BUSI 1475 Management in Critical Context Essay: Globalization & Tech
VerifiedAdded on 2021/08/11
|13
|3796
|102
Essay
AI Summary
This essay, submitted by a student at the University of Greenwich, explores management in a critical context, focusing on the impact of globalization, technology, and conflict. The introduction highlights data breaches and privacy concerns, referencing the Facebook data leak and the Cambridge Analytica scandal, emphasizing the public's growing concern for data privacy. The essay then delves into the impact of social media on globalization, discussing the role of digital technologies in facilitating communication and the limitations of internet freedom in various countries. It also addresses digital privacy challenges, including data protection policies and the use of AI in social media. The essay further examines how AI is transforming products through networks, such as Facebook, Instagram, Twitter, and LinkedIn, and simplifying repetitive tasks associated with social media management. It discusses how AI is used in social media marketing, including content creation, social media intelligence, and customer relationship management. The essay concludes by emphasizing the importance of understanding these interconnected elements in modern business management.
University of Greenwich (UOG)
Bachelor of Arts (Hons) Business Management (Top Up)
ASSIGNMENT / PROJECT COVER SHEET
(to be completed individually by student)
UOG ID Number 001146040
Course Specialization
(*Please delete whichever is not
applicable)
Marketing and Sales
Subject Code/Name BUSI 1475 / Management in Critical Context
Assignment Title Essay (100%)
Lecturer/Supervisor Mr. Chris Paget
Word count 3158
DECLARATION
I, the above named student, confirm that by submitting, or causing the attached
assignment to be submitted, I have not plagiarized any other person’s work in
this assignment and except where appropriately acknowledged, this assignment
is my own work, has been expressed in my own words, and has not previously
been submitted for assessment.
1
Bachelor of Arts (Hons) Business Management (Top Up)
ASSIGNMENT / PROJECT COVER SHEET
(to be completed individually by student)
UOG ID Number 001146040
Course Specialization
(*Please delete whichever is not
applicable)
Marketing and Sales
Subject Code/Name BUSI 1475 / Management in Critical Context
Assignment Title Essay (100%)
Lecturer/Supervisor Mr. Chris Paget
Word count 3158
DECLARATION
I, the above named student, confirm that by submitting, or causing the attached
assignment to be submitted, I have not plagiarized any other person’s work in
this assignment and except where appropriately acknowledged, this assignment
is my own work, has been expressed in my own words, and has not previously
been submitted for assessment.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
I. INTRODUCTION
.................................................................................................................3
II. GLOBALIZATION
..............................................................................................................3
1. The impact of social media on globalization.............................................................................3
2. Globalization and Digital privacy..............................................................................................5
III. TECHNOLOGY AND NETWORK
...................................................................................6
IV. CONFLICT AND CO-OPERATION
................................................................................9
1. Conflict.........................................................................................................................................9
2. Collaboration...............................................................................................................................9
V. CONCLUSION
...................................................................................................................10
REFERENCES
.......................................................................................................................11
2
I. INTRODUCTION
.................................................................................................................3
II. GLOBALIZATION
..............................................................................................................3
1. The impact of social media on globalization.............................................................................3
2. Globalization and Digital privacy..............................................................................................5
III. TECHNOLOGY AND NETWORK
...................................................................................6
IV. CONFLICT AND CO-OPERATION
................................................................................9
1. Conflict.........................................................................................................................................9
2. Collaboration...............................................................................................................................9
V. CONCLUSION
...................................................................................................................10
REFERENCES
.......................................................................................................................11
2

I. INTRODUCTION
From article from the BBC News “Facebook leak: Irish regulator probes 'old' data
dump”, Ireland's Data Protection Commission (DPC) is investigating the leak of Facebook
user information. Facebook said this was an previous leak, which it found and repaired more
than a year ago. However, cybersecurity officials remain concerned because of the large scale
of the leak, particularly it covers more than 530 million users in 106 countries around the
world. Facebook users whose privacy are affected by a major data breach are advised against
the technology giant to take legal action. About 530 million users were leaked with personal
data, including telephone numbers in some cases. On behalf of the EU people concerned, an
association on data privacy is about to take a case to the Irish courts. Facebook disputes
misconduct by claiming that the details were "scrapped" out of material available on the web.
Throughout the Cambridge Analytica breach, Facebook is being charged for not protecting
the personal data of users. The crisis was that 87 million users have been used for publicity
during elections were mined from Facebook records. Mass court proceedings against
Facebook over privacy theft are being held in England and Wales by over one million people.
The UK database watchdog fined £500,000 on Facebook for its involvement in the
Cambridge Analytica leak in October 2018. Facebook has authorized a "significant violation"
of the rules, the Information Commissioner's Office (ICO). Facebook excused and allowed
users to search the "banned applications" they had accessed.
In recent years social media users have become increasingly concerned for their
privacy. Data incidents have frightened many people and compelled them to replenish their
social media relationships and the safety of their personal information. The dramatic case of
the Cambridge Analytica consulting agency is an example. The company used more than 50
million Facebook users' private information to manipulate the presidential 2016 election in
the United States. This example and others have continuously worsened consumer confidence
and caused many consumers to ask if they have lost control of their own results. 80% of
social media consumers report worrying about companies and marketers who view and use
social media content, according to a survey by Pew trust. This increasing questions about
privacy have sparked stricter rules. Moreover, they have put more scrutiny into the business
of protecting personal records.
Only a couple of decades ago, it was impossible to present to strangers that sort of
physical pictures an data some of us get on social media today. Internet way and cultural
media have radically altered our attitdes about privacy. (Watson, P.W., Apr. 2018) increasing
questions about privacy have sparked stricter rules. Moreover, they have put more security
into the business of protecting personal information.
The social networks are used by 40% of the world's population. According to
information gathered by Hootesuite, 3.48 billion users are connected to some types of social
media. This links will make users more insecure. If personal data is in the wrong hands, it
may have damaging effects.
