Ask a question from expert
A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
24 Pages27021 Words250 Views
Added on 2021-07-02
About This Document
Digital Object Identifier xxx A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures VIKAS HASSIJA 1 , VINAY CHAMOLA2 , VIKAS SAXENA 1 , DIVYANSH JAIN 1 , PRANAV GOYAL 1 and BIPLAB SIKDAR3 1 Department of CSE and IT, Jaypee Institute of Information Technology, Noida, 201309 India (e-mail: vikas.has
A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
Added on 2021-07-02
BookmarkShareRelated Documents
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecommons.org/licenses/by/3.0/.This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI10.1109/ACCESS.2019.2924045, IEEE AccessDate of publication xxxx 00, 0000, date of current version xxxx 00, 0000.Digital Object Identifier xxxA Survey on IoT Security: ApplicationAreas, Security Threats, and SolutionArchitecturesVIKAS HASSIJA1, VINAY CHAMOLA2, VIKAS SAXENA1, DIVYANSH JAIN1, PRANAVGOYAL1and BIPLAB SIKDAR31Department of CSE and IT, Jaypee Institute of Information Technology, Noida, 201309 India (e-mail: {vikas.hassija, vikas.saxena}@jiit.ac.in), (e-mail:{divyansh.bjain,pranav.goyal1297}@gmail.com)2Department of EEE, Birla Institute of Technology & Science (BITS), Pilani, Rajasthan 333031 India (e-mail: vinay.chamola@pilani.bits-pilani.ac.in)3Department of Electrical and Computer Engineering, National University of Singapore, 117583 Singapore (e-mail: bsikdar@nus.edu.sg)Corresponding author:Vinay Chamola(e-mail: vinay.chamola@pilani.bits-pilani.ac.in).ABSTRACTInternet of things (IoT) is the next era of communication. Using IoT, physical objects canbe empowered to create, receive and exchange data in a seamless manner. Various IoT applications focuson automating different tasks and are trying to empower the inanimate physical objects to act without anyhuman intervention. The existing and upcoming IoT applications are highly promising to increase the levelof comfort,efficiency,and automation for the users.To be able to implementsuch a world in an evergrowing fashion requires high security, privacy, authentication, and recovery from attacks. In this regard, itis imperative to make the required changes in the architecture of IoT applications for achieving end-to-endsecure IoT environments. In this paper, a detailed review of the security-related challenges and sources ofthreat in IoT applications is presented. After discussing the security issues, various emerging and existingtechnologies focused on achieving a high degree of trust in IoT applications are discussed. Four differenttechnologies: Blockchain,fog computing,edge computing,and machine learning to increase the level ofsecurity in IoT are discussed.INDEX TERMSIoT, IoT Security, Blockchain, Fog Computing, Edge Computing, Machine Learning, IoTapplications, Distributed Systems.I.INTRODUCTIONTHE pace of connecting physicaldevices around us tothe Internet is increasing rapidly. According to a recentGartner report,there willbe around 8.4 billion connectedthings worldwide in 2020. This number is expected to growto 20.4 billion by 2022 [1].The use ofIoT applicationsis increasing in allparts ofthe world.The majordrivingcountries in this include western Europe,North America,and China [1].The number of machine to machine (M2M)connections is expected to grow from 5.6 billion in 2016 to27 billion in 2024 [1].This leap in numbers itself declaresIoT to be one of the major upcoming markets that could forma cornerstone ofthe expanding digitaleconomy.The IoTindustry is expected to grow in terms of revenue from $892billion in 2018 to $4 trillion by 2025 [2]. M2M connectionscover a broad range of applications like smart cities,smartenvironment,smartgrids,smartretail,smartfarming,etc.