Comprehensive VPN Design, Implementation, and Security Analysis
VerifiedAdded on 2020/03/23
|10
|1797
|334
Project
AI Summary
This project focuses on the design and implementation of a Virtual Private Network (VPN) for small and medium-sized enterprises (SMEs). It encompasses a detailed analysis of VPN technology, including its introduction, scopes, and limitations. The project outlines the hardware and software requirements, logical and physical designs, network topologies, and IP addressing schemes necessary for a functional VPN. It delves into the security features and policies, emphasizing the reduction of cyber-attack risks and the enhancement of productivity and security. The assignment also covers redundancy and failover plans, including IPsec stateful failover and hot standby routing protocol for high availability. Furthermore, the project explores the implementation of VPN services and concludes with a discussion on the overall benefits and considerations for SMEs. The document provides a comprehensive guide to VPN design, security, and implementation, offering valuable insights for network administrators and IT professionals. The project is contributed by a student to be published on the website Desklib, a platform which provides all the necessary AI based study tools for students.

VIRTUAL PRIVATE NETWORK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction...................................................................................................................................2
2. Scopes............................................................................................................................................2
3. Limitations.....................................................................................................................................2
4. Requirements................................................................................................................................2
5. Solution Diagram...........................................................................................................................3
5.1 Logical Design........................................................................................................................3
5.2 Physical Design......................................................................................................................5
5.3 Network Topologies...............................................................................................................5
5.4 IP addressing..........................................................................................................................6
5.5 Security Features and Policies...............................................................................................6
5.6 Redundancy and Failover Plans.............................................................................................7
5.7 VPN service Implementation.................................................................................................8
6. Conclusion.....................................................................................................................................8
References.............................................................................................................................................8
1
1. Introduction...................................................................................................................................2
2. Scopes............................................................................................................................................2
3. Limitations.....................................................................................................................................2
4. Requirements................................................................................................................................2
5. Solution Diagram...........................................................................................................................3
5.1 Logical Design........................................................................................................................3
5.2 Physical Design......................................................................................................................5
5.3 Network Topologies...............................................................................................................5
5.4 IP addressing..........................................................................................................................6
5.5 Security Features and Policies...............................................................................................6
5.6 Redundancy and Failover Plans.............................................................................................7
5.7 VPN service Implementation.................................................................................................8
6. Conclusion.....................................................................................................................................8
References.............................................................................................................................................8
1

1. Introduction
The virtual private network is a technology that makes an encrypted and safe connection
through a network. It was developed as a way to allow a remoter users and branches offices to
securely accessing the application and resources. It provides the safety for data travels through the
secure Tunnels. The VPN users are should be using the authentication methods to avoid the hacking.
The authentication methods are passwords identification. token identification and unique
identification to gain the access to the VPN. The Small and medium enterprise using the VPN
network for accessing the remote connection and it provides the security and productivity for a
business data and functions. The VPN logical and physical design will be done. The hardware and
software requirement for VPN network design will be identified. The Network design IP addressing
will be identified. The VPN security features and policies will be discussed. VPN services are will be
implemented.
2. Scopes
Main scope of this project is to create and design VPN connection for small and medium sized
enterprise. The Network design includes the logical and physical design. These two designs will be
created and analysed in detail. The VPN connection security features and policies are will be
analysed. The VPN services are will be implemented [1].
3. Limitations
The VPN connection has various limitations. These are listed below.
VPN requires the detailed understanding of network security issues and careful
configuration and installation to ensure the sufficient protection on a network.
The Performance and reliability of an VPN is not based on Organization direct control.
The VPN products and solutions are using the same vendor because the different vendors
have not always been compatible. It Provides the VPN technology issues [2].
4. Requirements
The small and medium enterprise VPN network component is shown in below.
Component Quantity Products
2
The virtual private network is a technology that makes an encrypted and safe connection
through a network. It was developed as a way to allow a remoter users and branches offices to
securely accessing the application and resources. It provides the safety for data travels through the
secure Tunnels. The VPN users are should be using the authentication methods to avoid the hacking.
The authentication methods are passwords identification. token identification and unique
identification to gain the access to the VPN. The Small and medium enterprise using the VPN
network for accessing the remote connection and it provides the security and productivity for a
business data and functions. The VPN logical and physical design will be done. The hardware and
software requirement for VPN network design will be identified. The Network design IP addressing
will be identified. The VPN security features and policies will be discussed. VPN services are will be
implemented.
