Wireless Network and Security
VerifiedAdded on 2023/04/07
|16
|4456
|155
AI Summary
This article discusses the importance of wireless network security and provides insights on designing and implementing a secure network. It also explores the ethical implications of network security and introduces Boson Netsim as a tool for network simulation.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

TITLE: WIRELESS NETWORK AND SECURITY
Wireless Network and security
Wireless Network and security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abstract
A wireless network has become the core in our today life both in businesses and also in our homes.
Good design and implementation should, therefore, be employed to ensure proper working of the
network. Ethics in a network is the most important aspect since these principles will help govern
and prevent its efficiency. IT experts are the personnel's to be relied on. They can help us to secure a
network from unauthorized access. Sensitive information of a business or a company should be kept
undisclosed to malicious people who want to manipulate for there own benefits but against the
businesses or companies wishes [1]. There should be no access to information by anybody except
only the authorized people who can keep data safe and they are responsible in any case. In modern
technology, there are different types of IT experts who use their skills for goodwill and also there
are those who use their skills for malicious purposes. Good design and implementation of the
wireless network is required since this as emerge to be a widely used type of network and many
people have trusted its availability and accessibility. Security of this wireless network is, therefore,
the most important. Information such passwords of the network should be kept confidential, secure
and unavailable to unauthorized people. In case of any malicious act on the network then its
important to consult the IT expert immediately before the malicious person gain access to the most
important and sensitive information [3].
Introduction
The most confidential way of sending data to the intended client is through encryption.
Confidentiality is the most and important way of communicating since the information to be passed
might be very important and agent therefore to avoid misconduct then it should be encrypted only.
WPA2 will generate keys for encryption for data being transmitted and RADIUS will perform the
authentication process. Integrity is paramount for communication in all aspects of life. Real
information should always reach out to the targeted client for communication to be effective. Both
WPA2 and RADIUS performs an important role in ensuring the information being sent is secured
by encrypting and only to be accessed by the authorized users [2]. In our businesses or our personal
lives, we always want information to be available to our clients or partners. The use of RADIUS
and WPA2 will make the availability of the information to be easy and efficient. Through
encryption and authentication of the data to the right people, this availability will be possible.
Sometimes information can be distorted by malicious people hence the communication will be
killed to make the information unavailable. This two methods of wireless security as a played a
major role. Information must always be authenticated to users. RADIUS has made this process very
easy and reliable. WPA2 also performs a key role in the encryption of data. Information must
always reach out to the authorized people. Through encryption of data by WPA2 process, then only
authorized clients will have access to the information [4].
A wireless network has become the core in our today life both in businesses and also in our homes.
Good design and implementation should, therefore, be employed to ensure proper working of the
network. Ethics in a network is the most important aspect since these principles will help govern
and prevent its efficiency. IT experts are the personnel's to be relied on. They can help us to secure a
network from unauthorized access. Sensitive information of a business or a company should be kept
undisclosed to malicious people who want to manipulate for there own benefits but against the
businesses or companies wishes [1]. There should be no access to information by anybody except
only the authorized people who can keep data safe and they are responsible in any case. In modern
technology, there are different types of IT experts who use their skills for goodwill and also there
are those who use their skills for malicious purposes. Good design and implementation of the
wireless network is required since this as emerge to be a widely used type of network and many
people have trusted its availability and accessibility. Security of this wireless network is, therefore,
the most important. Information such passwords of the network should be kept confidential, secure
and unavailable to unauthorized people. In case of any malicious act on the network then its
important to consult the IT expert immediately before the malicious person gain access to the most
important and sensitive information [3].
Introduction
The most confidential way of sending data to the intended client is through encryption.
Confidentiality is the most and important way of communicating since the information to be passed
might be very important and agent therefore to avoid misconduct then it should be encrypted only.
WPA2 will generate keys for encryption for data being transmitted and RADIUS will perform the
authentication process. Integrity is paramount for communication in all aspects of life. Real
information should always reach out to the targeted client for communication to be effective. Both
WPA2 and RADIUS performs an important role in ensuring the information being sent is secured
by encrypting and only to be accessed by the authorized users [2]. In our businesses or our personal
lives, we always want information to be available to our clients or partners. The use of RADIUS
and WPA2 will make the availability of the information to be easy and efficient. Through
encryption and authentication of the data to the right people, this availability will be possible.
Sometimes information can be distorted by malicious people hence the communication will be
killed to make the information unavailable. This two methods of wireless security as a played a
major role. Information must always be authenticated to users. RADIUS has made this process very
easy and reliable. WPA2 also performs a key role in the encryption of data. Information must
always reach out to the authorized people. Through encryption of data by WPA2 process, then only
authorized clients will have access to the information [4].

Ethical implications of secure wireless network
A wireless network has become the core in our today life both in businesses and also in our homes.
Good design and implementation should, therefore, be employed to ensure proper working of the
network. Ethics in a network is the most important aspect since these principles will help govern
and prevent its efficiency. IT experts are the personnel's to be relied on. They can help us to secure a
network from unauthorized access. Sensitive information of a business or a company should be kept
undisclosed to malicious people who want to manipulate for there own benefits but against the
businesses or companies wishes. There should be no access to information by anybody except only
the authorized people who can keep data safe and they are responsible in any case. In modern
technology, there are different types of IT experts who use their skills for goodwill and also there
are those who use their skills for malicious purposes. They are known as hackers. Hacking is trying
to access information by breaking into somebody's network either by there knowledge or without
there knowledge. The "black hat" hackers are the malicious experts who want to manipulate the
information with the owns permission and they use such information for there own purposes. The
"white hat" hackers are the good experts whose use their skills to help the business or company to
acquire or have access to the information in case the password is lost or if malicious hackers had
tried to manipulate the companies information. The "white hat" hackers are most trusted experts
when it comes to the ethics of the business network. Security is the most important thing in any
business or company since that's the storage of everything nowadays are found in clouds [5].
Good design and implementation of the wireless network is required since this as emerge to be a
widely used type of network and many people have trusted its availability and accessibility.
Security of this wireless network is, therefore, the most important. Information such passwords of
the network should be kept confidential, secure and unavailable to unauthorized people. In case of
any malicious act on the network then its important to consult the IT expert immediately before the
malicious person gain access to the most important and sensitive information [6].
A wireless network has become the core in our today life both in businesses and also in our homes.
Good design and implementation should, therefore, be employed to ensure proper working of the
network. Ethics in a network is the most important aspect since these principles will help govern
and prevent its efficiency. IT experts are the personnel's to be relied on. They can help us to secure a
network from unauthorized access. Sensitive information of a business or a company should be kept
undisclosed to malicious people who want to manipulate for there own benefits but against the
businesses or companies wishes. There should be no access to information by anybody except only
the authorized people who can keep data safe and they are responsible in any case. In modern
technology, there are different types of IT experts who use their skills for goodwill and also there
are those who use their skills for malicious purposes. They are known as hackers. Hacking is trying
to access information by breaking into somebody's network either by there knowledge or without
there knowledge. The "black hat" hackers are the malicious experts who want to manipulate the
information with the owns permission and they use such information for there own purposes. The
"white hat" hackers are the good experts whose use their skills to help the business or company to
acquire or have access to the information in case the password is lost or if malicious hackers had
tried to manipulate the companies information. The "white hat" hackers are most trusted experts
when it comes to the ethics of the business network. Security is the most important thing in any
business or company since that's the storage of everything nowadays are found in clouds [5].
Good design and implementation of the wireless network is required since this as emerge to be a
widely used type of network and many people have trusted its availability and accessibility.
