Security and Privacy Analysis: HR Data in SaaS and On-Premise Systems
VerifiedAdded on 2020/03/01
|24
|5598
|311
Report
AI Summary
This report provides an in-depth analysis of security and privacy risks associated with HR data, comparing the vulnerabilities of traditional in-house databases with those of cloud-based SaaS applications. The report focuses on the Department of Administrative Services (DAS) in Australia, detailing the Shared Services Approach and its implications for data security. It explores risks such as excessive privileges, cyber attacks, malware, poor auditing mechanisms, and security breaches in backup disks within the in-house system. The analysis extends to the SaaS model, examining risks related to third-party access, provider instability, transparency issues, and identity theft. The report assesses the security and privacy of employee data, addresses digital identity issues, and considers data sensitivity and jurisdiction, providing a comprehensive overview of the challenges and potential mitigation strategies for protecting sensitive employee information in a cloud environment.

Running head: SECURITY AND PRIVACY
Security and privacy
Name of the Student
Name of the University
Author Note
Security and privacy
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
The following report discusses about the various security and privacy risks and threats that are
associated with the conventional HR database and the cloud based approaches. The model of
cloud approach used here is the SaaS model. The chosen organization is the Department of
Administrative Service located in Australia. The report also discusses about the digital identity
issues and the jurisdictions associated with data security and cloud computing.
The following report discusses about the various security and privacy risks and threats that are
associated with the conventional HR database and the cloud based approaches. The model of
cloud approach used here is the SaaS model. The chosen organization is the Department of
Administrative Service located in Australia. The report also discusses about the digital identity
issues and the jurisdictions associated with data security and cloud computing.

Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Security of employee data:..........................................................................................................4
Risks and threats in the in house HR database of the DAS:....................................................4
Risks and threats after migration to SaaS application:............................................................6
Assessment of resulting Security of Employee Data...............................................................8
Privacy of employee data:.........................................................................................................11
Risks and threats in the privacy of the data in the in house HR database:............................11
Risks and threats after the migration to SaaS applications:...................................................12
Assessment of Privacy of Employee Data:............................................................................13
Digital identity issues:...............................................................................................................17
Provider solution issues:............................................................................................................18
Data sensitivity and jurisdiction:...............................................................................................19
Conclusion:....................................................................................................................................20
References:....................................................................................................................................22
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Security of employee data:..........................................................................................................4
Risks and threats in the in house HR database of the DAS:....................................................4
Risks and threats after migration to SaaS application:............................................................6
Assessment of resulting Security of Employee Data...............................................................8
Privacy of employee data:.........................................................................................................11
Risks and threats in the privacy of the data in the in house HR database:............................11
Risks and threats after the migration to SaaS applications:...................................................12
Assessment of Privacy of Employee Data:............................................................................13
Digital identity issues:...............................................................................................................17
Provider solution issues:............................................................................................................18
Data sensitivity and jurisdiction:...............................................................................................19
Conclusion:....................................................................................................................................20
References:....................................................................................................................................22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction:
The Department of Administrative Services (DAS) is used to provide public services to
the other department s present in the Australian state government. The services that are provided
include the personnel management and HR, management of contract tendering, payroll,
procurement and contractor management. The data centre of the department is responsible for
providing such services.
This report discusses about the approach that is being made by the DAS. This approach is
the Shared Services Approach. The report also includes the securities and the privacy issues that
are associated by adopting the various intended requirements. The report also covers the identity
risks that can be associated with the approach. In addition, the risks of the provider of such
services along with the sensitivity in data are also included in the report.
Discussion:
The main concept to be applied is the Shared Services approach. The main idea of this
approach is to centralize the services that are being provided by the DAS. These services are now
been made to be provided to the whole government. The requirements of this approach are the
need of different departments of the government to migrate their resources to the central server.
The departments who were intending their data and resources for their users now need to upload
the resources to the central servers to incorporate the idea of shared services. This migration will
be done on the DAS central database. After the migration of the data and resources, the DAS will
be responsible for sharing the gathered resources among all the present departments of the
government. This approach is further strengthened by the presence of a government policy that
The Department of Administrative Services (DAS) is used to provide public services to
the other department s present in the Australian state government. The services that are provided
include the personnel management and HR, management of contract tendering, payroll,
procurement and contractor management. The data centre of the department is responsible for
providing such services.
This report discusses about the approach that is being made by the DAS. This approach is
the Shared Services Approach. The report also includes the securities and the privacy issues that
are associated by adopting the various intended requirements. The report also covers the identity
risks that can be associated with the approach. In addition, the risks of the provider of such
services along with the sensitivity in data are also included in the report.
