The main focus of the assignment is on Facebook
VerifiedAdded on 2022/08/24
|15
|3910
|12
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: MANAGEMENT
Business research on Security in social media
Name of the student:
Name of the university:
Author note:
Business research on Security in social media
Name of the student:
Name of the university:
Author note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
HUMAN RESOURCE MANAGEMENT
Table of contents
Introduction................................................................................................................................2
Research problem.......................................................................................................................2
Research gap..............................................................................................................................3
Literature review........................................................................................................................3
Security threats.......................................................................................................................3
Privacy issues in social media................................................................................................4
Privacy issues in Facebook....................................................................................................4
Comparative scholarly study..................................................................................................4
Methodology..............................................................................................................................8
Key findings...............................................................................................................................8
Conclusion and recommendations...........................................................................................11
References................................................................................................................................13
HUMAN RESOURCE MANAGEMENT
Table of contents
Introduction................................................................................................................................2
Research problem.......................................................................................................................2
Research gap..............................................................................................................................3
Literature review........................................................................................................................3
Security threats.......................................................................................................................3
Privacy issues in social media................................................................................................4
Privacy issues in Facebook....................................................................................................4
Comparative scholarly study..................................................................................................4
Methodology..............................................................................................................................8
Key findings...............................................................................................................................8
Conclusion and recommendations...........................................................................................11
References................................................................................................................................13

2
HUMAN RESOURCE MANAGEMENT
Introduction
Social media is an integral component for the business for expanding the scope and
arena. Information are uploaded for increasing the trafficking of the audience into the brand
image. Trust is an essential attribute in this process for luring the customers and achieving
their satisfaction. Securing the private information shared by the customers is the major
responsibility of the managers. Negligent approach in this direction aggravates the
complexities towards managing the information (Krämer and Schäwel 2019). This research
attempts to peek into the security and privacy issues, which prevail in the social networking
sites. The main focus of the assignment is on Facebook, however, other sites are also taken
into account for mapping the behaviour of the users towards the information posted.
Research problem
According to the current studies and programs, it has been found that 23% of the
Facebook users are dissatisfied with the security issues. This reflects the incapability of the
personnel towards attaching quality aspects in the privacy settings. The problems in this
direction are personalization slandering, defaming a person, which aggravates the
complexities in terms of advertising campaigns. Along with this, Youn and Shin (2019) states
that morphing techniques with fake ID, which degrades the trust of the individuals towards
sharing photos. All these issues adversely affect the trust issues regarding sharing
information, photos and other documents on the social media. Dwindling of the trust issues
distorts the communication process in terms of the data processing on the social media,
attaching negative connotation to the aspect of social learning theory. In the current business
scenario, data thefts relate to the loss of confidential data, compelling the companies and
organization like Woolworths to encounter vulnerability into the market position
(Woolworthsgroup.com.au 2020). This is one of the crucial challenges in terms of securing
the private information shared by the users. This research attempts to conduct literature
HUMAN RESOURCE MANAGEMENT
Introduction
Social media is an integral component for the business for expanding the scope and
arena. Information are uploaded for increasing the trafficking of the audience into the brand
image. Trust is an essential attribute in this process for luring the customers and achieving
their satisfaction. Securing the private information shared by the customers is the major
responsibility of the managers. Negligent approach in this direction aggravates the
complexities towards managing the information (Krämer and Schäwel 2019). This research
attempts to peek into the security and privacy issues, which prevail in the social networking
sites. The main focus of the assignment is on Facebook, however, other sites are also taken
into account for mapping the behaviour of the users towards the information posted.
Research problem
According to the current studies and programs, it has been found that 23% of the
Facebook users are dissatisfied with the security issues. This reflects the incapability of the
personnel towards attaching quality aspects in the privacy settings. The problems in this
direction are personalization slandering, defaming a person, which aggravates the
complexities in terms of advertising campaigns. Along with this, Youn and Shin (2019) states
that morphing techniques with fake ID, which degrades the trust of the individuals towards
sharing photos. All these issues adversely affect the trust issues regarding sharing
information, photos and other documents on the social media. Dwindling of the trust issues
distorts the communication process in terms of the data processing on the social media,
attaching negative connotation to the aspect of social learning theory. In the current business
scenario, data thefts relate to the loss of confidential data, compelling the companies and
organization like Woolworths to encounter vulnerability into the market position
(Woolworthsgroup.com.au 2020). This is one of the crucial challenges in terms of securing
the private information shared by the users. This research attempts to conduct literature

3
HUMAN RESOURCE MANAGEMENT
review for enhancing the awareness of the readers regarding the challenges prevailing in the
social network mechanisms as a whole.
Research gap
The previous assignment lacks linkage with the theories, which deprives the readers
from gaining an insight into the security mechanisms in the social media platforms.
Dissatisfaction with the privacy settings is something, which reflects the incapability of the
staffs regarding the ensuring that the confidentiality in the information shared by the
individuals is maintained. Data processing is also not portrayed properly, which relates to the
lack of awareness regarding the mechanisms of the social media interactions. The articles
used lacks proper research in terms of the behaviour of the users towards the data processed
in the social networking sites. Theories like Hypodermic/Bullet theory and Hypodermic
Needle Theory have been used, however, it is without alignment to the requirements for using
the social media for executing the operations.
Literature review
Security threats
The security threats in social networking include profile cloning, phising, spam,
hijacking, malware issues among others. Profile cloning is of two types: existing profile
cloning and cross site profile cloning. In this context, the ease of the hackers is projected on
the profiles of the users, which exists. Cross site cloning reflects to the illegal practice of
intervening in the profile of the people, who are listed on the friend list of the users’ account
as well as the other networks. Spams are of two types, which the hackers experiment through
hacking the emails. Broadcast spam and context aware spam intensify the threats in the
security of the data processing. In case of the hijacking session, the activities of the attacker is
spread to the other networks. Seargeant and Tagg (2019) states that malware issues relate to
HUMAN RESOURCE MANAGEMENT
review for enhancing the awareness of the readers regarding the challenges prevailing in the
social network mechanisms as a whole.
