Analysis of Dark Web Services, Threats, and Mitigation Strategies
VerifiedAdded on 2023/04/05
|9
|2156
|186
Report
AI Summary
This report provides a detailed analysis of dark web services, exploring their components, impact, and associated threats. It begins by defining the surface web, deep web, and dark web, highlighting their key characteristics and differences. The report then delves into the impact of dark web services, including their use in illegal activities such as scams, human trafficking, and money laundering. It examines various threats, including ATM fraud, economic losses caused by malware attacks like Notpetya, and the vulnerabilities exploited by phishing and ransomware. The report discusses methods for threat analysis, such as OnionScan, and explains the functionalities of Tor for anonymous browsing. It also covers the literature on security breaches, focusing on ransomware, its success factors, and the role of Bitcoin in its spread. Finally, it provides insights into protecting against ransomware, including user training, spam filters, anti-virus software, and data backups. This report is a valuable resource for understanding the complexities of the dark web and the importance of cybersecurity measures.

THE ASSESSMENT OF WORK AND PROGRESS TOWARDS LEARNING
OUTCOMES OF QUESTION
1 to 4.
By
Name ----------------------------------------------------------------------------------------
Lecturer
Name -------------------------------------------------------
March/2019.
OUTCOMES OF QUESTION
1 to 4.
By
Name ----------------------------------------------------------------------------------------
Lecturer
Name -------------------------------------------------------
March/2019.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Solution.
Task 1.
Description of Dark web service.
The World Wide Web is composed of three main parts that are dark web, deep web and surface
web. According to Finklea( 2017) explained that surface web is accessed by everyone by just
typing in a Uniform resource locator or searching in web browsers for a resource or information
you need or want to use. For example, using Firefox or Google Chrome, you can type in the
URL. The URL of the website user want to access, for example when user want to use Microsoft
websites to download Microsoft word setup. what user need is to type the URL of Microsoft
website and user will be able to access the website to download Microsoft word setup, or user
search using google, yahoo search access to Microsoft website for example by typing a word
“Microsoft website” all information about Microsoft website will be displayed, and user can
click on a link or information user need.
According to Sui, Caverlee and Rudesill (2015) explained that the deep web is the web that you
cannot see. It uses a software called web crawler to index web search engines. Indexing enables
pages to be accessible and visible, to access pages you need URL and login details.
The information on the web which is not indexing on search engines cannot be accessed because
it is invisible. The Deep web has the largest portion size on the web. The Deep web is the biggest
among all other parts of the web (surface and dark web).many organization, companies and
people uses deep web for their daily transactions.According to Tarquin (2019) stated that about
96% of resources on the World Wide Web is being used by Deep web. According to Dickson
(2017) explained that the dark web has a tiny portion of the web that is only visible and accessed
using particular software for example Tor networks. The Dark web is known as Darknet. After
deep web there is dark web. According to Sirull (2019) explained that When Tor Brower is being
not installed on user computer. The user access world wide web, IP address of computer can be
accessed by government agencies which monitor and control the internet or even hackers but
when Tor Browser is installed on user computer all online activities are hidden and cannot
accessible by anyone.
Impact of dark web services.
According to C.M (2018) published and explained well impacts of dark web services.
Organization, company and people who are involved in the wrong, illegal or criminal acts ,for
example scamming, pornography, human traffic, hacking, money laundry and fraud activities
use the dark web to hide or protect themselves from governing bodies which monitors and
controls web.
According to Beep web ,admin(2015) explained that the dark web services has a high capacity to
increase on a number of several harmful activities in the near future, so it needs to be monitored
and controlled.
Task 1.
Description of Dark web service.
The World Wide Web is composed of three main parts that are dark web, deep web and surface
web. According to Finklea( 2017) explained that surface web is accessed by everyone by just
typing in a Uniform resource locator or searching in web browsers for a resource or information
you need or want to use. For example, using Firefox or Google Chrome, you can type in the
URL. The URL of the website user want to access, for example when user want to use Microsoft
websites to download Microsoft word setup. what user need is to type the URL of Microsoft
website and user will be able to access the website to download Microsoft word setup, or user
search using google, yahoo search access to Microsoft website for example by typing a word
“Microsoft website” all information about Microsoft website will be displayed, and user can
click on a link or information user need.
