Strategic Information Systems Analysis for Bell Studio (HI5019)
VerifiedAdded on 2023/01/18

Unit code: HI5019
Unit Title: Strategic Information Systems for Business and Enterprise
Name: MD SHAHRIAR ALAM
Student Id: OED2391
Paraphrase This Document

Table of Contents
Executive summary................................................................................................................................1
Introduction..............................................................................................................................................2
Data flow diagram of purchases and cash disbursement systems...........................................3
Internal control weakness and risks associated.........................................................................4
Remedies to the weaknesses in the purchasing and cash disbursement system.............5
Data flow diagram of payroll system.................................................................................................6
Internal Weaknesses of the payroll system and risks they pose............................................8
Remedies to the risks posed by the internal weakness of the payroll system...................8
System flowchart of purchases system............................................................................................9
Internal control weakness of purchases system and their risks..........................................11
Remedies to the weaknesses of the purchases system.........................................................11
System flowchart of cash disbursement system..........................................................................12
Internal control weakness of the cash disbursement system...............................................12
Remedy to the internal control weakness..................................................................................13
System flowchart of payroll system.................................................................................................13
Internal control weaknesses of the payroll system and their risks......................................14
Remedies to the weakness of the payroll system....................................................................14
Conclusion.............................................................................................................................................15
Recommendation..................................................................................................................................15
Bibliography..........................................................................................................................................16

Executive summary
This report comes as a response to the request made by the chief operating officer to
evaluate the processes, risks and internal controls of Bell Studios for its expenditure
cycle. When evaluating the processes, data flow diagrams and system flowcharts were
drawn to depict the operation of the individual systems; purchase and cash
disbursement system and the payroll system for proper analysis. The internal control
weaknesses identified are the failure of the system to automatically generate an alert
message or report when the quantity of certain goods is low, the allocation of system
responsibilities to humans, manual generation of reports, manual storage of data and
lack of proper measures to check the integrity, reliability and accuracy of data. The
report suggests remedies for internal control weaknesses as implementing a business
intelligent information system for generating reports and calculating employee working
hours.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The report depicts the flow of activities using data flow diagrams and system flow chart
diagrams that are; the data flow diagram of purchases and cash disbursements
systems, the data flow diagram of payroll system, system flowchart of purchases
system, system flowchart of cash disbursements and system flowchart of the payroll
system. The description of internal control weakness in each system and risks
associated with the identified weakness is also articulated in the report. The report
expounds on how these risks might affect Bell Studios and how they can be mitigated,
providing solutions for each and every internal control weakness experienced in the
