Detailed Analysis of the Ukraine Power Grid Cybersecurity Case Study
VerifiedAdded on 2023/06/09
|21
|3498
|492
Case Study
AI Summary
This case study analyzes the cybersecurity risks and operational resilience of the Ukraine Power Grid. It begins with an inherent risk matrix, identifying vulnerabilities and their impact, including issues like insecure wireless connections, SCADA hijacking, and denial-of-service attacks. The study then recommends security mechanisms like encryption and firewalls. It further examines different operational domains, including communication, monitoring, knowledge management, compliance, and technology management, using the CERT Resilience Management Model. For each domain, it outlines goals, practices, and measurement techniques. A communication matrix is provided to outline communication strategies. The analysis also suggests additional security measures and provides recommendations for improving the power grid's overall security posture. Finally, it assesses controls and suggests countermeasures for identified risks, as well as identifies vulnerabilities by CVE and appropriate patch solutions.

Running head: UKRAINE POWER GRID
Case study: Ukraine Power Grid
Name of the student:
Name of the university:
Case study: Ukraine Power Grid
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1UKRAINE POWER GRID
Table of Contents
1. Inherent risk matrix for the Ukraine Power Grid case study.......................................................2
2. Different operational domains.....................................................................................................7
2.1 Communication......................................................................................................................7
2.2 Monitoring...........................................................................................................................13
2.3 Knowledge and information management (KIM)...............................................................13
2.4 Compliance..........................................................................................................................13
2.5 Technology management.....................................................................................................14
3. Other appropriate measures.......................................................................................................14
3.1 Review and suggested changes for the policies to develop for the organization................14
3.2 Review and suggest controls required to countermeasure the risks and tolls available for
monitoring and measure the operational resilience...................................................................15
3.3 Identification of the vulnerabilities by CVE and appropriate patch solution to remediate
those...........................................................................................................................................15
References......................................................................................................................................17
Table of Contents
1. Inherent risk matrix for the Ukraine Power Grid case study.......................................................2
2. Different operational domains.....................................................................................................7
2.1 Communication......................................................................................................................7
2.2 Monitoring...........................................................................................................................13
2.3 Knowledge and information management (KIM)...............................................................13
2.4 Compliance..........................................................................................................................13
2.5 Technology management.....................................................................................................14
3. Other appropriate measures.......................................................................................................14
3.1 Review and suggested changes for the policies to develop for the organization................14
3.2 Review and suggest controls required to countermeasure the risks and tolls available for
monitoring and measure the operational resilience...................................................................15
