UML and Cryptography
12 Pages3025 Words447 Views
Added on 2023-04-21
About This Document
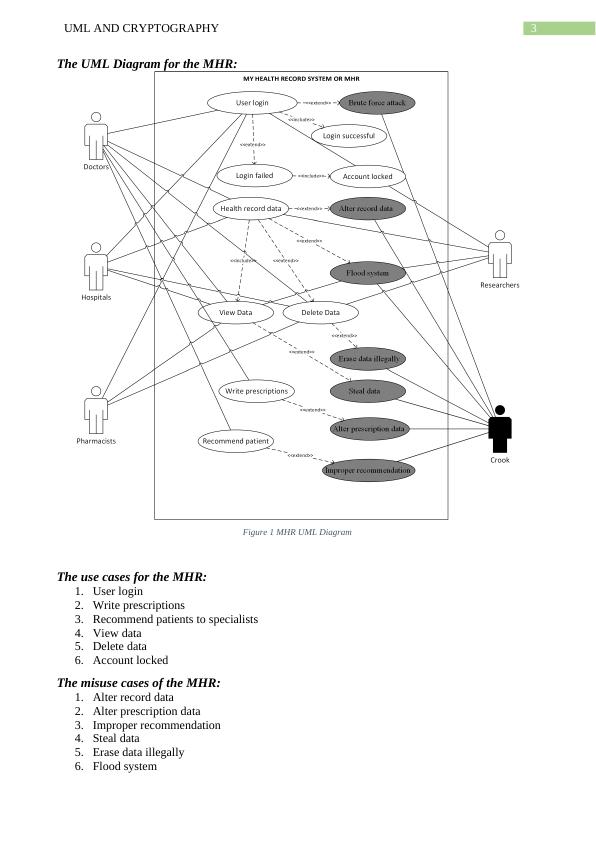
This report explores the use of UML and Cryptography in the Australian My Health Record (MHR) system. It discusses the use cases and misuse cases of the MHR system, compares symmetric and asymmetric key algorithms, and analyzes cipher substitution algorithms. It also proposes the implementation of a new cryptographic algorithm in the MHR system for improved security.
UML and Cryptography
Added on 2023-04-21
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
The cryptographic algorithm assignment
|9
|1446
|21
Principle and Method in Cryptographic Security | Discussion
|4
|638
|19
Symmetric Encryption Assignment
|5
|884
|175
Cryptographic Algorithms for Australian My Health Record System
|6
|1809
|47
Security at an Instant Messaging Service
|15
|3178
|96
Cryptographic Techniques
|6
|2878
|62