system. At the end of the report, there is a conclusion that gives an informed summary
of the report and a recommendation on what Bell Studios can do to eliminate the
internal control weaknesses and avoid the risks associated with them.
Paraphrase This Document
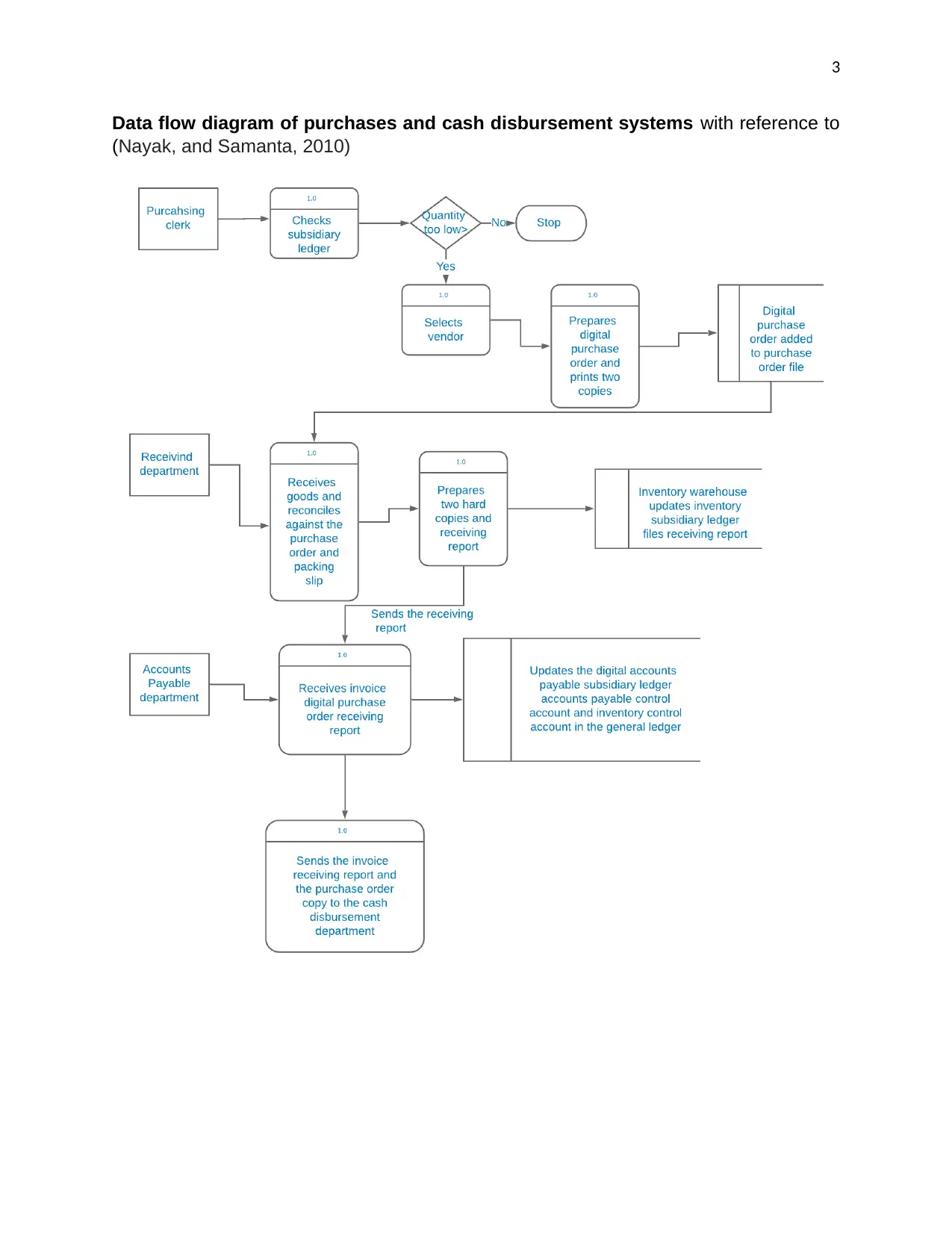
Data flow diagram of purchases and cash disbursement systems with reference to
(Nayak, and Samanta, 2010)
Internal control weakness and risks associated
The purchasing clerk checks the subsidiary ledger daily to find out whether the quantity
of the goods is too low or not in order to do the purchasing. Though done digitally, the
checking is manual. A business intelligence system should automatically check the
stock of the goods available in the store by analyzing the subsidiary ledger and notify
the purchasing clerk through a popup message. This will make the purchasing clerk’s
work easier because there will be no need for doing the manual daily checkups on the
subsidiary ledger.
The manual process of the purchasing clerk checking the subsidiary ledger can lead to
errors in the purchase order for instance, stating a purchase order for an incorrect
amount of goods. A purchasing clerk can just make modifications on the purchasing
order for his or her own fraudulent ambitions for instance, profiting from selling the
excess ordered goods or even crippling Bell Studios’ operation.
In the receiving department, when the clerk receives goods he or she prepares two
receiving reports manually. The manual preparation of the report is a weakness in the
system because it is prone to many human-oriented risks and threats. The human
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

component of a computer system is prone to make errors during the preparation of the
receiving report. The computation will never be accurate all the time.
The printed digital purchase order and the receiving report are filed manually in the
purchase and cash disbursement system. The manual filing of the reports is very
disastrous to Bell Studios business because of the following risks associated to the
data; data loss caused by natural calamities or misplacement of the files by the clerks
handling them. Hard copies of data are also easy to access, modify or destroy by
unauthorized personnel once they gain access to the store and purchasing
departments.
Remedies to the weaknesses in the purchasing and cash disbursement system.
Bell Studios need to implement a business intelligent system according to (Turban,
Sharda & Delen 2010) and (Duan, and Da Xu, 2012) that automatically checks whether
the quantity of goods is low or still in stock and generate an alert message alerting the
purchasing clerk of the stock level when the quantity of goods is too low. This will help
minimize the fraudulent risks that Bell Studios is up against leaving all the control issues
on the purchasing clerk.
Bell Studios should keep a record of all the transaction logs (Lee, Khan & Kim, 2011).
The logs record the information on when a transaction or an event was initiated, who
initiated the transaction and what effect the transaction had on the stored data or the
internal control of the system. Transaction logs help mitigate repudiation attacks where
a purchasing clerk or the clerk in the store denies performing or initiating a certain
process in the system.
The manual filling process should be eliminated from the system. All the records and
files should be stored in a centralized database where all the departments in Bell
Studios can update it whenever necessary. The files should also be backed up using
the available backup techniques like; online backup, offline backups using physical hard
drives placed in a separate location and cloud backup. Doing this, Bell Studios will avoid
unnecessary data loss caused by natural calamity or erroneous human actions.
The professional ethics framework should be set and upheld by the management of Bell
Studios. The ethics will be a guideline for professional responsibility and a depiction of
professional maturity (Bayou, Reinstein & Williams, 2011) for employees at Bell Studios.
The framework will help reduce the fraudulent behaviors that employees might develop.
It should also identify the pressure points in the work environment and find a way to
reduce or ease the pressure on the employees.
