Internet of Things Report: Analysis of Key IoT Concepts and Laws
VerifiedAdded on 2020/02/19
|10
|2299
|196
Report
AI Summary
This report provides a comprehensive overview of the Internet of Things (IoT), examining various facets of its architecture and implications. It begins by discussing the evolution of user interfaces, highlighting the shift towards no-interface interactions and providing examples like automated payment systems and keyless car entry. The report then delves into the different types of cables used for wide network communication, comparing twisted pair, coaxial, and optical fiber cables across various characteristics such as bandwidth, cost, security, and noise interference. Furthermore, it contrasts Radio Frequency Identification (RFID), sensors, and video tracking technologies, outlining their advantages, disadvantages, and key applications. The report also addresses security threats within the IoT, categorizing deliberate and accidental vulnerabilities and suggesting mitigation strategies. An analysis of application trigger time and propagation delay is presented to optimize application design. Finally, the report discusses Nielsen's Law and its relevance to IoT, comparing it to Moore's Law and emphasizing the importance of efficient bandwidth usage in web design. The report is well-referenced with multiple sources.

Running head: INTERNET OF THINGS
Internet of Things
Name of the Student
Name of the University
Author’s notes
Internet of Things
Name of the Student
Name of the University
Author’s notes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNET OF THINGS
Table of Contents
Answer 1..............................................................................................................................2
Answer 2..............................................................................................................................3
Answer 3..............................................................................................................................5
Answer 4..............................................................................................................................6
Answer 5..............................................................................................................................6
Answer 6..............................................................................................................................7
References............................................................................................................................9
INTERNET OF THINGS
Table of Contents
Answer 1..............................................................................................................................2
Answer 2..............................................................................................................................3
Answer 3..............................................................................................................................5
Answer 4..............................................................................................................................6
Answer 5..............................................................................................................................6
Answer 6..............................................................................................................................7
References............................................................................................................................9

2
INTERNET OF THINGS
Answer 1
User interface is a design that takes the help of information technology to enable the
interaction between a user and computer. Any user can communicate and use any applications
and websites because of the presence of the user interface. Recent studies have shown that users
prefer the use of no interface. They prefer to interact in a natural way rather than through any
device. Information technology has starting incorporating the use of no interface by introducing
the voice user interface. This can be considered to be the first or initial step towards the no user
graphical interface (Singh, Tripathi & Jara, 2014). People are not much comfortable in using the
graphical user interfaces. The use of no user interface will make the lives of the people easier.
Two examples where this no user interface can be applied are given as follows:
Automatic procedure of payment: Whenever a customer enters a store he/she has to take
several steps before paying the bill amount. This hectic and chaotic procedure can be mitigated
by automating the procedure for payment. By incorporating a RFID chip in the payment cards of
the user. This will enable the customers to enter the store and leave the store without any exit
queues. The procedure has been made simple by an app known as the Pay with Square app. This
app has helped the customers to buy and leave the store without facing any problem.
Automatic procedure of unlocking car: When a person wants to drive a car then he or she
has to walk up to the car, take out the keys from the bag and then unlock the car. This approach
is a time consuming method. The no user interface approach can be used in order to simplify the
entire process. The drivers can just simply walk to the car and open the door. In the year 1991,
this keyless strategy was applied by Mercedes-Benz. This helped the car users to save time and
energy.
INTERNET OF THINGS
Answer 1
User interface is a design that takes the help of information technology to enable the
interaction between a user and computer. Any user can communicate and use any applications
and websites because of the presence of the user interface. Recent studies have shown that users
prefer the use of no interface. They prefer to interact in a natural way rather than through any
device. Information technology has starting incorporating the use of no interface by introducing
the voice user interface. This can be considered to be the first or initial step towards the no user
graphical interface (Singh, Tripathi & Jara, 2014). People are not much comfortable in using the
graphical user interfaces. The use of no user interface will make the lives of the people easier.
Two examples where this no user interface can be applied are given as follows:
Automatic procedure of payment: Whenever a customer enters a store he/she has to take
several steps before paying the bill amount. This hectic and chaotic procedure can be mitigated
by automating the procedure for payment. By incorporating a RFID chip in the payment cards of
the user. This will enable the customers to enter the store and leave the store without any exit
queues. The procedure has been made simple by an app known as the Pay with Square app. This
app has helped the customers to buy and leave the store without facing any problem.
