Analysis of the Future of Fog Domain in IoT Networks
VerifiedAdded on 2023/01/23
|17
|3771
|85
Report
AI Summary
This report provides a comprehensive analysis of the future of the fog domain, a new model in cloud computing environment, and its critical role in the Internet of Things (IoT). The study delves into the functionalities of fog and cloud computing, assessing the readiness of fog for future network paradigms. It explores various components of the fog domain, architectural technologies, and security threats such as hidden channel attacks and data plane attacks. Through a literature review, the report highlights the advantages of fog computing, including lower latency, a larger number of nodes, higher velocity, and greater energy control capabilities compared to cloud computing. The findings emphasize the importance of fog in IoT, such as the absence of network congestion, ease of integration, and scalability. The report concludes that fog computing is a crucial element in the modern world. The report also analyses the security issues in the fog domain and cloud domain.

Running head: THE FUTURE OF FOG DOMAIN 1
Future of the Fog Domain
Name
Institutional Affiliation
Future of the Fog Domain
Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

THE FUTURE OF FOG DOMAIN 2
Abstract
Industrial revolution in the fourth phase signifies a paradigm shift in which things,
processes, people, network and data connect and communicate with each other. Moreover,
computing infrastructure are making ways to satisfy intense growth in demand emanating from
massive linked heterogeneous end points through network to meet quality service levels. IoT has
extended its scope and capabilities of service provisions with integration of both cloud and fog
computing domain. Cloud domain involves data storage and computing power without full direct
management by the user. The issues in the cloud domain include reliability, security, availability
of services and data, costs, hidden channel attack, control plane attack and data plane attack. Fog
is a new model in computing environment and is characterized with data storage, network
services and facility computation. The issues with fog domain include jamming attacks and
sniffer attacks. This research study focuses on the current functionalities of fog as well as cloud
computing domain and also assesses readiness of fog domain for future network paradigm.
Through the purpose of the research, various components of fog domain have been demonstrated
and architectural technologies surrounding fog domain have been determined. Furthermore,
through literature review, security threats to cloud computing such as hidden channel attack, and
data plan attack are analyzed. Moreover, fog domain is found to be more essential than cloud
domain in network connection since fog computing has lower latency, larger number of nodes,
higher velocity and larger energy controlling capability over cloud domain, thereby projected as
future network paradigm. In conclusion, fog domain has been found to have a range of
importance in IoT such as; no network congestion, enables management and ease in integration
with IoT environments and also offers scale, thus fog domain is future network paradigm.
Key words: Cloud domain, fog domain, network, security, IoT and computing
Abstract
Industrial revolution in the fourth phase signifies a paradigm shift in which things,
processes, people, network and data connect and communicate with each other. Moreover,
computing infrastructure are making ways to satisfy intense growth in demand emanating from
massive linked heterogeneous end points through network to meet quality service levels. IoT has
extended its scope and capabilities of service provisions with integration of both cloud and fog
computing domain. Cloud domain involves data storage and computing power without full direct
management by the user. The issues in the cloud domain include reliability, security, availability
of services and data, costs, hidden channel attack, control plane attack and data plane attack. Fog
is a new model in computing environment and is characterized with data storage, network
services and facility computation. The issues with fog domain include jamming attacks and
sniffer attacks. This research study focuses on the current functionalities of fog as well as cloud
computing domain and also assesses readiness of fog domain for future network paradigm.
Through the purpose of the research, various components of fog domain have been demonstrated
and architectural technologies surrounding fog domain have been determined. Furthermore,
through literature review, security threats to cloud computing such as hidden channel attack, and
data plan attack are analyzed. Moreover, fog domain is found to be more essential than cloud
domain in network connection since fog computing has lower latency, larger number of nodes,
higher velocity and larger energy controlling capability over cloud domain, thereby projected as
future network paradigm. In conclusion, fog domain has been found to have a range of
importance in IoT such as; no network congestion, enables management and ease in integration
with IoT environments and also offers scale, thus fog domain is future network paradigm.