According to Sui, Caverlee and Rudesill (2015) explained that the deep web is the web that you
cannot see. It uses a software called web crawler to index web search engines. Indexing enables
pages to be accessible and visible, to access pages you need URL and login details.
The information on the web which is not indexing on search engines cannot be accessed because
it is invisible. The Deep web has the largest portion size on the web. The Deep web is the biggest
among all other parts of the web (surface and dark web).many organization, companies and
people uses deep web for their daily transactions.According to Tarquin (2019) stated that about
96% of resources on the World Wide Web is being used by Deep web. According to Dickson
(2017) explained that the dark web has a tiny portion of the web that is only visible and accessed
using particular software for example Tor networks. The Dark web is known as Darknet. After
deep web there is dark web. According to Sirull (2019) explained that When Tor Brower is being
not installed on user computer. The user access world wide web, IP address of computer can be
accessed by government agencies which monitor and control the internet or even hackers but
when Tor Browser is installed on user computer all online activities are hidden and cannot
accessible by anyone.
Impact of dark web services.
According to C.M (2018) published and explained well impacts of dark web services.
Organization, company and people who are involved in the wrong, illegal or criminal acts ,for
example scamming, pornography, human traffic, hacking, money laundry and fraud activities
use the dark web to hide or protect themselves from governing bodies which monitors and
controls web.
According to Beep web ,admin(2015) explained that the dark web services has a high capacity to
increase on a number of several harmful activities in the near future, so it needs to be monitored
and controlled.

Compare and contrast.
According to Sirull (2019) explained that indexing is done on Surface Web while indexing is not
done the Deep Web is mostly being used compare to surface web. The Government
easilymonitor cybercrime on the surface web as compared to the deep web where hackers hide.
Threat analysis.
Operations which are not being controlled on the dark web leads to illegal activities.
According to the FBI from 2016, much money is stolen in the USA about $2.5. There are
uncontrolled activities on web. This activities, are like to occur more in the future.
Atm fraud.
Fraud of money from ATM has evolved from skimmer of magstripe, use of malware and now
hackers fraud on hidden network
Criminals uses pluteus D malware to attack ATM mostly in the USA for short period ATM is
affected .Mostly windows XP.It is good to updates ATM to high version of windows for
example window 7 or window 8 which is not affected by such malware of recent.
Economic loss.
Notpetya malware attacked Maersk one of the leading company in the business of shipping.
It affected Maersk’s network in worldwide and paralyzed the operation of about 76 of their ports
in the world. A lot of business being lost in a short period of time. The Company lost about $200
to 300 million. Personal data was affected and the system went down. The company had to
replace about 4,000 and 45,000 affected computers and workstations respectively
Method used and reason
OnionScan is the best method to be used because it helps to identify websites or systems
“vulnerabilities, misconfigurations, and operational security holes in onion services”.
This act is called Phishing. According to Schneider (2016) explained that Phishing is a method
of fraud of accessing personal information, so it is an act of hacking.
According to Schneider (2016) explained different type of malware in details which includes Trojan
horses, Rootkits, Spyware and Ransomware.
Trojan Horses.
These are harmful software which pretends to be genuine and beneficial programs coming from a
legit source and convince victims to install them. Trojan allows unauthorized people to access
computers and attack computers by obtaining information from users for example login
credentials, financial transactions details and computer IP addresses. It gives room to
cybercrimes.
Examples of Trojan horses are “Magic Lantern”, “FinFisher”, “WARRIOR PRIDE” and “
Blackhole exploit kit”.
Spyware.
Spyware is a program developed to get people’s data or information from people without them
noticing example login details, information on websites and financial truncation of the company.
For example, it is alleged that the Russian government interfered with the USA election to make
president trump a winner. It may have used such kind of spyware if it is true.
Ransomware.
