Network Systems Assignment 1: Practical Problem Solving Report
VerifiedAdded on 2022/10/01
|44
|5505
|482
Report
AI Summary
This report details the practical problem-solving tasks undertaken for a network systems assignment. It covers setting up remote desktop connections between two computers, exploring file operations such as moving, renaming, and downloading files. The report also includes the setup and configuration of virtual machines using VirtualBox, including network configurations within the virtual environment. Furthermore, the assignment addresses IPv4 subnetting and concludes with reflections on the processes and outcomes. The report provides step-by-step instructions, configurations, and commands used to complete each task, offering a comprehensive overview of the network systems concepts and practical applications. The student utilized tools like Putty, Xming and GUI interfaces for the remote access and file management tasks.

TITLE: NETWORK SYSTEM
NETWORK SYSTEM
i
NETWORK SYSTEM
i
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Page
TITLE................................................................................................................…………... ……..i
TABLE OF CONTENTS .............................................................................................………….ii
ABSTRACT ........................................................................................……………………………iii
INTRODUCTION ........................................................................................................................ .v
Task 1
Sub-task 1
Remote Desktop………………………………………………………………………………. ..1
Sub-task 2
Remote desktop operation……………………………………………………………………... 10
Sub-task 3
Operation of remote computer from the local computer…………………………………….… 12
Task 2
Remote Connections
Sub-task 1
Setting up remote connection of the two computers for file operations………………….…...14
Sub-task 2
File Operations………………………………………………………………………………..15
Task 3
Virtual Machine
Sub-task 1
Virtual Machine set up on VirtualBox………………………………………………………..18
Sub-task 2
Virtual Machine Network set up……………………………………………………………..24
Task 4
IPv4 subneting…………………………………………………………………………..…..27
Task 5
Reflections…………………………………………………………………………………..29
CONCLUSION …………………………………………………………………………....30
REFERENCES ............................................................................................................….…31
ii
Page
TITLE................................................................................................................…………... ……..i
TABLE OF CONTENTS .............................................................................................………….ii
ABSTRACT ........................................................................................……………………………iii
INTRODUCTION ........................................................................................................................ .v
Task 1
Sub-task 1
Remote Desktop………………………………………………………………………………. ..1
Sub-task 2
Remote desktop operation……………………………………………………………………... 10
Sub-task 3
Operation of remote computer from the local computer…………………………………….… 12
Task 2
Remote Connections
Sub-task 1
Setting up remote connection of the two computers for file operations………………….…...14
Sub-task 2
File Operations………………………………………………………………………………..15
Task 3
Virtual Machine
Sub-task 1
Virtual Machine set up on VirtualBox………………………………………………………..18
Sub-task 2
Virtual Machine Network set up……………………………………………………………..24
Task 4
IPv4 subneting…………………………………………………………………………..…..27
Task 5
Reflections…………………………………………………………………………………..29
CONCLUSION …………………………………………………………………………....30
REFERENCES ............................................................................................................….…31
ii

Abstract
Users can move files from local to remote computer only if they are privileged during the session.
In this case, one cannot have full control of the remote computer for file transfers hence it is only
possible under some circumstances. It will also depend on the administrator permission that has
granted you over the file upload to the remote computer or to download them from the local
computer. It will only be possible on certain directories because of restrictions on some paths on the
remote or local systems. File transfer is easy since one can drag and drop them or use upload and
download button. If you right click on the file you would like to transfer, menu will pop-up where
there are several options such as creating a new directory; rename, deleting or opening the
files.Windows operating systems have desktop connection. If two or more computers are connected
using internet, then you will be able to accessseveral network resources from the one computer to
other. It is only possible if you have login from both systems (Aaqib, and Sharma, 2019, pp. 441-
447).
iii
Users can move files from local to remote computer only if they are privileged during the session.
In this case, one cannot have full control of the remote computer for file transfers hence it is only
possible under some circumstances. It will also depend on the administrator permission that has
granted you over the file upload to the remote computer or to download them from the local
computer. It will only be possible on certain directories because of restrictions on some paths on the
remote or local systems. File transfer is easy since one can drag and drop them or use upload and
download button. If you right click on the file you would like to transfer, menu will pop-up where
there are several options such as creating a new directory; rename, deleting or opening the
files.Windows operating systems have desktop connection. If two or more computers are connected
using internet, then you will be able to accessseveral network resources from the one computer to
other. It is only possible if you have login from both systems (Aaqib, and Sharma, 2019, pp. 441-
447).
iii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
First, you have to locate the files you would like to delete from the local computer. You have to use
internet connection gain access and right click on the file you would like to delete. The menu will
pop-up where you will choose the delete option. I used putty emulator software to log into Linux
server from a Window OS. It was fine to use alone but when i combine with Xming then it was a
nice compliment. Xming is a software used mainly for graphic displays in a remote Linux servers. It
was more efficient when I combined the two. It was simple to use them since i just install and
follow some few instructions. I also used Graphical User Interface which is available in Linux
platform to edit files. During the session, i was privileged to move my files. Unfortunately, I didn’t
control the remote computer during file upload and download from local computer. GUIs are
mainly available in Linux platform. The most used and common is Nautilus (GNOME) and Dolphin
(KDE). They are both flexible and powerful. They can be operated as follows (Zhang,.., 2019, pp.
