Computer Security System Investigation
VerifiedAdded on 2023/02/01
|20
|4395
|42
AI Summary
This document provides a study and assessment of computer security system, including the installation process of virtual machine image file, inspection of security system, inspection report and details, and additional security system suggestions.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

University
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1. Project Goal...................................................................................................................................3
2. Installation Process of Virtual Machine (VM) Image File.............................................................3
3. Inspection of the Security System…………………………………………..…………………... . .9
4. Inspection Report and Details of the Security System.................................................................15
5. Additional Security System Suggestions.....................................................................................17
References...........................................................................................................................................20
2
1. Project Goal...................................................................................................................................3
2. Installation Process of Virtual Machine (VM) Image File.............................................................3
3. Inspection of the Security System…………………………………………..…………………... . .9
4. Inspection Report and Details of the Security System.................................................................15
5. Additional Security System Suggestions.....................................................................................17
References...........................................................................................................................................20
2

1) Project Goal
Every System is always under a constant threat of Data Theft or Information Hacking.
Security concern is one of the top most priorities to any Administrator. With the development
of sophisticated viruses and stubborn Malwares, it becomes more essential to keep the
System Safe and Secured. This protection can be of physical type or a Software based tool.
Security is an ongoing process and a constant developing model. Ultimately our goal is the
Security of our System. Delicate and important information that is handled by the System and
users accessing this data have to be careful. This is more the case for multi-users on a
common platform and a shared system. There should be an authorized way in which this
information is handled and used. Security System handles this part of the system, together
with improvements, suggestions, updates and vulnerable areas of the entire framework.
This Project’s Goal is System Security Study and Assessment. How best the existing tools
can be used to keep the security at its optimum level. We shall be making use of a VM
(Virtual Machine Image File) to conduct our Security Analysis and Evaluation. A “Virtual
Machine (VM)” is an emulation of a computer system. Virtual machines are based on
computer architectures and provide functionality of a physical computer. Their
implementations may involve specialized hardware, software, or a combination. They mimic a
normal computer with its full functionality. “Widget Inc” is a company involved in
manufacturing and distribution of Computer Hardware and Software. They are building an E-
commerce store and for that they require their VM files to be examined for security and safety
attributes. They are giving this job to another company called “Benny Vandergast Inc”. And
at this point we come in to the picture. Benny Vandergast wants us to test these VM image
files for Security concerns.
And thus we start with our project of System Security Evaluation, analysis, Reporting and
Consequences. We will conduct this on the VM image files as provided by Benny Vandergast.
This shall be carried out by using “Special Security Tools” of which we shall discuss in
detail, further ahead in this project. The parameter that we shall be using for this whole
security Project will include buy not limited to the following,
a. Understanding and preparing a Well-defined Security Inspection plan.
b. Select the best tools/ Methods that suits the Security plan.
c. Study the analyses after the Security Inspection has been completed.
d. Understand the weak, vulnerable areas and how to strengthen them.
3
Every System is always under a constant threat of Data Theft or Information Hacking.
Security concern is one of the top most priorities to any Administrator. With the development
of sophisticated viruses and stubborn Malwares, it becomes more essential to keep the
System Safe and Secured. This protection can be of physical type or a Software based tool.
Security is an ongoing process and a constant developing model. Ultimately our goal is the
Security of our System. Delicate and important information that is handled by the System and
users accessing this data have to be careful. This is more the case for multi-users on a
common platform and a shared system. There should be an authorized way in which this
information is handled and used. Security System handles this part of the system, together
with improvements, suggestions, updates and vulnerable areas of the entire framework.
This Project’s Goal is System Security Study and Assessment. How best the existing tools
can be used to keep the security at its optimum level. We shall be making use of a VM
(Virtual Machine Image File) to conduct our Security Analysis and Evaluation. A “Virtual
Machine (VM)” is an emulation of a computer system. Virtual machines are based on
computer architectures and provide functionality of a physical computer. Their
implementations may involve specialized hardware, software, or a combination. They mimic a
normal computer with its full functionality. “Widget Inc” is a company involved in
manufacturing and distribution of Computer Hardware and Software. They are building an E-
commerce store and for that they require their VM files to be examined for security and safety
attributes. They are giving this job to another company called “Benny Vandergast Inc”. And
at this point we come in to the picture. Benny Vandergast wants us to test these VM image
files for Security concerns.
And thus we start with our project of System Security Evaluation, analysis, Reporting and
Consequences. We will conduct this on the VM image files as provided by Benny Vandergast.
This shall be carried out by using “Special Security Tools” of which we shall discuss in
detail, further ahead in this project. The parameter that we shall be using for this whole
security Project will include buy not limited to the following,
a. Understanding and preparing a Well-defined Security Inspection plan.
b. Select the best tools/ Methods that suits the Security plan.
c. Study the analyses after the Security Inspection has been completed.
d. Understand the weak, vulnerable areas and how to strengthen them.
3
e. Security corrections and further precautions to be taken.