3.3 Identification of the vulnerabilities by CVE and appropriate patch solution to remediate
those...........................................................................................................................................15
References......................................................................................................................................17
1UKRAINE POWER GRID
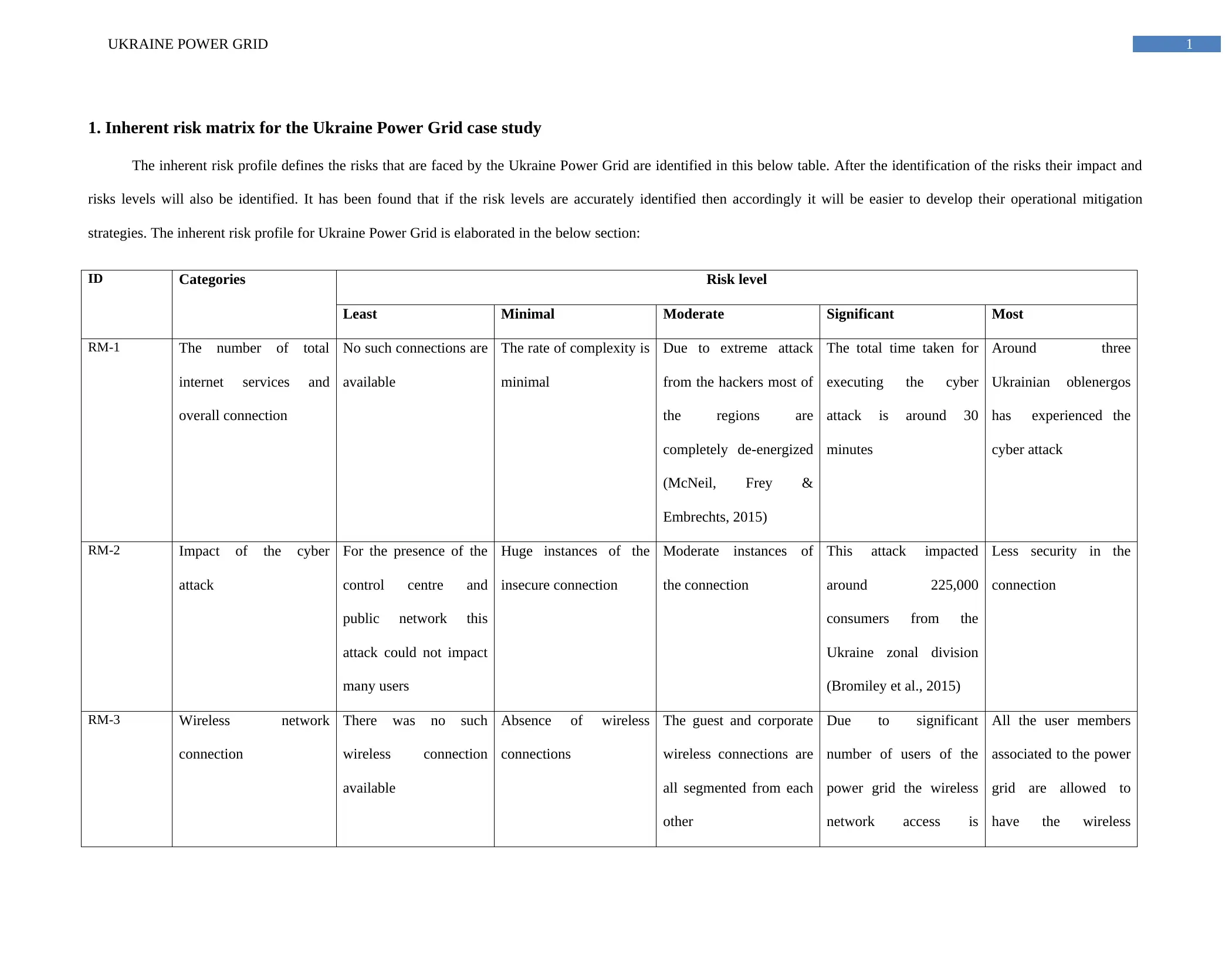
1. Inherent risk matrix for the Ukraine Power Grid case study
The inherent risk profile defines the risks that are faced by the Ukraine Power Grid are identified in this below table. After the identification of the risks their impact and
risks levels will also be identified. It has been found that if the risk levels are accurately identified then accordingly it will be easier to develop their operational mitigation
strategies. The inherent risk profile for Ukraine Power Grid is elaborated in the below section:
ID Categories Risk level
Least Minimal Moderate Significant Most
RM-1 The number of total
internet services and
overall connection
No such connections are
available
The rate of complexity is
minimal
Due to extreme attack
from the hackers most of
the regions are
completely de-energized
(McNeil, Frey &
Embrechts, 2015)
The total time taken for
executing the cyber
attack is around 30
minutes
Around three
Ukrainian oblenergos
has experienced the
cyber attack
RM-2 Impact of the cyber
attack
For the presence of the
control centre and
public network this
attack could not impact
many users
Huge instances of the
insecure connection
Moderate instances of
the connection
This attack impacted
around 225,000
consumers from the
Ukraine zonal division
(Bromiley et al., 2015)
Less security in the
connection
RM-3 Wireless network
connection
There was no such
wireless connection
available
Absence of wireless
connections
The guest and corporate
wireless connections are
all segmented from each
other
Due to significant
number of users of the
power grid the wireless
network access is
All the user members
associated to the power
grid are allowed to
have the wireless
1. Inherent risk matrix for the Ukraine Power Grid case study
The inherent risk profile defines the risks that are faced by the Ukraine Power Grid are identified in this below table. After the identification of the risks their impact and
risks levels will also be identified. It has been found that if the risk levels are accurately identified then accordingly it will be easier to develop their operational mitigation
strategies. The inherent risk profile for Ukraine Power Grid is elaborated in the below section:
ID Categories Risk level
Least Minimal Moderate Significant Most
RM-1 The number of total
internet services and
overall connection
No such connections are
available
The rate of complexity is
minimal
Due to extreme attack
from the hackers most of
the regions are
completely de-energized
(McNeil, Frey &
Embrechts, 2015)
The total time taken for
executing the cyber
attack is around 30
minutes
Around three
Ukrainian oblenergos
has experienced the
cyber attack
RM-2 Impact of the cyber
attack
For the presence of the
control centre and
public network this
attack could not impact
many users
Huge instances of the
insecure connection
Moderate instances of
the connection
This attack impacted
around 225,000
consumers from the
Ukraine zonal division
(Bromiley et al., 2015)
Less security in the
connection
RM-3 Wireless network
connection
There was no such
wireless connection
available
Absence of wireless
connections
The guest and corporate
wireless connections are
all segmented from each
other
Due to significant
number of users of the
power grid the wireless
network access is
All the user members
associated to the power
grid are allowed to
have the wireless
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2UKRAINE POWER GRID
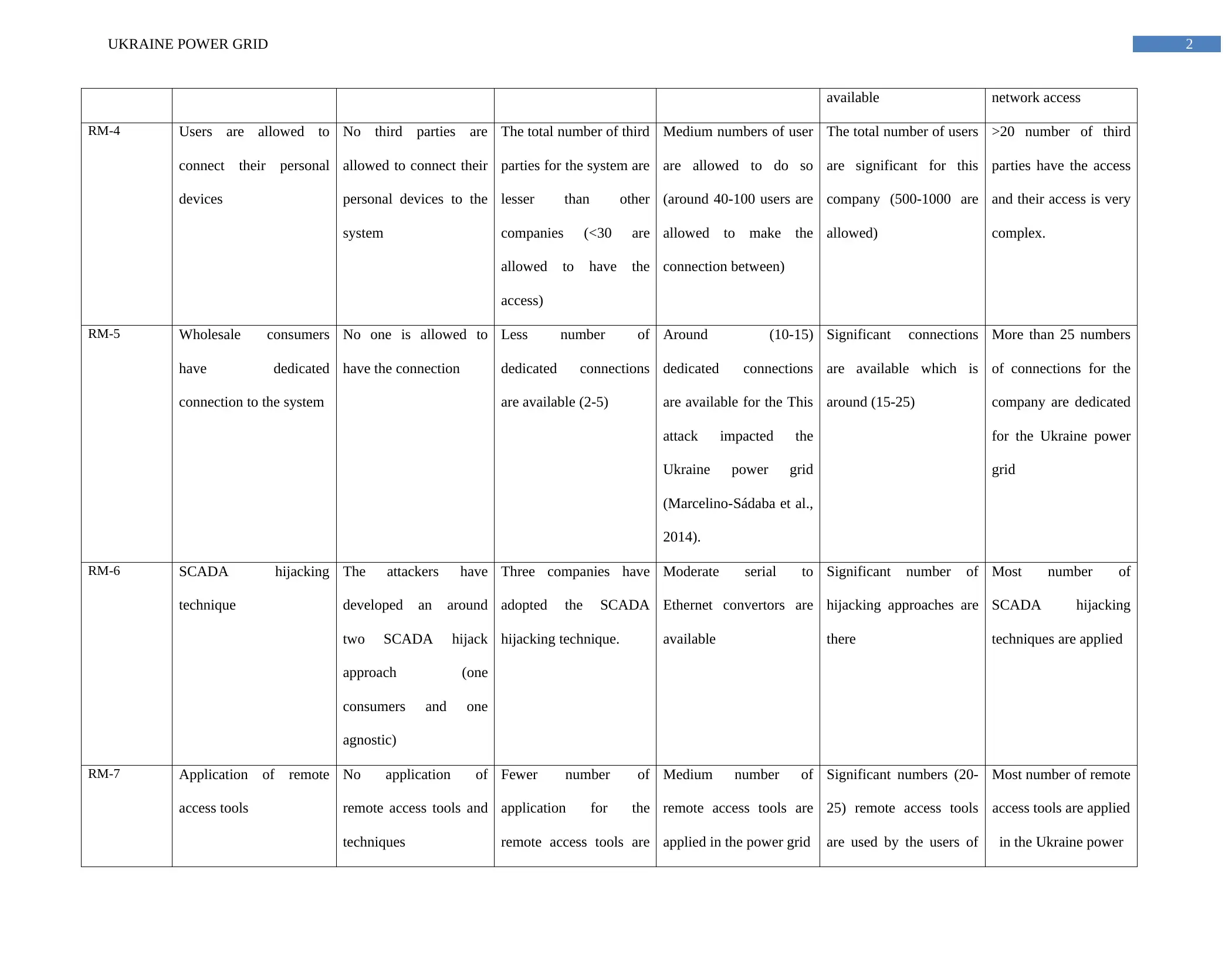
available network access
RM-4 Users are allowed to
connect their personal
devices
No third parties are
allowed to connect their
personal devices to the
system
The total number of third
parties for the system are
lesser than other
companies (<30 are
allowed to have the
access)
Medium numbers of user
are allowed to do so
(around 40-100 users are
allowed to make the
connection between)
The total number of users
are significant for this
company (500-1000 are
allowed)
>20 number of third
parties have the access
and their access is very
complex.
