Document on Network and Security
Added on 2020-04-07
20 Pages6226 Words54 Views
1. Application protocols(a) The HTTP is abbreviated as Hypertext transfer protocol. The HTTP is a application protocol in the distributedsystem, collaborative system and hypermedia systems. The HTTP is a kind of foundation in the data communicationon the internet. This is a kind of the structured text. This structured text will use the logical links known ashyperlinks. These links connected in nodes which have data. HTTP can be called as a protocol for the transferringdata. When user request for data the HTTP carries a request message to server and get the data. The first version ofHTTP was released in the year 1991 which is called as 0.9. The next version is 1.0 released in the year 1996. The 1.1version was released in the year 1997. The 2.0 version was released in the year 2015. The HTML is abbreviated asHypertext markup language. The HTML is a standard of markup language. The HTML is used for creating the pagesand applications in web with CCS, cascading style sheets. They also use JAVA script for World Wide Web. This willgenerally gives the structure of web page [1]. (b) The HTTP 1.1 has many advantages. It has Extensibility which makes compatibility with many other versions andsoftwares. The Caching will make device faster. It has best Bandwidth optimization. The Network kind of connectionmanagement is very good. It has best Message transmission facility. The Internet address related conservation isalso good [4]. The Error notification is also better. The Security high is with best integrity and the authentication. (c) The cookies are never a good idea. If someone is sending them try to warn them not to do so. You also never tryto send them back. If they are sending back again and again try to block them or take serious issue with cyberofficials. (d) ASCII is abbreviated as American standard code for information interchange. This is a kind of informationexchange system for the electronics and communications. The ASCII is generally used in computers and thecommunication systems. This is one of the best encoding system [3 ]. There are many advantages. ASCII will allow allthe computers to use the similar input data and the input characters. This is one of the standard code will allow tocreate many file possible. The general length of ASCII is 7 bit but the 7 bits will allow to store 128 binary patterns.And so on with the increase in character length and the bit length. 2. Application and security protocols(a) API is abbreviated as application program interface. The API are set of some proceduresLike protocol and some tools in the process of building software’s and its applications. We know the graphic userinterfaces will help the users in many ways, similarly the API will help the programmers for developing newsoftware. This is one way of integration of technology with the business models and other systems. This is one of thebest business ecosystems. The APIs are like blocks and one must integrate the blocks. They all must be joined for theforming a good system. The API can be applied to any systems like web technology, data systems, hardware of the

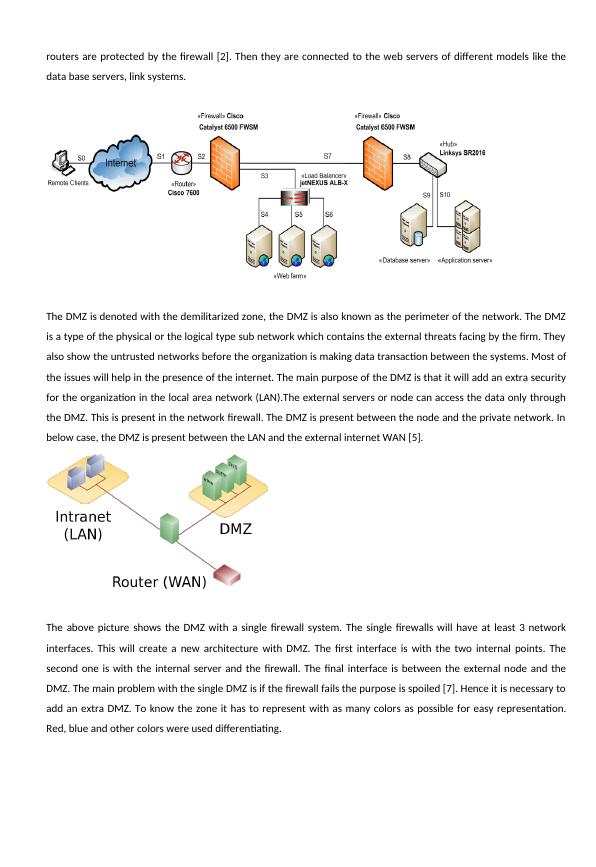
computers and many more. There is a concept known as the API calls. In this a call made by the user to server isknown as API call or the request. (b) In the given problem the Berkeley socket is discussed. Here the socket is a API to the internet with the Unix domainsocket are also used in IPC. The IPC is abbreviated as inter process communication. The IPC is used as linkablemodules. The socket is defined as an abstract place or the endpoint in the network or the communication path. TheBerkeley socket is a API which tells about the common interface to the input and output for the data. The next typeof Berkeley socket is the POSIX sockets. This is also termed as BSD socket. There are few things which are done bythe POSIX. They are the conversion of the text address into a packed address. The next one is to convert from thepacked address into the text address. The next kind is the forward lookup into a host name or service. The final oneis the reverse lookup to host name or the service. (c) Let us discuss some of the causes for the above question. In the data communication or the access the team of thenetwork security needs some kind of information for providing the access to the licensing the components. Some of the best examples for this kind of solution are the explained in the IBM model. In this they need somelicense key for the server access. This license is known as the floating license key. Few of it are imaged- this is alicense manager demon. The next kind is the vendor demon. They are denoted with key names like immortal, thenext one is the rational and the final one is the telelogic. Here the manager demon and the vendor demon both of the demons use the TCP to communicate, the applicationlayer protocol take control of the FLEXnet publisher which is proprietary over the TCP/IP. (d) When the license manger is involved with sending a hardware key for the client, then there are three cases, first oneis the accepted, next rejected and the final one is the expired. If the user is asking the same question after and afterfor the long time then they must check the process. There is a possible attacks in the communication. There are twocases of attacks, first one is the middle man attack and the next one is the end user attack. These can happenbecause if the third person is involving in your communication path. The best way to avoid these kind of problemsare by establishing the secure communication. Some of them are the encoding the key or data, the next one is theacknowledgement based method. 3.(a) The below system will not use the NAT, this is a non NAT model. This contains the remote clients, which is anend user. The remote client is connected to the internet. The internet access is done with the help of routers. The

routers are protected by the firewall [2]. Then they are connected to the web servers of different models like thedata base servers, link systems. The DMZ is denoted with the demilitarized zone, the DMZ is also known as the perimeter of the network. The DMZis a type of the physical or the logical type sub network which contains the external threats facing by the firm. Theyalso show the untrusted networks before the organization is making data transaction between the systems. Most ofthe issues will help in the presence of the internet. The main purpose of the DMZ is that it will add an extra securityfor the organization in the local area network (LAN).The external servers or node can access the data only throughthe DMZ. This is present in the network firewall. The DMZ is present between the node and the private network. Inbelow case, the DMZ is present between the LAN and the external internet WAN [5]. The above picture shows the DMZ with a single firewall system. The single firewalls will have at least 3 networkinterfaces. This will create a new architecture with DMZ. The first interface is with the two internal points. Thesecond one is with the internal server and the firewall. The final interface is between the external node and theDMZ. The main problem with the single DMZ is if the firewall fails the purpose is spoiled [7]. Hence it is necessary toadd an extra DMZ. To know the zone it has to represent with as many colors as possible for easy representation.Red, blue and other colors were used differentiating.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Evaluation of Web Testing Toollg...
|60
|10977
|230
Webpage Designlg...
|4
|652
|90
Web System Testing Tools - Doclg...
|5
|1186
|172
(PDF) Peer-to-peer (P2P) file sharing systemlg...
|5
|709
|195
Network Layerlg...
|7
|1165
|27
Implementing Security Architecture - Incorporating DMTFlg...
|4
|762
|19