Research gap
The previous assignment lacks linkage with the theories, which deprives the readers
from gaining an insight into the security mechanisms in the social media platforms.
Dissatisfaction with the privacy settings is something, which reflects the incapability of the
staffs regarding the ensuring that the confidentiality in the information shared by the
individuals is maintained. Data processing is also not portrayed properly, which relates to the
lack of awareness regarding the mechanisms of the social media interactions. The articles
used lacks proper research in terms of the behaviour of the users towards the data processed
in the social networking sites. Theories like Hypodermic/Bullet theory and Hypodermic
Needle Theory have been used, however, it is without alignment to the requirements for using
the social media for executing the operations.
Literature review
Security threats
The security threats in social networking include profile cloning, phising, spam,
hijacking, malware issues among others. Profile cloning is of two types: existing profile
cloning and cross site profile cloning. In this context, the ease of the hackers is projected on
the profiles of the users, which exists. Cross site cloning reflects to the illegal practice of
intervening in the profile of the people, who are listed on the friend list of the users’ account
as well as the other networks. Spams are of two types, which the hackers experiment through
hacking the emails. Broadcast spam and context aware spam intensify the threats in the
security of the data processing. In case of the hijacking session, the activities of the attacker is
spread to the other networks. Seargeant and Tagg (2019) states that malware issues relate to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
HUMAN RESOURCE MANAGEMENT
fake accounts and profiles, download attack, shortened and hidden links and cross site
scripting attacks.
Privacy issues in social media
In social media, privacy issues relate to spamming, phising, hacking and others, which
compels the users to suffer from intense loss of important data. According to the surveys in
2013, hackers intervened into the personal accounts of the users by stealing their user name
and passwords. The data is alarming for the accounts in Facebook, Google, Yahoo, LinkedIn,
Twitter and others. Nytimes.com (2020) states that highest privacy issues has been noted in
Facebook. Most of the users in the Facebook belong to teenage and are addicted towards
posting every single happening of their lives. Moreover, fake profiles attracts the hackers,
who intervene into the users’ account by accessing their other accounts like bank accounts.
Privacy issues in Facebook
The privacy settings in Facebook reflects the control measures regarding disclosure of
the data to be made public. The access to the posted information is to be within the decision
of the users. According to the revelations of Nytimes.com (2020), the privacy settings in the
Facebook has been altered. This is in response to the data thefts and cybercrimes, which
resulted in the customer turnover. The main change is to simplify the privacy settings,
especially the controls.
Comparative scholarly study
According to the arguments of Ayaburi and Treku (2020), information abuse
generates the situation of privacy violations and trust concerns for the clients and the
customers. In case of the violations, an apology form is levied for maintaining the stability in
the relationship with the customers. Organizational behaviour integrity model is used for
mapping the perceptions regarding data breach and spillover for the trust, loyalty and
integrity. Delving deep into the matter, security concerns adversely affects the trust. Post
breach instance mapping forms an integral part of the study, which helps in assessing the
HUMAN RESOURCE MANAGEMENT
fake accounts and profiles, download attack, shortened and hidden links and cross site
scripting attacks.
Privacy issues in social media
In social media, privacy issues relate to spamming, phising, hacking and others, which
compels the users to suffer from intense loss of important data. According to the surveys in
2013, hackers intervened into the personal accounts of the users by stealing their user name
and passwords. The data is alarming for the accounts in Facebook, Google, Yahoo, LinkedIn,
Twitter and others. Nytimes.com (2020) states that highest privacy issues has been noted in
Facebook. Most of the users in the Facebook belong to teenage and are addicted towards
posting every single happening of their lives. Moreover, fake profiles attracts the hackers,
who intervene into the users’ account by accessing their other accounts like bank accounts.
Privacy issues in Facebook
The privacy settings in Facebook reflects the control measures regarding disclosure of
the data to be made public. The access to the posted information is to be within the decision
of the users. According to the revelations of Nytimes.com (2020), the privacy settings in the
Facebook has been altered. This is in response to the data thefts and cybercrimes, which
resulted in the customer turnover. The main change is to simplify the privacy settings,
especially the controls.
Comparative scholarly study
According to the arguments of Ayaburi and Treku (2020), information abuse
generates the situation of privacy violations and trust concerns for the clients and the
customers. In case of the violations, an apology form is levied for maintaining the stability in
the relationship with the customers. Organizational behaviour integrity model is used for
mapping the perceptions regarding data breach and spillover for the trust, loyalty and
integrity. Delving deep into the matter, security concerns adversely affects the trust. Post
breach instance mapping forms an integral part of the study, which helps in assessing the

5
HUMAN RESOURCE MANAGEMENT
effectiveness of the strategies and planning for social media marketing. Penitence can be
related to the initiatives of formulating effective policies for revising the security policies.
As per the arguments of Krämer and Schäwel (2019), decision-making in terms of
self-disclosure in the social media is ‘multi-dimensional’. Complications also prevail in this
decision-making, which relates to the anticipation of the negative outcomes towards securing
the information provided by the individuals. Implementation of Maslow’s hierarchy of Needs
theory, Krämer and Schäwel states that humans have strong motivation for protecting the
privacy, which is fundamental and basic to the human nature. In this context, two
characteristic shades of humans are projected. One is the consciousness towards protecting
the privacy in the information and another is the self-disclosure of information for the
fulfilment of their own needs. ‘Mastering’ relates to the tactfulness in terms of disclosing
such information, which if disclosed, would not affect the privacy and most importantly, self-
respect.