Discussion:
The main concept to be applied is the Shared Services approach. The main idea of this
approach is to centralize the services that are being provided by the DAS. These services are now
been made to be provided to the whole government. The requirements of this approach are the
need of different departments of the government to migrate their resources to the central server.
The departments who were intending their data and resources for their users now need to upload
the resources to the central servers to incorporate the idea of shared services. This migration will
be done on the DAS central database. After the migration of the data and resources, the DAS will
be responsible for sharing the gathered resources among all the present departments of the
government. This approach is further strengthened by the presence of a government policy that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

requires the presence of incorporation of cloud computing architecture for the updating the
services present. The payroll of the DAS will b incorporated in the COTS (Commercial off the
Shelf) application that will help in managing the payroll related services directly from the cloud.
The DAS intranet will also be incorporated in to the Microsoft SharePoint PaaS to provide the
services associated with the intranet to all the departments of the government.
To meet the intended outcomes, the DAS has decided to adopt certain services to help
facilitate the service procurement. Firstly, the DAS is responsible for purchasing a HR and
personnel management application from an US based company. The main idea is to get Software
as a service (SaaS) model. The application software is supposed to include the HR management
and the personnel management application embedded on it. To apply this, the provider of the
application has informed the DAS about their main database situated in Dublin, Ireland.
Along with the HR and personnel management, the DAS will also acquire Contractor
management application software to help visualize and manage the contractor that is being
associated in the DAS.
Security of employee data:
Risks and threats in the in house HR database of the DAS:
The in house of the HR department is subjected to many threats and risks. The traditional
database grants many privileges in case of access and this invites many forms of risks and threats
to the data and resource involved. The first risk to the HR database is the excessive or misuse of
privileges granted (Ted et al., 2013). When employees are given access to the whole system, they
may cause damage depending on the intentions of the employee involved. For example, a banker
with full access to the employee savings account may change the data of any other employee to
services present. The payroll of the DAS will b incorporated in the COTS (Commercial off the
Shelf) application that will help in managing the payroll related services directly from the cloud.
The DAS intranet will also be incorporated in to the Microsoft SharePoint PaaS to provide the
services associated with the intranet to all the departments of the government.
To meet the intended outcomes, the DAS has decided to adopt certain services to help
facilitate the service procurement. Firstly, the DAS is responsible for purchasing a HR and
personnel management application from an US based company. The main idea is to get Software
as a service (SaaS) model. The application software is supposed to include the HR management
and the personnel management application embedded on it. To apply this, the provider of the
application has informed the DAS about their main database situated in Dublin, Ireland.
Along with the HR and personnel management, the DAS will also acquire Contractor
management application software to help visualize and manage the contractor that is being
associated in the DAS.
Security of employee data:
Risks and threats in the in house HR database of the DAS:
The in house of the HR department is subjected to many threats and risks. The traditional
database grants many privileges in case of access and this invites many forms of risks and threats
to the data and resource involved. The first risk to the HR database is the excessive or misuse of
privileges granted (Ted et al., 2013). When employees are given access to the whole system, they
may cause damage depending on the intentions of the employee involved. For example, a banker
with full access to the employee savings account may change the data of any other employee to

create a nuisance in the flow of operation. In addition, when an employee is terminated, the
access to the information remains and due to the change in emotional stability, the access of such
data can create problems by hampering the operation of the company or organization involved.
This unnecessary risk arises due to the acquisitions of full access to the database involved. The
more privilege given to an employee, the more vulnerable and the more prone to attacks the
system gets.
Risks and threats are also provided when an unauthorized user tries to get access to the
system by attacking the system (Aloul et al., 2012). This is termed as a cyber attack. The HR
database is the traditional one and for accessing this in an unauthorized process, the SQL
injection attack is used. This attack gives the rogue user access to the entire database and crucial
information is unethically accessed using this process. This is also another threat as it may affect
the security related aspects of the employees. Malware is also another form of unauthorized
access and the infected system is not aware of the state of it. The employees or users still work
on the infected computer and their information is unethically accessed. This is also another risk
to the employee data as the security and privacy of the data and resources are hampered. The
more information a data centre possesses, the more vulnerable and the more prone to attacks the
system gets.
The transactions that are ongoing in any company or organization involved must be
recorded automatically in the database servers. The failure to comply with such process may lead
to problems to be associated with the organizations as well as the employees concerned (Arasu et
al., 2013). For example, the transactions of one month for salary might not be recorded and the
database may show that the employees have their salaries even in the next month and might not
avail for the salary acquisition. This may lead to employee related problems. Organizations or
access to the information remains and due to the change in emotional stability, the access of such
data can create problems by hampering the operation of the company or organization involved.
