Internet of Things and Its Growth
VerifiedAdded on 2020/02/24
|11
|2533
|333
AI Summary
This assignment delves into the concept of the Internet of Things (IoT) and analyzes the factors driving its growth. It highlights the contrasting perspectives of Moore's Law and Nielsen's Law, arguing that Moore's Law, which predicts exponential growth in computing power, better reflects the trajectory of IoT development compared to Nielsen's Law, which focuses on data transfer rates. The assignment further emphasizes the implications of this rapid growth for various sectors.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Internet of Things
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Q1. What does the statement “the best interface for a system is no User interface”? When
might this apply and provide examples......................................................................................3
Q2. Compare the bandwidth, distance, interference rating, cost and security of a) twisted pair
cable, b. coaxial cable and c) fibre optic cable. Use current data, given specific details for at
least 3 types of cable within each category, these should have different specifications, rather
than simply different brand of same type.................................................................................3
Q3. The three common ways to obtain information from IOT devices are sensors, RFID, and
video tracking. Compare three technologies by addressing the advantages, disadvantages, key
requirements for the things. Provide two applications of each................................................5
Q4. Discuss the issues associated with security and privacy of the IoT..................................6
Q5. An IoT water level monitoring application requires updates from a sensor periodically,
using the command/response paradigm. The application triggers a request every 1s. The
round-trip propagation delay between the application and the sensor is 12ms. On average,
the sensor consumes 3ms to process each request. The application consumes 2ms to send or
receive any message. If the application blocks on every request to the sensor, how much of
its time budget can be saved by redesigning the application to use the publish
communication model in the lieu of the command approach?...................................................7
Q6. Describe Nielsen's Law. How does it relate to Moore’s law? What are the Implications
for the IoT?.................................................................................................................................9
Reference List..........................................................................................................................11
2
Q1. What does the statement “the best interface for a system is no User interface”? When
might this apply and provide examples......................................................................................3
Q2. Compare the bandwidth, distance, interference rating, cost and security of a) twisted pair
cable, b. coaxial cable and c) fibre optic cable. Use current data, given specific details for at
least 3 types of cable within each category, these should have different specifications, rather
than simply different brand of same type.................................................................................3
Q3. The three common ways to obtain information from IOT devices are sensors, RFID, and
video tracking. Compare three technologies by addressing the advantages, disadvantages, key
requirements for the things. Provide two applications of each................................................5
Q4. Discuss the issues associated with security and privacy of the IoT..................................6
Q5. An IoT water level monitoring application requires updates from a sensor periodically,
using the command/response paradigm. The application triggers a request every 1s. The
round-trip propagation delay between the application and the sensor is 12ms. On average,
the sensor consumes 3ms to process each request. The application consumes 2ms to send or
receive any message. If the application blocks on every request to the sensor, how much of
its time budget can be saved by redesigning the application to use the publish
communication model in the lieu of the command approach?...................................................7
Q6. Describe Nielsen's Law. How does it relate to Moore’s law? What are the Implications
for the IoT?.................................................................................................................................9
Reference List..........................................................................................................................11
2

Q1. What does the statement “the best interface for a system is no User interface”?
When might this apply and provide examples
The term No User Interface or Zero UI refers to the feature that enables users to have a
screen-less experience with their devices. According to (), it can be considered as a great
interface design that can make a device more user friendly by which people can complete
their tasks more efficiently. Nowadays, people have become more app-obsessed and they
always try to use best tools for their jobs. No one wants to go back to the age of flip-phone,
everyone needs a smart phone to get immediate solution for their job-related problems
(Kumar, Stecher & Tamura 2016, p.1870).
For example: In this context, it can be stated that, the automobile engineers can use this zero
UI concept in solving the transportation problems. With the help of the technological
progress the engineers can make a touch-screen central control that helps the driver to look at
their way while driving. Another application of this screen-based thinking can be the app, by
which people can get relief from swiping their smart phones (Al-Fuqaha, et. al., 2015). As
Apple has launched a new app through which people can speak can speak to their screens for
clicking a selfie or calling someone. This app may help the users to access the things more
easily that they care about.
Q2. Compare the bandwidth, distance, interference rating, cost and security of a)
twisted pair cable, b. coaxial cable and c) fibre optic cable. Use current data, given
specific details for at least 3 types of cable within each category, these should have
different specifications, rather than simply different brand of same type
Topics Twisted pair cable Coaxial cable Fibre optic cable
Bandwidth 0.4 MHz 6Mhz 100 petabit/km/s
Distance 300 ft 500m (1640.4 feet) 100 Mbit/s
Interference Rating Shielded and
Unshielded
Shielded Electrical feild
3
When might this apply and provide examples
The term No User Interface or Zero UI refers to the feature that enables users to have a
screen-less experience with their devices. According to (), it can be considered as a great
interface design that can make a device more user friendly by which people can complete
their tasks more efficiently. Nowadays, people have become more app-obsessed and they
always try to use best tools for their jobs. No one wants to go back to the age of flip-phone,
everyone needs a smart phone to get immediate solution for their job-related problems
(Kumar, Stecher & Tamura 2016, p.1870).