Youn and Shin (2019) is of the view that cognitive appraisal and parent-peer
communication adversely affects the teenagers’ perceptions regarding privacy concerns in the
social media platforms like Facebook. Coping strategies are required for coping up with the
potential risks in disclosures and advertising. One of the surveys conducted in US gains
prominence in the research of Youn and Shin, highlighting that benefit appraisal generates
high engagement in the advertisement posted in the news feed of Facebook. On the other
hand, perceptions regarding the risks of disclosure evokes reactive coping up with the
accumulation of effective strategies regarding regulative control.
According to Seargeant and Tagg (2019), filter bubble effect is reflected, which
upholds the user oriented suggestions regarding addressing the issues in the online actions in
Facebook. Communication strategies are employed for influencing the thought process of the
HUMAN RESOURCE MANAGEMENT
effectiveness of the strategies and planning for social media marketing. Penitence can be
related to the initiatives of formulating effective policies for revising the security policies.
As per the arguments of Krämer and Schäwel (2019), decision-making in terms of
self-disclosure in the social media is ‘multi-dimensional’. Complications also prevail in this
decision-making, which relates to the anticipation of the negative outcomes towards securing
the information provided by the individuals. Implementation of Maslow’s hierarchy of Needs
theory, Krämer and Schäwel states that humans have strong motivation for protecting the
privacy, which is fundamental and basic to the human nature. In this context, two
characteristic shades of humans are projected. One is the consciousness towards protecting
the privacy in the information and another is the self-disclosure of information for the
fulfilment of their own needs. ‘Mastering’ relates to the tactfulness in terms of disclosing
such information, which if disclosed, would not affect the privacy and most importantly, self-
respect.
Youn and Shin (2019) is of the view that cognitive appraisal and parent-peer
communication adversely affects the teenagers’ perceptions regarding privacy concerns in the
social media platforms like Facebook. Coping strategies are required for coping up with the
potential risks in disclosures and advertising. One of the surveys conducted in US gains
prominence in the research of Youn and Shin, highlighting that benefit appraisal generates
high engagement in the advertisement posted in the news feed of Facebook. On the other
hand, perceptions regarding the risks of disclosure evokes reactive coping up with the
accumulation of effective strategies regarding regulative control.
According to Seargeant and Tagg (2019), filter bubble effect is reflected, which
upholds the user oriented suggestions regarding addressing the issues in the online actions in
Facebook. Communication strategies are employed for influencing the thought process of the

6
HUMAN RESOURCE MANAGEMENT
individuals regarding posting information. In this context, the theory of planned action and
reasoned behaviour can be applied in terms of mapping the behaviour of the people on the
social networking sites. Self-actions and the control measures play an important role in
evoking emerging beliefs. Contextual understanding about the user oriented approach relates
to the situations in which the beliefs regarding security are practically implied while posting
the information. Filter bubble conundrum indicates the way in which the perceptions are
interpreted towards the information shared by the clients on the social media.
According to the arguments of Buccafurri et al. (2015), comparison is established in
the user behaviour in Facebook and Twitter regarding the information uploads. Multi-OSN
perspective is used for analysing the memberships and overlaps in terms of the degree of
reactiveness and awareness of the security mechanisms. In the analysis, common friendships
is reflected, which places the users into a group. These common friendships can be related to
the aspect of common thoughts and perceptions regarding sharing news, photos and images to
peers, bringing the communication and exchange theory into the discussion. This approach is
effective in terms of spreading positive word of mouth advertising. In case of Twitter, the
default privacy settings are public, which provides easy access to the hackers to extract
information. Privatisation of the timelines does not stay for long. Once a tweet is retweeted, it
automatically becomes visible to the public. The location services are enabled in Twitter,
which most of the users lack proper information. In this case, tweeting the personal home
address is risky.
Mention can be made of the Hypodermic/Bullet theory, which highlights the power of
social media in terms of ‘shooting or injecting’ the messages in a manner of influencing the
thought process of the users towards posting the information on social media. The mass
(audience) is portrayed as the passive viewers, who are affected by the thefts of data shared.
According to this theory, social media is one of an important forms of communication with
HUMAN RESOURCE MANAGEMENT
individuals regarding posting information. In this context, the theory of planned action and
reasoned behaviour can be applied in terms of mapping the behaviour of the people on the
social networking sites. Self-actions and the control measures play an important role in
evoking emerging beliefs. Contextual understanding about the user oriented approach relates
to the situations in which the beliefs regarding security are practically implied while posting
the information. Filter bubble conundrum indicates the way in which the perceptions are
interpreted towards the information shared by the clients on the social media.
According to the arguments of Buccafurri et al. (2015), comparison is established in
the user behaviour in Facebook and Twitter regarding the information uploads. Multi-OSN
perspective is used for analysing the memberships and overlaps in terms of the degree of
reactiveness and awareness of the security mechanisms. In the analysis, common friendships
is reflected, which places the users into a group. These common friendships can be related to
the aspect of common thoughts and perceptions regarding sharing news, photos and images to
peers, bringing the communication and exchange theory into the discussion. This approach is
effective in terms of spreading positive word of mouth advertising. In case of Twitter, the
default privacy settings are public, which provides easy access to the hackers to extract
information. Privatisation of the timelines does not stay for long. Once a tweet is retweeted, it
automatically becomes visible to the public. The location services are enabled in Twitter,
which most of the users lack proper information. In this case, tweeting the personal home
address is risky.
Mention can be made of the Hypodermic/Bullet theory, which highlights the power of
social media in terms of ‘shooting or injecting’ the messages in a manner of influencing the
thought process of the users towards posting the information on social media. The mass
(audience) is portrayed as the passive viewers, who are affected by the thefts of data shared.