Paraphrase This Document

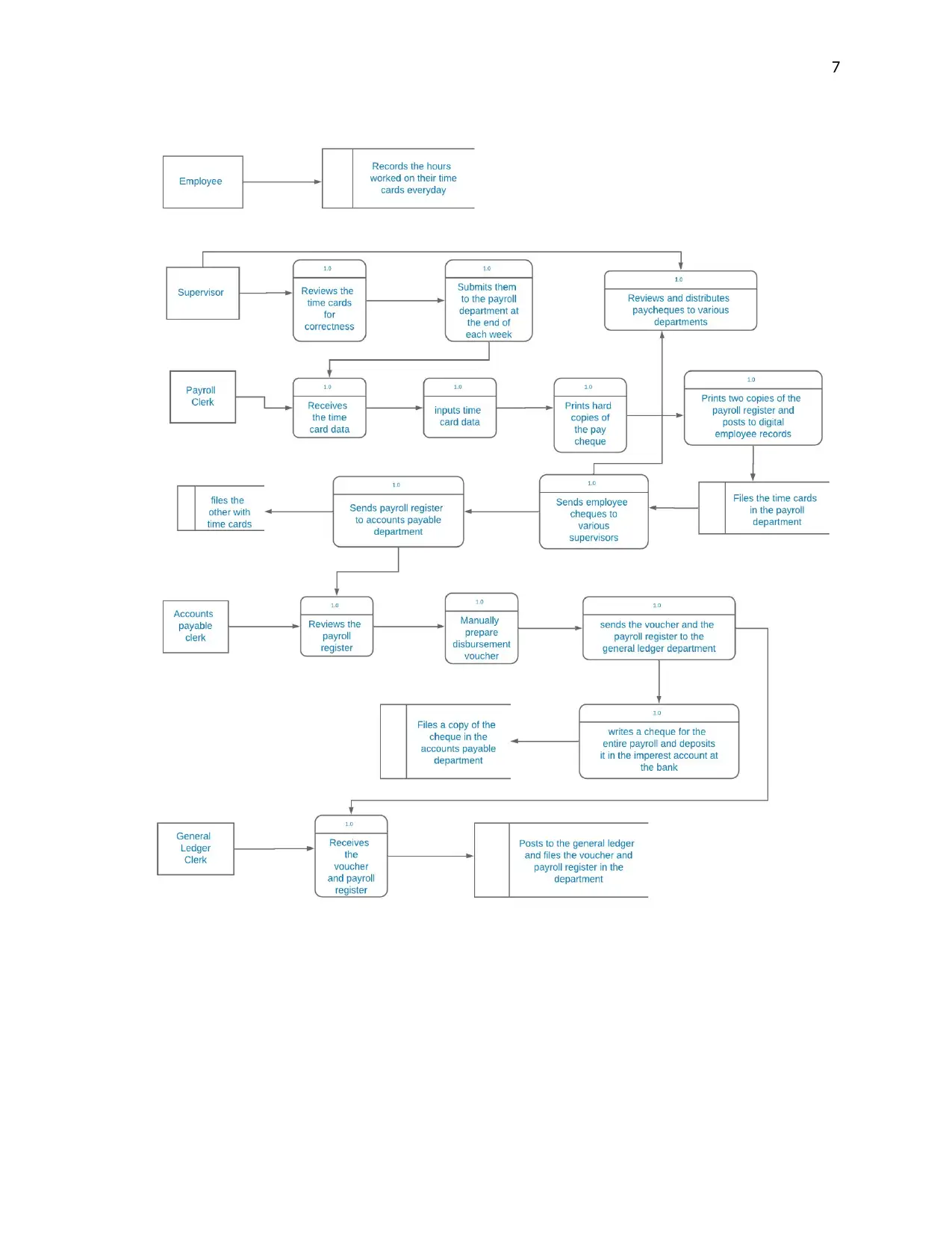
Data flow diagram of payroll system with reference to (Nayak, and Samanta, 2010)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internal Weaknesses of the payroll system and risks they pose
Employees recording their own working hours in their time cards and having their
supervisors counter check the working hours of the employees poses a great financial
risk to Bell Studios. Employees can collude with their supervisors to enter more working
hours than they actually did. This translates to more payment than it is supposed to be
for the management of Bell Studios. The privilege a supervisor has can be misused
when a supervisor and an employee are not in good terms with each other. The system
hands a lot of power to the supervisor whereby, after the payroll clerk has input the
working hours of the employees he or she sends the pay cheques to the supervisor for
review and distribution.
Manual input of the employee time card data by the payroll clerk is also a weakness in
internal control. The payroll clerk can input values deviating from the actual working
hours an employee did. This poses a risk on the integrity of the employee payment
computed by the system, because a payroll clerk can deliberately or unintentionally
input erroneous working hours to the system.