89-97):
v
First, you have to locate the files you would like to delete from the local computer. You have to use
internet connection gain access and right click on the file you would like to delete. The menu will
pop-up where you will choose the delete option. I used putty emulator software to log into Linux
server from a Window OS. It was fine to use alone but when i combine with Xming then it was a
nice compliment. Xming is a software used mainly for graphic displays in a remote Linux servers. It
was more efficient when I combined the two. It was simple to use them since i just install and
follow some few instructions. I also used Graphical User Interface which is available in Linux
platform to edit files. During the session, i was privileged to move my files. Unfortunately, I didn’t
control the remote computer during file upload and download from local computer. GUIs are
mainly available in Linux platform. The most used and common is Nautilus (GNOME) and Dolphin
(KDE). They are both flexible and powerful. They can be operated as follows (Zhang,.., 2019, pp.
89-97):
v
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 1
Sub-task 1
Remote Desktop
How to access Linux server from Windows using Putty & Xming
How to configure Putty & Xming
Putty and Xming can be configurations is simple step procedures that can be done without so much
complexity. Using Putty Window that is basically emulator software, one can log into a Linux
server. It can be used alone or with Xming since they can compliment each other. Xming is mainly
used to display graphics such as images from the remote Linux servers (Praptodiyono,.., 2019).
Installation and configurations of Xming
1) Download & install Xming
You will have to download free version of the Xming on google using the following link
http://www.straightrunning.com/XmingNotes/ and then just follow instructions of installing.
3) Download & install Xming Fonts
Xming Fonts can be downloaded and installed using the fellow link
http://www.straightrunning.com/XmingNotes/
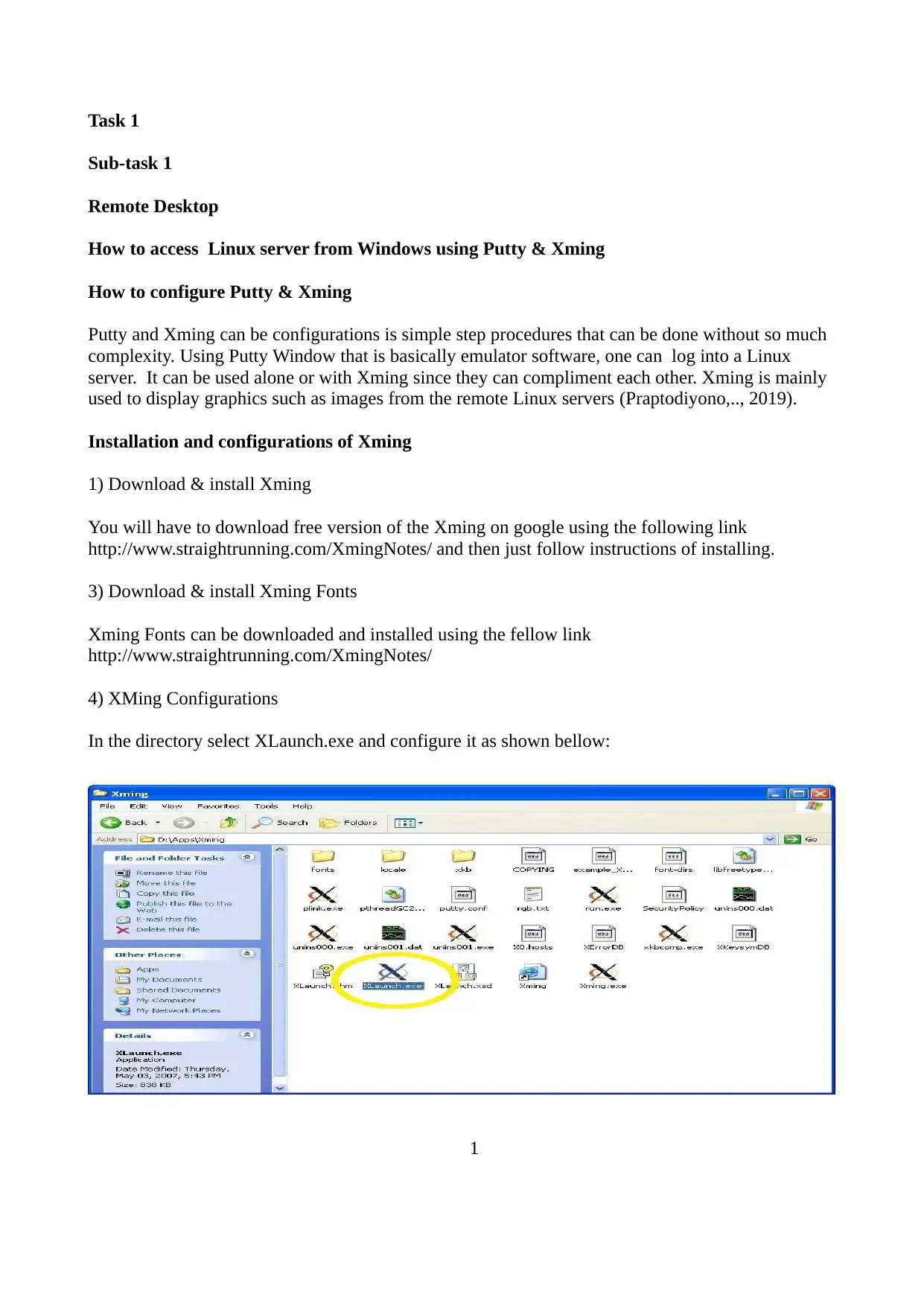
4) XMing Configurations
In the directory select XLaunch.exe and configure it as shown bellow:
1
Sub-task 1
Remote Desktop
How to access Linux server from Windows using Putty & Xming
How to configure Putty & Xming
Putty and Xming can be configurations is simple step procedures that can be done without so much
complexity. Using Putty Window that is basically emulator software, one can log into a Linux
server. It can be used alone or with Xming since they can compliment each other. Xming is mainly
used to display graphics such as images from the remote Linux servers (Praptodiyono,.., 2019).