Automatic procedure of unlocking car: When a person wants to drive a car then he or she
has to walk up to the car, take out the keys from the bag and then unlock the car. This approach
is a time consuming method. The no user interface approach can be used in order to simplify the
entire process. The drivers can just simply walk to the car and open the door. In the year 1991,
this keyless strategy was applied by Mercedes-Benz. This helped the car users to save time and
energy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTERNET OF THINGS
Answer 2
There are several types of cables present that are used for the purpose of communicating
over wide network. These cables are classified into twisted pair cables, optical fibers and coaxial
cables. These three cables have different characteristics that can be compared. The table
presented in this answer gives a clear overview of the different characteristics of the twisted pair,
optical fibers and coaxial cables.
Characteristics Twisted Pair Cable Coaxial Cable Optical Fiber
Bandwidth In comparison to the
other two cables, this
cable has the least
bandwidth.
In comparison to the
other two cables, this has
a level of bandwidth that
is medium.
In comparison to the
other two cables, this has
the highest level of
bandwidth.
Cost In comparison to the
other two cables, this has
the lowest cost.
In comparison to the
other two cables, it has a
moderate level of cost.
In comparison to the
other two cables, optical
fibers have got the
highest cost. It is very
expensive.
Security In comparison to the
other two cables, the
security factor is very
low.
In comparison to the
other two cables, it
provides medium
security.
In comparison to the
other two cables, the
security level provided
by this cable is the
highest.
Noise interference This is very high over
here.
This is extremely low. Its immunity towards
interference is high.
Noise cannot create any
interference in case of
INTERNET OF THINGS
Answer 2
There are several types of cables present that are used for the purpose of communicating
over wide network. These cables are classified into twisted pair cables, optical fibers and coaxial
cables. These three cables have different characteristics that can be compared. The table
presented in this answer gives a clear overview of the different characteristics of the twisted pair,
optical fibers and coaxial cables.
Characteristics Twisted Pair Cable Coaxial Cable Optical Fiber
Bandwidth In comparison to the
other two cables, this
cable has the least
bandwidth.
In comparison to the
other two cables, this has
a level of bandwidth that
is medium.
In comparison to the
other two cables, this has
the highest level of
bandwidth.
Cost In comparison to the
other two cables, this has
the lowest cost.
In comparison to the
other two cables, it has a
moderate level of cost.
In comparison to the
other two cables, optical
fibers have got the
highest cost. It is very
expensive.
Security In comparison to the
other two cables, the
security factor is very
low.
In comparison to the
other two cables, it
provides medium
security.
In comparison to the
other two cables, the
security level provided
by this cable is the
highest.
Noise interference This is very high over
here.
This is extremely low. Its immunity towards
interference is high.
Noise cannot create any
interference in case of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INTERNET OF THINGS
optical fibers and light
waves.
Distance The distance covered is 0
to 3.5 kHz.
The distance covered is
0 to 500 MHz.
The distance covered is
180 to 370 THz.
Table 1: Comparison between Twisted Pair, Coaxial and Optical Fiber Cable
(Source: Boyer & Heffron, 2015)
Three types of Optical Fibers are:
Single Mode: This type of optical fibers can transmit in a single mode and consists of a
single stand. The diameter of the single mode fiber is 10 microns (Winzer, 2014).
Multi Mode: The optical fibers falling under this category is can transmit in more than a
single mode. It has a very big diameter that is more than 50 and less than 100 microns.
Plastic Optic Fiber: This category is made of polymers having a refractive index of 1.46
or less.
Three types of Coaxial Cables are:
RG-9/U: It has 51 ohms of impedance. Its type is PE.
RG-11/U: It has 75 ohms of impedance. It is used for the purpose of long drops.
RG-56/U: It has 48 ohms of impedance. It is dielectric.
Three types of Twisted Pair Cables are:
Individual Shield: The shielding is done with aluminum foil for individual shielding.
INTERNET OF THINGS
optical fibers and light
waves.
Distance The distance covered is 0
to 3.5 kHz.
The distance covered is
0 to 500 MHz.
The distance covered is
180 to 370 THz.
Table 1: Comparison between Twisted Pair, Coaxial and Optical Fiber Cable
(Source: Boyer & Heffron, 2015)
Three types of Optical Fibers are:
Single Mode: This type of optical fibers can transmit in a single mode and consists of a
single stand. The diameter of the single mode fiber is 10 microns (Winzer, 2014).
Multi Mode: The optical fibers falling under this category is can transmit in more than a
single mode. It has a very big diameter that is more than 50 and less than 100 microns.
Plastic Optic Fiber: This category is made of polymers having a refractive index of 1.46
or less.
Three types of Coaxial Cables are:
RG-9/U: It has 51 ohms of impedance. Its type is PE.
RG-11/U: It has 75 ohms of impedance. It is used for the purpose of long drops.