For example: In this context, it can be stated that, the automobile engineers can use this zero
UI concept in solving the transportation problems. With the help of the technological
progress the engineers can make a touch-screen central control that helps the driver to look at
their way while driving. Another application of this screen-based thinking can be the app, by
which people can get relief from swiping their smart phones (Al-Fuqaha, et. al., 2015). As
Apple has launched a new app through which people can speak can speak to their screens for
clicking a selfie or calling someone. This app may help the users to access the things more
easily that they care about.
Q2. Compare the bandwidth, distance, interference rating, cost and security of a)
twisted pair cable, b. coaxial cable and c) fibre optic cable. Use current data, given
specific details for at least 3 types of cable within each category, these should have
different specifications, rather than simply different brand of same type
Topics Twisted pair cable Coaxial cable Fibre optic cable
Bandwidth 0.4 MHz 6Mhz 100 petabit/km/s
Distance 300 ft 500m (1640.4 feet) 100 Mbit/s
Interference Rating Shielded and
Unshielded
Shielded Electrical feild
3
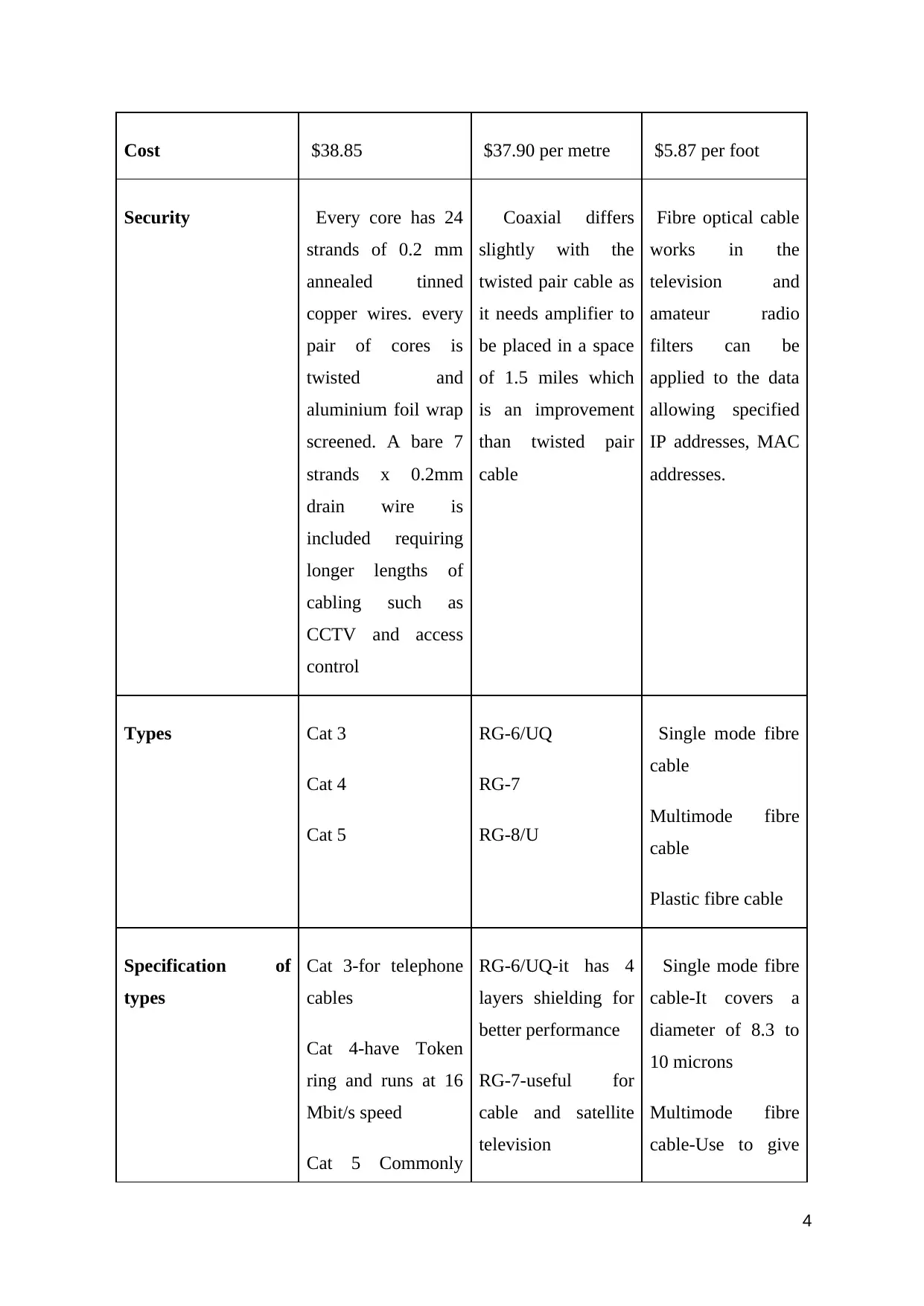
Cost $38.85 $37.90 per metre $5.87 per foot
Security Every core has 24
strands of 0.2 mm
annealed tinned
copper wires. every
pair of cores is
twisted and
aluminium foil wrap
screened. A bare 7
strands x 0.2mm
drain wire is
included requiring
longer lengths of
cabling such as
CCTV and access
control
Coaxial differs
slightly with the
twisted pair cable as
it needs amplifier to
be placed in a space
of 1.5 miles which
is an improvement
than twisted pair
cable
Fibre optical cable
works in the
television and
amateur radio
filters can be
applied to the data
allowing specified
IP addresses, MAC
addresses.