II. GLOBALIZATION
1. The impact of social media on globalization
This digital technologies, like Internet and mobile phones, make it easier and more
cost-effective for people from almost every corner of the world to exchange thoughts, facts,
photos and sounds opposed to conventional media tools like. It was better to take advantage
of digital media resources to engage in civic parties, protests and meetings, in person or via
Internet with suggestions. The effect of the Internet on culture and business since the late
1990s was widespread. New innovations, such as blogs, video sharing sites and social
3
From article from the BBC News “Facebook leak: Irish regulator probes 'old' data
dump”, Ireland's Data Protection Commission (DPC) is investigating the leak of Facebook
user information. Facebook said this was an previous leak, which it found and repaired more
than a year ago. However, cybersecurity officials remain concerned because of the large scale
of the leak, particularly it covers more than 530 million users in 106 countries around the
world. Facebook users whose privacy are affected by a major data breach are advised against
the technology giant to take legal action. About 530 million users were leaked with personal
data, including telephone numbers in some cases. On behalf of the EU people concerned, an
association on data privacy is about to take a case to the Irish courts. Facebook disputes
misconduct by claiming that the details were "scrapped" out of material available on the web.
Throughout the Cambridge Analytica breach, Facebook is being charged for not protecting
the personal data of users. The crisis was that 87 million users have been used for publicity
during elections were mined from Facebook records. Mass court proceedings against
Facebook over privacy theft are being held in England and Wales by over one million people.
The UK database watchdog fined £500,000 on Facebook for its involvement in the
Cambridge Analytica leak in October 2018. Facebook has authorized a "significant violation"
of the rules, the Information Commissioner's Office (ICO). Facebook excused and allowed
users to search the "banned applications" they had accessed.
In recent years social media users have become increasingly concerned for their
privacy. Data incidents have frightened many people and compelled them to replenish their
social media relationships and the safety of their personal information. The dramatic case of
the Cambridge Analytica consulting agency is an example. The company used more than 50
million Facebook users' private information to manipulate the presidential 2016 election in
the United States. This example and others have continuously worsened consumer confidence
and caused many consumers to ask if they have lost control of their own results. 80% of
social media consumers report worrying about companies and marketers who view and use
social media content, according to a survey by Pew trust. This increasing questions about
privacy have sparked stricter rules. Moreover, they have put more scrutiny into the business
of protecting personal records.
Only a couple of decades ago, it was impossible to present to strangers that sort of
physical pictures an data some of us get on social media today. Internet way and cultural
media have radically altered our attitdes about privacy. (Watson, P.W., Apr. 2018) increasing
questions about privacy have sparked stricter rules. Moreover, they have put more security
into the business of protecting personal information.
The social networks are used by 40% of the world's population. According to
information gathered by Hootesuite, 3.48 billion users are connected to some types of social
media. This links will make users more insecure. If personal data is in the wrong hands, it
may have damaging effects.
II. GLOBALIZATION
1. The impact of social media on globalization
This digital technologies, like Internet and mobile phones, make it easier and more
cost-effective for people from almost every corner of the world to exchange thoughts, facts,
photos and sounds opposed to conventional media tools like. It was better to take advantage
of digital media resources to engage in civic parties, protests and meetings, in person or via
Internet with suggestions. The effect of the Internet on culture and business since the late
1990s was widespread. New innovations, such as blogs, video sharing sites and social
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
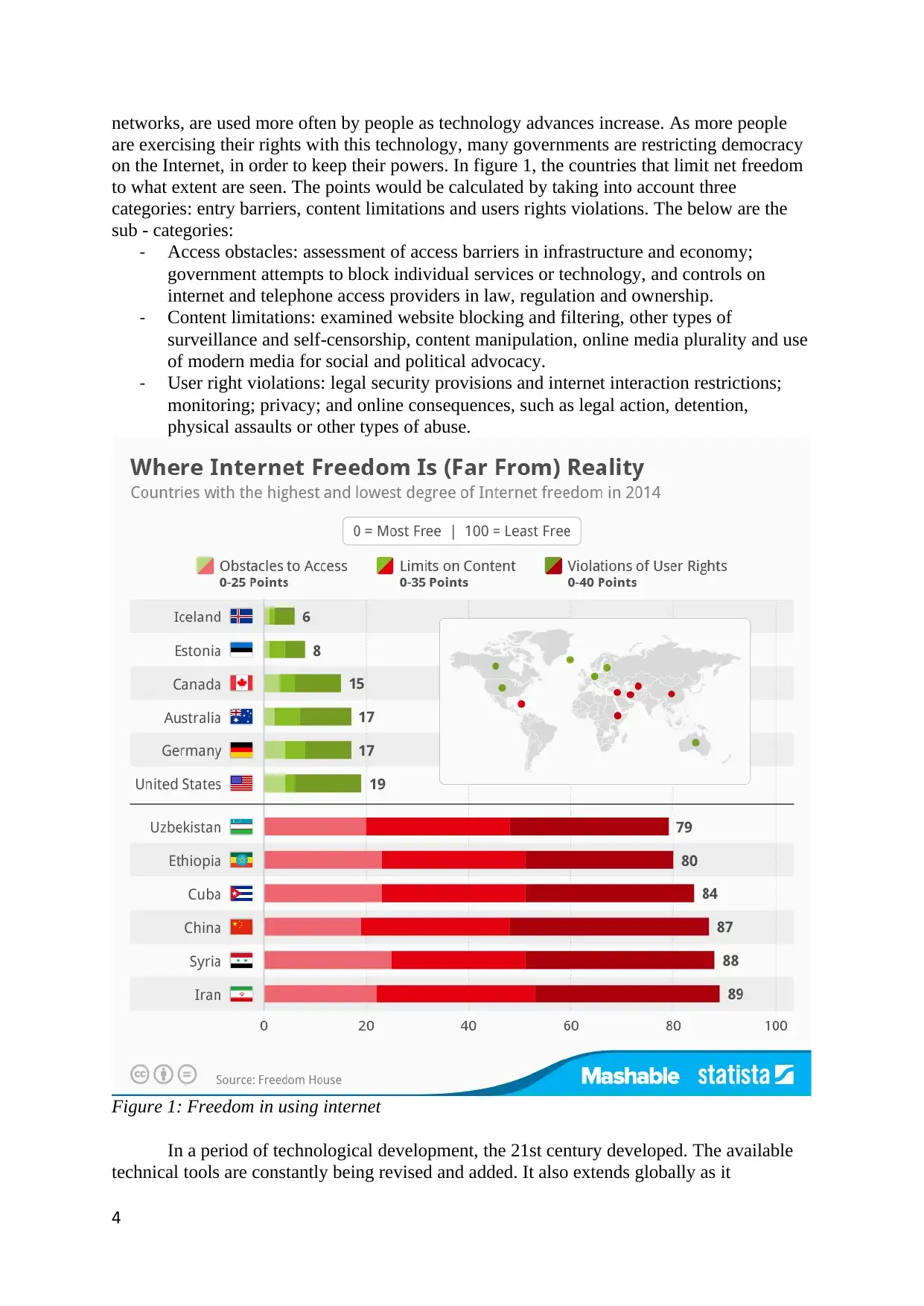
networks, are used more often by people as technology advances increase. As more people
are exercising their rights with this technology, many governments are restricting democracy
on the Internet, in order to keep their powers. In figure 1, the countries that limit net freedom
to what extent are seen. The points would be calculated by taking into account three
categories: entry barriers, content limitations and users rights violations. The below are the
sub - categories:
- Access obstacles: assessment of access barriers in infrastructure and economy;
government attempts to block individual services or technology, and controls on
internet and telephone access providers in law, regulation and ownership.