RM-5 Wholesale consumers
have dedicated
connection to the system
No one is allowed to
have the connection
Less number of
dedicated connections
are available (2-5)
Around (10-15)
dedicated connections
are available for the This
attack impacted the
Ukraine power grid
(Marcelino-Sádaba et al.,
2014).
Significant connections
are available which is
around (15-25)
More than 25 numbers
of connections for the
company are dedicated
for the Ukraine power
grid
RM-6 SCADA hijacking
technique
The attackers have
developed an around
two SCADA hijack
approach (one
consumers and one
agnostic)
Three companies have
adopted the SCADA
hijacking technique.
Moderate serial to
Ethernet convertors are
available
Significant number of
hijacking approaches are
there
Most number of
SCADA hijacking
techniques are applied
RM-7 Application of remote
access tools
No application of
remote access tools and
techniques
Fewer number of
application for the
remote access tools are
Medium number of
remote access tools are
applied in the power grid
Significant numbers (20-
25) remote access tools
are used by the users of
Most number of remote
access tools are applied
in the Ukraine power
available network access
RM-4 Users are allowed to
connect their personal
devices
No third parties are
allowed to connect their
personal devices to the
system
The total number of third
parties for the system are
lesser than other
companies (<30 are
allowed to have the
access)
Medium numbers of user
are allowed to do so
(around 40-100 users are
allowed to make the
connection between)
The total number of users
are significant for this
company (500-1000 are
allowed)
>20 number of third
parties have the access
and their access is very
complex.
RM-5 Wholesale consumers
have dedicated
connection to the system
No one is allowed to
have the connection
Less number of
dedicated connections
are available (2-5)
Around (10-15)
dedicated connections
are available for the This
attack impacted the
Ukraine power grid
(Marcelino-Sádaba et al.,
2014).
Significant connections
are available which is
around (15-25)
More than 25 numbers
of connections for the
company are dedicated
for the Ukraine power
grid
RM-6 SCADA hijacking
technique
The attackers have
developed an around
two SCADA hijack
approach (one
consumers and one
agnostic)
Three companies have
adopted the SCADA
hijacking technique.
Moderate serial to
Ethernet convertors are
available
Significant number of
hijacking approaches are
there
Most number of
SCADA hijacking
techniques are applied
RM-7 Application of remote
access tools
No application of
remote access tools and
techniques
Fewer number of
application for the
remote access tools are
Medium number of
remote access tools are
applied in the power grid
Significant numbers (20-
25) remote access tools
are used by the users of
Most number of remote
access tools are applied
in the Ukraine power
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3UKRAINE POWER GRID
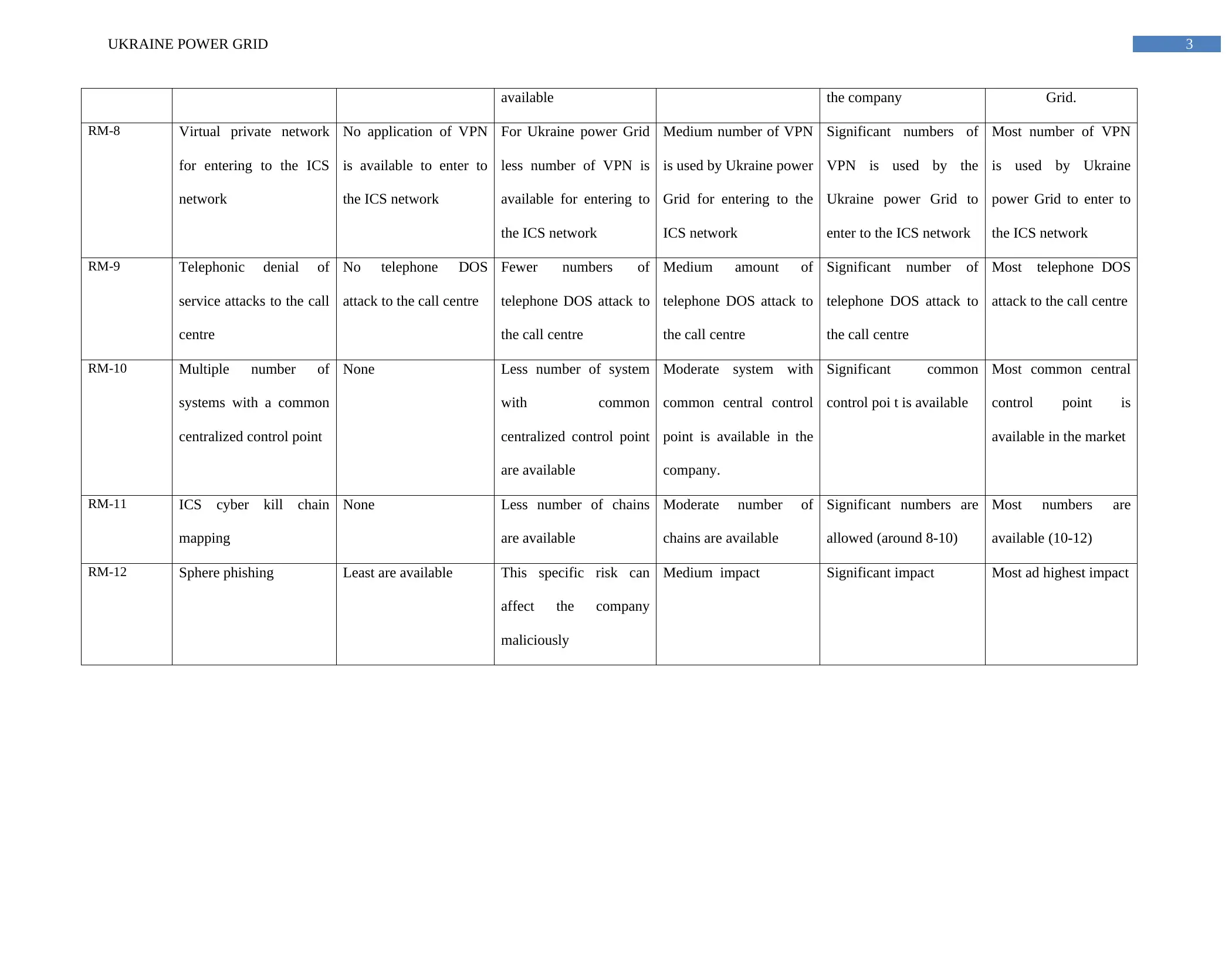
available the company Grid.