Key words: Cloud domain, fog domain, network, security, IoT and computing

THE FUTURE OF FOG DOMAIN 3
1. Introduction
1.1 Background of the Study
Fog domain is a new model in cloud computing environment. Also, it is an extension of
traditional cloud computing that functions on the simulated framework of network. In addition, it
provides stackable system of storage, network services, pool of resources, and facility of
computation. Fog domain is also vital in managing communication among heterogeneous
devices in completing task. On the other hand, internet of things can be termed as a system of
correlated computing devices, mechanical as well as digital machines, objects, people or animals
with unique identifiers and ability of transferring data over a network without involving human –
to – computer or human – to – human interaction.
Categorically, this report focuses on the new technology named Fog domain and security
issues found in the existing technology, for example, cloud computing that helps in clear
understanding of matters of fog domain. Besides, concepts of fog computing aids in provision of
network services to the edge of complete network. In addition, fog computing helps in provision
of data, data storage and data computation in accordance to the user’s requirements
1.2 Purpose of the Study
This research is aimed at the following;
To explain as well as demonstrate different components of fog domain as IoT.
To analyze the role as well as importance of fog domain in the current modern world.
To investigate as well as to propose different requirements of fog domain for real
world applications.
To determine existing as well as emerging architecture technologies for fog domain.
1. Introduction
1.1 Background of the Study
Fog domain is a new model in cloud computing environment. Also, it is an extension of
traditional cloud computing that functions on the simulated framework of network. In addition, it
provides stackable system of storage, network services, pool of resources, and facility of
computation. Fog domain is also vital in managing communication among heterogeneous
devices in completing task. On the other hand, internet of things can be termed as a system of
correlated computing devices, mechanical as well as digital machines, objects, people or animals
with unique identifiers and ability of transferring data over a network without involving human –
to – computer or human – to – human interaction.
Categorically, this report focuses on the new technology named Fog domain and security
issues found in the existing technology, for example, cloud computing that helps in clear
understanding of matters of fog domain. Besides, concepts of fog computing aids in provision of
network services to the edge of complete network. In addition, fog computing helps in provision
of data, data storage and data computation in accordance to the user’s requirements
1.2 Purpose of the Study
This research is aimed at the following;
To explain as well as demonstrate different components of fog domain as IoT.
To analyze the role as well as importance of fog domain in the current modern world.
To investigate as well as to propose different requirements of fog domain for real
world applications.
To determine existing as well as emerging architecture technologies for fog domain.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

THE FUTURE OF FOG DOMAIN 4
To not only describe but also evaluate various fog domain applications
1.3 Scope of the Research Study
This research study on fog domain aids in scrutinizing security issues and challenges
surrounding fog domain and also helps in determining preferred solutions for resolving security
issues efficiently to offer smooth functioning of fog domain in sharing files and services over the
network.
1.4 Statement of the Research Problem
For decision making on resource management, it is worth monitoring computing system
resources. Moreover, challenging issues in fog domain are majorly network congestion and
internet bandwidth, resource management challenges, application architecture deployment and
design, mobility and scalability.
2. Literature Review
This section discusses past research literatures and issues with current research studies on
both cloud and fog domain. Furthermore, security issues emanating in computer networks are
key to scrutiny in a broader perspective since network security is a vital concern in the internet.
