Cyber Security WannCry Attack Case Study 2022
VerifiedAdded on 2022/10/08
|11
|2314
|16
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
CYBERSECURITY 0
WannCry Attack
WannCry Attack
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CYBERSECURITY 1
Table of Contents
Introduction.............................................................................................................................................................. 2
WannaCry Walkthrough...................................................................................................................................... 2
What is WannCry Attack?............................................................................................................................... 2
How does WannCry attack work?............................................................................................................... 4
Real work example................................................................................................................................................. 6
Conclusion................................................................................................................................................................. 7
References................................................................................................................................................................. 9
Table of Contents
Introduction.............................................................................................................................................................. 2
WannaCry Walkthrough...................................................................................................................................... 2
What is WannCry Attack?............................................................................................................................... 2
How does WannCry attack work?............................................................................................................... 4
Real work example................................................................................................................................................. 6
Conclusion................................................................................................................................................................. 7
References................................................................................................................................................................. 9

CYBERSECURITY 2
Introduction
WannaCry is a part of the ransomware that was developed and implemented in the
year 2017 by a crypto worm that targeted computer running the Microsoft Windows
operating systems. It is one of the serious cyber-attacks which directly impacts on the
computing networks and devices used by companies (Anjana, 2017). Mainly, hackers
produce such kind of attack for earning money and collecting the private details of
companies without taking their permission. This investigation aims to inspect the key
features of WannCry attack and assess their operational principle along with the real-world
example. A walkthrough process will be included in this report in order to analyze the risk
factors that produce WannaCry type of ransomware attack in the companies. It is very
important to identify the risk elements which increase ransomware type of attacks and
companies require a platform where they can analysis security related issues linked with
computing networks. This report will provide a way where the students can enhance their
skills in the area of cyber-security attacks and evaluate the impacts of WannCry attack on
the personal data files.
WannaCry Walkthrough
What is WannCry Attack?
WannCry is defined as a cyber-attack that mainly developed by cryptoworm in tear
2017 from the perspective of hacking. It is a part of a ransomware attack that has the
potential to collect data of victims and businesses by transporting unauthentic signals to
the main server (Srinivasan, 2017). Such kind of security attack spread rapidly across
numbers of computing devices in May of 2017 and encrypt the sensitive data of consumers
by using malicious tools and networks. It is a common type of ransomware faced by
companies in the year 2017 and 2018 that sent unwanted signal and systems to the user's
devices and performs hacking-related activities (Arora, Yadav, & Sharma, 2018). There are
major two risk factors which increased the issue of wanna cry in 2017 including lack of
privacy and utilization of unauthentic networks.
Introduction
WannaCry is a part of the ransomware that was developed and implemented in the
year 2017 by a crypto worm that targeted computer running the Microsoft Windows
operating systems. It is one of the serious cyber-attacks which directly impacts on the
computing networks and devices used by companies (Anjana, 2017). Mainly, hackers
produce such kind of attack for earning money and collecting the private details of
companies without taking their permission. This investigation aims to inspect the key
features of WannCry attack and assess their operational principle along with the real-world
example. A walkthrough process will be included in this report in order to analyze the risk
factors that produce WannaCry type of ransomware attack in the companies. It is very
important to identify the risk elements which increase ransomware type of attacks and
companies require a platform where they can analysis security related issues linked with
computing networks. This report will provide a way where the students can enhance their
skills in the area of cyber-security attacks and evaluate the impacts of WannCry attack on
the personal data files.
WannaCry Walkthrough
What is WannCry Attack?
WannCry is defined as a cyber-attack that mainly developed by cryptoworm in tear
2017 from the perspective of hacking. It is a part of a ransomware attack that has the
potential to collect data of victims and businesses by transporting unauthentic signals to
the main server (Srinivasan, 2017). Such kind of security attack spread rapidly across
numbers of computing devices in May of 2017 and encrypt the sensitive data of consumers
by using malicious tools and networks. It is a common type of ransomware faced by
companies in the year 2017 and 2018 that sent unwanted signal and systems to the user's
devices and performs hacking-related activities (Arora, Yadav, & Sharma, 2018). There are
major two risk factors which increased the issue of wanna cry in 2017 including lack of
privacy and utilization of unauthentic networks.