2. Scopes
Main scope of this project is to create and design VPN connection for small and medium sized
enterprise. The Network design includes the logical and physical design. These two designs will be
created and analysed in detail. The VPN connection security features and policies are will be
analysed. The VPN services are will be implemented [1].
3. Limitations
The VPN connection has various limitations. These are listed below.
VPN requires the detailed understanding of network security issues and careful
configuration and installation to ensure the sufficient protection on a network.
The Performance and reliability of an VPN is not based on Organization direct control.
The VPN products and solutions are using the same vendor because the different vendors
have not always been compatible. It Provides the VPN technology issues [2].
4. Requirements
The small and medium enterprise VPN network component is shown in below.
Component Quantity Products
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Computers 4 Dell Computers
Printer 4 Canon Printers
Router 1 Cisco 1800 Series Routers
Switches 1 Cisco Small Business 500 Series Switch
Access point 4 Cisco Aironet 3602I Series Access Point
Server 1 Cisco UCS C220 M4 Rack Server
Firewall 1 Cisco ASA 5505 Firewall Edition Bundle - security
appliance
Operating System - Windows 7
Memory - 2 GB RAM
Hard Drive - 2.2 GB
5. Solution Diagram
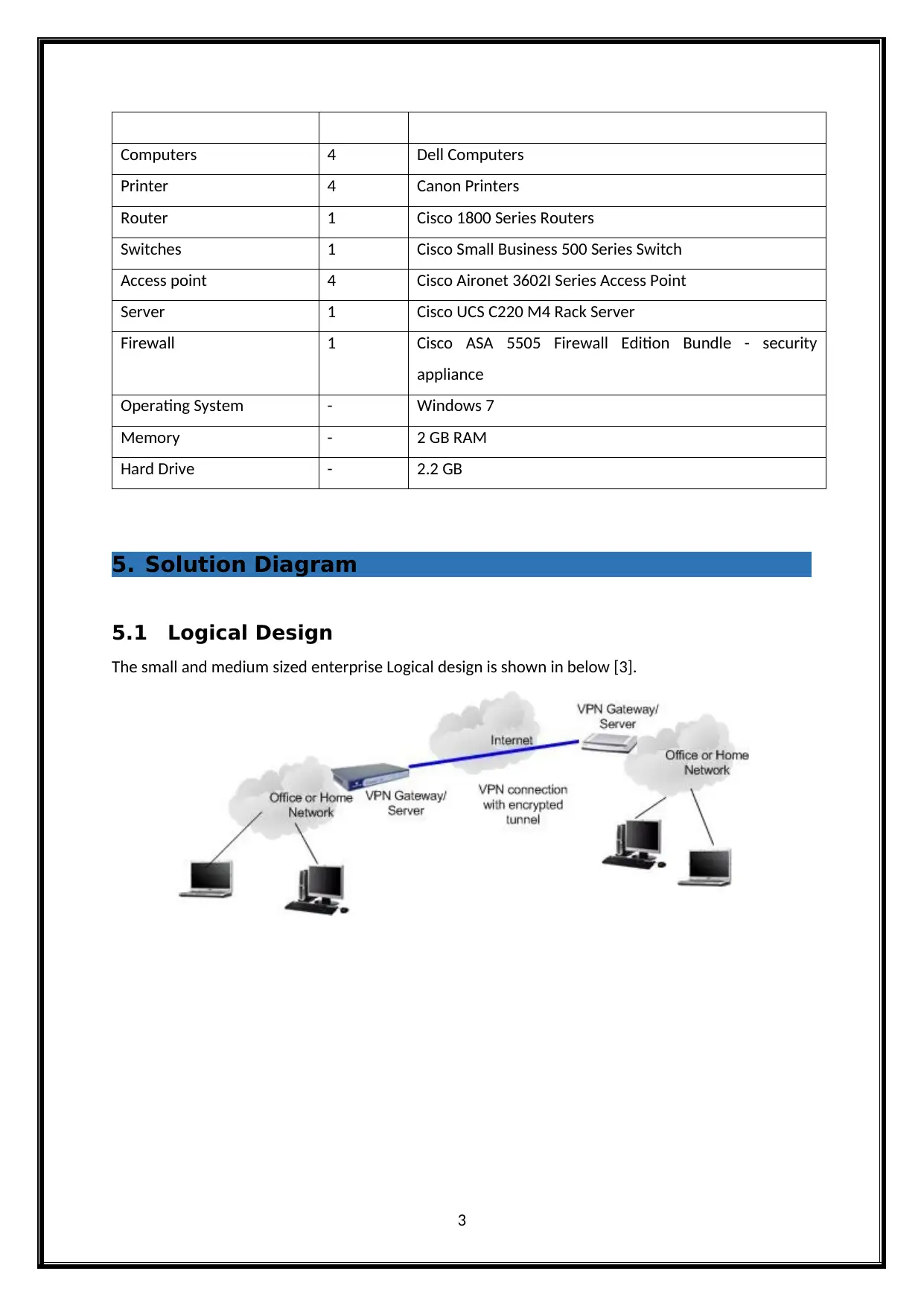
5.1 Logical Design
The small and medium sized enterprise Logical design is shown in below [3].
