UML and Cryptography
VerifiedAdded on 2023/04/21
|12
|3025
|447
AI Summary
This report explores the use of UML and Cryptography in the Australian My Health Record (MHR) system. It discusses the use cases and misuse cases of the MHR system, compares symmetric and asymmetric key algorithms, and analyzes cipher substitution algorithms. It also proposes the implementation of a new cryptographic algorithm in the MHR system for improved security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: UML AND CRYPTOGRAPHY
UML AND CRYPTOGRAPHY
Name of the Student:
Name of the University:
Author Note:
UML AND CRYPTOGRAPHY
Name of the Student:
Name of the University:
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1UML AND CRYPTOGRAPHY
Table of Contents
Introduction..........................................................................................................................................2
Description...........................................................................................................................................2
Use Case Scenario of the My Health Record or MHR System........................................................2
The UML Diagram for the MHR:.....................................................................................................3
The use cases for the MHR:.............................................................................................................3
The misuse cases of the MHR:.........................................................................................................3
Interactions between the actors and the selected use case:.............................................................4
Use case description:.......................................................................................................................4
Brief Survey on Cryptographic Algorithms.....................................................................................5
Symmetric versus Asymmetric Key Cryptography with examples:..................................................5
Comparison between two cipher substitution algorithms: Playfair and Caesar ciphers................7
Reflections on private and public keys and their association with the MHR:.................................8
A recent Cryptographic Algorithm...................................................................................................9
Identifying a new proposed algorithm:............................................................................................9
Working of the proposed algorithm:................................................................................................9
Reflections on applying the proposed algorithm in MHR system:.................................................10
Recommendation................................................................................................................................11
Conclusion..........................................................................................................................................11
References..........................................................................................................................................12
Table of Contents
Introduction..........................................................................................................................................2
Description...........................................................................................................................................2
Use Case Scenario of the My Health Record or MHR System........................................................2
The UML Diagram for the MHR:.....................................................................................................3
The use cases for the MHR:.............................................................................................................3
The misuse cases of the MHR:.........................................................................................................3
Interactions between the actors and the selected use case:.............................................................4
Use case description:.......................................................................................................................4
Brief Survey on Cryptographic Algorithms.....................................................................................5
Symmetric versus Asymmetric Key Cryptography with examples:..................................................5
Comparison between two cipher substitution algorithms: Playfair and Caesar ciphers................7
Reflections on private and public keys and their association with the MHR:.................................8
A recent Cryptographic Algorithm...................................................................................................9
Identifying a new proposed algorithm:............................................................................................9
Working of the proposed algorithm:................................................................................................9
Reflections on applying the proposed algorithm in MHR system:.................................................10
Recommendation................................................................................................................................11
Conclusion..........................................................................................................................................11
References..........................................................................................................................................12

2UML AND CRYPTOGRAPHY
Introduction
Cryptography is a field of science which deals with providing security to machines and data.
The basic idea of cryptography is to secure a piece of data by transforming it into a cryptogram
which cannot be decrypted by unauthorised people without its unique decoding key (Khan and
Tuteja, 2015). The process is known as encryption algorithm and it requires an encryption key as
input. To revert the data to its normal readable form a decryption algorithm is used which also uses
a decryption key.
In this report, the symmetric and the asymmetric cryptographic algorithms will be analysed.
Their interaction with the Australian My Health Record or MHR system will also be highlighted.
The use cases and misuse cases of the MHR systems will also be briefly discussed. In this paper, a
recent cryptographic algorithm will be discussed and how it can be implemented to the MHR
system of Australia.
Description
Use Case Scenario of the My Health Record or MHR System
The scenario given in this report is about the Australian MHR system. The MHR is a system
that keeps track of all the health information data in one secure place. The MHR can be accessed by
different users like doctors, hospitals and even pharmacists. This is the system’s primary use. For
secondary use, the system can be used by researchers and other people for academic purposes.
Introduction
Cryptography is a field of science which deals with providing security to machines and data.
The basic idea of cryptography is to secure a piece of data by transforming it into a cryptogram
which cannot be decrypted by unauthorised people without its unique decoding key (Khan and
Tuteja, 2015). The process is known as encryption algorithm and it requires an encryption key as
input. To revert the data to its normal readable form a decryption algorithm is used which also uses
a decryption key.
In this report, the symmetric and the asymmetric cryptographic algorithms will be analysed.
Their interaction with the Australian My Health Record or MHR system will also be highlighted.
The use cases and misuse cases of the MHR systems will also be briefly discussed. In this paper, a
recent cryptographic algorithm will be discussed and how it can be implemented to the MHR
system of Australia.
Description
Use Case Scenario of the My Health Record or MHR System
The scenario given in this report is about the Australian MHR system. The MHR is a system
that keeps track of all the health information data in one secure place. The MHR can be accessed by
different users like doctors, hospitals and even pharmacists. This is the system’s primary use. For
secondary use, the system can be used by researchers and other people for academic purposes.