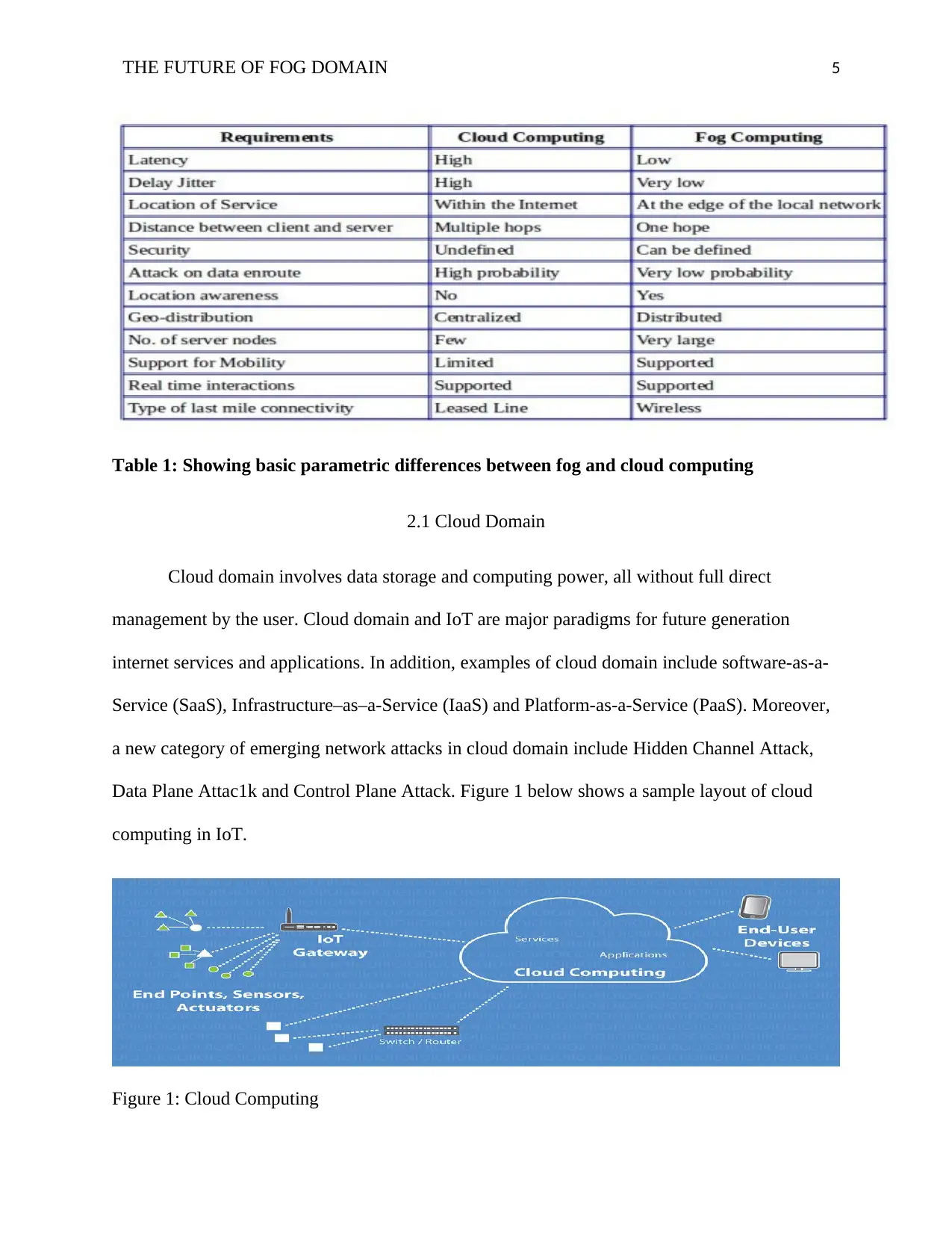
Security issues are therefore discussed in cloud domain as well as in fog domain. Table 1 below
gives an overview of differences in fog and cloud computing based on major parameters.
To not only describe but also evaluate various fog domain applications
1.3 Scope of the Research Study
This research study on fog domain aids in scrutinizing security issues and challenges
surrounding fog domain and also helps in determining preferred solutions for resolving security
issues efficiently to offer smooth functioning of fog domain in sharing files and services over the
network.
1.4 Statement of the Research Problem
For decision making on resource management, it is worth monitoring computing system
resources. Moreover, challenging issues in fog domain are majorly network congestion and
internet bandwidth, resource management challenges, application architecture deployment and
design, mobility and scalability.
2. Literature Review
This section discusses past research literatures and issues with current research studies on
both cloud and fog domain. Furthermore, security issues emanating in computer networks are
key to scrutiny in a broader perspective since network security is a vital concern in the internet.