CYBERSECURITY 3
A recent study argued that the WannaCry attack includes numbers of components,
for example, a copy of Tor, files including encryption keys, and a system which encrypts
and decrypts information. It arrives on the infected computing networks in the form of
unauthentic signals and networks which are able to reduce the performance of networks
used by companies and help the criminals to enter into the main server for obtaining
reliable data. The criminals mainly use botnet and malicious process in order to produce
unwanted signals and attack on the computing networks which reduce the security of data
and help to perform data breach-related activities in the servers (Chen, & Bridges, 2017).
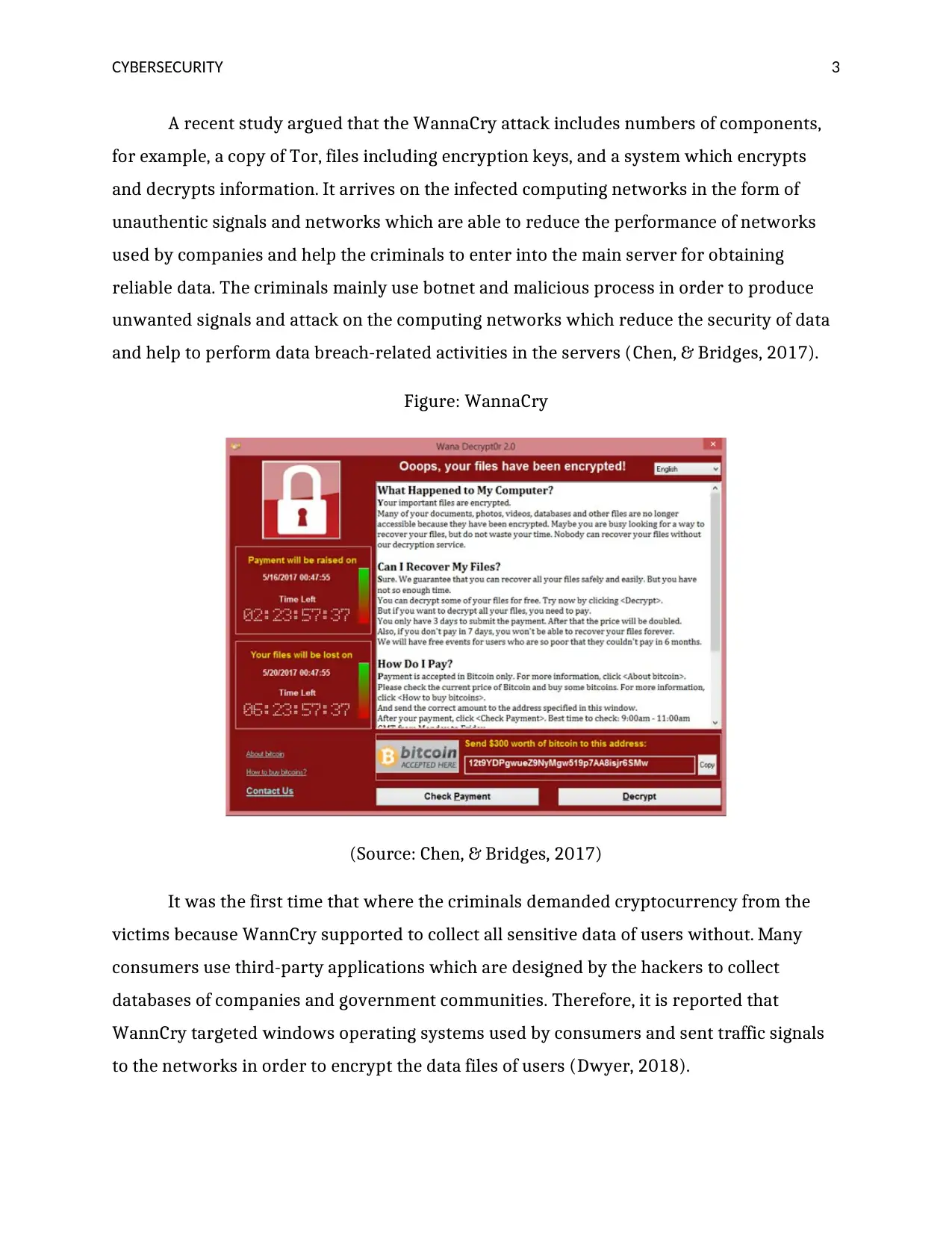
Figure: WannaCry
(Source: Chen, & Bridges, 2017)
It was the first time that where the criminals demanded cryptocurrency from the
victims because WannCry supported to collect all sensitive data of users without. Many
consumers use third-party applications which are designed by the hackers to collect
databases of companies and government communities. Therefore, it is reported that
WannCry targeted windows operating systems used by consumers and sent traffic signals
to the networks in order to encrypt the data files of users (Dwyer, 2018).
