Topic: An Investigation into Threat Modelling Tools and Technique Used in Securing E-Commerce Applications Online
VerifiedAdded on 2023/04/23
|84
|20598
|225
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

TOPIC: An Investigation into Threat Modelling Tools and
Technique Used in Securing E-Commerce
Applications Online
Technique Used in Securing E-Commerce
Applications Online
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Chapter One: Introduction..............................................................................................................5
1.1 Background Study................................................................................................................5
1.2 Problem Statement................................................................................................................6
1.3 Project Aims and Objectives.................................................................................................6
1.4 Scope of Study................................................................................................................7
1.5 Background of the study.................................................................................................7
Chapter 2: Overview of Security Issues in E-commerce.................................................................9
2.1 Definition of terms..............................................................................................................10
Chapter 3: Literature review.........................................................................................................11
3.1 Literature Review...............................................................................................................11
3.1.1 The Underlying Principles in Online Shopping using Credit Card and PayPal............11
3.1.2 E-commerce Security Tools.........................................................................................14
3.1.3 Firewalls......................................................................................................................15
3.1.4 Types of Firewalls........................................................................................................16
3.1.5 Public Key infrastructure.............................................................................................17
3.1.6 Encryption software Tools...........................................................................................18
3.1.7 Digital Certificates and Signatures Security Tool........................................................20
3.1.8 Biometrics Security Tool.............................................................................................22
3.1.9 Passwords Security Tool..............................................................................................23
3.1.10 Major Threat Modelling Approaches.........................................................................24
3.1.11 Benefit of Effective E-commerce Security.................................................................28
Chapter 4: Methodology...............................................................................................................30
4.1 System Methodology..........................................................................................................30
4.1.1 Prototype Method.........................................................................................................31
4.1.2 Dynamic Systems Development Model (DSDM)........................................................31
4.1.3 Spring Model...............................................................................................................32
4.1.4 Agile Scrum methodology...........................................................................................33
4.1.5 Ethical consideration conducted the following process:...............................................34
4.2 Data Collection...................................................................................................................35
4.3 Evidence of the interview Conducted Online (Template)...................................................36
4.4 Interview Summary.............................................................................................................38
4.5 Data Analysis from the Interview.......................................................................................39
A. Security Issues Associated with E-Bay App System........................................................39
B. Security Issues Associated with Amazon App System.....................................................40
Chapter One: Introduction..............................................................................................................5
1.1 Background Study................................................................................................................5
1.2 Problem Statement................................................................................................................6
1.3 Project Aims and Objectives.................................................................................................6
1.4 Scope of Study................................................................................................................7
1.5 Background of the study.................................................................................................7
Chapter 2: Overview of Security Issues in E-commerce.................................................................9
2.1 Definition of terms..............................................................................................................10
Chapter 3: Literature review.........................................................................................................11
3.1 Literature Review...............................................................................................................11
3.1.1 The Underlying Principles in Online Shopping using Credit Card and PayPal............11
3.1.2 E-commerce Security Tools.........................................................................................14
3.1.3 Firewalls......................................................................................................................15
3.1.4 Types of Firewalls........................................................................................................16
3.1.5 Public Key infrastructure.............................................................................................17
3.1.6 Encryption software Tools...........................................................................................18
3.1.7 Digital Certificates and Signatures Security Tool........................................................20
3.1.8 Biometrics Security Tool.............................................................................................22
3.1.9 Passwords Security Tool..............................................................................................23
3.1.10 Major Threat Modelling Approaches.........................................................................24
3.1.11 Benefit of Effective E-commerce Security.................................................................28
Chapter 4: Methodology...............................................................................................................30
4.1 System Methodology..........................................................................................................30
4.1.1 Prototype Method.........................................................................................................31
4.1.2 Dynamic Systems Development Model (DSDM)........................................................31
4.1.3 Spring Model...............................................................................................................32
4.1.4 Agile Scrum methodology...........................................................................................33
4.1.5 Ethical consideration conducted the following process:...............................................34
4.2 Data Collection...................................................................................................................35
4.3 Evidence of the interview Conducted Online (Template)...................................................36
4.4 Interview Summary.............................................................................................................38
4.5 Data Analysis from the Interview.......................................................................................39
A. Security Issues Associated with E-Bay App System........................................................39
B. Security Issues Associated with Amazon App System.....................................................40

C. Security Issues Associated with Konga App System........................................................40
Chapter 5: Implementation and Results........................................................................................41
4.1 Evidence of Developing a New Threat Modelling Technique............................................41
4.1.1 Project Result Website.................................................................................................41
4.2 Project Result Discussion...................................................................................................43
Goals.....................................................................................................................................43
Newly Developed E-commerce Application Decomposition................................................45
Application Entry Point........................................................................................................46
Application Assets................................................................................................................47
Application Security Trust Level..........................................................................................49
Application Security Data Flow Diagram.............................................................................50
Determining high ranking threats..........................................................................................51
Determining possible countermeasures and mitigation.........................................................53
Amazon E-commerce Application Decomposition...............................................................54
Amazon Entry Point..............................................................................................................55
Amazon Security Asset.........................................................................................................56
Amazon Security Trust level.................................................................................................58
Amazon Security Data Flow Diagram..................................................................................59
4.3 Evaluation of the Result......................................................................................................61
Chapter 6: Summary and Conclusion...........................................................................................62
6.1 Summary.........................................................................................................................62
6.2 Conclusion......................................................................................................................71
6.3 Recommendation............................................................................................................72
References....................................................................................................................................74
Appendix......................................................................................................................................82
1. Time Scale Plan................................................................................................................82
2. Support Used....................................................................................................................82
3. Skills Audit.......................................................................................................................83
Figure 1: E-commerce Shopping Cycle........................................................................................13
Figure 2: Encryption and Decryption Diagrammatic representation.............................................19
Figure 3: Digital signature Process...............................................................................................21
Figure 4: Stride Threat Modelling Approach................................................................................26
Figure 5: Diagram showing an Attack Tree on Credit Card System.............................................28
Figure 6: Diagrammatic representation of Spring Model methodology........................................32
Figure 7: Diagrammatic Representation of Scrum Iteration..........................................................34
Chapter 5: Implementation and Results........................................................................................41
4.1 Evidence of Developing a New Threat Modelling Technique............................................41
4.1.1 Project Result Website.................................................................................................41
4.2 Project Result Discussion...................................................................................................43
Goals.....................................................................................................................................43
Newly Developed E-commerce Application Decomposition................................................45
Application Entry Point........................................................................................................46
Application Assets................................................................................................................47
Application Security Trust Level..........................................................................................49
Application Security Data Flow Diagram.............................................................................50
Determining high ranking threats..........................................................................................51
Determining possible countermeasures and mitigation.........................................................53
Amazon E-commerce Application Decomposition...............................................................54
Amazon Entry Point..............................................................................................................55
Amazon Security Asset.........................................................................................................56
Amazon Security Trust level.................................................................................................58
Amazon Security Data Flow Diagram..................................................................................59
4.3 Evaluation of the Result......................................................................................................61
Chapter 6: Summary and Conclusion...........................................................................................62
6.1 Summary.........................................................................................................................62
6.2 Conclusion......................................................................................................................71
6.3 Recommendation............................................................................................................72
References....................................................................................................................................74
Appendix......................................................................................................................................82
1. Time Scale Plan................................................................................................................82
2. Support Used....................................................................................................................82
3. Skills Audit.......................................................................................................................83
Figure 1: E-commerce Shopping Cycle........................................................................................13
Figure 2: Encryption and Decryption Diagrammatic representation.............................................19
Figure 3: Digital signature Process...............................................................................................21
Figure 4: Stride Threat Modelling Approach................................................................................26
Figure 5: Diagram showing an Attack Tree on Credit Card System.............................................28
Figure 6: Diagrammatic representation of Spring Model methodology........................................32
Figure 7: Diagrammatic Representation of Scrum Iteration..........................................................34

Figure 8: Screenshot One showing the Website Page of the threat Modell for Securing E-
commerce Application..................................................................................................................41
Figure 9: Screenshot two showing the Website Page of the threat Modell for Securing E-
commerce Application..................................................................................................................42
Figure 10: Screenshot One showing the Website Page of the threat modelling for Securing E-
commerce Application..................................................................................................................42
Figure 11: New Application Security Data Flow Diagram...........................................................51
Figure 12: Amazon online Application Security Data Flow Diagram...........................................59
Table 1: Newly Developed E-commerce Application Decomposition..........................................46
Table 2: Application Entry Point..................................................................................................47
Table 3: Application Assets..........................................................................................................49
Table 4: Application Security Trust Level....................................................................................50
Table 5: High Ranking Threats.....................................................................................................53
Table 6: Countermeasures and Mitigation....................................................................................54
Table 7: Amazon E-commerce Application Decomposition.........................................................55
Table 8: Amazon Entry Point.......................................................................................................56
Table 9: Amazon Security Asset...................................................................................................58
Table 10: Amazon Security Trust level........................................................................................59
Table 11: High Ranking Threats...................................................................................................60
Table 12: Threat and Countermeasures.........................................................................................61
commerce Application..................................................................................................................41
Figure 9: Screenshot two showing the Website Page of the threat Modell for Securing E-
commerce Application..................................................................................................................42
Figure 10: Screenshot One showing the Website Page of the threat modelling for Securing E-
commerce Application..................................................................................................................42
Figure 11: New Application Security Data Flow Diagram...........................................................51
Figure 12: Amazon online Application Security Data Flow Diagram...........................................59
Table 1: Newly Developed E-commerce Application Decomposition..........................................46
Table 2: Application Entry Point..................................................................................................47
Table 3: Application Assets..........................................................................................................49
Table 4: Application Security Trust Level....................................................................................50
Table 5: High Ranking Threats.....................................................................................................53
Table 6: Countermeasures and Mitigation....................................................................................54
Table 7: Amazon E-commerce Application Decomposition.........................................................55
Table 8: Amazon Entry Point.......................................................................................................56
Table 9: Amazon Security Asset...................................................................................................58
Table 10: Amazon Security Trust level........................................................................................59
Table 11: High Ranking Threats...................................................................................................60
Table 12: Threat and Countermeasures.........................................................................................61
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Chapter One: Introduction
1.1 Background Study
To ensure that e-commerce information assets is not compromised, software security
vulnerabilities is the most important line of defense. The recent increase in the
complexity and volume of cyber security attacks gives convincing reasons for enhancing
the security of e-commerce software applications that monitors and regulate online
shopping information. This most recent global attack on e-commerce business was the
ransom ware attack. Most firms were affected. The nature at which the ransom ware
cyber attacked spread from nation to nation, and from one firm to another was very
worrisome. E-commerce is a very important and lucrative sector in any economy which
has strived positively since its introduction to the internet. This continues threat and
attack poses a security issues surrounding web applications today, and is a serious
concern to the e-commerce business.
Software security tools and model are proactive approach designed to combat computer
security threat that emerged about fifteen years ago. It addresses a vital need for software
applications to be designed and developed with security in mind. Threat modeling
techniques and analytical tools are among the practices utilized in the computer industry
to reduce the volume and severity of exploitable vulnerabilities to e-commerce software
applications. But most of these threat models are usually implement after the designed
and development of an e-commerce application which is not the best practice. There is a
trending knowledge that in other to produce dependable and secure applications, app
developers need to incorporate security into software development lifecycle 'SDLC' (Lee
1.1 Background Study
To ensure that e-commerce information assets is not compromised, software security
vulnerabilities is the most important line of defense. The recent increase in the
complexity and volume of cyber security attacks gives convincing reasons for enhancing
the security of e-commerce software applications that monitors and regulate online
shopping information. This most recent global attack on e-commerce business was the
ransom ware attack. Most firms were affected. The nature at which the ransom ware
cyber attacked spread from nation to nation, and from one firm to another was very
worrisome. E-commerce is a very important and lucrative sector in any economy which
has strived positively since its introduction to the internet. This continues threat and
attack poses a security issues surrounding web applications today, and is a serious
concern to the e-commerce business.
Software security tools and model are proactive approach designed to combat computer
security threat that emerged about fifteen years ago. It addresses a vital need for software
applications to be designed and developed with security in mind. Threat modeling
techniques and analytical tools are among the practices utilized in the computer industry
to reduce the volume and severity of exploitable vulnerabilities to e-commerce software
applications. But most of these threat models are usually implement after the designed
and development of an e-commerce application which is not the best practice. There is a
trending knowledge that in other to produce dependable and secure applications, app
developers need to incorporate security into software development lifecycle 'SDLC' (Lee

and Park, 2016). Embedding security into the design of different ‘SDLC’ allows security
analyst and developers to think proactively about the countermeasures to discover
available threat and avert future attack.
Threat modeling is vital in developing security system for all the SDLC stages as well as
in each specific stage. The aim of this project is on the use of threat modeling tools and
approach to identify and analyze security management in e-commerce applications.
1.2 Problem Statement
Most of the threat modeling tools used in developing E-business security systems today is
usually implement after the designed and development of an e-commerce application.
This is not the best practice because this approach increases the volume and severity of
exploitable vulnerabilities in the computer and E commerce industry.
1.3 Project Aims and Objectives
Project aims: The primary aim of the study is to investigate the tools that are required
for the threat modelling for utilizing while securing the e-commerce applications online.
These outlined aim would successfully help in investigating threat modelling tools and
technique used in securing e-commerce applications online. The Statue Quo of this study
is to investigate the current security challenges in e-commerce applications, by studying
past research work and recommending better approach.
Project Objectives: The objective of this project is focus on the specified requirements
to which E-commerce application should meet security standard. They are outlined
below:
analyst and developers to think proactively about the countermeasures to discover
available threat and avert future attack.
Threat modeling is vital in developing security system for all the SDLC stages as well as
in each specific stage. The aim of this project is on the use of threat modeling tools and
approach to identify and analyze security management in e-commerce applications.
1.2 Problem Statement
Most of the threat modeling tools used in developing E-business security systems today is
usually implement after the designed and development of an e-commerce application.
This is not the best practice because this approach increases the volume and severity of
exploitable vulnerabilities in the computer and E commerce industry.
1.3 Project Aims and Objectives
Project aims: The primary aim of the study is to investigate the tools that are required
for the threat modelling for utilizing while securing the e-commerce applications online.
These outlined aim would successfully help in investigating threat modelling tools and
technique used in securing e-commerce applications online. The Statue Quo of this study
is to investigate the current security challenges in e-commerce applications, by studying
past research work and recommending better approach.
Project Objectives: The objective of this project is focus on the specified requirements
to which E-commerce application should meet security standard. They are outlined
below:

Appraisal of the underlying principles in online shopping using credit card and
PayPal
Overview of E-commerce security.
Review the different security issues in E-commerce organization.
Review the available security tools and security modelling approaches in E-
commerce
Developing a standard security model for software development methodologies in
E-commerce organization.
Comparing the degree of successful developed security modelling approach for E-
commerce applications.
1.4 Scope of Study
This study focuses on the past and current challenges, threats securing e-commerce
applications online. Undergoing with this study the researcher aims at using past research
work, current research materials, and interactive social media platforms in getting the
most recent and up to date security models being used to curb or reduce security threats
online.
1.5 Background of the study
In the current global economy, application security plays a pivotal role in network
security. Consistently software hackers are using advance technologies and techniques to
access important data and carry out other significant activities to E-commerce network
application (Ott, 2008). In the electronic technologies sectors, Privacy and security are
major factor. The E-commerce sector also shares these views in line with other
technological fields. While some firms are faced with difficulties in making their website
PayPal
Overview of E-commerce security.
Review the different security issues in E-commerce organization.
Review the available security tools and security modelling approaches in E-
commerce
Developing a standard security model for software development methodologies in
E-commerce organization.
Comparing the degree of successful developed security modelling approach for E-
commerce applications.
1.4 Scope of Study
This study focuses on the past and current challenges, threats securing e-commerce
applications online. Undergoing with this study the researcher aims at using past research
work, current research materials, and interactive social media platforms in getting the
most recent and up to date security models being used to curb or reduce security threats
online.
1.5 Background of the study
In the current global economy, application security plays a pivotal role in network
security. Consistently software hackers are using advance technologies and techniques to
access important data and carry out other significant activities to E-commerce network
application (Ott, 2008). In the electronic technologies sectors, Privacy and security are
major factor. The E-commerce sector also shares these views in line with other
technological fields. While some firms are faced with difficulties in making their website
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

security sophisticated in order to provide customers with effective secure payment online,
other firms like Palpay, WePay and ProPay have provided their customers with the
security of assessing any website with an assurance that their information is safe.
Notwithstanding, big firms are investing heavily, in addressing E-commerce security
challenges using different tools and techniques. In analysing the security level of an
application, system and software, an approach is the threat modelling and security tools
(Li et al., 2012). It is a structured approach that enables one identify, measure and address
the security hazard associated with applications and software (Amini et 2017). This
project notwithstanding, will limit its scope to e-commerce applications such as E-bay,
Amazon and Konga.
There are basically three different types of threat modelling approaches available today,
they include fault tree Analysis, Attack trees, Stride and Dread (Wagner et al 2009).
These approaches and techniques to application security have proven to be ineffective,
this is evidence in their vulnerabilities, permitting applications to be attacked or damaged.
A challenging task is determining with approach will give the best result when applied to
specific software application or e-commerce applications. Therefore, determine how to
effectively solve this security challenge using the most effective tool is crux of this
project.
An overview of the problem statement is why security in e-commerce application is
needed, and the best approach to apply. This research survey evaluated the existing threat
modelling techniques and tools from the literature review. The report discussed various
methodologies to this research and give reason to why the agile methodology was
adopted in developing a new threat modelling technique framework. This new threat
other firms like Palpay, WePay and ProPay have provided their customers with the
security of assessing any website with an assurance that their information is safe.
Notwithstanding, big firms are investing heavily, in addressing E-commerce security
challenges using different tools and techniques. In analysing the security level of an
application, system and software, an approach is the threat modelling and security tools
(Li et al., 2012). It is a structured approach that enables one identify, measure and address
the security hazard associated with applications and software (Amini et 2017). This
project notwithstanding, will limit its scope to e-commerce applications such as E-bay,
Amazon and Konga.
There are basically three different types of threat modelling approaches available today,
they include fault tree Analysis, Attack trees, Stride and Dread (Wagner et al 2009).
These approaches and techniques to application security have proven to be ineffective,
this is evidence in their vulnerabilities, permitting applications to be attacked or damaged.
A challenging task is determining with approach will give the best result when applied to
specific software application or e-commerce applications. Therefore, determine how to
effectively solve this security challenge using the most effective tool is crux of this
project.
An overview of the problem statement is why security in e-commerce application is
needed, and the best approach to apply. This research survey evaluated the existing threat
modelling techniques and tools from the literature review. The report discussed various
methodologies to this research and give reason to why the agile methodology was
adopted in developing a new threat modelling technique framework. This new threat

modelling technique framework was proposed with a functional website discussing how
it should be use. The report also document the appropriate ethical conservation observed
following an interview conducted to observe how E-bay, Amazon and Konga e-
commerce mobile application users are concern with the security on this platform. Its
findings are discussed in the later chapter, where recommendations will be made.
Chapter 2: Overview of Security Issues in E-commerce
There has been a significant increase in the level of business transactions perfumed
electronically since the emergence of the Internet and the World Wide Web. For every
transaction that occurs on the web and the internet, security is of utmost important. The e-
commerce security threat is a major aspect of the trending security obstacles facing E-
business activities today. It covers all areas of the e-business including social networking,
marketing and other realm of Information security (Kelly and Rowland, 2000). E-
commerce security is one of the major security issues affecting most end user today;
through interactions with online businesses, which could be payment for service rendered
and other financial transactions.
Traditionally, authentication mechanism in e-commerce is based on providing personal
security identification and access control methods (Hanumesh and Sunder, 2000).
Though there has been improvement using modern day advance encryption and
compliment authentication mechanism, which employ authentication algorithm to
optimise security power in e-commerce. The advent of e-commerce has exposed the
banking industry to great opportunity, even though it created a new set of risks and
increase vulnerability and security threats. Information security should be seen as an
essential and integral part of management and technical requirement for any efficient and
it should be use. The report also document the appropriate ethical conservation observed
following an interview conducted to observe how E-bay, Amazon and Konga e-
commerce mobile application users are concern with the security on this platform. Its
findings are discussed in the later chapter, where recommendations will be made.
Chapter 2: Overview of Security Issues in E-commerce
There has been a significant increase in the level of business transactions perfumed
electronically since the emergence of the Internet and the World Wide Web. For every
transaction that occurs on the web and the internet, security is of utmost important. The e-
commerce security threat is a major aspect of the trending security obstacles facing E-
business activities today. It covers all areas of the e-business including social networking,
marketing and other realm of Information security (Kelly and Rowland, 2000). E-
commerce security is one of the major security issues affecting most end user today;
through interactions with online businesses, which could be payment for service rendered
and other financial transactions.
Traditionally, authentication mechanism in e-commerce is based on providing personal
security identification and access control methods (Hanumesh and Sunder, 2000).
Though there has been improvement using modern day advance encryption and
compliment authentication mechanism, which employ authentication algorithm to
optimise security power in e-commerce. The advent of e-commerce has exposed the
banking industry to great opportunity, even though it created a new set of risks and
increase vulnerability and security threats. Information security should be seen as an
essential and integral part of management and technical requirement for any efficient and

effective transactions and financial activities over the internet. Online e-commerce
applications that uses payments methods such as electronic transactions, debit cards,
credit cards, PayPal or other tokens stands a greater risk of been hacked, either network
servers, data loss or alteration of e-commerce applications (Lin, 2017).
2.1 Definition of terms
Online customer’s awareness about possible identity theft, financial fraud and other
irregularities when performing financial transaction on the web, has increase due to
warming from media houses on security and privacy breaches. This has placed
limitations on e-commerce businesses, in terms of growth and profit maximisation. A lot
of end users and customers are having declined to perform online exchanges due to lack
of trust and fear of losing their personal information to criminals (Bruton, 1999). End
users are no longer having confidence in e-business due to: -
Fraud: This is an act that can results in direct financial loss by, from a customer’s
account to a criminal’s accounts without any financial records update.
Electronic thief: It refers to an intruder that can disclose confidential or protected,
information to a third party, with sole aim of having financial gain. E-commerce system
is liable to irregularities which could result in interception of customers online shopping
activities, thereby resulting to distress.
Security confidentiality: giving customers the confidence that the data sent to e-
commerce firms are has integrity and confidentiality and not for public view.
E-commerce integrity: assuring customers that information provided and data is real,
accurate and safeguarded from unauthorized user modification, which is not usually the
applications that uses payments methods such as electronic transactions, debit cards,
credit cards, PayPal or other tokens stands a greater risk of been hacked, either network
servers, data loss or alteration of e-commerce applications (Lin, 2017).
2.1 Definition of terms
Online customer’s awareness about possible identity theft, financial fraud and other
irregularities when performing financial transaction on the web, has increase due to
warming from media houses on security and privacy breaches. This has placed
limitations on e-commerce businesses, in terms of growth and profit maximisation. A lot
of end users and customers are having declined to perform online exchanges due to lack
of trust and fear of losing their personal information to criminals (Bruton, 1999). End
users are no longer having confidence in e-business due to: -
Fraud: This is an act that can results in direct financial loss by, from a customer’s
account to a criminal’s accounts without any financial records update.
Electronic thief: It refers to an intruder that can disclose confidential or protected,
information to a third party, with sole aim of having financial gain. E-commerce system
is liable to irregularities which could result in interception of customers online shopping
activities, thereby resulting to distress.
Security confidentiality: giving customers the confidence that the data sent to e-
commerce firms are has integrity and confidentiality and not for public view.
E-commerce integrity: assuring customers that information provided and data is real,
accurate and safeguarded from unauthorized user modification, which is not usually the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

case. Insecure Firewall filters in e-commerce network and internet create loop holes in
files and information thereby allowing it into wrong hands.
Phishing: attack on e-commerce network and system by cyber criminals resulting in
vulnerable attacks on software and machines enabling cyber theft. Malicious Code sent to
attack e-commerce systems in form of worms by Trojans horse and bots which, can
replicated and spread from one file to another or from one system to another.
When it comes to buying and selling of goods and services online, e-commerce is still in
the forefront, shopping and making transactions with just a click using desktop and
mobile apps are effectively utilised. Because numerous web based mobile applications
are being created to satisfy client shopping desires, there is a need to address the e-
business security issues, by effectively using an appropriate tools and threat technique.
These tools and other existing ones will be evaluated in this report. Also, the possibility
of this threat modelling tools and approaches being imbedded into software development
processes in tackling security before e-commerce applications are developed.
Chapter 3: Literature review
3.1 Literature Review
3.1.1 The Underlying Principles in Online Shopping using Credit Card and PayPal
The current innovation of online card payments and PayPal payment occur with online
generated virtual personal account numbers. The account numbers are usually invisible to
individuals using the internet to make online purchases. All online shopping cards have
an internally writeable magnetic data stripe which enables, then to be used at a point-of-
sale tale, automated readable machines and E-business website. This is because the
files and information thereby allowing it into wrong hands.
Phishing: attack on e-commerce network and system by cyber criminals resulting in
vulnerable attacks on software and machines enabling cyber theft. Malicious Code sent to
attack e-commerce systems in form of worms by Trojans horse and bots which, can
replicated and spread from one file to another or from one system to another.
When it comes to buying and selling of goods and services online, e-commerce is still in
the forefront, shopping and making transactions with just a click using desktop and
mobile apps are effectively utilised. Because numerous web based mobile applications
are being created to satisfy client shopping desires, there is a need to address the e-
business security issues, by effectively using an appropriate tools and threat technique.
These tools and other existing ones will be evaluated in this report. Also, the possibility
of this threat modelling tools and approaches being imbedded into software development
processes in tackling security before e-commerce applications are developed.
Chapter 3: Literature review
3.1 Literature Review
3.1.1 The Underlying Principles in Online Shopping using Credit Card and PayPal
The current innovation of online card payments and PayPal payment occur with online
generated virtual personal account numbers. The account numbers are usually invisible to
individuals using the internet to make online purchases. All online shopping cards have
an internally writeable magnetic data stripe which enables, then to be used at a point-of-
sale tale, automated readable machines and E-business website. This is because the