Security issues are therefore discussed in cloud domain as well as in fog domain. Table 1 below
gives an overview of differences in fog and cloud computing based on major parameters.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
THE FUTURE OF FOG DOMAIN 5
Table 1: Showing basic parametric differences between fog and cloud computing
2.1 Cloud Domain
Cloud domain involves data storage and computing power, all without full direct
management by the user. Cloud domain and IoT are major paradigms for future generation
internet services and applications. In addition, examples of cloud domain include software-as-a-
Service (SaaS), Infrastructure–as–a-Service (IaaS) and Platform-as-a-Service (PaaS). Moreover,
a new category of emerging network attacks in cloud domain include Hidden Channel Attack,
Data Plane Attac1k and Control Plane Attack. Figure 1 below shows a sample layout of cloud
computing in IoT.
Figure 1: Cloud Computing
Table 1: Showing basic parametric differences between fog and cloud computing
2.1 Cloud Domain
Cloud domain involves data storage and computing power, all without full direct
management by the user. Cloud domain and IoT are major paradigms for future generation
internet services and applications. In addition, examples of cloud domain include software-as-a-
Service (SaaS), Infrastructure–as–a-Service (IaaS) and Platform-as-a-Service (PaaS). Moreover,
a new category of emerging network attacks in cloud domain include Hidden Channel Attack,
Data Plane Attac1k and Control Plane Attack. Figure 1 below shows a sample layout of cloud
computing in IoT.
Figure 1: Cloud Computing

THE FUTURE OF FOG DOMAIN 6
2.1.1 Hidden Channel Attack
According to Bazm, Lacoste, Südholt, and Menaud (2017), hidden channel attack refers
to any kind of attack benefiting from side – channel information. Besides, this kind of attack can
either be active or passive. Thus in passive attacks, it is noteworthy that the attacker observes
activities of the target and does not make any changes regarding the target so as to obtain
information. On the other hand, active attacks always change attack environment of target by
obliging the target to execute abnormal operations. In addition, there are three types of hidden
channels namely; CPU – based, time - based ones and cache - based ones. Figure 2 below shows
the CPU – based attack.
Figure 2: Hidden channel Attack
2.1.2 Data Plane Attack
A crafted packet may exploit software vulnerabilities thereby changing operations of
packet processor. For instance, when there is a change in software, an infinite loop can emerge
where same packet can be transmitted repeatedly (Nair & Nair, 2016). Thus such an approach is
damaging as the attack initiates from within the network. Moreover, the incoming packet diverts
control flow of the course and redirects it to malicious code residing inside the payload of the
2.1.1 Hidden Channel Attack
According to Bazm, Lacoste, Südholt, and Menaud (2017), hidden channel attack refers
to any kind of attack benefiting from side – channel information. Besides, this kind of attack can
either be active or passive. Thus in passive attacks, it is noteworthy that the attacker observes
activities of the target and does not make any changes regarding the target so as to obtain
information. On the other hand, active attacks always change attack environment of target by
obliging the target to execute abnormal operations. In addition, there are three types of hidden
channels namely; CPU – based, time - based ones and cache - based ones. Figure 2 below shows
the CPU – based attack.
Figure 2: Hidden channel Attack
2.1.2 Data Plane Attack
A crafted packet may exploit software vulnerabilities thereby changing operations of
packet processor. For instance, when there is a change in software, an infinite loop can emerge
where same packet can be transmitted repeatedly (Nair & Nair, 2016). Thus such an approach is
damaging as the attack initiates from within the network. Moreover, the incoming packet diverts
control flow of the course and redirects it to malicious code residing inside the payload of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

THE FUTURE OF FOG DOMAIN 7
attack packet. The main exploit attack is mostly an integer vulnerability. Some integer arithmetic
operations, based on the conditions, may lead to unexpected outcome. Truncation errors, sign
errors, underflow scan or integer overflows occur, which, if not keenly taken into consideration
before execution of the program, can lead to programs having security flaws and unexpected
behavior. Additionally, it is worth noting that the attack is centered on a vulnerability brought by
overflow of an integer.