Types Cat 3
Cat 4
Cat 5
RG-6/UQ
RG-7
RG-8/U
Single mode fibre
cable
Multimode fibre
cable
Plastic fibre cable
Specification of
types
Cat 3-for telephone
cables
Cat 4-have Token
ring and runs at 16
Mbit/s speed
Cat 5 Commonly
RG-6/UQ-it has 4
layers shielding for
better performance
RG-7-useful for
cable and satellite
television
Single mode fibre
cable-It covers a
diameter of 8.3 to
10 microns
Multimode fibre
cable-Use to give
4
Security Every core has 24
strands of 0.2 mm
annealed tinned
copper wires. every
pair of cores is
twisted and
aluminium foil wrap
screened. A bare 7
strands x 0.2mm
drain wire is
included requiring
longer lengths of
cabling such as
CCTV and access
control
Coaxial differs
slightly with the
twisted pair cable as
it needs amplifier to
be placed in a space
of 1.5 miles which
is an improvement
than twisted pair
cable
Fibre optical cable
works in the
television and
amateur radio
filters can be
applied to the data
allowing specified
IP addresses, MAC
addresses.
Types Cat 3
Cat 4
Cat 5
RG-6/UQ
RG-7
RG-8/U
Single mode fibre
cable
Multimode fibre
cable
Plastic fibre cable
Specification of
types
Cat 3-for telephone
cables
Cat 4-have Token
ring and runs at 16
Mbit/s speed
Cat 5 Commonly
RG-6/UQ-it has 4
layers shielding for
better performance
RG-7-useful for
cable and satellite
television
Single mode fibre
cable-It covers a
diameter of 8.3 to
10 microns
Multimode fibre
cable-Use to give
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
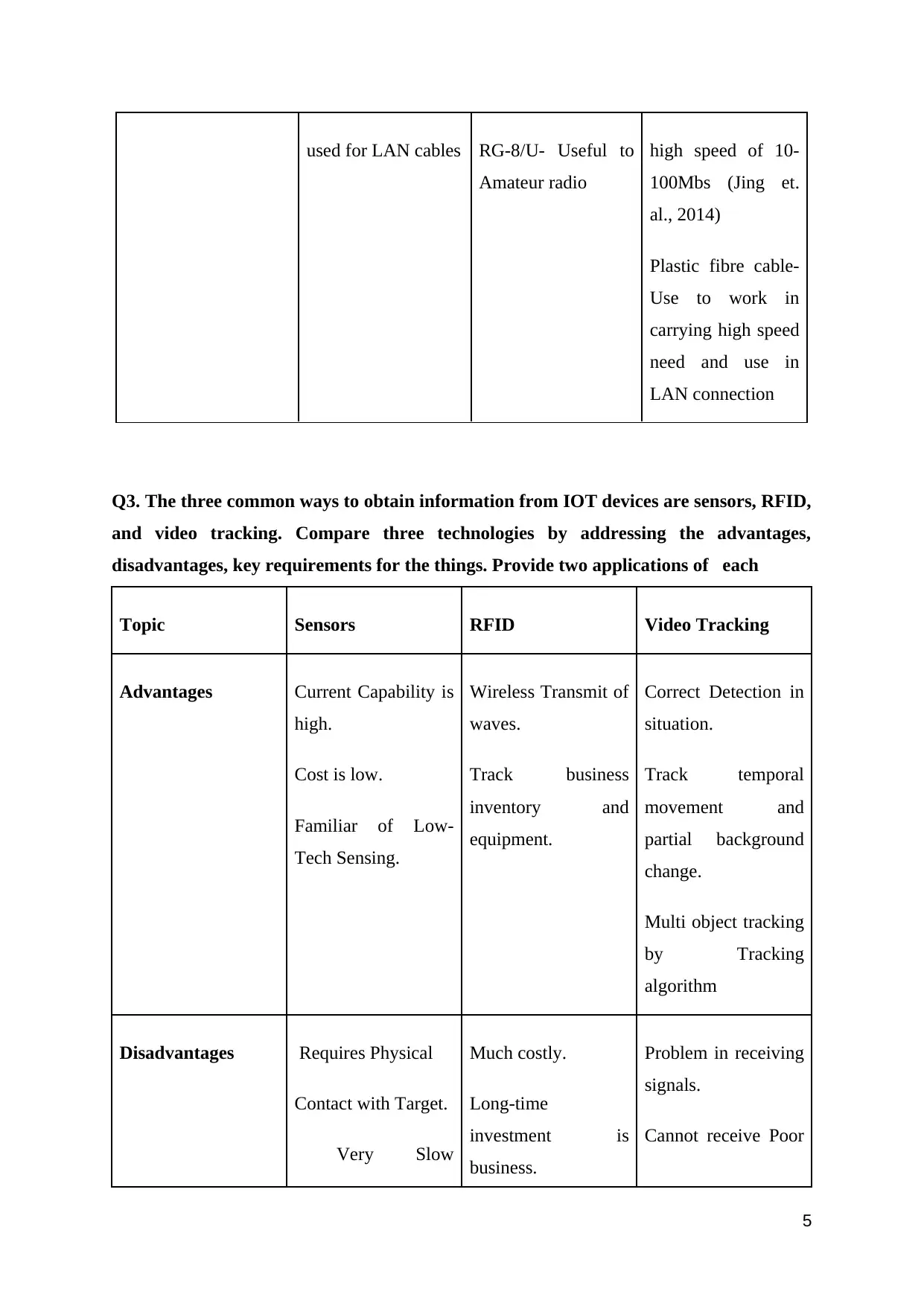
used for LAN cables RG-8/U- Useful to
Amateur radio
high speed of 10-
100Mbs (Jing et.
al., 2014)
Plastic fibre cable-