A recent study argued that the WannaCry attack includes numbers of components,
for example, a copy of Tor, files including encryption keys, and a system which encrypts
and decrypts information. It arrives on the infected computing networks in the form of
unauthentic signals and networks which are able to reduce the performance of networks
used by companies and help the criminals to enter into the main server for obtaining
reliable data. The criminals mainly use botnet and malicious process in order to produce
unwanted signals and attack on the computing networks which reduce the security of data
and help to perform data breach-related activities in the servers (Chen, & Bridges, 2017).
Figure: WannaCry
(Source: Chen, & Bridges, 2017)
It was the first time that where the criminals demanded cryptocurrency from the
victims because WannCry supported to collect all sensitive data of users without. Many
consumers use third-party applications which are designed by the hackers to collect
databases of companies and government communities. Therefore, it is reported that
WannCry targeted windows operating systems used by consumers and sent traffic signals
to the networks in order to encrypt the data files of users (Dwyer, 2018).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CYBERSECURITY 4
How does WannaCry attack work?
WannCry ransomware is very common which is propagated using a worm that
spread unwanted signals from one network to another using malware tools and
techniques. Generally, WannCfry infects Windows operating system, encrypting data files
of consumers and earn ransom from the consumers. The working of WannaCry is not much
complicated but it requires a platform where criminals can perform hacking-related
activities and issues. According to Hsiao, & Kao, (2018) Wanncry ransomware exploits
vulnerability in SMBv1 network of Microsoft by sharing unwanted signals and networks to
the main server. WannaCry utilizes the EternalBlue worm in order to obtain the personal
data of consumers. The working of WannaCry includes numerous steps and techniques but
it uses the working principle of a ransomware attack (Navarro, Legrand, Deruyver, &
Parrend, 2018).
The first step is to determine the target networks and servers for devices accepting
traffic signals that show the developed system is configured to run an SMB network
(Ioanid, Scarlat, & Militaru, 2017). After that, the attackers direct traffic signs to the chief
servers and networks and reduce the performance of computing devices. Moreover, the
hackers send fraud or spam mails to the consumers in order to access their computer
systems and encrypt all the personal data including financial details (Walker-Roberts,
Hammoudeh & Dehghantanha, 2018). The attack vector for wanna cry is more effective
rather than other attacks that use the key aspects of malicious tools in order to gather
reliable data. The server message block helps hackers to communicate with the consumer’s
networks and implement Trojan related activities in the main servers (Mohurle, & Patil,
2017). The below flow chart show the working of WannCry attack which includes various
kinds of networks and encryption system for obtaining the sensitive data of users and
companies.
Figure: Working of WannaCry
Arrive via exploit
How does WannaCry attack work?
WannCry ransomware is very common which is propagated using a worm that
spread unwanted signals from one network to another using malware tools and
techniques. Generally, WannCfry infects Windows operating system, encrypting data files
of consumers and earn ransom from the consumers. The working of WannaCry is not much
complicated but it requires a platform where criminals can perform hacking-related
activities and issues. According to Hsiao, & Kao, (2018) Wanncry ransomware exploits
vulnerability in SMBv1 network of Microsoft by sharing unwanted signals and networks to
the main server. WannaCry utilizes the EternalBlue worm in order to obtain the personal
data of consumers. The working of WannaCry includes numerous steps and techniques but
it uses the working principle of a ransomware attack (Navarro, Legrand, Deruyver, &
Parrend, 2018).
The first step is to determine the target networks and servers for devices accepting
traffic signals that show the developed system is configured to run an SMB network
(Ioanid, Scarlat, & Militaru, 2017). After that, the attackers direct traffic signs to the chief
servers and networks and reduce the performance of computing devices. Moreover, the
hackers send fraud or spam mails to the consumers in order to access their computer
systems and encrypt all the personal data including financial details (Walker-Roberts,
Hammoudeh & Dehghantanha, 2018). The attack vector for wanna cry is more effective
rather than other attacks that use the key aspects of malicious tools in order to gather
reliable data. The server message block helps hackers to communicate with the consumer’s
networks and implement Trojan related activities in the main servers (Mohurle, & Patil,
2017). The below flow chart show the working of WannCry attack which includes various
kinds of networks and encryption system for obtaining the sensitive data of users and
companies.
