Case Study: TSB IT System Failure - Ethics, Power, and Reliability
VerifiedAdded on 2023/04/20
|19
|3612
|111
Essay
AI Summary
This essay provides a comprehensive analysis of the TSB IT system failure, examining it through the lens of socio-technical systems theory, the ETHICS framework, and stakeholder power dynamics. It includes a system map illustrating the interactions between users, the software system, IT experts, and hardware engineers. The analysis identifies issues of power between developers, management, and middleware, and discusses how the ETHICS framework could have been applied to prevent the failure. The essay also explores the use of agile methodologies and evaluates the system's reliability and availability, highlighting why independently designed software components can still lead to system failure. Finally, it addresses privacy challenges using Daniel Solove’s privacy model and explains the false privacy versus security dichotomy.

University:
Essay Title:
Your Name:
Date:
Lecturer’s Name and Course Number:
Essay Title:
Your Name:
Date:
Lecturer’s Name and Course Number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 1
a. Consider the IT system described in the case study as a socio-technical system.
i. Draw a system map
Answer:
Figure 1: System Map
Figure one is a general system map, which is the basis of a social-technical design of TSB
system. It describes the interaction end of the system depending on which users/clients socially
interact with the system and also with the psychologist cognitive framework. The software
system stands as a computer as per scientist information system engineers. TSB bank system
infrastructure is placed below the middleware, which includes both the IT experts and data
handlers within the TSB bank. The TSB hardware system is the data centers hosted by IBM in
the UK which comprises the hardware engineers.
ii. Developing the systems map into a diagram showing the three components of
Technology, Organisation and People.
Answer:
Page 2 of 19
HardwareSystem(IBMDataCenter)SoftwareSytem(Middleware)CognitiveandSocialSystem(User/Client)
a. Consider the IT system described in the case study as a socio-technical system.
i. Draw a system map
Answer:
Figure 1: System Map
Figure one is a general system map, which is the basis of a social-technical design of TSB
system. It describes the interaction end of the system depending on which users/clients socially
interact with the system and also with the psychologist cognitive framework. The software
system stands as a computer as per scientist information system engineers. TSB bank system
infrastructure is placed below the middleware, which includes both the IT experts and data
handlers within the TSB bank. The TSB hardware system is the data centers hosted by IBM in
the UK which comprises the hardware engineers.
ii. Developing the systems map into a diagram showing the three components of
Technology, Organisation and People.
Answer:
Page 2 of 19
HardwareSystem(IBMDataCenter)SoftwareSytem(Middleware)CognitiveandSocialSystem(User/Client)

Figure 2: Social-Technical System
The components discussed in Figure 2, technology, organization and the people are the outcome.
Technology: In this diagram, both the hardware and the software are referred to as emerging
technologies. Similarly, computer science is considered as a hybrid of engineering and
mathematics. Thus, Information Technology (IT) is not a subset of computer science or
technology but a subset of engineering.
Organization: In the diagram, the organization comprises of technical infrastructure, system
access and workflow and process.
People: This section is comprised of the Job roles, user roles and social interactions
Page 3 of 19
Techn
ical
infrast
ructur
e
Syste
m
access
workfl
ow
and
proces
s
Job
Roles
User
Roles
Social
Intera
ctions
The components discussed in Figure 2, technology, organization and the people are the outcome.
Technology: In this diagram, both the hardware and the software are referred to as emerging
technologies. Similarly, computer science is considered as a hybrid of engineering and
mathematics. Thus, Information Technology (IT) is not a subset of computer science or
technology but a subset of engineering.
Organization: In the diagram, the organization comprises of technical infrastructure, system
access and workflow and process.
People: This section is comprised of the Job roles, user roles and social interactions
Page 3 of 19
Techn
ical
infrast
ructur
e
Syste
m
access
workfl
ow
and
proces
s
Job
Roles
User
Roles
Social
Intera
ctions
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

b. In about 150 words describe that way that the ETHICS framework could have been
applied when analyzing the IT system described in the case study.