Use to work in
carrying high speed
need and use in
LAN connection
Q3. The three common ways to obtain information from IOT devices are sensors, RFID,
and video tracking. Compare three technologies by addressing the advantages,
disadvantages, key requirements for the things. Provide two applications of each
Topic Sensors RFID Video Tracking
Advantages Current Capability is
high.
Cost is low.
Familiar of Low-
Tech Sensing.
Wireless Transmit of
waves.
Track business
inventory and
equipment.
Correct Detection in
situation.
Track temporal
movement and
partial background
change.
Multi object tracking
by Tracking
algorithm
Disadvantages Requires Physical
Contact with Target.
Very Slow
Much costly.
Long-time
investment is
business.
Problem in receiving
signals.
Cannot receive Poor
5
Amateur radio
high speed of 10-
100Mbs (Jing et.
al., 2014)
Plastic fibre cable-
Use to work in
carrying high speed
need and use in
LAN connection
Q3. The three common ways to obtain information from IOT devices are sensors, RFID,
and video tracking. Compare three technologies by addressing the advantages,
disadvantages, key requirements for the things. Provide two applications of each
Topic Sensors RFID Video Tracking
Advantages Current Capability is
high.
Cost is low.
Familiar of Low-
Tech Sensing.
Wireless Transmit of
waves.
Track business
inventory and
equipment.
Correct Detection in
situation.
Track temporal
movement and
partial background
change.
Multi object tracking
by Tracking
algorithm
Disadvantages Requires Physical
Contact with Target.
Very Slow
Much costly.
Long-time
investment is
business.
Problem in receiving
signals.