Figure: Working of WannaCry
Arrive via exploit
CYBERSECURITY 5
(Source: By Author)
It is observed that there are major five steps involves in the working of WannaCry
ransomware attack which is described below:
Arriving unwanted signals and data through exploit
Files delivered through exploit running as a service
Drop fraud and ransomware signals which perform data breach activities
Reduce the performance of computing networks by spreading the traffic signals
Enter into the main server and perform the encryption process
Encrypt local and shared files
(Source: By Author)
It is observed that there are major five steps involves in the working of WannaCry
ransomware attack which is described below:
Arriving unwanted signals and data through exploit
Files delivered through exploit running as a service
Drop fraud and ransomware signals which perform data breach activities
Reduce the performance of computing networks by spreading the traffic signals
Enter into the main server and perform the encryption process
Encrypt local and shared files
CYBERSECURITY 6
Therefore, with the help of all these steps, the criminals can perform WannCry
ransomware and encrypt the sensitive data of consumers in order to earn some ransom.
After collecting all reliable data the criminals communicate with the victims through social
networks and demand some ransom.
Real world example
NHS is one of the best examples for understanding the impacts of WannaCry attack
and in the year 2017 NHS organization was suffered from security threats and data breach
issues. It is observed that in the year 2017 between 12 and 19 May the national health
services reported that the traffic signals and WannaCry attack were infected in their
systems and criminals encrypted their main servers along with the data centres (Field,
2018). This attack was given a name called WannaCry NHS attack that mainly affected
thousands of computer networks and devices used by the NHS.
Figure: NHS WannaCry attack
(Source: Field, 2018).
The outcomes of chosen attacks show positive responses towards the data breach
where the hackers caused around 19,000 appointments to be cancelled with the cost of
£92m (Petrenko, Petrenko, Makoveichuk, & Chetyrbok, 2018). A recent study identified
that WannaCry attack was carried out by spreading traffic signals to the networks and
servers used in NHS community. It is examined that WannaCry attack affected around
Therefore, with the help of all these steps, the criminals can perform WannCry
ransomware and encrypt the sensitive data of consumers in order to earn some ransom.
After collecting all reliable data the criminals communicate with the victims through social
networks and demand some ransom.
Real world example
NHS is one of the best examples for understanding the impacts of WannaCry attack
and in the year 2017 NHS organization was suffered from security threats and data breach
issues. It is observed that in the year 2017 between 12 and 19 May the national health
services reported that the traffic signals and WannaCry attack were infected in their
systems and criminals encrypted their main servers along with the data centres (Field,
2018). This attack was given a name called WannaCry NHS attack that mainly affected
thousands of computer networks and devices used by the NHS.
Figure: NHS WannaCry attack
(Source: Field, 2018).
The outcomes of chosen attacks show positive responses towards the data breach
where the hackers caused around 19,000 appointments to be cancelled with the cost of
£92m (Petrenko, Petrenko, Makoveichuk, & Chetyrbok, 2018). A recent study identified
that WannaCry attack was carried out by spreading traffic signals to the networks and
servers used in NHS community. It is examined that WannaCry attack affected around
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 7
200,000 computer systems by sending red-lettered error messages that encrypted the data
files stored in the computer devices and demanded the cryptocurrency bitcoin from the
consumers. This cyber-attack was blamed on elite North Korean criminals after one year’s
investigation and it also produced financial issues for management team of NHS and
hackers demanded some ransom for decrypting the collected data files. Mainly, the
criminals targeted MCA and authenticity related security systems used by NHS and helped
the criminals for sending the traffic signals using malicious tools.
There are major three consequences produced by the computing networks and
security systems including, data breach, hacking-related activities and reduced
performance of computing devices used by the employees. In order to control and manage
the WannaCry ransomware, NHS changed their IT infrastructures and adopted advanced
computer networks that helped them for reducing the rate of security threats (Sahi, 2017).
Moreover, the NHS communicated with the IT team and asked to provide better solutions
and identify the risk factors that produced such kind of issues in the workplace.