3
Printer 4 Canon Printers
Router 1 Cisco 1800 Series Routers
Switches 1 Cisco Small Business 500 Series Switch
Access point 4 Cisco Aironet 3602I Series Access Point
Server 1 Cisco UCS C220 M4 Rack Server
Firewall 1 Cisco ASA 5505 Firewall Edition Bundle - security
appliance
Operating System - Windows 7
Memory - 2 GB RAM
Hard Drive - 2.2 GB
5. Solution Diagram
5.1 Logical Design
The small and medium sized enterprise Logical design is shown in below [3].
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
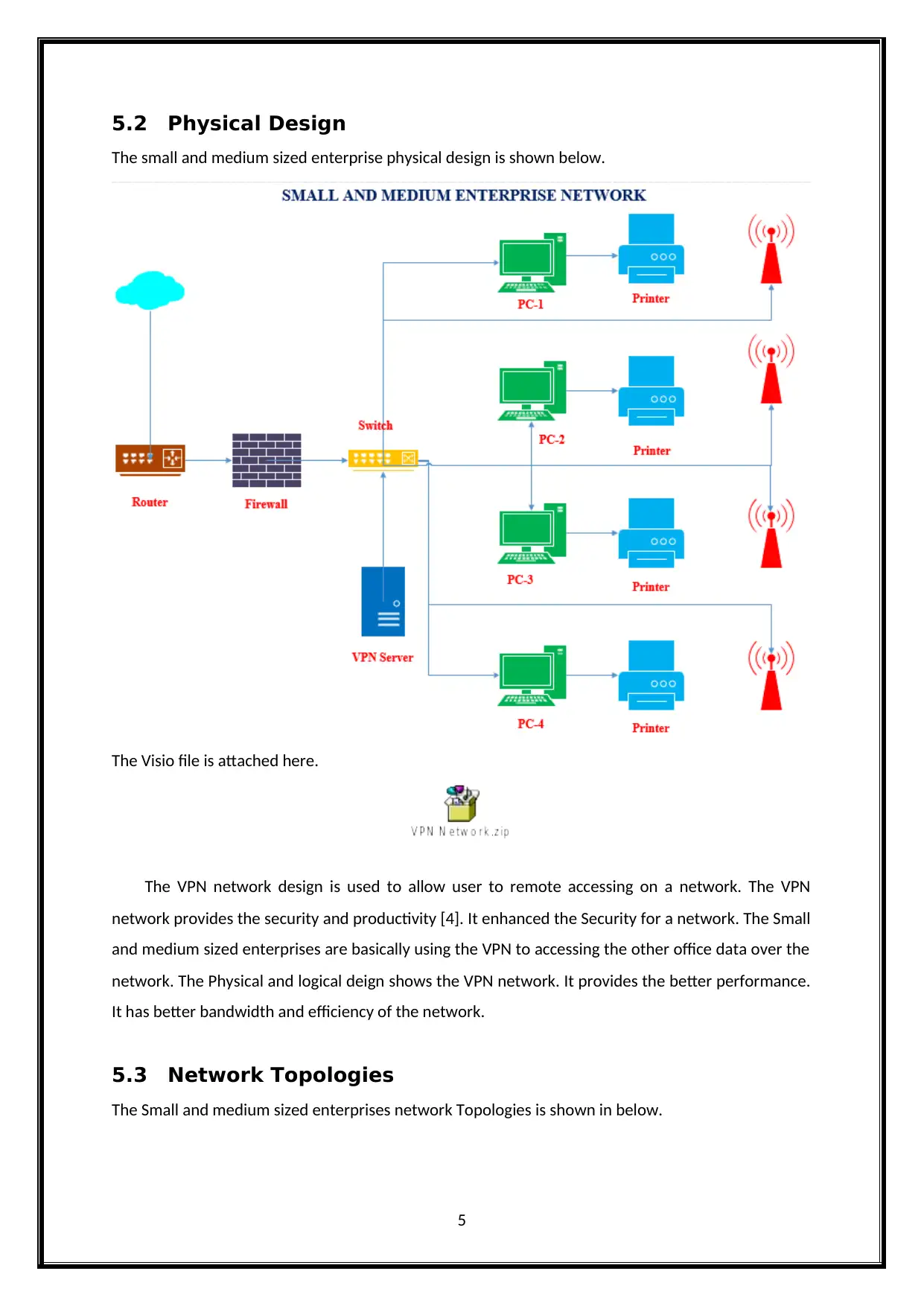
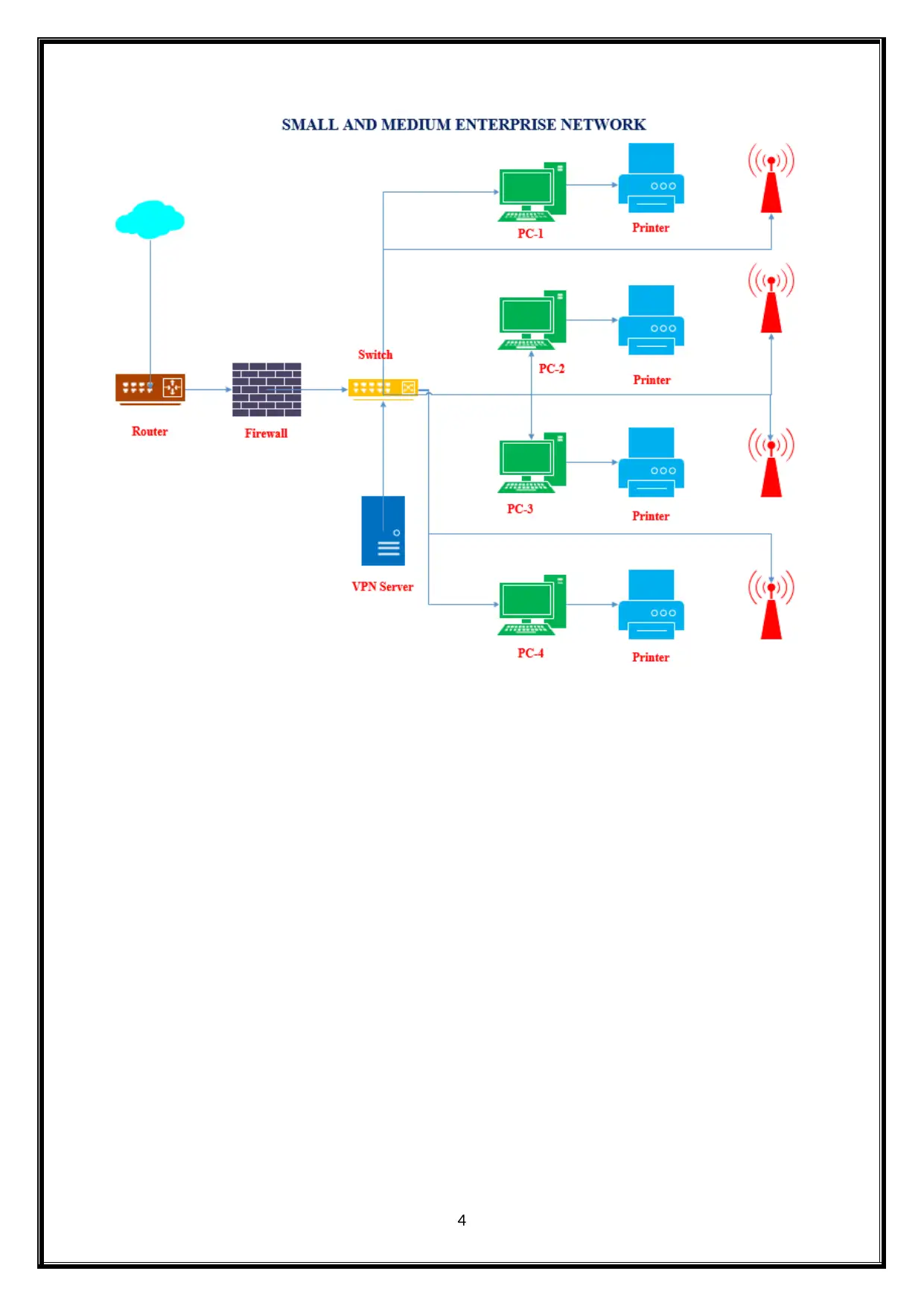
5.2 Physical Design
The small and medium sized enterprise physical design is shown below.