internally writeable magnetic data strips are readable with special payment readable
software's (Hayashi, 2012).
Automated online card payment system appears to be on most shopping website, to
permits faster, easier and verifiable transactions using the magnetic stripes on the back of
the cards which is link to a card number (Long and Vy, 2016). A card reader is used to
verify the card details in real-time to track fraudulent cards speedily and accurately (Long
and Vy, 2016). However online fraudsters are constantly looking for modern technique to
defeat online card reading machines (Virtue, 2013).
An online card could be MasterCard, Visa, Vector One and Other typical payment cards,
usually unique to identify an account holder (Virtue, 2013). A standard card contains a
customised personal account number usually a system number, bank number, user
account number or a cheque digit. The personal account number is associated an
expiration date and year issued my bank, in some cases the account holder's name or
business appears on the card as well as the bank unique sort code. On the other side of the
card is a 3-digit number (CVC), known as the card confirmation code. The CVC is not
embedded on the card, therefore different online system cannot print or store the number,
thus can only be approved by the card holder.
There two main sorts of transactions while a using Credit card, the online associate with
web transaction and offline associated with POS transactions (Dara and Gundemoni,
2017). For online transactions of any sort to be complete a card holder obtains a virtual
account online that can be used only once. The virtual online number is generated for a
user device intending to access an E-commerce website for transaction. PayPal is a
company in which its main service is to generate an online virtual account instead of
software's (Hayashi, 2012).
Automated online card payment system appears to be on most shopping website, to
permits faster, easier and verifiable transactions using the magnetic stripes on the back of
the cards which is link to a card number (Long and Vy, 2016). A card reader is used to
verify the card details in real-time to track fraudulent cards speedily and accurately (Long
and Vy, 2016). However online fraudsters are constantly looking for modern technique to
defeat online card reading machines (Virtue, 2013).
An online card could be MasterCard, Visa, Vector One and Other typical payment cards,
usually unique to identify an account holder (Virtue, 2013). A standard card contains a
customised personal account number usually a system number, bank number, user
account number or a cheque digit. The personal account number is associated an
expiration date and year issued my bank, in some cases the account holder's name or
business appears on the card as well as the bank unique sort code. On the other side of the
card is a 3-digit number (CVC), known as the card confirmation code. The CVC is not
embedded on the card, therefore different online system cannot print or store the number,
thus can only be approved by the card holder.
There two main sorts of transactions while a using Credit card, the online associate with
web transaction and offline associated with POS transactions (Dara and Gundemoni,
2017). For online transactions of any sort to be complete a card holder obtains a virtual
account online that can be used only once. The virtual online number is generated for a
user device intending to access an E-commerce website for transaction. PayPal is a
company in which its main service is to generate an online virtual account instead of
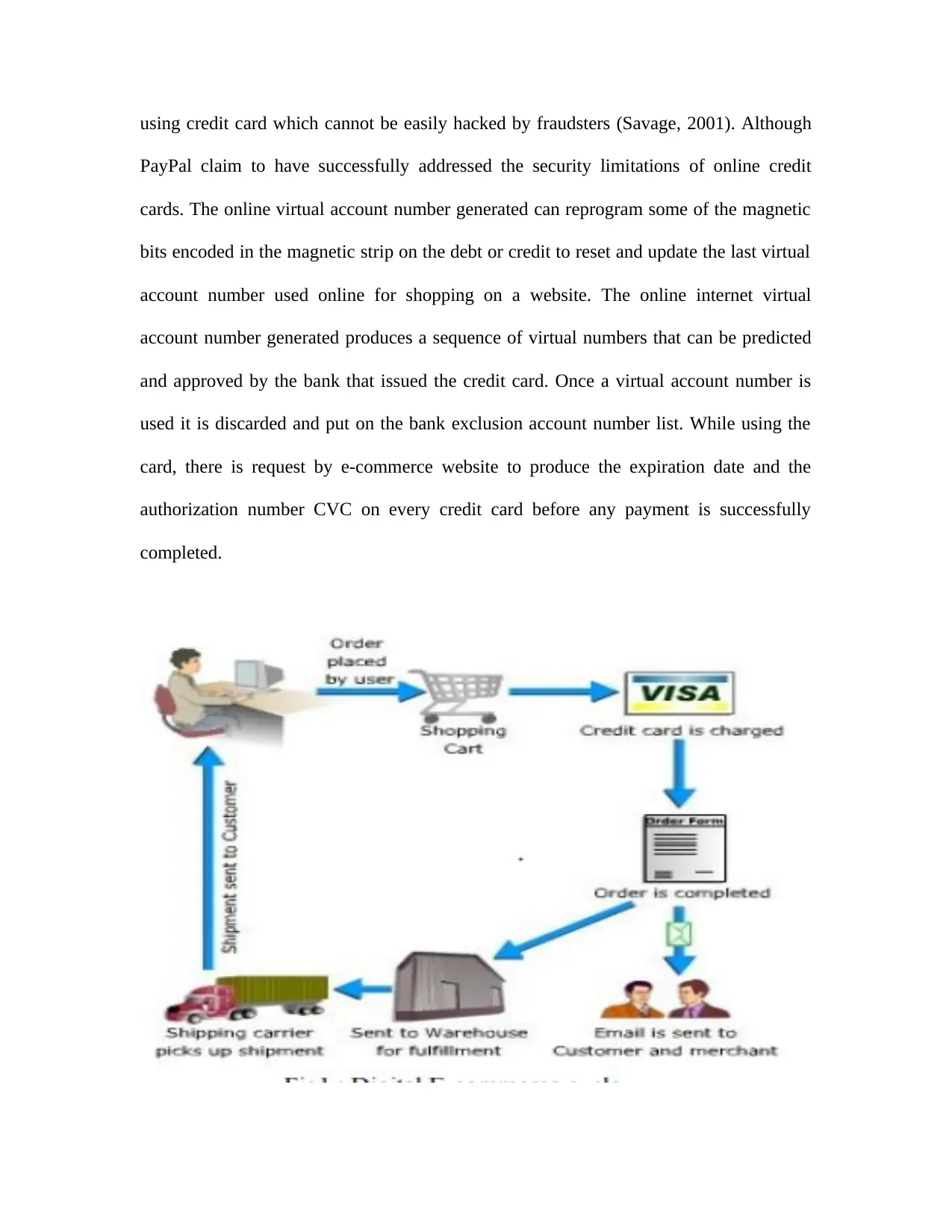
using credit card which cannot be easily hacked by fraudsters (Savage, 2001). Although
PayPal claim to have successfully addressed the security limitations of online credit
cards. The online virtual account number generated can reprogram some of the magnetic
bits encoded in the magnetic strip on the debt or credit to reset and update the last virtual
account number used online for shopping on a website. The online internet virtual
account number generated produces a sequence of virtual numbers that can be predicted
and approved by the bank that issued the credit card. Once a virtual account number is
used it is discarded and put on the bank exclusion account number list. While using the
card, there is request by e-commerce website to produce the expiration date and the
authorization number CVC on every credit card before any payment is successfully
completed.
PayPal claim to have successfully addressed the security limitations of online credit
cards. The online virtual account number generated can reprogram some of the magnetic
bits encoded in the magnetic strip on the debt or credit to reset and update the last virtual
account number used online for shopping on a website. The online internet virtual
account number generated produces a sequence of virtual numbers that can be predicted
and approved by the bank that issued the credit card. Once a virtual account number is
used it is discarded and put on the bank exclusion account number list. While using the
card, there is request by e-commerce website to produce the expiration date and the
authorization number CVC on every credit card before any payment is successfully
completed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 1: E-commerce Shopping Cycle
3.1.2 E-commerce Security Tools
Threat modelling tools allows users to systematically identify and rate the dangers that
are most likely to influence or affect a system’s functionality. These tools disguises’ and
rate threats, based on a solid understanding of the architecture design and implementation
of the software application tested (Weston, 2016). Security threats can be addressed with
proper countermeasures in a logical order, beginning with the threats that possess the
greatest risk. Threat modelling has a structured approach that is far more cost efficient
and viable than applying security features in a haphazard manner without knowing
precisely what each threat feature is supposed to address: (Jamil et al, 2015).
This review focuses on the current e-commerce tools and modelling approach used in
tackling security issues. The Microsoft threat analysis & modelling (TAM) tool
developed by their application consulting and engineering (ACE) team is an example for
the pragmatic technique employment for software acentric modelling approach. In
contrast, software-centric approaches are more suited for systems with an unknown
deployment pattern and designed to ensure the security of the software application's
underlying code in the context of rich server and client development. The security
development lifecycle (SDL) threat modelling tool, also by Microsoft, is an example of
the usage of a software-centric focus modelling approach. The attacker-centric focus
takes the adversary’s view to identify risks to the system. This requires the developer to
think like an attacker, to comprehend their inspiration and capabilities, which is likely to
pose a challenge to inexperienced users. Attack trees can also be called a threat tool used
to impart this information other examples include:
3.1.2 E-commerce Security Tools
Threat modelling tools allows users to systematically identify and rate the dangers that
are most likely to influence or affect a system’s functionality. These tools disguises’ and
rate threats, based on a solid understanding of the architecture design and implementation
of the software application tested (Weston, 2016). Security threats can be addressed with
proper countermeasures in a logical order, beginning with the threats that possess the
greatest risk. Threat modelling has a structured approach that is far more cost efficient
and viable than applying security features in a haphazard manner without knowing
precisely what each threat feature is supposed to address: (Jamil et al, 2015).
This review focuses on the current e-commerce tools and modelling approach used in
tackling security issues. The Microsoft threat analysis & modelling (TAM) tool
developed by their application consulting and engineering (ACE) team is an example for
the pragmatic technique employment for software acentric modelling approach. In
contrast, software-centric approaches are more suited for systems with an unknown
deployment pattern and designed to ensure the security of the software application's
underlying code in the context of rich server and client development. The security
development lifecycle (SDL) threat modelling tool, also by Microsoft, is an example of
the usage of a software-centric focus modelling approach. The attacker-centric focus
takes the adversary’s view to identify risks to the system. This requires the developer to
think like an attacker, to comprehend their inspiration and capabilities, which is likely to
pose a challenge to inexperienced users. Attack trees can also be called a threat tool used
to impart this information other examples include:

Firewalls – Software and Hardware.
Public key infrastructure.
Encryption software.
Digital certificates.
Digital signatures.
Biometrics – retinal scan, fingerprints, voice etc.
Passwords.
Locks and bars – network operations centre (Cobb, 2011).
3.1.3 Firewalls
The firewall is a software tools that allows or deny both incoming and outgoing
communications through a computer's ports or local network (Anicas 2015). Firewalls
filter traffic based on variety of factors and rules, which includes rules, IP address, local
connection and online connections. Firewall act as a bouncer, sending away traffic that
doesn’t fit a system or network connectivity. Firewall can also be used to blocks websites
pop and restrict unwanted online ads an application or website user doesn’t wish to
access. They can also filter sites known to be sources of malware from deterring users
from accidentally downloading a virus. Firewall depends on the network concerned,
namely multiple firewalls, multiple internal networks, VPNs, Extranets and perimeter
networks. There could also be a variety of connection types, for example TCP and UDP,
audio or video streaming, and downloading of applets. Different firewall configuration is
applied to different system and application connections. Several firewall products also
exist in the market from different vendors.
Public key infrastructure.
Encryption software.
Digital certificates.
Digital signatures.
Biometrics – retinal scan, fingerprints, voice etc.
Passwords.
Locks and bars – network operations centre (Cobb, 2011).
3.1.3 Firewalls
The firewall is a software tools that allows or deny both incoming and outgoing
communications through a computer's ports or local network (Anicas 2015). Firewalls
filter traffic based on variety of factors and rules, which includes rules, IP address, local
connection and online connections. Firewall act as a bouncer, sending away traffic that
doesn’t fit a system or network connectivity. Firewall can also be used to blocks websites
pop and restrict unwanted online ads an application or website user doesn’t wish to
access. They can also filter sites known to be sources of malware from deterring users
from accidentally downloading a virus. Firewall depends on the network concerned,
namely multiple firewalls, multiple internal networks, VPNs, Extranets and perimeter
networks. There could also be a variety of connection types, for example TCP and UDP,
audio or video streaming, and downloading of applets. Different firewall configuration is
applied to different system and application connections. Several firewall products also
exist in the market from different vendors.

3.1.4 Types of Firewalls
Packet Filtering: This is a basic firewall, with simple functionalities and operations to
block connections to and from specific hosts, network and ports (Eastep, 2017). Packet
filtering essentially examines a connection packet, and determines whether it has the
confirmation set rules that will permit it to go through the packet channel of the packet
header, IP address, port and grant. Due to its simplicity nature of operations, they have
the advantages of both speed and efficiency. An additional advantage is that they do their
job quite independently of the user's knowledge or internal and external gateway systems
inside Filter Demilitarized Zone (DMZ) Filter Outside 3 assistances, i.e., they have good
transparency (Meyer, 2006a). They are cheap because they use software already resident
in the router, and provide a good level of security since they are placed strategically at the
choke point (Meyer, 2006b).
Circuit Filtering: Circuit Proxy is mainly different from the packet filtering firewall as
circuit proxy addresses all communicators' channels and must address their packets
individually. Assuming access has been granted, the circuit proxy replaces the original
address with its own address of the intended destination. It has the drawback of laying
claim to the processing resources needed to modify the header, and the benefit of
masking the IP address of the target system (Zalenski , 2002). However, there is a
potential of hurting data to break through to its channel to the internal customer system
with the ideal that the package has being analysed properly.
Application Proxy Firewalls: These firewalls are a more complicated process than
circuit and packet filtering firewalls. The application proxy understands online
applications protocol and data, as well as intercepting any information intended to harm
Packet Filtering: This is a basic firewall, with simple functionalities and operations to
block connections to and from specific hosts, network and ports (Eastep, 2017). Packet
filtering essentially examines a connection packet, and determines whether it has the
confirmation set rules that will permit it to go through the packet channel of the packet
header, IP address, port and grant. Due to its simplicity nature of operations, they have
the advantages of both speed and efficiency. An additional advantage is that they do their
job quite independently of the user's knowledge or internal and external gateway systems
inside Filter Demilitarized Zone (DMZ) Filter Outside 3 assistances, i.e., they have good
transparency (Meyer, 2006a). They are cheap because they use software already resident
in the router, and provide a good level of security since they are placed strategically at the
choke point (Meyer, 2006b).
Circuit Filtering: Circuit Proxy is mainly different from the packet filtering firewall as
circuit proxy addresses all communicators' channels and must address their packets
individually. Assuming access has been granted, the circuit proxy replaces the original
address with its own address of the intended destination. It has the drawback of laying
claim to the processing resources needed to modify the header, and the benefit of
masking the IP address of the target system (Zalenski , 2002). However, there is a
potential of hurting data to break through to its channel to the internal customer system
with the ideal that the package has being analysed properly.
Application Proxy Firewalls: These firewalls are a more complicated process than
circuit and packet filtering firewalls. The application proxy understands online
applications protocol and data, as well as intercepting any information intended to harm
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

an online application (Savola and Abie, 2009). These firewalls are helpful in
counteracting assaults on procedures such HTTP and SMTP, guarding against SQL
infusion and DDoS assaults at the beginning of an attack. They can authenticate users and
judge whether any of the data could pose a threat. Application proxies are referred to as
proxy services, and the host machines running them as application gateways (Корнієнко,
2006).
Stateful Multilayer Inspection: This firewall is a combination of packet filtering, circuit
proxy and application layer firewalls discussed above. Although, it is a complex and
effective firewall that is more reliable than just the basic firewall. This firewall is self-
protecting as there are no administrators needed to regulate it frequently as it is self-
regulating and is proficient in protecting online packages (Chopra, 2016).
3.1.5 Public Key infrastructure
Complex business systems like e-commerce and automated business transactions require
robust and rigorous security measures. Public Key infrastructure supports the open key
contained in SSL declarations that permits distribution and identification of public
encryption key and secure network or data (Morgan, 2004a). Utilizing public key
infrastructure is a similar way to securing E-businesses and generally certificate
authorisation. Web assets such as programs, servers, customer emails and different types
of hardware equipment and software programming can be incorporated into public key
infrastructure to boost online security (Morgan, 2004b). Systems that often require public
key infrastructure based security mechanisms include email, various chip cards within e-
commerce (e.g. debit and credit cards) and electronic postal systems.
The Public Key Infrastructure environment is made up of five components:
counteracting assaults on procedures such HTTP and SMTP, guarding against SQL
infusion and DDoS assaults at the beginning of an attack. They can authenticate users and
judge whether any of the data could pose a threat. Application proxies are referred to as
proxy services, and the host machines running them as application gateways (Корнієнко,
2006).
Stateful Multilayer Inspection: This firewall is a combination of packet filtering, circuit
proxy and application layer firewalls discussed above. Although, it is a complex and
effective firewall that is more reliable than just the basic firewall. This firewall is self-
protecting as there are no administrators needed to regulate it frequently as it is self-
regulating and is proficient in protecting online packages (Chopra, 2016).
3.1.5 Public Key infrastructure
Complex business systems like e-commerce and automated business transactions require
robust and rigorous security measures. Public Key infrastructure supports the open key
contained in SSL declarations that permits distribution and identification of public
encryption key and secure network or data (Morgan, 2004a). Utilizing public key
infrastructure is a similar way to securing E-businesses and generally certificate
authorisation. Web assets such as programs, servers, customer emails and different types
of hardware equipment and software programming can be incorporated into public key
infrastructure to boost online security (Morgan, 2004b). Systems that often require public
key infrastructure based security mechanisms include email, various chip cards within e-
commerce (e.g. debit and credit cards) and electronic postal systems.
The Public Key Infrastructure environment is made up of five components:

1. Certification Authority (CA) - serves as the root of trust that authenticates the
identity of individuals, computers and other entities in the network.
2. Registration Authority (RA) - is certified by a root CA to issue certificates for
uses permitted by the CA. In a Microsoft PKI environment, the RA is normally
called a subordinate CA.
3. Certificate Database - saves certificate requests issued and revoked certificates
from the RA or CA.
4. Certificate Store - saves issued certificates and pending or rejected certificate
requests from the local computer.
5. Key Archival Server - saves encrypted private keys in a certificate database for
disaster recovery purposes in case the Certificate Database is lost (Gritzalis,
2005).
3.1.6 Encryption software Tools
Data encryption software tools are systems with the ability to encrypt data both for
transmission over a non-secure network and stored for future use (Kumar, 2017a).
Encryption doesn’t it self prevents interference of data, but denies the intelligence content
of the data to be revealed or intercepted by an unwanted individual or user. Encryption is
extremely important in e-commerce as it allows confidential information’s such as credit
card details to be used safely while shopping online (Kumar, 2017b). Encryption works
by scrambling the original message with a very large bit of code making it unreadable for
anybody else attempting to access it. After the data is encrypted, the sender and receiver
are the only users with the ability to decrypt the scrambled info back to a readable
identity of individuals, computers and other entities in the network.
2. Registration Authority (RA) - is certified by a root CA to issue certificates for
uses permitted by the CA. In a Microsoft PKI environment, the RA is normally
called a subordinate CA.
3. Certificate Database - saves certificate requests issued and revoked certificates
from the RA or CA.
4. Certificate Store - saves issued certificates and pending or rejected certificate
requests from the local computer.
5. Key Archival Server - saves encrypted private keys in a certificate database for
disaster recovery purposes in case the Certificate Database is lost (Gritzalis,
2005).
3.1.6 Encryption software Tools
Data encryption software tools are systems with the ability to encrypt data both for
transmission over a non-secure network and stored for future use (Kumar, 2017a).
Encryption doesn’t it self prevents interference of data, but denies the intelligence content
of the data to be revealed or intercepted by an unwanted individual or user. Encryption is
extremely important in e-commerce as it allows confidential information’s such as credit
card details to be used safely while shopping online (Kumar, 2017b). Encryption works
by scrambling the original message with a very large bit of code making it unreadable for
anybody else attempting to access it. After the data is encrypted, the sender and receiver
are the only users with the ability to decrypt the scrambled info back to a readable
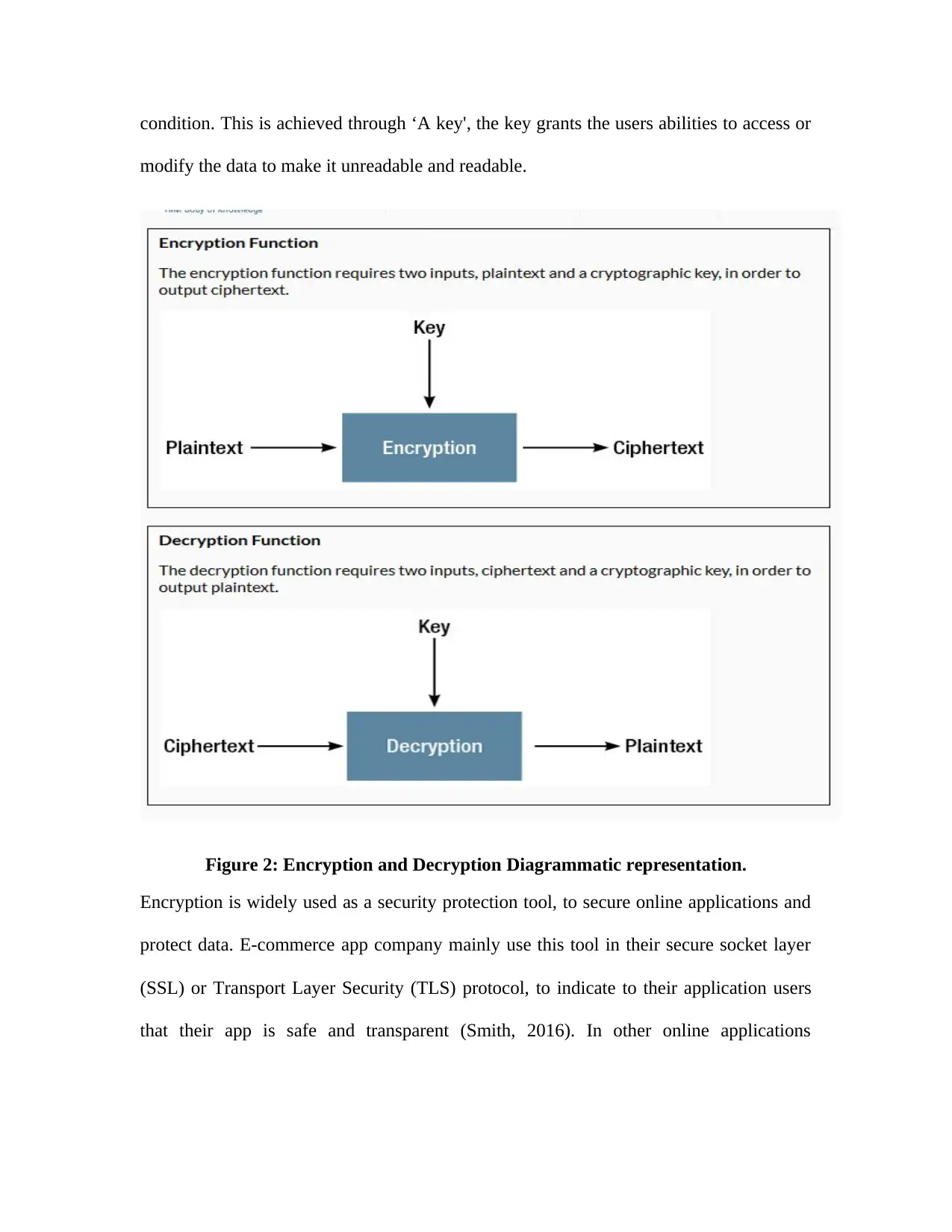
condition. This is achieved through ‘A key', the key grants the users abilities to access or
modify the data to make it unreadable and readable.
Figure 2: Encryption and Decryption Diagrammatic representation.
Encryption is widely used as a security protection tool, to secure online applications and
protect data. E-commerce app company mainly use this tool in their secure socket layer
(SSL) or Transport Layer Security (TLS) protocol, to indicate to their application users
that their app is safe and transparent (Smith, 2016). In other online applications
modify the data to make it unreadable and readable.
Figure 2: Encryption and Decryption Diagrammatic representation.
Encryption is widely used as a security protection tool, to secure online applications and
protect data. E-commerce app company mainly use this tool in their secure socket layer
(SSL) or Transport Layer Security (TLS) protocol, to indicate to their application users
that their app is safe and transparent (Smith, 2016). In other online applications
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

encryption are also used to enter a password to encrypt or decrypt the protected data if a
cryptographic key is used as the password.
The SSL protocol and TLS are the primary end-to-end security encryption protocols used
to protect information traversing the Internet. The most common scenario of using this
protocol is when used as web browser acting as a client for human users interacting with
a web server. Thus, using SSL and TLS as an encryption between a web browser and a
web server can be used important data from unauthorized parties or users.
Finally, encryption tool can be used to secure a hard drive, USB and end to end users
over a local computer networks. This is possible as unauthorised users cannot reproduce
the plaintext used to encrypt the drivers and servers without the cryptographic key. This
is another major way of ensuring e-commerce security.
3.1.7 Digital Certificates and Signatures Security Tool
Digital signature tool facilities the safe exchange of electronic documents and files by
providing a way to test the authenticity and the integrity of the information exchange
online or digitally (Mason, 2014a). It is otherwise an encrypted digital hash message used
to verify if the message was tampered with by hashing the received message and
comparing the message value with a decryption signature. A digital signature is created
by a series of mathematical processes that transform data into a uniquely coded 'message
digest'(Mason, 2014b). The message digested is an attached encrypted file to a message
being interchanged from a digital signature for security between the message sender and
message recipient.
cryptographic key is used as the password.
The SSL protocol and TLS are the primary end-to-end security encryption protocols used
to protect information traversing the Internet. The most common scenario of using this
protocol is when used as web browser acting as a client for human users interacting with
a web server. Thus, using SSL and TLS as an encryption between a web browser and a
web server can be used important data from unauthorized parties or users.
Finally, encryption tool can be used to secure a hard drive, USB and end to end users
over a local computer networks. This is possible as unauthorised users cannot reproduce
the plaintext used to encrypt the drivers and servers without the cryptographic key. This
is another major way of ensuring e-commerce security.
3.1.7 Digital Certificates and Signatures Security Tool
Digital signature tool facilities the safe exchange of electronic documents and files by
providing a way to test the authenticity and the integrity of the information exchange
online or digitally (Mason, 2014a). It is otherwise an encrypted digital hash message used
to verify if the message was tampered with by hashing the received message and
comparing the message value with a decryption signature. A digital signature is created
by a series of mathematical processes that transform data into a uniquely coded 'message
digest'(Mason, 2014b). The message digested is an attached encrypted file to a message
being interchanged from a digital signature for security between the message sender and
message recipient.
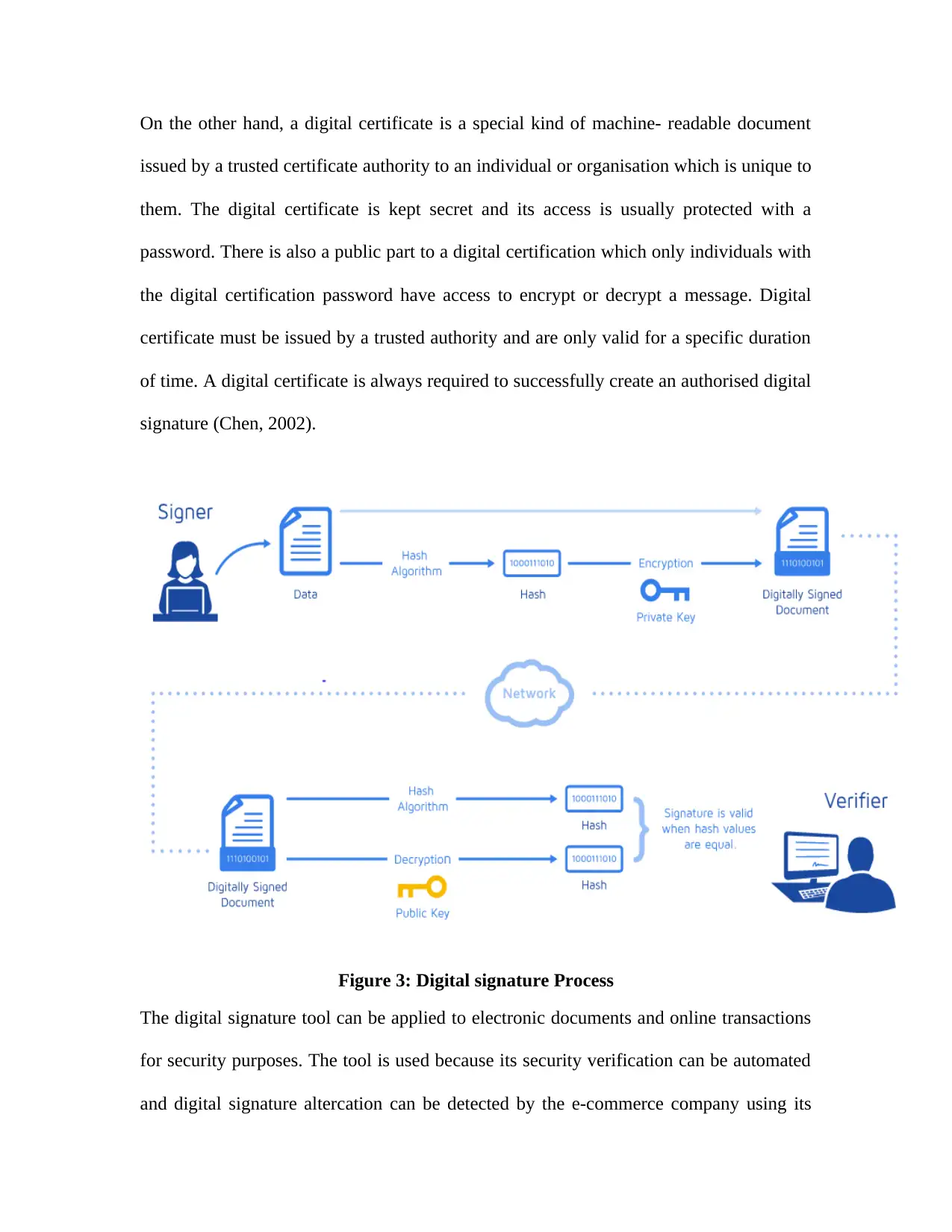
On the other hand, a digital certificate is a special kind of machine- readable document
issued by a trusted certificate authority to an individual or organisation which is unique to
them. The digital certificate is kept secret and its access is usually protected with a
password. There is also a public part to a digital certification which only individuals with
the digital certification password have access to encrypt or decrypt a message. Digital
certificate must be issued by a trusted authority and are only valid for a specific duration
of time. A digital certificate is always required to successfully create an authorised digital
signature (Chen, 2002).
Figure 3: Digital signature Process
The digital signature tool can be applied to electronic documents and online transactions
for security purposes. The tool is used because its security verification can be automated
and digital signature altercation can be detected by the e-commerce company using its
issued by a trusted certificate authority to an individual or organisation which is unique to
them. The digital certificate is kept secret and its access is usually protected with a
password. There is also a public part to a digital certification which only individuals with
the digital certification password have access to encrypt or decrypt a message. Digital
certificate must be issued by a trusted authority and are only valid for a specific duration
of time. A digital certificate is always required to successfully create an authorised digital
signature (Chen, 2002).
Figure 3: Digital signature Process
The digital signature tool can be applied to electronic documents and online transactions
for security purposes. The tool is used because its security verification can be automated
and digital signature altercation can be detected by the e-commerce company using its

services. While a digital certificate is used to bind public keys to a person or a group of
people to ensure a digital signature is not easily forged by unauthorized users. Employing
digital signatures and certification tools to a company's system grants a secure control.
This is capable of enforce policies that requires effective separation of duties among
colleagues of e-commerce company, higher authenticities and senior administrative from
their superiors. The digital certificate is used on transaction website based on HTTPS
belonging to e-commerce firm and government agencies to increase trustworthiness of its
users.
3.1.8 Biometrics Security Tool
Biometric security tool is a method of verifying a software or system identity based on
the individual unique physical features or an action (Indi and Raut 2012). This biometric
measurement could be applied to a document as an evidence of an individual’s personal
signature. Biometric authentication is based on the specific physical features and
behaviour characteristic of individuals. These attributes are mainly from an individual's
facial recognition, finger print, hand geometry, iris, keystroke, signature, and voice
recognition.
Biometrics securities are inherently more reliable than password based authentication as
individual traits cannot be lost or stolen by unwanted persons. In addition, biometric traits
are difficult to copy, share and distribute by hackers as they require the person being
authenticated to be present at the time and point authentication before a security breach
can occur.
Biometric systems are becoming used increasingly in relation to recognizing individuals;
regulate access to physical spaces, information, services and to other rights and benefits,
people to ensure a digital signature is not easily forged by unauthorized users. Employing
digital signatures and certification tools to a company's system grants a secure control.
This is capable of enforce policies that requires effective separation of duties among
colleagues of e-commerce company, higher authenticities and senior administrative from
their superiors. The digital certificate is used on transaction website based on HTTPS
belonging to e-commerce firm and government agencies to increase trustworthiness of its
users.
3.1.8 Biometrics Security Tool
Biometric security tool is a method of verifying a software or system identity based on
the individual unique physical features or an action (Indi and Raut 2012). This biometric
measurement could be applied to a document as an evidence of an individual’s personal
signature. Biometric authentication is based on the specific physical features and
behaviour characteristic of individuals. These attributes are mainly from an individual's
facial recognition, finger print, hand geometry, iris, keystroke, signature, and voice
recognition.
Biometrics securities are inherently more reliable than password based authentication as
individual traits cannot be lost or stolen by unwanted persons. In addition, biometric traits
are difficult to copy, share and distribute by hackers as they require the person being
authenticated to be present at the time and point authentication before a security breach
can occur.
Biometric systems are becoming used increasingly in relation to recognizing individuals;
regulate access to physical spaces, information, services and to other rights and benefits,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

including the ability of individuals to cross international borders (Moore, 2007). They
also help to improve the convenience and efficient of routine access transactions,
reducing online fraud and enhancing public safety and national security
3.1.9 Passwords Security Tool
Password tools are the unique keys to IT software, an abuse or misuse of any IT
password or key will result in credential data leakage and breach of privacy (Riley and
Chaparro, 2006a). To improve control over password and prevent secured data breaches
from occurring, organisations must store them securely, change them regularly and
monitor their usage.
Passwords are commonly used in conjunction with a username. However, on most secure
e-commerce websites they may also be used alongside other methods of identification
such as a separate pin, memorable information and touch ID. In some other major
website, online users are also tended be ask customers to enter only certain characters of
your password, for additional security.
To verify that a user entered the right user ID, that individual is requested to provide an
identification or password. This password and username must only be known to that
individual using the system or application. Most network developers suggest that
systems’ end users should change their passwords on a periodic basis to enhance their
personal security.
The term password is typically a word or group of sentences between four and thirty-two
characters, depending on how the computer system is set up (Riley and Chaparro, 2006b).
When a password is entered, the computer system is careful not to display the characters
also help to improve the convenience and efficient of routine access transactions,
reducing online fraud and enhancing public safety and national security
3.1.9 Passwords Security Tool
Password tools are the unique keys to IT software, an abuse or misuse of any IT
password or key will result in credential data leakage and breach of privacy (Riley and
Chaparro, 2006a). To improve control over password and prevent secured data breaches
from occurring, organisations must store them securely, change them regularly and
monitor their usage.
Passwords are commonly used in conjunction with a username. However, on most secure
e-commerce websites they may also be used alongside other methods of identification
such as a separate pin, memorable information and touch ID. In some other major
website, online users are also tended be ask customers to enter only certain characters of
your password, for additional security.
To verify that a user entered the right user ID, that individual is requested to provide an
identification or password. This password and username must only be known to that
individual using the system or application. Most network developers suggest that
systems’ end users should change their passwords on a periodic basis to enhance their
personal security.
The term password is typically a word or group of sentences between four and thirty-two
characters, depending on how the computer system is set up (Riley and Chaparro, 2006b).
When a password is entered, the computer system is careful not to display the characters

on the display screen, in most cases; otherwise other individuals might see it. App
developers suggests system passwords need to be very difficult in other not to get cracked
through by using guessing, brute force cracking, dictionary attacks or other common
methods. Password hardening is one of the major measures taken to make it more
difficult for an intruder to circumvent the authentication process of any e-commerce
system or applications.
3.1.10 Major Threat Modelling Approaches
The concept of threat modelling is not a new term but a clear definition has changed in
recent years toward internet security dimension. Threat modelling is an approach for
analysing the security of an online application or system (Semple, 2015). It is a structured
approach that enables software engineers to identify, quantify, analysis and address the
security risks associated with an application or software. Threat modelling isn’t an
approach to reviewing code, but it rather complements the security code reviewing
process of an application. Threat modelling can be view into two different contexts
especially when it relates to e-commerce (Pye and Warren, 2007). They are the security
approach that uses architecture implementation or structure of the application
functionalities to help map out its security requirements. On the other hand, are the
possible attackable components or assets of the e-commerce application. The various
available threat modelling technique has their major goal of implementing
countermeasures against different applications, however will be majorly concern with the
threat modelling approach related to e-commerce applications in this review. According
to Potter (2009) the different threat modelling approaches are grouped into;
developers suggests system passwords need to be very difficult in other not to get cracked
through by using guessing, brute force cracking, dictionary attacks or other common
methods. Password hardening is one of the major measures taken to make it more
difficult for an intruder to circumvent the authentication process of any e-commerce
system or applications.
3.1.10 Major Threat Modelling Approaches
The concept of threat modelling is not a new term but a clear definition has changed in
recent years toward internet security dimension. Threat modelling is an approach for
analysing the security of an online application or system (Semple, 2015). It is a structured
approach that enables software engineers to identify, quantify, analysis and address the
security risks associated with an application or software. Threat modelling isn’t an
approach to reviewing code, but it rather complements the security code reviewing
process of an application. Threat modelling can be view into two different contexts
especially when it relates to e-commerce (Pye and Warren, 2007). They are the security
approach that uses architecture implementation or structure of the application
functionalities to help map out its security requirements. On the other hand, are the
possible attackable components or assets of the e-commerce application. The various
available threat modelling technique has their major goal of implementing
countermeasures against different applications, however will be majorly concern with the
threat modelling approach related to e-commerce applications in this review. According
to Potter (2009) the different threat modelling approaches are grouped into;

