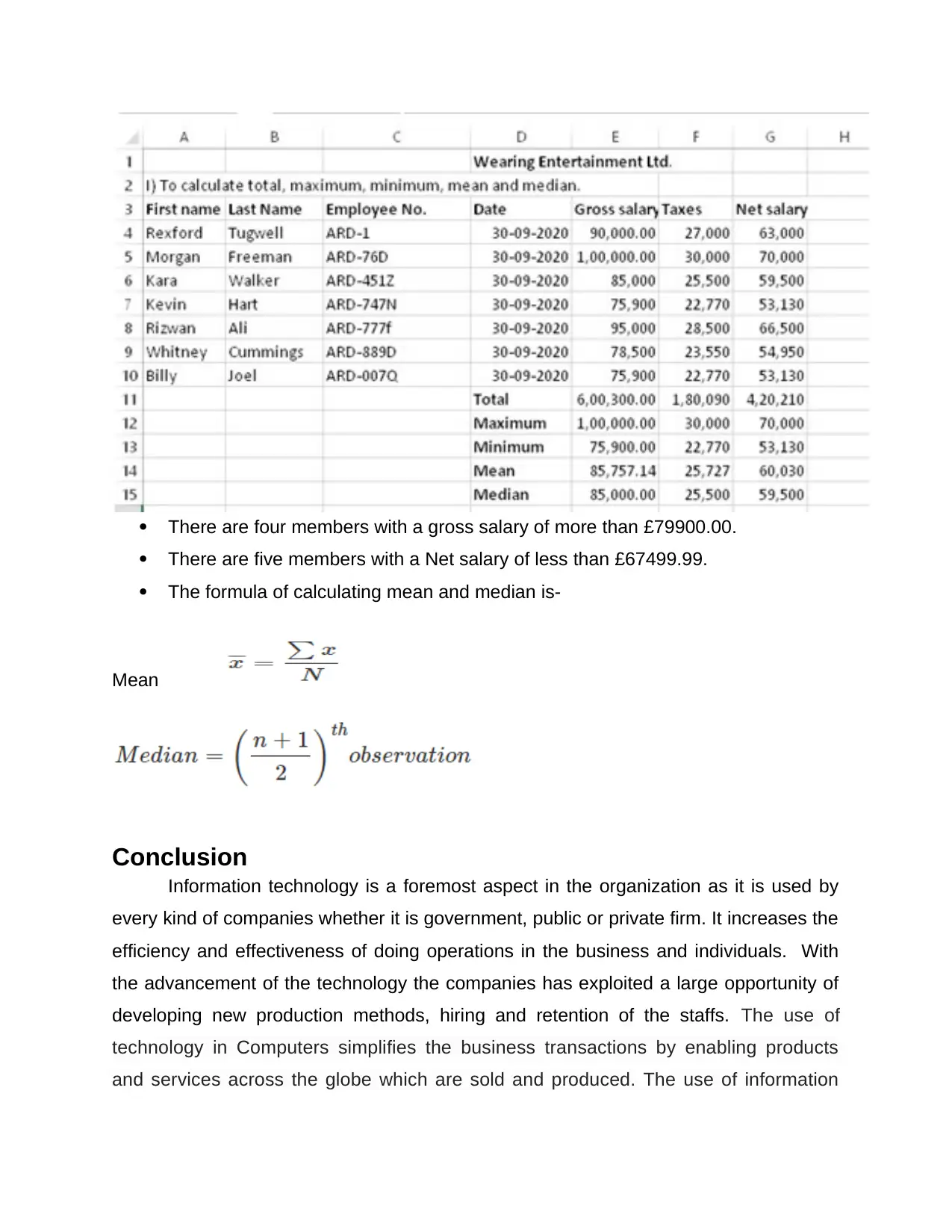
There are four members with a gross salary of more than £79900.00.
There are five members with a Net salary of less than £67499.99.
The formula of calculating mean and median is-
Mean
Conclusion
Information technology is a foremost aspect in the organization as it is used by
every kind of companies whether it is government, public or private firm. It increases the
efficiency and effectiveness of doing operations in the business and individuals. With
the advancement of the technology the companies has exploited a large opportunity of
developing new production methods, hiring and retention of the staffs. The use of
technology in Computers simplifies the business transactions by enabling products
and services across the globe which are sold and produced. The use of information
There are five members with a Net salary of less than £67499.99.
The formula of calculating mean and median is-
Mean
Conclusion
Information technology is a foremost aspect in the organization as it is used by
every kind of companies whether it is government, public or private firm. It increases the
efficiency and effectiveness of doing operations in the business and individuals. With
the advancement of the technology the companies has exploited a large opportunity of
developing new production methods, hiring and retention of the staffs. The use of
technology in Computers simplifies the business transactions by enabling products
and services across the globe which are sold and produced. The use of information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

technology helps in storing more information than thousands of file folders and
cabinets. In IT sector the use of big data analytics stores the huge volume of data of
banking, manufacturing, colleges and universities and provides the speedy of getting
information from one place. It also protects from the hackers by providing high storage
capacity. The use of cellular network helps in connectivity and exchanging information
from anywhere through communication over mobile phones.
cabinets. In IT sector the use of big data analytics stores the huge volume of data of
banking, manufacturing, colleges and universities and provides the speedy of getting
information from one place. It also protects from the hackers by providing high storage
capacity. The use of cellular network helps in connectivity and exchanging information
from anywhere through communication over mobile phones.