So now we shall actually start our Project by keeping the above points as our tasks for
the Security System Evaluation of our VM Image files.
2) Installation Process for Virtual Machine (VM) Image File
To use the VM image file, we shall first install the “VMware Work Station” on our platform.
The steps involved in this are,
(“VMware Workstation” it enables users to set up virtual machines (VMs) on a single
physical machine, and use them simultaneously along with the actual machine. Each virtual
machine can execute its own operating system).
Download the VMware Station on our Portal from the VMware website.
Install the VMware Station once the downloading has been completed.
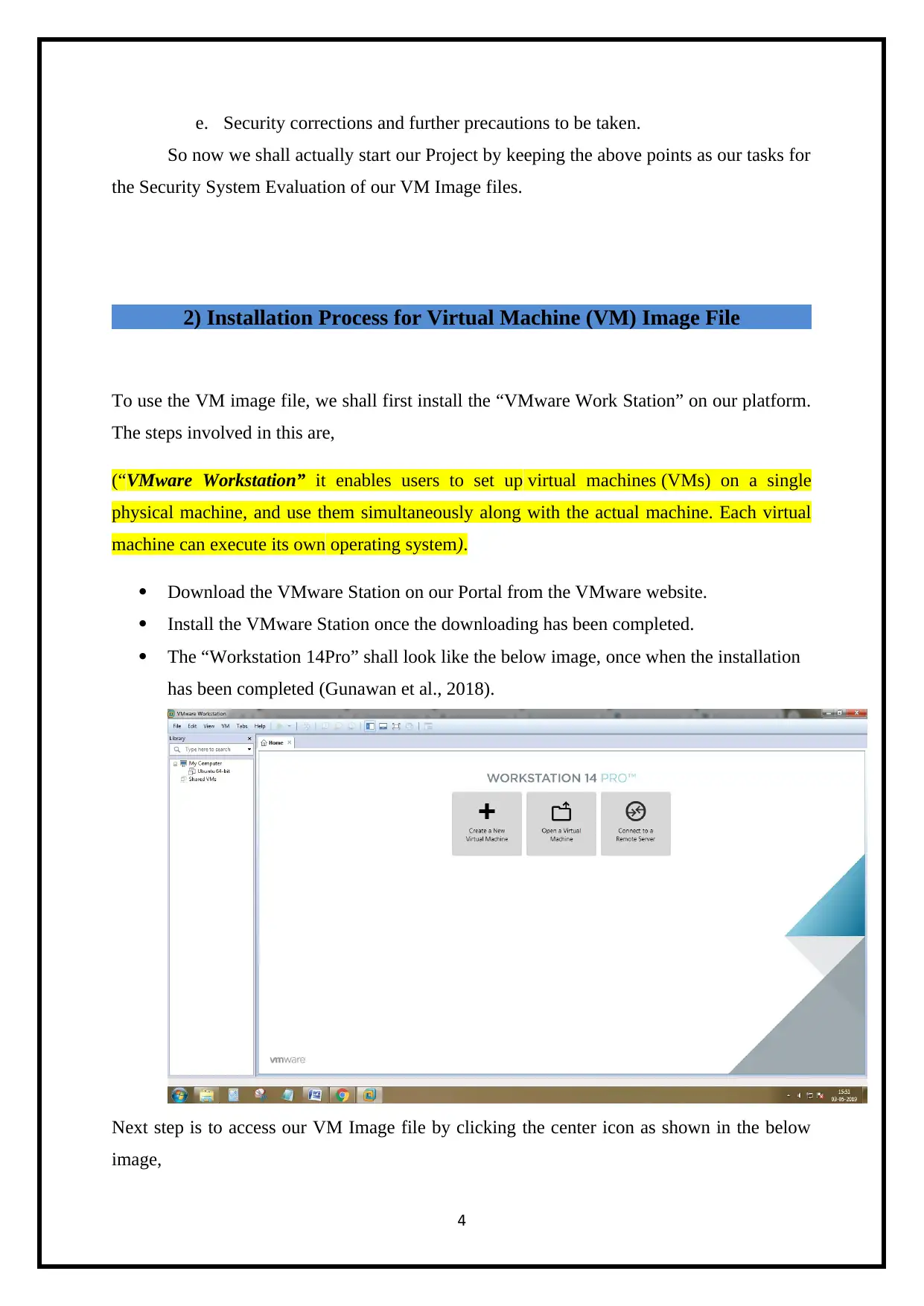
The “Workstation 14Pro” shall look like the below image, once when the installation
has been completed (Gunawan et al., 2018).
Next step is to access our VM Image file by clicking the center icon as shown in the below
image,
4
So now we shall actually start our Project by keeping the above points as our tasks for
the Security System Evaluation of our VM Image files.
2) Installation Process for Virtual Machine (VM) Image File
To use the VM image file, we shall first install the “VMware Work Station” on our platform.
The steps involved in this are,
(“VMware Workstation” it enables users to set up virtual machines (VMs) on a single
physical machine, and use them simultaneously along with the actual machine. Each virtual
machine can execute its own operating system).