Answer:
During the development period, the factors like testing analyzing, troubleshooting issues or
maintaining in TSB applications and records ought to been have possibly interrogated if they are
identified with an issue. Showing samples of pages, documents, report output or business flow in
the documentation, suitable measures required been taken to mask the data and to protect the
identity of the individual(s) related to the information. For benefits of presentation, development,
maintaining, testing, examining, or investigating, accurate measures are to be taken for data
camouflage to ensure the personality of the individual (s) is associated with the information. The
information contained in log documents and databases need not be revealed before the need of
the IT group to create, investigate, maintain and perform diagnostics excluding the instruction
received from legitimate TSB or lawful specialists. Lastly, viewing any information in databases
or logs that fall out of the staff accountability shall be prohibited
c. In about 150 words, suggest and describe at least three issues of power between at least
three of the key stakeholders in this IT system.
Answer:
The key stakeholders are TSB IT system is
i. Developers - The developer has the power to request the TSB bank to run the new system
concurrently with the old one before the bank opts for running the system for the testing purpose.
Page 4 of 19
applied when analyzing the IT system described in the case study.
Answer:
During the development period, the factors like testing analyzing, troubleshooting issues or
maintaining in TSB applications and records ought to been have possibly interrogated if they are
identified with an issue. Showing samples of pages, documents, report output or business flow in
the documentation, suitable measures required been taken to mask the data and to protect the
identity of the individual(s) related to the information. For benefits of presentation, development,
maintaining, testing, examining, or investigating, accurate measures are to be taken for data
camouflage to ensure the personality of the individual (s) is associated with the information. The
information contained in log documents and databases need not be revealed before the need of
the IT group to create, investigate, maintain and perform diagnostics excluding the instruction
received from legitimate TSB or lawful specialists. Lastly, viewing any information in databases
or logs that fall out of the staff accountability shall be prohibited
c. In about 150 words, suggest and describe at least three issues of power between at least
three of the key stakeholders in this IT system.
Answer:
The key stakeholders are TSB IT system is
i. Developers - The developer has the power to request the TSB bank to run the new system
concurrently with the old one before the bank opts for running the system for the testing purpose.
Page 4 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This highlights the issue of powers with the bank since the company fails to consult with the
developers before executing the application.
ii. Management - Management stands the primary department of the decision making process and
execution of the same decision. The execution and workability of the system are conducted by
seeking technical advice from the sources like middleware and IBM who were expected to
monitor and run the program.
iii. Middleware - Since the launch of the program, middleware is accountable for running the
program. Despite having effective knowledge regarding IT, middleware could have incorporated
both the IBM and the developers in the initial running of the program.
Page 5 of 19
developers before executing the application.
ii. Management - Management stands the primary department of the decision making process and
execution of the same decision. The execution and workability of the system are conducted by
seeking technical advice from the sources like middleware and IBM who were expected to
monitor and run the program.
iii. Middleware - Since the launch of the program, middleware is accountable for running the
program. Despite having effective knowledge regarding IT, middleware could have incorporated
both the IBM and the developers in the initial running of the program.
Page 5 of 19

Question 2
a. Definition of methods in system methodology
Answer:
Methods is a set of concept and analytic approach, which is also a general approach based on
system methodology comprising of decision-making processes.
The evolution of high-speed technology as the means of simulating mathematical models:
The theory of information feedback systems and the use of mathematical models highlights in
simulating convoluted systems. Further, method development involves five distinct phases which
are problem structuring, dynamic modeling, causal looping, scenario modeling and planning as
well as execution and organizational learning. Nonetheless, methods do not require all phases to
be carried out.
b. Making use of Agile
Answer:
Recently, an international bank decided on perceiving how clients would react to another email
offer. This included pulling together of a mailing list, tidied it up, iterated on duplicate and
structure and checking with legitimate for a few time to get the required approvals. Seven
weeks later, they were prepared to connect Agile with the organization's advertising system.
Agile, in the marketing setting implying information and examination to continuously source
promising answers or opportunities for progressive issues, deploying tests, assessing outcomes,
Page 6 of 19
a. Definition of methods in system methodology
Answer:
Methods is a set of concept and analytic approach, which is also a general approach based on
system methodology comprising of decision-making processes.
The evolution of high-speed technology as the means of simulating mathematical models:
The theory of information feedback systems and the use of mathematical models highlights in
simulating convoluted systems. Further, method development involves five distinct phases which
are problem structuring, dynamic modeling, causal looping, scenario modeling and planning as
well as execution and organizational learning. Nonetheless, methods do not require all phases to
be carried out.
b. Making use of Agile
Answer:
Recently, an international bank decided on perceiving how clients would react to another email
offer. This included pulling together of a mailing list, tidied it up, iterated on duplicate and
structure and checking with legitimate for a few time to get the required approvals. Seven
weeks later, they were prepared to connect Agile with the organization's advertising system.