Manual preparation and storage of data also pose data modification, error propagation
and data loss risks to Bell Studios. Data stored manually can be lost through natural
calamities like fire, floods and tsunamis. It can also be misplaced, modified or destroyed
intentionally or unintentionally by the same employees handling the data.
Remedies to the risks posed by the internal weakness of the payroll system.
Bell Studios should implement an attendance recording system (Chintalapati, and
Raghunadh, 2013) where employees only record their time in and the time out of the
premises of Bell Studios. The system should then calculate the working hours by
subtracting the time in from the time out and record the working hours of each
employee. The information extracted after the calculation is the final one and one that
will be viewed by the payroll clerk when processing cheques. This will reduce the
workload given to employee supervisors who do the counter checking of the employee
working hours and review the working hours’ details send from the payroll clerk.
The attendance recording system will eliminate the risk of fraud and collusion from the
employee and the supervisor to fraudulently acquire high payments. It will also eliminate
the risk originating from the payroll clerk, employee or supervisor deliberately or
unintentionally making erroneous inputs of the employee working hours that deviate
from the actual working hours that the employees actually did.
Paraphrase This Document

System flowchart of purchases system with reference to (Nayak, and Samanta,
2010)
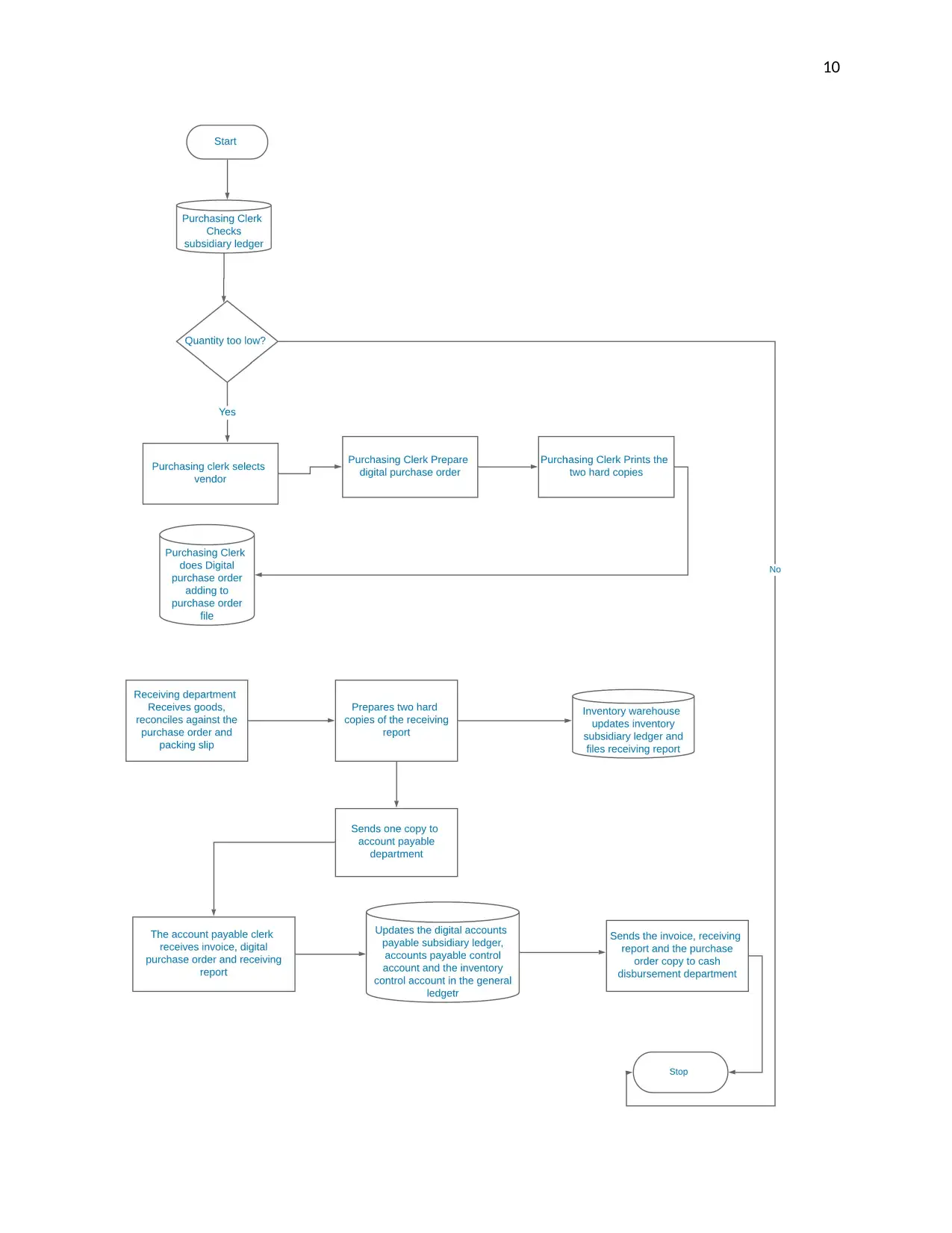
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internal control weakness of purchases system and their risks
The purchase system hands a human; the purchasing clerk, the task of checking stock
or determining whether the quantity of certain goods is too low instead of handing the
task to the system. This may lead to inappropriate handling of the stock renewal
because the purchasing clerk might interpret the stock wrongly. For instance,
misquotation of the required amount of goods which may lead to over budgeting or
under budgeting.