The Visio file is attached here.
The VPN network design is used to allow user to remote accessing on a network. The VPN
network provides the security and productivity [4]. It enhanced the Security for a network. The Small
and medium sized enterprises are basically using the VPN to accessing the other office data over the
network. The Physical and logical deign shows the VPN network. It provides the better performance.
It has better bandwidth and efficiency of the network.
5.3 Network Topologies
The Small and medium sized enterprises network Topologies is shown in below.
5
The small and medium sized enterprise physical design is shown below.
The Visio file is attached here.
The VPN network design is used to allow user to remote accessing on a network. The VPN
network provides the security and productivity [4]. It enhanced the Security for a network. The Small
and medium sized enterprises are basically using the VPN to accessing the other office data over the
network. The Physical and logical deign shows the VPN network. It provides the better performance.
It has better bandwidth and efficiency of the network.
5.3 Network Topologies
The Small and medium sized enterprises network Topologies is shown in below.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
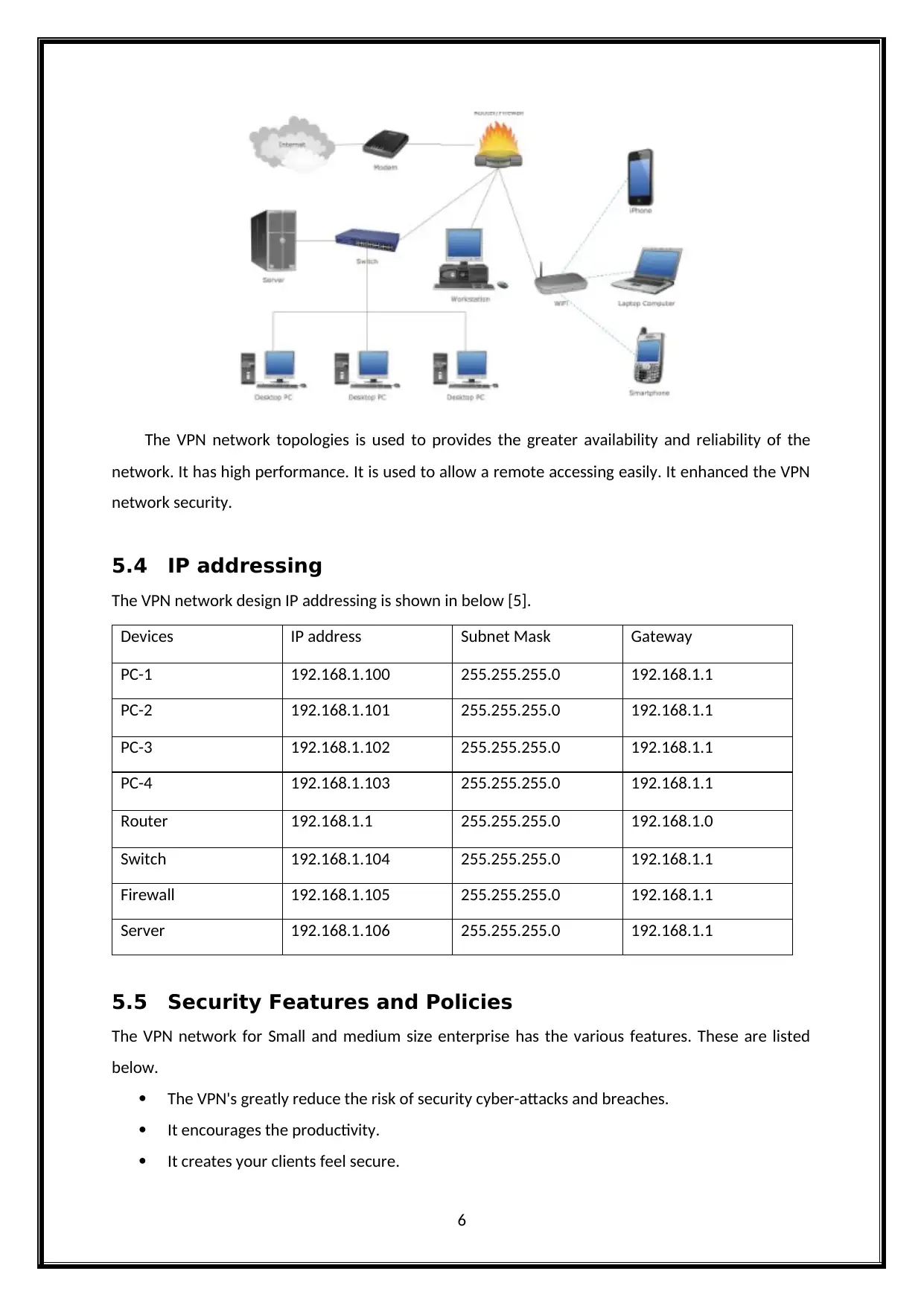
The VPN network topologies is used to provides the greater availability and reliability of the
network. It has high performance. It is used to allow a remote accessing easily. It enhanced the VPN
network security.
