IT Ethics: Ethical Theory Analysis of Programmer Dilemma
VerifiedAdded on 2022/12/19
|6
|1271
|40
Essay
AI Summary
This essay delves into the ethical challenges faced by programmers, particularly concerning unethical and illegal activities within organizations. The analysis centers on a case study involving an intern asked to copy source code, highlighting issues of plagiarism and intellectual property rights. The essay then applies various ethical theories, including utilitarianism, deontological ethics, contract theory, and virtue ethics, to evaluate the morality of such actions. It argues that copying code is unethical and illegal, regardless of the intent, and could lead to legal repercussions. The application of these theories emphasizes the importance of honesty, respect, and trust in the workplace and the potential impact of unethical behavior on an organization's reputation and legal standing. The essay concludes by advocating for proper measures to ensure ethical and legal conduct within organizations, especially in software development.

Running head: TOPIC IN IT ETHICS
ANALYSIS OF ETHICAL THEORY
Name of the Student
Name of the University
Author Note
ANALYSIS OF ETHICAL THEORY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TOPIC IN IT ETHICS
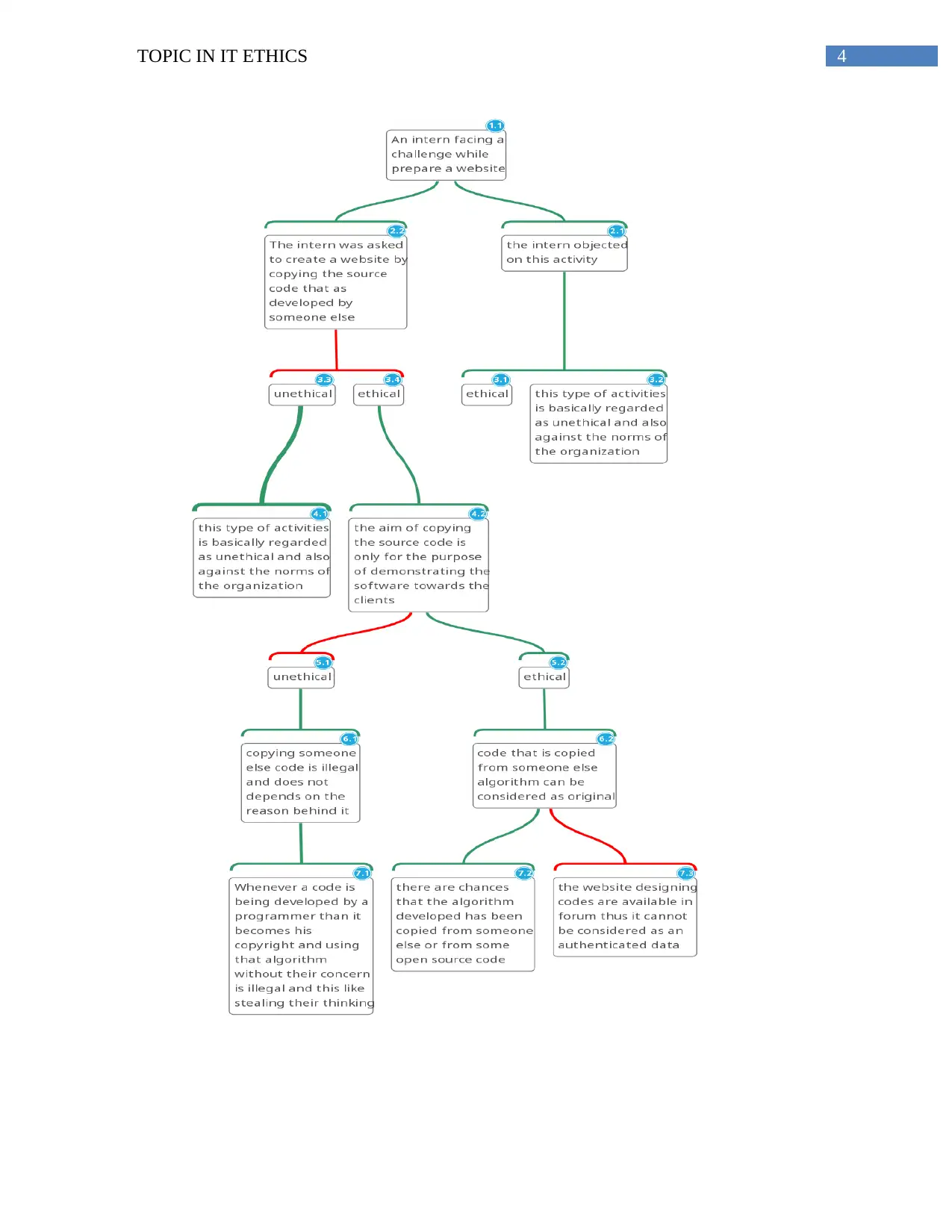
Dilemma faced by programmers regarding the unethical and illegal activities
From the case study it is being analyzed that sometimes employees within an
organization are asked to perform unethical activities even when they are not willing to do so.