The receiving clerk prepares and sends the receiving reports manually to the accounts
payable clerk. Hard copies of reports are vulnerable to natural calamities like fire and
floods, human manipulation and access by unauthorized personnel. This risks Bell
Studios losing their private and confidential data to natural calamities or to unauthorized
personnel.
Remedies to the weaknesses of the purchases system
The task of checking stock levels should be handed to the business intelligence system.
The systems should be checking the amount of each good from the stock every other
time it is updated and automatically generate a report or an alert for a purchase clerk
notifying him or her of a good gone out of stock or being low in quantity ( Atanasova
et.al; 2010). This reduces the responsibilities bestowed upon a purchases clerk and
reduces the possibilities of experiencing erroneous purchase orders that are the
probability of over budgeting and under-budgeting being experienced will be limited.
Having a computerized way of preparing reports helps in reducing the amount of time
needed to prepare the report (Gandomi, and Haider, 2015) and (Ko, Lee & Wah Lee,
2009). Handling and sending reports digitally reduces the risks of data loss through
natural calamities and unauthorized personnel because of the presence of backups for
data and encryption of data to ensure its safety during transit.
Paraphrase This Document
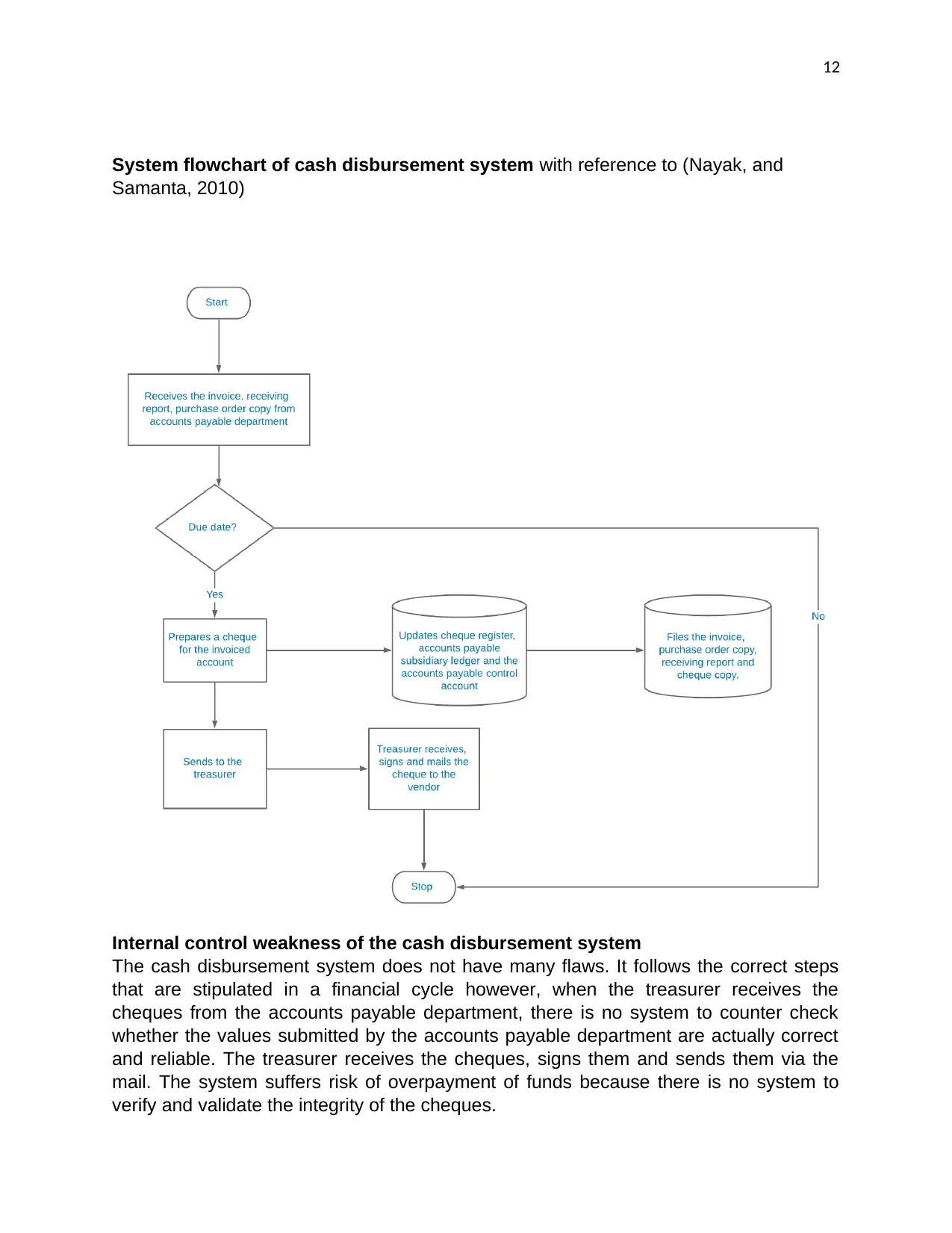
System flowchart of cash disbursement system with reference to (Nayak, and
Samanta, 2010)
Internal control weakness of the cash disbursement system
The cash disbursement system does not have many flaws. It follows the correct steps
that are stipulated in a financial cycle however, when the treasurer receives the
cheques from the accounts payable department, there is no system to counter check
whether the values submitted by the accounts payable department are actually correct
and reliable. The treasurer receives the cheques, signs them and sends them via the
mail. The system suffers risk of overpayment of funds because there is no system to
verify and validate the integrity of the cheques.