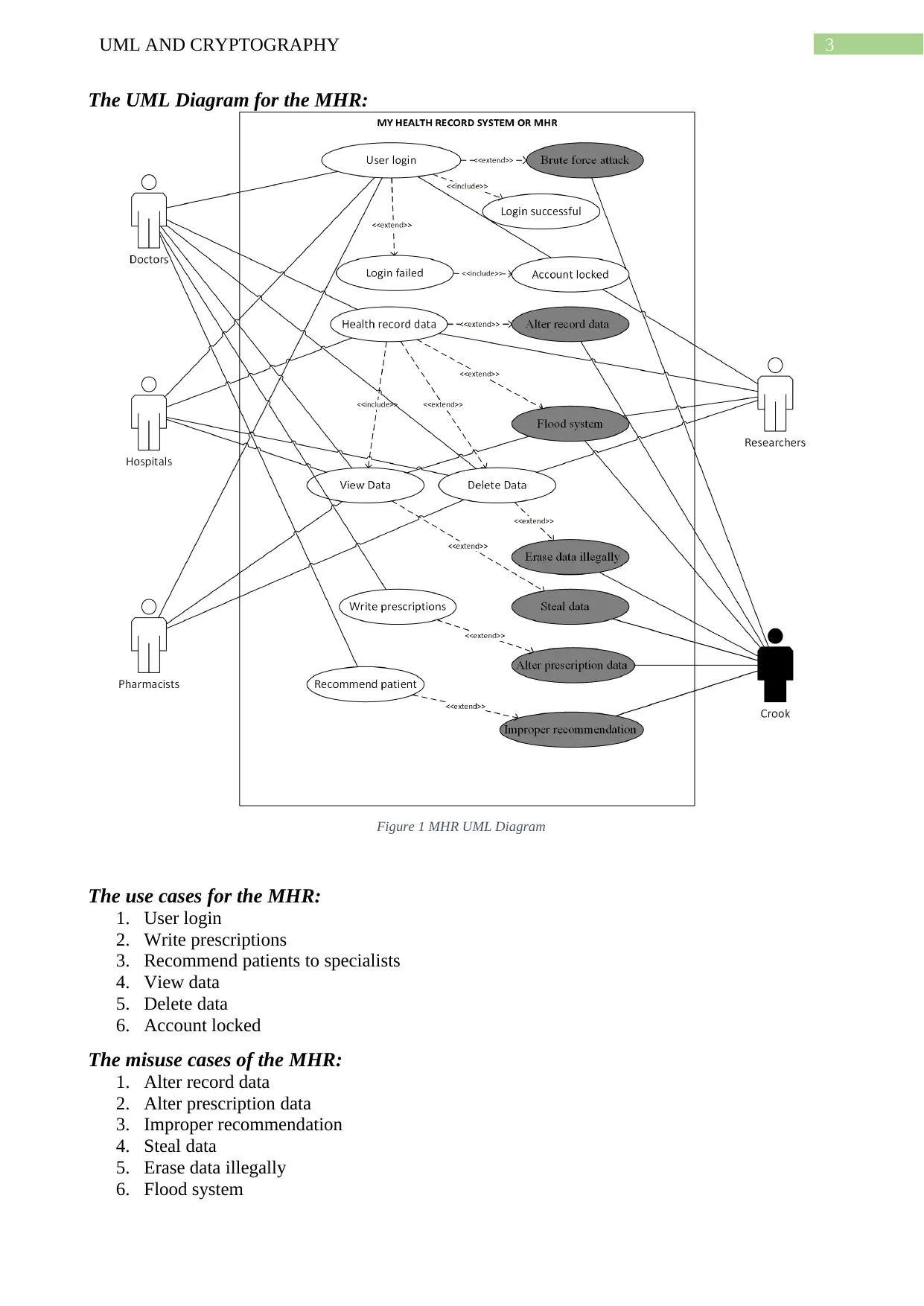
3UML AND CRYPTOGRAPHY
The UML Diagram for the MHR:
Figure 1 MHR UML Diagram
The use cases for the MHR:
1. User login
2. Write prescriptions
3. Recommend patients to specialists
4. View data
5. Delete data
6. Account locked
The misuse cases of the MHR:
1. Alter record data
2. Alter prescription data
3. Improper recommendation
4. Steal data
5. Erase data illegally
6. Flood system
The UML Diagram for the MHR:
Figure 1 MHR UML Diagram
The use cases for the MHR:
1. User login
2. Write prescriptions
3. Recommend patients to specialists
4. View data
5. Delete data
6. Account locked
The misuse cases of the MHR:
1. Alter record data
2. Alter prescription data
3. Improper recommendation
4. Steal data
5. Erase data illegally
6. Flood system
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4UML AND CRYPTOGRAPHY
7. Brute force attack
Interactions between the actors and the selected use case:
The “user login” use case is the first step toward accessing this system. The MHR uses
authentication to verify that the user is authorised to use it. All the actors interacting with the system
must use this use case to gain entry into the system (Bhuiyan, Haque and Shabnam. 2018). The
doctor, hospital, pharmacists and researchers all use their authentication details to login into the
system using this use case. The user inputs the login information into the system. The MHR
validates the input and then either allows access to the system if the input information is correct or
shows an “Incorrect details. Authentication failed.” message if the input information is wrong. The
system allows up to three attempts for login and after that blocks the user account for 24 hours to
prevent any unauthorised login such as brute force attack.
Use case description:
Use Case Name: User login
Trigger/Goal: Actors enter their login details to login into the system
Actors: Doctors, Hospitals, Pharmacists and Researchers
Main flow: 1. Actors input authentication details (username and password).
2. The system validates the input
3. The access to the system is granted if the username and password are correct.
Extensions: 2a. Entered login details are invalid:
1. The actor inputs cannot be validated by the system. The system notifies the actor.
2. The system allows the user three attempts to give correct login details.
3. The system locks the account for 24 hours if wrong input details are given three
times in a row. The system notifies the actor and leads to the termination of the use
case.
Brief Survey on Cryptographic Algorithms
Symmetric versus Asymmetric Key Cryptography with examples:
The two main types of cryptographic algorithms are symmetric key and asymmetric key
algorithms. The symmetric key algorithm is a commonly used and reliable algorithm that makes use
of only one secret key to both encryption and decryption the data. Blowfish is a good example of
symmetric key algorithm (Patil et al. 2016). It uses a block cipher method which is a computer
function that encryptions entire blocks of plain text into cipher text. The function then generates the
same key at receiver end to decryption the text back. The algorithm uses a 16 round Feistel cipher
method and has variable key
lengths of 32bits to 448bits.
7. Brute force attack
Interactions between the actors and the selected use case:
The “user login” use case is the first step toward accessing this system. The MHR uses
authentication to verify that the user is authorised to use it. All the actors interacting with the system
must use this use case to gain entry into the system (Bhuiyan, Haque and Shabnam. 2018). The
doctor, hospital, pharmacists and researchers all use their authentication details to login into the
system using this use case. The user inputs the login information into the system. The MHR
validates the input and then either allows access to the system if the input information is correct or
shows an “Incorrect details. Authentication failed.” message if the input information is wrong. The
system allows up to three attempts for login and after that blocks the user account for 24 hours to
prevent any unauthorised login such as brute force attack.