- Content limitations: examined website blocking and filtering, other types of
surveillance and self-censorship, content manipulation, online media plurality and use
of modern media for social and political advocacy.
- User right violations: legal security provisions and internet interaction restrictions;
monitoring; privacy; and online consequences, such as legal action, detention,
physical assaults or other types of abuse.
Figure 1: Freedom in using internet
In a period of technological development, the 21st century developed. The available
technical tools are constantly being revised and added. It also extends globally as it
4
are exercising their rights with this technology, many governments are restricting democracy
on the Internet, in order to keep their powers. In figure 1, the countries that limit net freedom
to what extent are seen. The points would be calculated by taking into account three
categories: entry barriers, content limitations and users rights violations. The below are the
sub - categories:
- Access obstacles: assessment of access barriers in infrastructure and economy;
government attempts to block individual services or technology, and controls on
internet and telephone access providers in law, regulation and ownership.
- Content limitations: examined website blocking and filtering, other types of
surveillance and self-censorship, content manipulation, online media plurality and use
of modern media for social and political advocacy.
- User right violations: legal security provisions and internet interaction restrictions;
monitoring; privacy; and online consequences, such as legal action, detention,
physical assaults or other types of abuse.
Figure 1: Freedom in using internet
In a period of technological development, the 21st century developed. The available
technical tools are constantly being revised and added. It also extends globally as it
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
progresses. The technology's global spread provides broad links that provide new possibilities
across a wider range. The new subject of technology globalization is the links provided by
social media networks. Social networking is a brilliant medium that those with access to it
can effectively use. When worldwide access is achieved, it provides openings for others who
are used to externalize innovations first. The use of social media is now being used to
continually adapt. Present and upcoming developments are and can use social media as a
platform of dissent. Social networking will quickly disseminate information to a wider
audience. If technology spreads, social media around the world is increasingly accessible.
The availability of social media provides global links. This global links allow countries to
share new and old interests to all. Modern improvement in some countries is a cause of
perturbation due to new information accessibility. Social media is an unavoidable force that is
now used for campaigning and will certainly be used more and more effectively in the future.
Technological innovation has allowed social media to expand across the globe. Widespread
links are established in the social media in most countries. There are wonderful possibilities
for these great relationships. The biggest thing is the use of social media as a social activist
advocacy. Activism in the social media has made the public known about contemporary
affairs. All the details are falsified with this exposition.
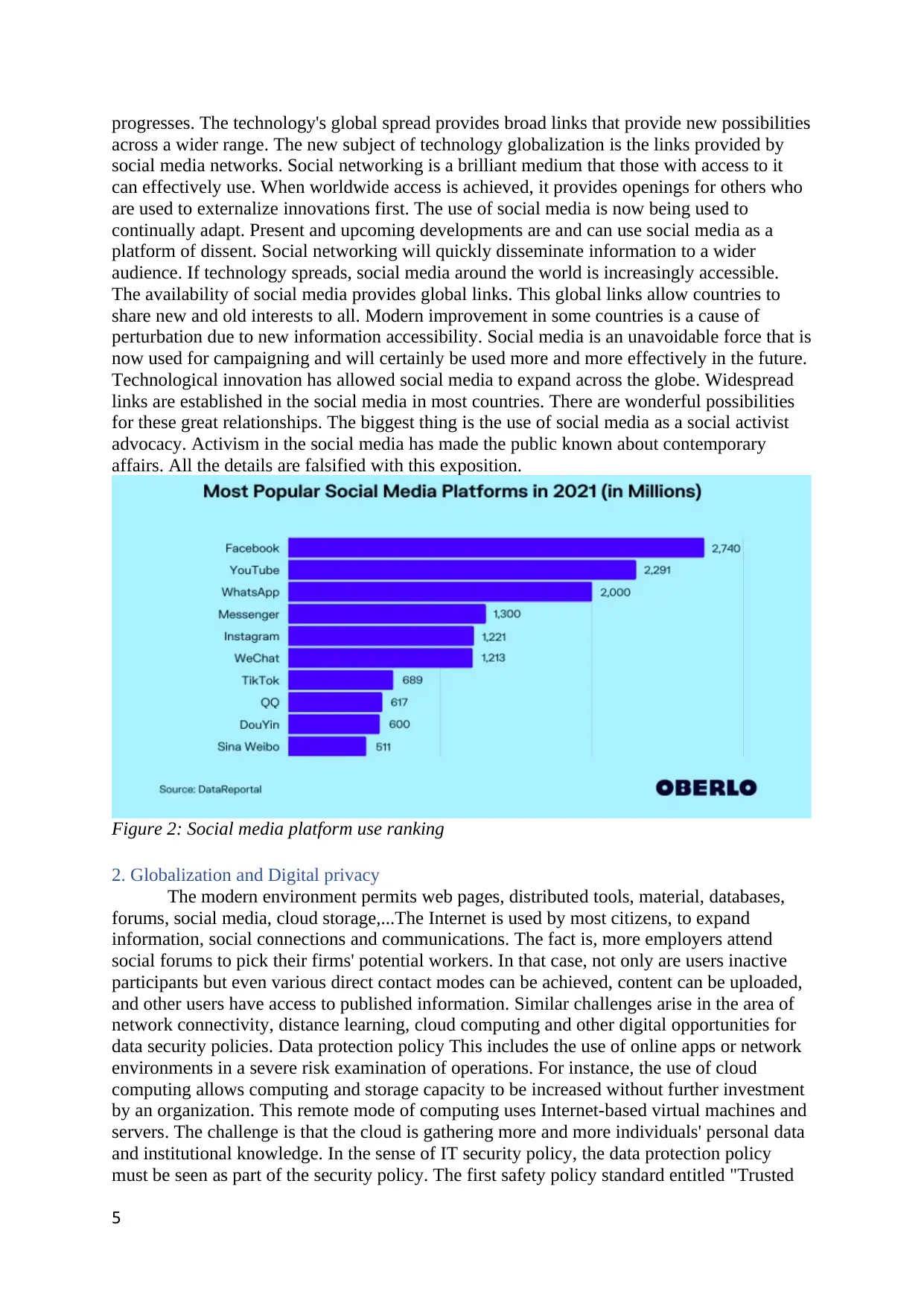
Figure 2: Social media platform use ranking
2. Globalization and Digital privacy
The modern environment permits web pages, distributed tools, material, databases,
forums, social media, cloud storage,...The Internet is used by most citizens, to expand
information, social connections and communications. The fact is, more employers attend
social forums to pick their firms' potential workers. In that case, not only are users inactive
participants but even various direct contact modes can be achieved, content can be uploaded,
and other users have access to published information. Similar challenges arise in the area of
network connectivity, distance learning, cloud computing and other digital opportunities for