Download the VMware Station on our Portal from the VMware website.
Install the VMware Station once the downloading has been completed.
The “Workstation 14Pro” shall look like the below image, once when the installation
has been completed (Gunawan et al., 2018).
Next step is to access our VM Image file by clicking the center icon as shown in the below
image,
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
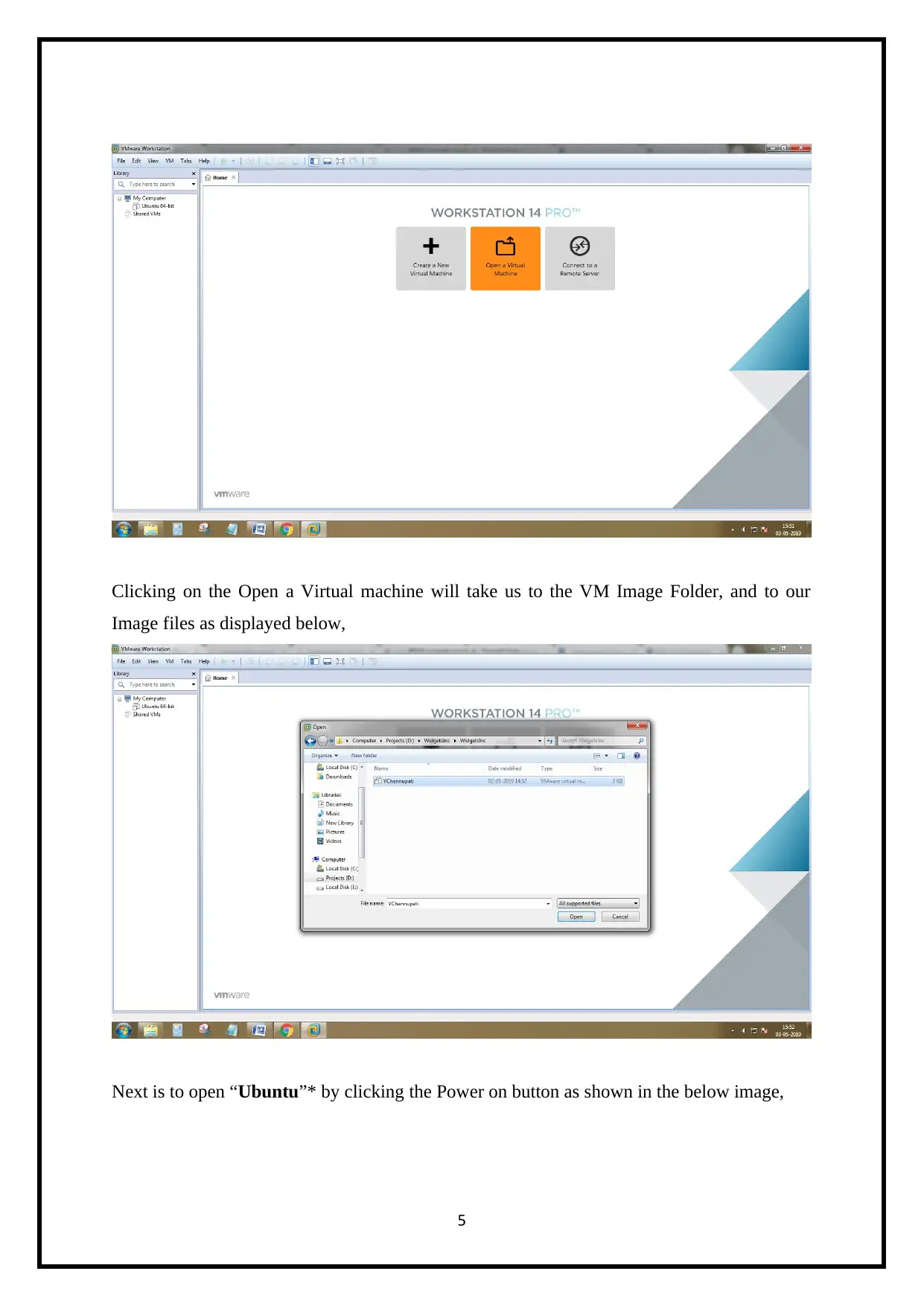
Clicking on the Open a Virtual machine will take us to the VM Image Folder, and to our
Image files as displayed below,
Next is to open “Ubuntu”* by clicking the Power on button as shown in the below image,