Use case description:
Use Case Name: User login
Trigger/Goal: Actors enter their login details to login into the system
Actors: Doctors, Hospitals, Pharmacists and Researchers
Main flow: 1. Actors input authentication details (username and password).
2. The system validates the input
3. The access to the system is granted if the username and password are correct.
Extensions: 2a. Entered login details are invalid:
1. The actor inputs cannot be validated by the system. The system notifies the actor.
2. The system allows the user three attempts to give correct login details.
3. The system locks the account for 24 hours if wrong input details are given three
times in a row. The system notifies the actor and leads to the termination of the use
case.
Brief Survey on Cryptographic Algorithms
Symmetric versus Asymmetric Key Cryptography with examples:
The two main types of cryptographic algorithms are symmetric key and asymmetric key
algorithms. The symmetric key algorithm is a commonly used and reliable algorithm that makes use
of only one secret key to both encryption and decryption the data. Blowfish is a good example of
symmetric key algorithm (Patil et al. 2016). It uses a block cipher method which is a computer
function that encryptions entire blocks of plain text into cipher text. The function then generates the
same key at receiver end to decryption the text back. The algorithm uses a 16 round Feistel cipher
method and has variable key
lengths of 32bits to 448bits.
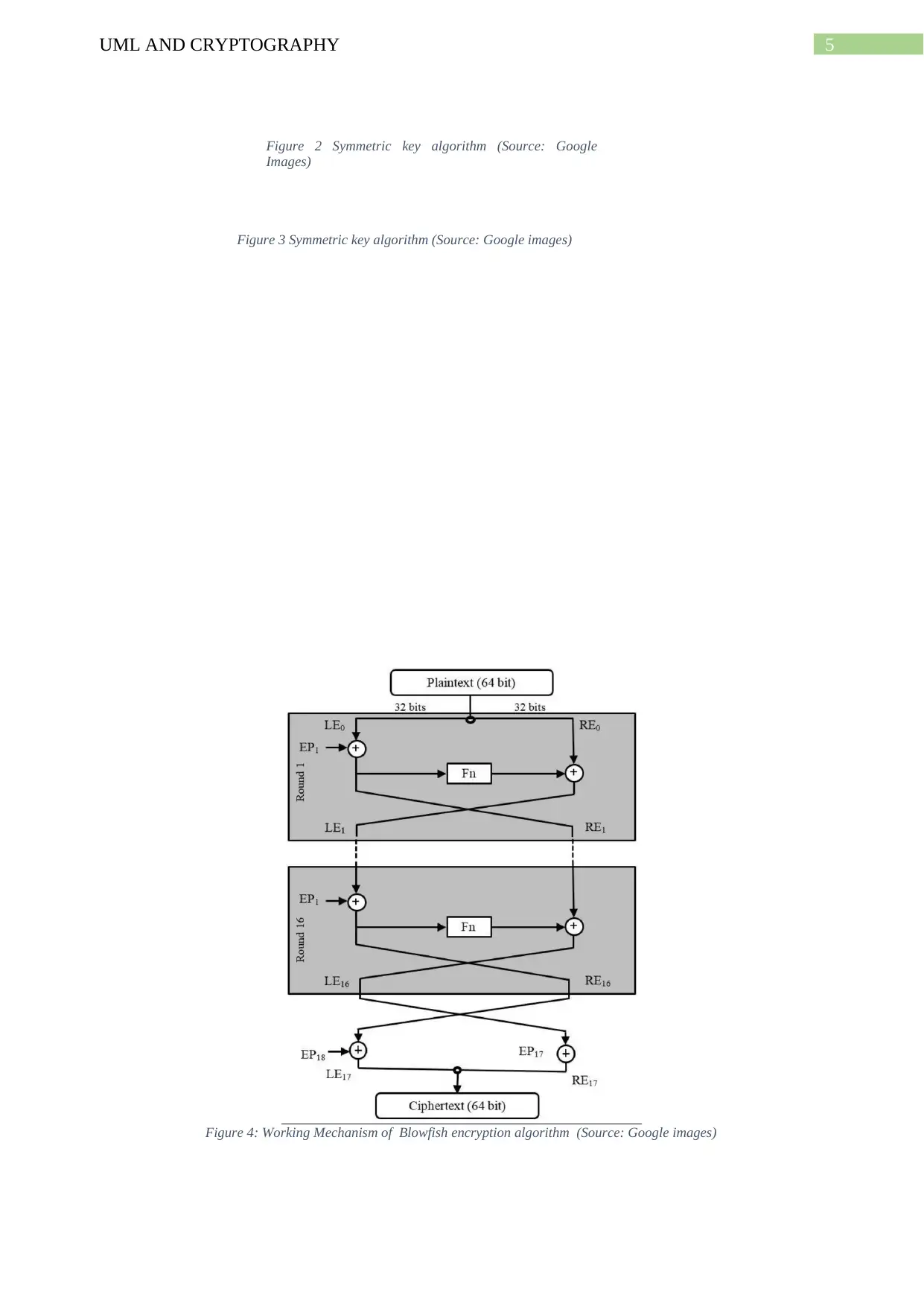
5UML AND CRYPTOGRAPHY
Figure 4: Working Mechanism of Blowfish encryption algorithm (Source: Google images)
Figure 2 Symmetric key algorithm (Source: Google
Images)
Figure 3 Symmetric key algorithm (Source: Google images)
Figure 4: Working Mechanism of Blowfish encryption algorithm (Source: Google images)
Figure 2 Symmetric key algorithm (Source: Google
Images)
Figure 3 Symmetric key algorithm (Source: Google images)

6UML AND CRYPTOGRAPHY
The asymmetric key algorithm is a new method which uses two different keys to encrypt a
text (Arya, Aswal and Kumar. 2015). One is a public key and the other is a private key. ElGamal is
a good example of asymmetric key algorithm. This algorithm uses three components: the key
generator, the encryption and the decryption (Patil et al. 2016). Two different keys are used and
each key uses asymmetrical encryption and decryption. The public key is used to encrypt the
message while sending and the private key is used to decrypt when the message is received.