data security policies. Data protection policy This includes the use of online apps or network
environments in a severe risk examination of operations. For instance, the use of cloud
computing allows computing and storage capacity to be increased without further investment
by an organization. This remote mode of computing uses Internet-based virtual machines and
servers. The challenge is that the cloud is gathering more and more individuals' personal data
and institutional knowledge. In the sense of IT security policy, the data protection policy
must be seen as part of the security policy. The first safety policy standard entitled "Trusted
5
across a wider range. The new subject of technology globalization is the links provided by
social media networks. Social networking is a brilliant medium that those with access to it
can effectively use. When worldwide access is achieved, it provides openings for others who
are used to externalize innovations first. The use of social media is now being used to
continually adapt. Present and upcoming developments are and can use social media as a
platform of dissent. Social networking will quickly disseminate information to a wider
audience. If technology spreads, social media around the world is increasingly accessible.
The availability of social media provides global links. This global links allow countries to
share new and old interests to all. Modern improvement in some countries is a cause of
perturbation due to new information accessibility. Social media is an unavoidable force that is
now used for campaigning and will certainly be used more and more effectively in the future.
Technological innovation has allowed social media to expand across the globe. Widespread
links are established in the social media in most countries. There are wonderful possibilities
for these great relationships. The biggest thing is the use of social media as a social activist
advocacy. Activism in the social media has made the public known about contemporary
affairs. All the details are falsified with this exposition.
Figure 2: Social media platform use ranking
2. Globalization and Digital privacy
The modern environment permits web pages, distributed tools, material, databases,
forums, social media, cloud storage,...The Internet is used by most citizens, to expand
information, social connections and communications. The fact is, more employers attend
social forums to pick their firms' potential workers. In that case, not only are users inactive
participants but even various direct contact modes can be achieved, content can be uploaded,
and other users have access to published information. Similar challenges arise in the area of
network connectivity, distance learning, cloud computing and other digital opportunities for
data security policies. Data protection policy This includes the use of online apps or network
environments in a severe risk examination of operations. For instance, the use of cloud
computing allows computing and storage capacity to be increased without further investment
by an organization. This remote mode of computing uses Internet-based virtual machines and
servers. The challenge is that the cloud is gathering more and more individuals' personal data
and institutional knowledge. In the sense of IT security policy, the data protection policy
must be seen as part of the security policy. The first safety policy standard entitled "Trusted
5
Computer System Assessment Criteria (TCSEC) Department of Defense" was approved in
the USA in 1985. The Security Policy is defined by TCSEC as a set of security guidelines,
principles, protocols, tools and specific guidance on managing, protecting and disseminating
information. This manual has guidelines on access control of information services. Digital
privacy has various challenges in the contemporary network world. For example, social
media privacy issues the preservation and safeguarding of consumer information. Differences
events with the user data such as unauthorized entry, malware, unlawful transmission to third
parties, etc can be avoided in the newspapers. Similar issues may be identified and even with
cloud platforms because cloud users need to ensure suppliers enforce appropriate data privacy
compliance policies.