According to this theory, social media is one of an important forms of communication with
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
HUMAN RESOURCE MANAGEMENT
the audience. Receiving and acceptance of the messages by the audience are integral for
communication to proceed in an efficient and effective manner. Jabee and Afshar (2016)
counters the argument that media is all powerful. This is because unless and until quality
contents are produced, media cannot exert its influence on the thought process and
perceptions of the users. The messages communicated in the channels are considered to be
‘magic bullets’, which instigates the users to take relevant actions for responding to the
affectation.
On the contrary, Hypodermic Needle Theory can be correlated in this context in terms
of mapping the linear communications between the passive audiences. There is no individual
difference in the information shared. Countering this, every individual possess exclusive
thoughts and perceptions regarding disclosing information. According to Two Step Flow
Theory, uncertainties are reflected in the beliefs regarding the influence created by the
audience in the process of responding to the activities on the social media. The basis of
decision-making in this context is the personal interactions between the peers. Raut and Patil
(2016) is of the view that Gatekeeping Theory is relevant in this context in terms of
enhancing the security of the information posted on the social media. The gates act as a
barrier in terms of blocking the unwanted personnel, which averts the instances of data thefts
and other forms of cybercrimes.
Decision makers are portrayed as the gate keepers, who play an important role in
securing the information on the social media. Managers, through the formulation of security
cookies and policies, play the role of the gate keepers, deciding on which information can be
processed on the social media for upgrading the knowledge of the users. Consciousness
towards influence and affectation depends on the ethical considerations through the
consideration of the socio-cultural factors (Panahi, Watson and Partridge 2016). Evaluative
research are conducted by the managers, which reduces the risks of the data thefts. Policies
HUMAN RESOURCE MANAGEMENT
the audience. Receiving and acceptance of the messages by the audience are integral for
communication to proceed in an efficient and effective manner. Jabee and Afshar (2016)
counters the argument that media is all powerful. This is because unless and until quality
contents are produced, media cannot exert its influence on the thought process and
perceptions of the users. The messages communicated in the channels are considered to be
‘magic bullets’, which instigates the users to take relevant actions for responding to the
affectation.
On the contrary, Hypodermic Needle Theory can be correlated in this context in terms
of mapping the linear communications between the passive audiences. There is no individual
difference in the information shared. Countering this, every individual possess exclusive
thoughts and perceptions regarding disclosing information. According to Two Step Flow
Theory, uncertainties are reflected in the beliefs regarding the influence created by the
audience in the process of responding to the activities on the social media. The basis of
decision-making in this context is the personal interactions between the peers. Raut and Patil
(2016) is of the view that Gatekeeping Theory is relevant in this context in terms of
enhancing the security of the information posted on the social media. The gates act as a
barrier in terms of blocking the unwanted personnel, which averts the instances of data thefts
and other forms of cybercrimes.
Decision makers are portrayed as the gate keepers, who play an important role in
securing the information on the social media. Managers, through the formulation of security
cookies and policies, play the role of the gate keepers, deciding on which information can be
processed on the social media for upgrading the knowledge of the users. Consciousness
towards influence and affectation depends on the ethical considerations through the
consideration of the socio-cultural factors (Panahi, Watson and Partridge 2016). Evaluative
research are conducted by the managers, which reduces the risks of the data thefts. Policies

8
HUMAN RESOURCE MANAGEMENT
act assistance in terms of driving the information of the user groups into right direction,
where they can gain accurate information regarding posting information on social media.
Reference can also be cited of the social learning theory, where interactions and group
discussions form an integral element in the learning mechanisms. Observations and
reflections are practiced by the groups in the process of interactions, which helps in
concretizing the experience regarding disclosing the information according to the
requirements. Role models are selected by the groups, which helps in bringing noticeable
changes in the behaviours regarding the social media information.
Methodology
Hypodermic Needle Theory and Hypodermic/Bullet theory would be used for delving
deeper into the mechanisms of the social media interactions. This approach would be
effective for achieving justification regarding the propositions and assumptions. Linking the
theories with the propositions would help in deducing relevant recommendations about
transferring the messages through social media in an efficient and effective manner.
Key findings
Social media is one of an efficient means of communication, where the users share
information and indulge in group discussions and forums regarding different subjects. The
interactions in the social media are diversified in nature, involving the aspects of e-
commerce, media sharing networks, discussion forums, bookmarking sites, social publishing,
and online reviews among others. According to the arguments of Umair, Nanda and He
(2017), social networking sites, which are commonly used are Facebook, Twitter, Instagram,
Pinterest among others. Privacy issues are crucial in terms of maintaining the privacy in the
information disclosed by the users in the social networking sites. Most of the cases reflects
negligence towards maintaining the security in the data processed. This negligence results in
HUMAN RESOURCE MANAGEMENT
act assistance in terms of driving the information of the user groups into right direction,
where they can gain accurate information regarding posting information on social media.
Reference can also be cited of the social learning theory, where interactions and group
discussions form an integral element in the learning mechanisms. Observations and
reflections are practiced by the groups in the process of interactions, which helps in
concretizing the experience regarding disclosing the information according to the
requirements. Role models are selected by the groups, which helps in bringing noticeable
changes in the behaviours regarding the social media information.
Methodology
Hypodermic Needle Theory and Hypodermic/Bullet theory would be used for delving
deeper into the mechanisms of the social media interactions. This approach would be
effective for achieving justification regarding the propositions and assumptions. Linking the
theories with the propositions would help in deducing relevant recommendations about
transferring the messages through social media in an efficient and effective manner.