RM-8 Virtual private network
for entering to the ICS
network
No application of VPN
is available to enter to
the ICS network
For Ukraine power Grid
less number of VPN is
available for entering to
the ICS network
Medium number of VPN
is used by Ukraine power
Grid for entering to the
ICS network
Significant numbers of
VPN is used by the
Ukraine power Grid to
enter to the ICS network
Most number of VPN
is used by Ukraine
power Grid to enter to
the ICS network
RM-9 Telephonic denial of
service attacks to the call
centre
No telephone DOS
attack to the call centre
Fewer numbers of
telephone DOS attack to
the call centre
Medium amount of
telephone DOS attack to
the call centre
Significant number of
telephone DOS attack to
the call centre
Most telephone DOS
attack to the call centre
RM-10 Multiple number of
systems with a common
centralized control point
None Less number of system
with common
centralized control point
are available
Moderate system with
common central control
point is available in the
company.
Significant common
control poi t is available
Most common central
control point is
available in the market
RM-11 ICS cyber kill chain
mapping
None Less number of chains
are available
Moderate number of
chains are available
Significant numbers are
allowed (around 8-10)
Most numbers are
available (10-12)
RM-12 Sphere phishing Least are available This specific risk can
affect the company
maliciously
Medium impact Significant impact Most ad highest impact
available the company Grid.
RM-8 Virtual private network
for entering to the ICS
network
No application of VPN
is available to enter to
the ICS network
For Ukraine power Grid
less number of VPN is
available for entering to
the ICS network
Medium number of VPN
is used by Ukraine power
Grid for entering to the
ICS network
Significant numbers of
VPN is used by the
Ukraine power Grid to
enter to the ICS network
Most number of VPN
is used by Ukraine
power Grid to enter to
the ICS network
RM-9 Telephonic denial of
service attacks to the call
centre
No telephone DOS
attack to the call centre
Fewer numbers of
telephone DOS attack to
the call centre
Medium amount of
telephone DOS attack to
the call centre
Significant number of
telephone DOS attack to
the call centre
Most telephone DOS
attack to the call centre
RM-10 Multiple number of
systems with a common
centralized control point
None Less number of system
with common
centralized control point
are available
Moderate system with
common central control
point is available in the
company.
Significant common
control poi t is available
Most common central
control point is
available in the market
RM-11 ICS cyber kill chain
mapping
None Less number of chains
are available
Moderate number of
chains are available
Significant numbers are
allowed (around 8-10)
Most numbers are
available (10-12)
RM-12 Sphere phishing Least are available This specific risk can
affect the company
maliciously
Medium impact Significant impact Most ad highest impact

4UKRAINE POWER GRID
Recommendations for the missing information
Though many significant security measures are considered in the risk matrix but
still certain additional security measures are needed for successfully mitigated the issues.
For the missing information the security based recommendations those are to be
incorporated are elaborated below:
Security mechanism Description
Encryption technology Encryption mechanism is referred to as a
very important mechanism that is widely
used by the business organizations to keep
their information confidentiality secured
from the external attackers. In case of
encryption technology a shared key is used
by both the service providers and the
receiver. The key must not be shared with
any of third parties (Elzamly & Hussin, B.
(2015). It is expected that, with the
successful usage of the encryption
technology none of the unwanted users will
be able to access information from the
server without permission
Firewall technology Application firewall is another mechanism
must be used by the Ukraine power Grid to
keep their information secured from the
Recommendations for the missing information
Though many significant security measures are considered in the risk matrix but
still certain additional security measures are needed for successfully mitigated the issues.
For the missing information the security based recommendations those are to be
incorporated are elaborated below:
Security mechanism Description
Encryption technology Encryption mechanism is referred to as a
very important mechanism that is widely
used by the business organizations to keep
their information confidentiality secured
from the external attackers. In case of
encryption technology a shared key is used
by both the service providers and the
receiver. The key must not be shared with
any of third parties (Elzamly & Hussin, B.
(2015). It is expected that, with the
successful usage of the encryption
technology none of the unwanted users will
be able to access information from the
server without permission
Firewall technology Application firewall is another mechanism
must be used by the Ukraine power Grid to
keep their information secured from the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
5UKRAINE POWER GRID
external attackers. The information
transmission channel will be keep secured
from the external attackers if proper
firewall application technologies are
applied by the company (Brisley et al.,
2016). The Seven layered protection
approach can integrate the mitigation
strategies all together with the DDOS
attack. It prevents the data leakage.
2. Different operational domains
Different operations domains are being identified for the Ukraine Power Grid and
the generic goal for managing the metrics are summaries in the below table:
GG2.GP1 Process governance establishment
GG2.GP2 Assigning responsibilities
GG2.GP3 Resource allocation
GG2.GP4 Responsibility assigning
GG2.GP5 Arrangement of training
GG2.GP6 Managing product configuration
GG2.GP7 Stakeholder identification
GG2.GP8 Process of monitoring and control
GG2.GP9 Process evaluation
external attackers. The information
transmission channel will be keep secured
from the external attackers if proper
firewall application technologies are
applied by the company (Brisley et al.,
2016). The Seven layered protection
approach can integrate the mitigation
strategies all together with the DDOS
attack. It prevents the data leakage.