1. Soft-Centric - These approaches involve designing threat systems that can be
illustrated using software architecture diagram such as data-flow diagram (DFD),
use case diagram or component diagrams. Examples of soft-centric are
Microsoft's Security Development Lifecycle Frame and Microsoft Threat
Analysis and modelling Tools.
2. Asset-Centric - These approaches involve identifying the assets of an
organisation entrusted to system or software that is sensitive and are of high
potential attack by cyber- criminals. Examples are Attack tree, Attack graph,
Trike and Amenaza's Securitree.
3. Attacker-Centric- These threats modelling approaches involves modelling a
specific attack requirement profile for an attacker based on its known
characteristics, skill-set and motivation to exploit vulnerability to an online
system or software. The threat approach is then built on the understood attacker’s
profile, which is most likely to execute a specific type of exploitation and
mitigation using its known strategy accordingly. However, there is no specific
example, majority of attacker-centric approaches done my major security
company’s such as Threat Modeller and MyAppSecurity’s using the principle of
Attack tree technique.
It is has being noticed that different firms attack security from different perspective and
style; however, the attack centric and the asset centric are the mainly used once.
Technique 1 STRIDE: Is a modelling approach used to meet the security properties of
Confidentiality, Integrity, and Availability (CIA), along with Authorization. Microsoft
uses its STRIDE methodology which is mainly used by Microsoft for authentication and
illustrated using software architecture diagram such as data-flow diagram (DFD),
use case diagram or component diagrams. Examples of soft-centric are
Microsoft's Security Development Lifecycle Frame and Microsoft Threat
Analysis and modelling Tools.
2. Asset-Centric - These approaches involve identifying the assets of an
organisation entrusted to system or software that is sensitive and are of high
potential attack by cyber- criminals. Examples are Attack tree, Attack graph,
Trike and Amenaza's Securitree.
3. Attacker-Centric- These threats modelling approaches involves modelling a
specific attack requirement profile for an attacker based on its known
characteristics, skill-set and motivation to exploit vulnerability to an online
system or software. The threat approach is then built on the understood attacker’s
profile, which is most likely to execute a specific type of exploitation and
mitigation using its known strategy accordingly. However, there is no specific
example, majority of attacker-centric approaches done my major security
company’s such as Threat Modeller and MyAppSecurity’s using the principle of
Attack tree technique.
It is has being noticed that different firms attack security from different perspective and
style; however, the attack centric and the asset centric are the mainly used once.
Technique 1 STRIDE: Is a modelling approach used to meet the security properties of
Confidentiality, Integrity, and Availability (CIA), along with Authorization. Microsoft
uses its STRIDE methodology which is mainly used by Microsoft for authentication and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
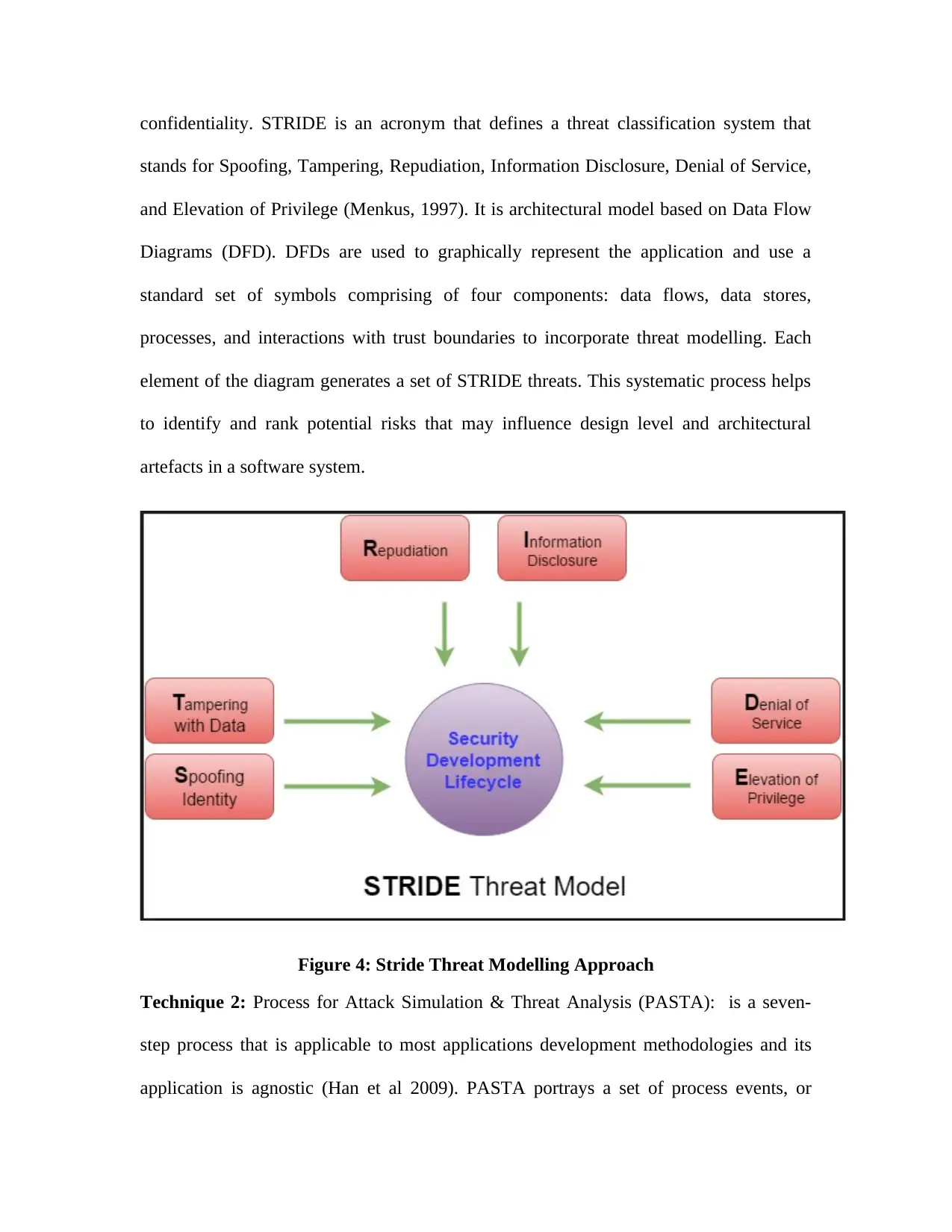
confidentiality. STRIDE is an acronym that defines a threat classification system that
stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service,
and Elevation of Privilege (Menkus, 1997). It is architectural model based on Data Flow
Diagrams (DFD). DFDs are used to graphically represent the application and use a
standard set of symbols comprising of four components: data flows, data stores,
processes, and interactions with trust boundaries to incorporate threat modelling. Each
element of the diagram generates a set of STRIDE threats. This systematic process helps
to identify and rank potential risks that may influence design level and architectural
artefacts in a software system.
Figure 4: Stride Threat Modelling Approach
Technique 2: Process for Attack Simulation & Threat Analysis (PASTA): is a seven-
step process that is applicable to most applications development methodologies and its
application is agnostic (Han et al 2009). PASTA portrays a set of process events, or
stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service,
and Elevation of Privilege (Menkus, 1997). It is architectural model based on Data Flow
Diagrams (DFD). DFDs are used to graphically represent the application and use a
standard set of symbols comprising of four components: data flows, data stores,
processes, and interactions with trust boundaries to incorporate threat modelling. Each
element of the diagram generates a set of STRIDE threats. This systematic process helps
to identify and rank potential risks that may influence design level and architectural
artefacts in a software system.
Figure 4: Stride Threat Modelling Approach
Technique 2: Process for Attack Simulation & Threat Analysis (PASTA): is a seven-
step process that is applicable to most applications development methodologies and its
application is agnostic (Han et al 2009). PASTA portrays a set of process events, or

stages, through the recommendation of set process inputs and the normal process outputs.
These outcomes create the execution of activities of each stage. Each of the seven stages
has specific objectives and expected deliverables (Sangita and Madhuri, 2015). PASTA
methodology maps well into most requirements definition phase of a given SDLC
process by listing any administrations related issues, alongside potential risk and business
impact considerations. The seven key activities in PASTA are as follows:
Define Business Objectives
Define Tech Scope
App Decomposition
Threat Analysis
Vulnerability Detection
Attack Enumeration
Risk and Impact Analysis (Mehta, 2016).
Technique 3: Attack Trees provide a formal, systematic method of describing the
security of systems, based on varying attacks. Essentially the tree structure is to represent
attacks against a system, with its objective as the root node and different ways of
achieving that goal as leaf nodes (Schneier, 2000). The nodes become sub goals with the
way to achieving that sub goal being children of each node. OR nodes are used to
represent alternatives and AND nodes are used to represent different steps toward
achieving the same goal. Once the tree is assembled, one can assign values to the various
leaf nodes, and then make calculations about the nodes. The security of the goal can also
be calculated once the values are assigned. The attack attributes help in relating risk with
an attack. An Attack Tree can include special knowledge or equipment that is needed, the
These outcomes create the execution of activities of each stage. Each of the seven stages
has specific objectives and expected deliverables (Sangita and Madhuri, 2015). PASTA
methodology maps well into most requirements definition phase of a given SDLC
process by listing any administrations related issues, alongside potential risk and business
impact considerations. The seven key activities in PASTA are as follows:
Define Business Objectives
Define Tech Scope
App Decomposition
Threat Analysis
Vulnerability Detection
Attack Enumeration
Risk and Impact Analysis (Mehta, 2016).
Technique 3: Attack Trees provide a formal, systematic method of describing the
security of systems, based on varying attacks. Essentially the tree structure is to represent
attacks against a system, with its objective as the root node and different ways of
achieving that goal as leaf nodes (Schneier, 2000). The nodes become sub goals with the
way to achieving that sub goal being children of each node. OR nodes are used to
represent alternatives and AND nodes are used to represent different steps toward
achieving the same goal. Once the tree is assembled, one can assign values to the various
leaf nodes, and then make calculations about the nodes. The security of the goal can also
be calculated once the values are assigned. The attack attributes help in relating risk with
an attack. An Attack Tree can include special knowledge or equipment that is needed, the

time required to complete a step, and the physical and legal risks assumed by the attacker
(DSouza, 2016). The Attack Tree’s values could be operational or development expenses.
It supports design and requirement decisions. Suppose an attack costs the perpetrator
more than the benefit, that attack will most likely not occur. However, if there are simple
attacks that may result in benefit, then those need a protection.
Figure 5: Diagram showing an Attack Tree on Credit Card System
3.1.11 Benefit of Effective E-commerce Security
Change as it is commonly said is the only constant commodity to mankind. It is a trend
that would never become obsolete. Humanity over the years has witnessed diverse
tremendous, significant and notable technological advancement.
Arguably, one of the greatest inventions of all times was the advent of the internet. That
alone catapulted information technology to a whole new dimension. Information in
(DSouza, 2016). The Attack Tree’s values could be operational or development expenses.
It supports design and requirement decisions. Suppose an attack costs the perpetrator
more than the benefit, that attack will most likely not occur. However, if there are simple
attacks that may result in benefit, then those need a protection.
Figure 5: Diagram showing an Attack Tree on Credit Card System
3.1.11 Benefit of Effective E-commerce Security
Change as it is commonly said is the only constant commodity to mankind. It is a trend
that would never become obsolete. Humanity over the years has witnessed diverse
tremendous, significant and notable technological advancement.
Arguably, one of the greatest inventions of all times was the advent of the internet. That
alone catapulted information technology to a whole new dimension. Information in
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

diverse forms can now be dispersed and gotten at the speed of light. The right
information is needed by every organisation to thrive at its maximum capacity. Ever since
the year 2000, e-commerce has revolutionized the dynamics of both the international and
local market place (McGrath, 2017). It is near impossible for the 21st century trade to
have elevated to its present altitude without e-commerce.
However, a new level of advancement comes with its own challenges. As with other
routes of trade, the necessity of security which is a major public concern in e-commerce
cannot be over emphasized. Security is perhaps the most significant aspect when
developing any ecommerce website. Having the physical security measures, such as
Secure Server Connection (SSL Certificate) is essential but it also needs to be made very
clear to potential buyers that all the information that they submit is secured by the best
security measures available, with clear display of all security badges and to attack online
customers.
Firstly, a secure system would build the confidence of potential investors and buyers in
the online store. Customers need to be assured that all their details, both personal and
financial are all kept safe for e-commerce growth (Herrmann and Herrmann, 2004). An
insecure buyer would always shy away from a great deal online, for fear of a scam and
hacking of personal details.
Secondly, online security is needed to avoid unnecessary cash loss. Business is all about
providing goods and services to make the maximum profits available, so if we constantly
run into losses due to hackers breaking into our websites and law suits from clients, then
the main aim of running that platform is defeated.
information is needed by every organisation to thrive at its maximum capacity. Ever since
the year 2000, e-commerce has revolutionized the dynamics of both the international and
local market place (McGrath, 2017). It is near impossible for the 21st century trade to
have elevated to its present altitude without e-commerce.
However, a new level of advancement comes with its own challenges. As with other
routes of trade, the necessity of security which is a major public concern in e-commerce
cannot be over emphasized. Security is perhaps the most significant aspect when
developing any ecommerce website. Having the physical security measures, such as
Secure Server Connection (SSL Certificate) is essential but it also needs to be made very
clear to potential buyers that all the information that they submit is secured by the best
security measures available, with clear display of all security badges and to attack online
customers.
Firstly, a secure system would build the confidence of potential investors and buyers in
the online store. Customers need to be assured that all their details, both personal and
financial are all kept safe for e-commerce growth (Herrmann and Herrmann, 2004). An
insecure buyer would always shy away from a great deal online, for fear of a scam and
hacking of personal details.
Secondly, online security is needed to avoid unnecessary cash loss. Business is all about
providing goods and services to make the maximum profits available, so if we constantly
run into losses due to hackers breaking into our websites and law suits from clients, then
the main aim of running that platform is defeated.

Thirdly, e-commerce has transformed the banking sector as well. The banking system,
building society or finance house cannot function without adequate security measures on
ground by e-commerce business (Samant, 2008). A secure and satisfied client would also
refer more clients to you, thereby increasing customer base. People tend to work with
organizations who they believe have a good track record for security.
Chapter 4: Methodology
4.1 System Methodology
A Software development methodology is a framework that is used to structure, plan, and
control the process of developing an information system. (IT Knowledge Portal, 2015).
System methodology is used in this work in order to improve upon existing working
software or framework as it develops, enabling for regular inspection of the product.
Research methodology provides the right analysis and product for a system to be done
accurately by allowing for constant communication between a researcher, designer, tester
and users. Furthermore, research methodology enables a clear visibility of a project by
helping to ensure that any necessary decisions can be made at the earliest possible
opportunity. This outcome is normally done to avoid unforeseen circumstances while
there is still time to avoid any risk outcome. Also, research methodology is an efficient
way of effectively managing time for a project.
In this work, four research methodologies were selected to be applied in the analysis
process of Threat Modelling Tools and Technique used in securing e-commerce
applications online. They include:
Prototype Methods
building society or finance house cannot function without adequate security measures on
ground by e-commerce business (Samant, 2008). A secure and satisfied client would also
refer more clients to you, thereby increasing customer base. People tend to work with
organizations who they believe have a good track record for security.
Chapter 4: Methodology
4.1 System Methodology
A Software development methodology is a framework that is used to structure, plan, and
control the process of developing an information system. (IT Knowledge Portal, 2015).
System methodology is used in this work in order to improve upon existing working
software or framework as it develops, enabling for regular inspection of the product.
Research methodology provides the right analysis and product for a system to be done
accurately by allowing for constant communication between a researcher, designer, tester
and users. Furthermore, research methodology enables a clear visibility of a project by
helping to ensure that any necessary decisions can be made at the earliest possible
opportunity. This outcome is normally done to avoid unforeseen circumstances while
there is still time to avoid any risk outcome. Also, research methodology is an efficient
way of effectively managing time for a project.
In this work, four research methodologies were selected to be applied in the analysis
process of Threat Modelling Tools and Technique used in securing e-commerce
applications online. They include:
Prototype Methods

Dynamic Systems Development Model (DSDM)
Spring
Agile Scrum Development
4.1.1 Prototype Method
Evolutionary prototype is the process of continuous development by creating multiple
prototypes based on the feedback received from the past prototype and requirements
gathered from a client (Shah, 2001). This software methodology encourages requirements
churning, by delivering the system in small parts to the users for better understanding.
Any new changes can be recognized and integrated into the next prototype, alongside the
newly found research developments. Essentially, the prototype starts out very small and
grows in size and structure as different sections are added (Carey & Mason, 1983). This
methodology is normally used alongside the agile methodology because of its mix range
in planning and documentation of a project. It is swift to react to changes in client
requirements, as well as dealing with any problems which may arise as the projects
increases.
4.1.2 Dynamic Systems Development Model (DSDM)
The Dynamic Systems Development Method (DSDM) is an agile project delivery
framework principally used as a software development method. It is a methodology
which encapsulates a significant part of the current project knowledge and how to
manage the knowledge in developing a new artefact. This method was established by
software improvement group, however programming advancement, led to designing and
Spring
Agile Scrum Development
4.1.1 Prototype Method
Evolutionary prototype is the process of continuous development by creating multiple
prototypes based on the feedback received from the past prototype and requirements
gathered from a client (Shah, 2001). This software methodology encourages requirements
churning, by delivering the system in small parts to the users for better understanding.
Any new changes can be recognized and integrated into the next prototype, alongside the
newly found research developments. Essentially, the prototype starts out very small and
grows in size and structure as different sections are added (Carey & Mason, 1983). This
methodology is normally used alongside the agile methodology because of its mix range
in planning and documentation of a project. It is swift to react to changes in client
requirements, as well as dealing with any problems which may arise as the projects
increases.
4.1.2 Dynamic Systems Development Model (DSDM)
The Dynamic Systems Development Method (DSDM) is an agile project delivery
framework principally used as a software development method. It is a methodology
which encapsulates a significant part of the current project knowledge and how to
manage the knowledge in developing a new artefact. This method was established by
software improvement group, however programming advancement, led to designing and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

subsequently producing an engineering and business project development methodology.
The methodology has generally changed the way large framework and complex problem
project tasks can be easily solved. I considered this approach for this research because of
its ability to produce flexible prototype result that is direct and immediate and as well
visible. More so, it eliminates bureaucracy and breaking down communication barriers
between the project researcher and different parties involved in the project. However, this
methodology was not used for this project because of its difficulties in understanding and
successful implementations. The strictness towards adhering to its principle, made this
methodology difficult to control when applied to the development of the new security
thread modelling framework.
4.1.3 Spring Model
The spring model was proposed by Boehm in 1986, it was aimed to minimize the risk
within the software development process by early detection of potential problem areas
(Nilsson, 2012). The spring model utilizes an iterative design which incorporates five
stages; objectives settings, risk assessment, development, validation and constant
planning.
The methodology has generally changed the way large framework and complex problem
project tasks can be easily solved. I considered this approach for this research because of
its ability to produce flexible prototype result that is direct and immediate and as well
visible. More so, it eliminates bureaucracy and breaking down communication barriers
between the project researcher and different parties involved in the project. However, this
methodology was not used for this project because of its difficulties in understanding and
successful implementations. The strictness towards adhering to its principle, made this
methodology difficult to control when applied to the development of the new security
thread modelling framework.
4.1.3 Spring Model
The spring model was proposed by Boehm in 1986, it was aimed to minimize the risk
within the software development process by early detection of potential problem areas
(Nilsson, 2012). The spring model utilizes an iterative design which incorporates five
stages; objectives settings, risk assessment, development, validation and constant
planning.
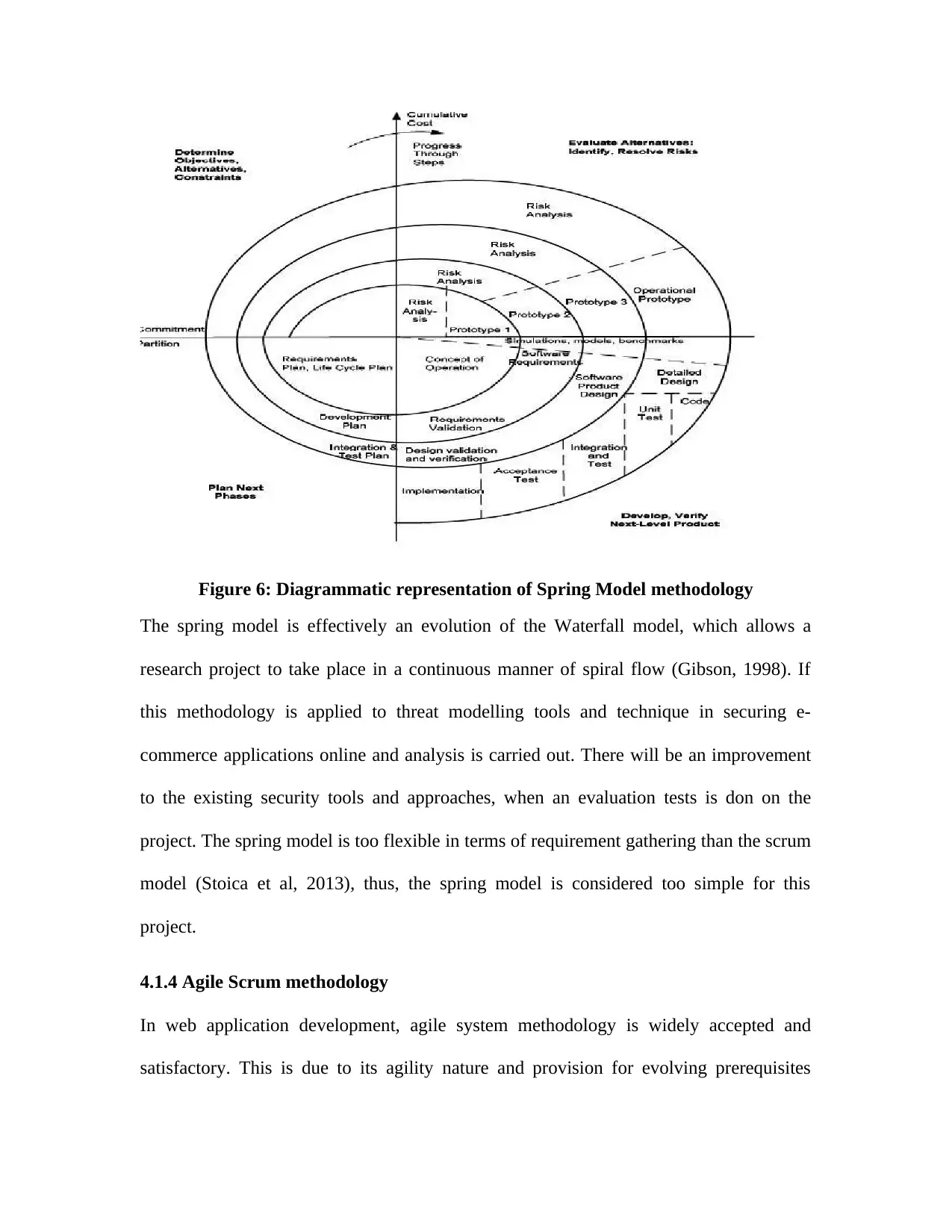
Figure 6: Diagrammatic representation of Spring Model methodology
The spring model is effectively an evolution of the Waterfall model, which allows a
research project to take place in a continuous manner of spiral flow (Gibson, 1998). If
this methodology is applied to threat modelling tools and technique in securing e-
commerce applications online and analysis is carried out. There will be an improvement
to the existing security tools and approaches, when an evaluation tests is don on the
project. The spring model is too flexible in terms of requirement gathering than the scrum
model (Stoica et al, 2013), thus, the spring model is considered too simple for this
project.
4.1.4 Agile Scrum methodology
In web application development, agile system methodology is widely accepted and
satisfactory. This is due to its agility nature and provision for evolving prerequisites
The spring model is effectively an evolution of the Waterfall model, which allows a
research project to take place in a continuous manner of spiral flow (Gibson, 1998). If
this methodology is applied to threat modelling tools and technique in securing e-
commerce applications online and analysis is carried out. There will be an improvement
to the existing security tools and approaches, when an evaluation tests is don on the
project. The spring model is too flexible in terms of requirement gathering than the scrum
model (Stoica et al, 2013), thus, the spring model is considered too simple for this
project.
4.1.4 Agile Scrum methodology
In web application development, agile system methodology is widely accepted and
satisfactory. This is due to its agility nature and provision for evolving prerequisites

instead of waterfall methodology (Pressman, 2009). This method emphasizes on client
collaboration and satisfaction, defect rate reduction and most importantly their short
iterative nature within a time frame. Agile is a preferred method for most design as it
aims to shorten this timescale and add value to the project with each iteration there are
several agile methodologies; however, this report will focus on SCRUM methodology.
Background information on Scrum methodology will be provided to give a clear
understanding of this choice of methodology. An evaluation is done to provide clear view
as to why it was selected.
Fig 7.1 shows how the SCRUM process works. Design that constantly changes requires
the SCRUM methodology. This method helps in breaking down large design into smaller
tasks, which are called ‘sprints’ it requires communication and teamwork between team
members from different levels as well as user. The major people involved in the project
are the ‘ScrumMaster’ who is the project researcher and the project supervisor whom
offers support to the framework development. SCRUM will derive a quicker requirement
achievement as the time frame for implementing this project is reduced, because it has an
effective iterations management.
collaboration and satisfaction, defect rate reduction and most importantly their short
iterative nature within a time frame. Agile is a preferred method for most design as it
aims to shorten this timescale and add value to the project with each iteration there are
several agile methodologies; however, this report will focus on SCRUM methodology.
Background information on Scrum methodology will be provided to give a clear
understanding of this choice of methodology. An evaluation is done to provide clear view
as to why it was selected.
Fig 7.1 shows how the SCRUM process works. Design that constantly changes requires
the SCRUM methodology. This method helps in breaking down large design into smaller
tasks, which are called ‘sprints’ it requires communication and teamwork between team
members from different levels as well as user. The major people involved in the project
are the ‘ScrumMaster’ who is the project researcher and the project supervisor whom
offers support to the framework development. SCRUM will derive a quicker requirement
achievement as the time frame for implementing this project is reduced, because it has an
effective iterations management.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Figure 7: Diagrammatic Representation of Scrum Iteration
In addressing question about ethical consideration which is based on accumulation of
values and principles that address questions, one of the clearest definitions is simply the
conflict of interest between researchers and people being researched (Dickens and Cook,
2005). It ensures that the researcher must take measure that every single form of ethical
code is followed to the letter to avoid any unforeseen risk to the research project. To
further eliminate risk, the researcher had to obtain written consent from the research
participant. An overview the consent piece of data collected using the British Educational
Research Association (BERA) process for ensuring the subject understands what he/she
is doing and why it is necessary to the research.
4.1.5 Ethical consideration conducted the following process:
Negotiating access to information in the e-commerce sector
Informing individuals and companies of their personal consent before using it for
this project.
Abiding to the United Kingdom Data Protection Act 1998.
Give rights to respondents of the project to withdraw at any time without or with
justification.
Privacy and disclosure i.e. the procedures regarding confidentiality will be clearly
explained to e-
commerce firms (e.g. use of names, pseudonyms, anonymization of data, etc.).
The use of the data in research project, publications, sharing and archiving will be
explained to staffs of the e-commerce firms.
In addressing question about ethical consideration which is based on accumulation of
values and principles that address questions, one of the clearest definitions is simply the
conflict of interest between researchers and people being researched (Dickens and Cook,
2005). It ensures that the researcher must take measure that every single form of ethical
code is followed to the letter to avoid any unforeseen risk to the research project. To
further eliminate risk, the researcher had to obtain written consent from the research
participant. An overview the consent piece of data collected using the British Educational
Research Association (BERA) process for ensuring the subject understands what he/she
is doing and why it is necessary to the research.
4.1.5 Ethical consideration conducted the following process:
Negotiating access to information in the e-commerce sector
Informing individuals and companies of their personal consent before using it for
this project.
Abiding to the United Kingdom Data Protection Act 1998.
Give rights to respondents of the project to withdraw at any time without or with
justification.
Privacy and disclosure i.e. the procedures regarding confidentiality will be clearly
explained to e-
commerce firms (e.g. use of names, pseudonyms, anonymization of data, etc.).
The use of the data in research project, publications, sharing and archiving will be
explained to staffs of the e-commerce firms.