It is the program that denies the user access, takes control of the computer system and requests
the user to pay some money to access the computer again. According to Wilmington Trust
According to Sirull (2019) explained that indexing is done on Surface Web while indexing is not
done the Deep Web is mostly being used compare to surface web. The Government
easilymonitor cybercrime on the surface web as compared to the deep web where hackers hide.
Threat analysis.
Operations which are not being controlled on the dark web leads to illegal activities.
According to the FBI from 2016, much money is stolen in the USA about $2.5. There are
uncontrolled activities on web. This activities, are like to occur more in the future.
Atm fraud.
Fraud of money from ATM has evolved from skimmer of magstripe, use of malware and now
hackers fraud on hidden network
Criminals uses pluteus D malware to attack ATM mostly in the USA for short period ATM is
affected .Mostly windows XP.It is good to updates ATM to high version of windows for
example window 7 or window 8 which is not affected by such malware of recent.
Economic loss.
Notpetya malware attacked Maersk one of the leading company in the business of shipping.
It affected Maersk’s network in worldwide and paralyzed the operation of about 76 of their ports
in the world. A lot of business being lost in a short period of time. The Company lost about $200
to 300 million. Personal data was affected and the system went down. The company had to
replace about 4,000 and 45,000 affected computers and workstations respectively
Method used and reason
OnionScan is the best method to be used because it helps to identify websites or systems
“vulnerabilities, misconfigurations, and operational security holes in onion services”.
This act is called Phishing. According to Schneider (2016) explained that Phishing is a method
of fraud of accessing personal information, so it is an act of hacking.
According to Schneider (2016) explained different type of malware in details which includes Trojan
horses, Rootkits, Spyware and Ransomware.
Trojan Horses.
These are harmful software which pretends to be genuine and beneficial programs coming from a
legit source and convince victims to install them. Trojan allows unauthorized people to access
computers and attack computers by obtaining information from users for example login
credentials, financial transactions details and computer IP addresses. It gives room to
cybercrimes.
Examples of Trojan horses are “Magic Lantern”, “FinFisher”, “WARRIOR PRIDE” and “
Blackhole exploit kit”.
Spyware.
Spyware is a program developed to get people’s data or information from people without them
noticing example login details, information on websites and financial truncation of the company.
For example, it is alleged that the Russian government interfered with the USA election to make
president trump a winner. It may have used such kind of spyware if it is true.
Ransomware.
It is the program that denies the user access, takes control of the computer system and requests
the user to pay some money to access the computer again. According to Wilmington Trust
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Corporation (2018) explained that Ransomware is a very harmful software and they need to be
removed or prevent them.
Examples of ransomware are “Reveton”, “CryptoLocker”, and “CryptoWall”.
According to D'Amore (2015) presented about Tor in details as follows. Tor is The onion router
in full. The Tor can be accessed and download then used by everyone for free to protect
themselves from surveillance will surf the internet. It is developed for anonymous purpose while
the normal web browser is developed for non-anonymous purpose; it means available and can be
accessed by anyone.
According to Patel (2017) explained that Components of the tor are client, server, Tor
(onion) router and Directory server.
Tor protects users from being surveil lanced or monitored by government agencies or harmful
people or programs. For example when Emmanuel is to send a safe message (packet) to Tabitha
is using the Tor network. Tor will bring into existence a virtual network (private) for sending and
receiving of information.
According to D'Amore (2015) explained how Tor works.
First is to establish identify of all nodes available. Client “A” gets all number of nodes from the
server. The Tor selects the node without using any order so as the order or arrangement cannot
being noticed by any one person who can intercept communication.
The client produces a hidden (encrypted) message and sends to the first computer. The client on
computer does decryption for the first hidden message, established and identified on the next
computers.
The process continues until the position of the real receiver is being established, and it sends
decrypted messages to finish the process by no identifying name of the node.
removed or prevent them.
Examples of ransomware are “Reveton”, “CryptoLocker”, and “CryptoWall”.