Cannot receive Poor
5
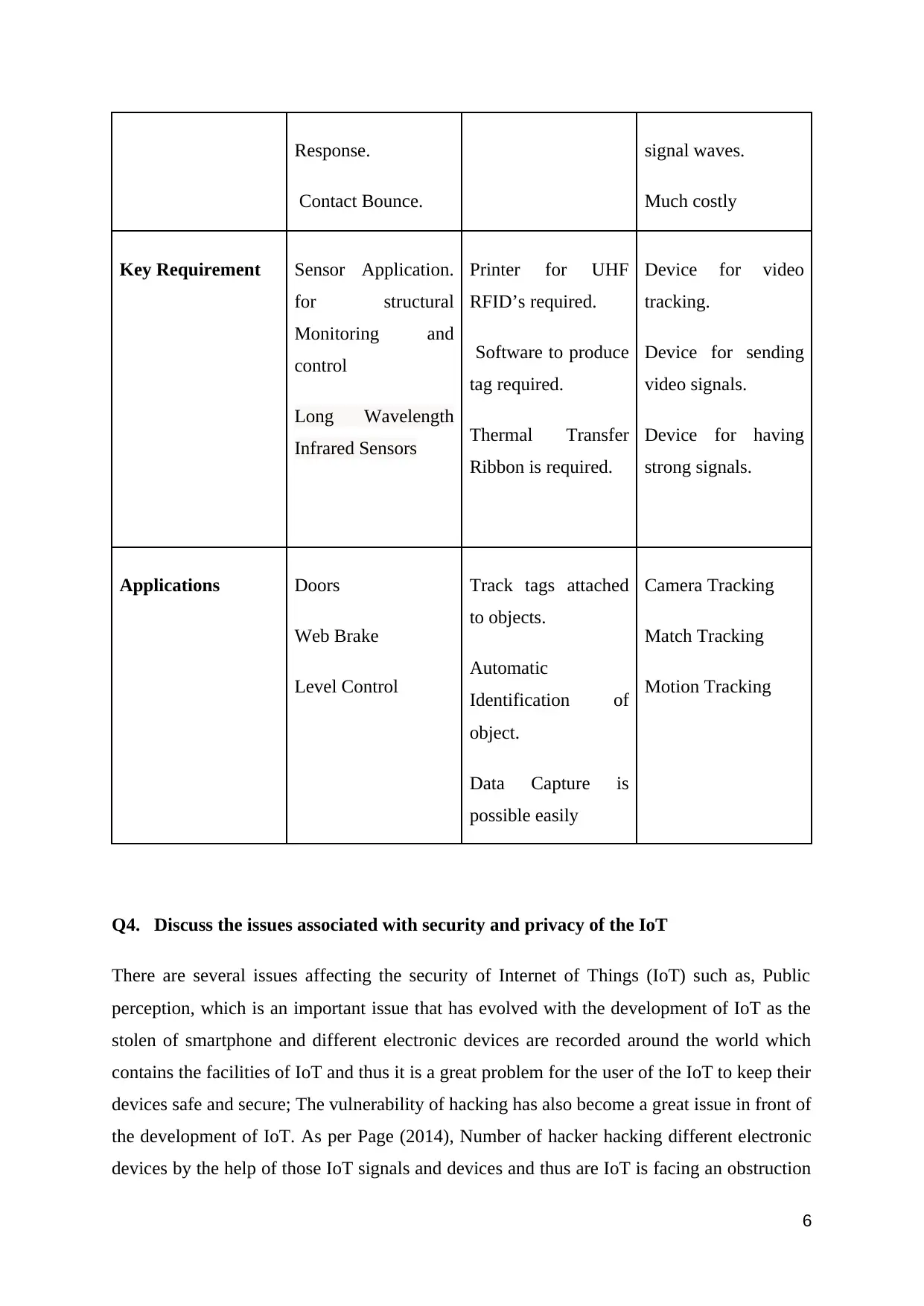
Response.
Contact Bounce.
signal waves.
Much costly
Key Requirement Sensor Application.
for structural
Monitoring and
control
Long Wavelength
Infrared Sensors
Printer for UHF
RFID’s required.
Software to produce
tag required.
Thermal Transfer
Ribbon is required.
Device for video
tracking.
Device for sending
video signals.
Device for having
strong signals.
Applications Doors
Web Brake
Level Control
Track tags attached
to objects.
Automatic
Identification of
object.
Data Capture is
possible easily
Camera Tracking
Match Tracking
Motion Tracking
Q4. Discuss the issues associated with security and privacy of the IoT
There are several issues affecting the security of Internet of Things (IoT) such as, Public
perception, which is an important issue that has evolved with the development of IoT as the
stolen of smartphone and different electronic devices are recorded around the world which
contains the facilities of IoT and thus it is a great problem for the user of the IoT to keep their
devices safe and secure; The vulnerability of hacking has also become a great issue in front of
the development of IoT. As per Page (2014), Number of hacker hacking different electronic
devices by the help of those IoT signals and devices and thus are IoT is facing an obstruction
6
Contact Bounce.
signal waves.
Much costly
Key Requirement Sensor Application.
for structural
Monitoring and
control
Long Wavelength
Infrared Sensors
Printer for UHF
RFID’s required.
Software to produce
tag required.
Thermal Transfer
Ribbon is required.
Device for video
tracking.
Device for sending
video signals.
Device for having
strong signals.
Applications Doors
Web Brake
Level Control
Track tags attached
to objects.
Automatic
Identification of
object.
Data Capture is
possible easily
Camera Tracking
Match Tracking
Motion Tracking
Q4. Discuss the issues associated with security and privacy of the IoT
There are several issues affecting the security of Internet of Things (IoT) such as, Public
perception, which is an important issue that has evolved with the development of IoT as the
stolen of smartphone and different electronic devices are recorded around the world which
contains the facilities of IoT and thus it is a great problem for the user of the IoT to keep their
devices safe and secure; The vulnerability of hacking has also become a great issue in front of
the development of IoT. As per Page (2014), Number of hacker hacking different electronic
devices by the help of those IoT signals and devices and thus are IoT is facing an obstruction
6

regarding the development of the IoT devices (p.130). This is one of the most important
security problem id IoT; Different Cyber security companies are getting much more
developed to act as a defence against the ethical hacker but the problem is that the hacker is
also developing their ways of hacking and thus creating problem for the cyber security and
the development of the IoT as well. One another problem is the lack of true security which is
affecting due to the ethical hacker. The hackers at any way are hacking the personal data of
different IoT user and thus this is also creating a big issue about the true security of the IoT
devices.