2.1.3 Control Plane Attack
Control plane attacks generally are more sophisticated as well as crafty as compared to
DoS attacks against the SDN infrastructure (Zhang et al., 2018). In addition, control plane attack
comprise of two phases namely; probing phase as well as triggering phase. Notably, the probing
phase is where attacker uses test packets, data plane stream as well as timing probing packets in
learning configurations of applications of control plane and their connection to data plane events.
Moreover from information attained from probing phase, attacker is thus capable of crafting the
patterns of attack packet stream patterns. In addition, in the triggering phase, the control plane is
triggered to issue several flow rule update messages within short intervals thus paralyzing
hardware switches.
2.1.4 Malware Injection Attack
This is an attack aiming at introducing a malicious service implementation to the cloud
system (Chouhan & Singh, 2016). Thus such a cloud malware serves any purpose the adversary
intends such as eavesdropping through subtle data modifications and blockings. Moreover, the
adversary creates malicious service implementation module and puts in cloud system then treats
the service as valid service. In addition, on the success of the service, cloud system thus redirects
attack packet. The main exploit attack is mostly an integer vulnerability. Some integer arithmetic
operations, based on the conditions, may lead to unexpected outcome. Truncation errors, sign
errors, underflow scan or integer overflows occur, which, if not keenly taken into consideration
before execution of the program, can lead to programs having security flaws and unexpected
behavior. Additionally, it is worth noting that the attack is centered on a vulnerability brought by
overflow of an integer.
2.1.3 Control Plane Attack
Control plane attacks generally are more sophisticated as well as crafty as compared to
DoS attacks against the SDN infrastructure (Zhang et al., 2018). In addition, control plane attack
comprise of two phases namely; probing phase as well as triggering phase. Notably, the probing
phase is where attacker uses test packets, data plane stream as well as timing probing packets in
learning configurations of applications of control plane and their connection to data plane events.
Moreover from information attained from probing phase, attacker is thus capable of crafting the
patterns of attack packet stream patterns. In addition, in the triggering phase, the control plane is
triggered to issue several flow rule update messages within short intervals thus paralyzing
hardware switches.
2.1.4 Malware Injection Attack
This is an attack aiming at introducing a malicious service implementation to the cloud
system (Chouhan & Singh, 2016). Thus such a cloud malware serves any purpose the adversary
intends such as eavesdropping through subtle data modifications and blockings. Moreover, the
adversary creates malicious service implementation module and puts in cloud system then treats
the service as valid service. In addition, on the success of the service, cloud system thus redirects
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

THE FUTURE OF FOG DOMAIN 8
valid user demands automatically to the malicious service implementations, followed by
execution of adversary’s code.
2.2 Fog Domain
Fog computing is a new model in to the distributed computing paradigms and also refers
to devolved platform for local computation at network edge and also extend very near cloud
capabilities to essential fog nodes. Moreover, fog computing offers same functionalities to cloud
computing to its users, however, fog domain has greater scope and proximity. In addition, the
central idea in fog computing is to bring networking resources closer to nodes that generate data.
Besides, fog platform is highly virtualized and accountable for providing storage, computation,
as well as networking services between traditional clouds and end nodes in IoT environment
(Syed, Fernandez, & Ilyas, 2016)
Figure 3: Fog Domain
valid user demands automatically to the malicious service implementations, followed by
execution of adversary’s code.
2.2 Fog Domain
Fog computing is a new model in to the distributed computing paradigms and also refers
to devolved platform for local computation at network edge and also extend very near cloud
capabilities to essential fog nodes. Moreover, fog computing offers same functionalities to cloud
computing to its users, however, fog domain has greater scope and proximity. In addition, the
central idea in fog computing is to bring networking resources closer to nodes that generate data.