5.4 IP addressing
The VPN network design IP addressing is shown in below [5].
Devices IP address Subnet Mask Gateway
PC-1 192.168.1.100 255.255.255.0 192.168.1.1
PC-2 192.168.1.101 255.255.255.0 192.168.1.1
PC-3 192.168.1.102 255.255.255.0 192.168.1.1
PC-4 192.168.1.103 255.255.255.0 192.168.1.1
Router 192.168.1.1 255.255.255.0 192.168.1.0
Switch 192.168.1.104 255.255.255.0 192.168.1.1
Firewall 192.168.1.105 255.255.255.0 192.168.1.1
Server 192.168.1.106 255.255.255.0 192.168.1.1
5.5 Security Features and Policies
The VPN network for Small and medium size enterprise has the various features. These are listed
below.
The VPN's greatly reduce the risk of security cyber-attacks and breaches.
It encourages the productivity.
It creates your clients feel secure.
6
network. It has high performance. It is used to allow a remote accessing easily. It enhanced the VPN
network security.
5.4 IP addressing
The VPN network design IP addressing is shown in below [5].
Devices IP address Subnet Mask Gateway
PC-1 192.168.1.100 255.255.255.0 192.168.1.1
PC-2 192.168.1.101 255.255.255.0 192.168.1.1
PC-3 192.168.1.102 255.255.255.0 192.168.1.1
PC-4 192.168.1.103 255.255.255.0 192.168.1.1
Router 192.168.1.1 255.255.255.0 192.168.1.0
Switch 192.168.1.104 255.255.255.0 192.168.1.1
Firewall 192.168.1.105 255.255.255.0 192.168.1.1
Server 192.168.1.106 255.255.255.0 192.168.1.1
5.5 Security Features and Policies
The VPN network for Small and medium size enterprise has the various features. These are listed
below.
The VPN's greatly reduce the risk of security cyber-attacks and breaches.
It encourages the productivity.
It creates your clients feel secure.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Virtual private networks are surprisingly affordable [6].
It enhanced the security when network connect to the VPN network.
IT has great advantage of having a VPN is that the information can be accessed remotely.
It easily shares the files.
It blocks the unwanted websites.
User need an IP address from another country, the VPN easily provide the IP address.
It also provides the better network performance.
It has greater bandwidth and efficiency of the network.
It reduces the maintenance costs [7].
VPN security Policies are listed below.
The VPN security policies are used to allow IP traffic to pass between the interfaces. User want
to limit communication to specific traffic by specifying the destination and source addresses. The
VPN policies requires the IPsec security policy. Th single policy can be enable the traffic outbound,
inbound or both directions. The route based VPN policy requires the Accept security policy for in
bound and out bound direction for specify the interface to the private network. The VPN network
defining the multiple IP sec policies for a same tunnel [8].
5.6 Redundancy and Failover Plans
The High availability VPN has the IP sec stateful failover. It is one of the features for VPN
network. It enables a router to continue processing a transmitting the packets after out planned or
planned outage. the IP sec stateful failover is designed work in hot standby router protocol and
reverse route injection with IPsec. These two protocols are used to provide the more IPsec with
Reverse router injection is designed to simplify the VPN design and it requires the redundancy and
routing. It works with static and dynamic crypt maps [9]. It causes the traffic flows by requiring the
IPsec to VPN router for correct security association. It is used to avoid IPsec policy mismatches.