2. Different operational domains
Different operations domains are being identified for the Ukraine Power Grid and
the generic goal for managing the metrics are summaries in the below table:
GG2.GP1 Process governance establishment
GG2.GP2 Assigning responsibilities
GG2.GP3 Resource allocation
GG2.GP4 Responsibility assigning
GG2.GP5 Arrangement of training
GG2.GP6 Managing product configuration
GG2.GP7 Stakeholder identification
GG2.GP8 Process of monitoring and control
GG2.GP9 Process evaluation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6UKRAINE POWER GRID
GG2.GP10 Project and process status review by the
senior managers
2.1 Communication
It is necessary for Ukraine Power Grid to design proper communication matrix
through which the company will be able to know the details approach of communication
that a company must utilize to avoid internal conflict. The communication details are
elaborated in the below section:
GG2.GP10 Project and process status review by the
senior managers
2.1 Communication
It is necessary for Ukraine Power Grid to design proper communication matrix
through which the company will be able to know the details approach of communication
that a company must utilize to avoid internal conflict. The communication details are
elaborated in the below section:
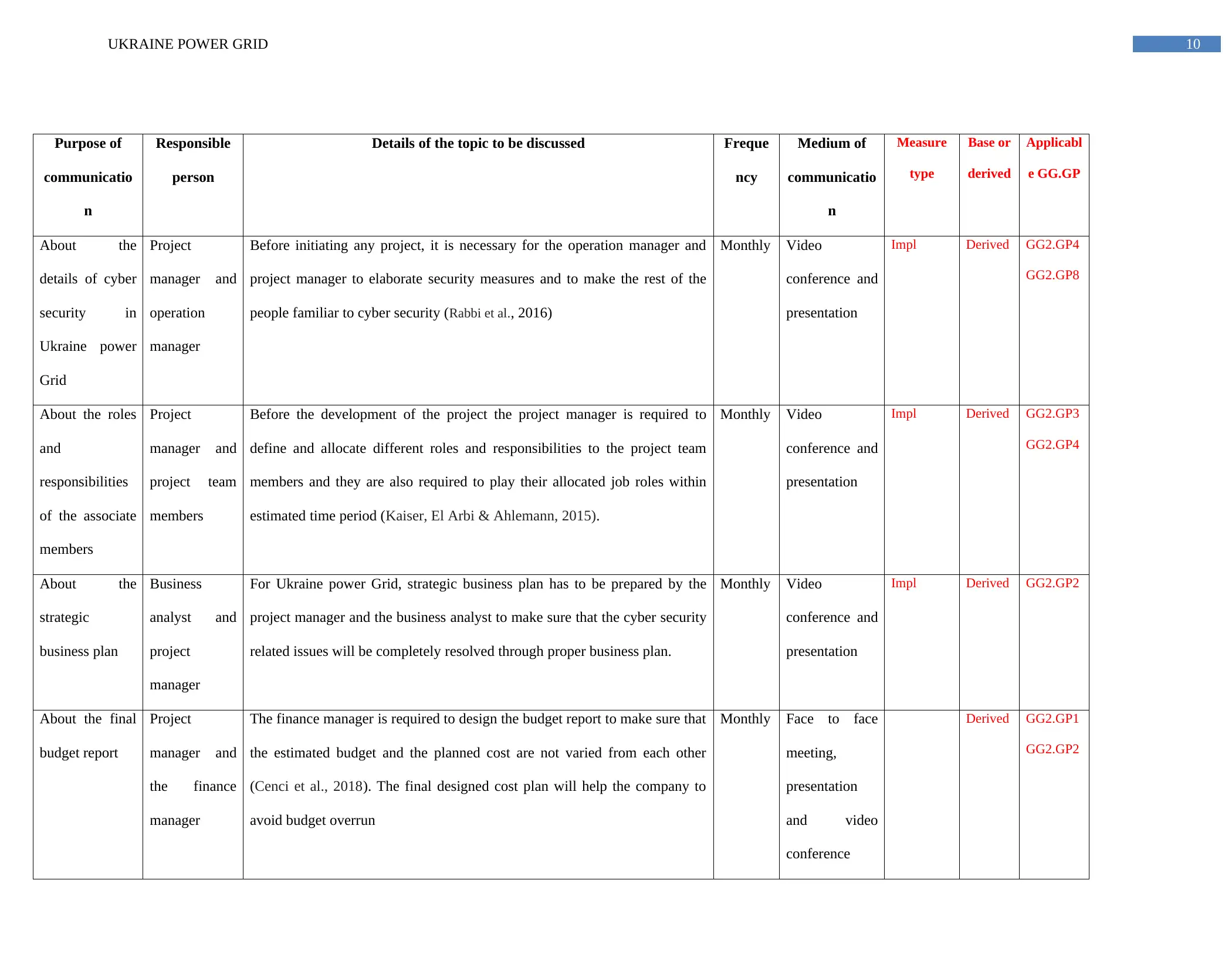
10UKRAINE POWER GRID
Purpose of
communicatio
n
Responsible
person
Details of the topic to be discussed Freque
ncy
Medium of
communicatio
n
Measure
type
Base or
derived
Applicabl
e GG.GP
About the
details of cyber
security in
Ukraine power
Grid
Project
manager and
operation
manager
Before initiating any project, it is necessary for the operation manager and
project manager to elaborate security measures and to make the rest of the
people familiar to cyber security (Rabbi et al., 2016)
Monthly Video
conference and
presentation
Impl Derived GG2.GP4
GG2.GP8
About the roles
and
responsibilities
of the associate
members
Project
manager and
project team
members
Before the development of the project the project manager is required to
define and allocate different roles and responsibilities to the project team
members and they are also required to play their allocated job roles within
estimated time period (Kaiser, El Arbi & Ahlemann, 2015).
Monthly Video
conference and
presentation
Impl Derived GG2.GP3
GG2.GP4
About the
strategic
business plan
Business
analyst and
project
manager
For Ukraine power Grid, strategic business plan has to be prepared by the
project manager and the business analyst to make sure that the cyber security
related issues will be completely resolved through proper business plan.