5
Image files as displayed below,
Next is to open “Ubuntu”* by clicking the Power on button as shown in the below image,
5
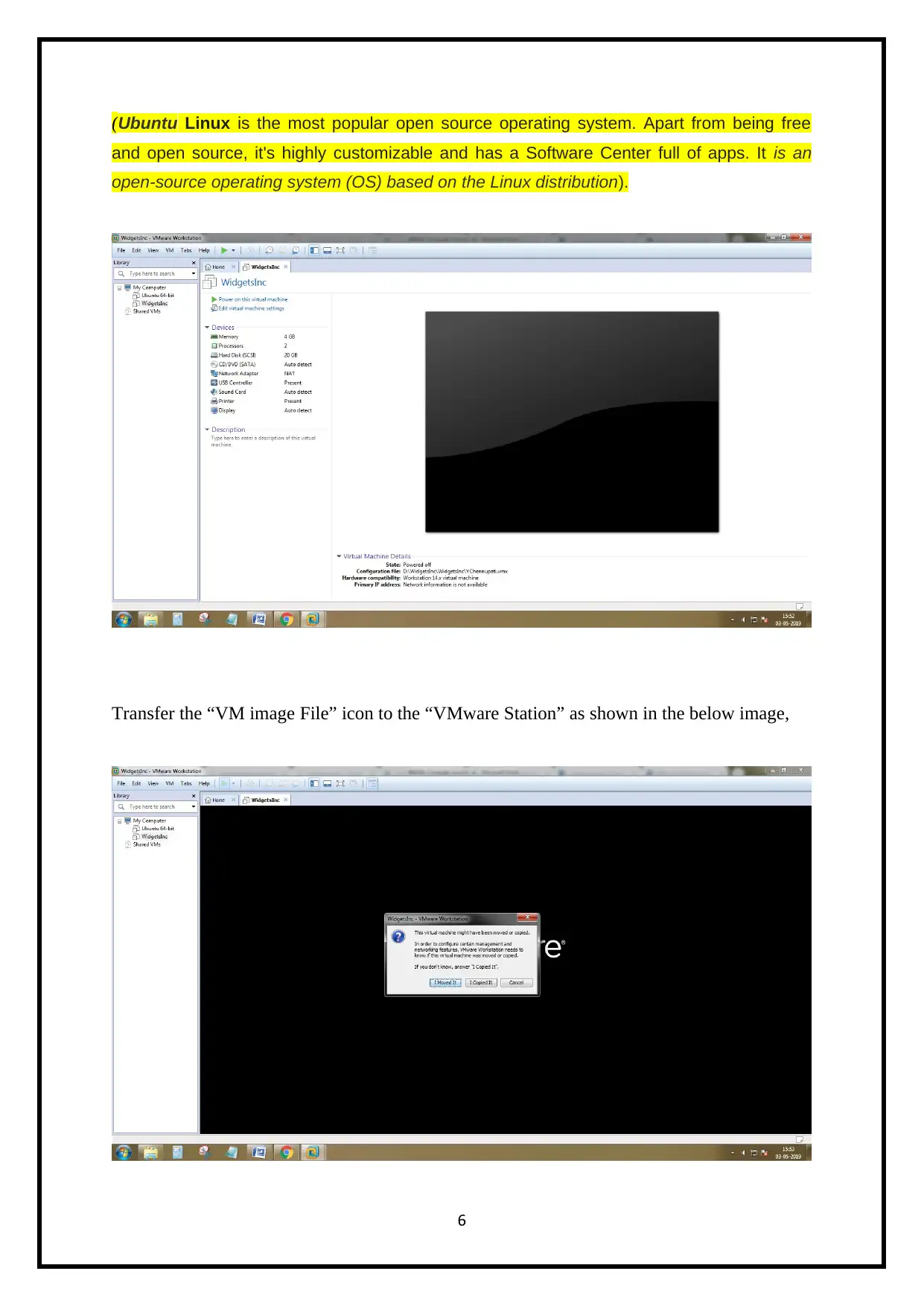
(Ubuntu Linux is the most popular open source operating system. Apart from being free
and open source, it's highly customizable and has a Software Center full of apps. It is an
open-source operating system (OS) based on the Linux distribution).
Transfer the “VM image File” icon to the “VMware Station” as shown in the below image,
6
and open source, it's highly customizable and has a Software Center full of apps. It is an
open-source operating system (OS) based on the Linux distribution).