The issues regarding the privacy of the IoT are likely, loading too much data in the IoT
devices are sometimes getting insecure and are getting public. As per Gubbi, et. Al. (2013),
several people are losing their personal data when they keep their data in their IoT devices
(p.130). The devices are getting failed for preserving too much private data of the user of the
IoT device. One another problem of privacy is unwanted public profile that is trying to get
access into the personal data of other and is creating problems to the privacy of the personal
data of the user of IoT device. Losing consumer confidence is also a matter of the issues
which are related the privacy of the IoT. Due to getting hacked the consumers are radically
losing their confidence on the IoT devices and obviously this lose is affecting the
trustworthiness if the IoT devices and the IoT as well.
Q5. An IoT water level monitoring application requires updates from a sensor
periodically, using the command/response paradigm. The application triggers a
request every 1s. The round-trip propagation delay between the application and the
sensor is 12ms. On average, the sensor consumes 3ms to process each request. The
application consumes 2ms to send or receive any message. If the application blocks on
every request to the sensor, how much of its time budget can be saved by redesigning
the application to use the publish communication model in the lieu of the command
approach?
As per the given data, Application consumes = 2 ms
Sensor consumes = 3 ms
Round trip propagation delay between the application and the sensor = 12 ms
Therefore, sensor command time = 12 ms – (2 ms + 3 ms)
7
security problem id IoT; Different Cyber security companies are getting much more
developed to act as a defence against the ethical hacker but the problem is that the hacker is
also developing their ways of hacking and thus creating problem for the cyber security and
the development of the IoT as well. One another problem is the lack of true security which is
affecting due to the ethical hacker. The hackers at any way are hacking the personal data of
different IoT user and thus this is also creating a big issue about the true security of the IoT
devices.
The issues regarding the privacy of the IoT are likely, loading too much data in the IoT
devices are sometimes getting insecure and are getting public. As per Gubbi, et. Al. (2013),
several people are losing their personal data when they keep their data in their IoT devices
(p.130). The devices are getting failed for preserving too much private data of the user of the
IoT device. One another problem of privacy is unwanted public profile that is trying to get
access into the personal data of other and is creating problems to the privacy of the personal
data of the user of IoT device. Losing consumer confidence is also a matter of the issues
which are related the privacy of the IoT. Due to getting hacked the consumers are radically
losing their confidence on the IoT devices and obviously this lose is affecting the
trustworthiness if the IoT devices and the IoT as well.
Q5. An IoT water level monitoring application requires updates from a sensor
periodically, using the command/response paradigm. The application triggers a
request every 1s. The round-trip propagation delay between the application and the
sensor is 12ms. On average, the sensor consumes 3ms to process each request. The
application consumes 2ms to send or receive any message. If the application blocks on
every request to the sensor, how much of its time budget can be saved by redesigning
the application to use the publish communication model in the lieu of the command
approach?
As per the given data, Application consumes = 2 ms
Sensor consumes = 3 ms
Round trip propagation delay between the application and the sensor = 12 ms
Therefore, sensor command time = 12 ms – (2 ms + 3 ms)
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

= 7 ms
Since, round trip propagation delay between the application and the sensor = 12 ms
Now, time for required delay command = 12 ms
And, time for required delay result = 12 ms
Therefore, Total resultant time = 12 ms + 12 ms + 12 ms
= 36 ms
Time for conducting 2 cycles = 36 ms + 36 ms
= 72 ms
Since, 1 second = 100 ms
And, Time consumed by application to trigger a request = 1 second = 100 ms
Therefore, Time left for Buffering = 100 ms - 72 ms
= 28 ms
However, time for 3rd cycle > buffering time
Therefore, 3rd cycle will not be possible.
Hence, if the application id redesigned for 2 cycles in total, it can reduce the time budge by
half of what was spent in the previous expenditure, reducing overall expenditure to half (1/2).
8
Since, round trip propagation delay between the application and the sensor = 12 ms
Now, time for required delay command = 12 ms
And, time for required delay result = 12 ms
Therefore, Total resultant time = 12 ms + 12 ms + 12 ms
= 36 ms
Time for conducting 2 cycles = 36 ms + 36 ms
= 72 ms
Since, 1 second = 100 ms
And, Time consumed by application to trigger a request = 1 second = 100 ms
Therefore, Time left for Buffering = 100 ms - 72 ms
= 28 ms
However, time for 3rd cycle > buffering time
Therefore, 3rd cycle will not be possible.
Hence, if the application id redesigned for 2 cycles in total, it can reduce the time budge by
half of what was spent in the previous expenditure, reducing overall expenditure to half (1/2).