Security of this wireless network is, therefore, the most important. Information such passwords of
the network should be kept confidential, secure and unavailable to unauthorized people. In case of
any malicious act on the network then its important to consult the IT expert immediately before the
malicious person gain access to the most important and sensitive information [6].

Wireless network designing using Boson Netsim
The Boson Netsim is a network technique design for simulators in Cisco. It is used to study the
traffics and there scenarios. Network simulation is scenario where a software or any other tool is
used to analyses the traffic or performs in a network concerning certain performance. This will
involve the monitoring and analyzing using network devices like routers, data links and packets in a
network. This is normally done in labs because sometimes it requires certain environments like
isolation. IT experts use it because of its versatility and powerfulness of network simulation. It is a
good software that can be used to simulate network traffic of the real network by designing and
controlling by the network experts. It allows the experts to create a very new topology and also they
can modify the existing ones. This tool helps you to work without packet tracer and therefore this is
the best alternative [7]. NetSim analytics are used for comparison and analyzing several protocols
under several networks like wireless or cellular. The data collected from analysis are presented by
use of graphs. This representations of data will let you compare the difference and note the changes
during the process. Mechanisms of allocating the available resources by each router depends on the
actions implemented by router to monitor the packets being buffered while are on the process of
submission [3]. The packets therefore, must queue in some manners for the buffer to use priority of
first-in-first-out . The packets will get served based on arrival time by the router. Priority technique
is used here so that smart flows of data can be done. Routing Information Protocol (RIP) is a
technique for computing routes where it allows hosts and gateways to interact in IP network.
Algorithm can be used in computation of this process. Routing will be invisible because of this IP
concept. Distance measurements are also included where the data-grams should have destination
entity.
A network model is the simplest and reliable way of showing devices and their relationship on how
they work. This comprises devices like switches, hubs, routers, cables etc. Modeling shows how
they work together and how mutually they depend on each other throughout the process. Netsim
network and its own architecture structures can be drawn using netsim software. It accepts the input
of data by the end-user through the process of configurations the flow of packets in the layers of
network. In every stage in layers then correct configurations and encryption of data is always done
appropriately in those layers hence data is secured. WiFi is more commonly used and its now
around 90% used every where because of its availability, offices and homes prefer it. It is very
simple to connect since you can only power on WiFi in your phone then all available WiFi will pop
up then you choose the one you want. All devices such as phones or laptops uses it. The device
required here is router where it will act like a distributor and the number of users can also be limited
[2].
The Boson Netsim is a network technique design for simulators in Cisco. It is used to study the
traffics and there scenarios. Network simulation is scenario where a software or any other tool is
used to analyses the traffic or performs in a network concerning certain performance. This will
involve the monitoring and analyzing using network devices like routers, data links and packets in a
network. This is normally done in labs because sometimes it requires certain environments like
isolation. IT experts use it because of its versatility and powerfulness of network simulation. It is a
good software that can be used to simulate network traffic of the real network by designing and
controlling by the network experts. It allows the experts to create a very new topology and also they
can modify the existing ones. This tool helps you to work without packet tracer and therefore this is
the best alternative [7]. NetSim analytics are used for comparison and analyzing several protocols
under several networks like wireless or cellular. The data collected from analysis are presented by
use of graphs. This representations of data will let you compare the difference and note the changes
during the process. Mechanisms of allocating the available resources by each router depends on the
actions implemented by router to monitor the packets being buffered while are on the process of
submission [3]. The packets therefore, must queue in some manners for the buffer to use priority of
first-in-first-out . The packets will get served based on arrival time by the router. Priority technique
is used here so that smart flows of data can be done. Routing Information Protocol (RIP) is a
technique for computing routes where it allows hosts and gateways to interact in IP network.
Algorithm can be used in computation of this process. Routing will be invisible because of this IP
concept. Distance measurements are also included where the data-grams should have destination
entity.
A network model is the simplest and reliable way of showing devices and their relationship on how
they work. This comprises devices like switches, hubs, routers, cables etc. Modeling shows how
they work together and how mutually they depend on each other throughout the process. Netsim
network and its own architecture structures can be drawn using netsim software. It accepts the input
of data by the end-user through the process of configurations the flow of packets in the layers of
network. In every stage in layers then correct configurations and encryption of data is always done
appropriately in those layers hence data is secured. WiFi is more commonly used and its now
around 90% used every where because of its availability, offices and homes prefer it. It is very
simple to connect since you can only power on WiFi in your phone then all available WiFi will pop
up then you choose the one you want. All devices such as phones or laptops uses it. The device
required here is router where it will act like a distributor and the number of users can also be limited
[2].
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
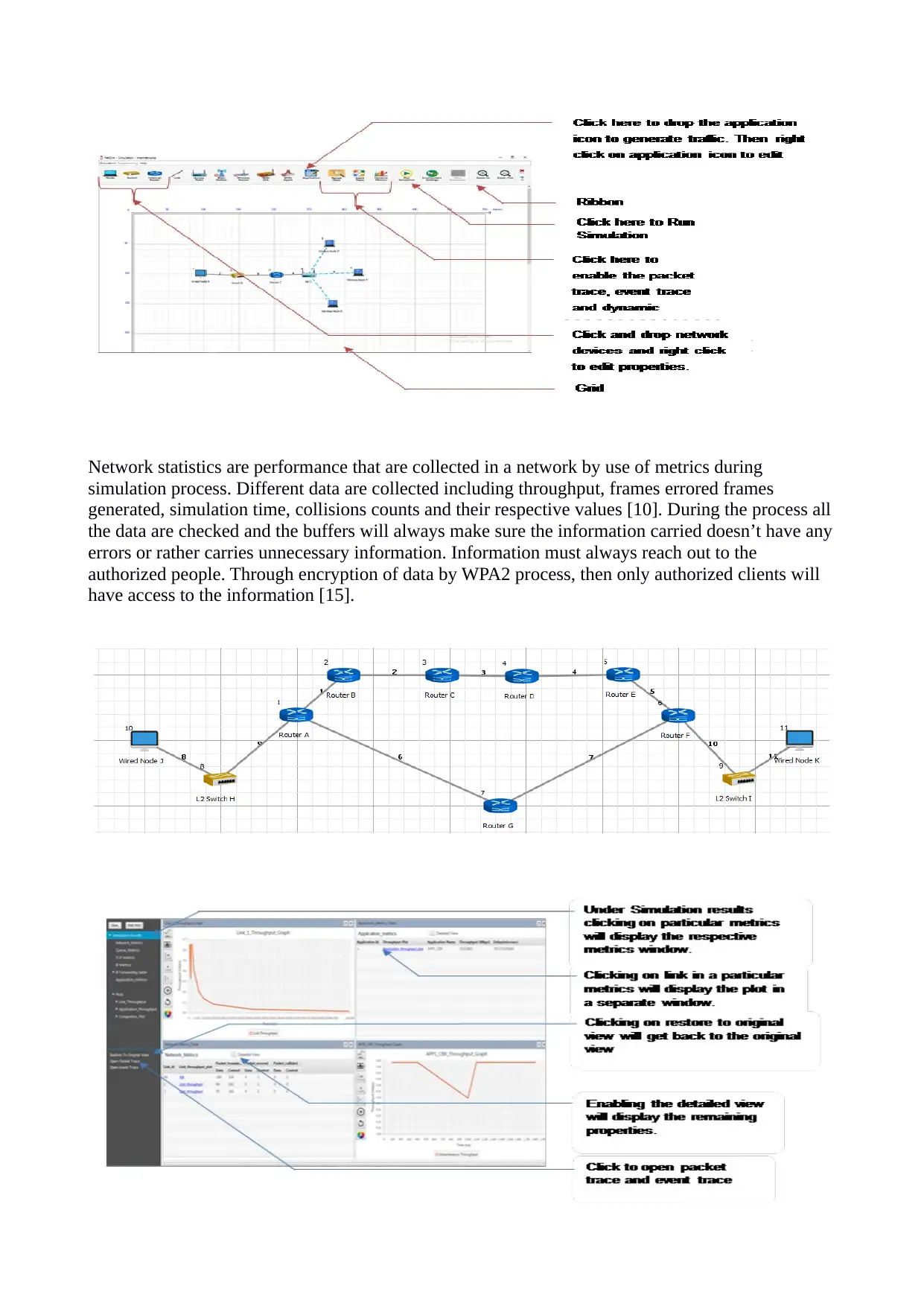
Network statistics are performance that are collected in a network by use of metrics during
simulation process. Different data are collected including throughput, frames errored frames
generated, simulation time, collisions counts and their respective values [10]. During the process all
the data are checked and the buffers will always make sure the information carried doesn’t have any
errors or rather carries unnecessary information. Information must always reach out to the
authorized people. Through encryption of data by WPA2 process, then only authorized clients will
have access to the information [15].