Installation and configurations of Xming
1) Download & install Xming
You will have to download free version of the Xming on google using the following link
http://www.straightrunning.com/XmingNotes/ and then just follow instructions of installing.
3) Download & install Xming Fonts
Xming Fonts can be downloaded and installed using the fellow link
http://www.straightrunning.com/XmingNotes/
4) XMing Configurations
In the directory select XLaunch.exe and configure it as shown bellow:
1
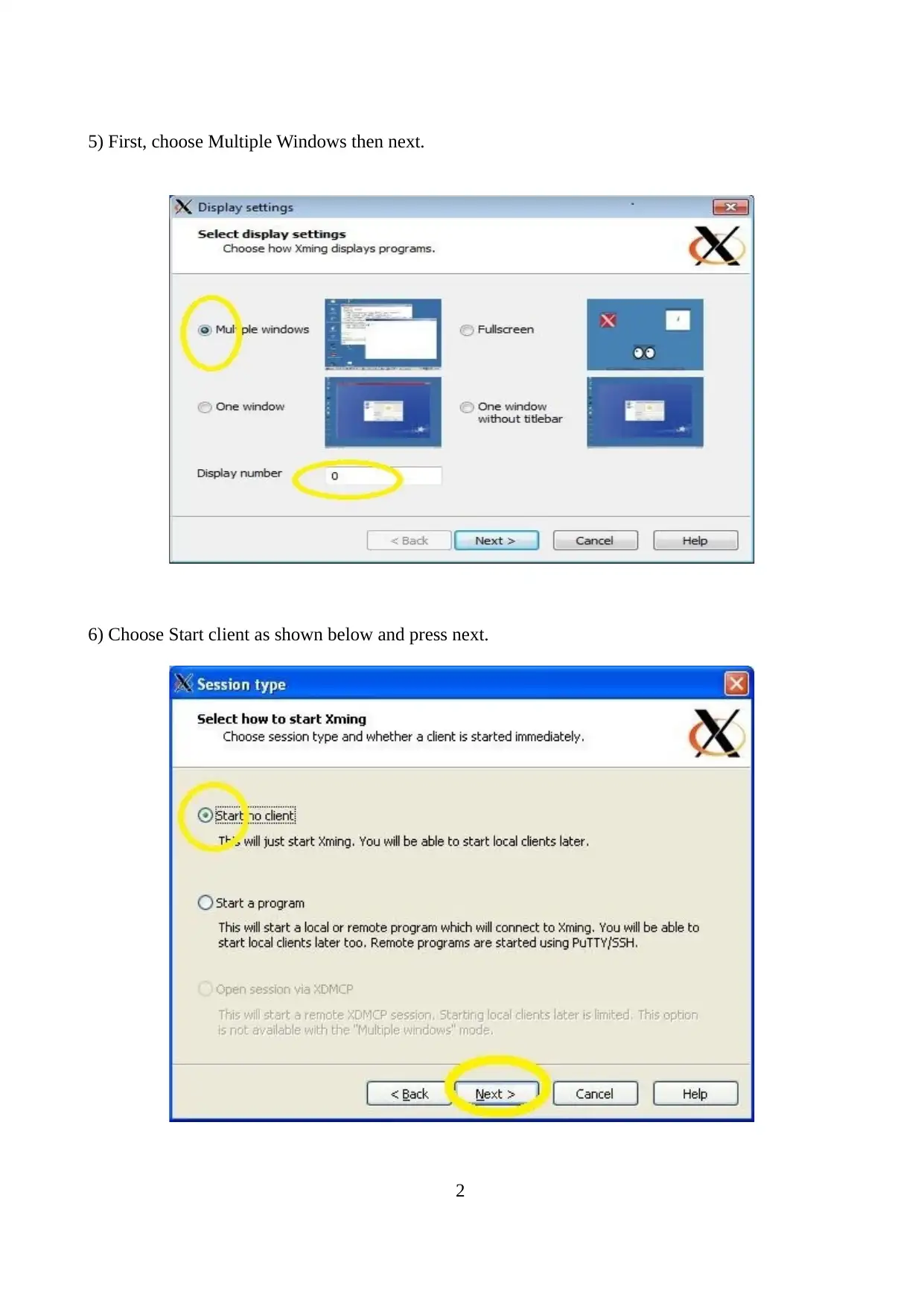
5) First, choose Multiple Windows then next.