According to D'Amore (2015) presented about Tor in details as follows. Tor is The onion router
in full. The Tor can be accessed and download then used by everyone for free to protect
themselves from surveillance will surf the internet. It is developed for anonymous purpose while
the normal web browser is developed for non-anonymous purpose; it means available and can be
accessed by anyone.
According to Patel (2017) explained that Components of the tor are client, server, Tor
(onion) router and Directory server.
Tor protects users from being surveil lanced or monitored by government agencies or harmful
people or programs. For example when Emmanuel is to send a safe message (packet) to Tabitha
is using the Tor network. Tor will bring into existence a virtual network (private) for sending and
receiving of information.
According to D'Amore (2015) explained how Tor works.
First is to establish identify of all nodes available. Client “A” gets all number of nodes from the
server. The Tor selects the node without using any order so as the order or arrangement cannot
being noticed by any one person who can intercept communication.
The client produces a hidden (encrypted) message and sends to the first computer. The client on
computer does decryption for the first hidden message, established and identified on the next
computers.
The process continues until the position of the real receiver is being established, and it sends
decrypted messages to finish the process by no identifying name of the node.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
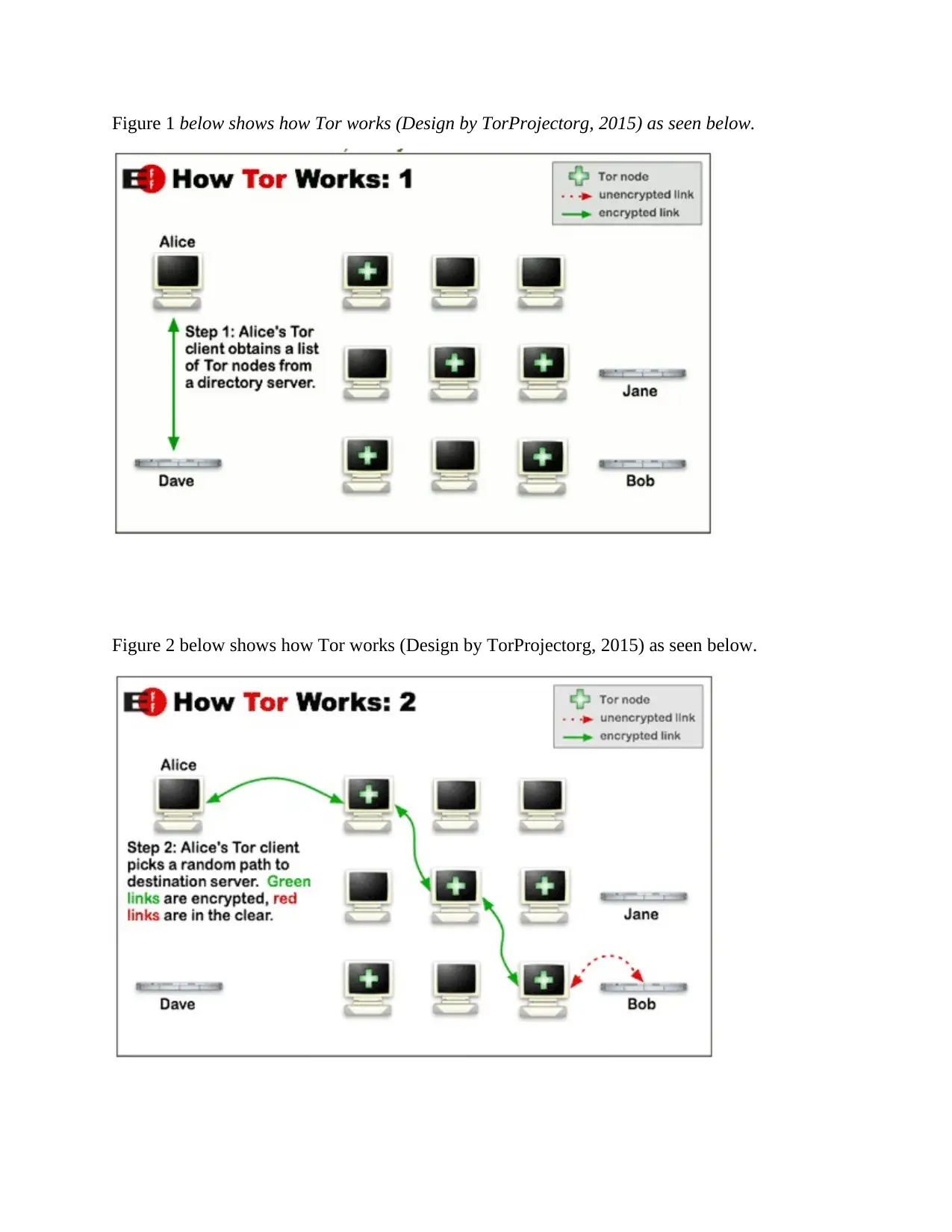
Figure 1 below shows how Tor works (Design by TorProjectorg, 2015) as seen below.