Figure 5 ElGamal
algorithm (Source:
Google images)
Comparison between two cipher substitution algorithms: Playfair and Caesar ciphers
The two common substitution cipher algorithms are the Caesar cipher and the Playfair
cipher (Perrig et al. 2017). The Caesar cipher is a mono alphabetic algorithm where each single
letter of the text is substituted by another letter. This is one of the simplest form of ciphering. The
replaced alphabet is shifted by any fixed number from 0 to 25. The “secret shift number” acts as the
key to decryption the cipher (Verma, Guha and Mishra. 2016).
The Caesar algorithm would encrypt an actor’s message in the MHR system using single
letter substitution method and the encrypted message then will be sent to the other actor who might
then use the generated secret shifted number key to decrypt the message. This can be done by
reverting the substituted letters in the message to their original position. This can be only applied to
messages in plain texts written in any language. Both the actors involved must know the language.
Figure 6 Asymmetric key algorithm (Source: Google Images)
The asymmetric key algorithm is a new method which uses two different keys to encrypt a
text (Arya, Aswal and Kumar. 2015). One is a public key and the other is a private key. ElGamal is
a good example of asymmetric key algorithm. This algorithm uses three components: the key
generator, the encryption and the decryption (Patil et al. 2016). Two different keys are used and
each key uses asymmetrical encryption and decryption. The public key is used to encrypt the
message while sending and the private key is used to decrypt when the message is received.
Figure 5 ElGamal
algorithm (Source:
Google images)
Comparison between two cipher substitution algorithms: Playfair and Caesar ciphers
The two common substitution cipher algorithms are the Caesar cipher and the Playfair
cipher (Perrig et al. 2017). The Caesar cipher is a mono alphabetic algorithm where each single
letter of the text is substituted by another letter. This is one of the simplest form of ciphering. The
replaced alphabet is shifted by any fixed number from 0 to 25. The “secret shift number” acts as the
key to decryption the cipher (Verma, Guha and Mishra. 2016).
