Comprehensive Report: AAA Framework in Network Security and Management
VerifiedAdded on 2023/01/06
|7
|1255
|30
Report
AI Summary
This report provides a comprehensive overview of the AAA framework, a crucial element in network security and access control. The introduction highlights the framework's role in managing computer resources, enforcing policies, and providing information for billing and auditing. The main body delves into the three key components: Authentication, which verifies user identity; Authorization, which defines user permissions; and Accounting, which tracks resource usage. The report also describes a network model incorporating switches, cloud computing, routers, a Linux system, TACACS+ server, GNS3, and RADIUS. The configuration of TACACS+ and GNS3 for authentication using the AAA framework is discussed, emphasizing the importance of up-to-date servers. The report concludes with references to relevant books and journals, providing a solid foundation for understanding the practical application of the AAA framework in securing and managing network resources.

The AAA Framework
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
AAA Framework.........................................................................................................................1
Network.......................................................................................................................................2
REFERENCE ..................................................................................................................................1
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
AAA Framework.........................................................................................................................1
Network.......................................................................................................................................2
REFERENCE ..................................................................................................................................1

INTRODUCTION
AAA framework is useful in controlling and accessing the prominent computer resources
in terms of enforcing policies, effective use of audit and also tens to offer prominent information
which is necessary in terms of billing for the service. This process tends to work for the effective
concert which is significant for the prominent networking, management and security. It is the
term which is used for the intelligently controlling and accessing the computer resources, and
also tends to combine the process for the prominent management. It is undertaken as the simple
way in terms of understanding the effective surrounding for accessing the ability of employees
for an organisation. It tends to depict the internet engineering task force and for this, the three
A'S represent for the Authenticate, authorise and accounting as these tends to understand and
craft effective policies for the framework which is useful in marking system more effective and
secure (Authentication, Authorization, Accounting and Identity Management, 2020).
MAIN BODY
AAA Framework
The prominent factors are mentioned as underneath: Authentication: This factor refers to the prominent security of process in terms of
describing the effective network and application by identifying the user in terms of
making sure the claim. For this, user need to enter effective username and password in
terms of granting the access that has prominent and unique set of identification
information. In this, user tends to make sure the proper authorisation for the access of
system considering the theft of data and information and security threats in terms of
becoming more advanced. As it tends to authenticate to prevent from identifying the theft
and also make sure the networking resources to get protected from various authentication
ways (Wong and et. al., 2017). Authorisation: It tends to under the effective process for enforcing the prominent policies
to identify the qualities for resources, activities and effective services that are permitted
by user to use accordingly. This factor tends to occur without the context of authenticate
as for this, user need to assign the authorisation level in terms of defining the access to
the network which is associated with effective resources. For instance, for the more
secure application of passwords, need to be stored salted with no prominent procedure for
1
AAA framework is useful in controlling and accessing the prominent computer resources
in terms of enforcing policies, effective use of audit and also tens to offer prominent information
which is necessary in terms of billing for the service. This process tends to work for the effective
concert which is significant for the prominent networking, management and security. It is the
term which is used for the intelligently controlling and accessing the computer resources, and
also tends to combine the process for the prominent management. It is undertaken as the simple
way in terms of understanding the effective surrounding for accessing the ability of employees
for an organisation. It tends to depict the internet engineering task force and for this, the three
A'S represent for the Authenticate, authorise and accounting as these tends to understand and
craft effective policies for the framework which is useful in marking system more effective and
secure (Authentication, Authorization, Accounting and Identity Management, 2020).