[3]. Figure 1 shows the past, present and future architectureof IoT.In future,the devices are notonly expected to beconnected to the Internet and other local devices but are alsoexpected to communicate with other devices on the Internetdirectly.Apart from the devices or things being connected,the concept of social IoT (SIoT) is also emerging. SIoT willenable different social networking users to be connected tothe devices and users can share the devices over the Internet[4].With allthis vastspectrum ofIoT applications comesthe issue ofsecurity and privacy.Withouta trusted andinteroperable IoT ecosystem, emerging IoT applications can-notreach high demand and may lose alltheirpotential.Along with the security issues faced generally by the Inter-net,cellular networks,and WSNs,IoT also has its specialsecurity challenges such as privacy issues,authenticationissues,managementissues,information storage and so on.Table 1 summarizes various factors due to which securingIoT environmentis much more challenging than securingVOLUME x, 20191

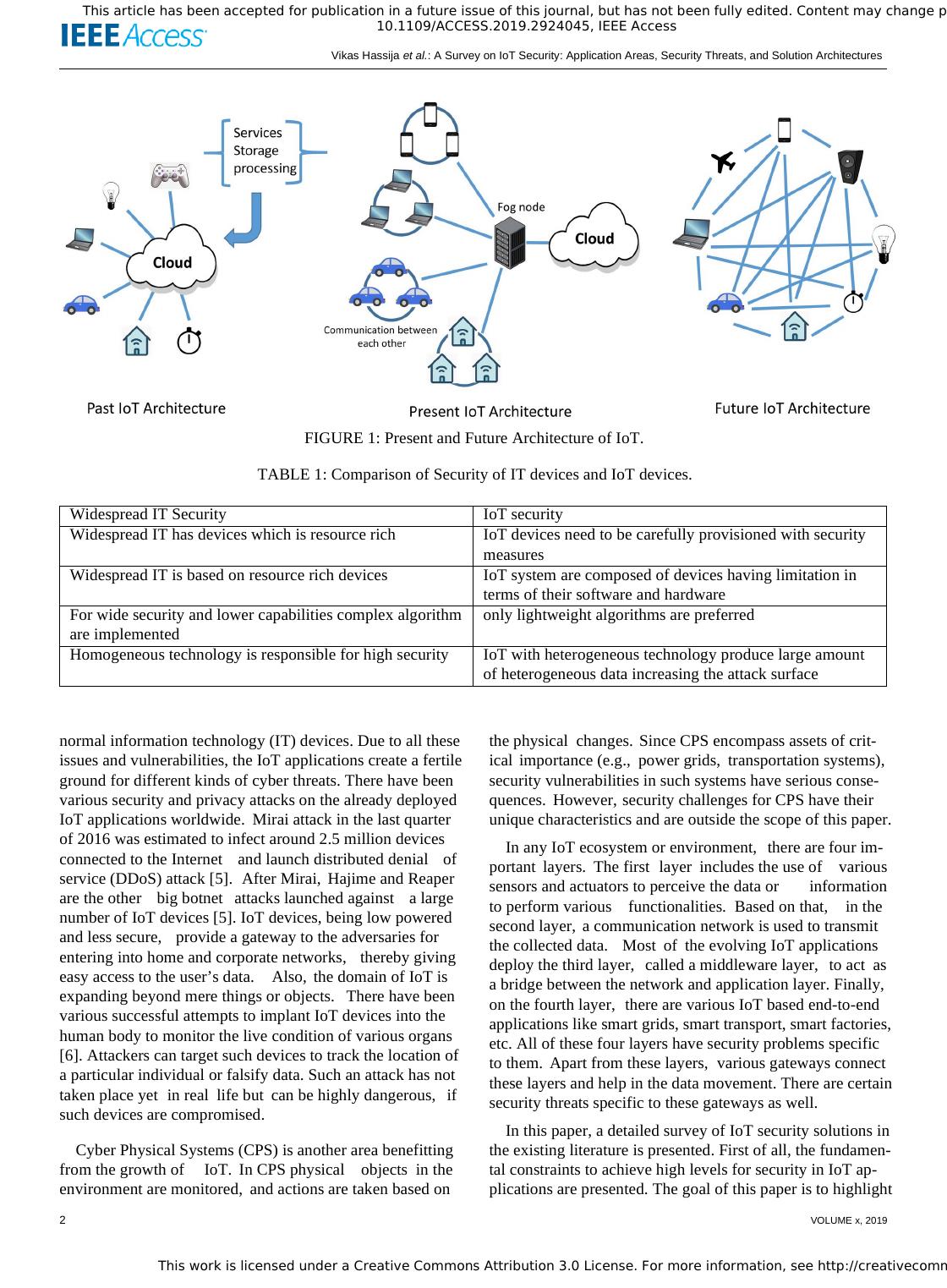
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecommons.org/licenses/by/3.0/.This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI10.1109/ACCESS.2019.2924045, IEEE AccessVikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution ArchitecturesFIGURE 1: Present and Future Architecture of IoT.TABLE 1: Comparison of Security of IT devices and IoT devices.Widespread IT SecurityIoT securityWidespread IT has devices which is resource richIoT devices need to be carefully provisioned with securitymeasuresWidespread IT is based on resource rich devicesIoT system are composed of devices having limitation interms of their software and hardwareFor wide security and lower capabilities complex algorithmare implementedonly lightweight algorithms are preferredHomogeneous technology is responsible for high securityIoT with heterogeneous technology produce large amountof heterogeneous data increasing the attack surfacenormal information technology (IT) devices. Due to all theseissues and vulnerabilities, the IoT applications create a fertileground for different kinds of cyber threats. There have beenvarious security and privacy attacks on the already deployedIoT applications worldwide.Mirai attack in the last quarterof 2016 was estimated to infect around 2.5 million devicesconnected to the Internetand launch distributed denialofservice (DDoS) attack [5].After Mirai,Hajime and Reaperare the otherbig botnetattacks launched againsta largenumber of IoT devices [5]. IoT devices, being low poweredand less secure,provide a gateway to the adversaries forentering into home and corporate networks,thereby givingeasy access to the user’s data.Also,the domain of IoT isexpanding beyond mere things or objects.There have beenvarious successful attempts to implant IoT devices into thehuman body to monitor the live condition of various organs[6]. Attackers can target such devices to track the location ofa particular individual or falsify data. Such an attack has nottaken place yetin reallife butcan be highly dangerous,ifsuch devices are compromised.Cyber Physical Systems (CPS) is another area benefittingfrom the growth ofIoT.In CPS physicalobjectsin theenvironment are monitored,and actions are taken based onthe physicalchanges.Since CPS encompass assets of crit-icalimportance (e.g.,power grids,transportation systems),security vulnerabilities in such systems have serious conse-quences.However,security challenges for CPS have theirunique characteristics and are outside the scope of this paper.In any IoT ecosystem or environment,there are four im-portantlayers.The firstlayerincludes the use ofvarioussensors and actuators to perceive the data orinformationto perform variousfunctionalities.Based on that,in thesecond layer,a communication network is used to transmitthe collected data.Mostofthe evolving IoT applicationsdeploy the third layer,called a middleware layer,to actasa bridge between the network and application layer. Finally,on the fourth layer,there are various IoT based end-to-endapplications like smart grids, smart transport, smart factories,etc. All of these four layers have security problems specificto them.Apart from these layers,various gateways connectthese layers and help in the data movement. There are certainsecurity threats specific to these gateways as well.In this paper, a detailed survey of IoT security solutions inthe existing literature is presented. First of all, the fundamen-tal constraints to achieve high levels for security in IoT ap-plications are presented. The goal of this paper is to highlight2VOLUME x, 2019