Reliable design for VPNs. and it reduce the configuration complexity on the remote peers. the Hot
standby routing protocol is used to provide the high network availability for VPN by routing the IP
traffic from hosts. To provide the network redundancy for IP networks by recovering the user traffic
immediately in network access. the Network administrator easily enables the HSRP and assign the
virtual IP address and also enables the IPsec stateful failover to verify the all processes are running
or not in VPN network by uses the shown crypto isakmp, show crypto IPsec and show ssp
7
It enhanced the security when network connect to the VPN network.
IT has great advantage of having a VPN is that the information can be accessed remotely.
It easily shares the files.
It blocks the unwanted websites.
User need an IP address from another country, the VPN easily provide the IP address.
It also provides the better network performance.
It has greater bandwidth and efficiency of the network.
It reduces the maintenance costs [7].
VPN security Policies are listed below.
The VPN security policies are used to allow IP traffic to pass between the interfaces. User want
to limit communication to specific traffic by specifying the destination and source addresses. The
VPN policies requires the IPsec security policy. Th single policy can be enable the traffic outbound,
inbound or both directions. The route based VPN policy requires the Accept security policy for in
bound and out bound direction for specify the interface to the private network. The VPN network
defining the multiple IP sec policies for a same tunnel [8].
5.6 Redundancy and Failover Plans
The High availability VPN has the IP sec stateful failover. It is one of the features for VPN
network. It enables a router to continue processing a transmitting the packets after out planned or
planned outage. the IP sec stateful failover is designed work in hot standby router protocol and
reverse route injection with IPsec. These two protocols are used to provide the more IPsec with
Reverse router injection is designed to simplify the VPN design and it requires the redundancy and
routing. It works with static and dynamic crypt maps [9]. It causes the traffic flows by requiring the
IPsec to VPN router for correct security association. It is used to avoid IPsec policy mismatches.
Reliable design for VPNs. and it reduce the configuration complexity on the remote peers. the Hot
standby routing protocol is used to provide the high network availability for VPN by routing the IP
traffic from hosts. To provide the network redundancy for IP networks by recovering the user traffic
immediately in network access. the Network administrator easily enables the HSRP and assign the
virtual IP address and also enables the IPsec stateful failover to verify the all processes are running
or not in VPN network by uses the shown crypto isakmp, show crypto IPsec and show ssp
7

5.7 VPN service Implementation
The Implementation of VPN service is used to protect the business data and it provide user with
a host of additional functions. The best business VPN services are listed below.
PureVPN
SaferVPN
HideMyAss
IbVPN
VyprVPN
The VPN service implementation is to ensure the user network connection has static IP address.
Many small and medium business class DSL and cable connections uses the dynamic address that is
IP address of the network connections changes occasionally. But IP address changes, the remote
user does not know the new address. So, the remote users are does not connect network. Most of
small and medium business class DSL and cable providers are use the static addressing. the Static
addressing connect the remote users always on the network. It has sufficient upstream bandwidth to
support the remote users and it also has the better network speed [10].
6. Conclusion
The Virtual private network for Small and medium sized enterprise is analysed and discussed
in detail. The VPN network was created and designed in successfully. The VPN network provides the
greater performance for SME’s. It also provides the productivity and security. The VPN network
design hardware and software components was identified and analysed in detail. The Network
design IP addressing was successfully identified. The VPN security features and policies are analysed
and discussed. The Implementation of VPN services is discussed in detail.
References
[1]i. Team, "8 advantages of using VPN - ibVPN.com", ibVPN.com, 2017. [Online]. Available:
https://www.ibvpn.com/2010/02/8-advantages-of-using-vpn/. [Accessed: 25- Sep- 2017].
[2]A. Bourque, "5 ways your company can benefit from using a VPN", 2017.
[3]"Here's Why You Should Be Using a VPN", Lifewire, 2017. [Online]. Available:
https://www.lifewire.com/advantages-and-benefits-of-a-vpn-818178. [Accessed: 25- Sep-
2017].
8
The Implementation of VPN service is used to protect the business data and it provide user with
a host of additional functions. The best business VPN services are listed below.
PureVPN
SaferVPN
HideMyAss
IbVPN
VyprVPN
The VPN service implementation is to ensure the user network connection has static IP address.
Many small and medium business class DSL and cable connections uses the dynamic address that is
IP address of the network connections changes occasionally. But IP address changes, the remote
user does not know the new address. So, the remote users are does not connect network. Most of
small and medium business class DSL and cable providers are use the static addressing. the Static
addressing connect the remote users always on the network. It has sufficient upstream bandwidth to
support the remote users and it also has the better network speed [10].