8
Q6. Describe Nielsen's Law. How does it relate to Moore’s law? What are the
Implications for the IoT?
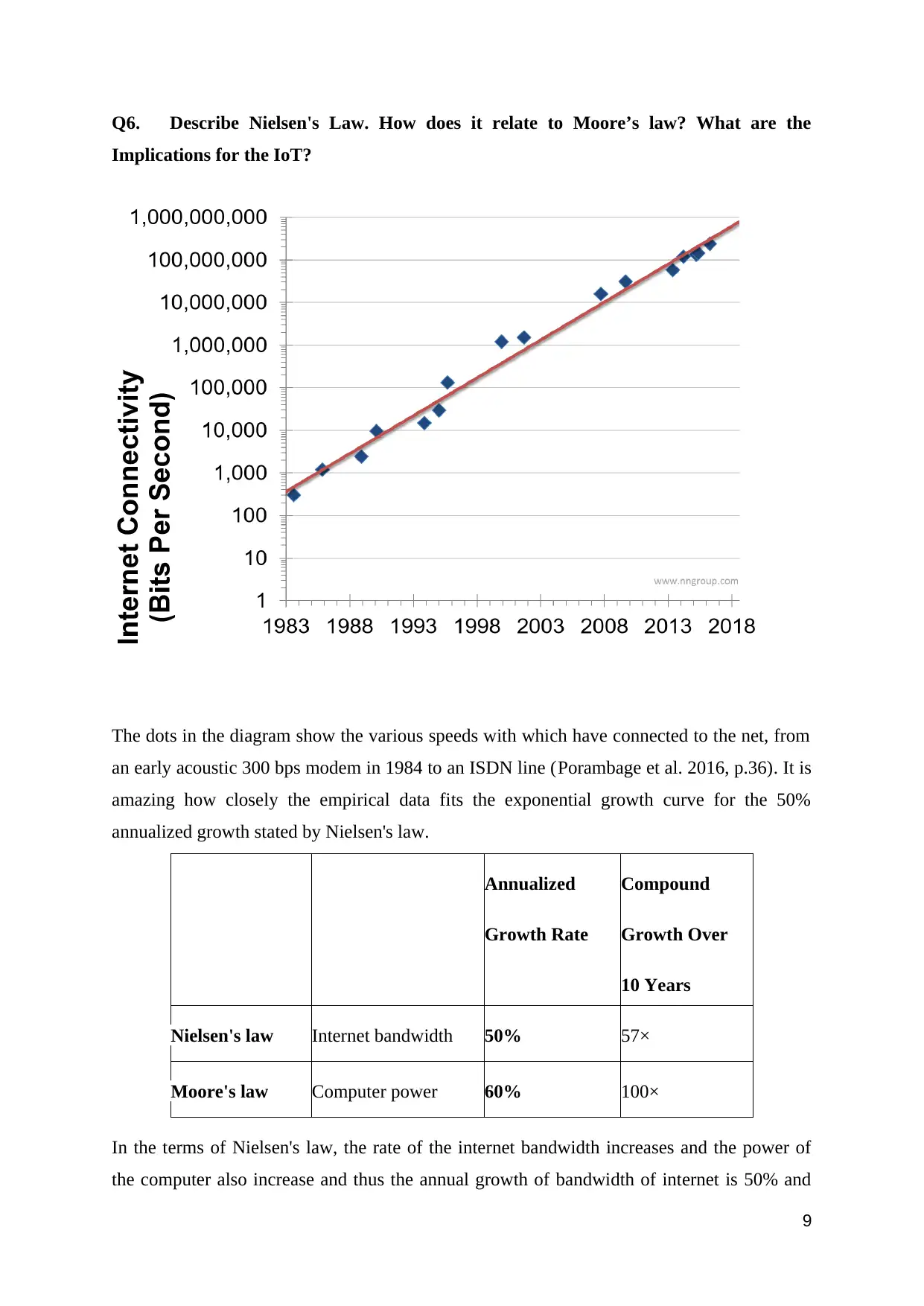
The dots in the diagram show the various speeds with which have connected to the net, from
an early acoustic 300 bps modem in 1984 to an ISDN line (Porambage et al. 2016, p.36). It is
amazing how closely the empirical data fits the exponential growth curve for the 50%
annualized growth stated by Nielsen's law.
Annualized
Growth Rate
Compound
Growth Over
10 Years
Nielsen's law Internet bandwidth 50% 57×
Moore's law Computer power 60% 100×
In the terms of Nielsen's law, the rate of the internet bandwidth increases and the power of
the computer also increase and thus the annual growth of bandwidth of internet is 50% and
9
Implications for the IoT?
The dots in the diagram show the various speeds with which have connected to the net, from
an early acoustic 300 bps modem in 1984 to an ISDN line (Porambage et al. 2016, p.36). It is
amazing how closely the empirical data fits the exponential growth curve for the 50%
annualized growth stated by Nielsen's law.