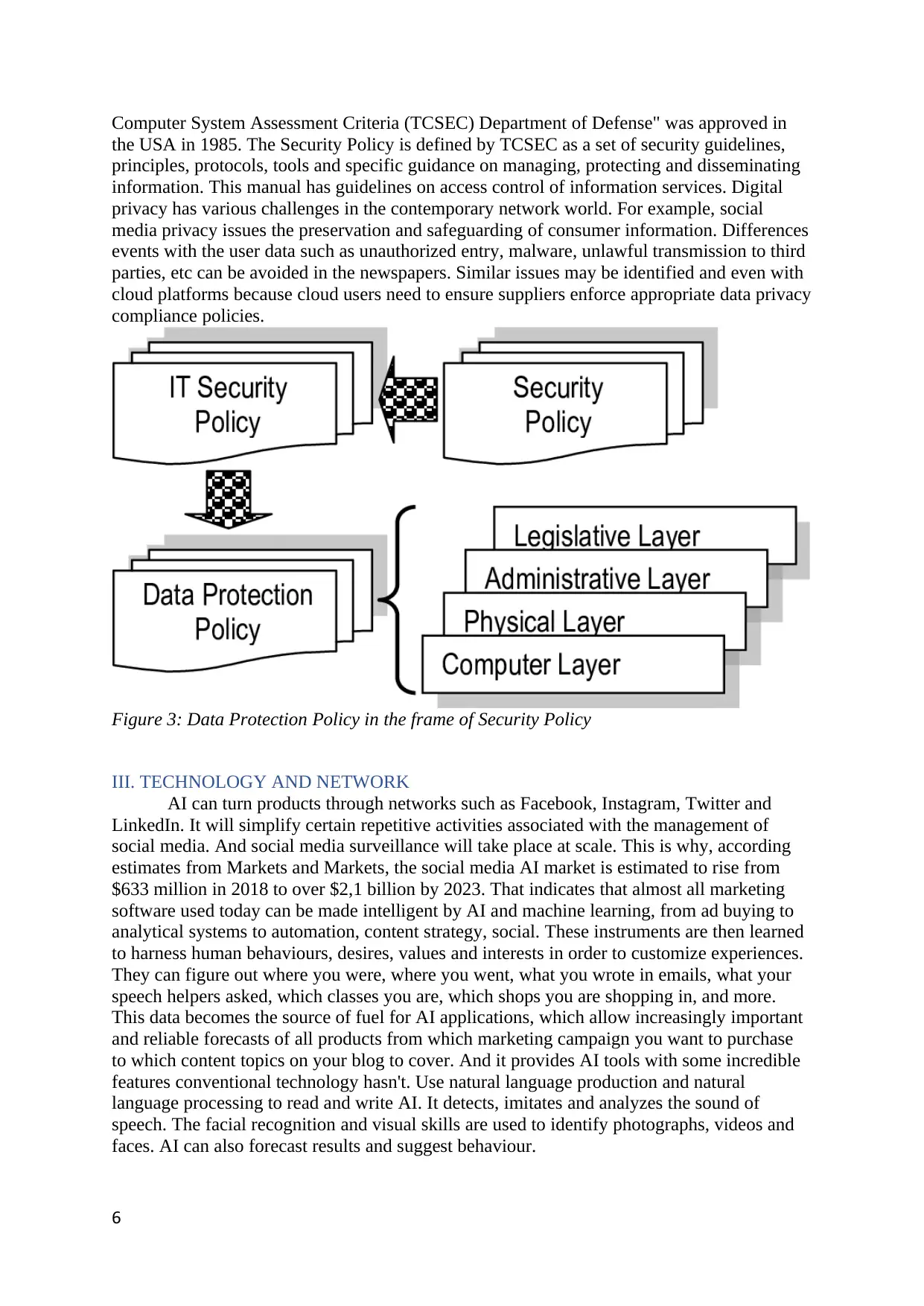
Figure 3: Data Protection Policy in the frame of Security Policy
III. TECHNOLOGY AND NETWORK
AI can turn products through networks such as Facebook, Instagram, Twitter and
LinkedIn. It will simplify certain repetitive activities associated with the management of
social media. And social media surveillance will take place at scale. This is why, according
estimates from Markets and Markets, the social media AI market is estimated to rise from
$633 million in 2018 to over $2,1 billion by 2023. That indicates that almost all marketing
software used today can be made intelligent by AI and machine learning, from ad buying to
analytical systems to automation, content strategy, social. These instruments are then learned
to harness human behaviours, desires, values and interests in order to customize experiences.
They can figure out where you were, where you went, what you wrote in emails, what your
speech helpers asked, which classes you are, which shops you are shopping in, and more.
This data becomes the source of fuel for AI applications, which allow increasingly important
and reliable forecasts of all products from which marketing campaign you want to purchase
to which content topics on your blog to cover. And it provides AI tools with some incredible
features conventional technology hasn't. Use natural language production and natural
language processing to read and write AI. It detects, imitates and analyzes the sound of
speech. The facial recognition and visual skills are used to identify photographs, videos and
faces. AI can also forecast results and suggest behaviour.
6
the USA in 1985. The Security Policy is defined by TCSEC as a set of security guidelines,
principles, protocols, tools and specific guidance on managing, protecting and disseminating
information. This manual has guidelines on access control of information services. Digital
privacy has various challenges in the contemporary network world. For example, social
media privacy issues the preservation and safeguarding of consumer information. Differences
events with the user data such as unauthorized entry, malware, unlawful transmission to third
parties, etc can be avoided in the newspapers. Similar issues may be identified and even with
cloud platforms because cloud users need to ensure suppliers enforce appropriate data privacy
compliance policies.
Figure 3: Data Protection Policy in the frame of Security Policy
III. TECHNOLOGY AND NETWORK
AI can turn products through networks such as Facebook, Instagram, Twitter and
LinkedIn. It will simplify certain repetitive activities associated with the management of
social media. And social media surveillance will take place at scale. This is why, according
estimates from Markets and Markets, the social media AI market is estimated to rise from
$633 million in 2018 to over $2,1 billion by 2023. That indicates that almost all marketing
software used today can be made intelligent by AI and machine learning, from ad buying to
analytical systems to automation, content strategy, social. These instruments are then learned
to harness human behaviours, desires, values and interests in order to customize experiences.
They can figure out where you were, where you went, what you wrote in emails, what your
speech helpers asked, which classes you are, which shops you are shopping in, and more.
This data becomes the source of fuel for AI applications, which allow increasingly important
and reliable forecasts of all products from which marketing campaign you want to purchase
to which content topics on your blog to cover. And it provides AI tools with some incredible
features conventional technology hasn't. Use natural language production and natural
language processing to read and write AI. It detects, imitates and analyzes the sound of
speech. The facial recognition and visual skills are used to identify photographs, videos and
faces. AI can also forecast results and suggest behaviour.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AI is an important part of the social networks that you use daily basis. For example,
Facebook uses automated machine learning, from content-related services to images to
advertising target audiences. Instagram (owned by Facebook) uses AI for visual
identification. LinkedIn uses AI to propose jobs, suggest users you would like to talk to and
serve those feed posts. This are only a few examples of how AI operates in the background in
order to power the most famous social networks worldwide. And AI and machine learing
regulates how the contents that you produce and the advertisements that you purchase are put
in front of consumers in ways that are not quite open to advertisers across all social media
channels. Here are some of the best ways social media advertisers will get to use AI, artificial
learning and smart automation technologies
- Management and social development: Marketers use a lot of time to create content for
the consumption of social media, and manage distribution and channel interaction. A
traditional tool for the management of social media aims to improve planning and
control of social media. Yet AI software continue to carry it. There are tools to
automatically create content for social media through platforms that provide hashtags
and short links automatically. There are also tools in place to auto-plan these bulk
shares. In general, an AI tool is capable of handling those forms of development and
maintenance of social media in minutes.
