Agency Risk Assessment 2022
This assignment requires you to plan, conduct and document a risk assessment based on a given scenario.
11 Pages2651 Words19 Views
Added on 2022-09-14
Agency Risk Assessment 2022
This assignment requires you to plan, conduct and document a risk assessment based on a given scenario.
Added on 2022-09-14
ShareRelated Documents
Assessment No:
Assessment Title:
Student Name & ID:
Subject Name and Code:
Student Email Address:
Assessment Title:
Student Name & ID:
Subject Name and Code:
Student Email Address:

UCLanRE Agency Risk Assessment
2
Table of Contents
Introduction................................................................................................................ 3
Risk Assessment......................................................................................................... 4
Risk identification.................................................................................................... 4
Assets................................................................................................................... 5
Threats................................................................................................................. 6
Vulnerabilities...................................................................................................... 7
Risk analysis and risk evaluation............................................................................. 7
Risk assessment with a quantitative method..........................................................7
Risk treatment......................................................................................................... 8
Risk acceptance and residual risk management.....................................................9
Information Security Risk Communication and Consultation...................................9
Risk monitoring and review..................................................................................... 9
Summary and Recommendations............................................................................... 9
References............................................................................................................... 11
2
Table of Contents
Introduction................................................................................................................ 3
Risk Assessment......................................................................................................... 4
Risk identification.................................................................................................... 4
Assets................................................................................................................... 5
Threats................................................................................................................. 6
Vulnerabilities...................................................................................................... 7
Risk analysis and risk evaluation............................................................................. 7
Risk assessment with a quantitative method..........................................................7
Risk treatment......................................................................................................... 8
Risk acceptance and residual risk management.....................................................9
Information Security Risk Communication and Consultation...................................9
Risk monitoring and review..................................................................................... 9
Summary and Recommendations............................................................................... 9
References............................................................................................................... 11

UCLanRE Agency Risk Assessment
3
Introduction
Risks analysis and assessment is one of the initial steps and primary way to
advance the security of an information system of an organization. For sure,
optimization implies input of more effort. Furthermore, it means doing it with
minimum resources (Institute, 2017). This means that if we ignore to analyze and
assess risks surrounding our IT infrastructure for fear of incurring a small cost, we
must be prepared to pay huge chunks of money once havoc has been caused. With
the enthusiasm of having enough security and minimize costs caused by insecurity
elements, risk analysis and assessment is very imperative for each IT environment.
It should be noted that risk management has been already incorporated in many of
the business enterprises of all kinds (Aven & Zio, 2018). It is so surprising how
UCLanRE agency is lacking this basic requirement since the computers were
introduced into the business environments. IT risk ought to have been taken care a
long time ago. In addition, the computer system is now in charge of critical
operations of UCLanRE agency processes, and IT risk assessment becomes one of
the primary risks of the agency today.
Risk assessment denotes to the determination of the value of risk in the relation of
the tangible situation and a known vulnerability on the basis of probability and the
impact. The risk level is as a result of the mentioned two factors. Risk assessment
for IT Infrastructure for an organization can take either qualitative or quantitative
risk assessment approaches (Dalezios, 2017). In our exercise of risk assessment for
UCLanRE agency, we will deploy a quantitative risk assessment approach.
This paper presents a risk assessment for UCLanRE agency in the following steps:
3
Introduction
Risks analysis and assessment is one of the initial steps and primary way to
advance the security of an information system of an organization. For sure,
optimization implies input of more effort. Furthermore, it means doing it with
minimum resources (Institute, 2017). This means that if we ignore to analyze and
assess risks surrounding our IT infrastructure for fear of incurring a small cost, we
must be prepared to pay huge chunks of money once havoc has been caused. With
the enthusiasm of having enough security and minimize costs caused by insecurity
elements, risk analysis and assessment is very imperative for each IT environment.
It should be noted that risk management has been already incorporated in many of
the business enterprises of all kinds (Aven & Zio, 2018). It is so surprising how
UCLanRE agency is lacking this basic requirement since the computers were
introduced into the business environments. IT risk ought to have been taken care a
long time ago. In addition, the computer system is now in charge of critical
operations of UCLanRE agency processes, and IT risk assessment becomes one of
the primary risks of the agency today.
Risk assessment denotes to the determination of the value of risk in the relation of
the tangible situation and a known vulnerability on the basis of probability and the
impact. The risk level is as a result of the mentioned two factors. Risk assessment
for IT Infrastructure for an organization can take either qualitative or quantitative
risk assessment approaches (Dalezios, 2017). In our exercise of risk assessment for
UCLanRE agency, we will deploy a quantitative risk assessment approach.
This paper presents a risk assessment for UCLanRE agency in the following steps:

UCLanRE Agency Risk Assessment
4
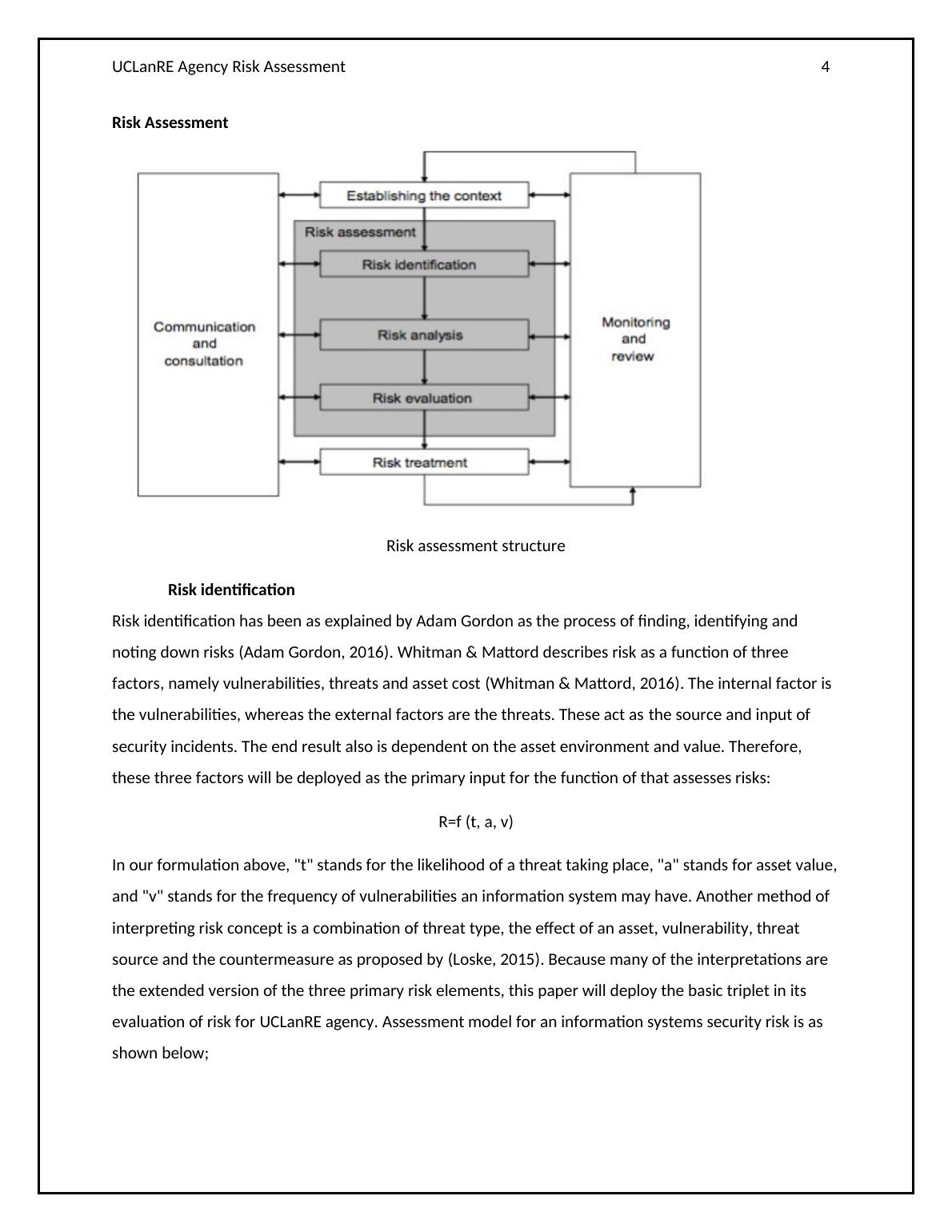
Risk Assessment
Risk assessment structure
Risk identification
Risk identification has been as explained by Adam Gordon as the process of finding,
identifying and noting down risks (Adam Gordon, 2016). Whitman & Mattord
describes risk as a function of three factors, namely vulnerabilities, threats and
asset cost (Whitman & Mattord, 2016). The internal factor is the vulnerabilities,
whereas the external factors are the threats. These act as the source and input of
security incidents. The end result also is dependent on the asset environment and
value. Therefore, these three factors will be deployed as the primary input for the
function of that assesses risks:
R=f (t, a, v)
In our formulation above, "t" stands for the likelihood of a threat taking place, "a"
stands for asset value, and "v" stands for the frequency of vulnerabilities an
information system may have. Another method of interpreting risk concept is a
combination of threat type, the effect of an asset, vulnerability, threat source and
the countermeasure as proposed by (Loske, 2015). Because many of the
interpretations are the extended version of the three primary risk elements, this
4
Risk Assessment
Risk assessment structure
Risk identification
Risk identification has been as explained by Adam Gordon as the process of finding,
identifying and noting down risks (Adam Gordon, 2016). Whitman & Mattord
describes risk as a function of three factors, namely vulnerabilities, threats and
asset cost (Whitman & Mattord, 2016). The internal factor is the vulnerabilities,
whereas the external factors are the threats. These act as the source and input of
security incidents. The end result also is dependent on the asset environment and
value. Therefore, these three factors will be deployed as the primary input for the
function of that assesses risks:
R=f (t, a, v)
In our formulation above, "t" stands for the likelihood of a threat taking place, "a"
stands for asset value, and "v" stands for the frequency of vulnerabilities an
information system may have. Another method of interpreting risk concept is a
combination of threat type, the effect of an asset, vulnerability, threat source and
the countermeasure as proposed by (Loske, 2015). Because many of the
interpretations are the extended version of the three primary risk elements, this
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Information System Security Management Report 2022lg...
|18
|4538
|10
Report on Implementing Security Management Program at Griffith University Medical GUMClg...
|16
|3393
|138
Security Risk Analysislg...
|7
|1068
|24