6) Choose Start client as shown below and press next.
2
6) Choose Start client as shown below and press next.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
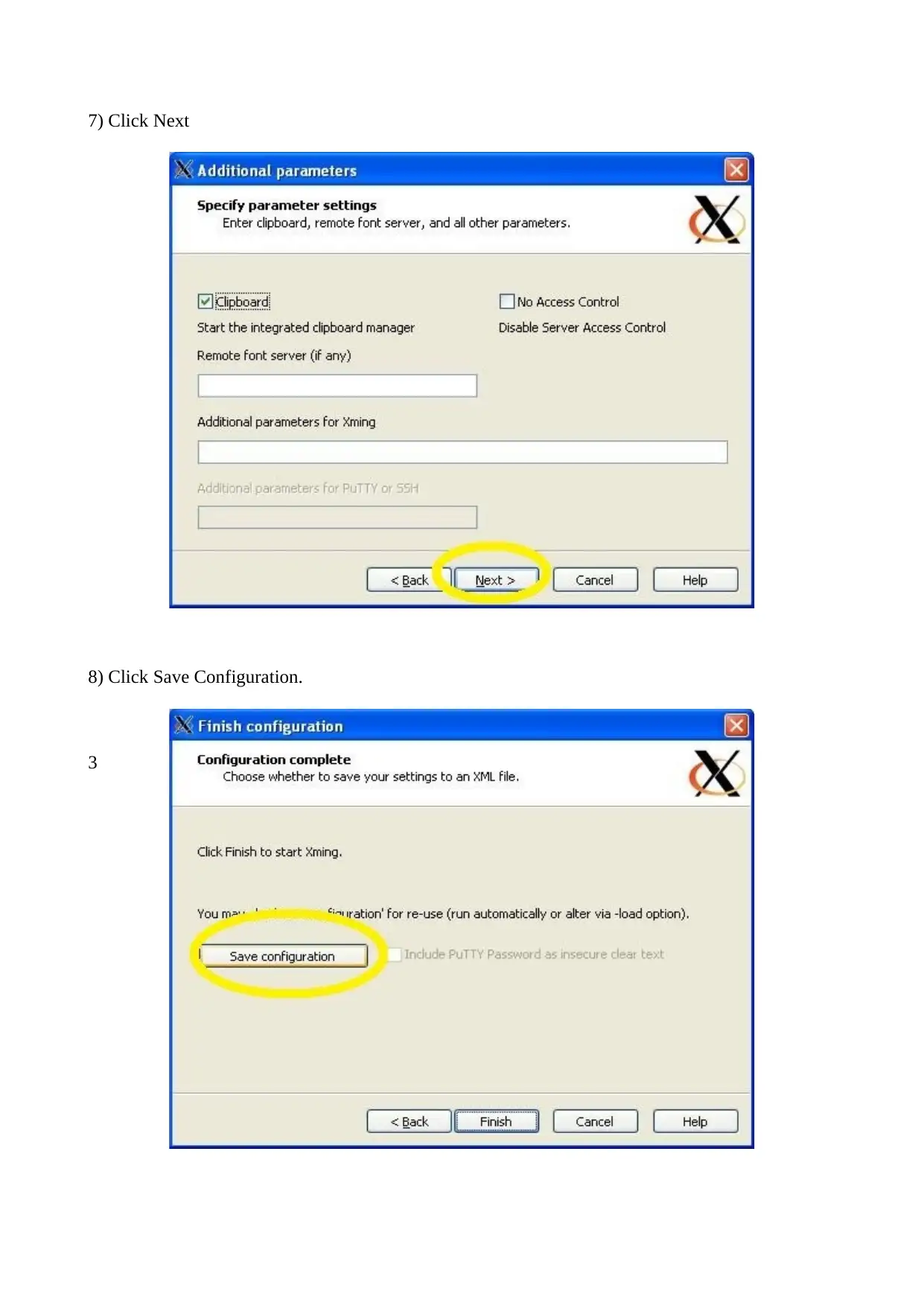
7) Click Next
8) Click Save Configuration.