The Caesar algorithm would encrypt an actor’s message in the MHR system using single
letter substitution method and the encrypted message then will be sent to the other actor who might
then use the generated secret shifted number key to decrypt the message. This can be done by
reverting the substituted letters in the message to their original position. This can be only applied to
messages in plain texts written in any language. Both the actors involved must know the language.
Figure 6 Asymmetric key algorithm (Source: Google Images)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
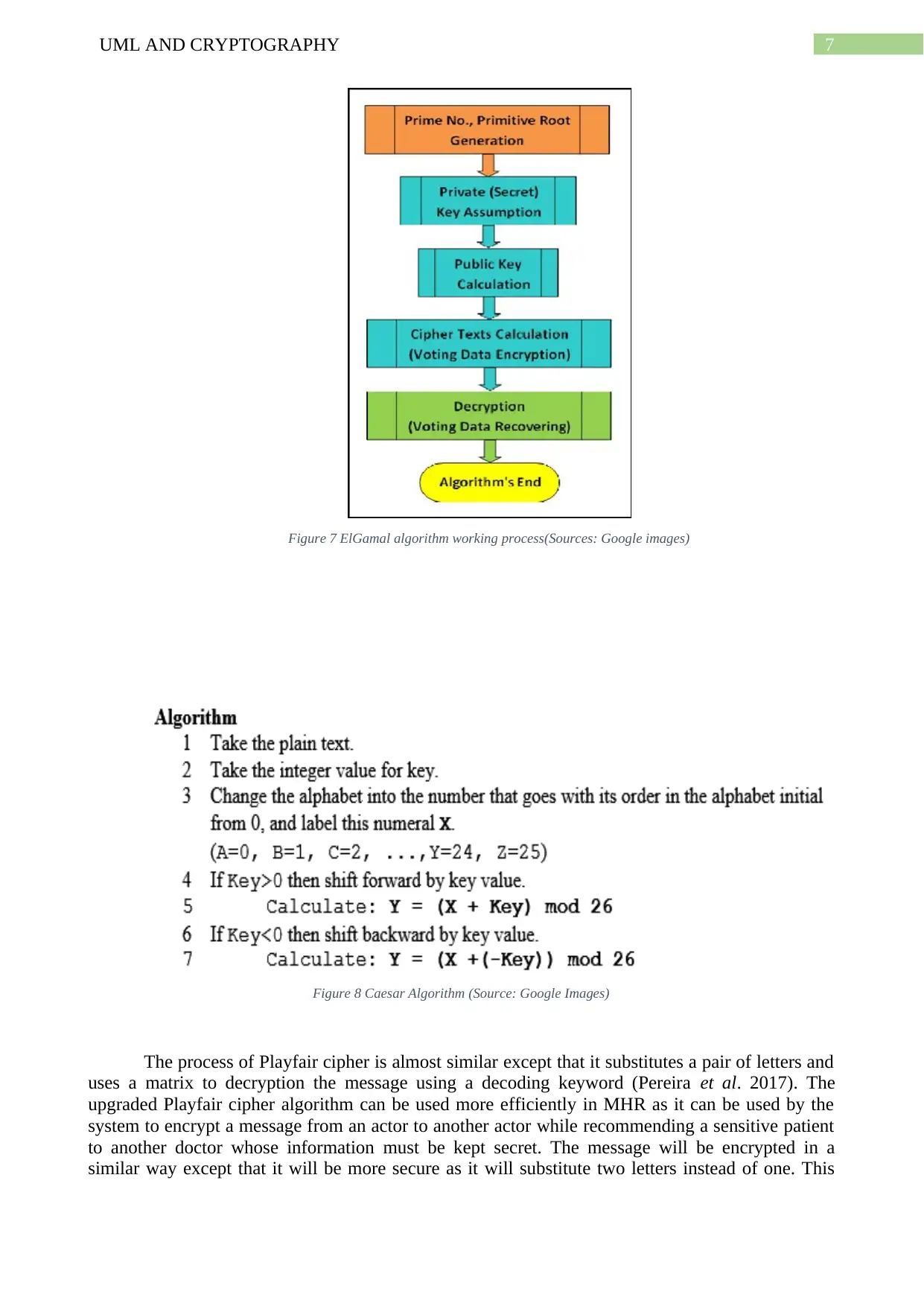
7UML AND CRYPTOGRAPHY
Figure 7 ElGamal algorithm working process(Sources: Google images)
Figure 8 Caesar Algorithm (Source: Google Images)
The process of Playfair cipher is almost similar except that it substitutes a pair of letters and
uses a matrix to decryption the message using a decoding keyword (Pereira et al. 2017). The
upgraded Playfair cipher algorithm can be used more efficiently in MHR as it can be used by the
system to encrypt a message from an actor to another actor while recommending a sensitive patient
to another doctor whose information must be kept secret. The message will be encrypted in a
similar way except that it will be more secure as it will substitute two letters instead of one. This
Figure 7 ElGamal algorithm working process(Sources: Google images)
Figure 8 Caesar Algorithm (Source: Google Images)
The process of Playfair cipher is almost similar except that it substitutes a pair of letters and
uses a matrix to decryption the message using a decoding keyword (Pereira et al. 2017). The
upgraded Playfair cipher algorithm can be used more efficiently in MHR as it can be used by the
system to encrypt a message from an actor to another actor while recommending a sensitive patient
to another doctor whose information must be kept secret. The message will be encrypted in a
similar way except that it will be more secure as it will substitute two letters instead of one. This
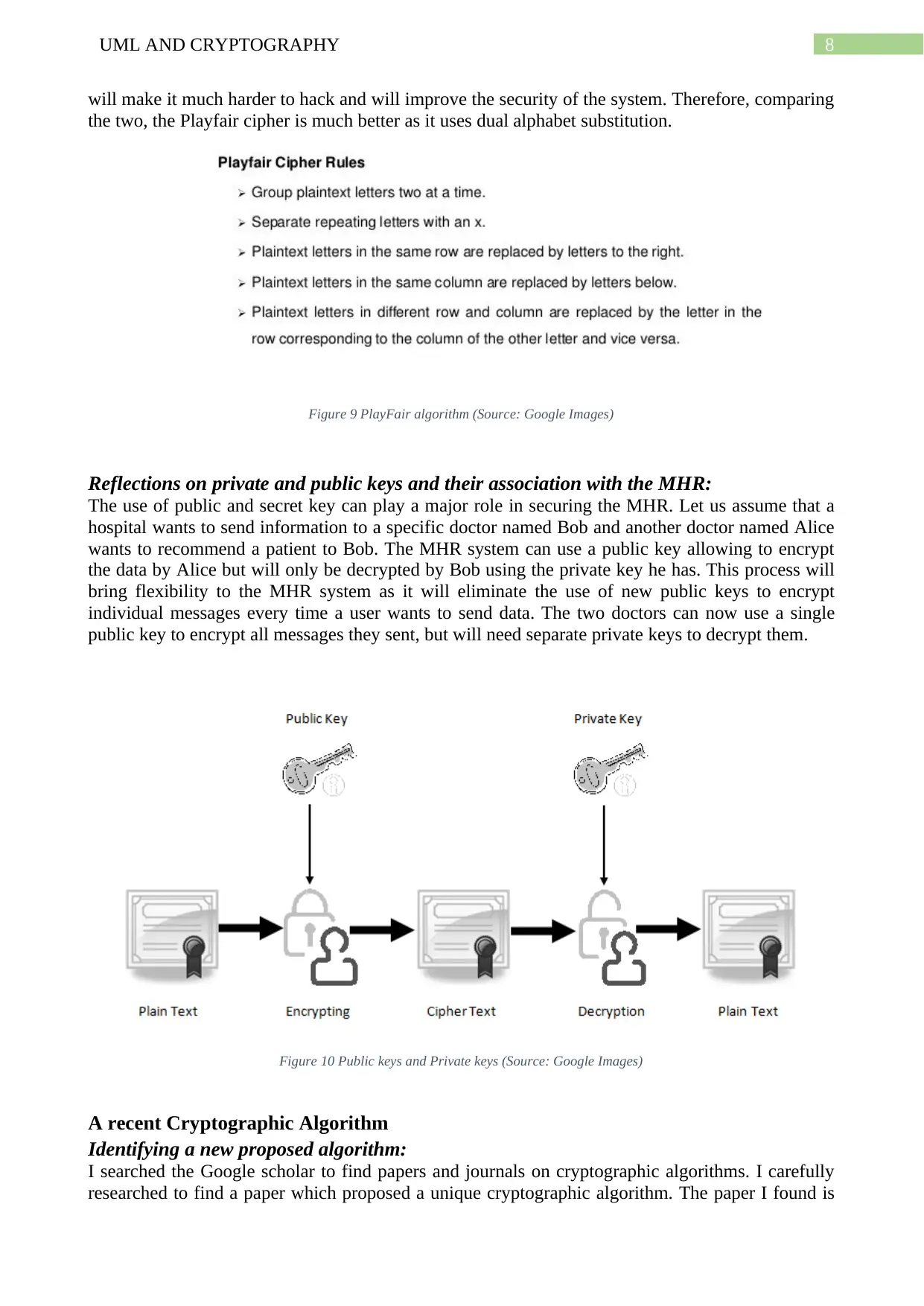
8UML AND CRYPTOGRAPHY
will make it much harder to hack and will improve the security of the system. Therefore, comparing
the two, the Playfair cipher is much better as it uses dual alphabet substitution.