Besides, fog platform is highly virtualized and accountable for providing storage, computation,
as well as networking services between traditional clouds and end nodes in IoT environment
(Syed, Fernandez, & Ilyas, 2016)
Figure 3: Fog Domain

THE FUTURE OF FOG DOMAIN 9
2.2.1 Authentication and Trust Issues
Fog is used as architecture for communication and also as control of network. Moreover,
figure 4 below shows a fog computing architecture in which different instances of devoted fogs
provide resources proximate to IoT environments and underlying fog nodes (Aazam, Zeadally, &
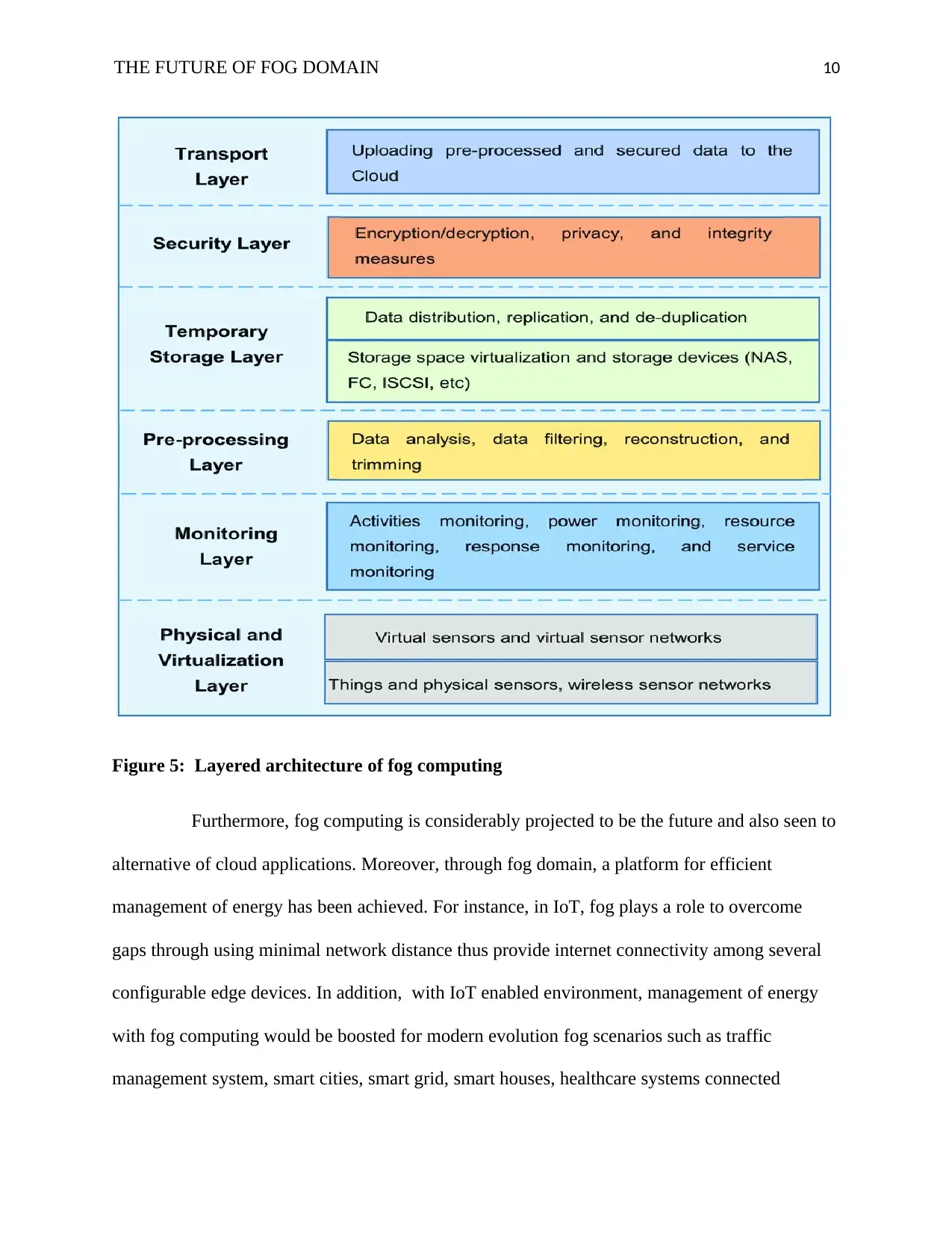
Harras, 2018). On the other hand, figure 5 below shows basic layers of fog architecture. In
addition, the lowest layer is made of physical and virtualization layer, which deals with any item
that connects to internet and also generates data. Also, at the monitoring layer, the next task to be
executed is determined. Additionally, monitoring of nodes are done at the layer for their energy
consumption in order to offload task according to state of the sensor. At the processing layer,
there is data management, data analysis, data filtering and trimming to minimize unnecessary
communication
Figure 4
2.2.1 Authentication and Trust Issues
Fog is used as architecture for communication and also as control of network. Moreover,
figure 4 below shows a fog computing architecture in which different instances of devoted fogs
provide resources proximate to IoT environments and underlying fog nodes (Aazam, Zeadally, &
Harras, 2018). On the other hand, figure 5 below shows basic layers of fog architecture. In
addition, the lowest layer is made of physical and virtualization layer, which deals with any item
that connects to internet and also generates data. Also, at the monitoring layer, the next task to be
executed is determined. Additionally, monitoring of nodes are done at the layer for their energy
consumption in order to offload task according to state of the sensor. At the processing layer,
there is data management, data analysis, data filtering and trimming to minimize unnecessary
communication
Figure 4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
THE FUTURE OF FOG DOMAIN 10
Figure 5: Layered architecture of fog computing
Furthermore, fog computing is considerably projected to be the future and also seen to
alternative of cloud applications. Moreover, through fog domain, a platform for efficient
management of energy has been achieved. For instance, in IoT, fog plays a role to overcome
gaps through using minimal network distance thus provide internet connectivity among several
configurable edge devices. In addition, with IoT enabled environment, management of energy
with fog computing would be boosted for modern evolution fog scenarios such as traffic
management system, smart cities, smart grid, smart houses, healthcare systems connected
Figure 5: Layered architecture of fog computing
Furthermore, fog computing is considerably projected to be the future and also seen to
alternative of cloud applications. Moreover, through fog domain, a platform for efficient
management of energy has been achieved. For instance, in IoT, fog plays a role to overcome