3
8) Click Save Configuration.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
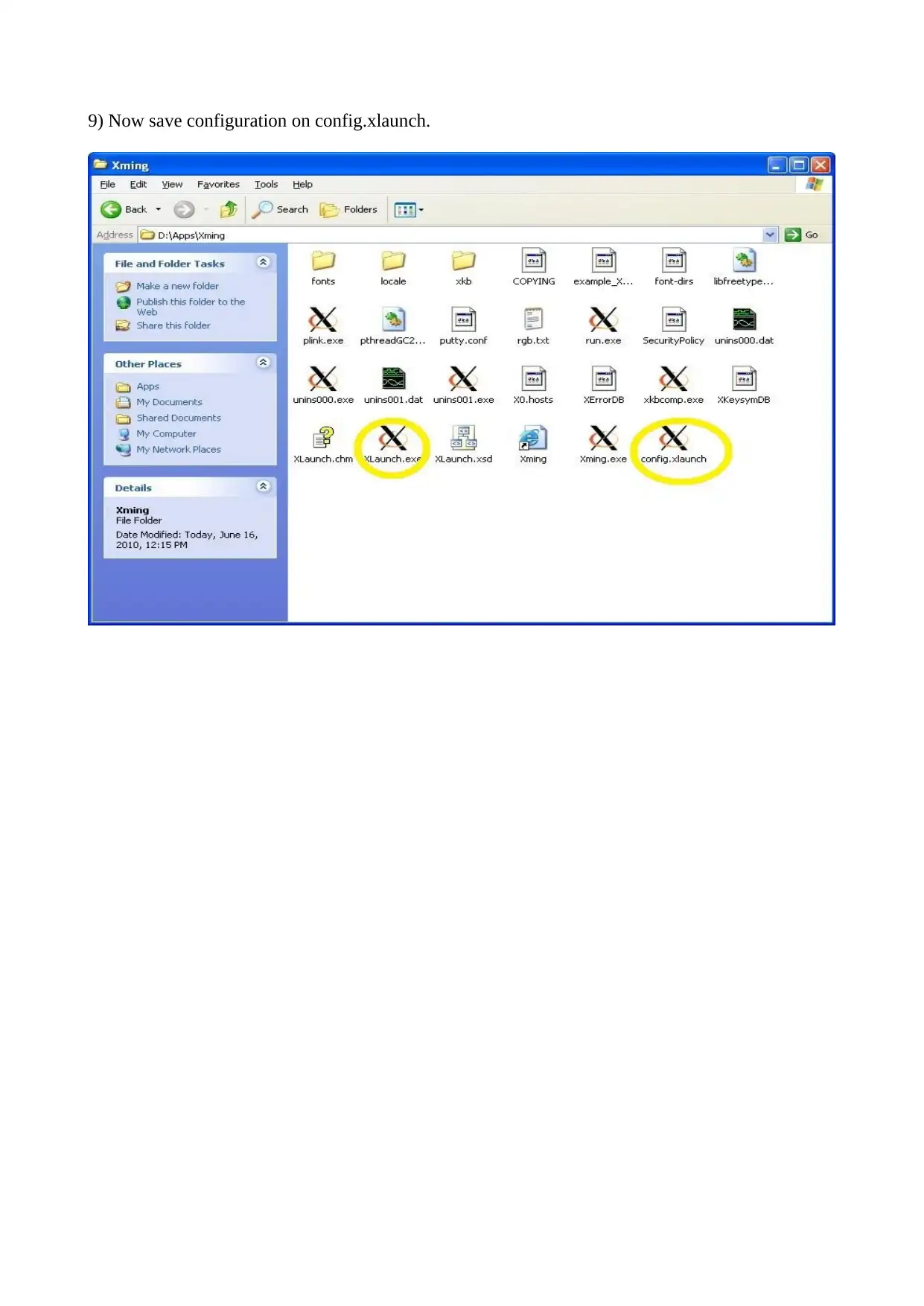
9) Now save configuration on config.xlaunch.