Transfer the “VM image File” icon to the “VMware Station” as shown in the below image,
6
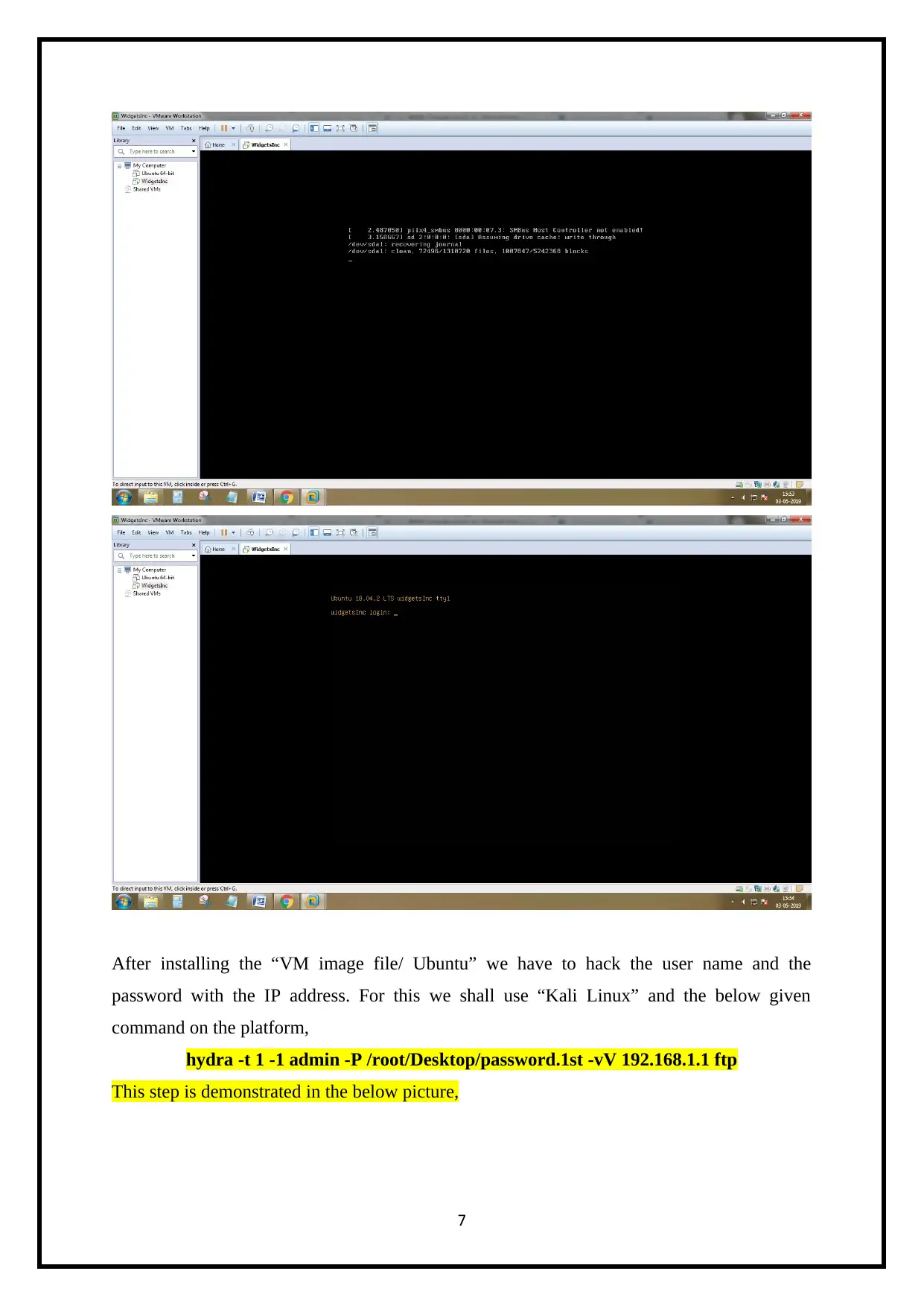
After installing the “VM image file/ Ubuntu” we have to hack the user name and the
password with the IP address. For this we shall use “Kali Linux” and the below given
command on the platform,
hydra -t 1 -1 admin -P /root/Desktop/password.1st -vV 192.168.1.1 ftp
This step is demonstrated in the below picture,
7
password with the IP address. For this we shall use “Kali Linux” and the below given
command on the platform,
hydra -t 1 -1 admin -P /root/Desktop/password.1st -vV 192.168.1.1 ftp
This step is demonstrated in the below picture,
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Once using the above mentioned command, enterthe platform for resetting the user name/
password as per the below values,
User name: admin
Password: admin
The idea behind this is to hack in to the VM image file as that is part of our Project.
Next is to enter the Ubuntu VM to do the credentials of Virtual Machine by use the below
steps,
1. Boot into the recovery mode
2. Drop to root shell prompt
3. Using the write access prompt, remount the root.
4. Reset the username and password
5. When the new password is entered, there will be an error displayed on the screen as,
“Authentication manipulation error” as shown below,
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
As the File we selected was only “Read Access”, this error was displayed. To remove the
error we have to remount the File System. Once this has been done, reset the user name and
the password as per the above values given.
There are security risks and issues faced by the VM image file at this time. They will be like,
8
password as per the below values,
User name: admin
Password: admin
The idea behind this is to hack in to the VM image file as that is part of our Project.
Next is to enter the Ubuntu VM to do the credentials of Virtual Machine by use the below
steps,
1. Boot into the recovery mode
2. Drop to root shell prompt
3. Using the write access prompt, remount the root.
4. Reset the username and password
5. When the new password is entered, there will be an error displayed on the screen as,
“Authentication manipulation error” as shown below,
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
As the File we selected was only “Read Access”, this error was displayed. To remove the
error we have to remount the File System. Once this has been done, reset the user name and
the password as per the above values given.
There are security risks and issues faced by the VM image file at this time. They will be like,
8

System Back Up issues
Malware/ Virus / Bugs threats
Network Issues
Issues related to Open SSL
Updating passwords in the system
Web Server Hardening
Data Encryption Issues
Communication Errors
Security Patches
Task 3 – Investigation on System Security
Any project that we undertake has to be well understood and pre-planned.