simulation process. Different data are collected including throughput, frames errored frames
generated, simulation time, collisions counts and their respective values [10]. During the process all
the data are checked and the buffers will always make sure the information carried doesn’t have any
errors or rather carries unnecessary information. Information must always reach out to the
authorized people. Through encryption of data by WPA2 process, then only authorized clients will
have access to the information [15].
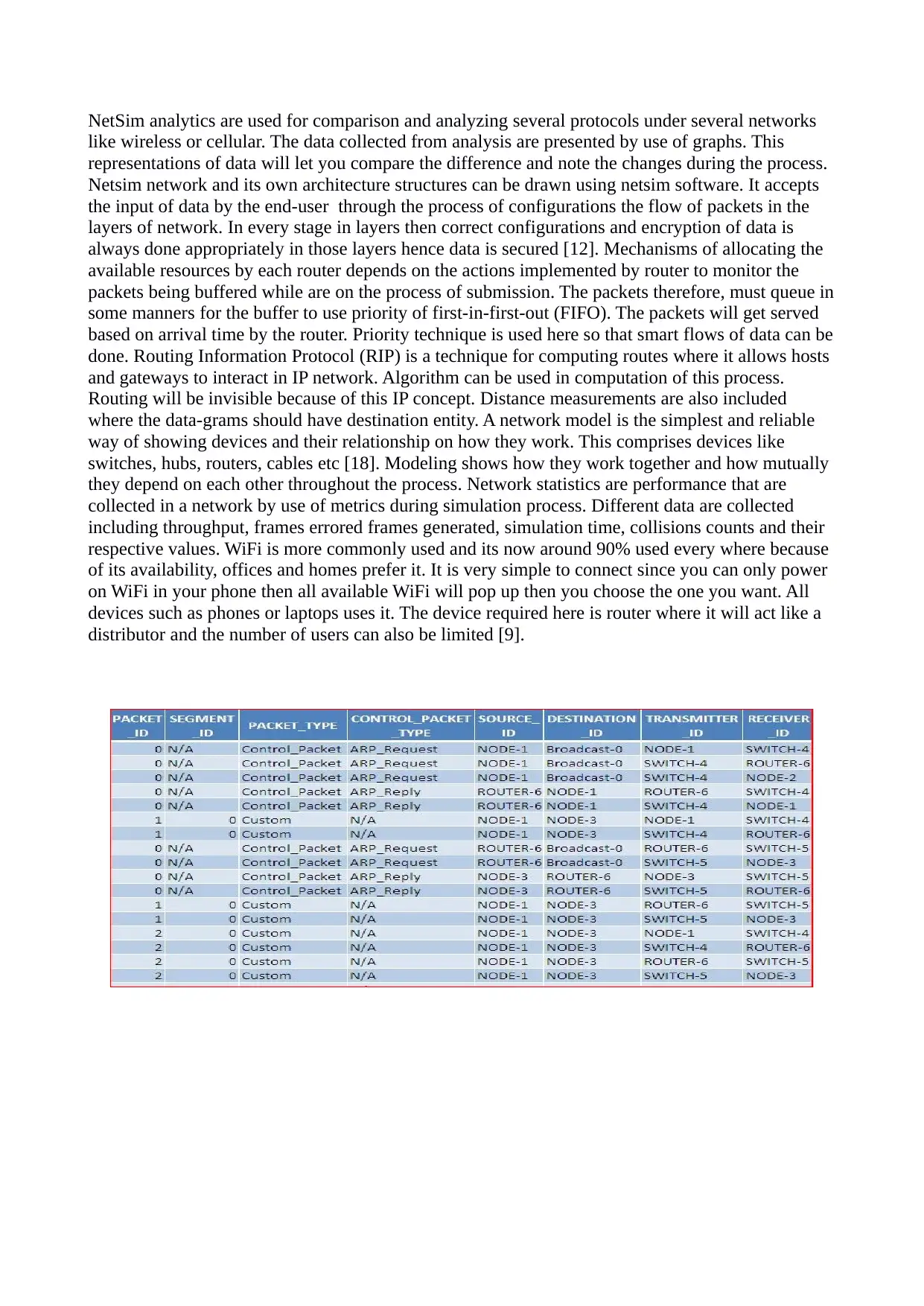
NetSim analytics are used for comparison and analyzing several protocols under several networks
like wireless or cellular. The data collected from analysis are presented by use of graphs. This
representations of data will let you compare the difference and note the changes during the process.
Netsim network and its own architecture structures can be drawn using netsim software. It accepts
the input of data by the end-user through the process of configurations the flow of packets in the
layers of network. In every stage in layers then correct configurations and encryption of data is
always done appropriately in those layers hence data is secured [12]. Mechanisms of allocating the
available resources by each router depends on the actions implemented by router to monitor the
packets being buffered while are on the process of submission. The packets therefore, must queue in
some manners for the buffer to use priority of first-in-first-out (FIFO). The packets will get served
based on arrival time by the router. Priority technique is used here so that smart flows of data can be
done. Routing Information Protocol (RIP) is a technique for computing routes where it allows hosts
and gateways to interact in IP network. Algorithm can be used in computation of this process.
Routing will be invisible because of this IP concept. Distance measurements are also included
where the data-grams should have destination entity. A network model is the simplest and reliable
way of showing devices and their relationship on how they work. This comprises devices like
switches, hubs, routers, cables etc [18]. Modeling shows how they work together and how mutually
they depend on each other throughout the process. Network statistics are performance that are
collected in a network by use of metrics during simulation process. Different data are collected
including throughput, frames errored frames generated, simulation time, collisions counts and their
respective values. WiFi is more commonly used and its now around 90% used every where because
of its availability, offices and homes prefer it. It is very simple to connect since you can only power
on WiFi in your phone then all available WiFi will pop up then you choose the one you want. All
devices such as phones or laptops uses it. The device required here is router where it will act like a
distributor and the number of users can also be limited [9].
like wireless or cellular. The data collected from analysis are presented by use of graphs. This
representations of data will let you compare the difference and note the changes during the process.