Figure 2 below shows how Tor works (Design by TorProjectorg, 2015) as seen below.
Figure 2 below shows how Tor works (Design by TorProjectorg, 2015) as seen below.
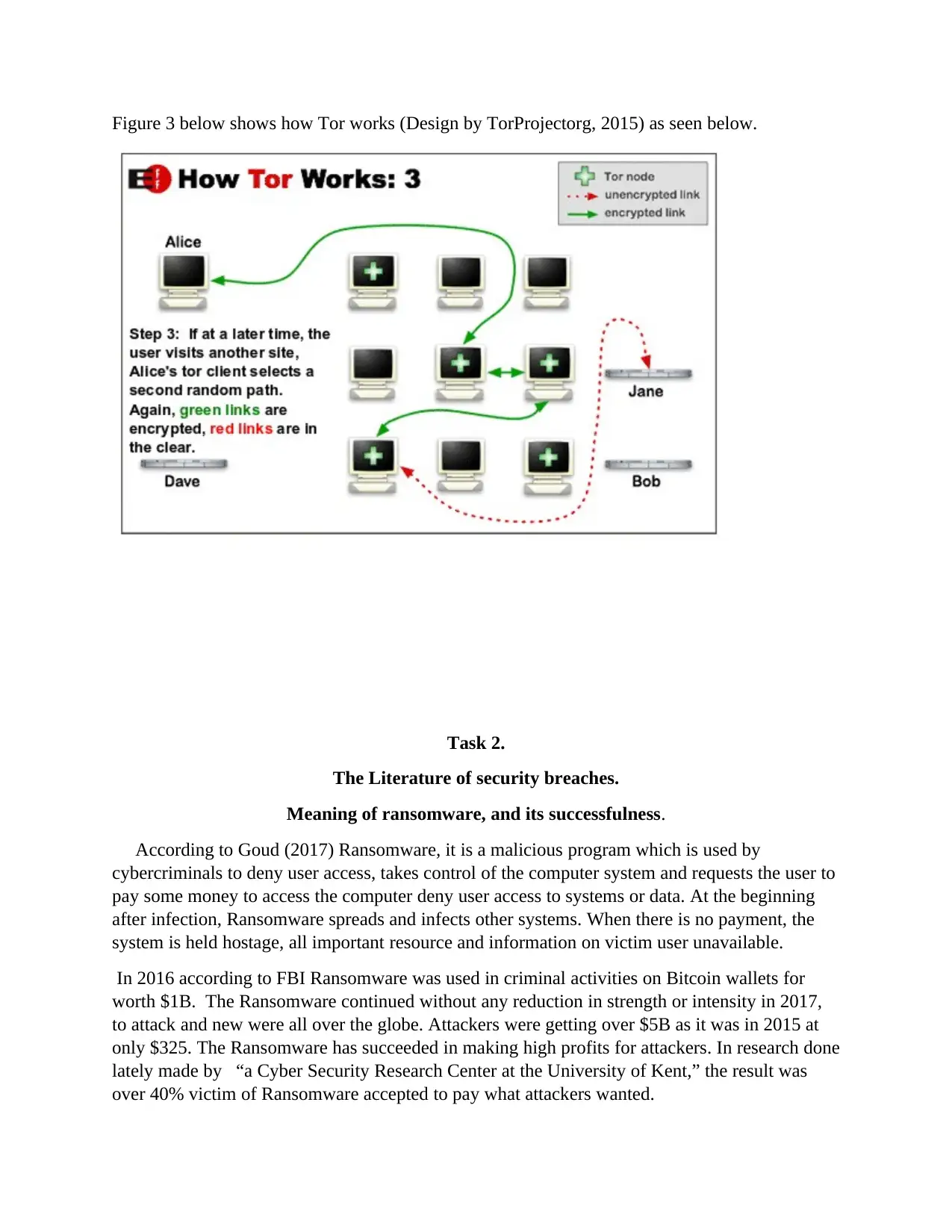
Figure 3 below shows how Tor works (Design by TorProjectorg, 2015) as seen below.