Agile, in the marketing setting implying information and examination to continuously source
promising answers or opportunities for progressive issues, deploying tests, assessing outcomes,
Page 6 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and quickly emphasizing. At scale, an advanced agile marketing organization can run many
campaigns at the same time and various new concepts as well on a constant basis.
There are various requirements for agile marketing to work. A promoting organization must have
a reasonable sense of what it needs to achieve with its agile activity (e.g., which client sections it
needs to secure or which client decisions it needs to enhance) and have adequate information
regarding the investigation and the correct sort of advertising innovation foundation set up. This
innovation segment enables marketers to catch, total, and oversee information from different
frameworks. It settles on choices depending on cutting edge inclination and next-best-activity
models. It also robotizes the conveyance of battles and messages crosswise over channels, and
feed client following and message execution into the framework. (It needs to come under notice
that the tech devices do not need to be immaculate. In fact, it can be a trap to focus on them
excessively. Most organizations have the surfeit of instruments.)
Another pivotal fundamental is sponsorship and moreover, stewardship is considered as the
attempt to agile by senior promoting leaders. They provide the key assets with critical support
during unavoidable opposition and ensure better approaches are given for working experience.
While the above-mentioned components are pivotal for progress, the most essential determinant
is people, responsible for uniting a little group of capable individuals able to cooperate
effectively at speed. It’s necessary for them to have aptitudes over various capacities (both
external and internal) that can be discharged from their business as usual day occupations to
cooperate all day and be collocated (War room). The mission of the war-room group is to
Page 7 of 19
campaigns at the same time and various new concepts as well on a constant basis.
There are various requirements for agile marketing to work. A promoting organization must have
a reasonable sense of what it needs to achieve with its agile activity (e.g., which client sections it
needs to secure or which client decisions it needs to enhance) and have adequate information
regarding the investigation and the correct sort of advertising innovation foundation set up. This
innovation segment enables marketers to catch, total, and oversee information from different
frameworks. It settles on choices depending on cutting edge inclination and next-best-activity
models. It also robotizes the conveyance of battles and messages crosswise over channels, and
feed client following and message execution into the framework. (It needs to come under notice
that the tech devices do not need to be immaculate. In fact, it can be a trap to focus on them