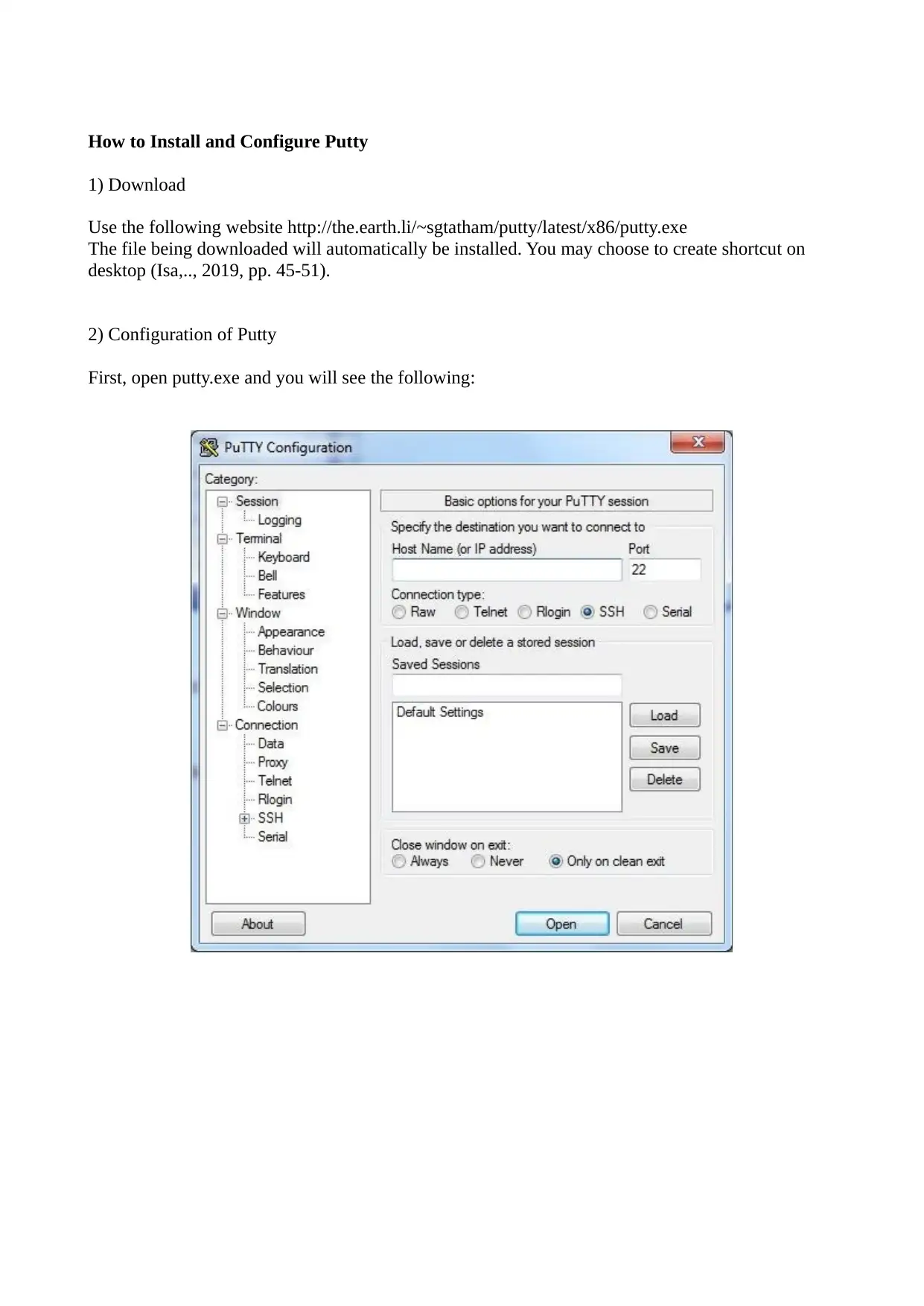
How to Install and Configure Putty
1) Download
Use the following website http://the.earth.li/~sgtatham/putty/latest/x86/putty.exe
The file being downloaded will automatically be installed. You may choose to create shortcut on
desktop (Isa,.., 2019, pp. 45-51).
2) Configuration of Putty
First, open putty.exe and you will see the following:
1) Download
Use the following website http://the.earth.li/~sgtatham/putty/latest/x86/putty.exe