Monthly Video
conference and
presentation
Impl Derived GG2.GP2
About the final
budget report
Project
manager and
the finance
manager
The finance manager is required to design the budget report to make sure that
the estimated budget and the planned cost are not varied from each other
(Cenci et al., 2018). The final designed cost plan will help the company to
avoid budget overrun
Monthly Face to face
meeting,
presentation
and video
conference
Derived GG2.GP1
GG2.GP2
Purpose of
communicatio
n
Responsible
person
Details of the topic to be discussed Freque
ncy
Medium of
communicatio
n
Measure
type
Base or
derived
Applicabl
e GG.GP
About the
details of cyber
security in
Ukraine power
Grid
Project
manager and
operation
manager
Before initiating any project, it is necessary for the operation manager and
project manager to elaborate security measures and to make the rest of the
people familiar to cyber security (Rabbi et al., 2016)
Monthly Video
conference and
presentation
Impl Derived GG2.GP4
GG2.GP8
About the roles
and
responsibilities
of the associate
members
Project
manager and
project team
members
Before the development of the project the project manager is required to
define and allocate different roles and responsibilities to the project team
members and they are also required to play their allocated job roles within
estimated time period (Kaiser, El Arbi & Ahlemann, 2015).
Monthly Video
conference and
presentation
Impl Derived GG2.GP3
GG2.GP4
About the
strategic
business plan
Business
analyst and
project
manager
For Ukraine power Grid, strategic business plan has to be prepared by the
project manager and the business analyst to make sure that the cyber security
related issues will be completely resolved through proper business plan.
Monthly Video
conference and
presentation
Impl Derived GG2.GP2
About the final
budget report
Project
manager and
the finance
manager
The finance manager is required to design the budget report to make sure that
the estimated budget and the planned cost are not varied from each other
(Cenci et al., 2018). The final designed cost plan will help the company to
avoid budget overrun
Monthly Face to face
meeting,
presentation
and video
conference
Derived GG2.GP1
GG2.GP2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
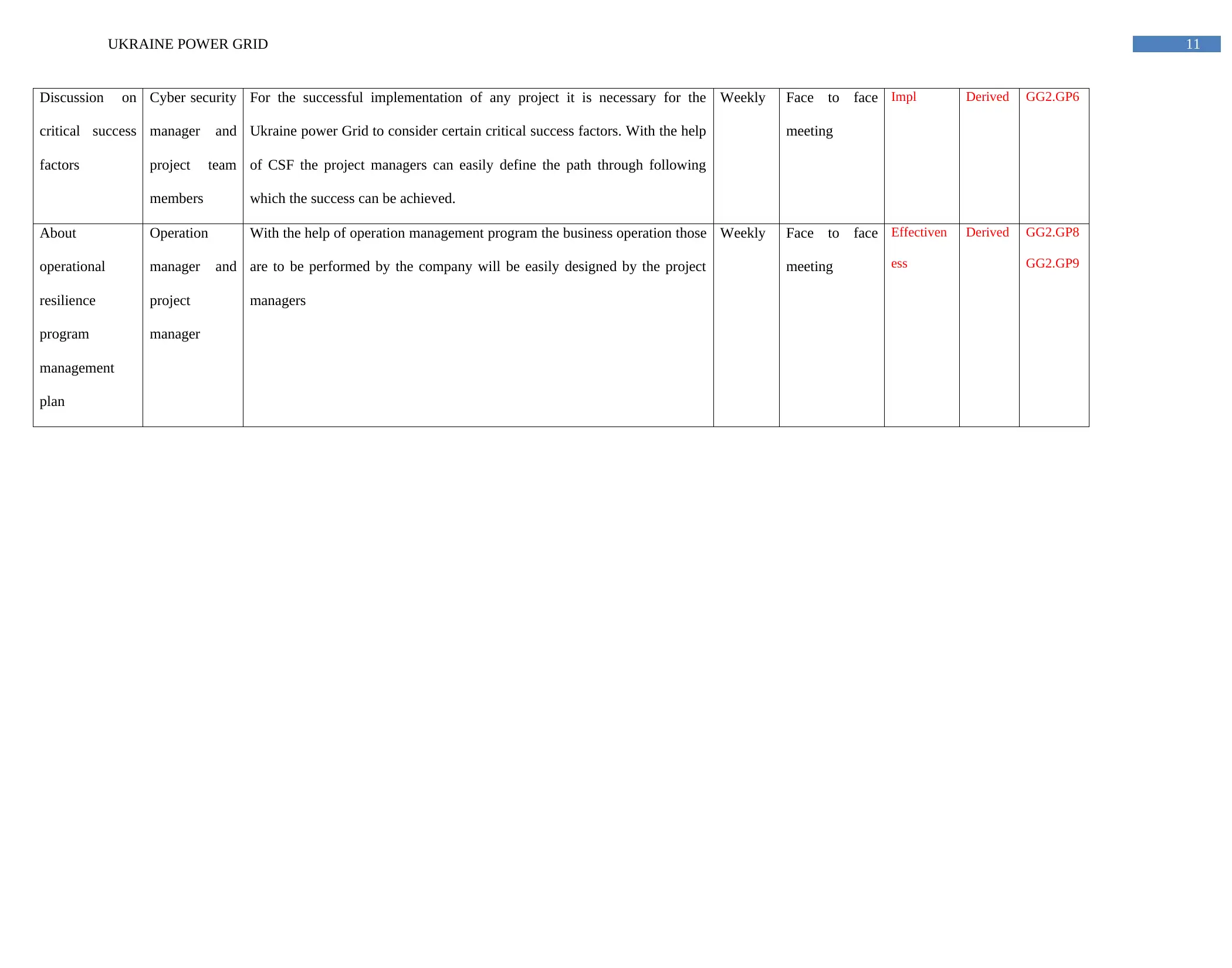
11UKRAINE POWER GRID
Discussion on
critical success
factors
Cyber security
manager and
project team
members
For the successful implementation of any project it is necessary for the
Ukraine power Grid to consider certain critical success factors. With the help
of CSF the project managers can easily define the path through following
which the success can be achieved.