After this attack, the management of NHS paid ransom to the hackers and stored
their personal data on cloud-based servers for securing sensitive data (Schirrmacher,
Ondrus, & Ter, 2018). Moreover, NHS developed and implemented security-related
strategies in the workplace and provided proper training to the employees for reducing the
utilization of unauthentic networks and third-party applications in the computing devices.
Conclusion
It is concluded that WannaCry is a very serious attack that directly impacts on the
private details of companies. This proposed research reviewed and analyzed the key
features of WannaCry and also highlighted their working principle. In order to improve the
effectiveness of research WannaCry attack on NHS also reviewed that lost around 19000
appointments due to lack of security and WannaCry ransomware. Therefore, it is stated
that wannacry attack can be reduced by providing proper training and education to the
consumers in the workplace and companies should develop security-related strategies and
policies.
200,000 computer systems by sending red-lettered error messages that encrypted the data
files stored in the computer devices and demanded the cryptocurrency bitcoin from the
consumers. This cyber-attack was blamed on elite North Korean criminals after one year’s
investigation and it also produced financial issues for management team of NHS and
hackers demanded some ransom for decrypting the collected data files. Mainly, the
criminals targeted MCA and authenticity related security systems used by NHS and helped
the criminals for sending the traffic signals using malicious tools.
There are major three consequences produced by the computing networks and
security systems including, data breach, hacking-related activities and reduced
performance of computing devices used by the employees. In order to control and manage
the WannaCry ransomware, NHS changed their IT infrastructures and adopted advanced
computer networks that helped them for reducing the rate of security threats (Sahi, 2017).
Moreover, the NHS communicated with the IT team and asked to provide better solutions
and identify the risk factors that produced such kind of issues in the workplace.
After this attack, the management of NHS paid ransom to the hackers and stored
their personal data on cloud-based servers for securing sensitive data (Schirrmacher,
Ondrus, & Ter, 2018). Moreover, NHS developed and implemented security-related
strategies in the workplace and provided proper training to the employees for reducing the
utilization of unauthentic networks and third-party applications in the computing devices.
Conclusion
It is concluded that WannaCry is a very serious attack that directly impacts on the
private details of companies. This proposed research reviewed and analyzed the key
features of WannaCry and also highlighted their working principle. In order to improve the
effectiveness of research WannaCry attack on NHS also reviewed that lost around 19000
appointments due to lack of security and WannaCry ransomware. Therefore, it is stated
that wannacry attack can be reduced by providing proper training and education to the
consumers in the workplace and companies should develop security-related strategies and
policies.

CYBERSECURITY 8

CYBERSECURITY 9
References
Anjana, T. K. (2017). Discussion On Ransomware, Wannacry Ransomware and Cloud
Storage Services Against Ransom Malware Attacks. International Journal for
Research Trends and Innovation, 2, 310-314.
Arora, A., Yadav, S. K., & Sharma, K. (2018). Denial-of-Service (DoS) Attack and Botnet:
Network Analysis, Research Tactics, and Mitigation. In Handbook of Research on
Network Forensics and Analysis Techniques (pp. 117-141). IGI Global.
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioural analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
Dwyer, A. C. (2018). The NHS cyber-attack: A look at the complex environmental conditions
of WannaCry. RAD Magazine, 44.
Field, M. (2018). WannaCry cyberattack cost the NHS £92m as 19,000 appointments
cancelled. Retrieved from:
https://www.telegraph.co.uk/technology/2018/10/11/wannacry-cyber-attack-
cost-nhs-92m-19000-appointments-cancelled/
Hsiao, S. C., & Kao, D. Y. (2018, February). The static analysis of WannaCry ransomware.
In 2018 20th International Conference on Advanced Communication Technology
(ICACT) (pp. 153-158). IEEE.
Ioanid, A., Scarlat, C., & Militaru, G. (2017, September). The Effect of Cybercrime on
Romanian SMEs in the Context of Wannacry Ransomware Attacks. In European
Conference on Innovation and Entrepreneurship (pp. 307-313). Academic
Conferences International Limited.
Kao, D. Y., & Hsiao, S. C. (2018, February). The dynamic analysis of WannaCry ransomware.
In 2018 20th International Conference on Advanced Communication Technology
(ICACT) (pp. 159-166). IEEE.
References
Anjana, T. K. (2017). Discussion On Ransomware, Wannacry Ransomware and Cloud
Storage Services Against Ransom Malware Attacks. International Journal for
Research Trends and Innovation, 2, 310-314.