Task 2.
The Literature of security breaches.
Meaning of ransomware, and its successfulness.
According to Goud (2017) Ransomware, it is a malicious program which is used by
cybercriminals to deny user access, takes control of the computer system and requests the user to
pay some money to access the computer deny user access to systems or data. At the beginning
after infection, Ransomware spreads and infects other systems. When there is no payment, the
system is held hostage, all important resource and information on victim user unavailable.
In 2016 according to FBI Ransomware was used in criminal activities on Bitcoin wallets for
worth $1B. The Ransomware continued without any reduction in strength or intensity in 2017,
to attack and new were all over the globe. Attackers were getting over $5B as it was in 2015 at
only $325. The Ransomware has succeeded in making high profits for attackers. In research done
lately made by “a Cyber Security Research Center at the University of Kent,” the result was
over 40% victim of Ransomware accepted to pay what attackers wanted.
Task 2.
The Literature of security breaches.
Meaning of ransomware, and its successfulness.
According to Goud (2017) Ransomware, it is a malicious program which is used by
cybercriminals to deny user access, takes control of the computer system and requests the user to
pay some money to access the computer deny user access to systems or data. At the beginning
after infection, Ransomware spreads and infects other systems. When there is no payment, the
system is held hostage, all important resource and information on victim user unavailable.
In 2016 according to FBI Ransomware was used in criminal activities on Bitcoin wallets for
worth $1B. The Ransomware continued without any reduction in strength or intensity in 2017,
to attack and new were all over the globe. Attackers were getting over $5B as it was in 2015 at
only $325. The Ransomware has succeeded in making high profits for attackers. In research done
lately made by “a Cyber Security Research Center at the University of Kent,” the result was
over 40% victim of Ransomware accepted to pay what attackers wanted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Successfulness of Ransomware.
Due to the increase in accessing information on the web, ransomware spreads fast, easy and not
risky. Monitoring is not being required on ransom as compared to cybercrime. Its series of
activities are streamlined and automated.
It uses attack based on Psychology which is called Phishing. A Lot of emails of phishing are
sent only one click on attached message on mail it takes users to URLs which is harmful which
requests for information to be given out when information is provided user can be hacked .It is
that simple and fast.
Bitcoin
According to KNUTSON (2018) explained about cryptocurrency. After the invention of Bitcoin,
attacks of ransomware has increased worldwide. Cybercriminal insists payments be made in
Bitcoin because the currency is unable to be found. It demands payments in Bitcoin.
Cybercriminals no longer use so much PayPal and western union because they have put
measures to cab fraud and PayPal is strict. Bitcoin helps so much ransomware virus to spread.
The Spread of Ransomware.
According to SentinelOne (2015) explained how Ransomware works in details.
Distributions.
Level of attainment is through ransomware attached on email and spread to computers.
Infection.
Ransomware malware reaches computer of users and infection starts.
Communication.
The Action of talking to encryption-key servers take place.
File Search.
Step of searching useful file or information on the computer starts for example documents,
videos, pictures, financial transaction and programs.
Encryption.
The Action of Ransom encrypting useful information is done renaming, encrypting and
renaming again.
Ransom demand.