Netsim network and its own architecture structures can be drawn using netsim software. It accepts
the input of data by the end-user through the process of configurations the flow of packets in the
layers of network. In every stage in layers then correct configurations and encryption of data is
always done appropriately in those layers hence data is secured [12]. Mechanisms of allocating the
available resources by each router depends on the actions implemented by router to monitor the
packets being buffered while are on the process of submission. The packets therefore, must queue in
some manners for the buffer to use priority of first-in-first-out (FIFO). The packets will get served
based on arrival time by the router. Priority technique is used here so that smart flows of data can be
done. Routing Information Protocol (RIP) is a technique for computing routes where it allows hosts
and gateways to interact in IP network. Algorithm can be used in computation of this process.
Routing will be invisible because of this IP concept. Distance measurements are also included
where the data-grams should have destination entity. A network model is the simplest and reliable
way of showing devices and their relationship on how they work. This comprises devices like
switches, hubs, routers, cables etc [18]. Modeling shows how they work together and how mutually
they depend on each other throughout the process. Network statistics are performance that are
collected in a network by use of metrics during simulation process. Different data are collected
including throughput, frames errored frames generated, simulation time, collisions counts and their
respective values. WiFi is more commonly used and its now around 90% used every where because
of its availability, offices and homes prefer it. It is very simple to connect since you can only power
on WiFi in your phone then all available WiFi will pop up then you choose the one you want. All
devices such as phones or laptops uses it. The device required here is router where it will act like a
distributor and the number of users can also be limited [9].
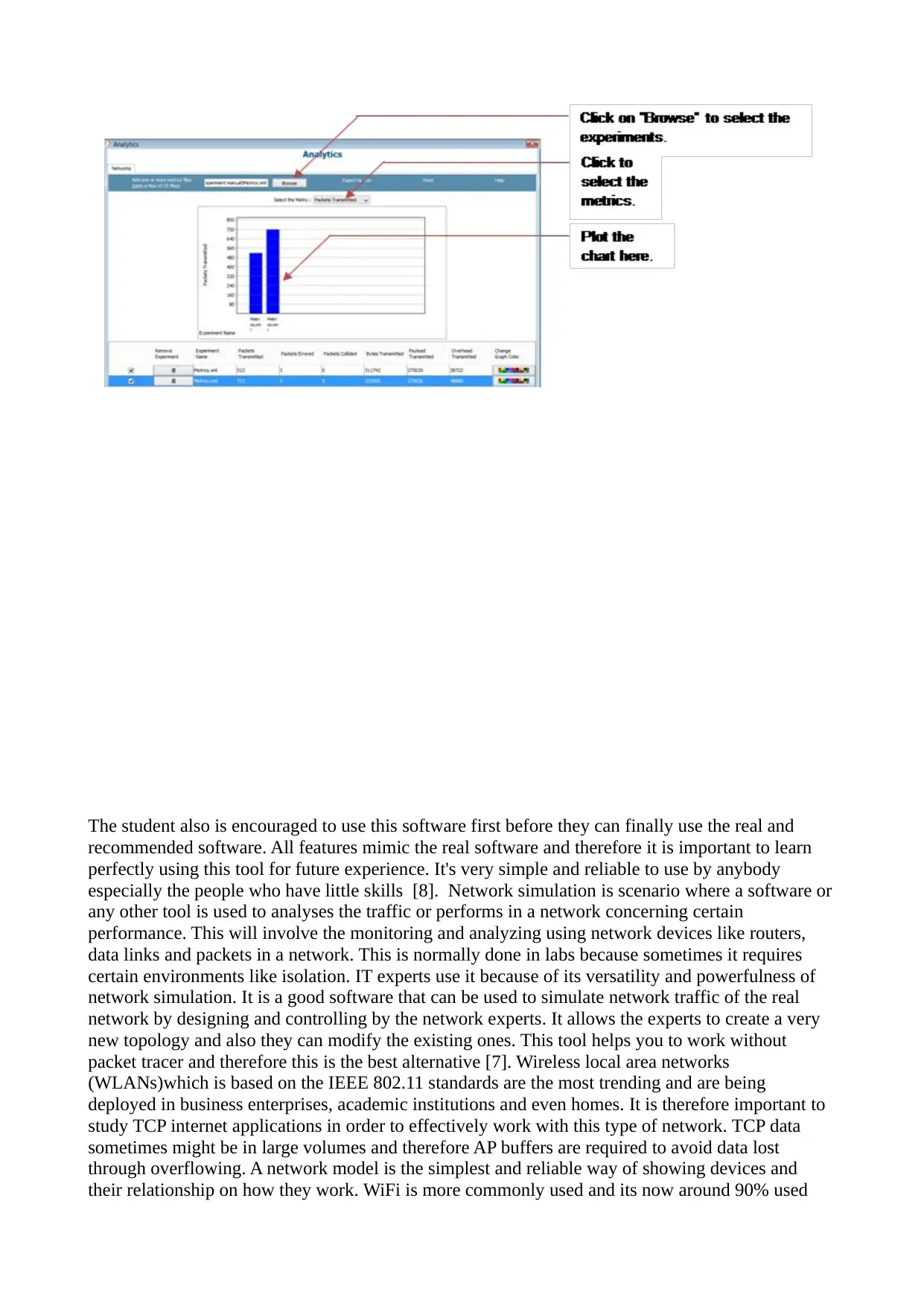
The student also is encouraged to use this software first before they can finally use the real and
recommended software. All features mimic the real software and therefore it is important to learn
perfectly using this tool for future experience. It's very simple and reliable to use by anybody
especially the people who have little skills [8]. Network simulation is scenario where a software or
any other tool is used to analyses the traffic or performs in a network concerning certain
performance. This will involve the monitoring and analyzing using network devices like routers,
data links and packets in a network. This is normally done in labs because sometimes it requires
certain environments like isolation. IT experts use it because of its versatility and powerfulness of
network simulation. It is a good software that can be used to simulate network traffic of the real
network by designing and controlling by the network experts. It allows the experts to create a very
new topology and also they can modify the existing ones. This tool helps you to work without
packet tracer and therefore this is the best alternative [7]. Wireless local area networks
(WLANs)which is based on the IEEE 802.11 standards are the most trending and are being
deployed in business enterprises, academic institutions and even homes. It is therefore important to
study TCP internet applications in order to effectively work with this type of network. TCP data
sometimes might be in large volumes and therefore AP buffers are required to avoid data lost
through overflowing. A network model is the simplest and reliable way of showing devices and
their relationship on how they work. WiFi is more commonly used and its now around 90% used
recommended software. All features mimic the real software and therefore it is important to learn
perfectly using this tool for future experience. It's very simple and reliable to use by anybody
especially the people who have little skills [8]. Network simulation is scenario where a software or
any other tool is used to analyses the traffic or performs in a network concerning certain
performance. This will involve the monitoring and analyzing using network devices like routers,
data links and packets in a network. This is normally done in labs because sometimes it requires
certain environments like isolation. IT experts use it because of its versatility and powerfulness of
network simulation. It is a good software that can be used to simulate network traffic of the real
network by designing and controlling by the network experts. It allows the experts to create a very
new topology and also they can modify the existing ones. This tool helps you to work without
packet tracer and therefore this is the best alternative [7]. Wireless local area networks
(WLANs)which is based on the IEEE 802.11 standards are the most trending and are being
deployed in business enterprises, academic institutions and even homes. It is therefore important to
study TCP internet applications in order to effectively work with this type of network. TCP data
sometimes might be in large volumes and therefore AP buffers are required to avoid data lost
through overflowing. A network model is the simplest and reliable way of showing devices and
their relationship on how they work. WiFi is more commonly used and its now around 90% used
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
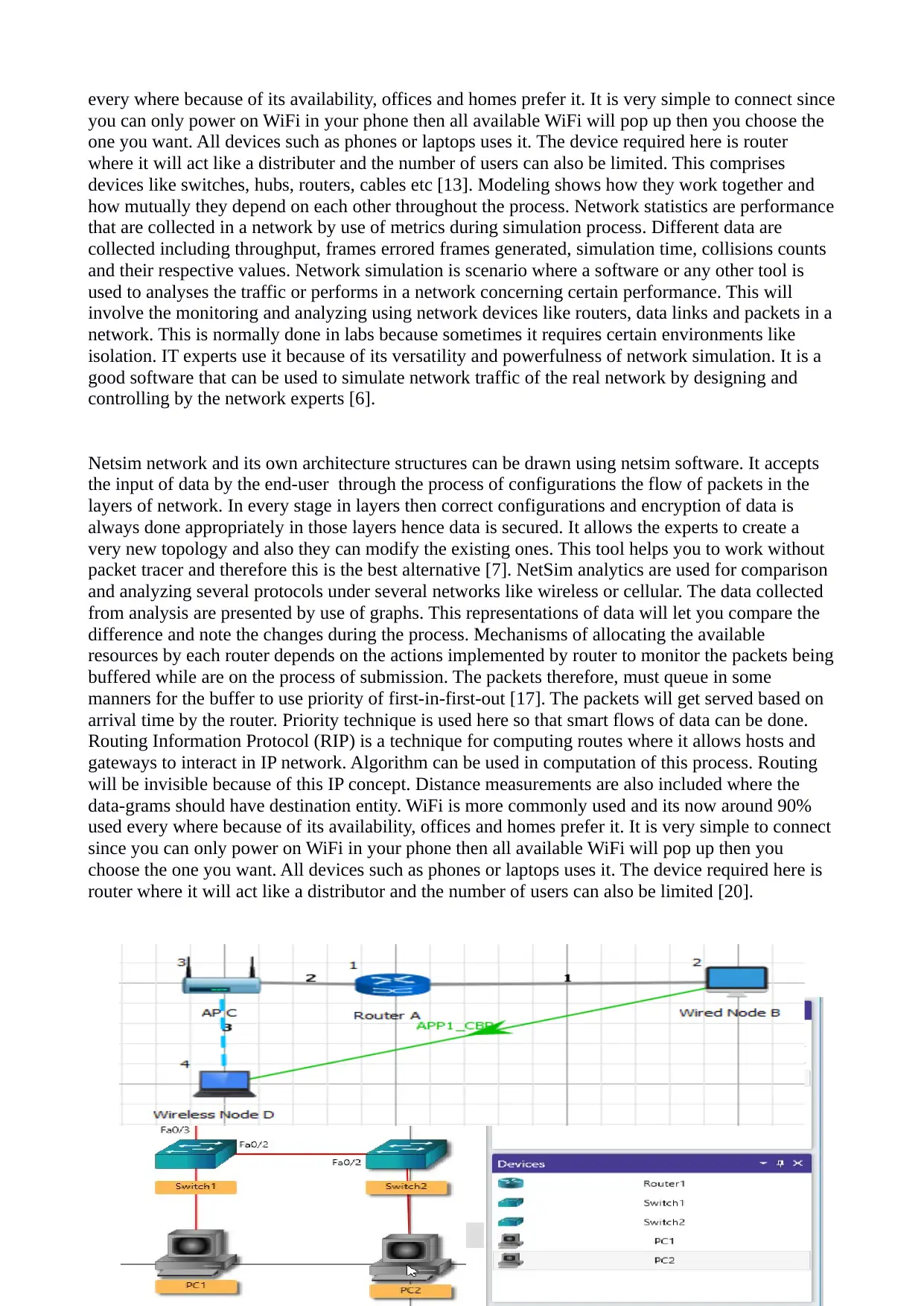
every where because of its availability, offices and homes prefer it. It is very simple to connect since
you can only power on WiFi in your phone then all available WiFi will pop up then you choose the