Remedy to the internal control weakness
The system should provide a module, process or a method through which the cheque
details handed to the treasurer for signing and mailing to the vendor can be verified for
reliability (Elbashir, Collier & Sutton, 2011) often termed as accounting.
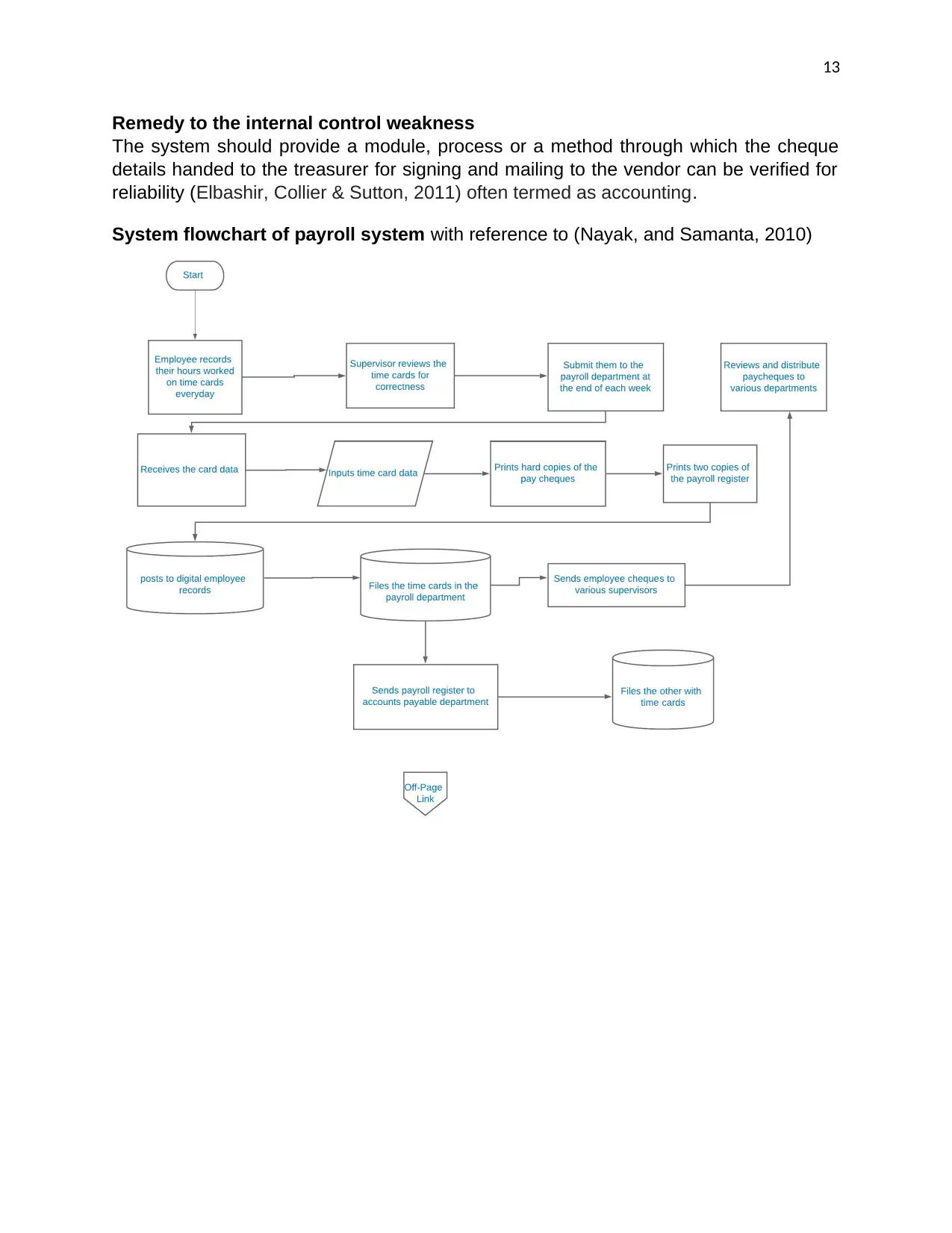
System flowchart of payroll system with reference to (Nayak, and Samanta, 2010)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Internal control weaknesses of the payroll system and their risks
The recording of the employee working hours is solely dependent on the employees
and their supervisors. This system suffers risk of operating on erroneous or fraudulent
employee working hours’ data, which can be caused by the employees and their
supervisors performing their duties unethically.