This unnecessary risk arises due to the acquisitions of full access to the database involved. The
more privilege given to an employee, the more vulnerable and the more prone to attacks the
system gets.
Risks and threats are also provided when an unauthorized user tries to get access to the
system by attacking the system (Aloul et al., 2012). This is termed as a cyber attack. The HR
database is the traditional one and for accessing this in an unauthorized process, the SQL
injection attack is used. This attack gives the rogue user access to the entire database and crucial
information is unethically accessed using this process. This is also another threat as it may affect
the security related aspects of the employees. Malware is also another form of unauthorized
access and the infected system is not aware of the state of it. The employees or users still work
on the infected computer and their information is unethically accessed. This is also another risk
to the employee data as the security and privacy of the data and resources are hampered. The
more information a data centre possesses, the more vulnerable and the more prone to attacks the
system gets.
The transactions that are ongoing in any company or organization involved must be
recorded automatically in the database servers. The failure to comply with such process may lead
to problems to be associated with the organizations as well as the employees concerned (Arasu et
al., 2013). For example, the transactions of one month for salary might not be recorded and the
database may show that the employees have their salaries even in the next month and might not
avail for the salary acquisition. This may lead to employee related problems. Organizations or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

companies with poor auditing mechanism face difficulties in streamlining their operations. As, a
result the companies or organizations involved turn to third party providers to give access to
system that helps in auditing. However, the most important thing to consider is the user interface
and detailed mechanism. The detailed mechanism of the third party processes do not consider all
the detailed transactions and thus fail to store all the information in the database (Jeun, Lee &
Won, 2012). Moreover, the software may use different platforms like the DB2 and the MS-SQL
logs, which are not compatible with the organizational structure. This also imposes another
constraint in the process of operation and affects the security and operation of the concerned
individuals.
Employee data is also hampered during security breaches for the backup disks in the system. As
the backup data is always unprotected, the breach to get such data is always prominent (Moore,
Spink & Lipp, 2012). The information present in the hacked database affects the concerned
resource of the organization or companies involved or the employees concerned. The more
information a data centre possesses, the more vulnerable and the more prone to attacks the
system gets.
Risks and threats after migration to SaaS application:
Security is a main concern which needs considering even after the incorporation of a new
project. Though the SaaS architecture is a new model, which is being used by many business
organizations or companies, the risks and threats associated with it are always considered (Chou,
2013). The risks are due to the presence of integration of the information in its internal data
center. The more information a data centre possesses, the more vulnerable and the more prone to
attacks the system gets.
result the companies or organizations involved turn to third party providers to give access to
system that helps in auditing. However, the most important thing to consider is the user interface
and detailed mechanism. The detailed mechanism of the third party processes do not consider all
the detailed transactions and thus fail to store all the information in the database (Jeun, Lee &
Won, 2012). Moreover, the software may use different platforms like the DB2 and the MS-SQL
logs, which are not compatible with the organizational structure. This also imposes another
constraint in the process of operation and affects the security and operation of the concerned
individuals.
Employee data is also hampered during security breaches for the backup disks in the system. As
the backup data is always unprotected, the breach to get such data is always prominent (Moore,
Spink & Lipp, 2012). The information present in the hacked database affects the concerned
resource of the organization or companies involved or the employees concerned. The more
information a data centre possesses, the more vulnerable and the more prone to attacks the
system gets.
Risks and threats after migration to SaaS application:
Security is a main concern which needs considering even after the incorporation of a new
project. Though the SaaS architecture is a new model, which is being used by many business
organizations or companies, the risks and threats associated with it are always considered (Chou,
2013). The risks are due to the presence of integration of the information in its internal data
center. The more information a data centre possesses, the more vulnerable and the more prone to
attacks the system gets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As the step to integration of information and resources to the SaaS needs the access of
such information to the third-party service providers, the question for access and consistency
always remains the same (Hussein & Khalid, 2016). This is the reason for employee and
company problems regarding who gets the access to their information.
Another risk that is present due to the presence of SaaS application is the instability due
to unavailability of the providers. As the services provided by the SaaS applications are great,
many companies and organizations are adopting the concept (Alani, 2014). This has made a need
for competition in the market among the providers of such services. However, not all companies
can take such investments and this creates problem in the competition, which may result in loss
of business of some providers. It may happen sometimes that the services taken from the
provider are no longer available due to their unavailability. The problem for employee data as
well as organizational resource hampering is the main thing affected by such risks. This risk is to
be considered before adoption of such services and the company needs to consider their policies
of mitigating such problems.