one you want. All devices such as phones or laptops uses it. The device required here is router
where it will act like a distributer and the number of users can also be limited. This comprises
devices like switches, hubs, routers, cables etc [13]. Modeling shows how they work together and
how mutually they depend on each other throughout the process. Network statistics are performance
that are collected in a network by use of metrics during simulation process. Different data are
collected including throughput, frames errored frames generated, simulation time, collisions counts
and their respective values. Network simulation is scenario where a software or any other tool is
used to analyses the traffic or performs in a network concerning certain performance. This will
involve the monitoring and analyzing using network devices like routers, data links and packets in a
network. This is normally done in labs because sometimes it requires certain environments like
isolation. IT experts use it because of its versatility and powerfulness of network simulation. It is a
good software that can be used to simulate network traffic of the real network by designing and
controlling by the network experts [6].
Netsim network and its own architecture structures can be drawn using netsim software. It accepts
the input of data by the end-user through the process of configurations the flow of packets in the
layers of network. In every stage in layers then correct configurations and encryption of data is
always done appropriately in those layers hence data is secured. It allows the experts to create a
very new topology and also they can modify the existing ones. This tool helps you to work without
packet tracer and therefore this is the best alternative [7]. NetSim analytics are used for comparison
and analyzing several protocols under several networks like wireless or cellular. The data collected
from analysis are presented by use of graphs. This representations of data will let you compare the
difference and note the changes during the process. Mechanisms of allocating the available
resources by each router depends on the actions implemented by router to monitor the packets being
buffered while are on the process of submission. The packets therefore, must queue in some
manners for the buffer to use priority of first-in-first-out [17]. The packets will get served based on
arrival time by the router. Priority technique is used here so that smart flows of data can be done.
Routing Information Protocol (RIP) is a technique for computing routes where it allows hosts and
gateways to interact in IP network. Algorithm can be used in computation of this process. Routing
will be invisible because of this IP concept. Distance measurements are also included where the
data-grams should have destination entity. WiFi is more commonly used and its now around 90%
used every where because of its availability, offices and homes prefer it. It is very simple to connect
since you can only power on WiFi in your phone then all available WiFi will pop up then you
choose the one you want. All devices such as phones or laptops uses it. The device required here is
router where it will act like a distributor and the number of users can also be limited [20].
you can only power on WiFi in your phone then all available WiFi will pop up then you choose the
one you want. All devices such as phones or laptops uses it. The device required here is router
where it will act like a distributer and the number of users can also be limited. This comprises
devices like switches, hubs, routers, cables etc [13]. Modeling shows how they work together and
how mutually they depend on each other throughout the process. Network statistics are performance
that are collected in a network by use of metrics during simulation process. Different data are
collected including throughput, frames errored frames generated, simulation time, collisions counts
and their respective values. Network simulation is scenario where a software or any other tool is
used to analyses the traffic or performs in a network concerning certain performance. This will
involve the monitoring and analyzing using network devices like routers, data links and packets in a
network. This is normally done in labs because sometimes it requires certain environments like
isolation. IT experts use it because of its versatility and powerfulness of network simulation. It is a
good software that can be used to simulate network traffic of the real network by designing and
controlling by the network experts [6].
Netsim network and its own architecture structures can be drawn using netsim software. It accepts
the input of data by the end-user through the process of configurations the flow of packets in the
layers of network. In every stage in layers then correct configurations and encryption of data is
always done appropriately in those layers hence data is secured. It allows the experts to create a
very new topology and also they can modify the existing ones. This tool helps you to work without
packet tracer and therefore this is the best alternative [7]. NetSim analytics are used for comparison
and analyzing several protocols under several networks like wireless or cellular. The data collected
from analysis are presented by use of graphs. This representations of data will let you compare the
difference and note the changes during the process. Mechanisms of allocating the available
resources by each router depends on the actions implemented by router to monitor the packets being
buffered while are on the process of submission. The packets therefore, must queue in some
manners for the buffer to use priority of first-in-first-out [17]. The packets will get served based on
arrival time by the router. Priority technique is used here so that smart flows of data can be done.