Figure 9 PlayFair algorithm (Source: Google Images)
Reflections on private and public keys and their association with the MHR:
The use of public and secret key can play a major role in securing the MHR. Let us assume that a
hospital wants to send information to a specific doctor named Bob and another doctor named Alice
wants to recommend a patient to Bob. The MHR system can use a public key allowing to encrypt
the data by Alice but will only be decrypted by Bob using the private key he has. This process will
bring flexibility to the MHR system as it will eliminate the use of new public keys to encrypt
individual messages every time a user wants to send data. The two doctors can now use a single
public key to encrypt all messages they sent, but will need separate private keys to decrypt them.
Figure 10 Public keys and Private keys (Source: Google Images)
A recent Cryptographic Algorithm
Identifying a new proposed algorithm:
I searched the Google scholar to find papers and journals on cryptographic algorithms. I carefully
researched to find a paper which proposed a unique cryptographic algorithm. The paper I found is
will make it much harder to hack and will improve the security of the system. Therefore, comparing
the two, the Playfair cipher is much better as it uses dual alphabet substitution.
Figure 9 PlayFair algorithm (Source: Google Images)
Reflections on private and public keys and their association with the MHR:
The use of public and secret key can play a major role in securing the MHR. Let us assume that a
hospital wants to send information to a specific doctor named Bob and another doctor named Alice
wants to recommend a patient to Bob. The MHR system can use a public key allowing to encrypt
the data by Alice but will only be decrypted by Bob using the private key he has. This process will
bring flexibility to the MHR system as it will eliminate the use of new public keys to encrypt
individual messages every time a user wants to send data. The two doctors can now use a single
public key to encrypt all messages they sent, but will need separate private keys to decrypt them.
Figure 10 Public keys and Private keys (Source: Google Images)
A recent Cryptographic Algorithm
Identifying a new proposed algorithm:
I searched the Google scholar to find papers and journals on cryptographic algorithms. I carefully
researched to find a paper which proposed a unique cryptographic algorithm. The paper I found is
9UML AND CRYPTOGRAPHY
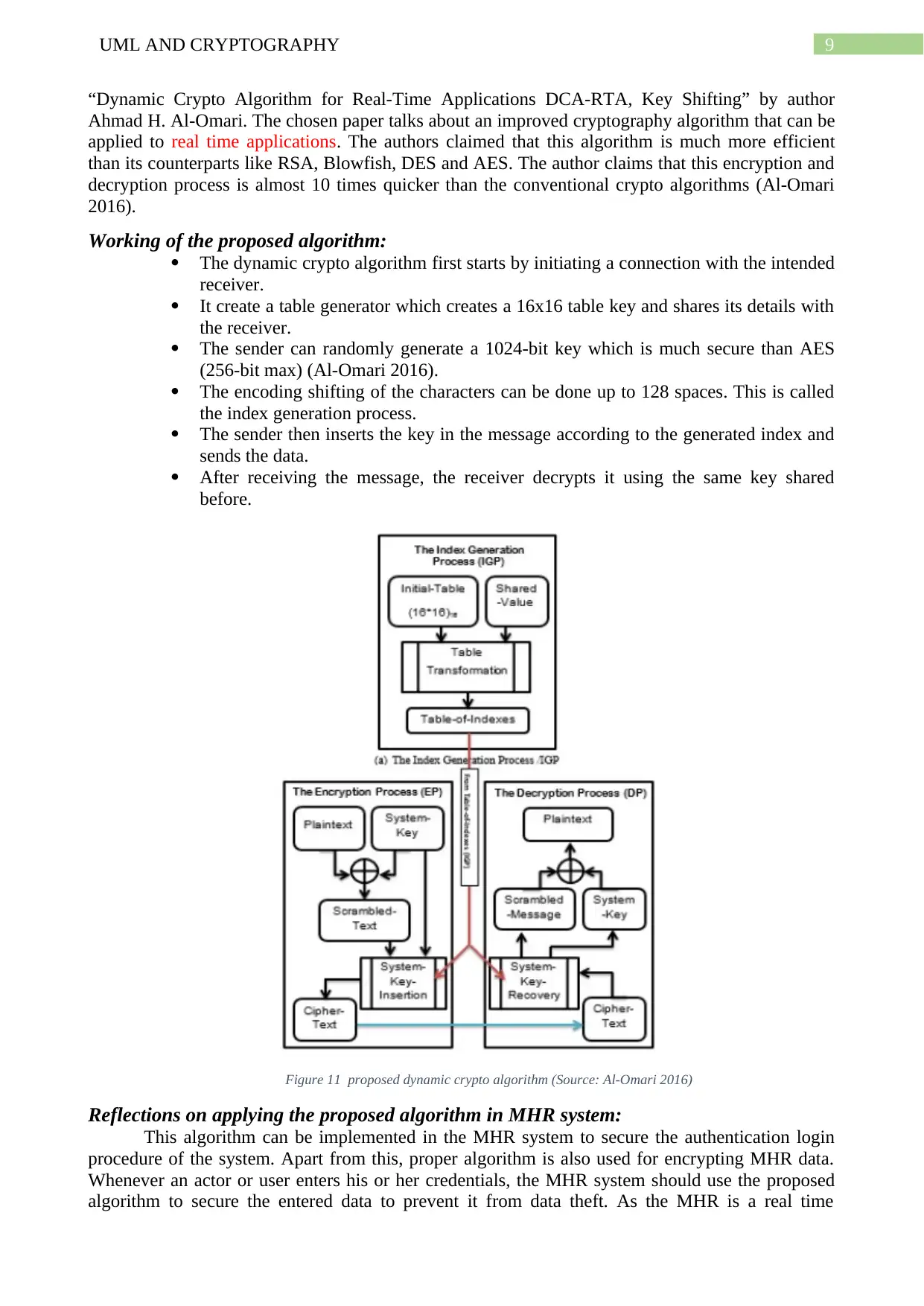
“Dynamic Crypto Algorithm for Real-Time Applications DCA-RTA, Key Shifting” by author
Ahmad H. Al-Omari. The chosen paper talks about an improved cryptography algorithm that can be
applied to real time applications. The authors claimed that this algorithm is much more efficient
than its counterparts like RSA, Blowfish, DES and AES. The author claims that this encryption and
decryption process is almost 10 times quicker than the conventional crypto algorithms (Al-Omari
2016).