Transparency is a concern among the organization accessing the application services
from the third-part vendors. The providers are often very secretive about their operation and
assure the clients about the services that are being provided. This is the reason of developing
distrust in the relationship among the providers and the clients (Lee, 2012). This results in less
data to be shared to them and creates vulnerabilities in security regarding the employee
information or organizational resources. Though the providers have reason to believe that hiding
the information about their centers can help in minimizing the risks associated with the
disclosure of information, the question of transparency still lies in the relationship.
such information to the third-party service providers, the question for access and consistency
always remains the same (Hussein & Khalid, 2016). This is the reason for employee and
company problems regarding who gets the access to their information.
Another risk that is present due to the presence of SaaS application is the instability due
to unavailability of the providers. As the services provided by the SaaS applications are great,
many companies and organizations are adopting the concept (Alani, 2014). This has made a need
for competition in the market among the providers of such services. However, not all companies
can take such investments and this creates problem in the competition, which may result in loss
of business of some providers. It may happen sometimes that the services taken from the
provider are no longer available due to their unavailability. The problem for employee data as
well as organizational resource hampering is the main thing affected by such risks. This risk is to
be considered before adoption of such services and the company needs to consider their policies
of mitigating such problems.
Transparency is a concern among the organization accessing the application services
from the third-part vendors. The providers are often very secretive about their operation and
assure the clients about the services that are being provided. This is the reason of developing