The agreement date and signature will be kept for referral purpose.
Company information will be stored securely and information will not be shared
with 3rd parties.
Written permission will be obtained from participants before commencement of
data collection.
(British Educational Research Association2001)
4.2 Data Collection
The interview was conducted with users of the case studied e-commerce firms. In the
process of conducting this interview, I contacted various people; they include selected IT
staff, users and suppliers. They were all treated fairly, regardless of age, gender,
ethnicity, religion and with freedom. Questions were asked in a manner that the
respondent were free to express themselves. Each of the users of the application
understood and agreed to undertake the interview without any duress. The users also
understood the process in which they will be engaged in and why they are participating in
the process. The entire participant was briefed on how and who to report to if not clear
about any procedure. The Interview was then carried out after written approval from
respondent.
A reasonable understanding was given to the respondent that this researcher will not
access to data or information givens unless it was agreed to preserve the confidentiality of
the data and agree to the terms specified by the firms and users. The selected
organizations will have the right to know how, where and why their data is being stored.
The transcription of the collected data was discussed in the interview analysis section.
Company information will be stored securely and information will not be shared
with 3rd parties.
Written permission will be obtained from participants before commencement of
data collection.
(British Educational Research Association2001)
4.2 Data Collection
The interview was conducted with users of the case studied e-commerce firms. In the
process of conducting this interview, I contacted various people; they include selected IT
staff, users and suppliers. They were all treated fairly, regardless of age, gender,
ethnicity, religion and with freedom. Questions were asked in a manner that the
respondent were free to express themselves. Each of the users of the application
understood and agreed to undertake the interview without any duress. The users also
understood the process in which they will be engaged in and why they are participating in
the process. The entire participant was briefed on how and who to report to if not clear
about any procedure. The Interview was then carried out after written approval from
respondent.
A reasonable understanding was given to the respondent that this researcher will not
access to data or information givens unless it was agreed to preserve the confidentiality of
the data and agree to the terms specified by the firms and users. The selected
organizations will have the right to know how, where and why their data is being stored.
The transcription of the collected data was discussed in the interview analysis section.

The main participants of this interview were mainly teen aged residents. The age range of
participants was from 20 to 30 this is because they are the active users of the selected e-
commerce organisations. I selected this age grade randomly, because according to
selection on the e-commerce application website, teens are their active users.
4.3 Evidence of the interview Conducted Online (Template)
Interview Questions Template
Ethic Understanding
Understand and confirm your choice by underlining the appropriate
I have read and understood the information about the project, as provided in the
Information Sheet dated 28/01/2017. Yes /No
I have been given the opportunity to ask questions about the project and my
participation. Yes/No
I understand I can withdraw at any time from the interview without giving reasons
and that I will not be penalised for withdrawing nor will I be questioned on why I
have withdrawn. Yes/ No
The procedures regarding confidentiality have been clearly explained (e.g. use of
names, pseudonyms, anonymization of data, etc.) to me. Yes/No
I would like my name used and understand what I have said or written as part of
this study will be used n reports, publications and other research outputs so that
anything I have contributed to this project can be recognised. Yes/ No
Name:
participants was from 20 to 30 this is because they are the active users of the selected e-
commerce organisations. I selected this age grade randomly, because according to
selection on the e-commerce application website, teens are their active users.
4.3 Evidence of the interview Conducted Online (Template)
Interview Questions Template
Ethic Understanding
Understand and confirm your choice by underlining the appropriate
I have read and understood the information about the project, as provided in the
Information Sheet dated 28/01/2017. Yes /No
I have been given the opportunity to ask questions about the project and my
participation. Yes/No
I understand I can withdraw at any time from the interview without giving reasons
and that I will not be penalised for withdrawing nor will I be questioned on why I
have withdrawn. Yes/ No
The procedures regarding confidentiality have been clearly explained (e.g. use of
names, pseudonyms, anonymization of data, etc.) to me. Yes/No
I would like my name used and understand what I have said or written as part of
this study will be used n reports, publications and other research outputs so that
anything I have contributed to this project can be recognised. Yes/ No
Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Signature:
Questions
Do you do use online shopping website. Yes/ No
Do you use your Credit Card or PayPal? Yes/No
Do you Consider security of your personal data whiling using the E-
commerce application? Yes/No
Who should be responsible for your personal data security, (Me / E-business
Company)? Yes/No
Do you shop with; -
i. eBay Yes/No
ii. Amazon Yes/No
iii. Konga Yes/No
Do u have any security Concern while using this website?
i. EBay Yes/No
ii. Amazon Yes/No
iii. Konga Yes/No
If (yes) please explain
Any further Suggestion on E-commerce issues:
Date
Questions
Do you do use online shopping website. Yes/ No
Do you use your Credit Card or PayPal? Yes/No
Do you Consider security of your personal data whiling using the E-
commerce application? Yes/No
Who should be responsible for your personal data security, (Me / E-business
Company)? Yes/No
Do you shop with; -
i. eBay Yes/No
ii. Amazon Yes/No
iii. Konga Yes/No
Do u have any security Concern while using this website?
i. EBay Yes/No
ii. Amazon Yes/No
iii. Konga Yes/No
If (yes) please explain
Any further Suggestion on E-commerce issues:
Date

Signature
4.4 Interview Summary
At the end of the interview, 80% of the participant accepted they had done online
shopping with their credit in an e-commerce website. Majority of the respondent hadn't
used PayPal; however, it was clear they engaged other services that were not PayPal, in
order to make transaction on an e-commerce website. Among the participant, those that
use their credit card ascertain that sometimes it is unsafe to use it on an e-commerce
website because of credit theft. However, participants were happy using their credit to
shop online because of the convenience it provides, compare to going out to shop from
regular shops. Notwithstanding, 95% of the participants would like the e-commerce firms
and their bank online credit card issuer to do more in providing adequate protection from
cybercriminals while using their online website and applications.
Other respondent who uses PayPal claimed they use it to secure their bank card due to
bad experience whilst using their online credit bank cards to shop on e-commerce
website. Other response was that they refuse to use PayPal because of the companies'
transactions chargers associated with using it to shop from e-commerce applications.
Whiles some PayPal users claim they could use the service to access some e-commerce
website. About 20% of the participant had issues of not getting through to their
customer’s services. However, no participant had any major security issues warranting
them to make online transactions on e-commerce website. Further-more, 100% of the
participant claims the e-commerce company and their bank should be held responsible for
the security of their data and information uploaded to their servers. The major security
4.4 Interview Summary
At the end of the interview, 80% of the participant accepted they had done online
shopping with their credit in an e-commerce website. Majority of the respondent hadn't
used PayPal; however, it was clear they engaged other services that were not PayPal, in
order to make transaction on an e-commerce website. Among the participant, those that
use their credit card ascertain that sometimes it is unsafe to use it on an e-commerce
website because of credit theft. However, participants were happy using their credit to
shop online because of the convenience it provides, compare to going out to shop from
regular shops. Notwithstanding, 95% of the participants would like the e-commerce firms
and their bank online credit card issuer to do more in providing adequate protection from
cybercriminals while using their online website and applications.
Other respondent who uses PayPal claimed they use it to secure their bank card due to
bad experience whilst using their online credit bank cards to shop on e-commerce
website. Other response was that they refuse to use PayPal because of the companies'
transactions chargers associated with using it to shop from e-commerce applications.
Whiles some PayPal users claim they could use the service to access some e-commerce
website. About 20% of the participant had issues of not getting through to their
customer’s services. However, no participant had any major security issues warranting
them to make online transactions on e-commerce website. Further-more, 100% of the
participant claims the e-commerce company and their bank should be held responsible for
the security of their data and information uploaded to their servers. The major security

threat participant observes and experience in the eBay, Amazon and Konga website are
documented in detail below.
4.5 Data Analysis from the Interview
A. Security Issues Associated with E-Bay App System
Most participant felt eBay was not meting up to standard in terms of providing adequate
security on their platform, because there are illegal sellers who adversities their products
on the app, but fails to deliver the item if after successfully purchased by a customer.
They also complained that eBay application security verification, two-step security
verification, is compatible with the Nokia and HTC mobile devices. Finally, some eBay
customers that participated in the interview claimed their account has been undermined
especially when the password is not strong enough to stand hackers, and eBay response
to security issue is slow especially when complain is made via email or telephone.
Although, some customers commended that it is an easy and convenient way to shop as
many participants claim, some even said they make lot of money from bargain eBay
application.
B. Security Issues Associated with Amazon App System
The response from participants that uses Amazon application had very few security
concern, they felt it was relative safe compared to other e-commerce applications. Some
participant claimed they experience other issues using the application. Some customers
complain about the delay in shipping period of delivery items when ordered from the
Amazon application. Another respondent claimed the app also shows a stipulated
delivery date, but there is always delay in delivery the item to the specific destination on
the delivery date stated. Some respondent thinks this is a major problem with the Amazon
documented in detail below.
4.5 Data Analysis from the Interview
A. Security Issues Associated with E-Bay App System
Most participant felt eBay was not meting up to standard in terms of providing adequate
security on their platform, because there are illegal sellers who adversities their products
on the app, but fails to deliver the item if after successfully purchased by a customer.
They also complained that eBay application security verification, two-step security
verification, is compatible with the Nokia and HTC mobile devices. Finally, some eBay
customers that participated in the interview claimed their account has been undermined
especially when the password is not strong enough to stand hackers, and eBay response
to security issue is slow especially when complain is made via email or telephone.
Although, some customers commended that it is an easy and convenient way to shop as
many participants claim, some even said they make lot of money from bargain eBay
application.
B. Security Issues Associated with Amazon App System
The response from participants that uses Amazon application had very few security
concern, they felt it was relative safe compared to other e-commerce applications. Some
participant claimed they experience other issues using the application. Some customers
complain about the delay in shipping period of delivery items when ordered from the
Amazon application. Another respondent claimed the app also shows a stipulated
delivery date, but there is always delay in delivery the item to the specific destination on
the delivery date stated. Some respondent thinks this is a major problem with the Amazon
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

application. Other complains include rigid polices towards returning a bought item from
their application. They want the process of returning items that's did not meet
specification via their amazon application. Another complained about the application
customers service team are very slow in responding to customer complain from the app.
Most complain are not linking to security issues.
C. Security Issues Associated with Konga App System
Among the interview carried out, about 30% of the participants were konga users. This is
an e-commerce based in Nigeria and sells item across the African continent. Participant
from Konga users had some major issues regarding security of their bank card being
stored on the website. They are also concerned that the website doesn’t accept some
banks online credit cards and PayPal. Although the, app users are very satisfied with the
delivery services. Some users complained that sometimes they deliver substandard or
damage product. Participant also complained about the apps customer’s services response
time, which is very slow. Other complained include hidden charges that are being
withdrawn from their account without their knowledge. Lastly some participant
complained about been unable to add selected items to the application cart and while
using their Nokia mobile device.
their application. They want the process of returning items that's did not meet
specification via their amazon application. Another complained about the application
customers service team are very slow in responding to customer complain from the app.
Most complain are not linking to security issues.
C. Security Issues Associated with Konga App System
Among the interview carried out, about 30% of the participants were konga users. This is
an e-commerce based in Nigeria and sells item across the African continent. Participant
from Konga users had some major issues regarding security of their bank card being
stored on the website. They are also concerned that the website doesn’t accept some
banks online credit cards and PayPal. Although the, app users are very satisfied with the
delivery services. Some users complained that sometimes they deliver substandard or
damage product. Participant also complained about the apps customer’s services response
time, which is very slow. Other complained include hidden charges that are being
withdrawn from their account without their knowledge. Lastly some participant
complained about been unable to add selected items to the application cart and while
using their Nokia mobile device.
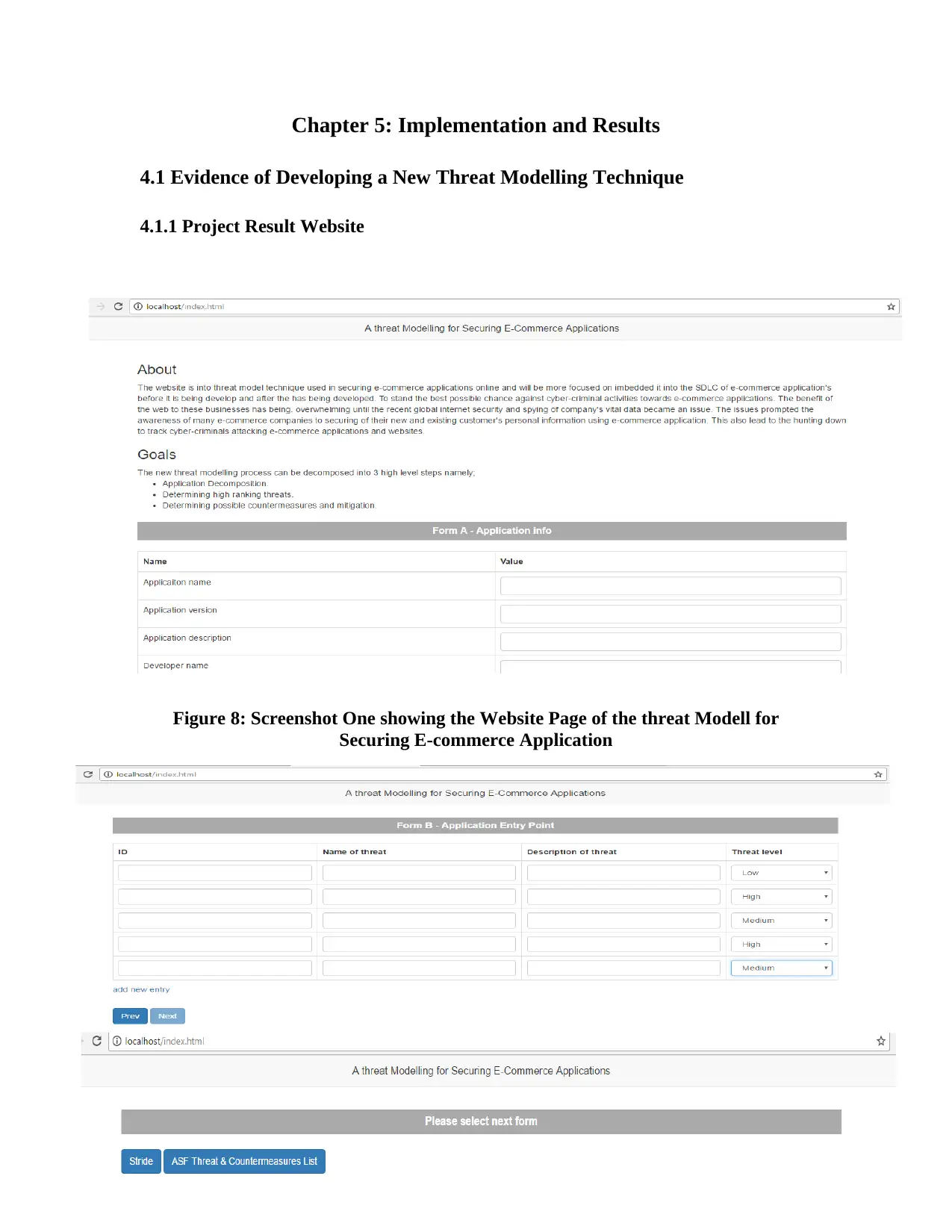
Chapter 5: Implementation and Results
4.1 Evidence of Developing a New Threat Modelling Technique
4.1.1 Project Result Website
Figure 8: Screenshot One showing the Website Page of the threat Modell for
Securing E-commerce Application
4.1 Evidence of Developing a New Threat Modelling Technique
4.1.1 Project Result Website
Figure 8: Screenshot One showing the Website Page of the threat Modell for
Securing E-commerce Application

Figure 9: Screenshot two showing the Website Page of the threat Modell for
Securing E-commerce Application
Figure 10: Screenshot One showing the Website Page of the threat modelling for
Securing E-commerce Application
4.2 Project Result Discussion
Goals
This threat modelling technique will ensure that all e-commerce applications are being
developed with security integration from the very beginning. This threat modelling
process will combine the documentation of the SDLC in e-commerce application
development to assist in maintaining a better operation and understanding of the system.
The system will have allowed the reviewer to see where the entry points to the
application are and the associated threats with each entry point.
This modern threat modelling tools, analyse an e-commerce application from a potential
attacker's perspective, it does not work on the defensive side. The model is primarily
applied to an application at the SDLC; level. Notwithstanding, it can be also being
Securing E-commerce Application
Figure 10: Screenshot One showing the Website Page of the threat modelling for
Securing E-commerce Application
4.2 Project Result Discussion
Goals
This threat modelling technique will ensure that all e-commerce applications are being
developed with security integration from the very beginning. This threat modelling
process will combine the documentation of the SDLC in e-commerce application
development to assist in maintaining a better operation and understanding of the system.
The system will have allowed the reviewer to see where the entry points to the
application are and the associated threats with each entry point.
This modern threat modelling tools, analyse an e-commerce application from a potential
attacker's perspective, it does not work on the defensive side. The model is primarily
applied to an application at the SDLC; level. Notwithstanding, it can be also being
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

applied to already existing applications to analyse major security threats associated with
the app.
The new threat modelling process can be broken down into 3 high level steps namely;
i. Application Decomposition.
ii. Determining high ranking threats.
iii. Determining possible countermeasures and mitigation.
Step 1: Application Decomposition: The first step in this threat modelling process is
concerned with gaining an understanding of the application and how it interacts with
external entities (app users and servers). This will be illustrated by creating use-case
diagram demonstrating and showcasing, how the e-commerce application is used in
identifying entry points to see where a potential attacker could interact with the
application.
In addition, application decomposition involves identified asset, which could be items or
areas that the attacker will be interested in attacking thus damaging the application. This
application decomposition information will be documented in the threat model document
to produce data flow diagrams (DFDs) for the e-commerce application. The DFDs will
show the different paths through the system and highlighting the privilege boundaries.
Step 2: Determining high ranking threats: Another criterion to the identification of
threats is using a threat categorization methodology. Threat categorization method such
as STRIDE and Application Security Frame (ASF) can be used to define the threat
the app.
The new threat modelling process can be broken down into 3 high level steps namely;
i. Application Decomposition.
ii. Determining high ranking threats.
iii. Determining possible countermeasures and mitigation.
Step 1: Application Decomposition: The first step in this threat modelling process is
concerned with gaining an understanding of the application and how it interacts with
external entities (app users and servers). This will be illustrated by creating use-case
diagram demonstrating and showcasing, how the e-commerce application is used in
identifying entry points to see where a potential attacker could interact with the
application.
In addition, application decomposition involves identified asset, which could be items or
areas that the attacker will be interested in attacking thus damaging the application. This
application decomposition information will be documented in the threat model document
to produce data flow diagrams (DFDs) for the e-commerce application. The DFDs will
show the different paths through the system and highlighting the privilege boundaries.
Step 2: Determining high ranking threats: Another criterion to the identification of
threats is using a threat categorization methodology. Threat categorization method such
as STRIDE and Application Security Frame (ASF) can be used to define the threat

ranking. The goal of the threat categorization is to help identify threats both from the
attacker (STRIDE) or the defensive perspective (ASF).
The DFDs produced in step 1 will them help to identify the potential threat targets from
the attacker's perspective using data sources, processes, data flows, and interactions with
users. These threats can be identified further as the roots for threat trees and there is one
tree for each threat goal. From the defensive perspective, ASF can help in categorizing
threat by identifying its weaknesses of security controls for threats. Common threat-lists
with examples will help in the identification of major e-commerce threats with qualitative
risk model based on general risk factors such as likelihood, impact and probability to be
constructed.
Step 3: Determining possible countermeasures and mitigation: Lack of protection
against specific system threat might indicate application vulnerability, risk exposure
towards hackers, breakdown of its functionalities and implementation. The most suitable
countermeasures towards these threats can be identified using the current existing threat-
counter measure mapping lists. The purpose of the counter measurement is to determine
if there is protective measure in place to prevent each previously identified threat analysis
from being realized. The priority of the available threat is to enhance the application
mitigation effort by applying the adequate countermeasures from the countermeasure
mapping list.
The risk mitigation strategy majorly involves evaluating the identified threats per the
business impact they pose and reducing the risk. While other might include taking the
risk and removing the risk posed by the threat completely, some may even prefer to do
nothing.
attacker (STRIDE) or the defensive perspective (ASF).
The DFDs produced in step 1 will them help to identify the potential threat targets from
the attacker's perspective using data sources, processes, data flows, and interactions with
users. These threats can be identified further as the roots for threat trees and there is one
tree for each threat goal. From the defensive perspective, ASF can help in categorizing
threat by identifying its weaknesses of security controls for threats. Common threat-lists
with examples will help in the identification of major e-commerce threats with qualitative
risk model based on general risk factors such as likelihood, impact and probability to be
constructed.
Step 3: Determining possible countermeasures and mitigation: Lack of protection
against specific system threat might indicate application vulnerability, risk exposure
towards hackers, breakdown of its functionalities and implementation. The most suitable
countermeasures towards these threats can be identified using the current existing threat-
counter measure mapping lists. The purpose of the counter measurement is to determine
if there is protective measure in place to prevent each previously identified threat analysis
from being realized. The priority of the available threat is to enhance the application
mitigation effort by applying the adequate countermeasures from the countermeasure
mapping list.
The risk mitigation strategy majorly involves evaluating the identified threats per the
business impact they pose and reducing the risk. While other might include taking the
risk and removing the risk posed by the threat completely, some may even prefer to do
nothing.
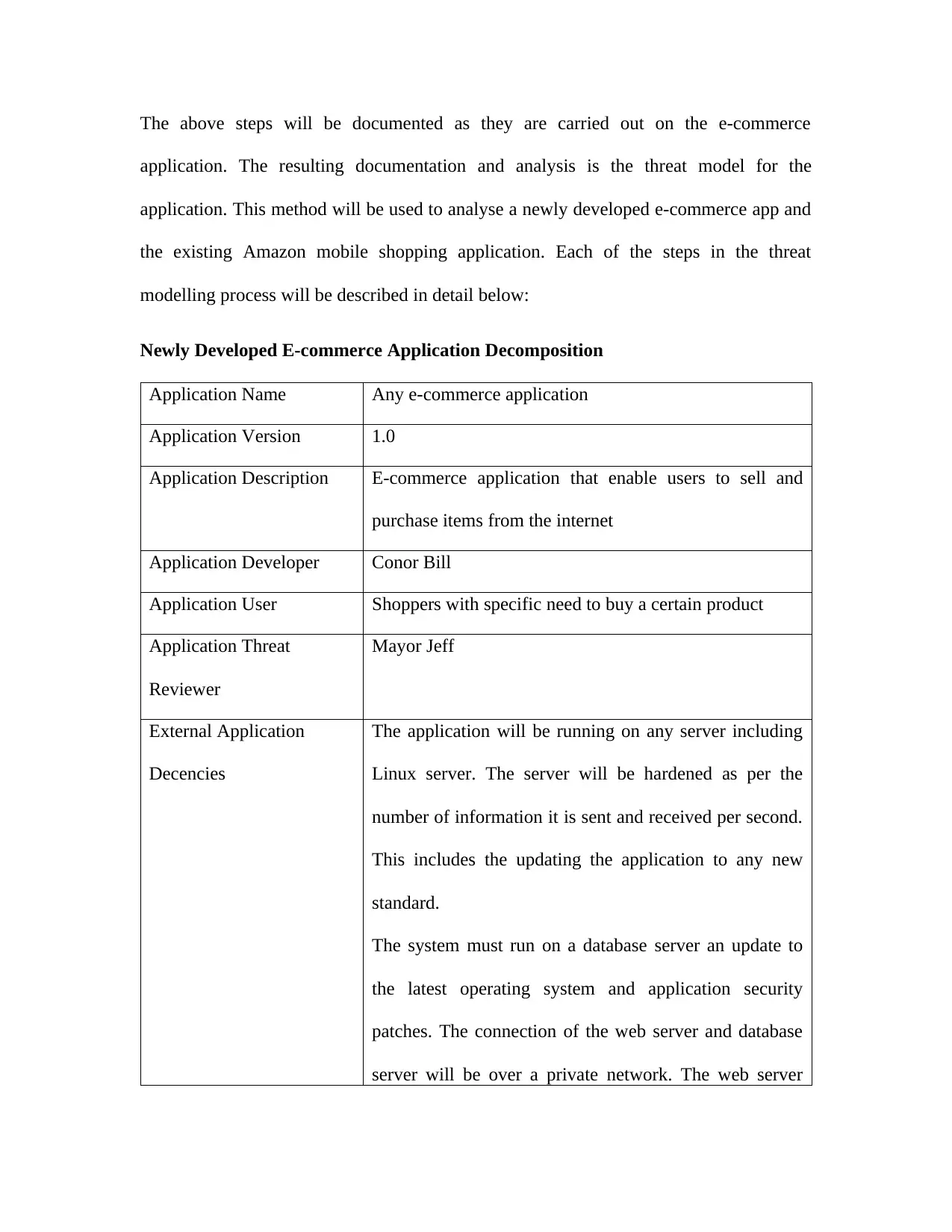
The above steps will be documented as they are carried out on the e-commerce
application. The resulting documentation and analysis is the threat model for the
application. This method will be used to analyse a newly developed e-commerce app and
the existing Amazon mobile shopping application. Each of the steps in the threat
modelling process will be described in detail below:
Newly Developed E-commerce Application Decomposition
Application Name Any e-commerce application
Application Version 1.0
Application Description E-commerce application that enable users to sell and
purchase items from the internet
Application Developer Conor Bill
Application User Shoppers with specific need to buy a certain product
Application Threat
Reviewer
Mayor Jeff
External Application
Decencies
The application will be running on any server including
Linux server. The server will be hardened as per the
number of information it is sent and received per second.
This includes the updating the application to any new
standard.
The system must run on a database server an update to
the latest operating system and application security
patches. The connection of the web server and database
server will be over a private network. The web server
application. The resulting documentation and analysis is the threat model for the
application. This method will be used to analyse a newly developed e-commerce app and
the existing Amazon mobile shopping application. Each of the steps in the threat
modelling process will be described in detail below:
Newly Developed E-commerce Application Decomposition
Application Name Any e-commerce application
Application Version 1.0
Application Description E-commerce application that enable users to sell and
purchase items from the internet
Application Developer Conor Bill
Application User Shoppers with specific need to buy a certain product
Application Threat
Reviewer
Mayor Jeff
External Application
Decencies
The application will be running on any server including
Linux server. The server will be hardened as per the
number of information it is sent and received per second.
This includes the updating the application to any new
standard.
The system must run on a database server an update to
the latest operating system and application security
patches. The connection of the web server and database
server will be over a private network. The web server
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