Key findings
Social media is one of an efficient means of communication, where the users share
information and indulge in group discussions and forums regarding different subjects. The
interactions in the social media are diversified in nature, involving the aspects of e-
commerce, media sharing networks, discussion forums, bookmarking sites, social publishing,
and online reviews among others. According to the arguments of Umair, Nanda and He
(2017), social networking sites, which are commonly used are Facebook, Twitter, Instagram,
Pinterest among others. Privacy issues are crucial in terms of maintaining the privacy in the
information disclosed by the users in the social networking sites. Most of the cases reflects
negligence towards maintaining the security in the data processed. This negligence results in
9
HUMAN RESOURCE MANAGEMENT
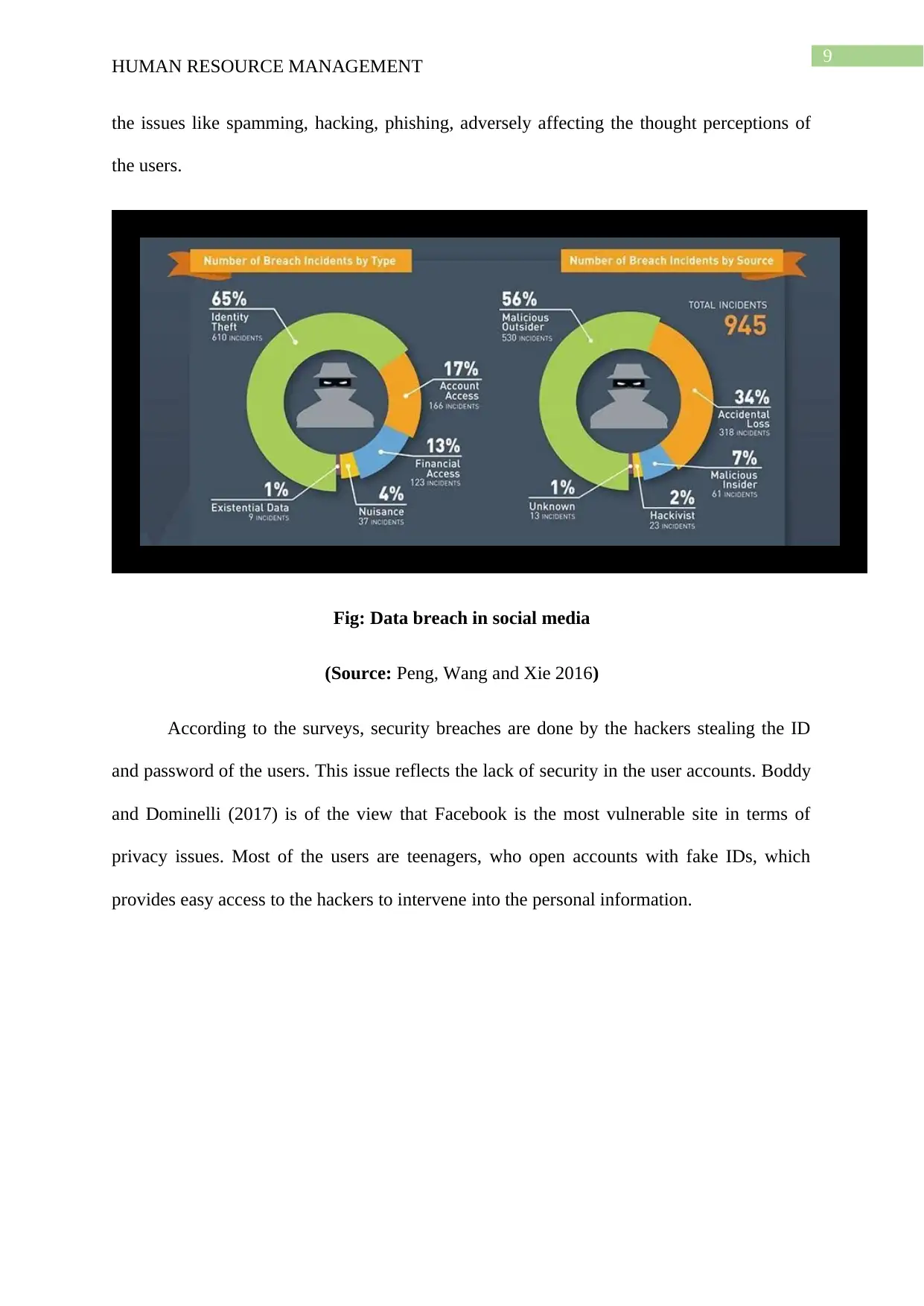
the issues like spamming, hacking, phishing, adversely affecting the thought perceptions of
the users.
Fig: Data breach in social media
(Source: Peng, Wang and Xie 2016)
According to the surveys, security breaches are done by the hackers stealing the ID
and password of the users. This issue reflects the lack of security in the user accounts. Boddy
and Dominelli (2017) is of the view that Facebook is the most vulnerable site in terms of
privacy issues. Most of the users are teenagers, who open accounts with fake IDs, which
provides easy access to the hackers to intervene into the personal information.
HUMAN RESOURCE MANAGEMENT
the issues like spamming, hacking, phishing, adversely affecting the thought perceptions of
the users.