distrust in the relationship among the providers and the clients (Lee, 2012). This results in less
data to be shared to them and creates vulnerabilities in security regarding the employee
information or organizational resources. Though the providers have reason to believe that hiding
the information about their centers can help in minimizing the risks associated with the
disclosure of information, the question of transparency still lies in the relationship.
Identity theft is another aspect, which requires security to be implemented. The providers
of the services require payment for providing the services. This is done by taking the credit card
information and then the payment is done. The risk it implies is still an ethical issue among many
users. The unethical providers are to be recognized before passing on the information of payment
related services to them as the use of this information can be used for doing wrong things
(Prasanth, 2012). The employees associated with the adoption of such services may pass the
payment information before researching about the vendors and unethical doings can be caused
by that. This is termed as identity theft.
In addition, the information shared with the application providers are not in control of the
individuals whose information is passed (Agrawal, El Abbadi & Wang, 2013). This results in
unease and absence in mind as the employee concerned is directly impacted in case of any
actions taken that affects their security and privacy.
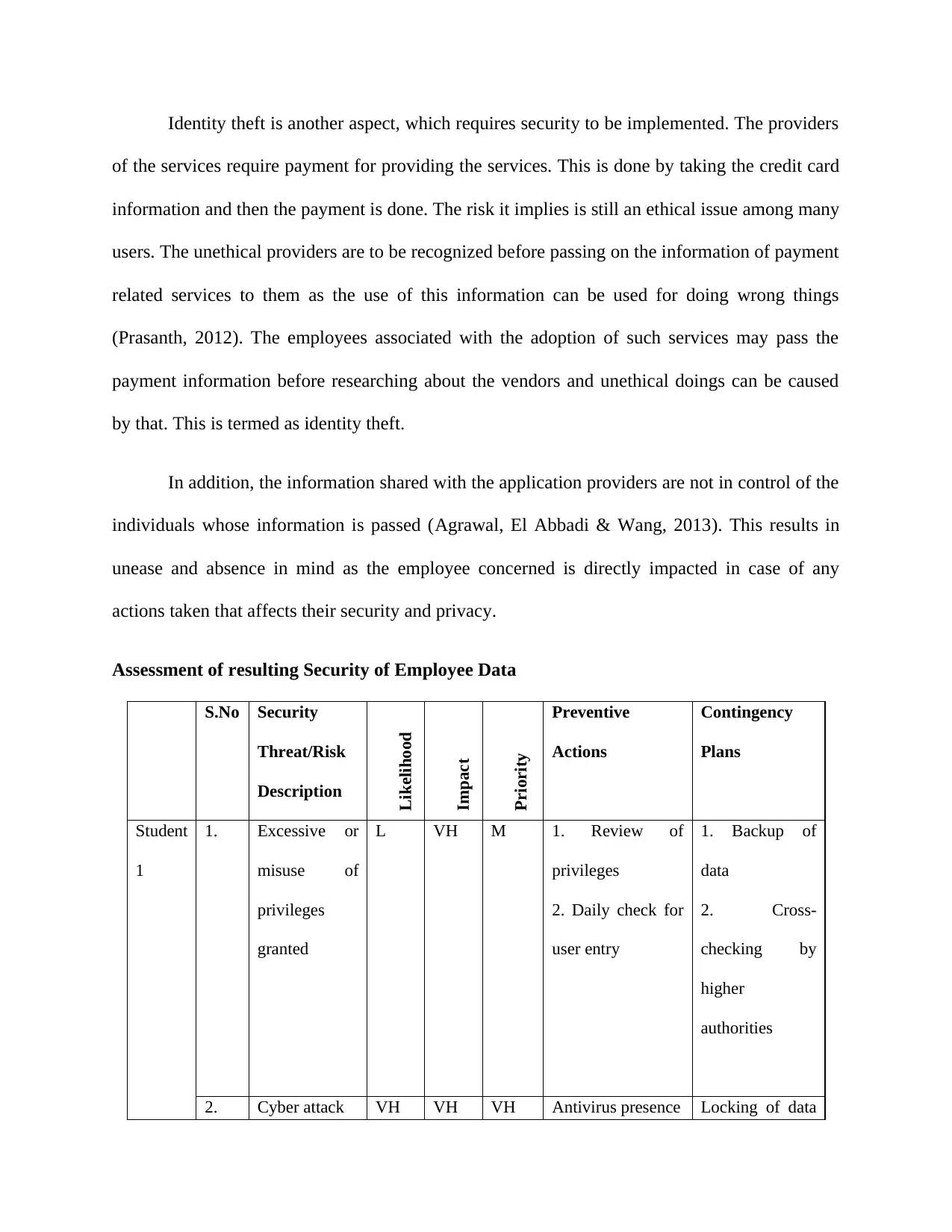
Assessment of resulting Security of Employee Data
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive
Actions
Contingency
Plans
Student
1
1. Excessive or
misuse of
privileges
granted
L VH M 1. Review of
privileges
2. Daily check for
user entry
1. Backup of
data
2. Cross-
checking by
higher
authorities
2. Cyber attack VH VH VH Antivirus presence Locking of data
of the services require payment for providing the services. This is done by taking the credit card
information and then the payment is done. The risk it implies is still an ethical issue among many
users. The unethical providers are to be recognized before passing on the information of payment