Weekly Face to face
meeting
Impl Derived GG2.GP6
About
operational
resilience
program
management
plan
Operation
manager and
project
manager
With the help of operation management program the business operation those
are to be performed by the company will be easily designed by the project
managers
Weekly Face to face
meeting
Effectiven
ess
Derived GG2.GP8
GG2.GP9
Discussion on
critical success
factors
Cyber security
manager and
project team
members
For the successful implementation of any project it is necessary for the
Ukraine power Grid to consider certain critical success factors. With the help
of CSF the project managers can easily define the path through following
which the success can be achieved.
Weekly Face to face
meeting
Impl Derived GG2.GP6
About
operational
resilience
program
management
plan
Operation
manager and
project
manager
With the help of operation management program the business operation those
are to be performed by the company will be easily designed by the project
managers
Weekly Face to face
meeting
Effectiven
ess
Derived GG2.GP8
GG2.GP9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
12UKRAINE POWER GRID
However, throughout the entire project development period the project manager
and the project team members are required to follow open communication. Open
communication will help to establish a relationship between the project manager and the
project team members (McNeil, Frey & Embrechts, 2015). With the help of open
communication the project team members will be able to share their ideas and creativity
with the rest of the members. Both the inter-organizational and intra-organizational
conflicts will be avoided with the help of proper communication approach.
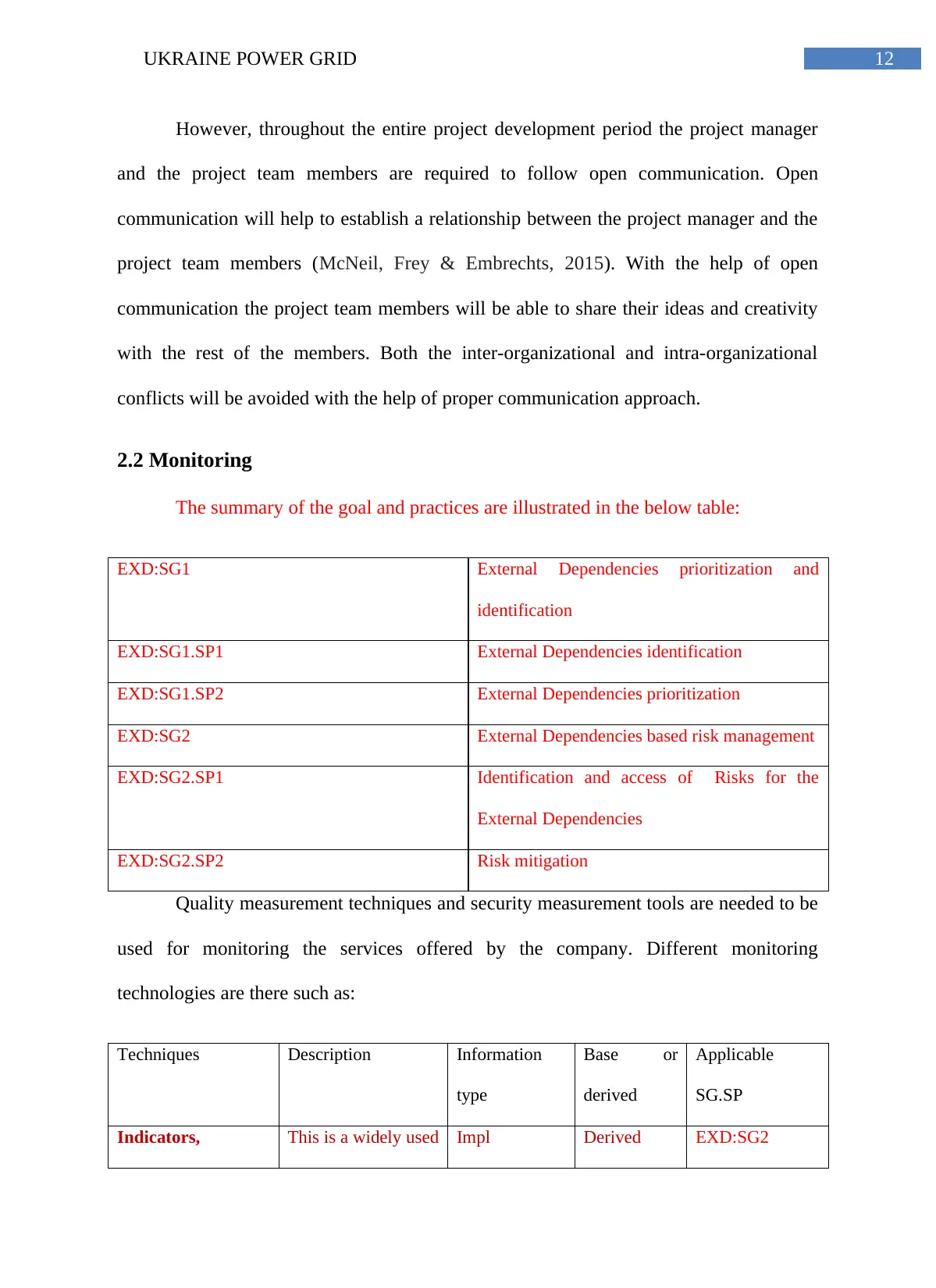
2.2 Monitoring
The summary of the goal and practices are illustrated in the below table:
EXD:SG1 External Dependencies prioritization and
identification
EXD:SG1.SP1 External Dependencies identification
EXD:SG1.SP2 External Dependencies prioritization
EXD:SG2 External Dependencies based risk management
EXD:SG2.SP1 Identification and access of Risks for the
External Dependencies
EXD:SG2.SP2 Risk mitigation
Quality measurement techniques and security measurement tools are needed to be
used for monitoring the services offered by the company. Different monitoring
technologies are there such as:
Techniques Description Information
type
Base or
derived
Applicable
SG.SP
Indicators, This is a widely used Impl Derived EXD:SG2
However, throughout the entire project development period the project manager
and the project team members are required to follow open communication. Open
communication will help to establish a relationship between the project manager and the
project team members (McNeil, Frey & Embrechts, 2015). With the help of open
communication the project team members will be able to share their ideas and creativity
with the rest of the members. Both the inter-organizational and intra-organizational
conflicts will be avoided with the help of proper communication approach.