Finally, ransom has full control of the system, and it demands payment.
Due to the increase in accessing information on the web, ransomware spreads fast, easy and not
risky. Monitoring is not being required on ransom as compared to cybercrime. Its series of
activities are streamlined and automated.
It uses attack based on Psychology which is called Phishing. A Lot of emails of phishing are
sent only one click on attached message on mail it takes users to URLs which is harmful which
requests for information to be given out when information is provided user can be hacked .It is
that simple and fast.
Bitcoin
According to KNUTSON (2018) explained about cryptocurrency. After the invention of Bitcoin,
attacks of ransomware has increased worldwide. Cybercriminal insists payments be made in
Bitcoin because the currency is unable to be found. It demands payments in Bitcoin.
Cybercriminals no longer use so much PayPal and western union because they have put
measures to cab fraud and PayPal is strict. Bitcoin helps so much ransomware virus to spread.
The Spread of Ransomware.
According to SentinelOne (2015) explained how Ransomware works in details.
Distributions.
Level of attainment is through ransomware attached on email and spread to computers.
Infection.
Ransomware malware reaches computer of users and infection starts.
Communication.
The Action of talking to encryption-key servers take place.
File Search.
Step of searching useful file or information on the computer starts for example documents,
videos, pictures, financial transaction and programs.
Encryption.
The Action of Ransom encrypting useful information is done renaming, encrypting and
renaming again.
Ransom demand.
Finally, ransom has full control of the system, and it demands payment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Protect from Ransomware.
According to CUNY (2017), some measures have to be taken to protect user, prevent
Ransomware and remove ransomware.
Train users and make them aware of method Ransom use to spread and how to attack
individuals.
Use spam filters to stop emails of phishing on reaching users and use email technologies of
authentications.
Scanning of all emails in the inbox, sent and outbox for threat alerts.
Install anti-virus and anti-malware on the computers.
Remove Ransomware.
Use access control by providing roles to each level no level should access information of other
levels.
Use of defensive software tools is important for example Configuration Management, Filtering,
Intrusion Detection, and Encryption.
Separate the infected computer as soon as possible from uninfected to prevent ransomware from
attacking others.
Separate and put off power for computers which are fully affected to prevent more damage.
Ensuring systems and data backups have no malware.
Report the act immediately to law enforcing agency.
According to CUNY (2017), some measures have to be taken to protect user, prevent
Ransomware and remove ransomware.
Train users and make them aware of method Ransom use to spread and how to attack
individuals.
Use spam filters to stop emails of phishing on reaching users and use email technologies of
authentications.
Scanning of all emails in the inbox, sent and outbox for threat alerts.
Install anti-virus and anti-malware on the computers.
Remove Ransomware.
Use access control by providing roles to each level no level should access information of other
levels.
Use of defensive software tools is important for example Configuration Management, Filtering,
Intrusion Detection, and Encryption.
Separate the infected computer as soon as possible from uninfected to prevent ransomware from
attacking others.
Separate and put off power for computers which are fully affected to prevent more damage.
Ensuring systems and data backups have no malware.
Report the act immediately to law enforcing agency.

References.
Finklea, K. (March 10, 2017). Congressional Research Service. Dark Web.
Sui ,D,Caverlee and Rudesill, D. (2016) .The Deep web and the Darknet:
A look inside the internet’s massive black box.
Tarquin .(14 March 2019).How To Access Notorious Dark Web Anonymously (10 Step Guide).
Retrieved March, 16, 2019 from https://darkwebnews.com/help-advice/access-dark-web/.
D'Amore, F. (May 2015).A SIMPLE INTRODUCTION TO TOR.The Onion Router.
SentinelOne .(2015).The Rise of Ransomware & How to Defend Against it.
Patel, A. (2017).Tor Network. What is Tor? , why Tor is required and how Tor works?
KNUTSON.C. (2018) Cryptocurrency, Cybercrime and the Darkweb.SBS institute. Exonerator.
Retrieved March, 13, 2019, from https://exonerator.torproject.org/.
Goud, N. (2017). Cyber Attack with Ransomware hidden inside PDF Documents.