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecommons.org/licenses/by/3.0/.This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI10.1109/ACCESS.2019.2924045, IEEE AccessVikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architecturesthe major existing and upcoming solutions for IoT security.Specifically, the four major classes of IoT security solutionsnamely:(1) blockchain based solutions;(2) fog computingbased solutions;(3) machine learning based solutions and(4) edge computing based solutions are highlighted. Table 3gives a list of acronyms related to IoT used in this paper.A.RELATED SURVEYS AND OUR CONTRIBUTIONSThere are various existing surveys on IoT security and pri-vacy issues.Yuchen etal. [10]have summarized varioussecurity issues in IoT applications. Authors of [11] have dis-cussed the security issues specific to location-based servicesin IoT. The authors target the particular problems related tolocalization and positioning of the IoT devices.Anne et al.in [12]focus mainly on the security issues related to IoTmiddleware and provide a detailed survey of related existingprotocols and their security issues. M. Guizani et al. in [14]have surveyed various trust management techniques for IoTalong with theirpros and cons.Security mechanisms forIoT security such as software defined networking (SDN)and network function virtualization (NFV)are discussedin [13].In [8] the authors have compared edge computingwith traditionalcloud systems to secure IoT systems.JieLin etal.in [9]have discussed the relationship betweenIoT and fog computing. Some of the security issues relatedto fog computing have also been discussed.Authors of [7]have discussed vulnerabilities faced by IoT in brief. Table 2summarizes the main contributions of the previous compre-hensive surveys on IoT security.Although there are severalworks in this direction,they are specific to certain limitedaspects ofIoT.This calls the need fora detailed surveyon all the existing and upcoming security challenges in IoTapplications. This paper will help the reader to get a detailedidea of the state-of-the-art in IoT security and will give thema general understanding of the area. The main contributionsof this work are as follows:1.A classification of different IoT applications and spe-cific security and privacy issues related to those appli-cations.2.A detailed explanation of differentthreatsources indifferent layers of IoT.3.Detailed and realistic recommendations to improve theIoT infrastructure to facilitate secure communications.4.Review on the proposed countermeasures to the secu-rity issues in IoT.5.An assessmentofthe open issues,challengesandfuture research directions fordeveloping secure IoTapplications.B.ORGANIZATIONThe organization of the rest of the paper is as follows: SectionIIdescribes various application areas ofIoT where highsecurity is required. Section III discusses various sources ofthreats in an IoT environment.In section IV various con-straints and requirements to be considered while developinga secure IoT application are reviewed.Four major IoT se-curity approaches, i.e., blockchain, fog computing, machinelearning,and edge computing are presented in Section V,VI, VII, and VIII, respectively. Section IX describes variousopen issues, challenges and upcoming research opportunitiesin IoT security and finally, Section X concludes the paper.II.SECURITY CRITICAL APPLICATION AREAS OF IOTSecurity is highly critical in almost all IoT