Routing Information Protocol (RIP) is a technique for computing routes where it allows hosts and
gateways to interact in IP network. Algorithm can be used in computation of this process. Routing
will be invisible because of this IP concept. Distance measurements are also included where the
data-grams should have destination entity. WiFi is more commonly used and its now around 90%
used every where because of its availability, offices and homes prefer it. It is very simple to connect
since you can only power on WiFi in your phone then all available WiFi will pop up then you
choose the one you want. All devices such as phones or laptops uses it. The device required here is
router where it will act like a distributor and the number of users can also be limited [20].

Analyzing a secured wireless network by use of WPA2 and the RADIUS server
Remote Authentication Dial-In User Service (RADIUS) is a network protocol for server/client. The
client act as a network access server(NAS) while the server is a daemon process on the machine.
The client will pass the information to the server where the server will respond and give out the
required information that was inquired by the client. The server will authenticate the user upon
receiving a request for connection then respond to the client by giving out the necessary and
requested information. A RADIUS server always acts as a proxy server to the client. The RADIUS
server can only perform the authentication but not the encryption process [9].
Remote Authentication Dial-In User Service (RADIUS) is a network protocol for server/client. The
client act as a network access server(NAS) while the server is a daemon process on the machine.
The client will pass the information to the server where the server will respond and give out the
required information that was inquired by the client. The server will authenticate the user upon
receiving a request for connection then respond to the client by giving out the necessary and
requested information. A RADIUS server always acts as a proxy server to the client. The RADIUS
server can only perform the authentication but not the encryption process [9].

WiFi Protected Access(WPA2) is basically wireless keys generation dynamically through
encryption on each data packet transmitted across the internet. This is the most secure since it
ensures the security of the data being transmitted hence avoiding tampering. WPA2 are mainly
found in two forms: WPA2-Enterprise commonly available in large scale businesses and WPA2-
personal which is only found in homes and small scale businesses. This is the most secured kind
way of keeping you WiFi save from malicious attacks and malfunctioning. WPA2 is an advanced
version of the WPA, therefore, more encryption securities are found in WPA2 because of the
upgrade to fit the modern world of the technology [10].
Categories of wireless network analysis using WPA2 and RADIUS server:
1. Confidentiality
The most confidential way of sending data to the intended client is through encryption.
Confidentiality is the most and important way of communicating since the information to be passed
might be very important and agent therefore to avoid misconduct then it should be encrypted only.
WPA2 will generate keys for encryption for data being transmitted and RADIUS will perform the
authentication process [11].
2. Integrity
Integrity is paramount for communication in all aspects of life. Real information should always
reach out to the targeted client for communication to be effective. Both WPA2 and RADIUS
performs an important role in ensuring the information being sent is secured by encrypting and only
to be accessed by the authorized users [12].
3. Availability
In our businesses or our personal lives, we always want information to be available to our clients or
partners. The use of RADIUS and WPA2 will make the availability of the information to be easy
and efficient. Through encryption and authentication of the data to the right people, this availability
will be possible. Sometimes information can be distorted by malicious people hence the
communication will be killed to make the information unavailable. This two methods of wireless
security as played a major role [13].
4. Authentication
Information must always be authenticated to users. RADIUS has made this process very easy and
reliable. WPA2 also performs a key role in the encryption of data [14].
5. Authorization
Information must always reach out to the authorized people. Through encryption of data by WPA2
process, then only authorized clients will have access to the information [15].
Implementation of a wireless network through WPA2 and the RADIUS server
encryption on each data packet transmitted across the internet. This is the most secure since it
ensures the security of the data being transmitted hence avoiding tampering. WPA2 are mainly
found in two forms: WPA2-Enterprise commonly available in large scale businesses and WPA2-
personal which is only found in homes and small scale businesses. This is the most secured kind
way of keeping you WiFi save from malicious attacks and malfunctioning. WPA2 is an advanced
version of the WPA, therefore, more encryption securities are found in WPA2 because of the
upgrade to fit the modern world of the technology [10].
Categories of wireless network analysis using WPA2 and RADIUS server:
1. Confidentiality
The most confidential way of sending data to the intended client is through encryption.
Confidentiality is the most and important way of communicating since the information to be passed
might be very important and agent therefore to avoid misconduct then it should be encrypted only.
WPA2 will generate keys for encryption for data being transmitted and RADIUS will perform the
authentication process [11].
2. Integrity
Integrity is paramount for communication in all aspects of life. Real information should always
reach out to the targeted client for communication to be effective. Both WPA2 and RADIUS
performs an important role in ensuring the information being sent is secured by encrypting and only
to be accessed by the authorized users [12].
3. Availability
In our businesses or our personal lives, we always want information to be available to our clients or
partners. The use of RADIUS and WPA2 will make the availability of the information to be easy
and efficient. Through encryption and authentication of the data to the right people, this availability
will be possible. Sometimes information can be distorted by malicious people hence the
communication will be killed to make the information unavailable. This two methods of wireless
security as played a major role [13].
4. Authentication
Information must always be authenticated to users. RADIUS has made this process very easy and
reliable. WPA2 also performs a key role in the encryption of data [14].
5. Authorization
Information must always reach out to the authorized people. Through encryption of data by WPA2
process, then only authorized clients will have access to the information [15].
Implementation of a wireless network through WPA2 and the RADIUS server
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Implementation of the wireless RADIUS server in a network depends on the intended use. The
server can be large or small depending on the number of clients you want to reach out at. Logically,
a small server will always be reliable to the small number of clients and a large server will also be
reliable to a large number of clients because of the information to be stored is voluminous and
therefore space should be enough to accumulate such information. Security is also one of the keys
to why the RADIUS server is chosen. Only authorized users can access the information in the
servers. Installation of RADIUS servers is economical depending on the use hence it is cost
effective because if you want for small scale business then it will always fit the budget.
Management also is very easy when it is always handled by IT experts [16].
WPA2 is the wireless network connection that is encouraged to be implemented because of the
network securities vulnerabilities over the previous version WPA. WPA2 will generate keys for
encryption for data being transmitted and RADIUS will perform the authentication process. This
type of network is now widely used among all the network companies on their networks since it is
very secured and vulnerable due to its nature of encryption. Installation requires experts with high
skills because of its securities measures. It is also economical because the cost will vary according
to the type of business or the number of clients to use. Management is quite easily because only a
few people will have access to it hence no tampering or such kinds of people trying to do there own
things. Also because of its security, the hackers cannot easily get into access hence it cannot cost
the business by such kinds of problems experienced by other people costing a lot of money to fix
and losing of important data of businesses or company [17].
Good design and implementation of the wireless network is required since this as emerge to be a
widely used type of network and many people have trusted its availability and accessibility.
Security of this wireless network is, therefore, the most important. Information such passwords of
the network should be kept confidential, secure and unavailable to unauthorized people. In case of
any malicious act on the network then its important to consult the IT expert immediately before the
malicious person gain access to the most important and sensitive information [18].
server can be large or small depending on the number of clients you want to reach out at. Logically,
a small server will always be reliable to the small number of clients and a large server will also be
reliable to a large number of clients because of the information to be stored is voluminous and
therefore space should be enough to accumulate such information. Security is also one of the keys
to why the RADIUS server is chosen. Only authorized users can access the information in the
servers. Installation of RADIUS servers is economical depending on the use hence it is cost
effective because if you want for small scale business then it will always fit the budget.