gaps through using minimal network distance thus provide internet connectivity among several
configurable edge devices. In addition, with IoT enabled environment, management of energy
with fog computing would be boosted for modern evolution fog scenarios such as traffic
management system, smart cities, smart grid, smart houses, healthcare systems connected
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

THE FUTURE OF FOG DOMAIN 11
vehicles, wireless sensors and actuator networks (WSANs) . Additionally, intercession of fog
computing offers comforts and reliefs such as adaptability, scalability and interoperability for
end users.
2.2.2 Importance of Fog Domain in IoT
Fog computing has emerged to be a powerful architecture over cloud services in IoT
therefore it has a wide range of importance in IoT Functional analysis. Thus fog distributes
efficiently allocation of functions in IoT networks thereby standardizes and simplifies IoT global
network operation like management and configuration. Secondly, according to Dar and
Ravindran (2019), unlike cloud computing, fog has no network congestion and shows low
latencies hence allowing for real time systems like virtual reality, real time control loops,
artificial intelligence and data streaming analytics. Also, fog networks embed and distribute
communication, computing, control flexibility and storage from cloud to device. This helps in
delivering IoT requirements like computing and storage, thus the distributed architecture ensures
network provision throughout.
Again, fog computing provides immersive distribution that enables flexibility for
management and ease in integration with IoT environments. In addition, fog does this by
interfacing with other fog devices, 5G and IoT and input from users. Finally, fog offers scale
which is also open fog acronym for cognition, security, latency, agility and efficiency.
3. Findings and Recommendations
3.1 Functional Analysis
To begin with, figure 1 shows that fog domain is a vital aspect of IoT environment. Moreover,
the functionalities in fog computing show potential future projection as people would need more
vehicles, wireless sensors and actuator networks (WSANs) . Additionally, intercession of fog
computing offers comforts and reliefs such as adaptability, scalability and interoperability for
end users.
2.2.2 Importance of Fog Domain in IoT
Fog computing has emerged to be a powerful architecture over cloud services in IoT
therefore it has a wide range of importance in IoT Functional analysis. Thus fog distributes
efficiently allocation of functions in IoT networks thereby standardizes and simplifies IoT global
network operation like management and configuration. Secondly, according to Dar and
Ravindran (2019), unlike cloud computing, fog has no network congestion and shows low
latencies hence allowing for real time systems like virtual reality, real time control loops,
artificial intelligence and data streaming analytics. Also, fog networks embed and distribute
communication, computing, control flexibility and storage from cloud to device. This helps in
delivering IoT requirements like computing and storage, thus the distributed architecture ensures
network provision throughout.