applications thathave already been deployed or are in the process of deploy-ment.The applications of IoT are increasing very rapidlyand penetrating mostofthe existing industries.Althoughoperators supportthese IoT applications through existingnetworking technologies,several of these applications needmore stringent security support from technologies they use.In this section various security critical IoT applications arediscussed.1.Smart Cities:Smartcities involve extensive use ofemerging computation and communication resourcesfor increasing the overall quality of life of the people[15].Itincludes smarthomes,smarttraffic manage-ment,smart disaster management,smart utilities,etc.There is a push to make cities smarter,and govern-ments worldwide are encouraging their developmentthrough various incentives [16].Although the use ofsmartapplications is intended to improve the overallquality of life of the citizens,itcomes with a threatto the privacy of the citizens. Smart card services tendto putthe card details and purchase behavior of thecitizens at risk.Smart mobility applications may leakthe location traces of the users. There are applicationsTABLE 2: Related Surveys on IoT SecurityYearAuthorContributions2016Arsalan Mosenia et al., [7]A brief discussion of vulnerabilities faced by the edge side layer of IoT2017Yu wei et al., [8]Survey on using Edge Computing to secure IoT2017Jie Lin ea al., [9]Discussion on relationship between IoT and Fog Computing2017Y yang et al., [10]A brief discussion on most relevant limitations of IoT devices2017L chen , S. Thombre et al., [11]security issues specific to location-based services in IoT2017A H Ngu, V. Metsis et al., [12]Security issues related to the IoT middle ware2018I Farris, T Taleb et al., [13]Security mechanism for IoT security like SDN and NFB2019Ikram Ud din, M. Guizani et al,. [14]Trust Management Techniques for Internet of ThingsVOLUME x, 20193
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecommons.org/licenses/by/3.0/.This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI10.1109/ACCESS.2019.2924045, IEEE AccessVikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution ArchitecturesTABLE 3: List of AcronymsNotationMeaningABSIAdaptive Binary Splitting InspectionAMIAdvanced Metering InfrastructureAMQPAdvanced Message Queuing ProtocolAPTAdvanced Persistent ThreatCoAPConstrained Application ProtocolDACDistributed Autonomous CorporationDAOsDecentalized Autonomous OrganizationsDDoSDistributed denial of serviceGPSGlobal Positioning SystemHANHome Area NetworkIIoTIndustrial Internet of ThingsIOEInternet of EverythingIoTInternet of ThingsM2MMachine to MachineMCCMobile Cloud ComputingMECMobile Edge ComputingMLPMulti-Layer PerceptronMQTTMessage Queuing Telemetry TransportNFCNear Field CommunicationNFVNetwork Function VirtualizationP2Ppeer to peerQoSQuality of ServiceRFIDRadio Frequency IdentificationRSNRFID sensor NetworksSDNSoftware-Defined NetworkingSHASecure Hash AlgorithmSIoTSocial Internet of ThingsSMQTTSecure Message Queue Telemetry TransportSTDSecurity Trust and DecentralizationWSNWireless Sensor NetworksXMPPExtensible Messaging and Presence ProtocolXSScross-site scriptingusing which parents can keep track of their child. How-ever, if such applications are hacked, then the safety ofthe child can come to risk.2.SmartEnvironment:SmartenvironmentincludesvariousIoT applicationssuch asfiredetection inforests,monitoring the levelofsnow in high alti-tude regions,preventing landslides, early detection ofearthquakes,pollution monitoring,etc.Allthese IoTapplications are closely related to the life of humanbeings and animals in those areas.The governmentagencies involved in such fields will also be relying onthe information from these IoT applications.Securitybreaches and vulnerability in any area related to suchIoT applications can have serious consequences. In thiscontext,both false negatives and false positives canlead to disastrous results for such IoT