MAIN BODY
AAA Framework
The prominent factors are mentioned as underneath: Authentication: This factor refers to the prominent security of process in terms of
describing the effective network and application by identifying the user in terms of
making sure the claim. For this, user need to enter effective username and password in
terms of granting the access that has prominent and unique set of identification
information. In this, user tends to make sure the proper authorisation for the access of
system considering the theft of data and information and security threats in terms of
becoming more advanced. As it tends to authenticate to prevent from identifying the theft
and also make sure the networking resources to get protected from various authentication
ways (Wong and et. al., 2017). Authorisation: It tends to under the effective process for enforcing the prominent policies
to identify the qualities for resources, activities and effective services that are permitted
by user to use accordingly. This factor tends to occur without the context of authenticate
as for this, user need to assign the authorisation level in terms of defining the access to
the network which is associated with effective resources. For instance, for the more
secure application of passwords, need to be stored salted with no prominent procedure for
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

decrypting, it also tends to secure the prominent application to enable password that
should be changed but never meant to be retrieved (Dhammawat and et. al., 2020).
Accounting: This method tends to make sure the prominent resources considering user
and its consumption power at the time of accessing for network and effective application
including, logging session, statistics and other user information. Effective use of
information is useful for the prominent authorisation for the controlling, billing, resource
usage, trend identification and so on. Accounting tends to make sure the effective audit
that leads to enable that administer need to login and view prominent actions that are
performed by the user and also tends to note significant time period. Therefore, proper
accounting tends to enable network and effective system to review for attempting the
access.
2
should be changed but never meant to be retrieved (Dhammawat and et. al., 2020).
Accounting: This method tends to make sure the prominent resources considering user
and its consumption power at the time of accessing for network and effective application
including, logging session, statistics and other user information. Effective use of
information is useful for the prominent authorisation for the controlling, billing, resource
usage, trend identification and so on. Accounting tends to make sure the effective audit
that leads to enable that administer need to login and view prominent actions that are
performed by the user and also tends to note significant time period. Therefore, proper
accounting tends to enable network and effective system to review for attempting the
access.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
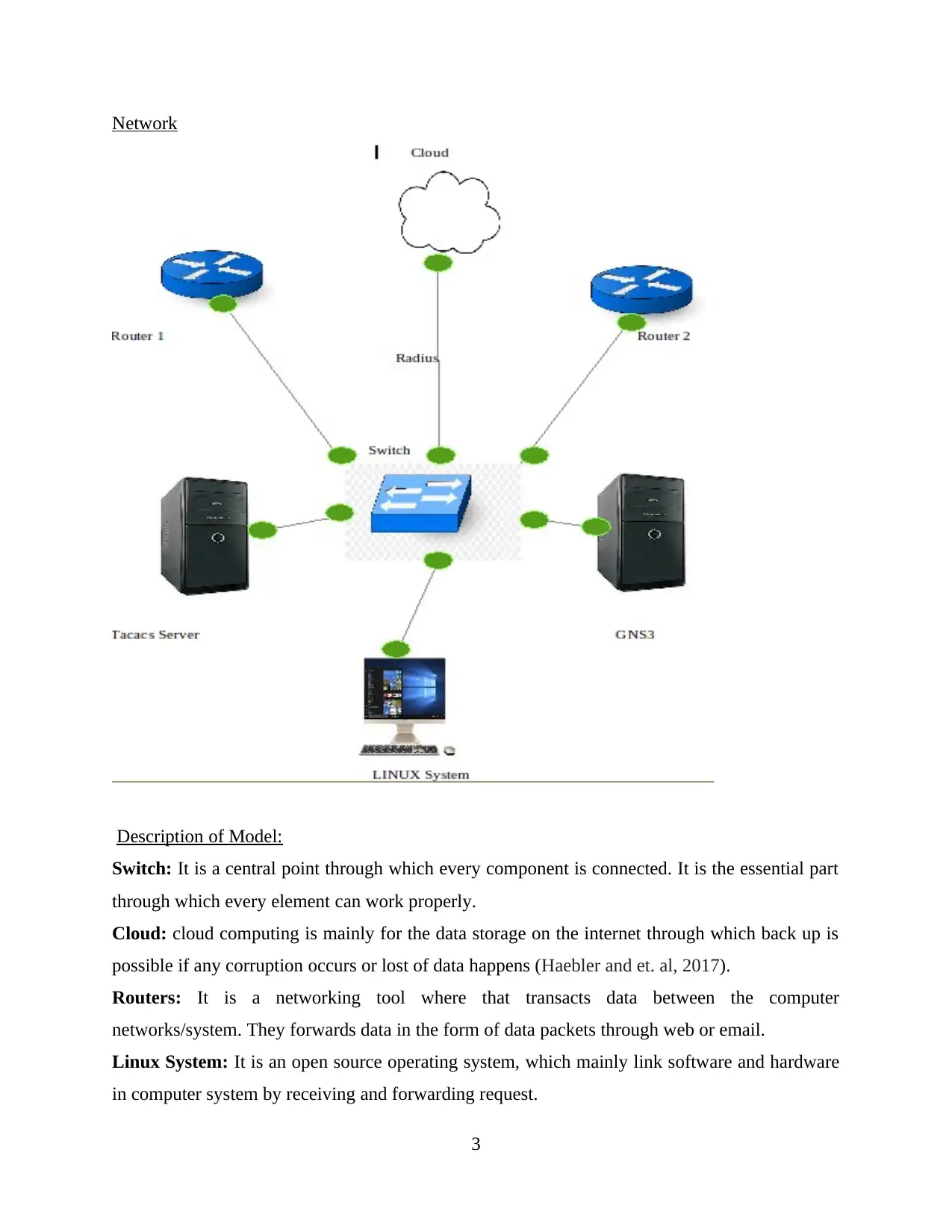
Network
Description of Model:
Switch: It is a central point through which every component is connected. It is the essential part
through which every element can work properly.
Cloud: cloud computing is mainly for the data storage on the internet through which back up is
possible if any corruption occurs or lost of data happens (Haebler and et. al, 2017).
Routers: It is a networking tool where that transacts data between the computer
networks/system. They forwards data in the form of data packets through web or email.
Linux System: It is an open source operating system, which mainly link software and hardware
in computer system by receiving and forwarding request.
3
Description of Model:
Switch: It is a central point through which every component is connected. It is the essential part
through which every element can work properly.
Cloud: cloud computing is mainly for the data storage on the internet through which back up is
possible if any corruption occurs or lost of data happens (Haebler and et. al, 2017).
Routers: It is a networking tool where that transacts data between the computer
networks/system. They forwards data in the form of data packets through web or email.
Linux System: It is an open source operating system, which mainly link software and hardware
in computer system by receiving and forwarding request.
3

Tacacs+ server: It stands for Terminal Access Controller Access Control Service Plus. It is a
security software which restricts the unauthorised access points to the server or router networks.
These are mainly maintained in a form of database usually UNIX or windows platforms. Access
is only possible when updated features are configured on the network. It generally serves
separate authentication, authorization and accounting facilities. It also permits the single user so
as to serve the facilities independently to each and every user. Each advantage of this server is
interconnected within them so authorised access is easy for the authenticated users. It's main aim
to serve multiple networks from single management services which is a very good technical
advancement in the field of information technology (Paramitha, Rochim and Fauzi, 2020).
GNS3: It stands for Graphical Network Simulator-3. It is referred to the fusion of real and virtual
devices used to integrate complicated networks.
Radius: It stands for remote access dial in user service. This is an open protocol written in heavy
code format and are available in the marketplace. It is mainly for the security of client server
system to protect from unauthorised and unauthenticated user. Some radius can run on all the
platforms and some are limited to specified platforms only.
This is the basic configuring Tacacs+ and GNS3 authentication using AAA Framework.
The purpose of designing this model is to use log in ID and password from Tacacs+
server and GNS3 for login authentication.
Before configuration these servers, it is necessary to check whether they are up to date or
not.
In this model, end device is Linux OS and Tacacs+ and GNS3 servers are using AAA
server (Thakare and et. al, 2017).
It can be downloaded on GNS3 marketplace but it is important to check that they are
connected to the internet or not.