Thus the article stated that the programmers had a discussion within an organization regarding
the unethical activities they are asked to perform within the organization. There are several
issues that came up regarding the programmer. Among this issues one of the issue that was
reported is regarding an intern facing a challenge while prepare a website. The intern was asked
to create a website by copying the source code that as developed by someone else. Thus this type
of activities is basically regarded as unethical and also against the norms of the organization.
Moreover when the intern objected on this activity he was being stated that the aim of copying
the source code is only for the purpose of demonstrating the software towards the clients. This
situation is referred to one of the illegal activities that take place within the organization.
However copying someone else code is illegal and does not depends on the reason behind it.
Stealing someone’s’ else data for personal use is against the IT ethics. Whenever a code is being
developed by a programmer than it becomes his copyright and using that algorithm without their
concern is illegal and this like stealing their thinking. In addition to this the code developed by
every developer varies widely as this are based on thinking level of the programmers.
According to the company the logic used behind the argument is that the code that is
copied from someone else algorithm can be considered as original, despite there are chances that
the algorithm developed has been copied from someone else or from some open source code.
The logic behind stating this statement is that with the growing knowledge the website designing
codes are available in forum thus it cannot be considered as an authenticated data.
Dilemma faced by programmers regarding the unethical and illegal activities
From the case study it is being analyzed that sometimes employees within an
organization are asked to perform unethical activities even when they are not willing to do so.
Thus the article stated that the programmers had a discussion within an organization regarding
the unethical activities they are asked to perform within the organization. There are several
issues that came up regarding the programmer. Among this issues one of the issue that was
reported is regarding an intern facing a challenge while prepare a website. The intern was asked
to create a website by copying the source code that as developed by someone else. Thus this type
of activities is basically regarded as unethical and also against the norms of the organization.
Moreover when the intern objected on this activity he was being stated that the aim of copying
the source code is only for the purpose of demonstrating the software towards the clients. This
situation is referred to one of the illegal activities that take place within the organization.
However copying someone else code is illegal and does not depends on the reason behind it.
Stealing someone’s’ else data for personal use is against the IT ethics. Whenever a code is being
developed by a programmer than it becomes his copyright and using that algorithm without their
concern is illegal and this like stealing their thinking. In addition to this the code developed by
every developer varies widely as this are based on thinking level of the programmers.
According to the company the logic used behind the argument is that the code that is
copied from someone else algorithm can be considered as original, despite there are chances that
the algorithm developed has been copied from someone else or from some open source code.
The logic behind stating this statement is that with the growing knowledge the website designing
codes are available in forum thus it cannot be considered as an authenticated data.

2TOPIC IN IT ETHICS
The ethical theory helps in analyzing the activities effectively and also checks whether
the organization is performing the activities effectively or not by following proper ethical rules.
As per the utilitarianism ethical theory an act is considered to be ethical whenever it produces
greatest goods towards the organization or a number of people. People associated with the
organization should be benefitted. However after analyzing the case that took place in this
organization it can be stated that the act of copying someone else’s code will be beneficial for the
organization but on a long term will have some repercussion. There is a high chance that the
company will face legal action in future if this situation gets revealed. This will impact the
reputation of the organization and will also impact the client’s future. Thus this kind of act has
the potential to impact the organization on long term and will impact everyone associated with
the organization.
The deontological theory of ethics states that if any action performed by an
individual needs to be assessed than it should be evaluated on the basis of rightness or wrongness
of that action. That is it should focus on the right implication rather than focusing on the outcome
of the action. Thus it can be stated that the morality of any activity needs to be judged based on
the nature of the action rather than focusing on the results that will come with the action.
However the act of copying someone else’s data cannot be justified with any argument. This act
will always remain illegal as there is a need to have proper permission from the owner code
before copying or manipulating the code for personal use. In addition to this the act of copying
someone code is not only illegal but is also against the ethics for an organization. Moreover there
is a high chance for the organization to face legal consequences at future. In case the
organization is able to hide this incident from others than it will become easy to manage the
The ethical theory helps in analyzing the activities effectively and also checks whether
the organization is performing the activities effectively or not by following proper ethical rules.
As per the utilitarianism ethical theory an act is considered to be ethical whenever it produces
greatest goods towards the organization or a number of people. People associated with the
organization should be benefitted. However after analyzing the case that took place in this
organization it can be stated that the act of copying someone else’s code will be beneficial for the
organization but on a long term will have some repercussion. There is a high chance that the
company will face legal action in future if this situation gets revealed. This will impact the
reputation of the organization and will also impact the client’s future. Thus this kind of act has
the potential to impact the organization on long term and will impact everyone associated with
the organization.
The deontological theory of ethics states that if any action performed by an
individual needs to be assessed than it should be evaluated on the basis of rightness or wrongness
of that action. That is it should focus on the right implication rather than focusing on the outcome
of the action. Thus it can be stated that the morality of any activity needs to be judged based on
the nature of the action rather than focusing on the results that will come with the action.