Understanding the System and the Security threats will help us to carry out the evaluation
more accurately and efficiently. As there is threat and risk to the Data and sensitive
information of the system (VM image file), it becomes more apparent to carry out the task
systematically so all the protocols are followed and taken care of.
Currently Virtual Machines (VMs) have many applications and their use is growing
constantly as the hardware gets more powerful and usage more regulated allowing for
scaling, monitoring, portability, security applications and many other uses. There are many
types of virtualization techniques that can be employed on many levels from simple sandbox
to full-fledged streamlined managed access. While scaling, software lifecycles and diversity
are just some of the security challenges faced by VM developers the failure to properly
implement those mechanisms may lead to VM escape, host access, denial of service and
more.
The Security should be able to fulfil the standards as set out by the concerned authorities. The
whole process will be checked regularly and the findings shall be well noted.Our VM image
file will be Ubuntu 18.04 for this task and all security assessments will be carried out on it.
Logs will be maintained throughout the whole process of Security Assessment. A pre-
planned checklist will be used as a reference point to compare and identify the issues during
the whole process. The translation of data into a secret code, Encryption makes it the most
effective way to achieve data security. To read an encrypted file, you must have access to a
9
Malware/ Virus / Bugs threats
Network Issues
Issues related to Open SSL
Updating passwords in the system
Web Server Hardening
Data Encryption Issues
Communication Errors
Security Patches
Task 3 – Investigation on System Security
Any project that we undertake has to be well understood and pre-planned.
Understanding the System and the Security threats will help us to carry out the evaluation
more accurately and efficiently. As there is threat and risk to the Data and sensitive
information of the system (VM image file), it becomes more apparent to carry out the task
systematically so all the protocols are followed and taken care of.
Currently Virtual Machines (VMs) have many applications and their use is growing
constantly as the hardware gets more powerful and usage more regulated allowing for
scaling, monitoring, portability, security applications and many other uses. There are many
types of virtualization techniques that can be employed on many levels from simple sandbox
to full-fledged streamlined managed access. While scaling, software lifecycles and diversity
are just some of the security challenges faced by VM developers the failure to properly
implement those mechanisms may lead to VM escape, host access, denial of service and
more.
The Security should be able to fulfil the standards as set out by the concerned authorities. The
whole process will be checked regularly and the findings shall be well noted.Our VM image
file will be Ubuntu 18.04 for this task and all security assessments will be carried out on it.
Logs will be maintained throughout the whole process of Security Assessment. A pre-
planned checklist will be used as a reference point to compare and identify the issues during
the whole process. The translation of data into a secret code, Encryption makes it the most
effective way to achieve data security. To read an encrypted file, you must have access to a
9

secret key or password that enables you to decrypt it. Unencrypted data is called plain
text; encrypted data is referred to as cipher text. In cryptography, encryption is the process
of encoding a message or information in such a way that only authorized parties can access it
and those who are not authorized cannot. Encryption does not itself prevent interference, but
denies the intelligible content to a would-be interceptor. By managing encryption keys in a
hardware security module, even if a hacker copies all data, the data will never be decrypted
without the cybercriminal physically accessing the premises where your data is kept.
Security not only means to protect the System, but it should also include all the connected
components, devices, software’s, Storage devices etc. Regular planned updates for the
System, software’s and packages help in maintaining the system at the latest version. This
will help in preventing and avoiding attacks from newer threats.
Today’s networks are constantly under attack and even the smallest vulnerabilities can be
quickly identified and exploited. System hardening, also called Operating
System hardening, helps minimize these security vulnerabilities. The purpose of
system hardening is to eliminate as many security risks as possible. This is typically done by
removing all non-essential software programs and utilities from the computer. Reducing
available ways of attack typically includes changing default passwords, the removal of
unnecessary software, unnecessary usernames or logins, and the disabling or removal of
unnecessary services.
Linux is the Operating system which is used extensively in the industry. Like any other
operating system working over a Network and exposed to the external web is prone to
vulnerabilities and attacks There should be a fine tuning for the System’s Performance and
the Security requirements. For our project this is also an important factor taken into
consideration.
Encrypt where possible
In Linux, Logical Volume Manager (LVM) is a device mapper target that provides logical
volume management for the Linux kernel. LVM allows for very flexible disk space
management. It provides features like the ability to add disk space to a logical volume and its
filesystem while that filesystem is mounted and active and it allows for the collection of
multiple physical hard drives and partitions into a single volume group which can then be
divided into logical volumes.
10
text; encrypted data is referred to as cipher text. In cryptography, encryption is the process
of encoding a message or information in such a way that only authorized parties can access it
and those who are not authorized cannot. Encryption does not itself prevent interference, but
denies the intelligible content to a would-be interceptor. By managing encryption keys in a
hardware security module, even if a hacker copies all data, the data will never be decrypted
without the cybercriminal physically accessing the premises where your data is kept.