Annualized
Growth Rate
Compound
Growth Over
10 Years
Nielsen's law Internet bandwidth 50% 57×
Moore's law Computer power 60% 100×
In the terms of Nielsen's law, the rate of the internet bandwidth increases and the power of
the computer also increase and thus the annual growth of bandwidth of internet is 50% and
9

the rate of increment in the power of the growth of Internet bandwidth is multiple of 57 on
the span of 10 year (Kopetz, 2011). According to the study this increment has occurred
because the internet providing company is conservative and they used upgrade themselves
with the speed of the internet bandwidth. They are investing a lot of money for the betterment
of the internet. However, the speed of development of internet and the power of the computer
are argued by Moore's Law that says that the power of the growth of the speed of the internet
bandwidth is more than that of the speed depicted by the Nielsen's law. According to Moore's
law the speed of the growth of the computer is 60% which is 10% more than that of the
Nielsen’s Law (Xia, et. al., 2012). It also said in the Moore’s law that the speed if increment
in the power of the computer is more than that of the Nielsen’s Law that is which is 100 % in
the span of 10 year.
10
the span of 10 year (Kopetz, 2011). According to the study this increment has occurred
because the internet providing company is conservative and they used upgrade themselves
with the speed of the internet bandwidth. They are investing a lot of money for the betterment
of the internet. However, the speed of development of internet and the power of the computer
are argued by Moore's Law that says that the power of the growth of the speed of the internet
bandwidth is more than that of the speed depicted by the Nielsen's law. According to Moore's
law the speed of the growth of the computer is 60% which is 10% more than that of the
Nielsen’s Law (Xia, et. al., 2012). It also said in the Moore’s law that the speed if increment
in the power of the computer is more than that of the Nielsen’s Law that is which is 100 % in
the span of 10 year.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Reference List
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet
of things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376. Retrieved from
http://yaramoozan.ir/download/Internet_of_Things.pdf
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer
systems, 29(7), 1645-1660. Retrieved from
http://www.sciencedirect.com/science/article/pii/S0167739X13000241
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of
things: Perspectives and challenges. Wireless Networks, 20(8), 2481-2501. Retrieved
from https://link.springer.com/article/10.1007/s11276-014-0761-7
Kumar, S., Stecher, G., & Tamura, K. (2016). MEGA7: Molecular Evolutionary Genetics
Analysis version 7.0 for bigger datasets. Molecular biology and evolution, 33(7), 1870-
1874. Retrieved from https://academic.oup.com/mbe/article/33/7/1870/2579089
Kopetz, H. (2011). Internet of things. In Real-time systems (pp. 307-323). Springer US.
Page, T. (2014). Skeuomorphism or flat design: future directions in mobile device User
Interface (UI) design education. International Journal of Mobile Learning and
Organisation, 8(2), 130-142. Retrieved from
http://www.inderscienceonline.com/doi/abs/10.1504/IJMLO.2014.062350
Porambage, P., Ylianttila, M., Schmitt, C., Kumar, P., Gurtov, A., & Vasilakos, A. V. (2016).
The quest for privacy in the internet of things. IEEE Cloud Computing, 3(2), 36-45.
Xia, F., Yang, L. T., Wang, L., & Vinel, A. (2012). Internet of things. International Journal
of Communication Systems, 25(9), 1101.
11
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet
of things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376. Retrieved from
http://yaramoozan.ir/download/Internet_of_Things.pdf
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer
systems, 29(7), 1645-1660. Retrieved from
http://www.sciencedirect.com/science/article/pii/S0167739X13000241
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of
things: Perspectives and challenges. Wireless Networks, 20(8), 2481-2501. Retrieved
from https://link.springer.com/article/10.1007/s11276-014-0761-7
Kumar, S., Stecher, G., & Tamura, K. (2016). MEGA7: Molecular Evolutionary Genetics
Analysis version 7.0 for bigger datasets. Molecular biology and evolution, 33(7), 1870-
1874. Retrieved from https://academic.oup.com/mbe/article/33/7/1870/2579089
Kopetz, H. (2011). Internet of things. In Real-time systems (pp. 307-323). Springer US.
Page, T. (2014). Skeuomorphism or flat design: future directions in mobile device User
Interface (UI) design education. International Journal of Mobile Learning and
Organisation, 8(2), 130-142. Retrieved from
http://www.inderscienceonline.com/doi/abs/10.1504/IJMLO.2014.062350
Porambage, P., Ylianttila, M., Schmitt, C., Kumar, P., Gurtov, A., & Vasilakos, A. V. (2016).
The quest for privacy in the internet of things. IEEE Cloud Computing, 3(2), 36-45.
Xia, F., Yang, L. T., Wang, L., & Vinel, A. (2012). Internet of things. International Journal
of Communication Systems, 25(9), 1101.
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