Again, fog computing provides immersive distribution that enables flexibility for
management and ease in integration with IoT environments. In addition, fog does this by
interfacing with other fog devices, 5G and IoT and input from users. Finally, fog offers scale
which is also open fog acronym for cognition, security, latency, agility and efficiency.
3. Findings and Recommendations
3.1 Functional Analysis
To begin with, figure 1 shows that fog domain is a vital aspect of IoT environment. Moreover,
the functionalities in fog computing show potential future projection as people would need more

THE FUTURE OF FOG DOMAIN 12
connection to internet with ease. In addition, distance between client and server is one hope
compared to multiple hopes in cloud computing. Also fog applications has been found to be
decentralized to end users compared to cloud domain which is centralized. Decentralization of
fog computing applications enable its users to access more services via internet.
Furthermore, network congestion in cloud computing is a factor causing low latencies
and bandwidth. In addition, portable Wi-Fi routers have been installed at various places
including homes and public spots like home theatres, traffic camera surveillances and
community theatres. Thus to exploit these network devices better, fog platform becomes most
suitable to collaborate with cloud computing to execute full operations. Thus it is worth noting
that fog domain would continue to be efficient platform and ideal for energy consumptions.
Moreover, fog computing platform has been found to be more convenient in Iot
enabled scenarios (Dar & Ravindran, 2019,). For instance, it is smart (cities, connected vehicles,
grids and traffic systems), geographically distributed, acts as transitional layer between edge and
cloud computing. In addition, fog computing has been found to show applications that are
latency bounded in real time sensitivity and also from various benefits it serves, is projected to
be the future alternative. Besides, figure 1 shows how cloud connects end users and other devices
as IoT through internet. In addition, figure 2 elaborates how hidden channel attack occurs in
cloud computing.
On the other hand, figure 3 shows on how fog computing domain helps connect
devices in IoT. Fog connects to IoT devices via fog nodes. Consequently, figure 4 shows layered
architecture of fog computing. Moreover, there are six layers of the architecture possessing
various functions with the lowest layer being physical and virtualization layer where sensor
networks do connections. At the monitory layer; power, resource, response and service
connection to internet with ease. In addition, distance between client and server is one hope
compared to multiple hopes in cloud computing. Also fog applications has been found to be
decentralized to end users compared to cloud domain which is centralized. Decentralization of
fog computing applications enable its users to access more services via internet.
Furthermore, network congestion in cloud computing is a factor causing low latencies
and bandwidth. In addition, portable Wi-Fi routers have been installed at various places
including homes and public spots like home theatres, traffic camera surveillances and
community theatres. Thus to exploit these network devices better, fog platform becomes most
suitable to collaborate with cloud computing to execute full operations. Thus it is worth noting
that fog domain would continue to be efficient platform and ideal for energy consumptions.
Moreover, fog computing platform has been found to be more convenient in Iot
enabled scenarios (Dar & Ravindran, 2019,). For instance, it is smart (cities, connected vehicles,
grids and traffic systems), geographically distributed, acts as transitional layer between edge and
cloud computing. In addition, fog computing has been found to show applications that are
latency bounded in real time sensitivity and also from various benefits it serves, is projected to
be the future alternative. Besides, figure 1 shows how cloud connects end users and other devices
as IoT through internet. In addition, figure 2 elaborates how hidden channel attack occurs in
cloud computing.
On the other hand, figure 3 shows on how fog computing domain helps connect
devices in IoT. Fog connects to IoT devices via fog nodes. Consequently, figure 4 shows layered
architecture of fog computing. Moreover, there are six layers of the architecture possessing
various functions with the lowest layer being physical and virtualization layer where sensor
networks do connections. At the monitory layer; power, resource, response and service
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