Security not only means to protect the System, but it should also include all the connected
components, devices, software’s, Storage devices etc. Regular planned updates for the
System, software’s and packages help in maintaining the system at the latest version. This
will help in preventing and avoiding attacks from newer threats.
Today’s networks are constantly under attack and even the smallest vulnerabilities can be
quickly identified and exploited. System hardening, also called Operating
System hardening, helps minimize these security vulnerabilities. The purpose of
system hardening is to eliminate as many security risks as possible. This is typically done by
removing all non-essential software programs and utilities from the computer. Reducing
available ways of attack typically includes changing default passwords, the removal of
unnecessary software, unnecessary usernames or logins, and the disabling or removal of
unnecessary services.
Linux is the Operating system which is used extensively in the industry. Like any other
operating system working over a Network and exposed to the external web is prone to
vulnerabilities and attacks There should be a fine tuning for the System’s Performance and
the Security requirements. For our project this is also an important factor taken into
consideration.
Encrypt where possible
In Linux, Logical Volume Manager (LVM) is a device mapper target that provides logical
volume management for the Linux kernel. LVM allows for very flexible disk space
management. It provides features like the ability to add disk space to a logical volume and its
filesystem while that filesystem is mounted and active and it allows for the collection of
multiple physical hard drives and partitions into a single volume group which can then be
divided into logical volumes.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
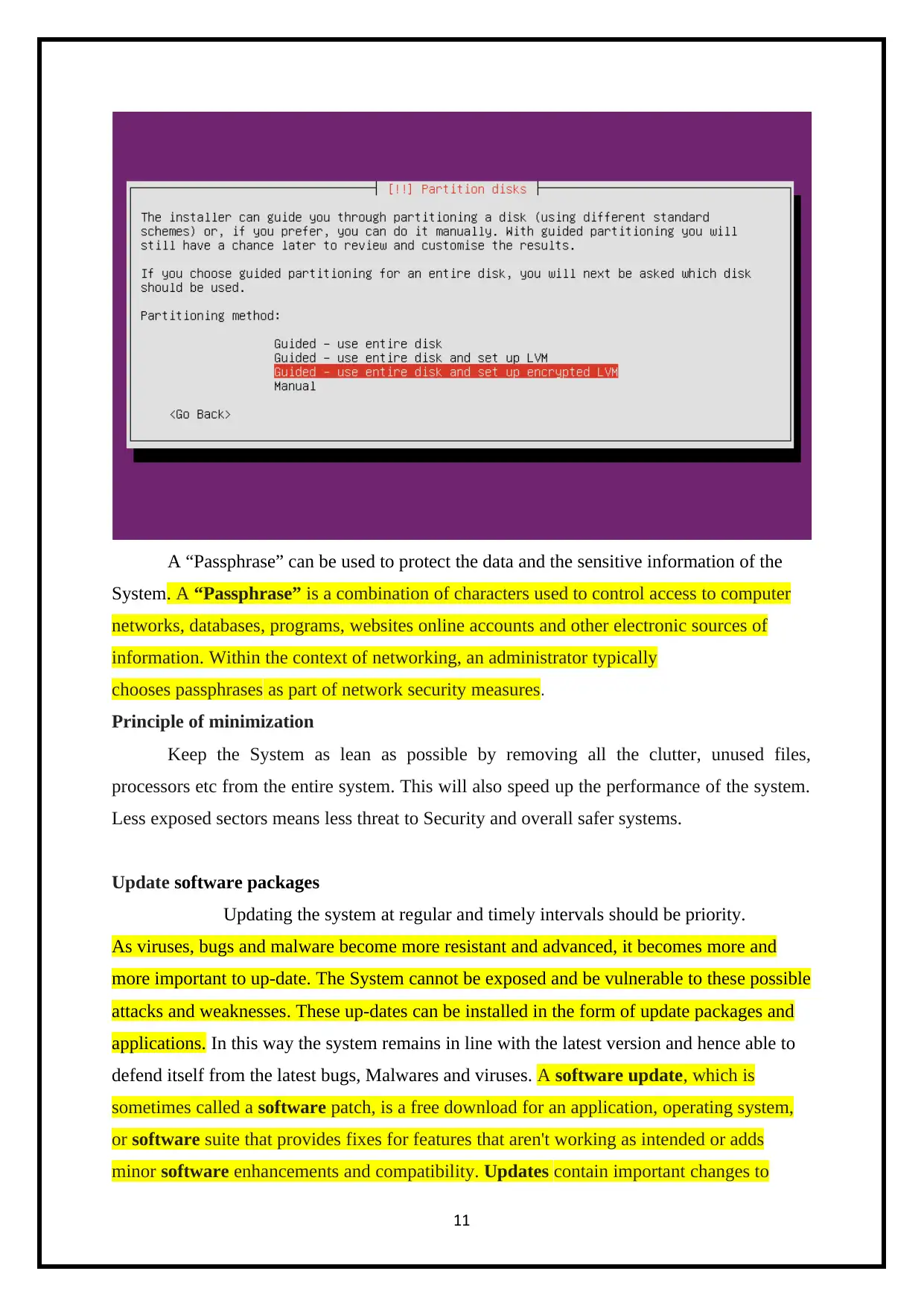
A “Passphrase” can be used to protect the data and the sensitive information of the
System. A “Passphrase” is a combination of characters used to control access to computer
networks, databases, programs, websites online accounts and other electronic sources of
information. Within the context of networking, an administrator typically
chooses passphrases as part of network security measures.