Manual input of the employee time card data by the payroll clerk is also a weakness in
internal control. The payroll clerk can input values deviating from the actual working
hours an employee did. This poses a risk on the integrity of the employee payment
computed by the system, because a payroll clerk can deliberately or unintentionally
input erroneous working hours to the system.
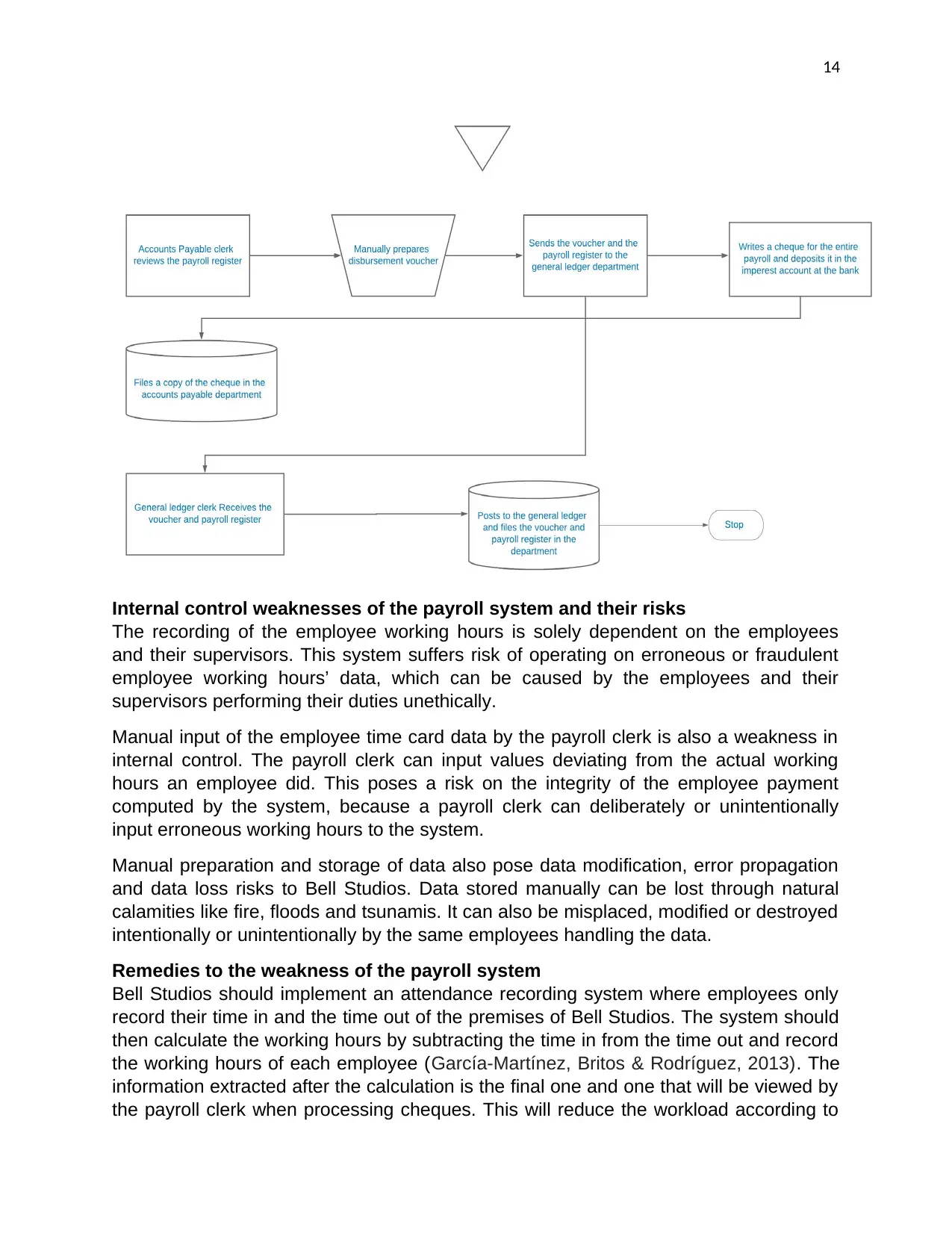
Manual preparation and storage of data also pose data modification, error propagation
and data loss risks to Bell Studios. Data stored manually can be lost through natural
calamities like fire, floods and tsunamis. It can also be misplaced, modified or destroyed
intentionally or unintentionally by the same employees handling the data.