Retrieved March, 13, 2019 from https://www.cybersecurity-insiders.com/cyber-attack-with-
ransomware-hidden-inside-pdf-documents/.
Wilmington Trust Corporation. (2018). Avoid Becoming a Victim of Ransomware Attacks.
Whether securing your business or yourself, the first step is to understand how cybercriminals
work.
C.M. (16 may 2018).Impact of the Dark Web on Cybersecurity and Internet Governance.
Retrieved 14,03,2019 from https://darkwebnews.com/dark-web/impact-of-darkweb-in-
cybersecurity-and-internet/.
Beep web admin. (November 30, 2015).The Impact of the Dark Web on Internet Governance and
Cyber Security. Retrieved 14,03,2019 from
https://www.deepweb-sites.com/the impact of the dark web on internet-governance and
cybersecurity
CUNY, J, S. (2017). Monitoring the Dark Web and Securing Onion Services.
Dickson, B. (2017).A beginner’s guide to the dark web.
Retrieved 15,03,2019 from https://www.dailydot.com/layer8/what-is-dark-web/.
Sirull, E. (March 7, 2019).Cybersecurity. What Is the Dark Web?Retrieved March 16, 2019 from
https://www.experian.com/blogs/ask-experian/what-is-the-dark-web/.
Schneier, B. (2016). Security Engineering. (5th Ed) Pearson.
TorProjectorg. (2015). Tor: Overview. Images Retrieved March 16, 2019
From https://www.torproject.org/about/overview.html.en.
Finklea, K. (March 10, 2017). Congressional Research Service. Dark Web.
Sui ,D,Caverlee and Rudesill, D. (2016) .The Deep web and the Darknet:
A look inside the internet’s massive black box.
Tarquin .(14 March 2019).How To Access Notorious Dark Web Anonymously (10 Step Guide).
Retrieved March, 16, 2019 from https://darkwebnews.com/help-advice/access-dark-web/.
D'Amore, F. (May 2015).A SIMPLE INTRODUCTION TO TOR.The Onion Router.
SentinelOne .(2015).The Rise of Ransomware & How to Defend Against it.
Patel, A. (2017).Tor Network. What is Tor? , why Tor is required and how Tor works?
KNUTSON.C. (2018) Cryptocurrency, Cybercrime and the Darkweb.SBS institute. Exonerator.
Retrieved March, 13, 2019, from https://exonerator.torproject.org/.
Goud, N. (2017). Cyber Attack with Ransomware hidden inside PDF Documents.
Retrieved March, 13, 2019 from https://www.cybersecurity-insiders.com/cyber-attack-with-
ransomware-hidden-inside-pdf-documents/.
Wilmington Trust Corporation. (2018). Avoid Becoming a Victim of Ransomware Attacks.
Whether securing your business or yourself, the first step is to understand how cybercriminals
work.
C.M. (16 may 2018).Impact of the Dark Web on Cybersecurity and Internet Governance.
Retrieved 14,03,2019 from https://darkwebnews.com/dark-web/impact-of-darkweb-in-
cybersecurity-and-internet/.
Beep web admin. (November 30, 2015).The Impact of the Dark Web on Internet Governance and
Cyber Security. Retrieved 14,03,2019 from
https://www.deepweb-sites.com/the impact of the dark web on internet-governance and
cybersecurity
CUNY, J, S. (2017). Monitoring the Dark Web and Securing Onion Services.
Dickson, B. (2017).A beginner’s guide to the dark web.
Retrieved 15,03,2019 from https://www.dailydot.com/layer8/what-is-dark-web/.
Sirull, E. (March 7, 2019).Cybersecurity. What Is the Dark Web?Retrieved March 16, 2019 from
https://www.experian.com/blogs/ask-experian/what-is-the-dark-web/.
Schneier, B. (2016). Security Engineering. (5th Ed) Pearson.
TorProjectorg. (2015). Tor: Overview. Images Retrieved March 16, 2019
From https://www.torproject.org/about/overview.html.en.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