should be protected behind strong firewalls.
Table 1: Newly Developed E-commerce Application Decomposition
Application Entry Point
Entry points define the interfaces or points through which potential attackers can interact
with an application to supply it with data. For a potential attacker to attack an application
an entry point must exist. Entry points in an application can be layered. For example,
each web page in a web application may contain multiple entry points. Entry points will
be documented as follows:
ID - A unique ID is assigned to the entry point. This will be used to cross
reference the entry point with any threats or vulnerabilities that will be identified.
Name - A descriptive name is used to identify the entry point and its purpose.
Description - A textual description detailing the interaction or processing that
occurs at the entry point.
Trust Levels - The level of access required at the entry point is documented here.
These will be cross referenced with the trusts levels defined later in the document.
ID Name Description Trust Level
1 HTTP The e-commerce app will be
accessible on any mobile phone with
internet once it has been downloaded
appropriately.
Anonymous web users.
Users with valid login
credential.
Users with invalid login
credentials.
1.1 Official
website
The main page of the e-commerce
application is an entry point for all
users.
Anonymous web users.
Users with valid login
credential.
Users with invalid login
credentials.
1.2 Application All the e-commerce customers with Staff.
Table 1: Newly Developed E-commerce Application Decomposition
Application Entry Point
Entry points define the interfaces or points through which potential attackers can interact
with an application to supply it with data. For a potential attacker to attack an application
an entry point must exist. Entry points in an application can be layered. For example,
each web page in a web application may contain multiple entry points. Entry points will
be documented as follows:
ID - A unique ID is assigned to the entry point. This will be used to cross
reference the entry point with any threats or vulnerabilities that will be identified.
Name - A descriptive name is used to identify the entry point and its purpose.
Description - A textual description detailing the interaction or processing that
occurs at the entry point.
Trust Levels - The level of access required at the entry point is documented here.
These will be cross referenced with the trusts levels defined later in the document.
ID Name Description Trust Level
1 HTTP The e-commerce app will be
accessible on any mobile phone with
internet once it has been downloaded
appropriately.
Anonymous web users.
Users with valid login
credential.
Users with invalid login
credentials.
1.1 Official
website
The main page of the e-commerce
application is an entry point for all
users.
Anonymous web users.
Users with valid login
credential.
Users with invalid login
credentials.
1.2 Application All the e-commerce customers with Staff.
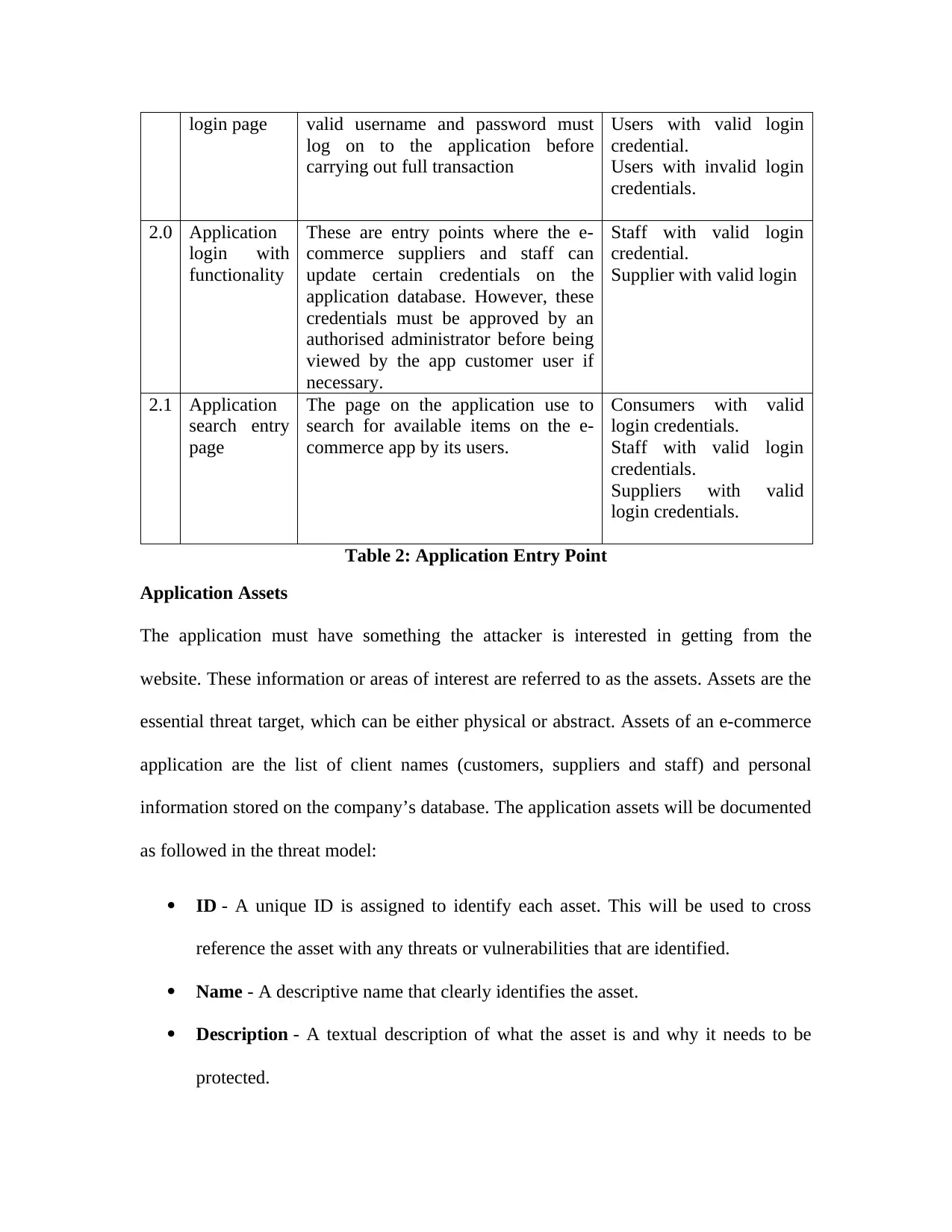
login page valid username and password must
log on to the application before
carrying out full transaction
Users with valid login
credential.
Users with invalid login
credentials.
2.0 Application
login with
functionality
These are entry points where the e-
commerce suppliers and staff can
update certain credentials on the
application database. However, these
credentials must be approved by an
authorised administrator before being
viewed by the app customer user if
necessary.
Staff with valid login
credential.
Supplier with valid login
2.1 Application
search entry
page
The page on the application use to
search for available items on the e-
commerce app by its users.
Consumers with valid
login credentials.
Staff with valid login
credentials.
Suppliers with valid
login credentials.
Table 2: Application Entry Point
Application Assets
The application must have something the attacker is interested in getting from the
website. These information or areas of interest are referred to as the assets. Assets are the
essential threat target, which can be either physical or abstract. Assets of an e-commerce
application are the list of client names (customers, suppliers and staff) and personal
information stored on the company’s database. The application assets will be documented
as followed in the threat model:
ID - A unique ID is assigned to identify each asset. This will be used to cross
reference the asset with any threats or vulnerabilities that are identified.
Name - A descriptive name that clearly identifies the asset.
Description - A textual description of what the asset is and why it needs to be
protected.
log on to the application before
carrying out full transaction
Users with valid login
credential.
Users with invalid login
credentials.
2.0 Application
login with
functionality
These are entry points where the e-
commerce suppliers and staff can
update certain credentials on the
application database. However, these
credentials must be approved by an
authorised administrator before being
viewed by the app customer user if
necessary.
Staff with valid login
credential.
Supplier with valid login
2.1 Application
search entry
page
The page on the application use to
search for available items on the e-
commerce app by its users.
Consumers with valid
login credentials.
Staff with valid login
credentials.
Suppliers with valid
login credentials.
Table 2: Application Entry Point
Application Assets
The application must have something the attacker is interested in getting from the
website. These information or areas of interest are referred to as the assets. Assets are the
essential threat target, which can be either physical or abstract. Assets of an e-commerce
application are the list of client names (customers, suppliers and staff) and personal
information stored on the company’s database. The application assets will be documented
as followed in the threat model:
ID - A unique ID is assigned to identify each asset. This will be used to cross
reference the asset with any threats or vulnerabilities that are identified.
Name - A descriptive name that clearly identifies the asset.
Description - A textual description of what the asset is and why it needs to be
protected.
Trust Levels – The trust level is the access requirement level to login to the entry
point. This will be documented for an e-commerce company here. These will be
cross referenced with the trust levels defined in the next step.
ID Name Description Trust Level
1.1 Customers user This involves the e-
commerce customers who
have registered with their
personal information and
bank details as assets to the
application
Very high level for only
customers with login
credentials.
1.2 Customer
unique
password and
ID
These are the e-commerce
customers; unique
credentials needed for
signing into the application.
Very high trust level unique
to just customers’ users,
database administrator or
reader and webserver user.
1.3 Staff login
details
These are the credentials
need to be stored in the e-
commerce app database to
verify a staff user.
Very high trust level, unique
to the staff user database
server administrator or
reader and the webserver
user.
1.4 Supplier login
details
These are the credentials
need to be stored in the e-
commerce app database to
verify a supplier user.
Very high trust level, unique
to the supplier’s user
database server administrator
or reader and the web
Server user.
1.5 Company legal
and private
trademark
documents.
These assets have to do with
the legal documents of the e-
commerce which doesn’t
have to be shared publicly.
Very high trust level unique
to certain staff with
authorisation to access these
fills.
2 System `Assets
2.0 The app
executive code
This is the e-commerce
development application
code, which is not to be open
source as it is a legal
document of the company.
Medium trust level, because
this document can be
outsourced to a third-party
company to help with its
regular testing maintenance,
and updating.
2.1 The app SQL or
my SQL
database
This is a major asset of the e-
commerce application that
stores data, retrieve then and
delete when necessary.
Medium trust level, because
this database can be
outsourced to a third-party
company to help with its
regular testing maintenance,
and updating.
2.2 The access to These are new information Very high trust level,
point. This will be documented for an e-commerce company here. These will be
cross referenced with the trust levels defined in the next step.
ID Name Description Trust Level
1.1 Customers user This involves the e-
commerce customers who
have registered with their
personal information and
bank details as assets to the
application
Very high level for only
customers with login
credentials.
1.2 Customer
unique
password and
ID
These are the e-commerce
customers; unique
credentials needed for
signing into the application.
Very high trust level unique
to just customers’ users,
database administrator or
reader and webserver user.
1.3 Staff login
details
These are the credentials
need to be stored in the e-
commerce app database to
verify a staff user.
Very high trust level, unique
to the staff user database
server administrator or
reader and the webserver
user.
1.4 Supplier login
details
These are the credentials
need to be stored in the e-
commerce app database to
verify a supplier user.
Very high trust level, unique
to the supplier’s user
database server administrator
or reader and the web
Server user.
1.5 Company legal
and private
trademark
documents.
These assets have to do with
the legal documents of the e-
commerce which doesn’t
have to be shared publicly.
Very high trust level unique
to certain staff with
authorisation to access these
fills.
2 System `Assets
2.0 The app
executive code
This is the e-commerce
development application
code, which is not to be open
source as it is a legal
document of the company.
Medium trust level, because
this document can be
outsourced to a third-party
company to help with its
regular testing maintenance,
and updating.
2.1 The app SQL or
my SQL
database
This is a major asset of the e-
commerce application that
stores data, retrieve then and
delete when necessary.
Medium trust level, because
this database can be
outsourced to a third-party
company to help with its
regular testing maintenance,
and updating.
2.2 The access to These are new information Very high trust level,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
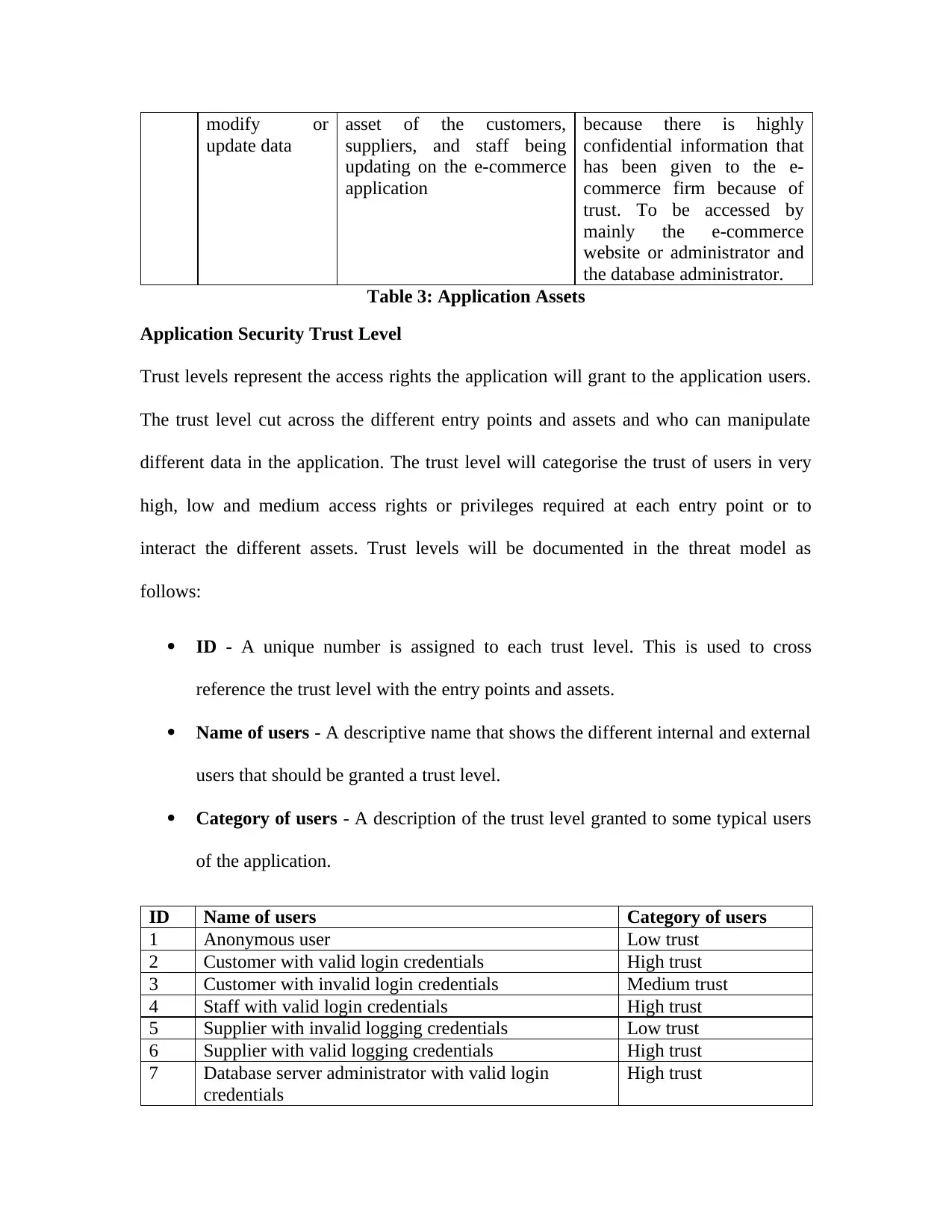
modify or
update data
asset of the customers,
suppliers, and staff being
updating on the e-commerce
application
because there is highly
confidential information that
has been given to the e-
commerce firm because of
trust. To be accessed by
mainly the e-commerce
website or administrator and
the database administrator.
Table 3: Application Assets
Application Security Trust Level
Trust levels represent the access rights the application will grant to the application users.
The trust level cut across the different entry points and assets and who can manipulate
different data in the application. The trust level will categorise the trust of users in very
high, low and medium access rights or privileges required at each entry point or to
interact the different assets. Trust levels will be documented in the threat model as
follows:
ID - A unique number is assigned to each trust level. This is used to cross
reference the trust level with the entry points and assets.
Name of users - A descriptive name that shows the different internal and external
users that should be granted a trust level.
Category of users - A description of the trust level granted to some typical users
of the application.
ID Name of users Category of users
1 Anonymous user Low trust
2 Customer with valid login credentials High trust
3 Customer with invalid login credentials Medium trust
4 Staff with valid login credentials High trust
5 Supplier with invalid logging credentials Low trust
6 Supplier with valid logging credentials High trust
7 Database server administrator with valid login
credentials
High trust
update data
asset of the customers,
suppliers, and staff being
updating on the e-commerce
application
because there is highly
confidential information that
has been given to the e-
commerce firm because of
trust. To be accessed by
mainly the e-commerce
website or administrator and
the database administrator.
Table 3: Application Assets
Application Security Trust Level
Trust levels represent the access rights the application will grant to the application users.
The trust level cut across the different entry points and assets and who can manipulate
different data in the application. The trust level will categorise the trust of users in very
high, low and medium access rights or privileges required at each entry point or to
interact the different assets. Trust levels will be documented in the threat model as
follows:
ID - A unique number is assigned to each trust level. This is used to cross
reference the trust level with the entry points and assets.
Name of users - A descriptive name that shows the different internal and external
users that should be granted a trust level.
Category of users - A description of the trust level granted to some typical users
of the application.
ID Name of users Category of users
1 Anonymous user Low trust
2 Customer with valid login credentials High trust
3 Customer with invalid login credentials Medium trust
4 Staff with valid login credentials High trust
5 Supplier with invalid logging credentials Low trust
6 Supplier with valid logging credentials High trust
7 Database server administrator with valid login
credentials
High trust