Remedies to the weakness of the payroll system
Bell Studios should implement an attendance recording system where employees only
record their time in and the time out of the premises of Bell Studios. The system should
then calculate the working hours by subtracting the time in from the time out and record
the working hours of each employee (García-Martínez, Britos & Rodríguez, 2013). The
information extracted after the calculation is the final one and one that will be viewed by
the payroll clerk when processing cheques. This will reduce the workload according to
Paraphrase This Document

(Chen, Chiang & Storey, 2012) given to employee supervisors who do the counter
checking of the employee working hours and review the working hours’ details send
from the payroll clerk.
Conclusion
The systems face common internal control weaknesses; misallocation of system-
oriented tasks and responsibilities to humans, manual processing and storing of data,
repetition of the data input process, lack of measures to check the reliability of
information and manual generation of reports. These weaknesses cause error
propagation, data loss and fraudulent practices going against the professional code of
ethics. These weaknesses are evident through; employees filling their time cards,
supervisors being given an additional responsibility of verifying the working hours of
employees in the time cards and validating the cheques, payroll clerk doing inputs of the
working hours from the time cards to the payroll system and the data processing being
achieved manually.
Recommendation
Bell Studios should implement business intelligence aspect of information systems in all
their systems. For instance, the report auto-generation in the purchasing department
where the purchase system automatically displays an alert message when the quantity
of goods becomes too low in the store. Automatic calculation and recording of the
employee working hours through the use of an attendance information system that only
takes the employee’s time in and time out of Bell Studios premises when their allocated
work is complete. Bell Studios should also upgrade the processing of data from manual,
as observed in the receiving department where receiving reports are generated
manually, to digital.

Bibliography
Atanasova, T., Kasheva, M., Sulova, S. and Vasilev, J., 2010, May. Analysis of the
possible application of Data Mining, Text Mining and Web Mining in business intelligent
systems. In The 33rd International Convention MIPRO (pp. 1294-1297). Ukraine, IEEE.
Bayou, M.E., Reinstein, A. and Williams, P.F., 2011. To tell the truth: A discussion of
issues concerning truth and ethics in accounting. Accounting, Organizations and
Society, 36(2), pp.109-124. New York, Elsevier.
Chen, H., Chiang, R.H. and Storey, V.C., 2012. Business intelligence and analytics:
From big data to big impact. MIS quarterly, 36(4).
Chintalapati, S. and Raghunadh, M.V., 2013, December. Automated attendance
management system based on face recognition algorithms. In 2013 IEEE International
Conference on Computational Intelligence and Computing Research (pp. 1-5). Cavtat,
Croatia. IEEE
Duan, L. and Da Xu, L., 2012. Business intelligence for enterprise systems: a
survey. IEEE Transactions on Industrial Informatics, 8(3), pp.679-687. Heidelberg.
Springer.
Elbashir, M.Z., Collier, P.A. and Sutton, S.G., 2011. The role of organizational
absorptive capacity in strategic use of business intelligence to support integrated
management control systems. The Accounting Review, 86(1), pp.155-184. Florida,
American Accounting Association. Accessed [21 April 2019] Accessed from:
https://www.jstor.org/stable/29780228?seq=1#metadata_info_tab_contents
Gandomi, A. and Haider, M., 2015. Beyond the hype: Big data concepts, methods, and
analytics. International journal of information management, 35(2), pp.137-144. King
Saud University. Accessed [21 April 2019] Retrieved from:
https://www.sciencedirect.com/science/article/pii/S0268401214001066
García-Martínez, R., Britos, P. and Rodríguez, D., 2013, June. Information mining
processes based on intelligent systems. In International Conference on Industrial,
Engineering and Other Applications of Applied Intelligent Systems (pp. 402-410). Berlin,
Heidelberg. Springer
Ko, R.K., Lee, S.S. and Wah Lee, E., 2009. Business process management (BPM)
standards: a survey. Business Process Management Journal, 15(5), pp.744-791.
Singapore. Nanyang Technologica University.
Lee, M.W., Khan, A.M. and Kim, T.S., 2011. A single tri-axial accelerometer-based real-
time personal life log system capable of human activity recognition and exercise
information generation. Personal and Ubiquitous Computing, 15(8), pp.887-898. Varlag,
London. Springer.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Nayak, A. and Samanta, D., 2010. Automatic test data synthesis using uml sequence
diagrams. journal of Object Technology, 9(2), pp.75-104.MIT Library. Accessed [21 April
2019]. Retrieved from:
http://eprints.manipal.edu/id/eprint/261
Turban, E., Sharda, R. and Delen, D., 2010. Decision Support and Business Intelligence
Systems (required). Google Scholar.
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.