excessively. Most organizations have the surfeit of instruments.)
Another pivotal fundamental is sponsorship and moreover, stewardship is considered as the
attempt to agile by senior promoting leaders. They provide the key assets with critical support
during unavoidable opposition and ensure better approaches are given for working experience.
While the above-mentioned components are pivotal for progress, the most essential determinant
is people, responsible for uniting a little group of capable individuals able to cooperate
effectively at speed. It’s necessary for them to have aptitudes over various capacities (both
external and internal) that can be discharged from their business as usual day occupations to
cooperate all day and be collocated (War room). The mission of the war-room group is to
Page 7 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
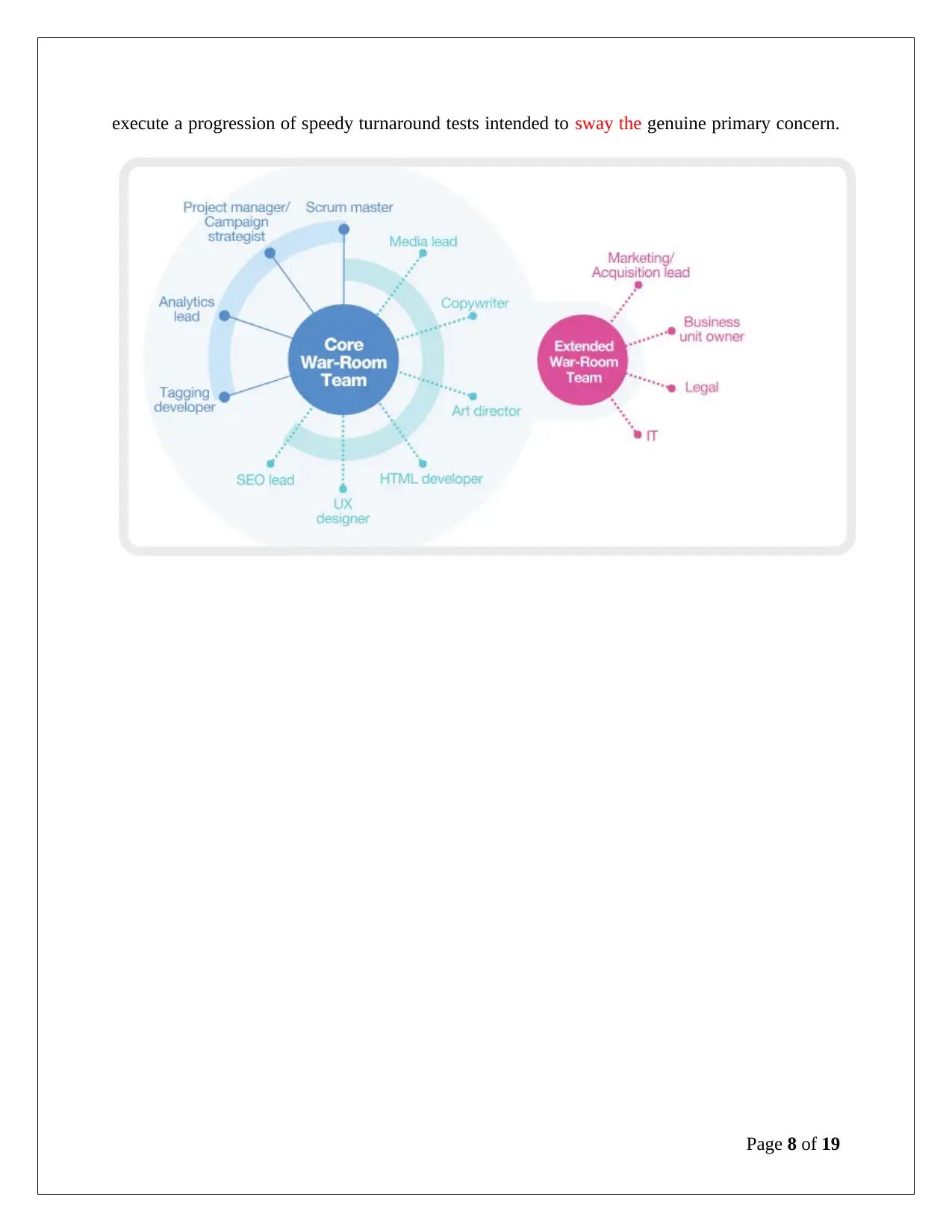
execute a progression of speedy turnaround tests intended to sway the genuine primary concern.
Page 8 of 19
Page 8 of 19

Question 3
a. The difference between reliability and availability
Answer
Reliability is an estimation of the likelihood of factors playing out beyond its planned capacity
for a predefined interim under expressed conditions. There is two generally utilized measure
of dependability:
* MTBF (Mean Time Between Failure), which is characterized as all out time in number/service
of flaws
* Failure Rate (λ) is characterized as a number of failures/all out of time in administration.
Availability is an Operations parameter, apparently defined the hardware that is accessible of
eighty-five per cent of the time, also developing at eighty-five per cent of the hardware's
technical point of confinement. Availability can also be estimated as Uptime + Downtime
(Uptime/Total time).
b. If a system has a mean time between failures (MTBF) of 800 hours and a mean time
to repair (MTTR) of 20 hours, what is its availability to three decimal places? Show your
working.
Answer:
Availability = MTTR/MTBF
Thus, 20/800
Page 9 of 19
a. The difference between reliability and availability
Answer
Reliability is an estimation of the likelihood of factors playing out beyond its planned capacity
for a predefined interim under expressed conditions. There is two generally utilized measure
of dependability:
* MTBF (Mean Time Between Failure), which is characterized as all out time in number/service
of flaws
* Failure Rate (λ) is characterized as a number of failures/all out of time in administration.
Availability is an Operations parameter, apparently defined the hardware that is accessible of
eighty-five per cent of the time, also developing at eighty-five per cent of the hardware's
technical point of confinement. Availability can also be estimated as Uptime + Downtime
(Uptime/Total time).
b. If a system has a mean time between failures (MTBF) of 800 hours and a mean time
to repair (MTTR) of 20 hours, what is its availability to three decimal places? Show your
working.