Arora, A., Yadav, S. K., & Sharma, K. (2018). Denial-of-Service (DoS) Attack and Botnet:
Network Analysis, Research Tactics, and Mitigation. In Handbook of Research on
Network Forensics and Analysis Techniques (pp. 117-141). IGI Global.
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioural analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
Dwyer, A. C. (2018). The NHS cyber-attack: A look at the complex environmental conditions
of WannaCry. RAD Magazine, 44.
Field, M. (2018). WannaCry cyberattack cost the NHS £92m as 19,000 appointments
cancelled. Retrieved from:
https://www.telegraph.co.uk/technology/2018/10/11/wannacry-cyber-attack-
cost-nhs-92m-19000-appointments-cancelled/
Hsiao, S. C., & Kao, D. Y. (2018, February). The static analysis of WannaCry ransomware.
In 2018 20th International Conference on Advanced Communication Technology
(ICACT) (pp. 153-158). IEEE.
Ioanid, A., Scarlat, C., & Militaru, G. (2017, September). The Effect of Cybercrime on
Romanian SMEs in the Context of Wannacry Ransomware Attacks. In European
Conference on Innovation and Entrepreneurship (pp. 307-313). Academic
Conferences International Limited.
Kao, D. Y., & Hsiao, S. C. (2018, February). The dynamic analysis of WannaCry ransomware.
In 2018 20th International Conference on Advanced Communication Technology
(ICACT) (pp. 159-166). IEEE.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CYBERSECURITY 10
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Navarro, J., Legrand, V., Deruyver, A., & Parrend, P. (2018). OMMA: open architecture for
Operator-guided Monitoring of Multi-step Attacks. EURASIP Journal on Information
Security, 2018(1), 6.
Petrenko, A. S., Petrenko, S. A., Makoveichuk, K. A., & Chetyrbok, P. V. (2018). Protection
model of PCS of the subway from attacks type «wanna cry», «Petya» and «bad
rabbit» IoT. In 2018 IEEE Conference of Russian Young Researchers in Electrical and
Electronic Engineering (EIConRus) (pp. 945-949). IEEE.
Sahi, S. K. (2017). A Study of WannaCry Ransomware Attack. International Journal of
Engineering Research in Computer Science and Engineering, 4(9), 5-7.
Schirrmacher, N. B., Ondrus, J., & Ter, C., (2018). Towards a Response to Ransomware:
Examining Digital Capabilities of the WannaCry Attack. In PACIS, 12(8), 210.
Srinivasan, C. R. (2017). Hobby hackers to billion-dollar industry: the evolution of
ransomware. Computer Fraud & Security, 2017(11), 7-9.
Walker-Roberts, S., Hammoudeh, M., & Dehghantanha, A. (2018). A systematic review of the
availability and efficacy of countermeasures to internal threats in healthcare critical
infrastructure. IEEE Access, 6(7), 25167-25177.
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Navarro, J., Legrand, V., Deruyver, A., & Parrend, P. (2018). OMMA: open architecture for
Operator-guided Monitoring of Multi-step Attacks. EURASIP Journal on Information
Security, 2018(1), 6.
Petrenko, A. S., Petrenko, S. A., Makoveichuk, K. A., & Chetyrbok, P. V. (2018). Protection
model of PCS of the subway from attacks type «wanna cry», «Petya» and «bad
rabbit» IoT. In 2018 IEEE Conference of Russian Young Researchers in Electrical and
Electronic Engineering (EIConRus) (pp. 945-949). IEEE.
Sahi, S. K. (2017). A Study of WannaCry Ransomware Attack. International Journal of
Engineering Research in Computer Science and Engineering, 4(9), 5-7.
Schirrmacher, N. B., Ondrus, J., & Ter, C., (2018). Towards a Response to Ransomware:
Examining Digital Capabilities of the WannaCry Attack. In PACIS, 12(8), 210.
Srinivasan, C. R. (2017). Hobby hackers to billion-dollar industry: the evolution of
ransomware. Computer Fraud & Security, 2017(11), 7-9.
Walker-Roberts, S., Hammoudeh, M., & Dehghantanha, A. (2018). A systematic review of the
availability and efficacy of countermeasures to internal threats in healthcare critical
infrastructure. IEEE Access, 6(7), 25167-25177.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