The file being downloaded will automatically be installed. You may choose to create shortcut on
desktop (Isa,.., 2019, pp. 45-51).
2) Configuration of Putty
First, open putty.exe and you will see the following:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
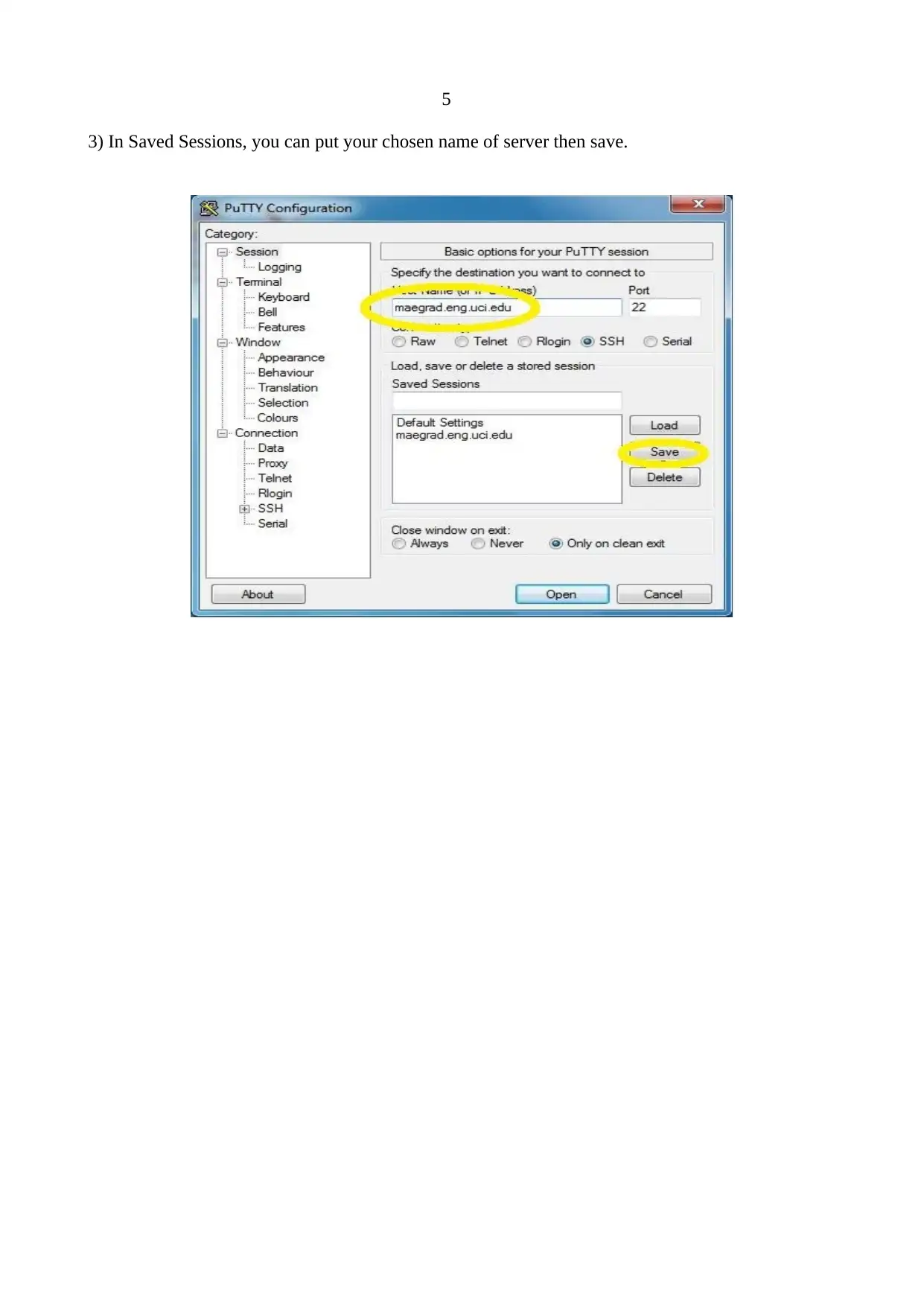
5
3) In Saved Sessions, you can put your chosen name of server then save.
3) In Saved Sessions, you can put your chosen name of server then save.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