related services to them as the use of this information can be used for doing wrong things
(Prasanth, 2012). The employees associated with the adoption of such services may pass the
payment information before researching about the vendors and unethical doings can be caused
by that. This is termed as identity theft.
In addition, the information shared with the application providers are not in control of the
individuals whose information is passed (Agrawal, El Abbadi & Wang, 2013). This results in
unease and absence in mind as the employee concerned is directly impacted in case of any
actions taken that affects their security and privacy.
Assessment of resulting Security of Employee Data
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive
Actions
Contingency
Plans
Student
1
1. Excessive or
misuse of
privileges
granted
L VH M 1. Review of
privileges
2. Daily check for
user entry
1. Backup of
data
2. Cross-
checking by
higher
authorities
2. Cyber attack VH VH VH Antivirus presence Locking of data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
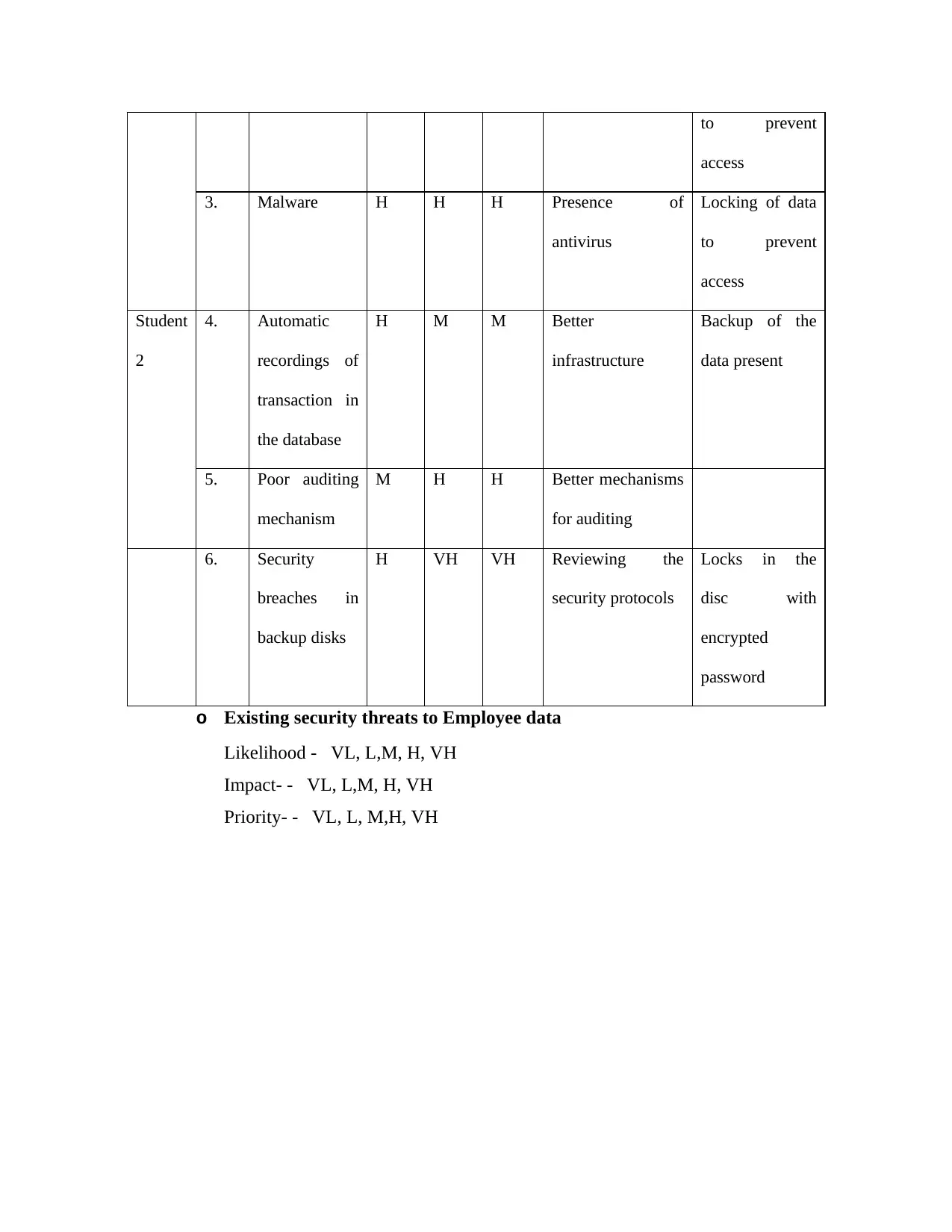
to prevent
access
3. Malware H H H Presence of
antivirus
Locking of data
to prevent
access
Student
2
4. Automatic
recordings of
transaction in
the database
H M M Better
infrastructure
Backup of the
data present
5. Poor auditing
mechanism
M H H Better mechanisms
for auditing
6. Security
breaches in
backup disks
H VH VH Reviewing the
security protocols
Locks in the
disc with
encrypted
password
o Existing security threats to Employee data
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
access
3. Malware H H H Presence of
antivirus
Locking of data
to prevent
access
Student
2
4. Automatic
recordings of
transaction in
the database
H M M Better
infrastructure
Backup of the
data present
5. Poor auditing
mechanism
M H H Better mechanisms
for auditing
6. Security
breaches in
backup disks
H VH VH Reviewing the
security protocols
Locks in the
disc with
encrypted
password
o Existing security threats to Employee data
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
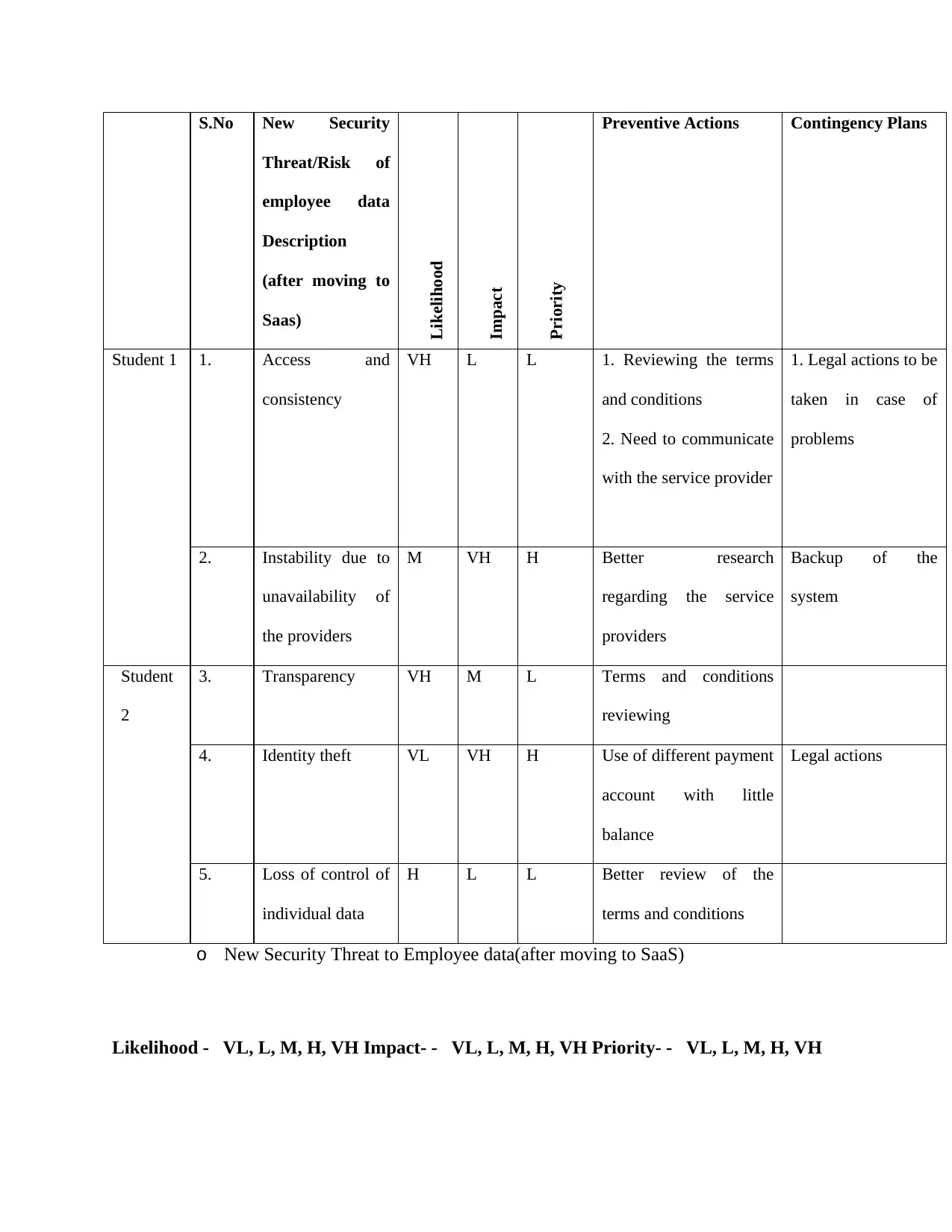