RG-56/U: It has 48 ohms of impedance. It is dielectric.
Three types of Twisted Pair Cables are:
Individual Shield: The shielding is done with aluminum foil for individual shielding.
5
INTERNET OF THINGS
Overall Shield: 100 ohms impedance twisted pair cable is used. This helps in preventing
the EMI from entering the cable.
Individual and overall shield: The inner foil is shielded individually and the outer foil has
done braided shielding.
Answer 3
Radio Frequency Identification, video tracking and sensors have different characteristics
and applications that can be compared. The comparison is shown below.
Characteristics RFID Sensors Video Tracking
Advantage Human intervention is not
required during tag
detection. This reduces
the cost of employment
(Zhu, Mukhopadhyay &
Kurata, 2012).
The price required for
implementation is low
(Bao & Chen, 2012).
There is no requirement
for heavy wiring.
The recorded data gives
the exact information.
Disadvantage Any defects can affect the
working mechanism of
the entire system. It
requires standardization.
This is less secure and it
has slow speed (Tozlu et
al., 2012).
Noise interference can
cause disturbance and it
is costly (Wang et al.,
2015).
Key Requirement Unique identification and
automatic identification.
Safety requirements Proper monitoring is
required.
Application Shopping stores and
logistics.
Traffic monitoring and
tracking objects.
CCTV surveillance and
health surveillance.
INTERNET OF THINGS
Overall Shield: 100 ohms impedance twisted pair cable is used. This helps in preventing
the EMI from entering the cable.
Individual and overall shield: The inner foil is shielded individually and the outer foil has
done braided shielding.
Answer 3
Radio Frequency Identification, video tracking and sensors have different characteristics
and applications that can be compared. The comparison is shown below.
Characteristics RFID Sensors Video Tracking
Advantage Human intervention is not
required during tag
detection. This reduces
the cost of employment
(Zhu, Mukhopadhyay &
Kurata, 2012).
The price required for
implementation is low
(Bao & Chen, 2012).
There is no requirement
for heavy wiring.
The recorded data gives
the exact information.
Disadvantage Any defects can affect the
working mechanism of
the entire system. It
requires standardization.
This is less secure and it
has slow speed (Tozlu et
al., 2012).
Noise interference can
cause disturbance and it
is costly (Wang et al.,
2015).
Key Requirement Unique identification and
automatic identification.
Safety requirements Proper monitoring is
required.
Application Shopping stores and
logistics.
Traffic monitoring and
tracking objects.
CCTV surveillance and
health surveillance.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INTERNET OF THINGS
Table 2: Comparison between RFID, Sensors and Video Tracking
(Source: Takai et al., 2013)
Answer 4
The information and communication technology has become an integral part of the lives
of the people. It makes the use of internet on a regular and consistent basis. Internet is
susceptible to various types of security threats. There can be deliberate and accidental security
threats in the system. Deliberate threats have huge exposure of risk because the attackers have a
motive behind it. Accidental threats are not much harmful as it can be rectified after
identification. There are can be several reasons behind the deliberate attacks (Borgohain, Kumar
& Sanyal, 2015). There can be loss of sensitive data and also there can be loss of money. If a
credit card gets hacked then the hacker can misuse the money of the user in a wrong way.
Several types of threats are hacking, denial of services, spoofing, and sniffing and virus attacks.
There can be modification of the information too. Loss of intellectual property can also take
place because of the security threats (Suo et al., 2012). In case of denial of service attack the
attacker keeps the server busy in different type of activities and utilizes the capacity of the
server. This makes the server slow and they cannot do the required task later on. These
vulnerabilities can be resolved by applying strong security policies in the system.
Answer 5
The following information is given in the question:
Application trigger time= 1s
Propagation delay in round trip between application and sensor= 12ms
INTERNET OF THINGS
Table 2: Comparison between RFID, Sensors and Video Tracking
(Source: Takai et al., 2013)
Answer 4
The information and communication technology has become an integral part of the lives
of the people. It makes the use of internet on a regular and consistent basis. Internet is
susceptible to various types of security threats. There can be deliberate and accidental security
threats in the system. Deliberate threats have huge exposure of risk because the attackers have a
motive behind it. Accidental threats are not much harmful as it can be rectified after
identification. There are can be several reasons behind the deliberate attacks (Borgohain, Kumar
& Sanyal, 2015). There can be loss of sensitive data and also there can be loss of money. If a
credit card gets hacked then the hacker can misuse the money of the user in a wrong way.
Several types of threats are hacking, denial of services, spoofing, and sniffing and virus attacks.