Fig: Data breach in social media
(Source: Peng, Wang and Xie 2016)
According to the surveys, security breaches are done by the hackers stealing the ID
and password of the users. This issue reflects the lack of security in the user accounts. Boddy
and Dominelli (2017) is of the view that Facebook is the most vulnerable site in terms of
privacy issues. Most of the users are teenagers, who open accounts with fake IDs, which
provides easy access to the hackers to intervene into the personal information.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
HUMAN RESOURCE MANAGEMENT
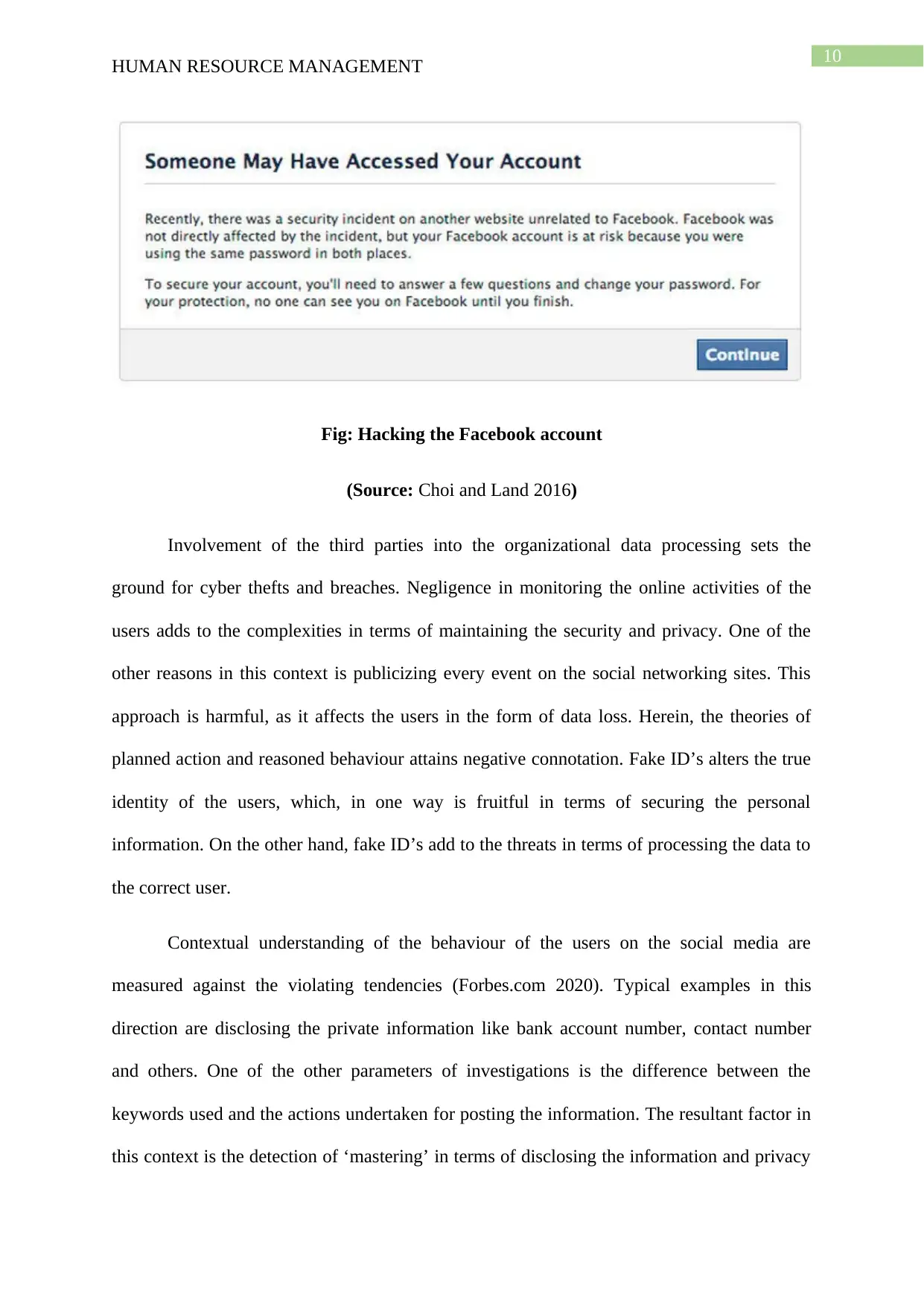
Fig: Hacking the Facebook account
(Source: Choi and Land 2016)
Involvement of the third parties into the organizational data processing sets the
ground for cyber thefts and breaches. Negligence in monitoring the online activities of the
users adds to the complexities in terms of maintaining the security and privacy. One of the
other reasons in this context is publicizing every event on the social networking sites. This
approach is harmful, as it affects the users in the form of data loss. Herein, the theories of
planned action and reasoned behaviour attains negative connotation. Fake ID’s alters the true
identity of the users, which, in one way is fruitful in terms of securing the personal
information. On the other hand, fake ID’s add to the threats in terms of processing the data to
the correct user.
Contextual understanding of the behaviour of the users on the social media are
measured against the violating tendencies (Forbes.com 2020). Typical examples in this
direction are disclosing the private information like bank account number, contact number
and others. One of the other parameters of investigations is the difference between the
keywords used and the actions undertaken for posting the information. The resultant factor in
this context is the detection of ‘mastering’ in terms of disclosing the information and privacy
HUMAN RESOURCE MANAGEMENT
Fig: Hacking the Facebook account
(Source: Choi and Land 2016)
Involvement of the third parties into the organizational data processing sets the
ground for cyber thefts and breaches. Negligence in monitoring the online activities of the
users adds to the complexities in terms of maintaining the security and privacy. One of the
other reasons in this context is publicizing every event on the social networking sites. This
approach is harmful, as it affects the users in the form of data loss. Herein, the theories of
planned action and reasoned behaviour attains negative connotation. Fake ID’s alters the true
identity of the users, which, in one way is fruitful in terms of securing the personal
information. On the other hand, fake ID’s add to the threats in terms of processing the data to
the correct user.
Contextual understanding of the behaviour of the users on the social media are
measured against the violating tendencies (Forbes.com 2020). Typical examples in this
direction are disclosing the private information like bank account number, contact number
and others. One of the other parameters of investigations is the difference between the
keywords used and the actions undertaken for posting the information. The resultant factor in
this context is the detection of ‘mastering’ in terms of disclosing the information and privacy

11
HUMAN RESOURCE MANAGEMENT
issues and concerns. In this context, the revelations of Woolworthsgroup.com.au (2020)
states that motivation and support influence the users to be concerned about the security and
privacy issues in the business of companies like Woolworths. If the example of teenagers’
response on the Facebook newsfeeds are considered, cognitive appraisal and social influence
becomes integral in terms of securing the information shared on the social networking sites.