8 Web server administrator with valid login. High trust
Table 4: Application Security Trust Level
Application Security Data Flow Diagram
All the information collected will be used to accurately model the application with a data
flow diagram. The DFD will help security analysis of the application to main better
understanding of the application by providing a better understanding of the application by
providing a visual representation of how the application processes its data. The DFD will
be used to focus on how the data send to the application moves through it and what
happens as it moves. The DFD will be made in a hierarchical structure, thus will be
decomposed in a subsystem and lower-lever subsystem to allow a clear focus on the
specific involvement of the e-commerce application.
Table 4: Application Security Trust Level
Application Security Data Flow Diagram
All the information collected will be used to accurately model the application with a data
flow diagram. The DFD will help security analysis of the application to main better
understanding of the application by providing a better understanding of the application by
providing a visual representation of how the application processes its data. The DFD will
be used to focus on how the data send to the application moves through it and what
happens as it moves. The DFD will be made in a hierarchical structure, thus will be
decomposed in a subsystem and lower-lever subsystem to allow a clear focus on the
specific involvement of the e-commerce application.
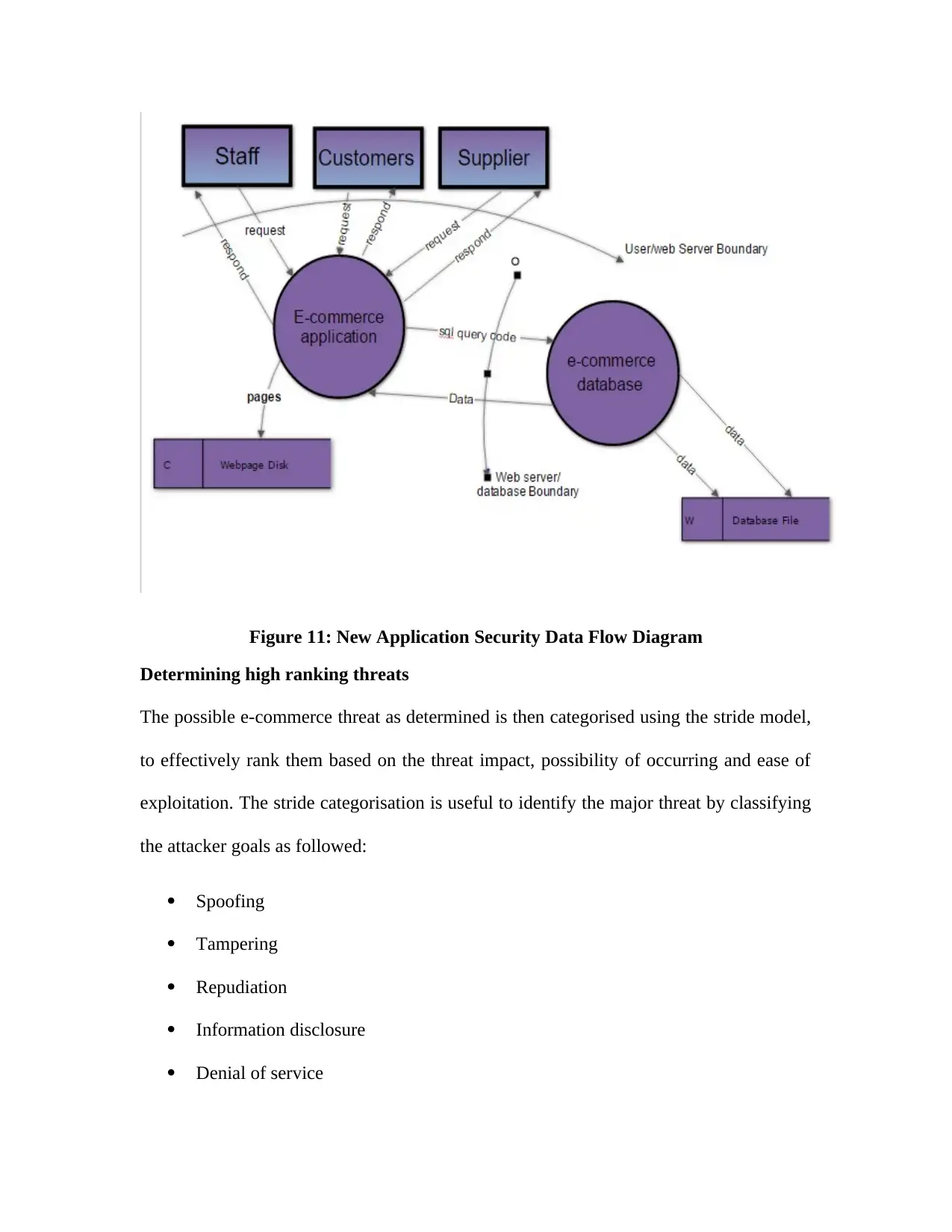
Figure 11: New Application Security Data Flow Diagram
Determining high ranking threats
The possible e-commerce threat as determined is then categorised using the stride model,
to effectively rank them based on the threat impact, possibility of occurring and ease of
exploitation. The stride categorisation is useful to identify the major threat by classifying
the attacker goals as followed:
Spoofing
Tampering
Repudiation
Information disclosure
Denial of service
Determining high ranking threats
The possible e-commerce threat as determined is then categorised using the stride model,
to effectively rank them based on the threat impact, possibility of occurring and ease of
exploitation. The stride categorisation is useful to identify the major threat by classifying
the attacker goals as followed:
Spoofing
Tampering
Repudiation
Information disclosure
Denial of service
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
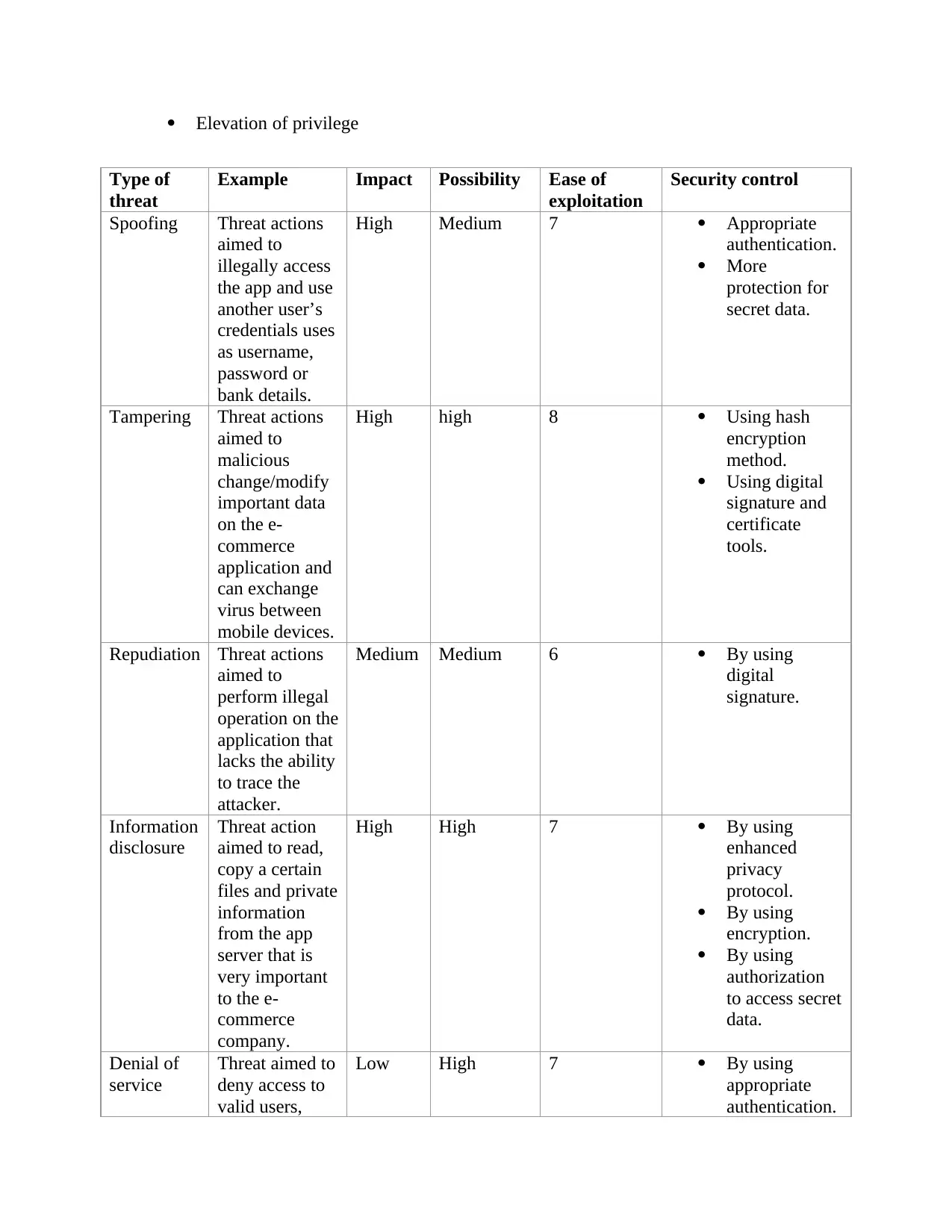
Elevation of privilege
Type of
threat
Example Impact Possibility Ease of
exploitation
Security control
Spoofing Threat actions
aimed to
illegally access
the app and use
another user’s
credentials uses
as username,
password or
bank details.
High Medium 7 Appropriate
authentication.
More
protection for
secret data.
Tampering Threat actions
aimed to
malicious
change/modify
important data
on the e-
commerce
application and
can exchange
virus between
mobile devices.
High high 8 Using hash
encryption
method.
Using digital
signature and
certificate
tools.
Repudiation Threat actions
aimed to
perform illegal
operation on the
application that
lacks the ability
to trace the
attacker.
Medium Medium 6 By using
digital
signature.
Information
disclosure
Threat action
aimed to read,
copy a certain
files and private
information
from the app
server that is
very important
to the e-
commerce
company.
High High 7 By using
enhanced
privacy
protocol.
By using
encryption.
By using
authorization
to access secret
data.
Denial of
service
Threat aimed to
deny access to
valid users,
Low High 7 By using
appropriate
authentication.
Type of
threat
Example Impact Possibility Ease of
exploitation
Security control
Spoofing Threat actions
aimed to
illegally access
the app and use
another user’s
credentials uses
as username,
password or
bank details.
High Medium 7 Appropriate
authentication.
More
protection for
secret data.
Tampering Threat actions
aimed to
malicious
change/modify
important data
on the e-
commerce
application and
can exchange
virus between
mobile devices.
High high 8 Using hash
encryption
method.
Using digital
signature and
certificate
tools.
Repudiation Threat actions
aimed to
perform illegal
operation on the
application that
lacks the ability
to trace the
attacker.
Medium Medium 6 By using
digital
signature.
Information
disclosure
Threat action
aimed to read,
copy a certain
files and private
information
from the app
server that is
very important
to the e-
commerce
company.
High High 7 By using
enhanced
privacy
protocol.
By using
encryption.
By using
authorization
to access secret
data.
Denial of
service
Threat aimed to
deny access to
valid users,
Low High 7 By using
appropriate
authentication.
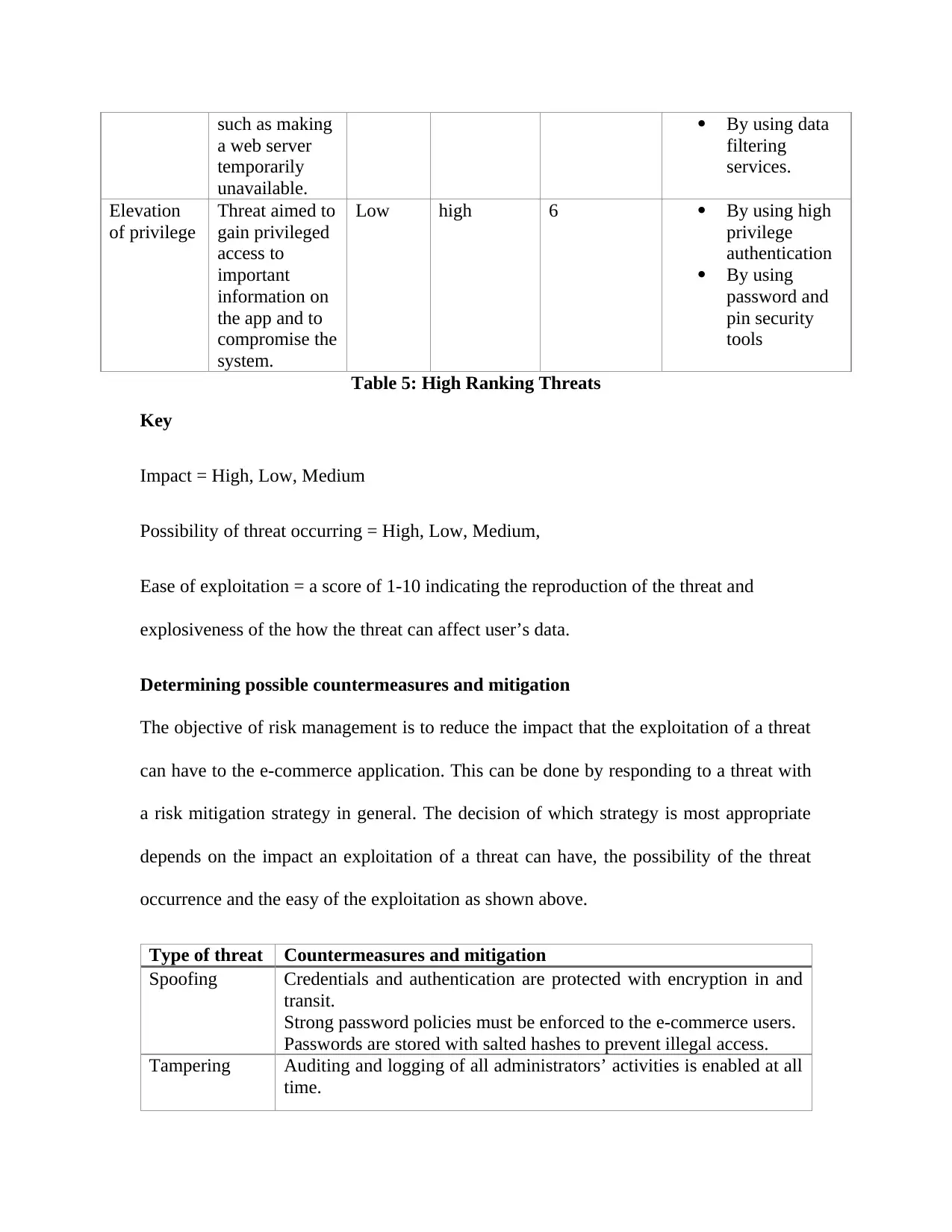
such as making
a web server
temporarily
unavailable.
By using data
filtering
services.
Elevation
of privilege
Threat aimed to
gain privileged
access to
important
information on
the app and to
compromise the
system.
Low high 6 By using high
privilege
authentication
By using
password and
pin security
tools
Table 5: High Ranking Threats
Key
Impact = High, Low, Medium
Possibility of threat occurring = High, Low, Medium,
Ease of exploitation = a score of 1-10 indicating the reproduction of the threat and
explosiveness of the how the threat can affect user’s data.
Determining possible countermeasures and mitigation
The objective of risk management is to reduce the impact that the exploitation of a threat
can have to the e-commerce application. This can be done by responding to a threat with
a risk mitigation strategy in general. The decision of which strategy is most appropriate
depends on the impact an exploitation of a threat can have, the possibility of the threat
occurrence and the easy of the exploitation as shown above.
Type of threat Countermeasures and mitigation
Spoofing Credentials and authentication are protected with encryption in and
transit.
Strong password policies must be enforced to the e-commerce users.
Passwords are stored with salted hashes to prevent illegal access.
Tampering Auditing and logging of all administrators’ activities is enabled at all
time.
a web server
temporarily
unavailable.
By using data
filtering
services.
Elevation
of privilege
Threat aimed to
gain privileged
access to
important
information on
the app and to
compromise the
system.
Low high 6 By using high
privilege
authentication
By using
password and
pin security
tools
Table 5: High Ranking Threats
Key
Impact = High, Low, Medium
Possibility of threat occurring = High, Low, Medium,
Ease of exploitation = a score of 1-10 indicating the reproduction of the threat and
explosiveness of the how the threat can affect user’s data.
Determining possible countermeasures and mitigation
The objective of risk management is to reduce the impact that the exploitation of a threat
can have to the e-commerce application. This can be done by responding to a threat with
a risk mitigation strategy in general. The decision of which strategy is most appropriate
depends on the impact an exploitation of a threat can have, the possibility of the threat
occurrence and the easy of the exploitation as shown above.
Type of threat Countermeasures and mitigation
Spoofing Credentials and authentication are protected with encryption in and
transit.
Strong password policies must be enforced to the e-commerce users.
Passwords are stored with salted hashes to prevent illegal access.
Tampering Auditing and logging of all administrators’ activities is enabled at all
time.
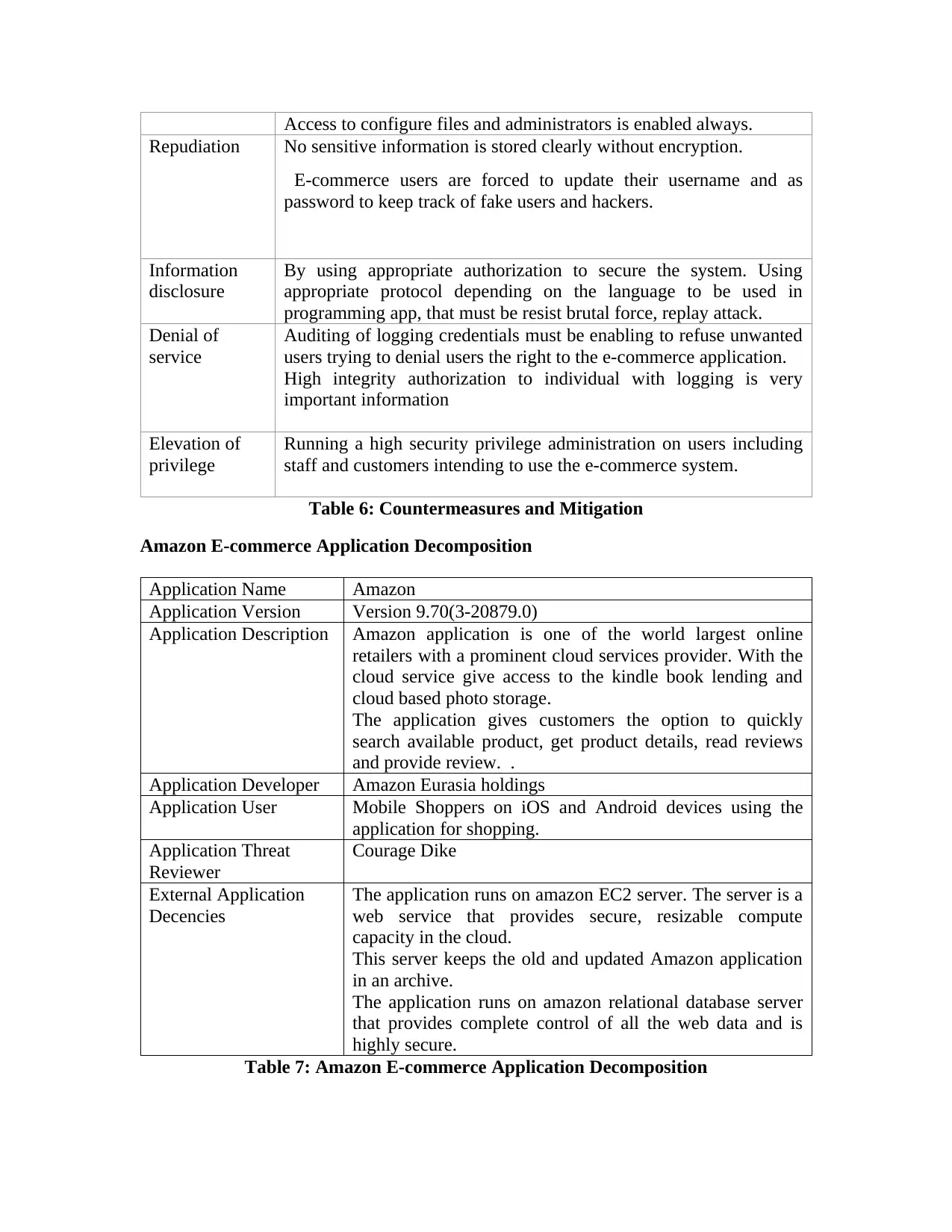
Access to configure files and administrators is enabled always.
Repudiation No sensitive information is stored clearly without encryption.
E-commerce users are forced to update their username and as
password to keep track of fake users and hackers.
Information
disclosure
By using appropriate authorization to secure the system. Using
appropriate protocol depending on the language to be used in
programming app, that must be resist brutal force, replay attack.
Denial of
service
Auditing of logging credentials must be enabling to refuse unwanted
users trying to denial users the right to the e-commerce application.
High integrity authorization to individual with logging is very
important information
Elevation of
privilege
Running a high security privilege administration on users including
staff and customers intending to use the e-commerce system.
Table 6: Countermeasures and Mitigation
Amazon E-commerce Application Decomposition
Application Name Amazon
Application Version Version 9.70(3-20879.0)
Application Description Amazon application is one of the world largest online
retailers with a prominent cloud services provider. With the
cloud service give access to the kindle book lending and
cloud based photo storage.
The application gives customers the option to quickly
search available product, get product details, read reviews
and provide review. .
Application Developer Amazon Eurasia holdings
Application User Mobile Shoppers on iOS and Android devices using the
application for shopping.
Application Threat
Reviewer
Courage Dike
External Application
Decencies
The application runs on amazon EC2 server. The server is a
web service that provides secure, resizable compute
capacity in the cloud.
This server keeps the old and updated Amazon application
in an archive.
The application runs on amazon relational database server
that provides complete control of all the web data and is
highly secure.
Table 7: Amazon E-commerce Application Decomposition
Repudiation No sensitive information is stored clearly without encryption.
E-commerce users are forced to update their username and as
password to keep track of fake users and hackers.
Information
disclosure
By using appropriate authorization to secure the system. Using
appropriate protocol depending on the language to be used in
programming app, that must be resist brutal force, replay attack.
Denial of
service
Auditing of logging credentials must be enabling to refuse unwanted
users trying to denial users the right to the e-commerce application.
High integrity authorization to individual with logging is very
important information
Elevation of
privilege
Running a high security privilege administration on users including
staff and customers intending to use the e-commerce system.
Table 6: Countermeasures and Mitigation
Amazon E-commerce Application Decomposition
Application Name Amazon
Application Version Version 9.70(3-20879.0)
Application Description Amazon application is one of the world largest online
retailers with a prominent cloud services provider. With the
cloud service give access to the kindle book lending and
cloud based photo storage.
The application gives customers the option to quickly
search available product, get product details, read reviews
and provide review. .
Application Developer Amazon Eurasia holdings
Application User Mobile Shoppers on iOS and Android devices using the
application for shopping.
Application Threat
Reviewer
Courage Dike
External Application
Decencies
The application runs on amazon EC2 server. The server is a
web service that provides secure, resizable compute
capacity in the cloud.
This server keeps the old and updated Amazon application
in an archive.
The application runs on amazon relational database server
that provides complete control of all the web data and is
highly secure.
Table 7: Amazon E-commerce Application Decomposition
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
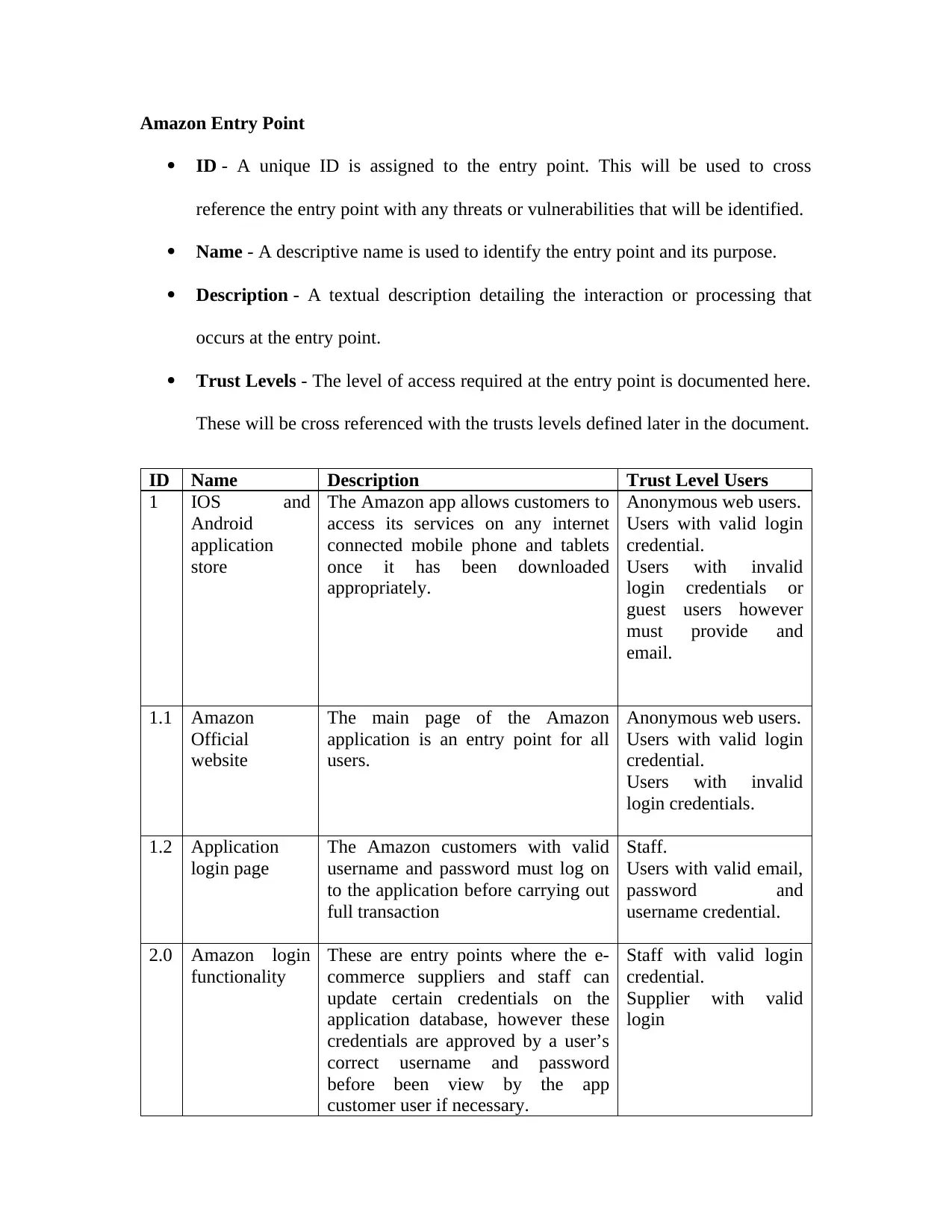
Amazon Entry Point
ID - A unique ID is assigned to the entry point. This will be used to cross
reference the entry point with any threats or vulnerabilities that will be identified.
Name - A descriptive name is used to identify the entry point and its purpose.
Description - A textual description detailing the interaction or processing that
occurs at the entry point.
Trust Levels - The level of access required at the entry point is documented here.
These will be cross referenced with the trusts levels defined later in the document.
ID Name Description Trust Level Users
1 IOS and
Android
application
store
The Amazon app allows customers to
access its services on any internet
connected mobile phone and tablets
once it has been downloaded
appropriately.
Anonymous web users.
Users with valid login
credential.
Users with invalid
login credentials or
guest users however
must provide and
email.
1.1 Amazon
Official
website
The main page of the Amazon
application is an entry point for all
users.
Anonymous web users.
Users with valid login
credential.
Users with invalid
login credentials.
1.2 Application
login page
The Amazon customers with valid
username and password must log on
to the application before carrying out
full transaction
Staff.
Users with valid email,
password and
username credential.
2.0 Amazon login
functionality
These are entry points where the e-
commerce suppliers and staff can
update certain credentials on the
application database, however these
credentials are approved by a user’s
correct username and password
before been view by the app
customer user if necessary.
Staff with valid login
credential.
Supplier with valid
login
ID - A unique ID is assigned to the entry point. This will be used to cross
reference the entry point with any threats or vulnerabilities that will be identified.
Name - A descriptive name is used to identify the entry point and its purpose.
Description - A textual description detailing the interaction or processing that
occurs at the entry point.
Trust Levels - The level of access required at the entry point is documented here.
These will be cross referenced with the trusts levels defined later in the document.
ID Name Description Trust Level Users
1 IOS and
Android
application
store
The Amazon app allows customers to
access its services on any internet
connected mobile phone and tablets
once it has been downloaded
appropriately.
Anonymous web users.
Users with valid login
credential.
Users with invalid
login credentials or
guest users however
must provide and
email.
1.1 Amazon
Official
website
The main page of the Amazon
application is an entry point for all
users.
Anonymous web users.
Users with valid login
credential.
Users with invalid
login credentials.
1.2 Application
login page
The Amazon customers with valid
username and password must log on
to the application before carrying out
full transaction
Staff.
Users with valid email,
password and
username credential.
2.0 Amazon login
functionality
These are entry points where the e-
commerce suppliers and staff can
update certain credentials on the
application database, however these
credentials are approved by a user’s
correct username and password
before been view by the app
customer user if necessary.
Staff with valid login
credential.
Supplier with valid
login
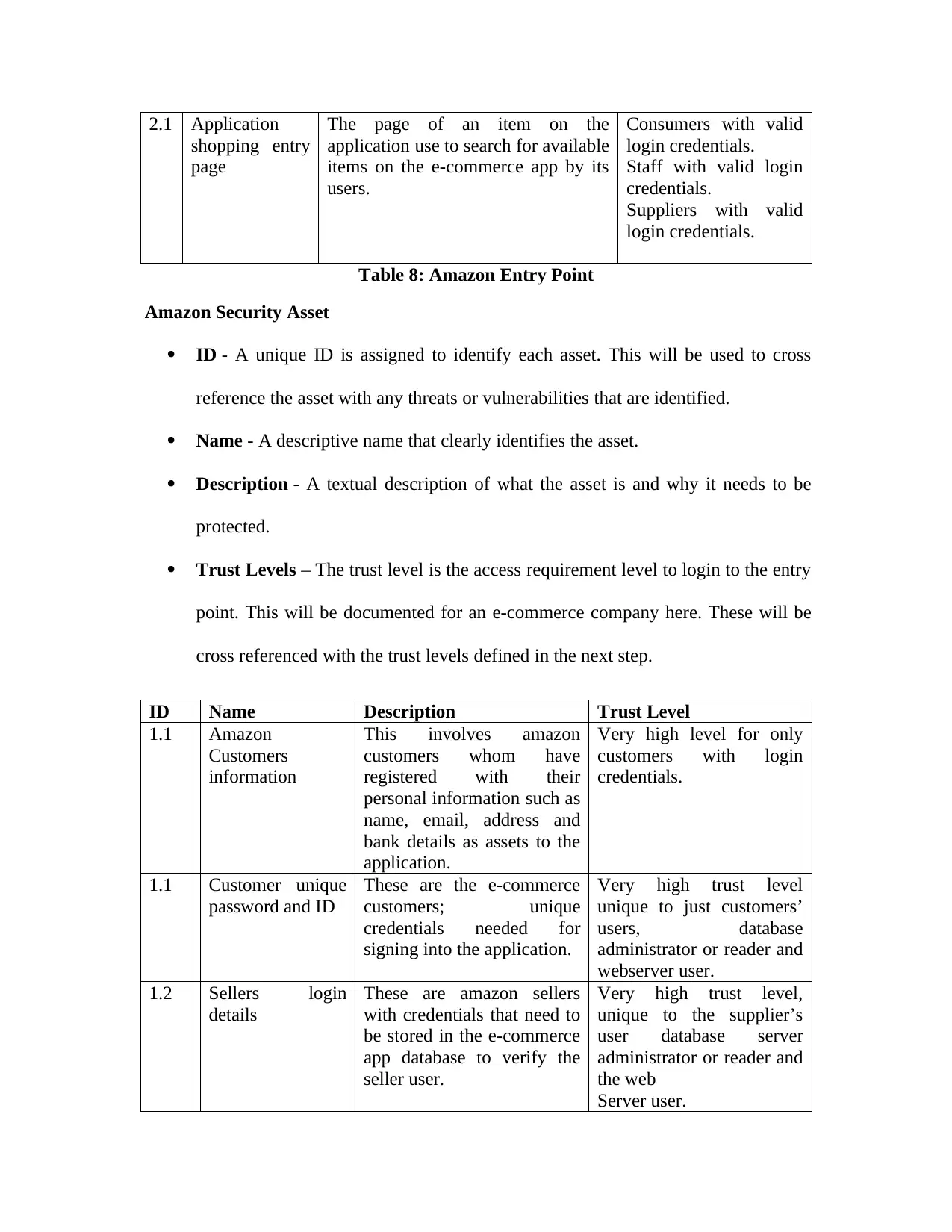
2.1 Application
shopping entry
page
The page of an item on the
application use to search for available
items on the e-commerce app by its
users.
Consumers with valid
login credentials.
Staff with valid login
credentials.
Suppliers with valid
login credentials.
Table 8: Amazon Entry Point
Amazon Security Asset
ID - A unique ID is assigned to identify each asset. This will be used to cross
reference the asset with any threats or vulnerabilities that are identified.
Name - A descriptive name that clearly identifies the asset.
Description - A textual description of what the asset is and why it needs to be
protected.
Trust Levels – The trust level is the access requirement level to login to the entry
point. This will be documented for an e-commerce company here. These will be
cross referenced with the trust levels defined in the next step.
ID Name Description Trust Level
1.1 Amazon
Customers
information
This involves amazon
customers whom have
registered with their
personal information such as
name, email, address and
bank details as assets to the
application.
Very high level for only
customers with login
credentials.
1.1 Customer unique
password and ID
These are the e-commerce
customers; unique
credentials needed for
signing into the application.
Very high trust level
unique to just customers’
users, database
administrator or reader and
webserver user.
1.2 Sellers login
details
These are amazon sellers
with credentials that need to
be stored in the e-commerce
app database to verify the
seller user.
Very high trust level,
unique to the supplier’s
user database server
administrator or reader and
the web
Server user.
shopping entry
page
The page of an item on the
application use to search for available
items on the e-commerce app by its
users.
Consumers with valid
login credentials.
Staff with valid login
credentials.
Suppliers with valid
login credentials.
Table 8: Amazon Entry Point
Amazon Security Asset
ID - A unique ID is assigned to identify each asset. This will be used to cross
reference the asset with any threats or vulnerabilities that are identified.
Name - A descriptive name that clearly identifies the asset.
Description - A textual description of what the asset is and why it needs to be
protected.
Trust Levels – The trust level is the access requirement level to login to the entry
point. This will be documented for an e-commerce company here. These will be
cross referenced with the trust levels defined in the next step.
ID Name Description Trust Level
1.1 Amazon
Customers
information
This involves amazon
customers whom have
registered with their
personal information such as
name, email, address and
bank details as assets to the
application.
Very high level for only
customers with login
credentials.
1.1 Customer unique
password and ID
These are the e-commerce
customers; unique
credentials needed for
signing into the application.
Very high trust level
unique to just customers’
users, database
administrator or reader and
webserver user.
1.2 Sellers login
details
These are amazon sellers
with credentials that need to
be stored in the e-commerce
app database to verify the
seller user.
Very high trust level,
unique to the supplier’s
user database server
administrator or reader and
the web
Server user.
1.3 Technology
officers with valid
login credentials
These are the technological
officers of amazon located at
different amazon warehouse
and with valid logging to
amazon app database
Very high trust level,
unique to different
technological officers
using the database and
server to access and read
various file.
1.4 Web server
administrator with
valid login
These are web server
administrators located at
amazon server location in
various countries with valid
logging to amazon app
database.
Very high trust level,
unique to different web
server administrator
updating the server to
allow regular transmission
of real time information.
1.5 Administrative
Directors with
valid login
These are the various
amazon administrative
directors in different country
that runs the day to day
activity of the location
Very high trust level,
unique to different
administrative directors.
1.6 Software
maintainer with
valid login
These are the various
amazon software
maintainers with valid
logging and critical
information of amazon need
for the amazon app to work
effectively.
Very high trust level,
unique to different
software maintainer
allowed to maintain
various amazon soft
systems.
1.7 Human resource
with valid login
These are the various
amazon human resources
with valid logging. They
have access to the pass and
current employee at amazon
this must be kept securely.
Very high trust level,
unique to different human
resource staff with unique
access to update all
employee records and
personal information.
1.8 Financial operator
with valid login
These are the various the
financial operative with the
job of keeping track of
customer’s receipt n paying
sellers as well as staff.
Very high trust level,
unique to different human
resource staff with unique
access to update all
employee records and
personal information.
1.9 Company legal
and private
trademark
documents.
These assets must do with
the legal documents of the e-
commerce which doesn’t
have to be shared publicly.
Very high trust level
unique to certain staff with
authorisation to access
these fills.
2 System `Assets
2.0 The app executive
code
This is the amazon
implemented application
code, which is not to be
open source as it is a legal
document of the company.
Medium trust level.
officers with valid
login credentials
These are the technological
officers of amazon located at
different amazon warehouse
and with valid logging to
amazon app database
Very high trust level,
unique to different
technological officers
using the database and
server to access and read
various file.
1.4 Web server
administrator with
valid login
These are web server
administrators located at
amazon server location in
various countries with valid
logging to amazon app
database.
Very high trust level,
unique to different web
server administrator
updating the server to
allow regular transmission
of real time information.
1.5 Administrative
Directors with
valid login
These are the various
amazon administrative
directors in different country
that runs the day to day
activity of the location
Very high trust level,
unique to different
administrative directors.
1.6 Software
maintainer with
valid login
These are the various
amazon software
maintainers with valid
logging and critical
information of amazon need
for the amazon app to work
effectively.
Very high trust level,
unique to different
software maintainer
allowed to maintain
various amazon soft
systems.
1.7 Human resource
with valid login
These are the various
amazon human resources
with valid logging. They
have access to the pass and
current employee at amazon
this must be kept securely.
Very high trust level,
unique to different human
resource staff with unique
access to update all
employee records and
personal information.
1.8 Financial operator
with valid login
These are the various the
financial operative with the
job of keeping track of
customer’s receipt n paying
sellers as well as staff.
Very high trust level,
unique to different human
resource staff with unique
access to update all
employee records and
personal information.
1.9 Company legal
and private
trademark
documents.
These assets must do with
the legal documents of the e-
commerce which doesn’t
have to be shared publicly.
Very high trust level
unique to certain staff with
authorisation to access
these fills.
2 System `Assets
2.0 The app executive
code
This is the amazon
implemented application
code, which is not to be
open source as it is a legal
document of the company.
Medium trust level.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
2.1 The amazon
relational
database
This is a major asset of the
e-commerce application that
stores data, retrieve then and
delete when necessary.
Medium trust level.
2.1 The access to
modify or update
data at
These are new information
asset of the customers,
suppliers, and staff being
updating on the e-commerce
application
Very high trust level,
because there is highly
confidential information
stored by amazon.
Table 9: Amazon Security Asset
Amazon Security Trust level
ID - A unique number is assigned to each trust level. This is used to cross
reference the trust level with the entry points and assets.
Name of users - A descriptive name that shows the different internal and external
users that should be granted a trust level.
Category of users - A description of the trust level granted to some typical users
of the application.
ID Name of users Category of users
1 A guest user Low trust
2 Customer with valid login credentials High trust
3 Amazon sellers with invalid logging credentials Low trust
4 Amazon sellers with valid logging credentials High trust
5 Technology officers with valid login credentials High trust
6 Web server administrator with valid login High trust
7 Director administrative with valid login High trust
8 Software maintainer with valid login High trust
9 Human resource with valid login High trust
10 Financial operator with valid login High trust
relational
database
This is a major asset of the
e-commerce application that
stores data, retrieve then and
delete when necessary.
Medium trust level.
2.1 The access to
modify or update
data at
These are new information
asset of the customers,
suppliers, and staff being
updating on the e-commerce
application
Very high trust level,
because there is highly
confidential information
stored by amazon.
Table 9: Amazon Security Asset
Amazon Security Trust level
ID - A unique number is assigned to each trust level. This is used to cross
reference the trust level with the entry points and assets.
Name of users - A descriptive name that shows the different internal and external
users that should be granted a trust level.
Category of users - A description of the trust level granted to some typical users
of the application.
ID Name of users Category of users
1 A guest user Low trust
2 Customer with valid login credentials High trust
3 Amazon sellers with invalid logging credentials Low trust
4 Amazon sellers with valid logging credentials High trust
5 Technology officers with valid login credentials High trust
6 Web server administrator with valid login High trust
7 Director administrative with valid login High trust
8 Software maintainer with valid login High trust
9 Human resource with valid login High trust
10 Financial operator with valid login High trust
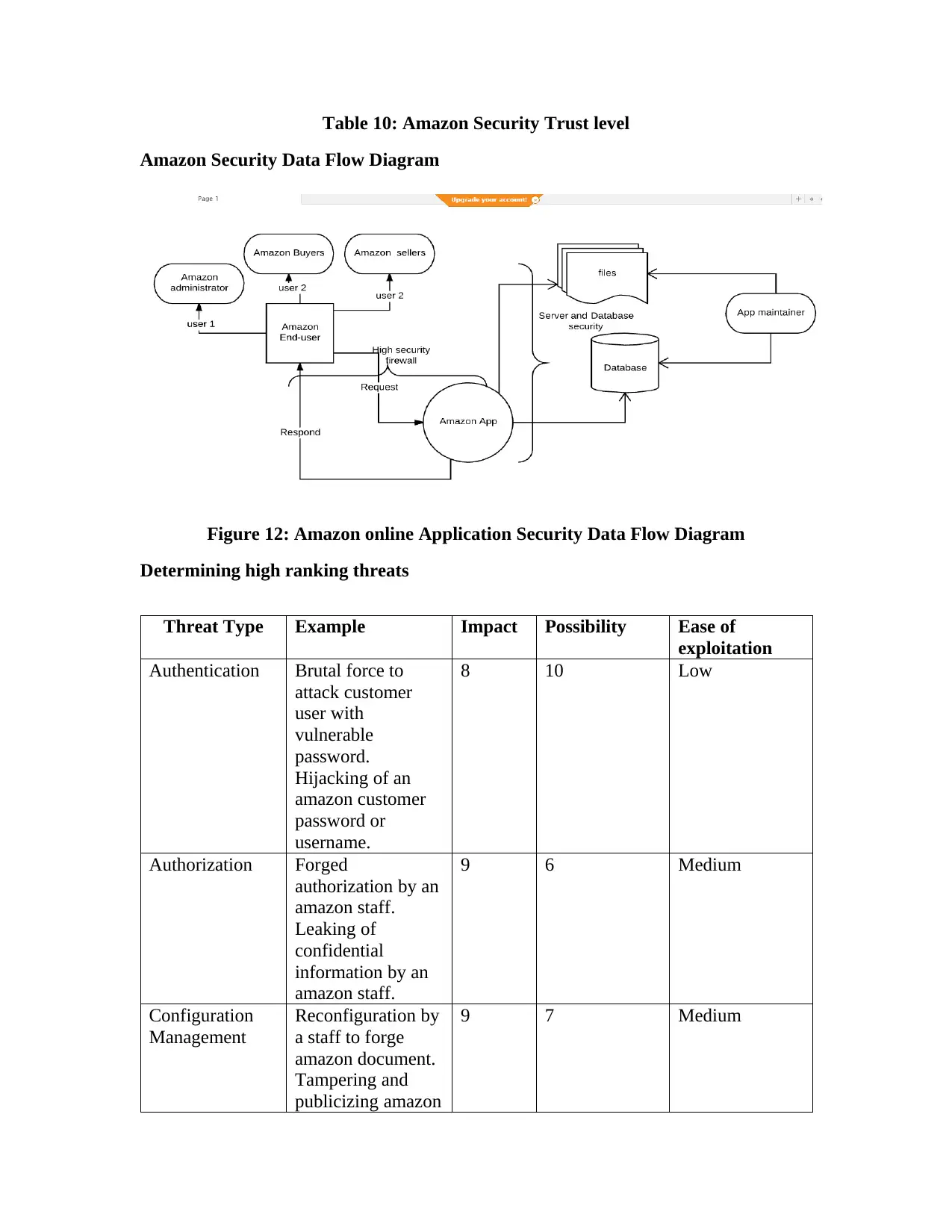
Table 10: Amazon Security Trust level
Amazon Security Data Flow Diagram
Figure 12: Amazon online Application Security Data Flow Diagram
Determining high ranking threats
Threat Type Example Impact Possibility Ease of
exploitation
Authentication Brutal force to
attack customer
user with
vulnerable
password.
Hijacking of an
amazon customer
password or
username.
8 10 Low
Authorization Forged
authorization by an
amazon staff.
Leaking of
confidential
information by an
amazon staff.
9 6 Medium
Configuration
Management
Reconfiguration by
a staff to forge
amazon document.
Tampering and
publicizing amazon
9 7 Medium
Amazon Security Data Flow Diagram
Figure 12: Amazon online Application Security Data Flow Diagram
Determining high ranking threats
Threat Type Example Impact Possibility Ease of
exploitation
Authentication Brutal force to
attack customer
user with
vulnerable
password.
Hijacking of an
amazon customer
password or
username.
8 10 Low
Authorization Forged
authorization by an
amazon staff.
Leaking of
confidential
information by an
amazon staff.
9 6 Medium
Configuration
Management
Reconfiguration by
a staff to forge
amazon document.
Tampering and
publicizing amazon
9 7 Medium
confidential
information.
Data Protection
in Storage and
Transit
Hacking of amazon
local server and
database.
Illegally decrypting
of amazon
encrypted files to
steal documents.
10 7 High
Data Validation /
Parameter
Validation
Exchanging of
security corrupt
files between
amazon staff and
its app users.
Amazon app not
coded on the right
platform.
8 5 Medium
Error Handling
and Exception
Management
Amazon handling
error message with
care so as to avoid
getting into the
wrong hand.
5 5 Low
User and Session
Management
Amazon cookies
inappropriately.
Amazon avoiding
to store sensitive
information in clear
text.
5 7 Medium
Auditing and
Logging
Amazon app
auditing not given
to trust worthy
individuals.
Amazon app
configured to
accept fake users
and avoid integrity
control.
10 8 Low
Table 11: High Ranking Threats
Key
Impact = High, Low, Medium
information.
Data Protection
in Storage and
Transit
Hacking of amazon
local server and
database.
Illegally decrypting
of amazon
encrypted files to
steal documents.
10 7 High
Data Validation /
Parameter
Validation
Exchanging of
security corrupt
files between
amazon staff and
its app users.
Amazon app not
coded on the right
platform.
8 5 Medium
Error Handling
and Exception
Management
Amazon handling
error message with
care so as to avoid
getting into the
wrong hand.
5 5 Low
User and Session
Management
Amazon cookies
inappropriately.
Amazon avoiding
to store sensitive
information in clear
text.
5 7 Medium
Auditing and
Logging
Amazon app
auditing not given
to trust worthy
individuals.
Amazon app
configured to
accept fake users
and avoid integrity
control.
10 8 Low
Table 11: High Ranking Threats
Key
Impact = High, Low, Medium
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
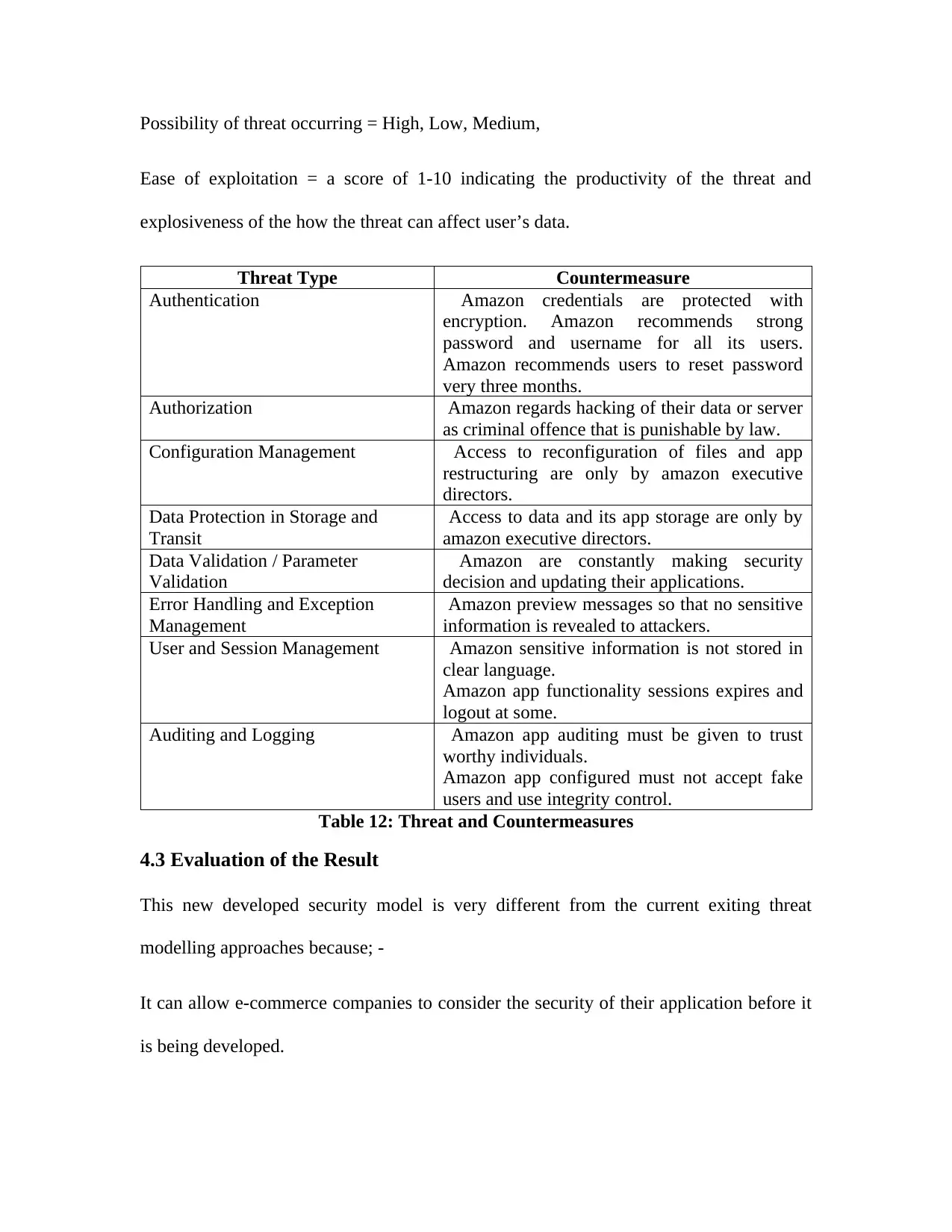
Possibility of threat occurring = High, Low, Medium,
Ease of exploitation = a score of 1-10 indicating the productivity of the threat and
explosiveness of the how the threat can affect user’s data.
Threat Type Countermeasure
Authentication Amazon credentials are protected with
encryption. Amazon recommends strong
password and username for all its users.
Amazon recommends users to reset password
very three months.
Authorization Amazon regards hacking of their data or server
as criminal offence that is punishable by law.
Configuration Management Access to reconfiguration of files and app
restructuring are only by amazon executive
directors.
Data Protection in Storage and
Transit
Access to data and its app storage are only by
amazon executive directors.
Data Validation / Parameter
Validation
Amazon are constantly making security
decision and updating their applications.
Error Handling and Exception
Management
Amazon preview messages so that no sensitive
information is revealed to attackers.
User and Session Management Amazon sensitive information is not stored in
clear language.
Amazon app functionality sessions expires and
logout at some.
Auditing and Logging Amazon app auditing must be given to trust
worthy individuals.
Amazon app configured must not accept fake
users and use integrity control.
Table 12: Threat and Countermeasures
4.3 Evaluation of the Result
This new developed security model is very different from the current exiting threat
modelling approaches because; -
It can allow e-commerce companies to consider the security of their application before it
is being developed.
Ease of exploitation = a score of 1-10 indicating the productivity of the threat and
explosiveness of the how the threat can affect user’s data.
Threat Type Countermeasure
Authentication Amazon credentials are protected with
encryption. Amazon recommends strong
password and username for all its users.
Amazon recommends users to reset password
very three months.
Authorization Amazon regards hacking of their data or server
as criminal offence that is punishable by law.
Configuration Management Access to reconfiguration of files and app
restructuring are only by amazon executive
directors.
Data Protection in Storage and
Transit
Access to data and its app storage are only by
amazon executive directors.
Data Validation / Parameter
Validation
Amazon are constantly making security
decision and updating their applications.
Error Handling and Exception
Management
Amazon preview messages so that no sensitive
information is revealed to attackers.
User and Session Management Amazon sensitive information is not stored in
clear language.
Amazon app functionality sessions expires and
logout at some.
Auditing and Logging Amazon app auditing must be given to trust
worthy individuals.
Amazon app configured must not accept fake
users and use integrity control.
Table 12: Threat and Countermeasures
4.3 Evaluation of the Result
This new developed security model is very different from the current exiting threat
modelling approaches because; -
It can allow e-commerce companies to consider the security of their application before it
is being developed.