There can be modification of the information too. Loss of intellectual property can also take
place because of the security threats (Suo et al., 2012). In case of denial of service attack the
attacker keeps the server busy in different type of activities and utilizes the capacity of the
server. This makes the server slow and they cannot do the required task later on. These
vulnerabilities can be resolved by applying strong security policies in the system.
Answer 5
The following information is given in the question:
Application trigger time= 1s
Propagation delay in round trip between application and sensor= 12ms
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INTERNET OF THINGS
Average time consumed for processing request=3 ms
Time taken in receiving and sending messages= 2 ms
Therefore, total time consumed= 1+12+3+2= 18 ms
This application design would save 18 ms and it is much better than the existing system.
Answer 6
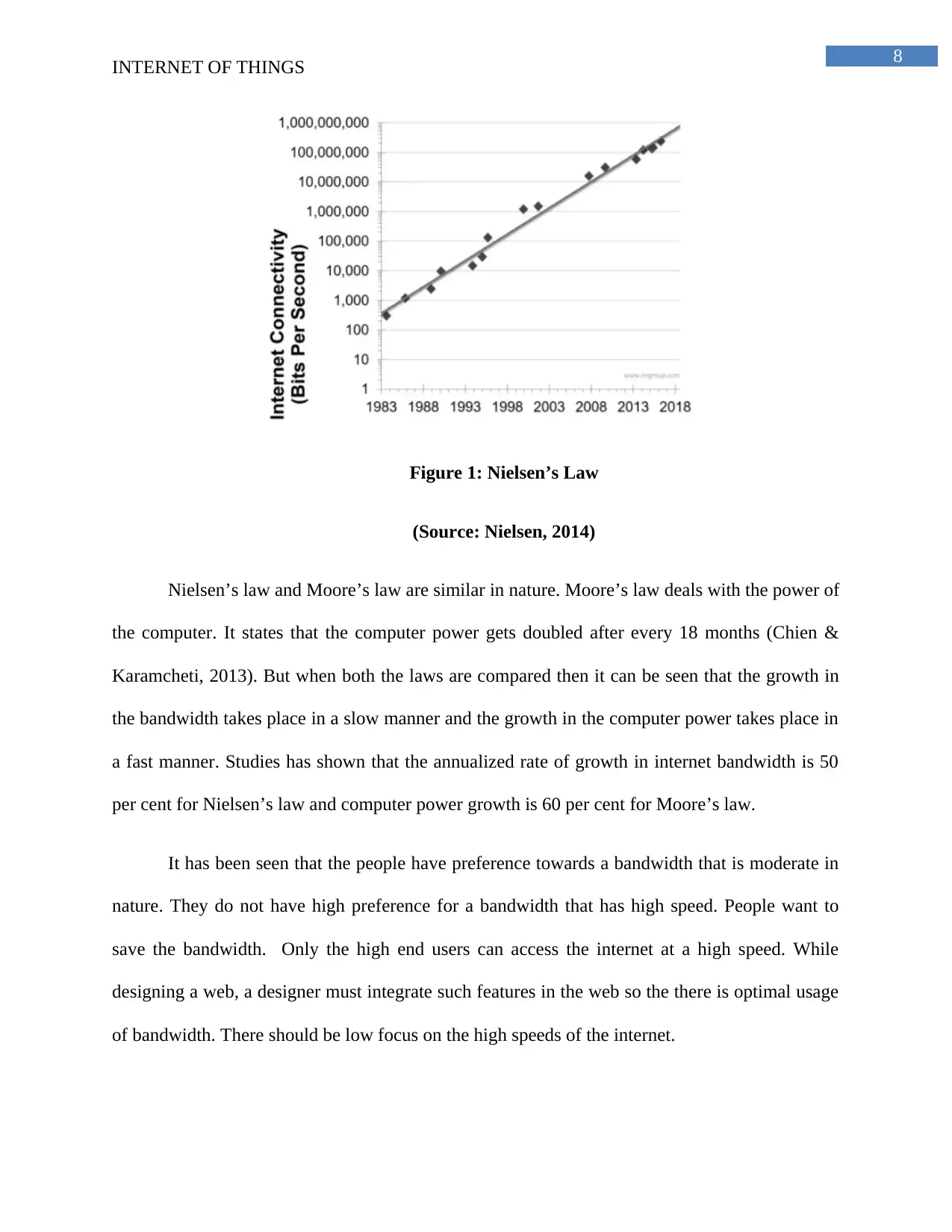
Nielsen’s law plays a major role in the internet of things. This law is applicable for the
purpose of finding out the speed. Nielsen’s law states that the connection speed increases by 50
per cent every year (Nielsen, 2014). This is applicable in the case of high end users only. In order
to prove the law, a graph is presented in this answer. The graph clearly shows that the internet
speed of connection is increasing. The graph shows the speed details from year 1984 to the year
2014. There is an exponential growth in the connection speed of the high end users that is shown
by the straight line. The X axis of the graph shows the year and the Y axis shows the internet
connectivity in bits per second. Straight line is the sign of exponential growth. Hence this law
can be easily proved.