- Social Media Intelligence and Social Media Listening: An AI-powered social
monitoring tool or social listening tool can deliver insights from your brand's social
media profiles and audience. This often involves using the power of AI to analyze
social data at scale, understand what's being said in them, then extracting insights
based on that information. That data, properly applied, allows AI social media
monitoring tools to help you track your global brand mentions, find emerging
consumer trends, find new audiences to target, keep tabs on brand reputation, monitor
every social mention, and identify promising new avenues for social media
promotions.These actionable insights are delivered in near real-time, giving brands a
leg up against the competition.
- Social networking advertising: almost every social media network enables advertisers
to advertise on the basis of extremely granular demographic and behavioural profiling
on the website and receive paid publicity. Today there are artificial intelligence tools
that really write you Facebook and Instagram advertising. Thanks to AI's ability to
anticipate which language will boost performance, the advertisements are tailored for
click and conversion purposes.
Facebook has grown as we have seen. Yesterday seems that all of us had an innocent
feeling of posting images with families and friends through this emerging social network.
Today, the site is much stable and constantly reveals new functions through simple
networking with old mates. The role Facebook Artificial Intelligence has in creating a
company with long-term prospects. By learning about its customers and packaging the
results, Facebook is developing its business at high speed for advertisers. The Business aims
to link every human on the planet in 100 years' time with technology products and services
owned by Facebook (for example Whatsapp, Instagram, Oculus and more). AI is the way to
break this challanges. The Facebook website is a highly useful repository of knowledge about
your lifestyle, desires, conduct habits and taste within and outside. How do each customer
like this? What do they not like? What do they not? Such data – willingly yet messily
structured – may be used at an exorbitant valuation for benefit. AI enters so that's where. AI
allows robots, themselves, to learn how to explain details. AI picture recognition to describe a
dog, without stating how a dog looks, would be the best example of this. This starts
7
Facebook uses automated machine learning, from content-related services to images to
advertising target audiences. Instagram (owned by Facebook) uses AI for visual
identification. LinkedIn uses AI to propose jobs, suggest users you would like to talk to and
serve those feed posts. This are only a few examples of how AI operates in the background in
order to power the most famous social networks worldwide. And AI and machine learing
regulates how the contents that you produce and the advertisements that you purchase are put
in front of consumers in ways that are not quite open to advertisers across all social media
channels. Here are some of the best ways social media advertisers will get to use AI, artificial
learning and smart automation technologies
- Management and social development: Marketers use a lot of time to create content for
the consumption of social media, and manage distribution and channel interaction. A
traditional tool for the management of social media aims to improve planning and
control of social media. Yet AI software continue to carry it. There are tools to
automatically create content for social media through platforms that provide hashtags
and short links automatically. There are also tools in place to auto-plan these bulk
shares. In general, an AI tool is capable of handling those forms of development and
maintenance of social media in minutes.
- Social Media Intelligence and Social Media Listening: An AI-powered social
monitoring tool or social listening tool can deliver insights from your brand's social
media profiles and audience. This often involves using the power of AI to analyze
social data at scale, understand what's being said in them, then extracting insights
based on that information. That data, properly applied, allows AI social media
monitoring tools to help you track your global brand mentions, find emerging
consumer trends, find new audiences to target, keep tabs on brand reputation, monitor
every social mention, and identify promising new avenues for social media
promotions.These actionable insights are delivered in near real-time, giving brands a
leg up against the competition.
- Social networking advertising: almost every social media network enables advertisers
to advertise on the basis of extremely granular demographic and behavioural profiling
on the website and receive paid publicity. Today there are artificial intelligence tools
that really write you Facebook and Instagram advertising. Thanks to AI's ability to
anticipate which language will boost performance, the advertisements are tailored for
click and conversion purposes.
Facebook has grown as we have seen. Yesterday seems that all of us had an innocent
feeling of posting images with families and friends through this emerging social network.
Today, the site is much stable and constantly reveals new functions through simple
networking with old mates. The role Facebook Artificial Intelligence has in creating a
company with long-term prospects. By learning about its customers and packaging the
results, Facebook is developing its business at high speed for advertisers. The Business aims
to link every human on the planet in 100 years' time with technology products and services
owned by Facebook (for example Whatsapp, Instagram, Oculus and more). AI is the way to
break this challanges. The Facebook website is a highly useful repository of knowledge about
your lifestyle, desires, conduct habits and taste within and outside. How do each customer
like this? What do they not like? What do they not? Such data – willingly yet messily
structured – may be used at an exorbitant valuation for benefit. AI enters so that's where. AI
allows robots, themselves, to learn how to explain details. AI picture recognition to describe a
dog, without stating how a dog looks, would be the best example of this. This starts
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

structuring unstructured files. It quantifies and reproduces it in a way that can then provide
comprehensible observations.
8
comprehensible observations.