It allows e-commerce web developers and designers consider security before developing
and design an application.
This new security threat model contains a website that helps users download their
security challenges in form of a pdf as it is being documented. This is to help security
analyst refer to the documentation when needed.
This new security threat modelling approaches is structured to help developers document
their major challenges effectively and applied the most suitable counter measures.
This new security threating modelling showcased how password, encryption other
security tools can be used to facilitate effective e-commerce security. Based on the
feedback got from the interview alongside the aim initially proposed in the proposal
project version, these feedback and objective was met.
Chapter 6: Summary and Conclusion
6.1 Summary
The entire study above has been focused to find out the security vulnerability that is
found in online services that can cause the most security issues in the e-commerce
platforms. The study shows how the security vulnerabilities in the cyber world can be a
threat to the e-commerce website, which in turn causes problems to the proprietors of the
e-commerce websites, the authority and the customers of the website as an extension. The
study was initiated because there have been some reports about security threats and
attacks that have been found in the previous times and it has also alarmed the authorities
of the e-commerce and digitized business to follow up the vulnerabilities in their websites
and run a full analysis of the business to find out any risk factor and eradicate them
and design an application.
This new security threat model contains a website that helps users download their
security challenges in form of a pdf as it is being documented. This is to help security
analyst refer to the documentation when needed.
This new security threat modelling approaches is structured to help developers document
their major challenges effectively and applied the most suitable counter measures.
This new security threating modelling showcased how password, encryption other
security tools can be used to facilitate effective e-commerce security. Based on the
feedback got from the interview alongside the aim initially proposed in the proposal
project version, these feedback and objective was met.
Chapter 6: Summary and Conclusion
6.1 Summary
The entire study above has been focused to find out the security vulnerability that is
found in online services that can cause the most security issues in the e-commerce
platforms. The study shows how the security vulnerabilities in the cyber world can be a
threat to the e-commerce website, which in turn causes problems to the proprietors of the
e-commerce websites, the authority and the customers of the website as an extension. The
study was initiated because there have been some reports about security threats and
attacks that have been found in the previous times and it has also alarmed the authorities
of the e-commerce and digitized business to follow up the vulnerabilities in their websites
and run a full analysis of the business to find out any risk factor and eradicate them

completely with the most effective solutions implemented. Not just the security
vulnerabilities, but there have also been ransomware attacks that have harmed the cyber
activities of the customers of these digitized organizations. In addition to that, it has also
been found that these ransomware attacks and the way by which they occur are spreading
rapidly, causing the potential customers of the business to opt out of considering them as
a feasible way of shopping. The attacks have not only spread from one customer to
another but have also attacked one business after another. This is why this particular
study was developed to find out the particular feedback taken from the companies and
running a security analysis on a chosen platform and find a feasible way of providing a
solution to the problems through collection of data through primary and secondary
sources and developing effective theories from them.
For this study especially, the software security tools are also analysed proactively to
make sure how they can be utilized to find a solution to the security threats. The study
has effectively utilized various forms of security tools in this regards, right from the
primitive forms of the utilized security tools for the approach to the recent developed
tools. With the analysis of the security tools and the security threats analysed at the
similar way makes it easier to understand the ways by which all the security threats have
been addressed at the e-commerce websites. Having said that, the research is developed
to find out an appropriate methodology that would be able to find out and formulate a
theoretical approach to further develop a methodology in applying the threat modelling
techniques. This threat modelling technique would formulate the utilization of the
analytical tools and the utility of the developed methodology put together and in this way
the solution would be formalised to find out a proper methodology for the website to
vulnerabilities, but there have also been ransomware attacks that have harmed the cyber
activities of the customers of these digitized organizations. In addition to that, it has also
been found that these ransomware attacks and the way by which they occur are spreading
rapidly, causing the potential customers of the business to opt out of considering them as
a feasible way of shopping. The attacks have not only spread from one customer to
another but have also attacked one business after another. This is why this particular
study was developed to find out the particular feedback taken from the companies and
running a security analysis on a chosen platform and find a feasible way of providing a
solution to the problems through collection of data through primary and secondary
sources and developing effective theories from them.
For this study especially, the software security tools are also analysed proactively to
make sure how they can be utilized to find a solution to the security threats. The study
has effectively utilized various forms of security tools in this regards, right from the
primitive forms of the utilized security tools for the approach to the recent developed
tools. With the analysis of the security tools and the security threats analysed at the
similar way makes it easier to understand the ways by which all the security threats have
been addressed at the e-commerce websites. Having said that, the research is developed
to find out an appropriate methodology that would be able to find out and formulate a
theoretical approach to further develop a methodology in applying the threat modelling
techniques. This threat modelling technique would formulate the utilization of the
analytical tools and the utility of the developed methodology put together and in this way
the solution would be formalised to find out a proper methodology for the website to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

make sure that the security vulnerabilities are met properly. The entire research has been
build up on finding out a proper way in developing and maintaining the website in such a
way that all these security vulnerabilities are eradicated from the system.
However, it has been found during the research that most of these threat modelling
techniques and analytical tools are among the practices utilized in the computer industry
to reduce the volume and severity of exploitable vulnerabilities to e-commerce software
applications. But most of these threat models are usually implement after the designed
and development of an e-commerce application which is not the best practice. Therefore,
the most probable version of utilizing this research was based upon the methodology of
SDLC or software development lifecycle technique. The research has found out that only
through the process of SDLC or software development lifecycle methods, a developer is
able to find out the proper way of application for the embedding of a dependable and
secure development of the website and imply it to the organization. While the SDLC
method is followed, the developer must include the embedded security within the design
to formulate an impermeable website development that allows security analyst and
developers to think proactively about the countermeasures to discover available threat
and avert future attack.
While the research process was formulated, it was necessary to generate a research
problem statement, which is usually a problem found in throughout the research work, or
mostly the problem that the research is trying to solve through the entire study. This
involves in formulating a way by which the problem statement is approached. In this
particular case, the problem statement has been identified as the traditional way in which
the website for e-commerce platforms are designed and developed. This is because, it has
build up on finding out a proper way in developing and maintaining the website in such a
way that all these security vulnerabilities are eradicated from the system.
However, it has been found during the research that most of these threat modelling
techniques and analytical tools are among the practices utilized in the computer industry
to reduce the volume and severity of exploitable vulnerabilities to e-commerce software
applications. But most of these threat models are usually implement after the designed
and development of an e-commerce application which is not the best practice. Therefore,
the most probable version of utilizing this research was based upon the methodology of
SDLC or software development lifecycle technique. The research has found out that only
through the process of SDLC or software development lifecycle methods, a developer is
able to find out the proper way of application for the embedding of a dependable and
secure development of the website and imply it to the organization. While the SDLC
method is followed, the developer must include the embedded security within the design
to formulate an impermeable website development that allows security analyst and
developers to think proactively about the countermeasures to discover available threat
and avert future attack.
While the research process was formulated, it was necessary to generate a research
problem statement, which is usually a problem found in throughout the research work, or
mostly the problem that the research is trying to solve through the entire study. This
involves in formulating a way by which the problem statement is approached. In this
particular case, the problem statement has been identified as the traditional way in which
the website for e-commerce platforms are designed and developed. This is because, it has

been found that through these traditional processes, there have been multiple barging into
the websites as there were security vulnerabilities found in the development process. The
outcome of the entire design and development was found to be faulty when it came to the
security system of the ecommerce applications. There were repeated reports of
ransomware attacks and other ways of manipulating or theft of information for which the
development process was to be blamed. This is why, the entire research has been
formulated to find out a feasible way in which the vulnerabilities can be identified and for
further development and design of the websites they can be avoided. Since, having
vulnerabilities in the e-commerce websites are not only causing problems to the
customers of the organization, but it is also becoming obligatory in framing up a good
reputation for the organization with the customers.
The next phase of the research was framed to find out the research aims and the research
objectives that needed to be identified before the research process was commenced
altogether. Therefore, the research was found to have a particular aim of investigating the
tools which have been utilized by the various software development system ever since it
has been implemented in software development. This would be required for the
investigation of the threat modelling for the successful design and development of the e-
commerce applications when they are available live to the customers online. The aim of
the research also pointed at the ways in which they have been done. This is due to the fact
that the reader must have a clear idea by which the research was initially planned to find
out the relevant research methodology followed for collecting the data for the research.
This has further raised the research objectives that was formulated so far from the
research aims. The main objectives of the research were found to be focusing on the
the websites as there were security vulnerabilities found in the development process. The
outcome of the entire design and development was found to be faulty when it came to the
security system of the ecommerce applications. There were repeated reports of
ransomware attacks and other ways of manipulating or theft of information for which the
development process was to be blamed. This is why, the entire research has been
formulated to find out a feasible way in which the vulnerabilities can be identified and for
further development and design of the websites they can be avoided. Since, having
vulnerabilities in the e-commerce websites are not only causing problems to the
customers of the organization, but it is also becoming obligatory in framing up a good
reputation for the organization with the customers.
The next phase of the research was framed to find out the research aims and the research
objectives that needed to be identified before the research process was commenced
altogether. Therefore, the research was found to have a particular aim of investigating the
tools which have been utilized by the various software development system ever since it
has been implemented in software development. This would be required for the
investigation of the threat modelling for the successful design and development of the e-
commerce applications when they are available live to the customers online. The aim of
the research also pointed at the ways in which they have been done. This is due to the fact
that the reader must have a clear idea by which the research was initially planned to find
out the relevant research methodology followed for collecting the data for the research.
This has further raised the research objectives that was formulated so far from the
research aims. The main objectives of the research were found to be focusing on the

specified requirements to which E-commerce application should meet security standard.
This included, appraisal of the underlying principles in online shopping using credit card
and PayPal, Overview of E-commerce security, reviewing of the different security issues
in E-commerce organization, reviewing of the available security tools and security
modelling approaches in E-commerce, developing a standard security model for software
development methodologies in E-commerce organization, and comparing the degree of
successful developed security modelling approach for E-commerce applications.
However, beyond all of the formulated methodologies, research aims and objectives, it
was also necessary to find out if there was any scope throughout the research. If there
was no scope through the research and development of the entire software for the e-
commerce websites there would be no point in developing the research further. The scope
of the research highlights that the challenges that website development has been facing
throughout the course of security issues since the time of its inception is the reason why
the research was commenced at the first place. This research was first identified to
provide solutions to the recent issues about the study the researcher aims at using past
research work, current research materials, and interactive social media platforms in
getting the most recent and up to date security models being used to curb or reduce
security threats online.
After that, the background of the entire study was formulated, which specifically implies
why the security issues of the software and website development needs to be eradicated at
the first place. This chapter specifically focuses on how the malicious hackers have been
making it difficult for the organizations to put up with the challenges they implement for
both the organization and the customers as a whole. The reasons why this particular issue
This included, appraisal of the underlying principles in online shopping using credit card
and PayPal, Overview of E-commerce security, reviewing of the different security issues
in E-commerce organization, reviewing of the available security tools and security
modelling approaches in E-commerce, developing a standard security model for software
development methodologies in E-commerce organization, and comparing the degree of
successful developed security modelling approach for E-commerce applications.
However, beyond all of the formulated methodologies, research aims and objectives, it
was also necessary to find out if there was any scope throughout the research. If there
was no scope through the research and development of the entire software for the e-
commerce websites there would be no point in developing the research further. The scope
of the research highlights that the challenges that website development has been facing
throughout the course of security issues since the time of its inception is the reason why
the research was commenced at the first place. This research was first identified to
provide solutions to the recent issues about the study the researcher aims at using past
research work, current research materials, and interactive social media platforms in
getting the most recent and up to date security models being used to curb or reduce
security threats online.
After that, the background of the entire study was formulated, which specifically implies
why the security issues of the software and website development needs to be eradicated at
the first place. This chapter specifically focuses on how the malicious hackers have been
making it difficult for the organizations to put up with the challenges they implement for
both the organization and the customers as a whole. The reasons why this particular issue
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

is forming a huge obligation to research about and find a solution for eradicating these
have been described in this chapter. Furthermore, this chapter describes that the software
hackers are using advance technologies and techniques in the consistent manner to access
important data and carry out other significant activities to E-commerce network
application. In addition to that, this section also describes the electronic technologies
sectors, Privacy and security are major factor. The E-commerce sector also shares these
views in line with other technological fields. While some firms are faced with difficulties
in making their website security sophisticated in order to provide customers with
effective secure payment online, other firms like Palpay, WePay and ProPay have
provided their customers with the security of assessing any website with an assurance
that their information is safe. This section also clarifies that the large organizations have
been investing in huge amounts of money in the ecommerce websites since the latest
advancement in the technology has made it even more lucrative to invest in digitized
organizations that promote ecommerce technologies. However, after it was found that
these security vulnerabilities are present in the entire development and design phase,
these organizations have started investing more in finding out a solution that would
address and resolve the issues of ecommerce security challenges utilizing various tools
and technologies. The research helps in formulating a a structured approach that enables
one identify, measure and address the security hazard associated with applications and
software. However, the research has its own limitations while conducting, out of which,
one was that the entire research was based only on the ecommerce application payment
systems that culminated through E-bay, Amazon and Konga. The research also finds out
the various types of threat modelling approaches available today. These threat modelling
have been described in this chapter. Furthermore, this chapter describes that the software
hackers are using advance technologies and techniques in the consistent manner to access
important data and carry out other significant activities to E-commerce network
application. In addition to that, this section also describes the electronic technologies
sectors, Privacy and security are major factor. The E-commerce sector also shares these
views in line with other technological fields. While some firms are faced with difficulties
in making their website security sophisticated in order to provide customers with
effective secure payment online, other firms like Palpay, WePay and ProPay have
provided their customers with the security of assessing any website with an assurance
that their information is safe. This section also clarifies that the large organizations have
been investing in huge amounts of money in the ecommerce websites since the latest
advancement in the technology has made it even more lucrative to invest in digitized
organizations that promote ecommerce technologies. However, after it was found that
these security vulnerabilities are present in the entire development and design phase,
these organizations have started investing more in finding out a solution that would
address and resolve the issues of ecommerce security challenges utilizing various tools
and technologies. The research helps in formulating a a structured approach that enables
one identify, measure and address the security hazard associated with applications and
software. However, the research has its own limitations while conducting, out of which,
one was that the entire research was based only on the ecommerce application payment
systems that culminated through E-bay, Amazon and Konga. The research also finds out
the various types of threat modelling approaches available today. These threat modelling

approached include fault tree Analysis, Attack trees, Stride and Dread. These approaches
and techniques to application security have proven to be ineffective, this is evidence in
their vulnerabilities, permitting applications to be attacked or damaged. A challenging
task is determining with approach will give the best result when applied to specific
software application or e-commerce applications. Therefore, determine how to effectively
solve this security challenge using the most effective tool is crux of this project. The
research scope also identifies the need of security in the ecommerce websites that forms
an integral approach of the entire research. The need of the security threat was found in
further details in the literature review chapter of the entire study, which finds out how the
entire conceptual framework was formulated to find out why the research was needed
from the aspect of the business organizations. It is an issue that needs to be addressed
while conducting the entire research because at the end of the day this would be
beneficial mostly to the business organizations so that they could invest in appropriately
and logically. It can also be said that this particular research would make it easier for the
decision making body to make effective decisions based on the research about investing
in properly while developing a website as an ecommerce platform. The threat modelling
technique framework that had been developed as a result mostly based upon the step by
step developmental phase of the website and further discussed on how the framework
should be used to make sure that the website is impermeable to the external hackers.
However, it is also not to be forgotten that the entire research as a whole should not
violate any kind of ethical framework that is developed during the conduction of a
research. Thus, the research follows how the research had been collecting data from
primary and secondary sources in the most appropriate and ethical way possible and
and techniques to application security have proven to be ineffective, this is evidence in
their vulnerabilities, permitting applications to be attacked or damaged. A challenging
task is determining with approach will give the best result when applied to specific
software application or e-commerce applications. Therefore, determine how to effectively
solve this security challenge using the most effective tool is crux of this project. The
research scope also identifies the need of security in the ecommerce websites that forms
an integral approach of the entire research. The need of the security threat was found in
further details in the literature review chapter of the entire study, which finds out how the
entire conceptual framework was formulated to find out why the research was needed
from the aspect of the business organizations. It is an issue that needs to be addressed
while conducting the entire research because at the end of the day this would be
beneficial mostly to the business organizations so that they could invest in appropriately
and logically. It can also be said that this particular research would make it easier for the
decision making body to make effective decisions based on the research about investing
in properly while developing a website as an ecommerce platform. The threat modelling
technique framework that had been developed as a result mostly based upon the step by
step developmental phase of the website and further discussed on how the framework
should be used to make sure that the website is impermeable to the external hackers.
However, it is also not to be forgotten that the entire research as a whole should not
violate any kind of ethical framework that is developed during the conduction of a
research. Thus, the research follows how the research had been collecting data from
primary and secondary sources in the most appropriate and ethical way possible and

make sure that the observing of the E-bay, Amazon and Konga e-commerce mobile
application users are concern with the security on this platform. Although the findings of
the study were described in details in the later chapters, this particular section described
that there were proper ethical considerations made during researching about the topic
entirely.
The next chapter provided an overview of the security issues in ecommerce and how they
have been addressed or found out about according to the literatures and the research
works by other researcher and analysts in the previous times. The entire chapter in this
regard can be considered as a data collection technique developed through literature
review. The articles previewed and reviewed in this regard would be considered as
secondary sources throughout the research. This particular chapter focuses on all the
developed methods that can be considered as an authenticated mechanism to the in e-
commerce websites which are based on providing personal security identification and
access control methods.
This chapter also defines the specific key terms which is required for the awareness of the
reader who would be going through the entire paper. The terms include, fraud, electronic
thief, Security confidentiality, e-commerce integrity, and phishing.
Then the chapter introduces the process of literature review, which is a conducted process
developed for the data collection method through secondary sources. This chapter
identifies the underlying principles in online shopping using credit card and PayPal, the
ecommerce security tools, firewalls, and the types of firewalls. Therefore, the entire
structure of the research has been linked to the research objective and the information or
data collected through the literature review or secondary sources.
application users are concern with the security on this platform. Although the findings of
the study were described in details in the later chapters, this particular section described
that there were proper ethical considerations made during researching about the topic
entirely.
The next chapter provided an overview of the security issues in ecommerce and how they
have been addressed or found out about according to the literatures and the research
works by other researcher and analysts in the previous times. The entire chapter in this
regard can be considered as a data collection technique developed through literature
review. The articles previewed and reviewed in this regard would be considered as
secondary sources throughout the research. This particular chapter focuses on all the
developed methods that can be considered as an authenticated mechanism to the in e-
commerce websites which are based on providing personal security identification and
access control methods.
This chapter also defines the specific key terms which is required for the awareness of the
reader who would be going through the entire paper. The terms include, fraud, electronic
thief, Security confidentiality, e-commerce integrity, and phishing.
Then the chapter introduces the process of literature review, which is a conducted process
developed for the data collection method through secondary sources. This chapter
identifies the underlying principles in online shopping using credit card and PayPal, the
ecommerce security tools, firewalls, and the types of firewalls. Therefore, the entire
structure of the research has been linked to the research objective and the information or
data collected through the literature review or secondary sources.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

This forms the basic criterion for the primary data collection method as the formulated
questions for the research is developed with the help of this particular method of
literature review.
The next chapter is thus utilized for the adapted methodology which enables a clear
visibility of a project by helping to ensure that any necessary decisions can be made at the
earliest possible opportunity. This outcome is normally done to avoid unforeseen
circumstances while there is still time to avoid any risk outcome. In addition to that,
research methodology is an efficient way of effectively managing time for a project. The
chapter describes the four research methodologies were selected to be applied in the
analysis process of Threat Modelling Tools and Technique used in securing e-commerce
applications online, which include, prototype methods, DSDM or Dynamic Systems
Development Model, Spring and Scrum. During this process as well, the ethical
considerations have been taken into account and followed vigorously.
The next chapter frames the data collection process that needs the evidence for the
interview that has been conducted online for the entire research and includes a summary
of the entire conducted research as a result. This helps in finding out all the relevant
information that was needed to be found out during the research process as a whole. This
is why the entire research was conducted to find out the relevant information regarding
the security issues in the above mentioned areas of the ecommerce websites and how a
solution can be formulated for the further development of the ecommerce websites
without any sort of security issues occurring further.
questions for the research is developed with the help of this particular method of
literature review.
The next chapter is thus utilized for the adapted methodology which enables a clear
visibility of a project by helping to ensure that any necessary decisions can be made at the
earliest possible opportunity. This outcome is normally done to avoid unforeseen
circumstances while there is still time to avoid any risk outcome. In addition to that,
research methodology is an efficient way of effectively managing time for a project. The
chapter describes the four research methodologies were selected to be applied in the
analysis process of Threat Modelling Tools and Technique used in securing e-commerce
applications online, which include, prototype methods, DSDM or Dynamic Systems
Development Model, Spring and Scrum. During this process as well, the ethical
considerations have been taken into account and followed vigorously.
The next chapter frames the data collection process that needs the evidence for the
interview that has been conducted online for the entire research and includes a summary
of the entire conducted research as a result. This helps in finding out all the relevant
information that was needed to be found out during the research process as a whole. This
is why the entire research was conducted to find out the relevant information regarding
the security issues in the above mentioned areas of the ecommerce websites and how a
solution can be formulated for the further development of the ecommerce websites
without any sort of security issues occurring further.