However the act of copying someone else’s data cannot be justified with any argument. This act
will always remain illegal as there is a need to have proper permission from the owner code
before copying or manipulating the code for personal use. In addition to this the act of copying
someone code is not only illegal but is also against the ethics for an organization. Moreover there
is a high chance for the organization to face legal consequences at future. In case the
organization is able to hide this incident from others than it will become easy to manage the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3TOPIC IN IT ETHICS
details within the organization. Thus after analyzing the theory with the case study it can be
stated that this act cannot be treated as an ethical one.
The third theory of ethic is contract theory that states if any action is performed based on
the agreement than it can be stated that the plan is legal for the organization. Whenever a client
approaches an organization for a new website generation than he will never expect to have a
code that is being copied from somewhere else. After analyzing the activity the theory states that
this act is not illegal.
The theory of virtue ethics states that ethical aspect of every activity needs to be assessed
based on the moral character of a person that will help in executing the activity. Thus virtue
ethics from actions needs to be analyzed effectively.
While working within the organization it is important to work towards the virtues related
to every individual this virtue includes honesty, respect, commitment and trust. Thus when a
organization or an individual tries to steal information from somewhere without their permission
or acknowledgement than it leads to violation of honesty and trust. Moreover when the
organization aims at delivering the project they are not disclosing the original facts. In this
situation the legal aspects gets violated again. Thus the organization faces huge legal and ethical
issues. This will impact the working of the organization and thus will hamper the benefits
obtained. Therefore it can be stated that the professional ethics gets impacted with this kinds of
activity. Thus the activity of stealing the data from someone else will be treated as illegal and
will be against moral virtues. Hence it can be concluded that the activity is not ethically correct
and the project manager needs to implement proper measures for having better control over the
organization. This will ensure that the activities are performed legally within the organization.
details within the organization. Thus after analyzing the theory with the case study it can be
stated that this act cannot be treated as an ethical one.
The third theory of ethic is contract theory that states if any action is performed based on
the agreement than it can be stated that the plan is legal for the organization. Whenever a client
approaches an organization for a new website generation than he will never expect to have a
code that is being copied from somewhere else. After analyzing the activity the theory states that
this act is not illegal.
The theory of virtue ethics states that ethical aspect of every activity needs to be assessed
based on the moral character of a person that will help in executing the activity. Thus virtue
ethics from actions needs to be analyzed effectively.
While working within the organization it is important to work towards the virtues related
to every individual this virtue includes honesty, respect, commitment and trust. Thus when a
organization or an individual tries to steal information from somewhere without their permission
or acknowledgement than it leads to violation of honesty and trust. Moreover when the
organization aims at delivering the project they are not disclosing the original facts. In this
situation the legal aspects gets violated again. Thus the organization faces huge legal and ethical
issues. This will impact the working of the organization and thus will hamper the benefits
obtained. Therefore it can be stated that the professional ethics gets impacted with this kinds of
activity. Thus the activity of stealing the data from someone else will be treated as illegal and
will be against moral virtues. Hence it can be concluded that the activity is not ethically correct
and the project manager needs to implement proper measures for having better control over the
organization. This will ensure that the activities are performed legally within the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4TOPIC IN IT ETHICS

5TOPIC IN IT ETHICS
References
Ferrell, O. C. (2016). A framework for understanding organizational ethics. In Business ethics:
New challenges for business schools and corporate leaders (pp. 15-29). Routledge.
Harju, A. (2018). Mind map, MindMup: A material package of digitally available applications
for language teachers.
Lapsley, D. (2016). Moral self-identity and the social-cognitive theory of virtue. Developing the
virtues: Integrating perspectives, 34-68.
Macnamara, J. (2016). The continuing convergence of journalism and PR: New insights for
ethical practice from a three-country study of senior practitioners. Journalism & Mass
Communication Quarterly, 93(1), 118-141.
Martin, K. E. (2015). Ethical issues in the big data industry. MIS Quarterly Executive, 14, 2.
Vaughn, L. (2015). Doing ethics: Moral reasoning and contemporary issues. WW Norton &
Company.
References
Ferrell, O. C. (2016). A framework for understanding organizational ethics. In Business ethics:
New challenges for business schools and corporate leaders (pp. 15-29). Routledge.
Harju, A. (2018). Mind map, MindMup: A material package of digitally available applications
for language teachers.
Lapsley, D. (2016). Moral self-identity and the social-cognitive theory of virtue. Developing the
virtues: Integrating perspectives, 34-68.
Macnamara, J. (2016). The continuing convergence of journalism and PR: New insights for
ethical practice from a three-country study of senior practitioners. Journalism & Mass
Communication Quarterly, 93(1), 118-141.
Martin, K. E. (2015). Ethical issues in the big data industry. MIS Quarterly Executive, 14, 2.
Vaughn, L. (2015). Doing ethics: Moral reasoning and contemporary issues. WW Norton &
Company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