8
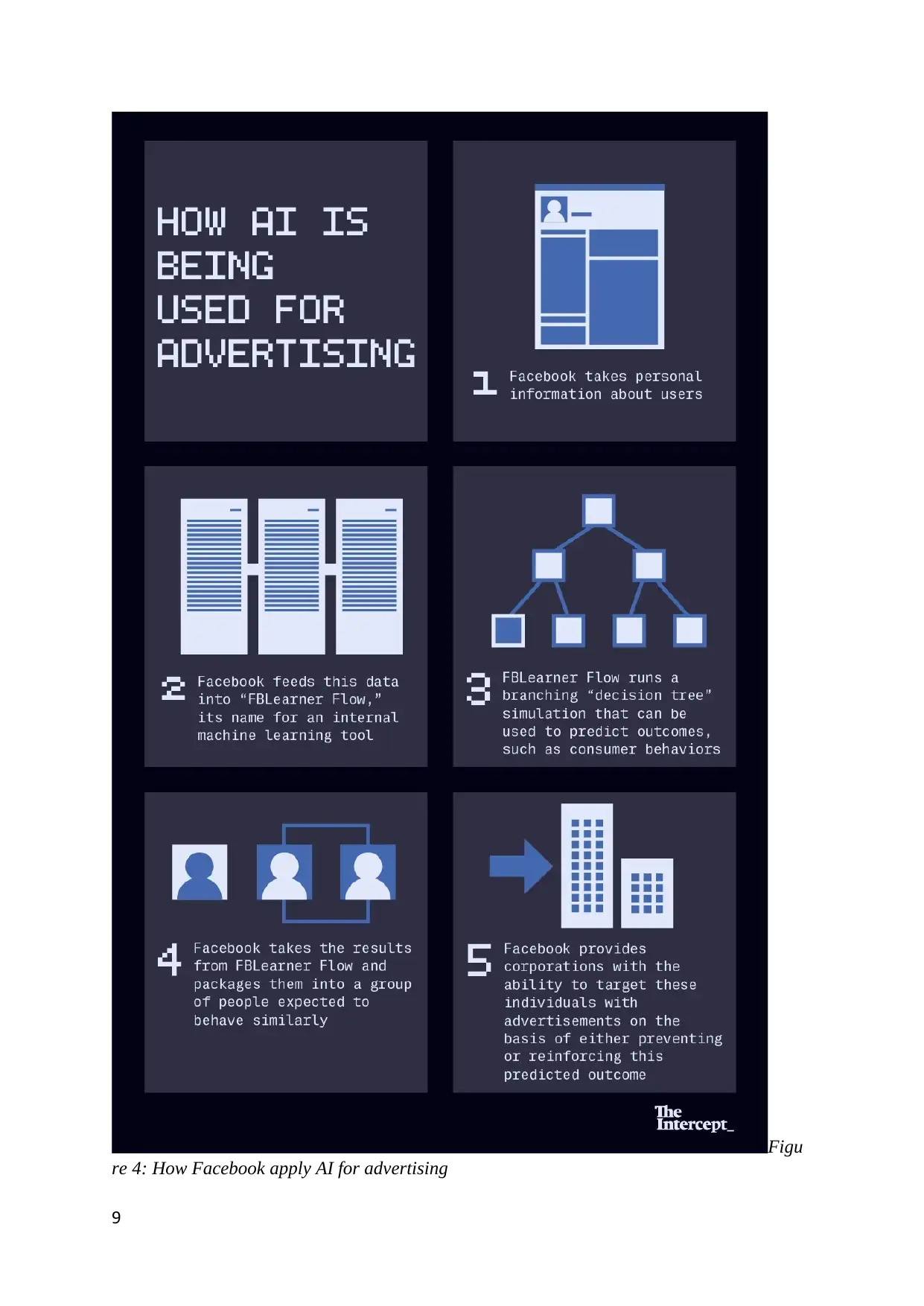
Figu
re 4: How Facebook apply AI for advertising
9
re 4: How Facebook apply AI for advertising
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IV. CONFLICT AND CO-OPERATION
1. Conflict
Criminals are capable of deceiving social media users to pass confidential information
through, steal personal data, and obtain access to private accounts. Then there are typical
risks on social media
- Data Exploit: Almost everyone sets underneath a data trail on the network. They have
personal information that could include the name, date of birth, location and private
preferences any time someone opens a new social media account. Companies also
gather details on consumer behaviour: when, how and where people communicate.
All these data are saved and used by businesses to target their users more effectively.
Often organizations exchange customer data, often without the information or the
agreement of customers, with third-party agencies.
- Cyber-Attack Attempts: Phishing is one of the most often used methods in which
hackers want access to private personal information. A phishing attack also introduces
itself as a letter from a reputable organisation, in the form of an e-mail, a text message
or a phone call. These messages lead people to share personal information, including
information about passwords, banking or credit card numbers. Phishing attacks also
present themselves as outlets for social media. In August 2019, a huge phishing
campaign aimed Instagram users to log in to a fake Instagram website, acting as a
two-factor authentication scheme, according to Forbe News.
- Sharing of malware: Malware is designed to access and contain data on computers.
Malware (malicious software). Once malware has infected a user's computer,
confidential data (spyware), extort money, or profit from forced ads can be stealed It
can be used (adware). Social networking sites are a perfect malware distribution
mechanism. When your account is hacked, cybercriminals will take over this account
(oft by credentials obtained through a phishing attack) and spread malware to all user
friends or contacts.
- Attacks on Botnet: Social media bots are automated accounts which generate posts or
follow new people automatically if a certain term is specified. A wide number of bots
may create a botnet network. Bots and snapshots on social media are commonly used
to rob information, deliver spam, and conduct distributed Denial-of-Service attacks
(DDoSs), which allow cyber criminals to access computers and networks of people.
When the UK Parliament posted a bunch of internal emails from top managers on
Facebook, it was a matter of whether social media sites were "selling" user information.
Among them was a chain that had little more but the notion of effectively charging
developers a fee for accessing consumer data by buying advertisements, selling articles or
merely writing a search on Facebook. Although the firm made great efforts to stress that the
proposal never ended, the very fact that the company's founder openly discussed charging a
per user charge to access user data showed that it really views its users as money-raising
entities that are used by a profit-making firm and not as a benevolent business that seeks to
co-operate with others. In addition, the equivalence of Zuckerberg between advertisement
revenues and checks shows that the business finds no distinction in advertising sales control
and access sales by checks.
2. Collaboration
One of the most existential issues on the digital web is the income generation of
online businesses. Today's Site specifically represents one solution to this question: the web
where everything is open, but our privacy pays for it. The Internet has become transformed
into a dystopian surveillance state where businesses stalk the unwitting victims across the
network, derive maximum value by eliminating every shred of anonymity and reputation,
10
1. Conflict
Criminals are capable of deceiving social media users to pass confidential information
through, steal personal data, and obtain access to private accounts. Then there are typical
risks on social media
- Data Exploit: Almost everyone sets underneath a data trail on the network. They have
personal information that could include the name, date of birth, location and private
preferences any time someone opens a new social media account. Companies also
gather details on consumer behaviour: when, how and where people communicate.
All these data are saved and used by businesses to target their users more effectively.
Often organizations exchange customer data, often without the information or the
agreement of customers, with third-party agencies.
- Cyber-Attack Attempts: Phishing is one of the most often used methods in which
hackers want access to private personal information. A phishing attack also introduces
itself as a letter from a reputable organisation, in the form of an e-mail, a text message
or a phone call. These messages lead people to share personal information, including
information about passwords, banking or credit card numbers. Phishing attacks also
present themselves as outlets for social media. In August 2019, a huge phishing
campaign aimed Instagram users to log in to a fake Instagram website, acting as a
two-factor authentication scheme, according to Forbe News.