6.2 Conclusion
It will be a grievous mistake for one to underestimate the importance of threat modelling.
Evidence has shown that there is an increase in the number of businesses going online for
the sale of their products. In this report, appraisal has been made regarding the
importance of e-commerce shopping and the underlying principles behind using online
credit card and PayPal. Further analyses revealed the different security issues faced by
my contemporary e-commerce firm, with emphasis on why a security tool and threat
approach is important. The current e-commerce security tools and approaches that are
been used to curtail security challenges affecting the online businesses has been
evaluated. However, this study identified major areas where key security issues were not
properly considered by the previous e-ecommerce website and application developers.
Furthermore, it was also identified that the current existing software development cycles
and early once did not fully take into cognisance application security. This paves way for
many software engineers and software developers not considering security at the very
beginning of their various e-commerce application developments. This has had an
adverse effect in the growing e-commerce sector, thus discouraging business
cooperation’s and small businesses owners are very cautious and thoughtful before
migrating to online systems.
The threat modelling approach is a dynamic process, owing to the fact that threat and its
initiators are constantly researching looking for loop holes for different online
applications. This constant lookout is to investigate ways to hack e-commerce
applications, thereby compromising vital information. To prevent such, every security
analyst has to be proactive vigilant before an application is built and after. In bit to go
It will be a grievous mistake for one to underestimate the importance of threat modelling.
Evidence has shown that there is an increase in the number of businesses going online for
the sale of their products. In this report, appraisal has been made regarding the
importance of e-commerce shopping and the underlying principles behind using online
credit card and PayPal. Further analyses revealed the different security issues faced by
my contemporary e-commerce firm, with emphasis on why a security tool and threat
approach is important. The current e-commerce security tools and approaches that are
been used to curtail security challenges affecting the online businesses has been
evaluated. However, this study identified major areas where key security issues were not
properly considered by the previous e-ecommerce website and application developers.
Furthermore, it was also identified that the current existing software development cycles
and early once did not fully take into cognisance application security. This paves way for
many software engineers and software developers not considering security at the very
beginning of their various e-commerce application developments. This has had an
adverse effect in the growing e-commerce sector, thus discouraging business
cooperation’s and small businesses owners are very cautious and thoughtful before
migrating to online systems.
The threat modelling approach is a dynamic process, owing to the fact that threat and its
initiators are constantly researching looking for loop holes for different online
applications. This constant lookout is to investigate ways to hack e-commerce
applications, thereby compromising vital information. To prevent such, every security
analyst has to be proactive vigilant before an application is built and after. In bit to go

ahead of the attackers this research was conceived. This leads to a new security approach
of tackling security e-commerce application using an application de-composition,
determining high ranking threats and determining possible countermeasure and
mitigation.
Agile methodology was used to develop this approach, with constant researching and
observations on the current treat towards e-commerce application. Additionally,
explanation has been made how this report can help security analyst and developers to
use the methods explained before and after they have created an e-commerce application.
Finally a website was developed as a procedure to how this new security threat modelling
approach has been documented and explained. This is to protect e-commerce applications
from continues security threat. This will invariably assist e-commerce enterprises to
reduce cost, increase market share, and improve relationship between buyers and sellers
on their application. An appropriated ethical consideration was at the forefront of this
research as well as a documentation of the time plan for this report to be completed.
6.3 Recommendation
It is expected that further research should be carried out in securing e-commerce
applications considering the global threat to online business. In addition, appropriate
security method and techniques should be considered before web developers proceed into
developing an e-commerce application. Due to the daily increase in the number of
challenges in securing e-commerce applications, I am proposing that modern software
development life cycle should contain security as a main requirement or process. This is
because the old version of SDLC like waterfall and prototype approach did not give any
of tackling security e-commerce application using an application de-composition,
determining high ranking threats and determining possible countermeasure and
mitigation.
Agile methodology was used to develop this approach, with constant researching and
observations on the current treat towards e-commerce application. Additionally,
explanation has been made how this report can help security analyst and developers to
use the methods explained before and after they have created an e-commerce application.
Finally a website was developed as a procedure to how this new security threat modelling
approach has been documented and explained. This is to protect e-commerce applications
from continues security threat. This will invariably assist e-commerce enterprises to
reduce cost, increase market share, and improve relationship between buyers and sellers
on their application. An appropriated ethical consideration was at the forefront of this
research as well as a documentation of the time plan for this report to be completed.
6.3 Recommendation
It is expected that further research should be carried out in securing e-commerce
applications considering the global threat to online business. In addition, appropriate
security method and techniques should be considered before web developers proceed into
developing an e-commerce application. Due to the daily increase in the number of
challenges in securing e-commerce applications, I am proposing that modern software
development life cycle should contain security as a main requirement or process. This is
because the old version of SDLC like waterfall and prototype approach did not give any
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

detail about security, which has led to software developers, not considering security as a
major challenge.
Also, large e-commerce companies should collaborate to raise funds to support research
that will help in securing their system. E-commerce firm should provide an avenue where
they can constantly assure their users that information provided are secured and privacy
will not be comprised. Also, regular contact with the application users on how to keep it
secure from cybercriminals, to enhance good consumer relationship needed for rapid
growth in the e-commerce industries will be a welcome idea.
major challenge.
Also, large e-commerce companies should collaborate to raise funds to support research
that will help in securing their system. E-commerce firm should provide an avenue where
they can constantly assure their users that information provided are secured and privacy
will not be comprised. Also, regular contact with the application users on how to keep it
secure from cybercriminals, to enhance good consumer relationship needed for rapid
growth in the e-commerce industries will be a welcome idea.

References
Amini, A., Jamil, N., Ahmad, AR and Z`aba, AR (2017). Threat Modelling Approaches
for Securing Cloud Computing. [Online] Available at: http://scialert.net/fulltext/?
doi=jas.2015.953.967&org=11 [Accessed 29 Mar. 2017].
Anicas, M (2015). "What Is A Firewall And How Does It Work? | Digital ocean".
Digitalocean.com. N.p., 2017. Web. 11 Apr. 2017.
British Educational Research Association (2001). Ethical Guidelines for Educational
Research. 1st ed. [eBook] Endsleigh Street, London WC1H 0ED: British Educational
Research Association, pp.5-7. Available at:
http://moodle.bcu.ac.uk/pluginfile.php/1162449/mod_resource/content/1/BERA-Ethical-
Guidelines-2011.pdf [Accessed 3 May 2017].
Bruton, W. (1999). Fraud on the Revenue: Emerging Cyber Cash, Cyber Banks and
Fraud. Journal of Financial Crime, 7(1), pp.75-78.
Carey, T, & Mason, R (1983), 'Information System Prototyping: Technique, Tools and
Methodologies', Infor, 21, 3, pp. 177-191, Business Source Complete, EBSCOhost,
viewed 28 February 2015
Chopra, A. (2016). Security Issues of Firewall. International Journal of P2P Network
Trends and Technology, 22(1), pp.4-9.
Cobb, M. (2011) Add threat modelling to your web application security best practices.
Available at: http://www.computerweekly.com/tip/Add-threat-modelling-to-your-Web-
application-security-best-practices (Accessed: 8 February 2017).
Amini, A., Jamil, N., Ahmad, AR and Z`aba, AR (2017). Threat Modelling Approaches
for Securing Cloud Computing. [Online] Available at: http://scialert.net/fulltext/?
doi=jas.2015.953.967&org=11 [Accessed 29 Mar. 2017].
Anicas, M (2015). "What Is A Firewall And How Does It Work? | Digital ocean".
Digitalocean.com. N.p., 2017. Web. 11 Apr. 2017.
British Educational Research Association (2001). Ethical Guidelines for Educational
Research. 1st ed. [eBook] Endsleigh Street, London WC1H 0ED: British Educational
Research Association, pp.5-7. Available at:
http://moodle.bcu.ac.uk/pluginfile.php/1162449/mod_resource/content/1/BERA-Ethical-
Guidelines-2011.pdf [Accessed 3 May 2017].
Bruton, W. (1999). Fraud on the Revenue: Emerging Cyber Cash, Cyber Banks and
Fraud. Journal of Financial Crime, 7(1), pp.75-78.
Carey, T, & Mason, R (1983), 'Information System Prototyping: Technique, Tools and
Methodologies', Infor, 21, 3, pp. 177-191, Business Source Complete, EBSCOhost,
viewed 28 February 2015
Chopra, A. (2016). Security Issues of Firewall. International Journal of P2P Network
Trends and Technology, 22(1), pp.4-9.
Cobb, M. (2011) Add threat modelling to your web application security best practices.
Available at: http://www.computerweekly.com/tip/Add-threat-modelling-to-your-Web-
application-security-best-practices (Accessed: 8 February 2017).

Dara, J. and Gundemoni, L. (2017). Credit card security and e-payment : enquiry into
credit card fraud in e-payment. [online] Diva-portal.org. Available at: http://www.diva-
portal.org/smash/record.jsf?pid=diva2%3A1023638&dswid=-7453 [Accessed 30 Mar.
2017].
Dickens, B. and Cook, R. (2005). Conflict of interest: Legal and ethical aspects.
International Journal of Gynaecology & Obstetrics, 92(2), pp.192-197.
DSouza, R. (2016) 3 approaches to threat modelling. Available at:
http://threatmodeler.com/approaches-to-threat-modeling/ (Accessed: 8 February 2017).
Eastep, T. (2017). Basic Two-Interface Firewall. [Online] Shorewall.org. Available at:
http://shorewall.org/two-interface.htm [Accessed 18 Apr. 2017].
Gibson, R (1998), 'Software process modelling: theory, results and commentary',
Proceedings Of The Thirty-First Hawaii International Conference On System Sciences, 3,
p. 399, Publisher Provided Full Text Searching File, EBSCOhost, viewed 28 February
2015.
Gritzalis, S. (2005). Public Key Infrastructure: Research and Applications. International
Journal of Information Security, 5(1), pp.1-2.
Han, K.H., Kang, J.G. and Song, M. (2009) ‘Two-stage process analysis using the
process-based performance measurement framework and business process simulation’,
Expert Systems with Applications, 36(3), pp. 7080–7086.
Hanumesh, V. and Sunder, K. (2000). A Study of Security Issues in E-Commerce
Applications. IETE Technical Review, 17(4), pp.209-214.
credit card fraud in e-payment. [online] Diva-portal.org. Available at: http://www.diva-
portal.org/smash/record.jsf?pid=diva2%3A1023638&dswid=-7453 [Accessed 30 Mar.
2017].
Dickens, B. and Cook, R. (2005). Conflict of interest: Legal and ethical aspects.
International Journal of Gynaecology & Obstetrics, 92(2), pp.192-197.
DSouza, R. (2016) 3 approaches to threat modelling. Available at:
http://threatmodeler.com/approaches-to-threat-modeling/ (Accessed: 8 February 2017).
Eastep, T. (2017). Basic Two-Interface Firewall. [Online] Shorewall.org. Available at:
http://shorewall.org/two-interface.htm [Accessed 18 Apr. 2017].
Gibson, R (1998), 'Software process modelling: theory, results and commentary',
Proceedings Of The Thirty-First Hawaii International Conference On System Sciences, 3,
p. 399, Publisher Provided Full Text Searching File, EBSCOhost, viewed 28 February
2015.
Gritzalis, S. (2005). Public Key Infrastructure: Research and Applications. International
Journal of Information Security, 5(1), pp.1-2.
Han, K.H., Kang, J.G. and Song, M. (2009) ‘Two-stage process analysis using the
process-based performance measurement framework and business process simulation’,
Expert Systems with Applications, 36(3), pp. 7080–7086.
Hanumesh, V. and Sunder, K. (2000). A Study of Security Issues in E-Commerce
Applications. IETE Technical Review, 17(4), pp.209-214.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Hayashi, F. (2012). The Economics of Payment Card Fee Structure: Policy
Considerations of Payment Card Rewards. SSRN Electronic Journal, 1.
Herrmann, G. and Herrmann, P. (2004). Introduction: Security and Trust in Electronic
Commerce. Electronic Commerce Research, 4(1/2), pp.5-7.
Indi T, and Raut, S. (2012). Biometric Feature based Person Unique Identification
System. International Journal of Computer Applications, 51(13), pp.7-12.
IT knowledge portal, (2015), Software Development Methodologies. available:
http://www.itinfo.am/eng/software-development-methodologies/. Last accessed 23th
March 2015
Jamil, A., Jamil, D., Ahmad, A.R. and Z`aba, M.R. (2015) ‘Threat modeling approaches
for securing cloud Computing’, Journal of Applied Sciences, 15(7), pp. 953–967.
Kelly, E. and Rowland, H. (2000). Ethical and online privacy issues in electronic
commerce. Business Horizons, 43(3), pp.3-12.
Корнієнко, Б. (2006). Analysis technologies firewall. Proceedings of National Aviation
University, 28(2).
Kumar, S. (2017a). Review on Network Security and Cryptography. [online]
Pubs.sciepub.com. Available at: http://pubs.sciepub.com/iteces/3/1/1/ [Accessed 21 Apr.
2017].
Kumar, S. (2017b). Review on Network Security and Cryptography. [online]
Pubs.sciepub.com. Available at: http://pubs.sciepub.com/iteces/3/1/1/ [Accessed 21 Apr.
2017].
Considerations of Payment Card Rewards. SSRN Electronic Journal, 1.
Herrmann, G. and Herrmann, P. (2004). Introduction: Security and Trust in Electronic
Commerce. Electronic Commerce Research, 4(1/2), pp.5-7.
Indi T, and Raut, S. (2012). Biometric Feature based Person Unique Identification
System. International Journal of Computer Applications, 51(13), pp.7-12.
IT knowledge portal, (2015), Software Development Methodologies. available:
http://www.itinfo.am/eng/software-development-methodologies/. Last accessed 23th
March 2015
Jamil, A., Jamil, D., Ahmad, A.R. and Z`aba, M.R. (2015) ‘Threat modeling approaches
for securing cloud Computing’, Journal of Applied Sciences, 15(7), pp. 953–967.
Kelly, E. and Rowland, H. (2000). Ethical and online privacy issues in electronic
commerce. Business Horizons, 43(3), pp.3-12.
Корнієнко, Б. (2006). Analysis technologies firewall. Proceedings of National Aviation
University, 28(2).
Kumar, S. (2017a). Review on Network Security and Cryptography. [online]
Pubs.sciepub.com. Available at: http://pubs.sciepub.com/iteces/3/1/1/ [Accessed 21 Apr.
2017].
Kumar, S. (2017b). Review on Network Security and Cryptography. [online]
Pubs.sciepub.com. Available at: http://pubs.sciepub.com/iteces/3/1/1/ [Accessed 21 Apr.
2017].

Lee, K.-H. and Park, Y.B. (2016) ‘Adaption of integrated secure guide for secure
software development Lifecycle’, International Journal of Security and Its Applications,
10(6), pp. 145–154.
Li, X., He, K., Feng, Z. and Xu, G. (2012). Unified threat model for analyzing and
evaluating software threats. Security and Communication Networks, p.n/a-n/a.
Lin, K. (2017). Online Transaction Security Risk Management for E-commerce Web
Applications. [Online] Article.sciencepublishinggroup.com. Available at:
http://article.sciencepublishinggroup.com/html/10.11648.j.ajomis.20170201.12.html
[Accessed 16 Apr. 2017].
Long, P. and Vy, P. (2016a). Internet Banking Service Quality, Customer Satisfaction
and Customer Loyalty. International Journal of Strategic Decision Sciences, 7(1), pp.1-
17.
Long, P. and Vy, P. (2016b). Internet Banking Service Quality, Customer Satisfaction
and Customer Loyalty:. International Journal of Strategic Decision Sciences, 7(1), pp.1-
17.
Mason, S. (2014). World electronic signature legislation. Digital Evidence and
Electronic Signature Law Review, 10(0).
McGrath, J. (2017). How has technology changed the way we conduct business. [Online]
HowStuffWorks. Available at: http://money.howstuffworks.com/technology-changed-
business.htm [Accessed 15 May 2017].
software development Lifecycle’, International Journal of Security and Its Applications,
10(6), pp. 145–154.
Li, X., He, K., Feng, Z. and Xu, G. (2012). Unified threat model for analyzing and
evaluating software threats. Security and Communication Networks, p.n/a-n/a.
Lin, K. (2017). Online Transaction Security Risk Management for E-commerce Web
Applications. [Online] Article.sciencepublishinggroup.com. Available at:
http://article.sciencepublishinggroup.com/html/10.11648.j.ajomis.20170201.12.html
[Accessed 16 Apr. 2017].
Long, P. and Vy, P. (2016a). Internet Banking Service Quality, Customer Satisfaction
and Customer Loyalty. International Journal of Strategic Decision Sciences, 7(1), pp.1-
17.
Long, P. and Vy, P. (2016b). Internet Banking Service Quality, Customer Satisfaction
and Customer Loyalty:. International Journal of Strategic Decision Sciences, 7(1), pp.1-
17.
Mason, S. (2014). World electronic signature legislation. Digital Evidence and
Electronic Signature Law Review, 10(0).
McGrath, J. (2017). How has technology changed the way we conduct business. [Online]
HowStuffWorks. Available at: http://money.howstuffworks.com/technology-changed-
business.htm [Accessed 15 May 2017].

Mehta, R. (2016) Threat Modeling_Seminar. Available at:
http://www.slideshare.net/RoshanMehta1/threat-modelingseminar (Accessed: 8 February
2017).
Menkus, B. (1997) ‘Understanding the denial of service threat’, EDPACS, 24(9), pp. 11–
17.
Meyer, H. (2006a). Firewall fights intranet threat. Computers & Security, 15(6), p.519.
Meyer, H. (2006b). Firewall fights intranet threat. Computers & Security, 11(3), p.432.
Moore, A. (2007). Biometric technologies — an introduction. Biometric Technology
Today, 15(1), pp.6-7.
Morgan, D. (2004a). Network security and custom Web applications. Network Security,
2004(4), pp.15-17.
Morgan, D. (2004b). Network security and custom Web applications. Network Security,
2004(4), pp.20-22.
Nilsson, A, & Wilson, T (2012), 'Reflections on Barry W. Boehm's "A spiral model of
software development and enhancement International Journal Of Managing Projects In
Business, 5, 4, p. 737, Publisher Provided Full Text Searching File, EBSCOhost, viewed
28 February 2015.
Ott, W.E. (2008) ‘The threat of hackers: The need to secure patient data & other
important records on your agency’s notebook computers’, JEMS: Journal of Emergency
Medical Services, 33(8), pp. 68–71.
http://www.slideshare.net/RoshanMehta1/threat-modelingseminar (Accessed: 8 February
2017).
Menkus, B. (1997) ‘Understanding the denial of service threat’, EDPACS, 24(9), pp. 11–
17.
Meyer, H. (2006a). Firewall fights intranet threat. Computers & Security, 15(6), p.519.
Meyer, H. (2006b). Firewall fights intranet threat. Computers & Security, 11(3), p.432.
Moore, A. (2007). Biometric technologies — an introduction. Biometric Technology
Today, 15(1), pp.6-7.
Morgan, D. (2004a). Network security and custom Web applications. Network Security,
2004(4), pp.15-17.
Morgan, D. (2004b). Network security and custom Web applications. Network Security,
2004(4), pp.20-22.
Nilsson, A, & Wilson, T (2012), 'Reflections on Barry W. Boehm's "A spiral model of
software development and enhancement International Journal Of Managing Projects In
Business, 5, 4, p. 737, Publisher Provided Full Text Searching File, EBSCOhost, viewed
28 February 2015.
Ott, W.E. (2008) ‘The threat of hackers: The need to secure patient data & other
important records on your agency’s notebook computers’, JEMS: Journal of Emergency
Medical Services, 33(8), pp. 68–71.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Potter, B. (2009). Microsoft SDL Threat Modelling Tool. Network Security, 2009(1),
pp.15-18.
Pressman, R.S. (2009) Software engineering: A practitioner’s approach. 7th edn. Boston:
McGraw Hill Higher Education.
Pye, G. and Warren, M. (2007). E-business security benchmarking: a model and
framework. International Journal of Information and Computer Security, 1(4), p.378.
Riley, S. and Chaparro, B. (2006a). User Password Generation Practices and Strong
Password Guideline Compliance. Proceedings of the Human Factors and Ergonomics
Society Annual Meeting, 50(17), pp.1812-1816.
Riley, S. and Chaparro, B. (2006b). User Password Generation Practices and Strong
Password Guideline Compliance. Proceedings of the Human Factors and Ergonomics
Society Annual Meeting, 50(17), pp.1814-1819.
Samant, A. (2008). Managerial finance. 1st ed. [Bradford, England]: Emerald, pp.23-25.
Sangita, D. and Madhuri, S. (2015) ‘Securing online banking transaction using predictive
approach of hidden Markov model’, International Journal of Computer Applications,
128(7), pp. 14–17.
Savola, R. and Abie, H. (2009). On-Line and Off-Line Security Measurement Framework
for Mobile Ad Hoc Networks. Journal of Networks, 4(7).
Savage, M. (2001). PayPal success in Web payments market could threaten e-purse. Card
Technology Today, 13(6), pp.3-4.
pp.15-18.
Pressman, R.S. (2009) Software engineering: A practitioner’s approach. 7th edn. Boston:
McGraw Hill Higher Education.
Pye, G. and Warren, M. (2007). E-business security benchmarking: a model and
framework. International Journal of Information and Computer Security, 1(4), p.378.
Riley, S. and Chaparro, B. (2006a). User Password Generation Practices and Strong
Password Guideline Compliance. Proceedings of the Human Factors and Ergonomics
Society Annual Meeting, 50(17), pp.1812-1816.
Riley, S. and Chaparro, B. (2006b). User Password Generation Practices and Strong
Password Guideline Compliance. Proceedings of the Human Factors and Ergonomics
Society Annual Meeting, 50(17), pp.1814-1819.
Samant, A. (2008). Managerial finance. 1st ed. [Bradford, England]: Emerald, pp.23-25.
Sangita, D. and Madhuri, S. (2015) ‘Securing online banking transaction using predictive
approach of hidden Markov model’, International Journal of Computer Applications,
128(7), pp. 14–17.
Savola, R. and Abie, H. (2009). On-Line and Off-Line Security Measurement Framework
for Mobile Ad Hoc Networks. Journal of Networks, 4(7).
Savage, M. (2001). PayPal success in Web payments market could threaten e-purse. Card
Technology Today, 13(6), pp.3-4.

Schneier, B. (2000) Secrets and lies: Digital security in a networked world. 2nd edn.
New York, NY: John Wiley & Sons.
Sample, W. (2015). A threat-based approach to security. Computer Fraud & Security,
2015(2), pp.7-10.
Shah, A ( 2001), 'A Framework for the Prototype-based Software Development
Methodologies', Journal Of King Saud University - Computer And Information Sciences,
13, pp. 111-131, ScienceDirect, EBSCOhost, viewed 28 February 2015
Smith, F. (2016). 10 Tips to Improve Application Performance | NGINX. [Online]
NGINX. Available at: https://www.nginx.com/blog/10-tips-for-10x-application-
performance/ [Accessed 21 Mar. 2017].
Stoica, M, Mircea, M,& Ghilic-Micu,B (2013), ‘Software Development: Agile Vs
Traditional’, Informatica Economica, 17, 14, pp 64-65, Business Source Compelete,
EBSCOhost, viewed 8 May 2017.
Tomlinson, M. (2000) ‘Tackling e-commerce security issues head on’, Computer Fraud
& Security, 2000(11), pp. 10–13.
Virtue, T. (2013a). Payment card industry data security standard handbook. 1st ed.
Hoboken, N.J.: Wiley.
Virtue, T. (2013b). Payment card industry data security standard handbook. 1st ed.
Hoboken, N.J.: Wiley
Wagner, S., Madsen, P. and Ammer, C. (2009) ‘Evaluation of different approaches for
modelling individual tree seedling height growth’, Trees, 23(4), pp. 701–715.
New York, NY: John Wiley & Sons.
Sample, W. (2015). A threat-based approach to security. Computer Fraud & Security,
2015(2), pp.7-10.
Shah, A ( 2001), 'A Framework for the Prototype-based Software Development
Methodologies', Journal Of King Saud University - Computer And Information Sciences,
13, pp. 111-131, ScienceDirect, EBSCOhost, viewed 28 February 2015
Smith, F. (2016). 10 Tips to Improve Application Performance | NGINX. [Online]
NGINX. Available at: https://www.nginx.com/blog/10-tips-for-10x-application-
performance/ [Accessed 21 Mar. 2017].
Stoica, M, Mircea, M,& Ghilic-Micu,B (2013), ‘Software Development: Agile Vs
Traditional’, Informatica Economica, 17, 14, pp 64-65, Business Source Compelete,
EBSCOhost, viewed 8 May 2017.
Tomlinson, M. (2000) ‘Tackling e-commerce security issues head on’, Computer Fraud
& Security, 2000(11), pp. 10–13.
Virtue, T. (2013a). Payment card industry data security standard handbook. 1st ed.
Hoboken, N.J.: Wiley.
Virtue, T. (2013b). Payment card industry data security standard handbook. 1st ed.
Hoboken, N.J.: Wiley
Wagner, S., Madsen, P. and Ammer, C. (2009) ‘Evaluation of different approaches for
modelling individual tree seedling height growth’, Trees, 23(4), pp. 701–715.

Weston, S. (2016) Applications threat modelling. Available at:
http://resources.infosecinstitute.com/applications-threat-modeling/#gre (Accessed: 8
February 2017).
Chen, Y. (2002). Signature files and signature trees. Information Processing Letters,
82(4), pp.213-221.
Zalenski, R. (2002). Firewall technologies. IEEE Potentials, 21(1), pp.24-29.
http://resources.infosecinstitute.com/applications-threat-modeling/#gre (Accessed: 8
February 2017).
Chen, Y. (2002). Signature files and signature trees. Information Processing Letters,
82(4), pp.213-221.
Zalenski, R. (2002). Firewall technologies. IEEE Potentials, 21(1), pp.24-29.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
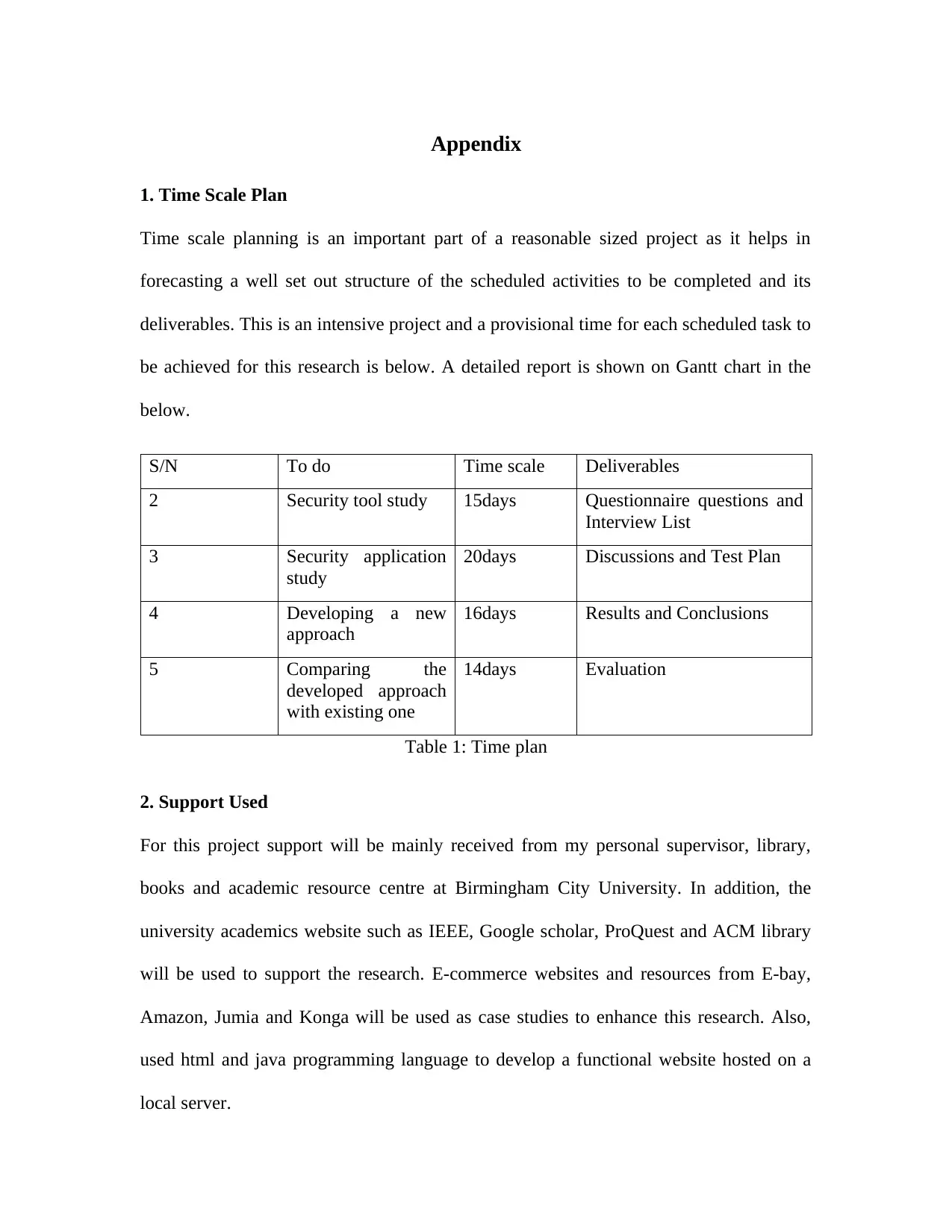
Appendix
1. Time Scale Plan
Time scale planning is an important part of a reasonable sized project as it helps in
forecasting a well set out structure of the scheduled activities to be completed and its
deliverables. This is an intensive project and a provisional time for each scheduled task to
be achieved for this research is below. A detailed report is shown on Gantt chart in the
below.
S/N To do Time scale Deliverables
2 Security tool study 15days Questionnaire questions and
Interview List
3 Security application
study
20days Discussions and Test Plan
4 Developing a new
approach
16days Results and Conclusions
5 Comparing the
developed approach
with existing one
14days Evaluation
Table 1: Time plan
2. Support Used
For this project support will be mainly received from my personal supervisor, library,
books and academic resource centre at Birmingham City University. In addition, the
university academics website such as IEEE, Google scholar, ProQuest and ACM library
will be used to support the research. E-commerce websites and resources from E-bay,
Amazon, Jumia and Konga will be used as case studies to enhance this research. Also,
used html and java programming language to develop a functional website hosted on a
local server.
1. Time Scale Plan
Time scale planning is an important part of a reasonable sized project as it helps in
forecasting a well set out structure of the scheduled activities to be completed and its
deliverables. This is an intensive project and a provisional time for each scheduled task to
be achieved for this research is below. A detailed report is shown on Gantt chart in the
below.
S/N To do Time scale Deliverables
2 Security tool study 15days Questionnaire questions and
Interview List
3 Security application
study
20days Discussions and Test Plan
4 Developing a new
approach
16days Results and Conclusions
5 Comparing the
developed approach
with existing one
14days Evaluation
Table 1: Time plan
2. Support Used
For this project support will be mainly received from my personal supervisor, library,
books and academic resource centre at Birmingham City University. In addition, the
university academics website such as IEEE, Google scholar, ProQuest and ACM library
will be used to support the research. E-commerce websites and resources from E-bay,
Amazon, Jumia and Konga will be used as case studies to enhance this research. Also,
used html and java programming language to develop a functional website hosted on a
local server.

3. Skills Audit
To complete any research process skills are needed to be put in practice for a successful
project. Over the last one year, I have gained a lot of skills that was of great benefit to
helping, completing this research. Some of the research skills gained included data flow
diagram, database evaluation, business intelligence, strategic IT planning data
correlation, research skills, project management and time management. In addition, my
ability to comprehensively read, document report academically and paraphrase sentences
professionally has improved. However, for this project to be successfully completed they
were skills I needed to develop. Developed skills in using JavaScript and html to making
a website and framework development. Also, gained insight conducting academic
interviews, research analysis, research design, research and implementation and testing
process to help me increase understanding of the entire project.
To complete any research process skills are needed to be put in practice for a successful
project. Over the last one year, I have gained a lot of skills that was of great benefit to
helping, completing this research. Some of the research skills gained included data flow
diagram, database evaluation, business intelligence, strategic IT planning data
correlation, research skills, project management and time management. In addition, my
ability to comprehensively read, document report academically and paraphrase sentences
professionally has improved. However, for this project to be successfully completed they
were skills I needed to develop. Developed skills in using JavaScript and html to making
a website and framework development. Also, gained insight conducting academic
interviews, research analysis, research design, research and implementation and testing
process to help me increase understanding of the entire project.
1 out of 84
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