6. Conclusion
The Virtual private network for Small and medium sized enterprise is analysed and discussed
in detail. The VPN network was created and designed in successfully. The VPN network provides the
greater performance for SME’s. It also provides the productivity and security. The VPN network
design hardware and software components was identified and analysed in detail. The Network
design IP addressing was successfully identified. The VPN security features and policies are analysed
and discussed. The Implementation of VPN services is discussed in detail.
References
[1]i. Team, "8 advantages of using VPN - ibVPN.com", ibVPN.com, 2017. [Online]. Available:
https://www.ibvpn.com/2010/02/8-advantages-of-using-vpn/. [Accessed: 25- Sep- 2017].
[2]A. Bourque, "5 ways your company can benefit from using a VPN", 2017.
[3]"Here's Why You Should Be Using a VPN", Lifewire, 2017. [Online]. Available:
https://www.lifewire.com/advantages-and-benefits-of-a-vpn-818178. [Accessed: 25- Sep-
2017].
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[4]"Defining VPN security policies", Help.fortinet.com, 2017. [Online]. Available:
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-ipsecvpn-52/
Defining_VPN_Policies/Defining_VPN_Security_Policies.htm. [Accessed: 25- Sep- 2017].
[5]P. Services, C. Software, C. IOS, C. Deployments and W. Papers, "IPSec Stateful Failover (VPN High
Availability) Feature Module", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/td/docs/ios/12_2/12_2y/12_2yx11/feature/guide/
ft_vpnha.html#wp1122512. [Accessed: 25- Sep- 2017].
[6]C. Verkoelen, Policy Based Network Management - Dynamic Virtual Private Network. Den Haag:
TNO, 2008.
[7]"5 Best Business VPN Services Essential for Your Office - BestVPN.com", BestVPN.com, 2017.
[Online]. Available: https://www.bestvpn.com/best-business-vpn-services/. [Accessed: 25- Sep-
2017].
[8]P. Venezia, "Small Business VPN Primer: Set Up Your Office Network for
Telecommuting", PCWorld, 2017. [Online]. Available:
https://www.pcworld.com/article/240762/small_business_vpn_primer_set_up_your_office_ne
twork_for_telecommuting.html. [Accessed: 25- Sep- 2017].
[9]"What is virtual private network (VPN)? - Definition from WhatIs.com", SearchNetworking, 2017.
[Online]. Available: http://searchnetworking.techtarget.com/definition/virtual-private-network.
[Accessed: 25- Sep- 2017].
[10]V. Pick, "Best VPN for Small & Medium Business – VPNPick.com", Vpnpick.com, 2017. [Online].
Available: https://vpnpick.com/best-vpn-business/. [Accessed: 25- Sep- 2017].
9
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-ipsecvpn-52/
Defining_VPN_Policies/Defining_VPN_Security_Policies.htm. [Accessed: 25- Sep- 2017].
[5]P. Services, C. Software, C. IOS, C. Deployments and W. Papers, "IPSec Stateful Failover (VPN High
Availability) Feature Module", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/td/docs/ios/12_2/12_2y/12_2yx11/feature/guide/
ft_vpnha.html#wp1122512. [Accessed: 25- Sep- 2017].
[6]C. Verkoelen, Policy Based Network Management - Dynamic Virtual Private Network. Den Haag:
TNO, 2008.
[7]"5 Best Business VPN Services Essential for Your Office - BestVPN.com", BestVPN.com, 2017.
[Online]. Available: https://www.bestvpn.com/best-business-vpn-services/. [Accessed: 25- Sep-
2017].
[8]P. Venezia, "Small Business VPN Primer: Set Up Your Office Network for
Telecommuting", PCWorld, 2017. [Online]. Available:
https://www.pcworld.com/article/240762/small_business_vpn_primer_set_up_your_office_ne
twork_for_telecommuting.html. [Accessed: 25- Sep- 2017].
[9]"What is virtual private network (VPN)? - Definition from WhatIs.com", SearchNetworking, 2017.
[Online]. Available: http://searchnetworking.techtarget.com/definition/virtual-private-network.
[Accessed: 25- Sep- 2017].
[10]V. Pick, "Best VPN for Small & Medium Business – VPNPick.com", Vpnpick.com, 2017. [Online].
Available: https://vpnpick.com/best-vpn-business/. [Accessed: 25- Sep- 2017].
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