- Sharing of malware: Malware is designed to access and contain data on computers.
Malware (malicious software). Once malware has infected a user's computer,
confidential data (spyware), extort money, or profit from forced ads can be stealed It
can be used (adware). Social networking sites are a perfect malware distribution
mechanism. When your account is hacked, cybercriminals will take over this account
(oft by credentials obtained through a phishing attack) and spread malware to all user
friends or contacts.
- Attacks on Botnet: Social media bots are automated accounts which generate posts or
follow new people automatically if a certain term is specified. A wide number of bots
may create a botnet network. Bots and snapshots on social media are commonly used
to rob information, deliver spam, and conduct distributed Denial-of-Service attacks
(DDoSs), which allow cyber criminals to access computers and networks of people.
When the UK Parliament posted a bunch of internal emails from top managers on
Facebook, it was a matter of whether social media sites were "selling" user information.
Among them was a chain that had little more but the notion of effectively charging
developers a fee for accessing consumer data by buying advertisements, selling articles or
merely writing a search on Facebook. Although the firm made great efforts to stress that the
proposal never ended, the very fact that the company's founder openly discussed charging a
per user charge to access user data showed that it really views its users as money-raising
entities that are used by a profit-making firm and not as a benevolent business that seeks to
co-operate with others. In addition, the equivalence of Zuckerberg between advertisement
revenues and checks shows that the business finds no distinction in advertising sales control
and access sales by checks.
2. Collaboration
One of the most existential issues on the digital web is the income generation of
online businesses. Today's Site specifically represents one solution to this question: the web
where everything is open, but our privacy pays for it. The Internet has become transformed
into a dystopian surveillance state where businesses stalk the unwitting victims across the
network, derive maximum value by eliminating every shred of anonymity and reputation,
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

socialize the risks of data breakage or harm to the customer and privatize the monetary
advantage through its usage. Social networking sites also produce a large proportion of their
income by selling hyper goal advertisements dependent on the algorithmic mining unwilling
users every second. Yet the company itself argues that it doesn't "sell" the data of its
customers.
An innovative digital marketing strategy is being built on social media data analysis.
It eliminates instinct-based marketing needs. With social media insights, companies can
precisely see how they view and communicate with their brand and make strategic
adjustments that pass the market needle. When this information is collected, business will
start to mark patterns, measure commitment and draw perspective which will allow them to
achieve these five marketing targets effectively and efficiently:
- Optimize the social content
- Inform terms of service
- Update SEO framework
- Brand Image Monitor
- Identify customers with interest
V. CONCLUSION
Social media networks are an excellent way to communicate and connect with people.
It helps users lift space and time constraints and interact with the whole globe. However, the
proven risks of consumer privacy breaches are another issue. Thanks to the growing tendency
to log on a number of web-sites using one user account these risks becoming more of a
challenge. In response, every internet user must be cautious and authorities must impose
more pressure on these website owners to ensure the safety of internet users.
11
advantage through its usage. Social networking sites also produce a large proportion of their
income by selling hyper goal advertisements dependent on the algorithmic mining unwilling
users every second. Yet the company itself argues that it doesn't "sell" the data of its
customers.
An innovative digital marketing strategy is being built on social media data analysis.
It eliminates instinct-based marketing needs. With social media insights, companies can
precisely see how they view and communicate with their brand and make strategic
adjustments that pass the market needle. When this information is collected, business will
start to mark patterns, measure commitment and draw perspective which will allow them to
achieve these five marketing targets effectively and efficiently:
- Optimize the social content
- Inform terms of service
- Update SEO framework
- Brand Image Monitor
- Identify customers with interest
V. CONCLUSION
Social media networks are an excellent way to communicate and connect with people.
It helps users lift space and time constraints and interact with the whole globe. However, the
proven risks of consumer privacy breaches are another issue. Thanks to the growing tendency
to log on a number of web-sites using one user account these risks becoming more of a
challenge. In response, every internet user must be cautious and authorities must impose
more pressure on these website owners to ensure the safety of internet users.
11

REFERENCES
Watson, P., 2021. This Is The End Of Privacy As We Know It. [online] Forbes. Available at:
<https://www.forbes.com/sites/patrickwwatson/2018/04/26/this-is-the-end-of-privacy-as-we-
know-it/?sh=1b9f7e436875> [Accessed 29 April 2021].
Doffman, Z., 2021. Instagram Security Warning: Millions At Risk From ‘Believable’ New
Phishing Attack. [online] Forbes. Available at:
<https://www.forbes.com/sites/zakdoffman/2019/08/24/new-critical-security-warning-issued-
for-1-billion-instagram-users/?sh=59adcf902f6e> [Accessed 29 April 2021].
Oberlo.com. 2021. Most Popular Social Media Platforms [Updated March 2021]. [online]
Available at: <https://www.oberlo.com/statistics/most-popular-social-media-platforms>
[Accessed 29 April 2021].
Marketsandmarkets.com. 2021. AI in Social Media Market worth 2,197.1 Million USD by
2023. [online] Available at: <https://www.marketsandmarkets.com/PressReleases/ai-in-
social-media.asp> [Accessed 29 April 2021].
12
Watson, P., 2021. This Is The End Of Privacy As We Know It. [online] Forbes. Available at:
<https://www.forbes.com/sites/patrickwwatson/2018/04/26/this-is-the-end-of-privacy-as-we-
know-it/?sh=1b9f7e436875> [Accessed 29 April 2021].
Doffman, Z., 2021. Instagram Security Warning: Millions At Risk From ‘Believable’ New
Phishing Attack. [online] Forbes. Available at:
<https://www.forbes.com/sites/zakdoffman/2019/08/24/new-critical-security-warning-issued-
for-1-billion-instagram-users/?sh=59adcf902f6e> [Accessed 29 April 2021].
Oberlo.com. 2021. Most Popular Social Media Platforms [Updated March 2021]. [online]
Available at: <https://www.oberlo.com/statistics/most-popular-social-media-platforms>
[Accessed 29 April 2021].
Marketsandmarkets.com. 2021. AI in Social Media Market worth 2,197.1 Million USD by
2023. [online] Available at: <https://www.marketsandmarkets.com/PressReleases/ai-in-
social-media.asp> [Accessed 29 April 2021].
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