applications. Forexample, if the application starts detecting earthquakesfalsely,then itwilllead to monetary losses forthegovernment and businesses.On the other hand,if theapplication is not able to predict the earthquake,thenit will lead to the loss of both property and life. There-fore, smart environment applications have to be highlyprecise, and security breaches and data tampering mustbe avoided.3.Smart Metering and Smart Grids:Smart meteringincludes applications related to various measurements,monitoring,and management.The most common ap-plication of smartmetering is smartgrids,where theelectricity consumption is measured and monitored.Smart metering may also be used to address the prob-lem of electricity theft [17]. Other applications of smartmetering include monitoring ofwater,oiland gaslevels in storage tanks and cisterns.Smart meters arealso used to monitor and optimize the performance ofsolar energy plants by dynamically changing the angleof solar panels to harvest the maximum possible solarenergy. There also exist some IoT applications that usesmartmeters to measure the water pressure in watertransport systems or to measure the weight of goods.However,smartmetering systems are vulnerable toboth physical and cyber-attacks as compared to analogmeters that can be tampered only by physical attacks.Also,smartmeters or advanced metering infrastruc-ture (AMI) are intended to perform functions beyondgeneric energy usage recording. In a smart home areanetwork (HAN) all electric equipment at home are con-nected to smartmeters and the information collectedfrom these equipments can be used for load and costmanagement.Intentionalintrusion in such communi-cation systems by the consumer or an adversary maymodify the collected information, leading to monetaryloss for the service providers or consumers [18].4.Security and Emergencies: Security and emergenciesis another importantarea where various IoT applica-tions are being deployed. It includes applications suchas allowing only authorized people in restricted areasetc. Another application in this domain is the detectionof leakage of hazardous gases in industrialareas orareas around chemical factories.Radiation levels canalso be measured in the areas around nuclear powerreactorsorcellularbase stationsand alertscan begenerated when the radiation level is high.There arevarious buildings whose systems have sensitive data orthathouse sensitive goods.Security applications canbe deployed to protectsensitive data and goods.IoTapplications that detect various liquids can also be usedto prevent corrosion and break downs in such sensitivebuildings.Security breaches in such applications canalso have various serious consequences. For example,the criminals may try to enter the restricted areas byattacking the vulnerabilities in such applications. Also,false radiation level alarms can have serious immediateand long term impacts.Forexample,ifinfants areexposed to high levels of radiation,then itmay leadto serious life threatening diseases in long term.4VOLUME x, 2019

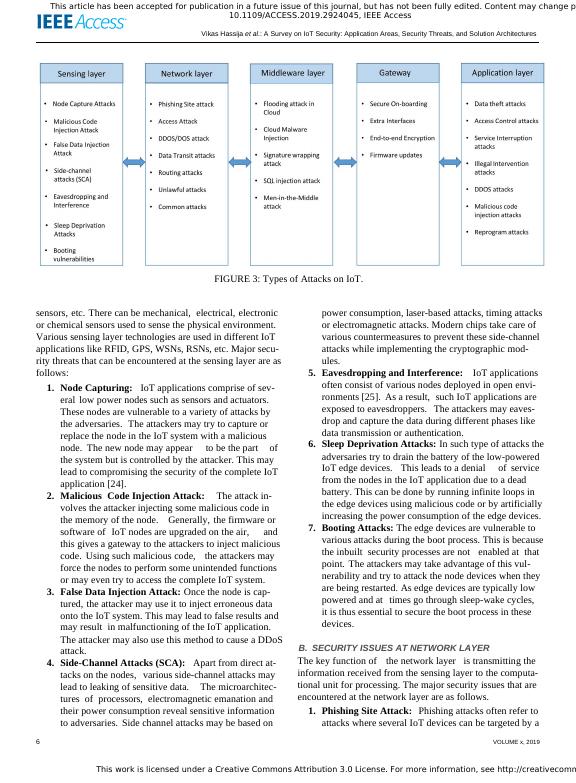
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecommons.org/licenses/by/3.0/.This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI10.1109/ACCESS.2019.2924045, IEEE AccessVikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures5.Smart Retail:IoT applications are being extensivelyused in the retail sector. Various applications have beendeveloped to monitorthe storage conditions ofthegoods as they move along the supply chain. IoT is alsobeing used to controlthe tracking of products in thewarehouses so that restocking can be done optimally.Various intelligent shopping applications are also beingdeveloped for assisting the customers based on theirpreferences,habits,allergies to certain components,etc.Mechanisms to provide the experience of onlineshopping to offline retailers using augmented realitytechniques have also been developed. Various compa-nies in retailhave