Coping strategies are needed for tracking the information shared by the users, specially the
teenagers, as they need to be protected from the instances of data thefts.
User oriented approaches generates open debates regarding filtering the news and
information. Bubble conundrum relates to the conversations between the users. Actions of the
users contributes towards mapping the response towards processing the information. It has
been observed that Facebook users are dissatisfied with the security and privacy settings.
Online impersonation slandering, defame are the common issues, which degrades the security
and privacy issues (Theconversation.com 2020). These issues affect the trust of the users in
terms of sharing photos and news on social media. Morphing techniques are applied on the
photos to deform them, which processes wrong information to the peer groups. These
techniques contradict the security cookies and policies and their mechanisms towards
protecting the information uploaded by the users.
Content sharing social networks are the most relevant in this context, which helps in
mapping the behaviour of the users towards the contents used in advertisement on sites like
Facebook. As a matter of specification, the privacy and security influencing factors revolve
around ease of use, utility for the friends and others. This utility analysis is effective for
assessing the behaviour of the users and the groups. Information sharing attains value when it
is within the boundary of the users and the peer groups (Ayaburi and Treku 2020).
Intervention of the third parties becomes risky towards securing the private details.
HUMAN RESOURCE MANAGEMENT
issues and concerns. In this context, the revelations of Woolworthsgroup.com.au (2020)
states that motivation and support influence the users to be concerned about the security and
privacy issues in the business of companies like Woolworths. If the example of teenagers’
response on the Facebook newsfeeds are considered, cognitive appraisal and social influence
becomes integral in terms of securing the information shared on the social networking sites.
Coping strategies are needed for tracking the information shared by the users, specially the
teenagers, as they need to be protected from the instances of data thefts.
User oriented approaches generates open debates regarding filtering the news and
information. Bubble conundrum relates to the conversations between the users. Actions of the
users contributes towards mapping the response towards processing the information. It has
been observed that Facebook users are dissatisfied with the security and privacy settings.
Online impersonation slandering, defame are the common issues, which degrades the security
and privacy issues (Theconversation.com 2020). These issues affect the trust of the users in
terms of sharing photos and news on social media. Morphing techniques are applied on the
photos to deform them, which processes wrong information to the peer groups. These
techniques contradict the security cookies and policies and their mechanisms towards
protecting the information uploaded by the users.
Content sharing social networks are the most relevant in this context, which helps in
mapping the behaviour of the users towards the contents used in advertisement on sites like
Facebook. As a matter of specification, the privacy and security influencing factors revolve
around ease of use, utility for the friends and others. This utility analysis is effective for
assessing the behaviour of the users and the groups. Information sharing attains value when it
is within the boundary of the users and the peer groups (Ayaburi and Treku 2020).
Intervention of the third parties becomes risky towards securing the private details.

12
HUMAN RESOURCE MANAGEMENT
Conclusion and recommendations
Privacy issues in Facebook aggravates the complexities in sharing the information to
large mass of audience. Security threats are evident from the instance of hacker interventions,
which results in the loss of essential data. Hypodermic/Bullet theory has been suggested in
this research for monitoring and controlling the mechanisms through which the messages are
sent in the social media. For avoiding these instances, the users need to remember not to
publicize every information on the social media. Rationality and logical approach is needed
for gaining mastery over the information posted on the sites like Facebook and others.
Personal information like bank account numbers, address, email IDs need not be shared. It is
crucial for logging off the account, which would enhance the security issues. Tactfulness is
essential in terms of handling the third party interferences. Friend request from the strangers
is to be avoided for maintaining the privacy in the personal details. Additional precautions
need to be taken for averting the instances of stalking, harassment and others.
HUMAN RESOURCE MANAGEMENT
Conclusion and recommendations
Privacy issues in Facebook aggravates the complexities in sharing the information to
large mass of audience. Security threats are evident from the instance of hacker interventions,
which results in the loss of essential data. Hypodermic/Bullet theory has been suggested in
this research for monitoring and controlling the mechanisms through which the messages are
sent in the social media. For avoiding these instances, the users need to remember not to
publicize every information on the social media. Rationality and logical approach is needed
for gaining mastery over the information posted on the sites like Facebook and others.
Personal information like bank account numbers, address, email IDs need not be shared. It is
crucial for logging off the account, which would enhance the security issues. Tactfulness is
essential in terms of handling the third party interferences. Friend request from the strangers
is to be avoided for maintaining the privacy in the personal details. Additional precautions
need to be taken for averting the instances of stalking, harassment and others.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
HUMAN RESOURCE MANAGEMENT
References
Ayaburi, E.W. and Treku, D.N., 2020. Effect of penitence on social media trust and privacy
concerns: The case of Facebook. International Journal of Information Management, 50,
pp.171-181.
Boddy, J. and Dominelli, L., 2017. Social media and social work: The challenges of a new
ethical space. Australian Social Work, 70(2), pp.172-184.
Buccafurri, F., Lax, G., Nicolazzo, S. and Nocera, A., 2015. Comparing Twitter and
Facebook user behavior: Privacy and other aspects. Computers in Human Behavior, 52,
pp.87-95.
Choi, B.C. and Land, L., 2016. The effects of general privacy concerns and transactional
privacy concerns on Facebook apps usage. Information & Management, 53(7), pp.868-877.