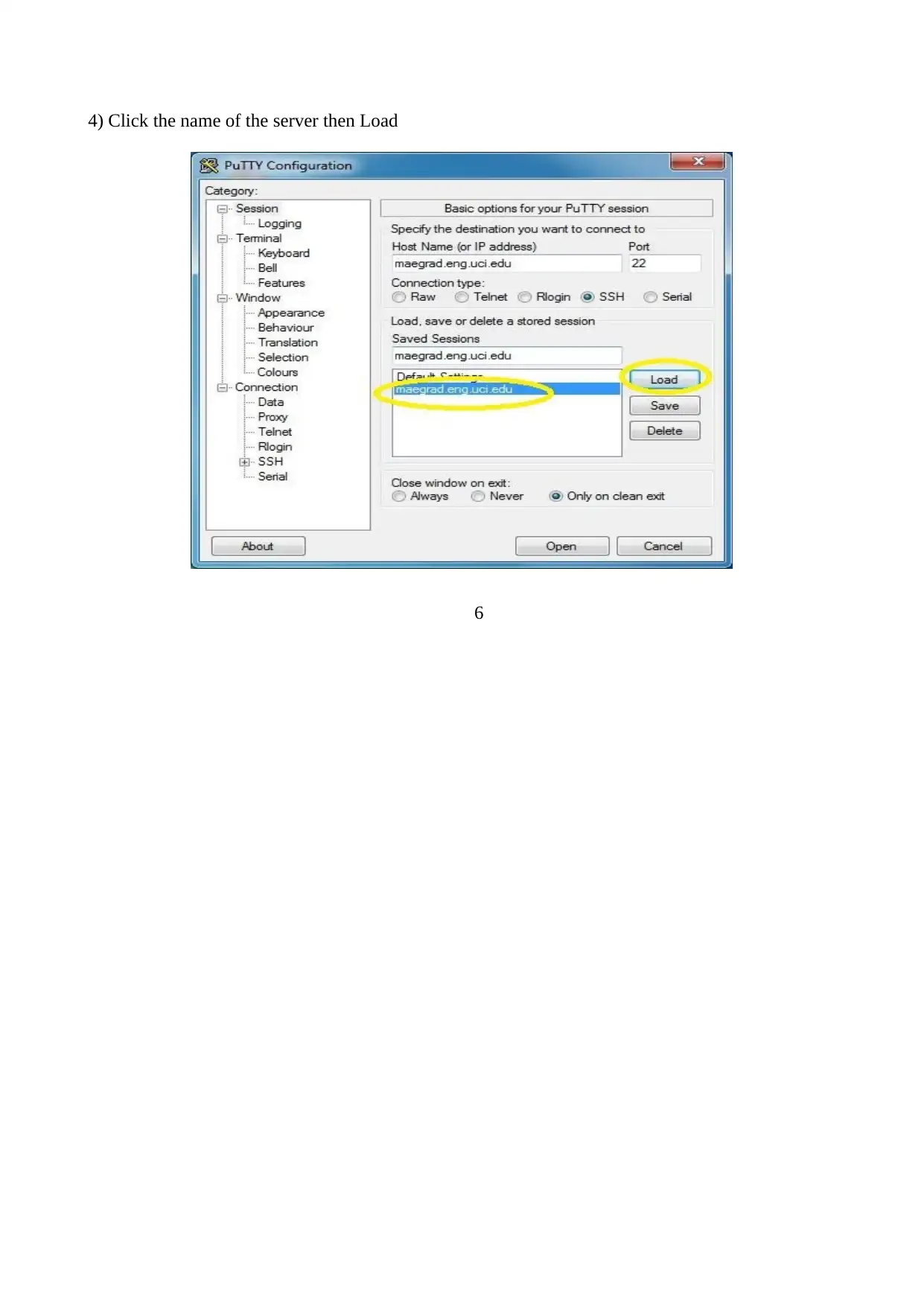
4) Click the name of the server then Load
6
6
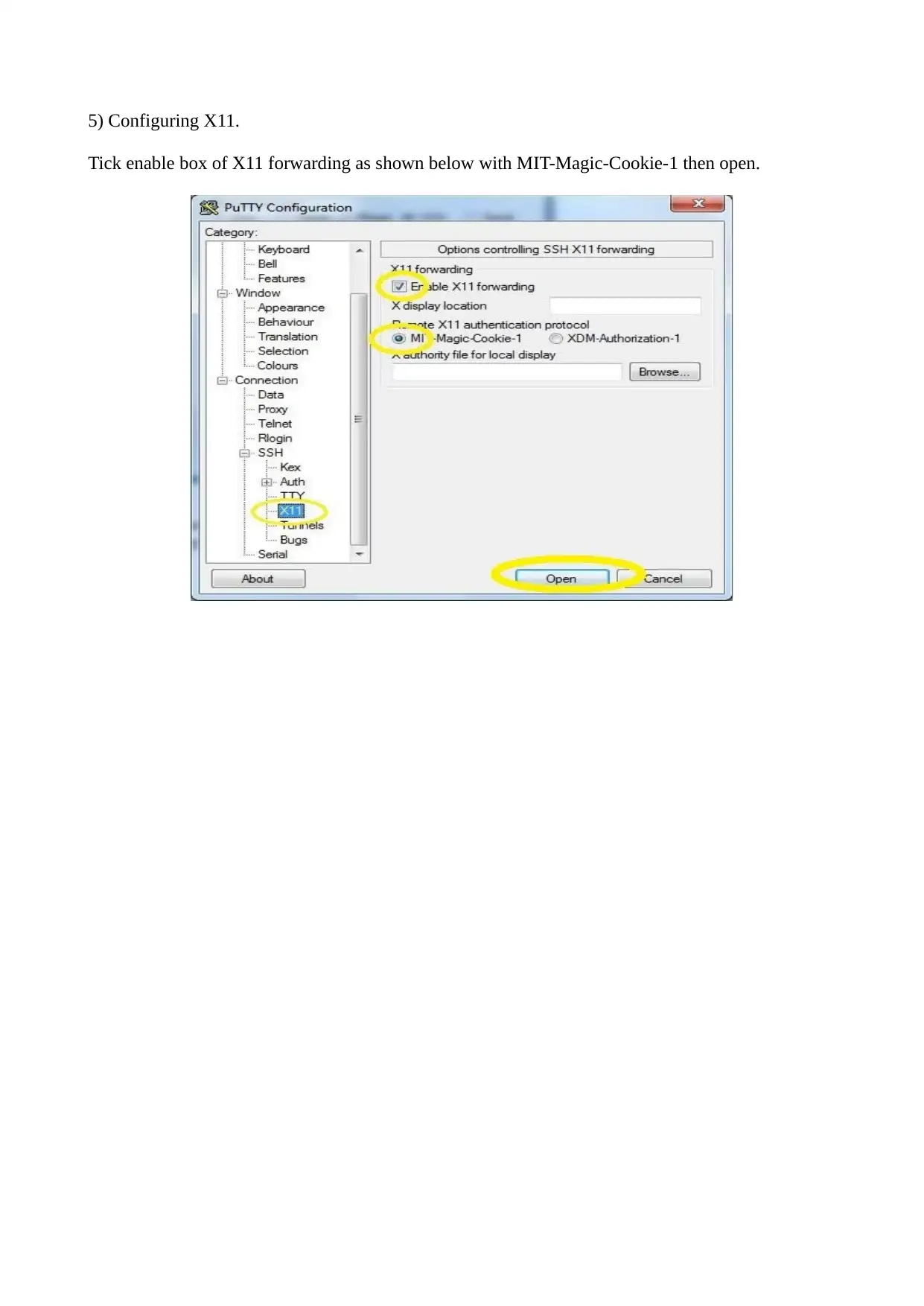
5) Configuring X11.
Tick enable box of X11 forwarding as shown below with MIT-Magic-Cookie-1 then open.
Tick enable box of X11 forwarding as shown below with MIT-Magic-Cookie-1 then open.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 44
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