faced security issues in deployingand using various IoT applications. Some of these com-panies include Apple, Home Depot, JP Morgan Chaseand Sony [19]. Adversaries may try to compromise theIoT applications associated with storage conditions ofthe goods and may try to send wrong information aboutthe products to the users in order to increase the sale.If security features are not implemented in smart retail,attackers may steal debit and credit card information,phone numbers, email-addresses, etc. of the customerswhich can lead to monetary losses for the customersand retailers.6.SmartAgriculture and AnimalFarming:Smartagriculture includes monitoring soil moisture, control-ling micro-climate conditions,selective irrigation indry zones,and controlling humidity and temperature.Usage of such advanced features in agriculture can helpin achieving high yields and can save farmers frommonetary losses. Control of temperature and humiditylevels in various grain and vegetable production canhelp in preventing fungus and other microbial contam-inants. Controlling the climate conditions can also helpin increasing the vegetable and crop yield and quality.Just like crop monitoring, there are IoT applications tomonitor the activities and the health condition of farmanimals by attaching sensors to the animals.If suchapplications are compromised, then it may lead to thetheft of animals from the farm and adversaries may alsodamage the crops.7.Home Automation: Home automation is one of themost widely used and deployed IoT applications. Thisincludes applications such as those for remotely con-trolling electricalappliances to save energy,systemsdeployed on windows and doors to detect intruders, etc.Monitoring systems are being applied to track energyand water supply consumption, and users are being ad-vised to save cost and resources. Authors in [20] haveproposed the use oflogic based security algorithmsto enhance security level in homes. Intrusions are de-tected by comparing the user actions at key locationsof the home with normal behavior of the user in theselocations.However,attackers may gain unauthorizedaccess of the IoT devices in the home and try to harmthe users. For instance, cases of home burglaries haveFIGURE 2: Layers in IoT System.increased rapidly after the deployment of various homeautomation systems [20]. There have also been variouscases in the past where the adversaries try to analyzethe type and volume of Internet traffic to/from the smarthome forjudging the behaviorand presence oftheresidents.III.SOURCES OF SECURITY THREATS IN IOTAPPLICATIONSAs discussed in Section I, any IoT application can be dividedinto four layers: (1) sensing layer; (2) network layer; (3) mid-dleware layer; and (4) application layer. Each of these layersin an IoT application uses diverse technologies that bring anumber of issues and security threats. Figure 2 shows varioustechnologies,devices,and applications at these four layers.This section discusses various possible security threats inIoT applications for these four layers.Figure 3 shows thepossible attacks on these four layers.The specialsecurityissues associated with the gateways that connect these layersare also discussed in this section.A.SECURITY ISSUES AT SENSING LAYERThe sensing layer mainly deals with physical IoT sensors andactuators. Sensors sense the physical phenomenon happeningaround them [21]–[23]. Actuators, on the other hand, performa certain action on the physicalenvironment,based on thesensed data.There are various kinds ofsensors forsens-ing differentkinds of data,e.g.,ultrasonic sensors,camerasensors, smoke detection sensors, temperature and humidityVOLUME x, 20195