2.2 Monitoring
The summary of the goal and practices are illustrated in the below table:
EXD:SG1 External Dependencies prioritization and
identification
EXD:SG1.SP1 External Dependencies identification
EXD:SG1.SP2 External Dependencies prioritization
EXD:SG2 External Dependencies based risk management
EXD:SG2.SP1 Identification and access of Risks for the
External Dependencies
EXD:SG2.SP2 Risk mitigation
Quality measurement techniques and security measurement tools are needed to be
used for monitoring the services offered by the company. Different monitoring
technologies are there such as:
Techniques Description Information
type
Base or
derived
Applicable
SG.SP
Indicators, This is a widely used Impl Derived EXD:SG2
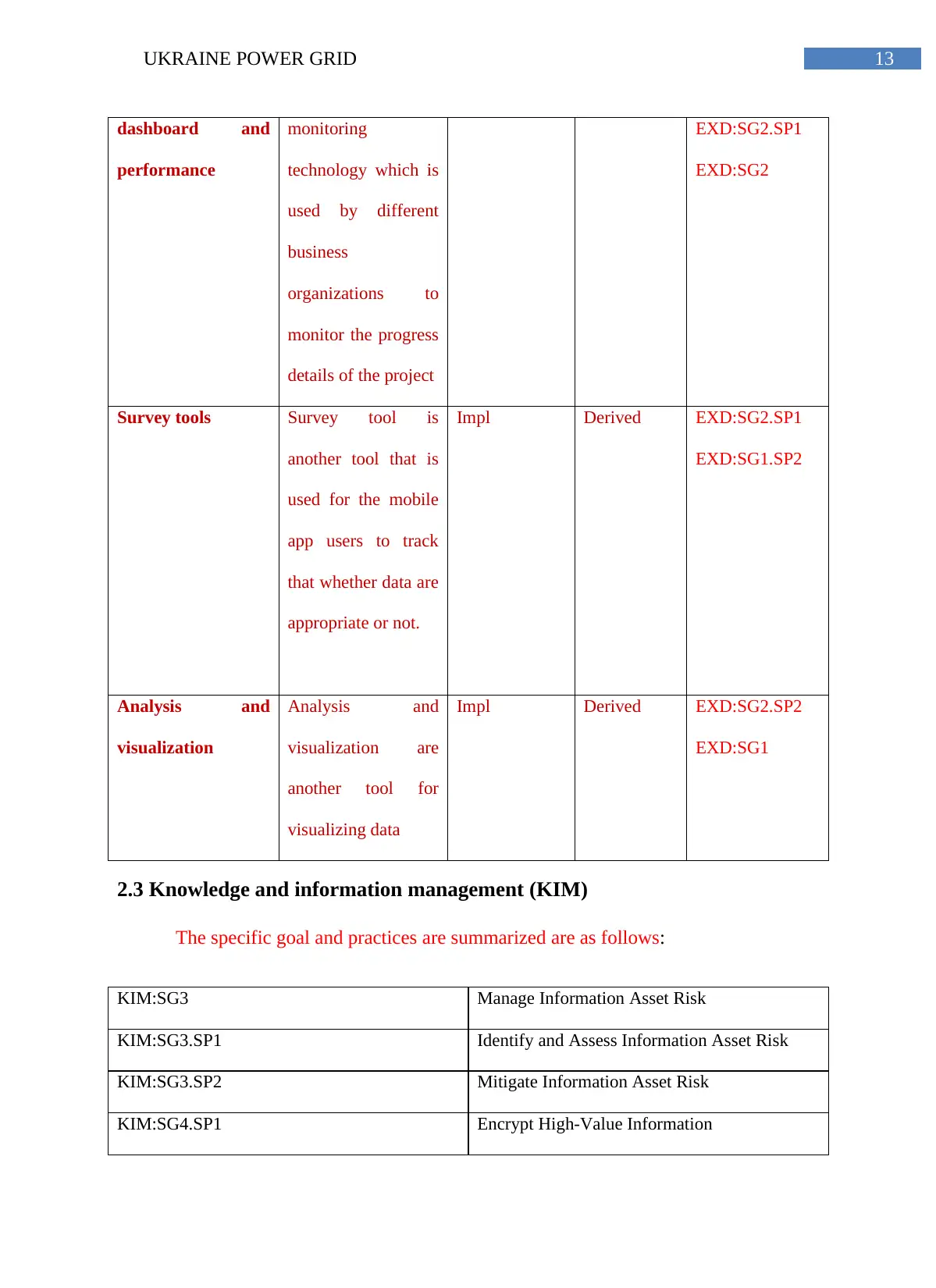
13UKRAINE POWER GRID
dashboard and
performance
monitoring
technology which is
used by different
business
organizations to
monitor the progress
details of the project
EXD:SG2.SP1
EXD:SG2
Survey tools Survey tool is
another tool that is
used for the mobile
app users to track
that whether data are
appropriate or not.
Impl Derived EXD:SG2.SP1
EXD:SG1.SP2
Analysis and
visualization
Analysis and
visualization are
another tool for
visualizing data
Impl Derived EXD:SG2.SP2
EXD:SG1
2.3 Knowledge and information management (KIM)
The specific goal and practices are summarized are as follows:
KIM:SG3 Manage Information Asset Risk
KIM:SG3.SP1 Identify and Assess Information Asset Risk
KIM:SG3.SP2 Mitigate Information Asset Risk
KIM:SG4.SP1 Encrypt High-Value Information
dashboard and
performance
monitoring
technology which is
used by different
business
organizations to
monitor the progress
details of the project
EXD:SG2.SP1
EXD:SG2
Survey tools Survey tool is
another tool that is
used for the mobile
app users to track
that whether data are
appropriate or not.
Impl Derived EXD:SG2.SP1
EXD:SG1.SP2
Analysis and
visualization
Analysis and
visualization are
another tool for
visualizing data
Impl Derived EXD:SG2.SP2
EXD:SG1
2.3 Knowledge and information management (KIM)
The specific goal and practices are summarized are as follows:
KIM:SG3 Manage Information Asset Risk
KIM:SG3.SP1 Identify and Assess Information Asset Risk
KIM:SG3.SP2 Mitigate Information Asset Risk
KIM:SG4.SP1 Encrypt High-Value Information
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