S.No New Security
Threat/Risk of
employee data
Description
(after moving to
Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1 1. Access and
consistency
VH L L 1. Reviewing the terms
and conditions
2. Need to communicate
with the service provider
1. Legal actions to be
taken in case of
problems
2. Instability due to
unavailability of
the providers
M VH H Better research
regarding the service
providers
Backup of the
system
Student
2
3. Transparency VH M L Terms and conditions
reviewing
4. Identity theft VL VH H Use of different payment
account with little
balance
Legal actions
5. Loss of control of
individual data
H L L Better review of the
terms and conditions
o New Security Threat to Employee data(after moving to SaaS)
Likelihood - VL, L, M, H, VH Impact- - VL, L, M, H, VH Priority- - VL, L, M, H, VH
Threat/Risk of
employee data
Description
(after moving to
Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1 1. Access and
consistency
VH L L 1. Reviewing the terms
and conditions
2. Need to communicate
with the service provider
1. Legal actions to be
taken in case of
problems
2. Instability due to
unavailability of
the providers
M VH H Better research
regarding the service
providers
Backup of the
system
Student
2
3. Transparency VH M L Terms and conditions
reviewing
4. Identity theft VL VH H Use of different payment
account with little
balance
Legal actions
5. Loss of control of
individual data
H L L Better review of the
terms and conditions
o New Security Threat to Employee data(after moving to SaaS)
Likelihood - VL, L, M, H, VH Impact- - VL, L, M, H, VH Priority- - VL, L, M, H, VH
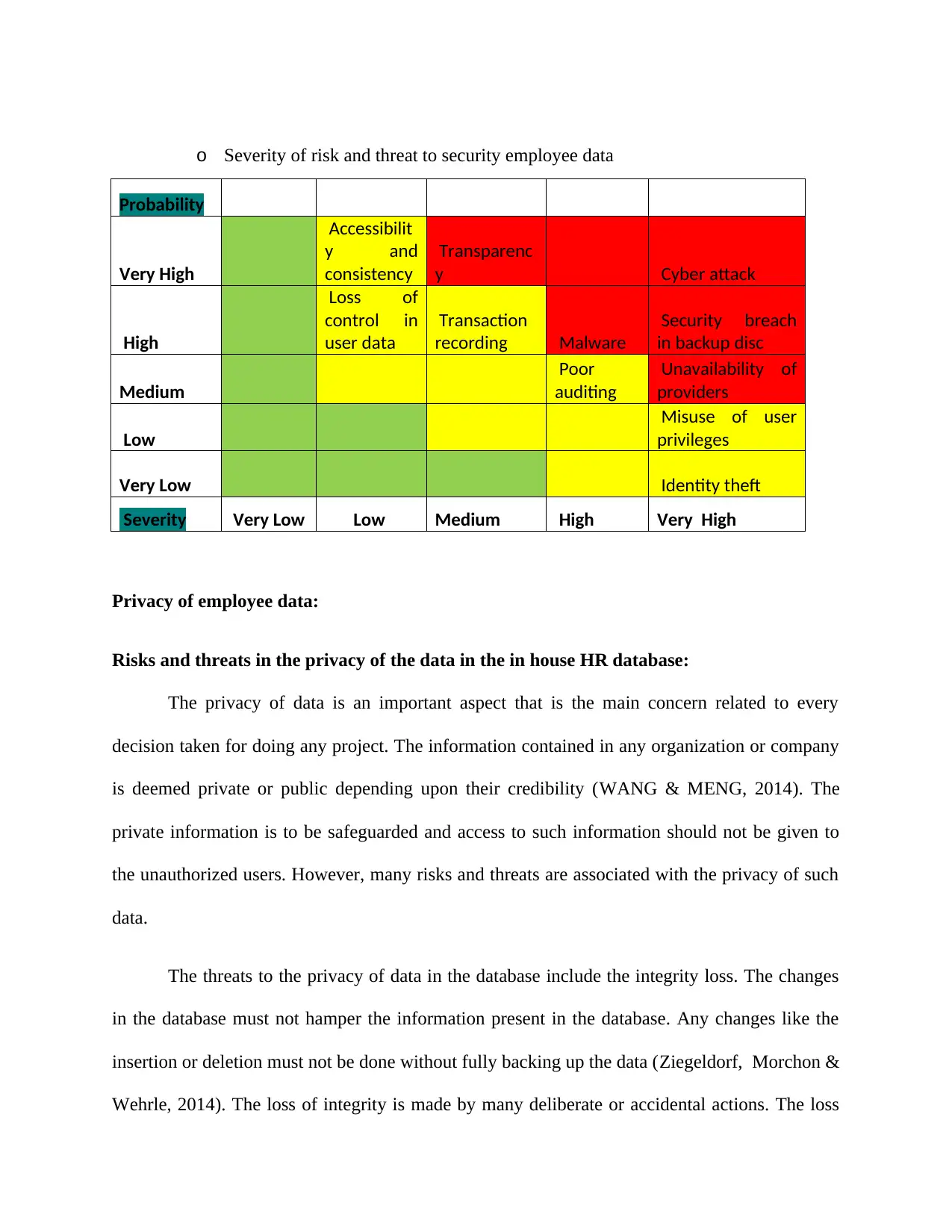
o Severity of risk and threat to security employee data
Probability
Very High
Accessibilit
y and
consistency
Transparenc
y Cyber attack
High
Loss of
control in
user data
Transaction
recording Malware
Security breach
in backup disc
Medium
Poor
auditing
Unavailability of
providers
Low
Misuse of user
privileges
Very Low Identity theft
Severity Very Low Low Medium High Very High
Privacy of employee data:
Risks and threats in the privacy of the data in the in house HR database:
The privacy of data is an important aspect that is the main concern related to every
decision taken for doing any project. The information contained in any organization or company
is deemed private or public depending upon their credibility (WANG & MENG, 2014). The
private information is to be safeguarded and access to such information should not be given to
the unauthorized users. However, many risks and threats are associated with the privacy of such
data.
The threats to the privacy of data in the database include the integrity loss. The changes
in the database must not hamper the information present in the database. Any changes like the
insertion or deletion must not be done without fully backing up the data (Ziegeldorf, Morchon &
Wehrle, 2014). The loss of integrity is made by many deliberate or accidental actions. The loss
Probability
Very High
Accessibilit
y and
consistency
Transparenc
y Cyber attack
High
Loss of
control in
user data
Transaction
recording Malware
Security breach
in backup disc
Medium
Poor
auditing
Unavailability of
providers
Low
Misuse of user
privileges
Very Low Identity theft
Severity Very Low Low Medium High Very High
Privacy of employee data:
Risks and threats in the privacy of the data in the in house HR database:
The privacy of data is an important aspect that is the main concern related to every
decision taken for doing any project. The information contained in any organization or company
is deemed private or public depending upon their credibility (WANG & MENG, 2014). The
private information is to be safeguarded and access to such information should not be given to
the unauthorized users. However, many risks and threats are associated with the privacy of such
data.
The threats to the privacy of data in the database include the integrity loss. The changes
in the database must not hamper the information present in the database. Any changes like the
insertion or deletion must not be done without fully backing up the data (Ziegeldorf, Morchon &
Wehrle, 2014). The loss of integrity is made by many deliberate or accidental actions. The loss
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