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecommons.org/licenses/by/3.0/.This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI10.1109/ACCESS.2019.2924045, IEEE AccessVikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution ArchitecturesFIGURE 3: Types of Attacks on IoT.sensors,etc.There can be mechanical,electrical,electronicor chemical sensors used to sense the physical environment.Various sensing layer technologies are used in different IoTapplications like RFID, GPS, WSNs, RSNs, etc. Major secu-rity threats that can be encountered at the sensing layer are asfollows:1.Node Capturing:IoT applications comprise of sev-erallow power nodes such as sensors and actuators.These nodes are vulnerable to a variety of attacks bythe adversaries.The attackers may try to capture orreplace the node in the IoT system with a maliciousnode.The new node may appearto be the partofthe system but is controlled by the attacker. This maylead to compromising the security of the complete IoTapplication [24].2.MaliciousCode Injection Attack:The attack in-volves the attacker injecting some malicious code inthe memory of the node.Generally,the firmware orsoftware ofIoT nodes are upgraded on the air,andthis gives a gateway to the attackers to inject maliciouscode.Using such malicious code,the attackers mayforce the nodes to perform some unintended functionsor may even try to access the complete IoT system.3.False Data Injection Attack: Once the node is cap-tured,the attacker may use it to inject erroneous dataonto the IoT system. This may lead to false results andmay resultin malfunctioning of the IoT application.The attacker may also use this method to cause a DDoSattack.4.Side-Channel Attacks (SCA):Apart from direct at-tacks on the nodes,various side-channel attacks maylead to leaking of sensitive data.The microarchitec-turesofprocessors,electromagnetic emanation andtheir power consumption reveal sensitive informationto adversaries.Side channel attacks may be based onpower consumption, laser-based attacks, timing attacksor electromagnetic attacks. Modern chips take care ofvarious countermeasures to prevent these side-channelattacks while implementing the cryptographic mod-ules.5.Eavesdropping and Interference:IoT applicationsoften consist of various nodes deployed in open envi-ronments [25].As a result,such IoT applications areexposed to eavesdroppers.The attackers may eaves-drop and capture the data during different phases likedata transmission or authentication.6.Sleep Deprivation Attacks: In such type of attacks theadversaries try to drain the battery of the low-poweredIoT edge devices.This leads to a denialofservicefrom the nodes in the IoT application due to a deadbattery.This can be done by running infinite loops inthe edge devices using malicious code or by artificiallyincreasing the power consumption of the edge devices.7.Booting Attacks: The edge devices are vulnerable tovarious attacks during the boot process. This is becausethe inbuiltsecurity processes are notenabled atthatpoint.The attackers may take advantage of this vul-nerability and try to attack the node devices when theyare being restarted. As edge devices are typically lowpowered and attimes go through sleep-wake cycles,it is thus essential to secure the boot process in thesedevices.B.SECURITY ISSUES AT NETWORK LAYERThe key function ofthe network layeris transmitting theinformation received from the sensing layer to the computa-tional unit for processing. The major security issues that areencountered at the network layer are as follows.1.Phishing Site Attack:Phishing attacks often refer toattacks where several IoT devices can be targeted by a6VOLUME x, 2019
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Analysis of Lightweight Encryption Scheme for Fog-to-Things Communicationlg...
|11
|10056
|476
Security of Internet of Things - Issues, Vulnerabilities and Measureslg...
|12
|555
|406
IoT Security and Privacy Regime/Challenges in All Domains of IoTlg...
|2
|1568
|228
Internet of Things: A Review of Literature and Security Issueslg...
|8
|810
|321
Internet Of Things Ethical Issueslg...
|11
|2668
|43
Investigation Internet of Things (IoT) Device using Integrated Digital Forensics Investigation Framework (IDFIF)lg...
|8
|2846
|482