Management also is very easy when it is always handled by IT experts [16].
WPA2 is the wireless network connection that is encouraged to be implemented because of the
network securities vulnerabilities over the previous version WPA. WPA2 will generate keys for
encryption for data being transmitted and RADIUS will perform the authentication process. This
type of network is now widely used among all the network companies on their networks since it is
very secured and vulnerable due to its nature of encryption. Installation requires experts with high
skills because of its securities measures. It is also economical because the cost will vary according
to the type of business or the number of clients to use. Management is quite easily because only a
few people will have access to it hence no tampering or such kinds of people trying to do there own
things. Also because of its security, the hackers cannot easily get into access hence it cannot cost
the business by such kinds of problems experienced by other people costing a lot of money to fix
and losing of important data of businesses or company [17].
Good design and implementation of the wireless network is required since this as emerge to be a
widely used type of network and many people have trusted its availability and accessibility.
Security of this wireless network is, therefore, the most important. Information such passwords of
the network should be kept confidential, secure and unavailable to unauthorized people. In case of
any malicious act on the network then its important to consult the IT expert immediately before the
malicious person gain access to the most important and sensitive information [18].
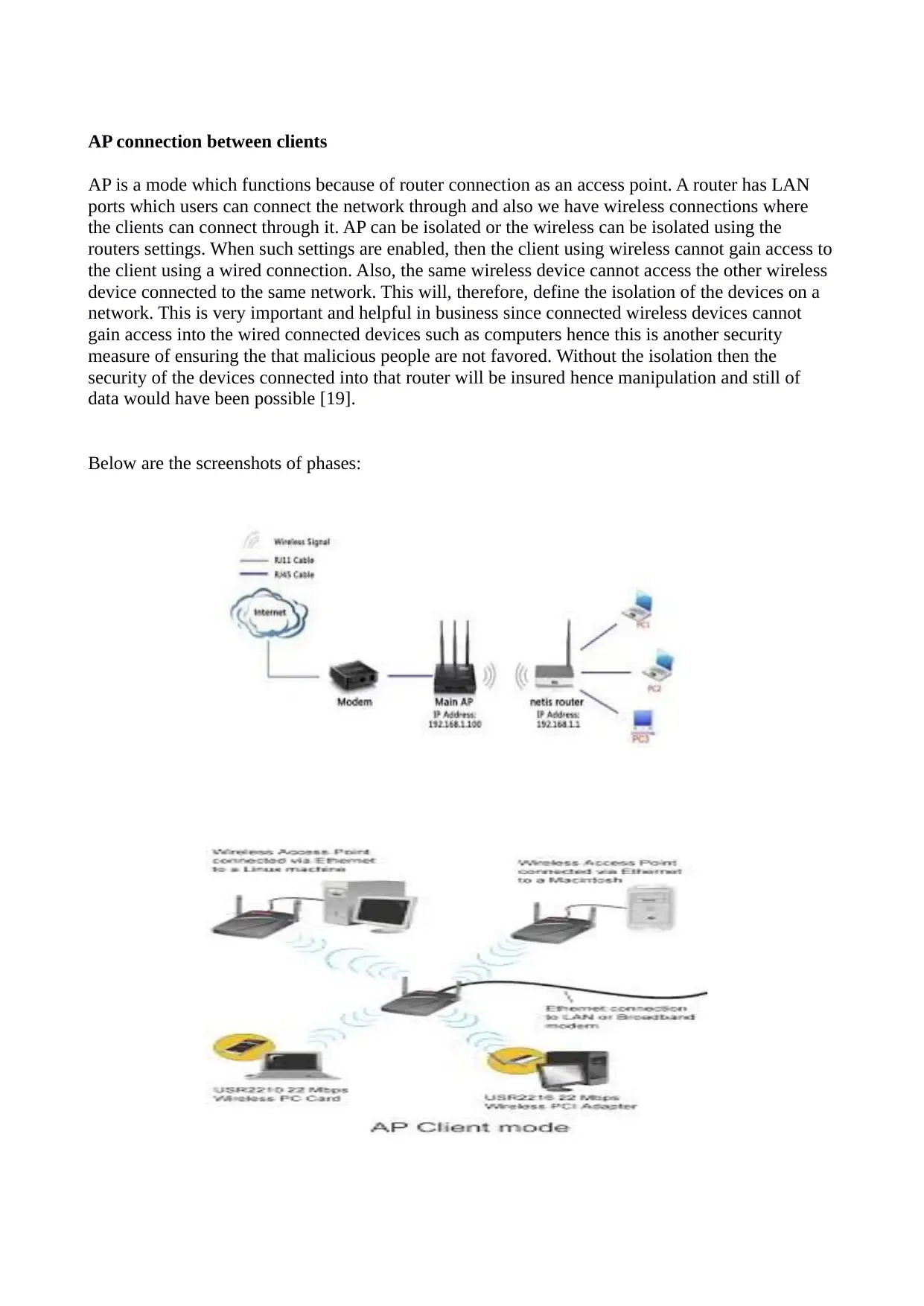
AP connection between clients
AP is a mode which functions because of router connection as an access point. A router has LAN
ports which users can connect the network through and also we have wireless connections where
the clients can connect through it. AP can be isolated or the wireless can be isolated using the
routers settings. When such settings are enabled, then the client using wireless cannot gain access to
the client using a wired connection. Also, the same wireless device cannot access the other wireless
device connected to the same network. This will, therefore, define the isolation of the devices on a
network. This is very important and helpful in business since connected wireless devices cannot
gain access into the wired connected devices such as computers hence this is another security
measure of ensuring the that malicious people are not favored. Without the isolation then the
security of the devices connected into that router will be insured hence manipulation and still of
data would have been possible [19].
Below are the screenshots of phases:
AP is a mode which functions because of router connection as an access point. A router has LAN
ports which users can connect the network through and also we have wireless connections where
the clients can connect through it. AP can be isolated or the wireless can be isolated using the
routers settings. When such settings are enabled, then the client using wireless cannot gain access to
the client using a wired connection. Also, the same wireless device cannot access the other wireless
device connected to the same network. This will, therefore, define the isolation of the devices on a
network. This is very important and helpful in business since connected wireless devices cannot
gain access into the wired connected devices such as computers hence this is another security
measure of ensuring the that malicious people are not favored. Without the isolation then the
security of the devices connected into that router will be insured hence manipulation and still of
data would have been possible [19].
Below are the screenshots of phases:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
Good design and implementation of the wireless network is required since this as emerge to be a
widely used type of network and many people have trusted its availability and accessibility.
Security of this wireless network is, therefore, the most important. Information such passwords of
the network should be kept confidential, secure and unavailable to unauthorized people. In case of
any malicious act on the network then its important to consult the IT expert immediately before the
malicious person gain access to the most important and sensitive information [20].
Good design and implementation of the wireless network is required since this as emerge to be a
widely used type of network and many people have trusted its availability and accessibility.
Security of this wireless network is, therefore, the most important. Information such passwords of
the network should be kept confidential, secure and unavailable to unauthorized people. In case of
any malicious act on the network then its important to consult the IT expert immediately before the
malicious person gain access to the most important and sensitive information [20].

Reference
1. Yu.E. Khokhlov, F.S. Voroiskiy, "Projecting of distributed logical library network LibWeb",
Telematics 97: Materials of All-Russian scientific methodical conference, pp. 26-30, 1996.
2. V.A. Kozlov, Creation of single information space of Russia by applying international
standards //Standards, and Quality, pp. 2, 1996.