Working of the proposed algorithm:
The dynamic crypto algorithm first starts by initiating a connection with the intended
receiver.
It create a table generator which creates a 16x16 table key and shares its details with
the receiver.
The sender can randomly generate a 1024-bit key which is much secure than AES
(256-bit max) (Al-Omari 2016).
The encoding shifting of the characters can be done up to 128 spaces. This is called
the index generation process.
The sender then inserts the key in the message according to the generated index and
sends the data.
After receiving the message, the receiver decrypts it using the same key shared
before.
Figure 11 proposed dynamic crypto algorithm (Source: Al-Omari 2016)
Reflections on applying the proposed algorithm in MHR system:
This algorithm can be implemented in the MHR system to secure the authentication login
procedure of the system. Apart from this, proper algorithm is also used for encrypting MHR data.
Whenever an actor or user enters his or her credentials, the MHR system should use the proposed
algorithm to secure the entered data to prevent it from data theft. As the MHR is a real time
“Dynamic Crypto Algorithm for Real-Time Applications DCA-RTA, Key Shifting” by author
Ahmad H. Al-Omari. The chosen paper talks about an improved cryptography algorithm that can be
applied to real time applications. The authors claimed that this algorithm is much more efficient
than its counterparts like RSA, Blowfish, DES and AES. The author claims that this encryption and
decryption process is almost 10 times quicker than the conventional crypto algorithms (Al-Omari
2016).
Working of the proposed algorithm:
The dynamic crypto algorithm first starts by initiating a connection with the intended
receiver.
It create a table generator which creates a 16x16 table key and shares its details with
the receiver.
The sender can randomly generate a 1024-bit key which is much secure than AES
(256-bit max) (Al-Omari 2016).
The encoding shifting of the characters can be done up to 128 spaces. This is called
the index generation process.
The sender then inserts the key in the message according to the generated index and
sends the data.
After receiving the message, the receiver decrypts it using the same key shared
before.
Figure 11 proposed dynamic crypto algorithm (Source: Al-Omari 2016)
Reflections on applying the proposed algorithm in MHR system:
This algorithm can be implemented in the MHR system to secure the authentication login
procedure of the system. Apart from this, proper algorithm is also used for encrypting MHR data.
Whenever an actor or user enters his or her credentials, the MHR system should use the proposed
algorithm to secure the entered data to prevent it from data theft. As the MHR is a real time
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10UML AND CRYPTOGRAPHY
application based software the algorithm would perfectly fit its purpose. The proposed 1024 bit
encryption is so advanced for our time that it would make it impossible to hack the system (Al-
Omari 2016). Also due to the huge amount of traffic handled by the system, the new algorithm will
reduce the wait times by almost 90%.
Recommendation
The My Health Record or the MHR system can be improved in quite a few departments. The
following recommendations can be implemented in the MHR system:
The authentication part of the system could be improved using a better and more
sophisticated encryption algorithm. The proposed dynamic crypto algorithm can be used to
secure the authentication process by implementing 1024-bit encryption and 128 spaces
substitution encryption process. This will be a major improvement over Caesar or Playfair
cipher. This will help in preventing and securing the system against hackers and cyber
criminals.
The data that the system handles is very sensitive in nature. Such data are meant to be kept
in secrecy and should be encrypted properly. A cryptographic algorithm like the Blowfish
can be used to cipher the data and hide it from criminals. This will ensure the confidentiality
of the hospitals, doctors and the patients.
Secure data transmission between different actors (SSL or TSL which is needed for securing
communication between the various actors. SSL stands for secure socket layer is known to
be a standard for maintaining the overall security of internet connection. It is all about
safeguarding of sensitive data which is transmitted between two systems. The main notion
of this technology is preventing criminals from any kind of modification of transferred
information like personal details. TSL is just an update version which is very much secured
than SSL.
SHA-1 or MD5 is needed for hashing login details that is username and password after this
MHR system server will compare hash digest with rainbow table entry. MD5 is known to be
a series of message-digest algorithm which produces 128-bit value. It is generally expressed
in text format that is 32-digit hexadecimal number. SHA is a cryptographic hash algorithm
which produces 160-bit value. It is expressed in the form of 40 digit hexadecimal numbers.
SHA-1 is known to be a member of secure hash algorithm family.
Conclusion
The report totally focuses on the given scenario and discussed the various users that were
interacting with the system. These users were hospitals, doctors, researchers and pharmacists. The
data that the system handled was mainly the health information of patients. The report provides an
idea about the use cases and the misuse cases of the system. The report also highlights about the
different cryptographic algorithms available and discussed their working. The algorithms discussed
in this report were the symmetric key and asymmetric key algorithms along with the substitution
cipher algorithms. Each of these algorithms were explained with proper examples and their
functioning were highlighted. A reflection was also given about the use of public and private keys
in cryptography and the MHR.
The report also discussed about a new proposed algorithm that could be used to improve the
MHR further. Such an algorithm was chosen after reviewing multiple academic papers and journals
and discussed thoroughly in this report. The improved features and working of the proposed
algorithm was also stated. To conclude, the report covered all the important aspects of cryptography
and stated the ways in which such algorithms could be applied to the given scenario and further
improve the MHR.
application based software the algorithm would perfectly fit its purpose. The proposed 1024 bit
encryption is so advanced for our time that it would make it impossible to hack the system (Al-
Omari 2016). Also due to the huge amount of traffic handled by the system, the new algorithm will
reduce the wait times by almost 90%.
Recommendation
The My Health Record or the MHR system can be improved in quite a few departments. The
following recommendations can be implemented in the MHR system:
The authentication part of the system could be improved using a better and more
sophisticated encryption algorithm. The proposed dynamic crypto algorithm can be used to
secure the authentication process by implementing 1024-bit encryption and 128 spaces
substitution encryption process. This will be a major improvement over Caesar or Playfair
cipher. This will help in preventing and securing the system against hackers and cyber
criminals.