Answer:
Availability = MTTR/MTBF
Thus, 20/800
Page 9 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

= 0.025
c. Evaluate the overall reliability of the system, to 3 significant digits
Answer:
rKR20 is the Kuder-Richardson formula 20
k = total number of test items
Σ = sum
σ2 = variation of the reliability
Sum of reliability = 0.750 + 0.600 + 0.850 = 2.2
Σpq = 2.2
σ2 = 0.85 - 0.600 = (0.25)^2
=0.063
Substituting the values = (3/ (3-1)) (1 - (2.2/0.063)
= -20.600
d. Explain in around 100 words why a system using independently designed software
components can still fail
Page 10 of 19
c. Evaluate the overall reliability of the system, to 3 significant digits
Answer:
rKR20 is the Kuder-Richardson formula 20
k = total number of test items
Σ = sum
σ2 = variation of the reliability
Sum of reliability = 0.750 + 0.600 + 0.850 = 2.2
Σpq = 2.2
σ2 = 0.85 - 0.600 = (0.25)^2
=0.063
Substituting the values = (3/ (3-1)) (1 - (2.2/0.063)
= -20.600
d. Explain in around 100 words why a system using independently designed software
components can still fail
Page 10 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Answer
Failure of any part of the system results in the breakdown of the entire framework. It has been
discovered while considering total frameworks at their fundamental subsystem level that these
are organized dependability savvy following a series setup. When inspecting components are
designed independently, it has been found that the least reliable segment has the greatest impact
on the reliability quality of the framework. Nevertheless, the section having the most astounding
dependability has the greatest impact on the framework's reliability quality, since the most
reliable component would in total probability fail atlas.
Page 11 of 19
Failure of any part of the system results in the breakdown of the entire framework. It has been
discovered while considering total frameworks at their fundamental subsystem level that these
are organized dependability savvy following a series setup. When inspecting components are
designed independently, it has been found that the least reliable segment has the greatest impact
on the reliability quality of the framework. Nevertheless, the section having the most astounding
dependability has the greatest impact on the framework's reliability quality, since the most
reliable component would in total probability fail atlas.
Page 11 of 19

Question 4
a. Using Daniel Solove’s privacy model explain three key challenges to privacy that could
have been considered which may have helped Irish government ministers and officials
involved in building and operating the Public Services Card IT system.
Answer
Security: In the tools like the internet, hackers can find it extremely simple to get access to any
system or computer as long as it is linked to the web. Hackers can easily employ an Internet
Protocol (IP) address to access a client's computers based information and gather users’
confidential data. Similarly, the widespread network cookies that collect information at any
given point using the network would create high risks of conflicting interests and fraud. Most
leading organizations utilize these cookies to figure out which service or product they can
promote. With the support of online banking, the transaction of money can be easily hindered by
hackers and the entire financial amount can be easily exchanged to their ideal records, which
would cause trouble for both banks and its customer to incur severe threat who are using web-
based managing accounting subject
Copyright Infringement: It is easy for a customer to get any information or antiquity at anygiven
time by using IT. With the advancements of music sharing framework and photograph recording
websites, numerous unique developers in the specific domain are losing the credibility of works,
because customers in the IT domain can obtain access with allot easiness and offer that data with
peers. Free document and music downloading websites are springing up on the web each day, a
lot of unique work like music albums, books, are being downloaded file that is not required.
Page 12 of 19
a. Using Daniel Solove’s privacy model explain three key challenges to privacy that could
have been considered which may have helped Irish government ministers and officials
involved in building and operating the Public Services Card IT system.
Answer
Security: In the tools like the internet, hackers can find it extremely simple to get access to any
system or computer as long as it is linked to the web. Hackers can easily employ an Internet
Protocol (IP) address to access a client's computers based information and gather users’
confidential data. Similarly, the widespread network cookies that collect information at any
given point using the network would create high risks of conflicting interests and fraud. Most
leading organizations utilize these cookies to figure out which service or product they can
promote. With the support of online banking, the transaction of money can be easily hindered by
hackers and the entire financial amount can be easily exchanged to their ideal records, which
would cause trouble for both banks and its customer to incur severe threat who are using web-
based managing accounting subject
Copyright Infringement: It is easy for a customer to get any information or antiquity at anygiven
time by using IT. With the advancements of music sharing framework and photograph recording
websites, numerous unique developers in the specific domain are losing the credibility of works,
because customers in the IT domain can obtain access with allot easiness and offer that data with
peers. Free document and music downloading websites are springing up on the web each day, a
lot of unique work like music albums, books, are being downloaded file that is not required.
Page 12 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