3. NIST Special Publication 500 220, Computer System Laboratory (CSL), October. 1994.
4. Yakubov M. Kh, Information flows management in the network of distributed databases of
documental information on the basis of imitation modeling. Informational announcement 264,
Tashkent: Publishing house FAN, 1981.
5. B. Haines, T. Kramer, "802.11 Wireless - Infrastructure Attacks" in Seven Deadliest Wireless
Technology Attacks, New York: Elsevier, pp. 01-05, 2010.
6. Chen, J.-C., Wang, Y.-P.: Extensible authentication protocol (EAP) and IEEE 802.1x: tutorial and
empirical experience. IEEE Communication Magzine 43(12), s26–s32 (2005)
7. M. Gast, "Introduction to Wireless Networks" in 802.11 Wireless Networks: The Definitive
Guide, New York: O'Reilly, pp. 01-06, 2002.
8. S. Sobh, Tarek, "Wi-Fi Networks Security and Accessing Control" in, International Journal of
Computer Network and Information Security (IJCNIS), vol. 5, no. 7, pp. 9, 2013.
9. M. Le. Tung, Liu Ren Ping, Hedley Mark, "Rogue access point detection and localization",
Personal Indoor and Mobile Radio Communications (PIMRC) 2012 IEEE 23rd International
Symposium on. IEEE, 2012.
10. Sasu Emanuel Ciprian, Octavian Prostean, "Network simulation for MAC spoofing detection
using DTF method", Applied Computational Intelligence and Informatics (SACI) 2012 7th IEEE
International Symposium on. IEEE, 2012.
1. Yu.E. Khokhlov, F.S. Voroiskiy, "Projecting of distributed logical library network LibWeb",
Telematics 97: Materials of All-Russian scientific methodical conference, pp. 26-30, 1996.
2. V.A. Kozlov, Creation of single information space of Russia by applying international
standards //Standards, and Quality, pp. 2, 1996.
3. NIST Special Publication 500 220, Computer System Laboratory (CSL), October. 1994.
4. Yakubov M. Kh, Information flows management in the network of distributed databases of
documental information on the basis of imitation modeling. Informational announcement 264,
Tashkent: Publishing house FAN, 1981.
5. B. Haines, T. Kramer, "802.11 Wireless - Infrastructure Attacks" in Seven Deadliest Wireless
Technology Attacks, New York: Elsevier, pp. 01-05, 2010.
6. Chen, J.-C., Wang, Y.-P.: Extensible authentication protocol (EAP) and IEEE 802.1x: tutorial and
empirical experience. IEEE Communication Magzine 43(12), s26–s32 (2005)
7. M. Gast, "Introduction to Wireless Networks" in 802.11 Wireless Networks: The Definitive
Guide, New York: O'Reilly, pp. 01-06, 2002.
8. S. Sobh, Tarek, "Wi-Fi Networks Security and Accessing Control" in, International Journal of
Computer Network and Information Security (IJCNIS), vol. 5, no. 7, pp. 9, 2013.
9. M. Le. Tung, Liu Ren Ping, Hedley Mark, "Rogue access point detection and localization",
Personal Indoor and Mobile Radio Communications (PIMRC) 2012 IEEE 23rd International
Symposium on. IEEE, 2012.
10. Sasu Emanuel Ciprian, Octavian Prostean, "Network simulation for MAC spoofing detection
using DTF method", Applied Computational Intelligence and Informatics (SACI) 2012 7th IEEE
International Symposium on. IEEE, 2012.

11. Fabian Andre Perez, "Security in current commercial wireless networks: A survey" in, School of
Electrical and Computer Engineering, Purdue University West Lafayette, 2004.
12. Chungen Xu, Yang Yanjiong, "Password guessing attack on a key exchange protocol based on
ECDLP", IEEE, vol. 1, 2010.
13. Maryam, H. Saeed, Shahhoseini Shahriar, Mackvandi Ali, "An improved two-party Password
Authenticated Key Exchange protocol without server's public key", Communication Software and
Networks (ICCSN) 2011 IEEE 3rd International Conference on. IEEE, 2011.
14. Zhu Ming-xun, Xin-xing Luo, "Trustworthy Software Reliability Research Based on UNIX
Login Packet Security Analysis", E-Business and E-Government (ICEE) 2010 International
Conference on. IEEE, 2010.
15. Jingtang Luo, Yang Xiaolong, "The NewShrew attack: A new type of low-rate TCP- Targeted
DoS attack", Communications (ICC) 2014 IEEE International Conference on. IEEE, 2014.
16. Martin Egan, "A practical cryptographic denial of service attack against 802.11 I TKIP and
CCMP" in, Cryptology and Network Security. Springer Berlin Heidelberg, pp. 62-75, 2010.
17. Shuichi Ohno et al., "Optimization of transmitting signals to interfere eavesdropping in a
wireless LAN", Acoustics Speech and Signal Processing (ICASSP) 2014 IEEE International
Conference on. IEEE, 2014.
18. Chao Yang, Song Yimin, Gu. Guofei, "Active User-Side Evil Twin Access Point Detection
Using Statistical Techniques" in, Information Forensics and Security, IEEE Transactions on, vol.
7.5, pp. 1638-1651, 2012.
19. Kemal Bicakci et al., "Mobile Authentication Secure Against Man- In- The-Middle Attacks",
Mobile Cloud Computing Services and Engineering (MobileCloud) 2014 2nd IEEE International
Conference on. IEEE, 2014.
20. Andre Teixeira et al., "Security of smart distribution grids: Data integrity attacks on integrated
volt/VAR control and countermeasures", American Control Conference (ACC) 2014. IEEE, 2014.
Electrical and Computer Engineering, Purdue University West Lafayette, 2004.
12. Chungen Xu, Yang Yanjiong, "Password guessing attack on a key exchange protocol based on
ECDLP", IEEE, vol. 1, 2010.
13. Maryam, H. Saeed, Shahhoseini Shahriar, Mackvandi Ali, "An improved two-party Password
Authenticated Key Exchange protocol without server's public key", Communication Software and
Networks (ICCSN) 2011 IEEE 3rd International Conference on. IEEE, 2011.
14. Zhu Ming-xun, Xin-xing Luo, "Trustworthy Software Reliability Research Based on UNIX
Login Packet Security Analysis", E-Business and E-Government (ICEE) 2010 International
Conference on. IEEE, 2010.
15. Jingtang Luo, Yang Xiaolong, "The NewShrew attack: A new type of low-rate TCP- Targeted
DoS attack", Communications (ICC) 2014 IEEE International Conference on. IEEE, 2014.
16. Martin Egan, "A practical cryptographic denial of service attack against 802.11 I TKIP and
CCMP" in, Cryptology and Network Security. Springer Berlin Heidelberg, pp. 62-75, 2010.
17. Shuichi Ohno et al., "Optimization of transmitting signals to interfere eavesdropping in a
wireless LAN", Acoustics Speech and Signal Processing (ICASSP) 2014 IEEE International
Conference on. IEEE, 2014.
18. Chao Yang, Song Yimin, Gu. Guofei, "Active User-Side Evil Twin Access Point Detection
Using Statistical Techniques" in, Information Forensics and Security, IEEE Transactions on, vol.
7.5, pp. 1638-1651, 2012.
19. Kemal Bicakci et al., "Mobile Authentication Secure Against Man- In- The-Middle Attacks",
Mobile Cloud Computing Services and Engineering (MobileCloud) 2014 2nd IEEE International
Conference on. IEEE, 2014.
20. Andre Teixeira et al., "Security of smart distribution grids: Data integrity attacks on integrated
volt/VAR control and countermeasures", American Control Conference (ACC) 2014. IEEE, 2014.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