INTERNET OF THINGS
Average time consumed for processing request=3 ms
Time taken in receiving and sending messages= 2 ms
Therefore, total time consumed= 1+12+3+2= 18 ms
This application design would save 18 ms and it is much better than the existing system.
Answer 6
Nielsen’s law plays a major role in the internet of things. This law is applicable for the
purpose of finding out the speed. Nielsen’s law states that the connection speed increases by 50
per cent every year (Nielsen, 2014). This is applicable in the case of high end users only. In order
to prove the law, a graph is presented in this answer. The graph clearly shows that the internet
speed of connection is increasing. The graph shows the speed details from year 1984 to the year
2014. There is an exponential growth in the connection speed of the high end users that is shown
by the straight line. The X axis of the graph shows the year and the Y axis shows the internet
connectivity in bits per second. Straight line is the sign of exponential growth. Hence this law
can be easily proved.
8
INTERNET OF THINGS
Figure 1: Nielsen’s Law
(Source: Nielsen, 2014)
Nielsen’s law and Moore’s law are similar in nature. Moore’s law deals with the power of
the computer. It states that the computer power gets doubled after every 18 months (Chien &
Karamcheti, 2013). But when both the laws are compared then it can be seen that the growth in
the bandwidth takes place in a slow manner and the growth in the computer power takes place in
a fast manner. Studies has shown that the annualized rate of growth in internet bandwidth is 50
per cent for Nielsen’s law and computer power growth is 60 per cent for Moore’s law.
It has been seen that the people have preference towards a bandwidth that is moderate in
nature. They do not have high preference for a bandwidth that has high speed. People want to
save the bandwidth. Only the high end users can access the internet at a high speed. While
designing a web, a designer must integrate such features in the web so the there is optimal usage
of bandwidth. There should be low focus on the high speeds of the internet.
INTERNET OF THINGS
Figure 1: Nielsen’s Law
(Source: Nielsen, 2014)
Nielsen’s law and Moore’s law are similar in nature. Moore’s law deals with the power of
the computer. It states that the computer power gets doubled after every 18 months (Chien &
Karamcheti, 2013). But when both the laws are compared then it can be seen that the growth in
the bandwidth takes place in a slow manner and the growth in the computer power takes place in
a fast manner. Studies has shown that the annualized rate of growth in internet bandwidth is 50
per cent for Nielsen’s law and computer power growth is 60 per cent for Moore’s law.
It has been seen that the people have preference towards a bandwidth that is moderate in
nature. They do not have high preference for a bandwidth that has high speed. People want to
save the bandwidth. Only the high end users can access the internet at a high speed. While
designing a web, a designer must integrate such features in the web so the there is optimal usage
of bandwidth. There should be low focus on the high speeds of the internet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INTERNET OF THINGS
References
Bao, X., & Chen, L. (2012). Recent progress in distributed fiber optic sensors. Sensors, 12(7),
8601-8639.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of
Internet of Things. arXiv preprint arXiv:1501.02211.
Boyer, R. J., & Heffron, J. F. (2015). U.S. Patent Application No. 14/775,870.
Chien, A. A., & Karamcheti, V. (2013). Moore's law: The first ending and a new
beginning. Computer, 46(12), 48-53.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE
world forum on (pp. 287-292). IEEE.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international
conference on (Vol. 3, pp. 648-651). IEEE.
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet
of things: A practical approach. IEEE Communications Magazine, 50(6).
INTERNET OF THINGS
References
Bao, X., & Chen, L. (2012). Recent progress in distributed fiber optic sensors. Sensors, 12(7),
8601-8639.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of
Internet of Things. arXiv preprint arXiv:1501.02211.
Boyer, R. J., & Heffron, J. F. (2015). U.S. Patent Application No. 14/775,870.
Chien, A. A., & Karamcheti, V. (2013). Moore's law: The first ending and a new
beginning. Computer, 46(12), 48-53.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE
world forum on (pp. 287-292). IEEE.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international
conference on (Vol. 3, pp. 648-651). IEEE.
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet
of things: A practical approach. IEEE Communications Magazine, 50(6).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