Forbes.com 2020. Using Blockchain To Eliminate Social Media Challenges Available at:
https://www.forbes.com/sites/forbestechcouncil/2020/01/08/using-blockchain-to-eliminate-
social-media-challenges/#24eca8ff7722 [Accessed on 18th Jan 2020]
Jabee, R. and Afshar, M., 2016. Issues and challenges of cyber security for social networking
sites (Facebook). International Journal of Computer Applications, 144(3), pp.36-40.
Krämer, N.C. and Schäwel, J., 2019. Mastering the challenge of balancing self-disclosure and
privacy in social media. Current opinion in psychology.
Nytimes.com 2020. Facebook Bows to Pressure Over Privacy Available at:
https://www.nytimes.com/2010/05/27/technology/27facebook.html?hp [Accessed on 19th Jan
2020]
Panahi, S., Watson, J. and Partridge, H., 2016. Social media and physicians: exploring the
benefits and challenges. Health informatics journal, 22(2), pp.99-112.
HUMAN RESOURCE MANAGEMENT
References
Ayaburi, E.W. and Treku, D.N., 2020. Effect of penitence on social media trust and privacy
concerns: The case of Facebook. International Journal of Information Management, 50,
pp.171-181.
Boddy, J. and Dominelli, L., 2017. Social media and social work: The challenges of a new
ethical space. Australian Social Work, 70(2), pp.172-184.
Buccafurri, F., Lax, G., Nicolazzo, S. and Nocera, A., 2015. Comparing Twitter and
Facebook user behavior: Privacy and other aspects. Computers in Human Behavior, 52,
pp.87-95.
Choi, B.C. and Land, L., 2016. The effects of general privacy concerns and transactional
privacy concerns on Facebook apps usage. Information & Management, 53(7), pp.868-877.
Forbes.com 2020. Using Blockchain To Eliminate Social Media Challenges Available at:
https://www.forbes.com/sites/forbestechcouncil/2020/01/08/using-blockchain-to-eliminate-
social-media-challenges/#24eca8ff7722 [Accessed on 18th Jan 2020]
Jabee, R. and Afshar, M., 2016. Issues and challenges of cyber security for social networking
sites (Facebook). International Journal of Computer Applications, 144(3), pp.36-40.
Krämer, N.C. and Schäwel, J., 2019. Mastering the challenge of balancing self-disclosure and
privacy in social media. Current opinion in psychology.
Nytimes.com 2020. Facebook Bows to Pressure Over Privacy Available at:
https://www.nytimes.com/2010/05/27/technology/27facebook.html?hp [Accessed on 19th Jan
2020]
Panahi, S., Watson, J. and Partridge, H., 2016. Social media and physicians: exploring the
benefits and challenges. Health informatics journal, 22(2), pp.99-112.

14
HUMAN RESOURCE MANAGEMENT
Peng, S., Wang, G. and Xie, D., 2016. Social influence analysis in social networking big data:
Opportunities and challenges. IEEE network, 31(1), pp.11-17.
Raut, V. and Patil, P., 2016. Use of Social Media in Education: Positive and Negative impact
on the students. International Journal on Recent and Innovation Trends in Computing and
Communication, 4(1), pp.281-285.
Seargeant, P. and Tagg, C., 2019. Social media and the future of open debate: A user-oriented
approach to Facebook’s filter bubble conundrum. Discourse, Context & Media, 27, pp.41-48.
Theconversation.com 2020. Australian media regulators face the challenge of dealing with
global platforms Google and Facebook Available at: http://theconversation.com/australian-
media-regulators-face-the-challenge-of-dealing-with-global-platforms-google-and-facebook-
121430 [Accessed on 18th Jan 2020]
Umair, A., Nanda, P. and He, X., 2017, August. Online social network information forensics:
A survey on use of various tools and determining how cautious facebook users are?. In 2017
IEEE Trustcom/BigDataSE/ICESS (pp. 1139-1144). IEEE.
Woolworthsgroup.com.au 2020. Annual report. Available at:
https://www.woolworthsgroup.com.au/icms_docs/195582_annual-report-2019.pdf
Youn, S. and Shin, W., 2019. Teens’ responses to Facebook newsfeed advertising: The
effects of cognitive appraisal and social influence on privacy concerns and coping strategies.
Telematics and Informatics, 38, pp.30-45.
HUMAN RESOURCE MANAGEMENT
Peng, S., Wang, G. and Xie, D., 2016. Social influence analysis in social networking big data:
Opportunities and challenges. IEEE network, 31(1), pp.11-17.
Raut, V. and Patil, P., 2016. Use of Social Media in Education: Positive and Negative impact
on the students. International Journal on Recent and Innovation Trends in Computing and
Communication, 4(1), pp.281-285.
Seargeant, P. and Tagg, C., 2019. Social media and the future of open debate: A user-oriented
approach to Facebook’s filter bubble conundrum. Discourse, Context & Media, 27, pp.41-48.
Theconversation.com 2020. Australian media regulators face the challenge of dealing with
global platforms Google and Facebook Available at: http://theconversation.com/australian-
media-regulators-face-the-challenge-of-dealing-with-global-platforms-google-and-facebook-
121430 [Accessed on 18th Jan 2020]
Umair, A., Nanda, P. and He, X., 2017, August. Online social network information forensics:
A survey on use of various tools and determining how cautious facebook users are?. In 2017
IEEE Trustcom/BigDataSE/ICESS (pp. 1139-1144). IEEE.
Woolworthsgroup.com.au 2020. Annual report. Available at:
https://www.woolworthsgroup.com.au/icms_docs/195582_annual-report-2019.pdf
Youn, S. and Shin, W., 2019. Teens’ responses to Facebook newsfeed advertising: The
effects of cognitive appraisal and social influence on privacy concerns and coping strategies.
Telematics and Informatics, 38, pp.30-45.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