4
security software which restricts the unauthorised access points to the server or router networks.
These are mainly maintained in a form of database usually UNIX or windows platforms. Access
is only possible when updated features are configured on the network. It generally serves
separate authentication, authorization and accounting facilities. It also permits the single user so
as to serve the facilities independently to each and every user. Each advantage of this server is
interconnected within them so authorised access is easy for the authenticated users. It's main aim
to serve multiple networks from single management services which is a very good technical
advancement in the field of information technology (Paramitha, Rochim and Fauzi, 2020).
GNS3: It stands for Graphical Network Simulator-3. It is referred to the fusion of real and virtual
devices used to integrate complicated networks.
Radius: It stands for remote access dial in user service. This is an open protocol written in heavy
code format and are available in the marketplace. It is mainly for the security of client server
system to protect from unauthorised and unauthenticated user. Some radius can run on all the
platforms and some are limited to specified platforms only.
This is the basic configuring Tacacs+ and GNS3 authentication using AAA Framework.
The purpose of designing this model is to use log in ID and password from Tacacs+
server and GNS3 for login authentication.
Before configuration these servers, it is necessary to check whether they are up to date or
not.
In this model, end device is Linux OS and Tacacs+ and GNS3 servers are using AAA
server (Thakare and et. al, 2017).
It can be downloaded on GNS3 marketplace but it is important to check that they are
connected to the internet or not.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCE
Books and Journals
Dhammawat and et. al., 2020. OPTIMIZED SIMULTANEOUS AUTHENTICATION OF
EQUALS (SAE) IDENTITY PRE-SHARED KEY (IPSK).
Haebler and et. al, 2017. Authentication, authorization, and/or accounting of power-consuming
devices. U.S. Patent 9,804,210.
Paramitha, A.P., Rochim, A.F. and Fauzi, A., 2020, April. Design and Implementation Network
Administrators Account Management System Based on Authentication, Authorization,
and Accounting Based on TACACS and LDAP. In IOP Conference Series: Materials
Science and Engineering (Vol. 803, No. 1, p. 012040). IOP Publishing.
Thakare and et. al, 2017. Secure negotiation of authentication capabilities. U.S. Patent
9,668,139.
Wong and et. al., 2017, September. Virtualized authentication, authorization and accounting (V-
AAA) in 5G networks. In 2017 IEEE Conference on Standards for Communications and
Networking (CSCN) (pp. 175-180). IEEE.
Online
Authentication, Authorization, Accounting and Identity Management. 2020 [Online] Available
Through: <https://www.ccsinet.com/blog/aaa-identity-management/>.
Books and Journals
Dhammawat and et. al., 2020. OPTIMIZED SIMULTANEOUS AUTHENTICATION OF
EQUALS (SAE) IDENTITY PRE-SHARED KEY (IPSK).
Haebler and et. al, 2017. Authentication, authorization, and/or accounting of power-consuming
devices. U.S. Patent 9,804,210.
Paramitha, A.P., Rochim, A.F. and Fauzi, A., 2020, April. Design and Implementation Network
Administrators Account Management System Based on Authentication, Authorization,
and Accounting Based on TACACS and LDAP. In IOP Conference Series: Materials
Science and Engineering (Vol. 803, No. 1, p. 012040). IOP Publishing.
Thakare and et. al, 2017. Secure negotiation of authentication capabilities. U.S. Patent
9,668,139.
Wong and et. al., 2017, September. Virtualized authentication, authorization and accounting (V-
AAA) in 5G networks. In 2017 IEEE Conference on Standards for Communications and
Networking (CSCN) (pp. 175-180). IEEE.
Online
Authentication, Authorization, Accounting and Identity Management. 2020 [Online] Available
Through: <https://www.ccsinet.com/blog/aaa-identity-management/>.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

![Data and System Security Assignment - [Course Name] Overview](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fea%2Fc6a7b1592b5747cb82c287512501193a.jpg&w=256&q=75)