References
Books and Journals
Breheny and et. al., 2018. The development of high technology industries: an
international survey (Vol. 9). Routledge.
Campeau, H., 2019. Institutional myths and generational boundaries: cultural inertia in
the police organisation. Policing and society, 29(1), pp.69-84.
Cure, K., 2019. A British Trade Union View of Organisation and JIT in the UK. In Just-in-
Time Systems and Euro-Japanese Industrial Collaboration (pp. 57-62).
Routledge.
Das, R., 2020. Acculturation in Organisation: A Critical Review. Reema Das, Dr
Chandranshu Sinha (March, 2020)," Acculturation In Organisation: A Critical
Review" Journal of Scientific & Technology Research (IJSTR) Volume.
Holmwood, L., 2018. Blame. Language. Sharing: Three Tips for Learning from Incidents
in Your Organisation.
Jaiswal and et. al., 2017. Study of Business and Organisation Turnaround.
Jarvis, T., 2017. Teaching Design and Technology in the Primary School (1993).
Routledge.
Kajornbun and et. al., 2019. Local administration organisation capacity development for
tourism promotion in the Andaman coastal provinces, Thailand. International
Journal of Tourism Policy, 9(4), pp.300-319.
McSweeney and et. al., 2019. Maintaining and disrupting global-North
hegemony/global-South dependence in a local African sport for development
organisation: The role of institutional work. International Journal of Sport Policy
and Politics, 11(3), pp.521-537.
Narimani and et. al., 2020. Using Government Procurement Policy Tool in Iran: Pre-
Commercial Public Procurement for Innovation or Government Procurement for
Supporting Innovation?(A Multi-case Study at the Center for National Macro
Technology Projects). Journal of Technology Development Management, 8(1),
pp.127-151.
Pedler and et. al., 2019. Regenerating the learning organisation: towards an alternative
paradigm. The Learning Organization.
Phung and et. al., 2019, September. Exploring Critical Success Factors for Managing
Sustainability in Construction Projects. In 14th Organisation, Technology &
Management in Construction Conference (pp. 374-388). Croatian Association for
Construction Management.
Books and Journals
Breheny and et. al., 2018. The development of high technology industries: an
international survey (Vol. 9). Routledge.
Campeau, H., 2019. Institutional myths and generational boundaries: cultural inertia in
the police organisation. Policing and society, 29(1), pp.69-84.
Cure, K., 2019. A British Trade Union View of Organisation and JIT in the UK. In Just-in-
Time Systems and Euro-Japanese Industrial Collaboration (pp. 57-62).
Routledge.
Das, R., 2020. Acculturation in Organisation: A Critical Review. Reema Das, Dr
Chandranshu Sinha (March, 2020)," Acculturation In Organisation: A Critical
Review" Journal of Scientific & Technology Research (IJSTR) Volume.
Holmwood, L., 2018. Blame. Language. Sharing: Three Tips for Learning from Incidents
in Your Organisation.
Jaiswal and et. al., 2017. Study of Business and Organisation Turnaround.
Jarvis, T., 2017. Teaching Design and Technology in the Primary School (1993).
Routledge.
Kajornbun and et. al., 2019. Local administration organisation capacity development for
tourism promotion in the Andaman coastal provinces, Thailand. International
Journal of Tourism Policy, 9(4), pp.300-319.
McSweeney and et. al., 2019. Maintaining and disrupting global-North
hegemony/global-South dependence in a local African sport for development
organisation: The role of institutional work. International Journal of Sport Policy
and Politics, 11(3), pp.521-537.
Narimani and et. al., 2020. Using Government Procurement Policy Tool in Iran: Pre-
Commercial Public Procurement for Innovation or Government Procurement for
Supporting Innovation?(A Multi-case Study at the Center for National Macro
Technology Projects). Journal of Technology Development Management, 8(1),
pp.127-151.
Pedler and et. al., 2019. Regenerating the learning organisation: towards an alternative
paradigm. The Learning Organization.
Phung and et. al., 2019, September. Exploring Critical Success Factors for Managing
Sustainability in Construction Projects. In 14th Organisation, Technology &
Management in Construction Conference (pp. 374-388). Croatian Association for
Construction Management.

Rai, A., 2018. Job crafting intervention: fostering individual job redesign for sustainable
organisation. Industrial and Commercial Training.
Selden and et. al., 2018. Lithic morphological organisation: Gahagan bifaces from the
Southern Caddo Area. Digital Applications in Archaeology and Cultural
Heritage, 10, p.e00080.
Stone and et. al., 2021. Filling the gaps: The potential and limitations of emergent, ICT-
enabled organisation in disaster–a case study of the Cajun Army. Environmental
Hazards, 20(1), pp.63-77.
Valença and et. al., 2020, August. A Systematic Mapping Study on the Organisation of
Corporate Hackathons. In 2020 46th Euromicro Conference on Software
Engineering and Advanced Applications (SEAA) (pp. 421-428). IEEE.
.
organisation. Industrial and Commercial Training.
Selden and et. al., 2018. Lithic morphological organisation: Gahagan bifaces from the
Southern Caddo Area. Digital Applications in Archaeology and Cultural
Heritage, 10, p.e00080.
Stone and et. al., 2021. Filling the gaps: The potential and limitations of emergent, ICT-
enabled organisation in disaster–a case study of the Cajun Army. Environmental
Hazards, 20(1), pp.63-77.
Valença and et. al., 2020, August. A Systematic Mapping Study on the Organisation of
Corporate Hackathons. In 2020 46th Euromicro Conference on Software
Engineering and Advanced Applications (SEAA) (pp. 421-428). IEEE.
.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