The data that the system handles is very sensitive in nature. Such data are meant to be kept
in secrecy and should be encrypted properly. A cryptographic algorithm like the Blowfish
can be used to cipher the data and hide it from criminals. This will ensure the confidentiality
of the hospitals, doctors and the patients.
Secure data transmission between different actors (SSL or TSL which is needed for securing
communication between the various actors. SSL stands for secure socket layer is known to
be a standard for maintaining the overall security of internet connection. It is all about
safeguarding of sensitive data which is transmitted between two systems. The main notion
of this technology is preventing criminals from any kind of modification of transferred
information like personal details. TSL is just an update version which is very much secured
than SSL.
SHA-1 or MD5 is needed for hashing login details that is username and password after this
MHR system server will compare hash digest with rainbow table entry. MD5 is known to be
a series of message-digest algorithm which produces 128-bit value. It is generally expressed
in text format that is 32-digit hexadecimal number. SHA is a cryptographic hash algorithm
which produces 160-bit value. It is expressed in the form of 40 digit hexadecimal numbers.
SHA-1 is known to be a member of secure hash algorithm family.
Conclusion
The report totally focuses on the given scenario and discussed the various users that were
interacting with the system. These users were hospitals, doctors, researchers and pharmacists. The
data that the system handled was mainly the health information of patients. The report provides an
idea about the use cases and the misuse cases of the system. The report also highlights about the
different cryptographic algorithms available and discussed their working. The algorithms discussed
in this report were the symmetric key and asymmetric key algorithms along with the substitution
cipher algorithms. Each of these algorithms were explained with proper examples and their
functioning were highlighted. A reflection was also given about the use of public and private keys
in cryptography and the MHR.
The report also discussed about a new proposed algorithm that could be used to improve the
MHR further. Such an algorithm was chosen after reviewing multiple academic papers and journals
and discussed thoroughly in this report. The improved features and working of the proposed
algorithm was also stated. To conclude, the report covered all the important aspects of cryptography
and stated the ways in which such algorithms could be applied to the given scenario and further
improve the MHR.

11UML AND CRYPTOGRAPHY
References
Al-Omari, A.H., 2016. Dynamic crypto algorithm for real-time applications DCA-RTA, key
shifting. IJACSA) International Journal of Advanced Computer Science and Applications, 7(1).
Arya, P.K., Aswal, M.S. and Kumar, V., 2015. Comparative Study of Asymmetric Key
Cryptographic Algorithms. International Journal of Computer Science & Communication
Networks, 5(1), pp.17-21.
Bhuiyan, M., Haque, F. and Shabnam, L., 2018. Integration of organisational models and UML Use
Case diagrams. Journal of Computers, 13(1), pp.1-18.
Dori, D., 2016. SysML: Use Case, Block, and State Machine Diagrams. In Model-Based Systems
Engineering with OPM and SysML (pp. 29-35). Springer, New York, NY.
Khan, S.S. and Tuteja, R.R., 2015. Security in cloud computing using cryptographic
algorithms. International Journal of Innovative Research in Computer and Communication
Engineering, 3(1), pp.148-155.
Patil, P., Narayankar, P., Narayan, D.G. and Meena, S.M., 2016. A comprehensive evaluation of
cryptographic algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Computer Science, 78,
pp.617-624.
Pereira, G.C., Alves, R.C., Silva, F.L.D., Azevedo, R.M., Albertini, B.C. and Margi, C.B., 2017.
Performance evaluation of cryptographic algorithms over IoT platforms and operating
systems. Security and Communication Networks, 2017.
Perrig, A., Szalachowski, P., Reischuk, R.M. and Chuat, L., 2017. Cryptographic Algorithms.
In SCION: A Secure Internet Architecture (pp. 381-386). Springer, Cham.
Verma, A., Guha, P. and Mishra, S., 2016. Comparative Study of Different Cryptographic
Algorithms. International Journal of Emerging Trends & Technology in Computer Science
(IJETTCS), 5(2), pp.58-63.
…..
References
Al-Omari, A.H., 2016. Dynamic crypto algorithm for real-time applications DCA-RTA, key
shifting. IJACSA) International Journal of Advanced Computer Science and Applications, 7(1).
Arya, P.K., Aswal, M.S. and Kumar, V., 2015. Comparative Study of Asymmetric Key
Cryptographic Algorithms. International Journal of Computer Science & Communication
Networks, 5(1), pp.17-21.
Bhuiyan, M., Haque, F. and Shabnam, L., 2018. Integration of organisational models and UML Use
Case diagrams. Journal of Computers, 13(1), pp.1-18.
Dori, D., 2016. SysML: Use Case, Block, and State Machine Diagrams. In Model-Based Systems
Engineering with OPM and SysML (pp. 29-35). Springer, New York, NY.
Khan, S.S. and Tuteja, R.R., 2015. Security in cloud computing using cryptographic
algorithms. International Journal of Innovative Research in Computer and Communication
Engineering, 3(1), pp.148-155.
Patil, P., Narayankar, P., Narayan, D.G. and Meena, S.M., 2016. A comprehensive evaluation of
cryptographic algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Computer Science, 78,
pp.617-624.
Pereira, G.C., Alves, R.C., Silva, F.L.D., Azevedo, R.M., Albertini, B.C. and Margi, C.B., 2017.
Performance evaluation of cryptographic algorithms over IoT platforms and operating
systems. Security and Communication Networks, 2017.
Perrig, A., Szalachowski, P., Reischuk, R.M. and Chuat, L., 2017. Cryptographic Algorithms.
In SCION: A Secure Internet Architecture (pp. 381-386). Springer, Cham.
Verma, A., Guha, P. and Mishra, S., 2016. Comparative Study of Different Cryptographic
Algorithms. International Journal of Emerging Trends & Technology in Computer Science
(IJETTCS), 5(2), pp.58-63.
…..
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