Principle of minimization
Keep the System as lean as possible by removing all the clutter, unused files,
processors etc from the entire system. This will also speed up the performance of the system.
Less exposed sectors means less threat to Security and overall safer systems.
Update software packages
Updating the system at regular and timely intervals should be priority.
As viruses, bugs and malware become more resistant and advanced, it becomes more and
more important to up-date. The System cannot be exposed and be vulnerable to these possible
attacks and weaknesses. These up-dates can be installed in the form of update packages and
applications. In this way the system remains in line with the latest version and hence able to
defend itself from the latest bugs, Malwares and viruses. A software update, which is
sometimes called a software patch, is a free download for an application, operating system,
or software suite that provides fixes for features that aren't working as intended or adds
minor software enhancements and compatibility. Updates contain important changes to
11
System. A “Passphrase” is a combination of characters used to control access to computer
networks, databases, programs, websites online accounts and other electronic sources of
information. Within the context of networking, an administrator typically
chooses passphrases as part of network security measures.
Principle of minimization
Keep the System as lean as possible by removing all the clutter, unused files,
processors etc from the entire system. This will also speed up the performance of the system.
Less exposed sectors means less threat to Security and overall safer systems.
Update software packages
Updating the system at regular and timely intervals should be priority.
As viruses, bugs and malware become more resistant and advanced, it becomes more and
more important to up-date. The System cannot be exposed and be vulnerable to these possible
attacks and weaknesses. These up-dates can be installed in the form of update packages and
applications. In this way the system remains in line with the latest version and hence able to
defend itself from the latest bugs, Malwares and viruses. A software update, which is
sometimes called a software patch, is a free download for an application, operating system,
or software suite that provides fixes for features that aren't working as intended or adds
minor software enhancements and compatibility. Updates contain important changes to
11

improve the performance, stability and security of the applications that run
on your computer. Installing them ensures that your software continues to run safely and
efficiently. Keep in mind that many web exploits look for outdated software with unpatched
security flaws. Thus the importance and the crucial aspect of “up-dates” cannot be ignored.
Weak configuration details
Understanding the applications and the software’s that we are using are important as
these systems have to be configured and applied. We have to evaluate its specifications and
try to make the system at its optimum best so that it is not exposed to potential threats.
Hardening a web server
Hardening web servers and ensuring server security is an important aspect of a
vulnerability management program. Potential attackers could exploit the flaws in web servers
which in turn may lead them to gain access to the systems hosting web servers and perform
unintended actions. Web server hardening involves the following factors, modifying the
configuration file to eliminate server misconfigurations, managing SSL/TSL certificates and
its settings to ensure secure communication between the client and server, and restricting
access permissions to the web server installation directory.
Use disk encryption
“Data Encryption” translates data into another form, or code, so that only people
with access to a secret key (formally called a decryption key) or password can read it.
Encrypted data is commonly referred to as cipher text, while unencrypted data is called
plaintext. Currently, encryption is one of the most popular and effective data security
methods used by organizations. The purpose of “Data Encryption” is to protect digital data
confidentiality as it is stored on computer systems and transmitted using the internet or other
computer networks. The outdated data encryption standard (DES) has been replaced by
modern encryption algorithms that play a critical role in the security of IT systems and
communications. These algorithms provide confidentiality and drive key security initiatives
including authentication, integrity, and non-repudiation. Authentication allows for the
verification of a message’s origin, and integrity provides proof that a message’s contents have
not changed since it was sent.
12
on your computer. Installing them ensures that your software continues to run safely and
efficiently. Keep in mind that many web exploits look for outdated software with unpatched
security flaws. Thus the importance and the crucial aspect of “up-dates” cannot be ignored.
Weak configuration details
Understanding the applications and the software’s that we are using are important as
these systems have to be configured and applied. We have to evaluate its specifications and
try to make the system at its optimum best so that it is not exposed to potential threats.
Hardening a web server
Hardening web servers and ensuring server security is an important aspect of a
vulnerability management program. Potential attackers could exploit the flaws in web servers
which in turn may lead them to gain access to the systems hosting web servers and perform
unintended actions. Web server hardening involves the following factors, modifying the
configuration file to eliminate server misconfigurations, managing SSL/TSL certificates and
its settings to ensure secure communication between the client and server, and restricting
access permissions to the web server installation directory.
Use disk encryption
“Data Encryption” translates data into another form, or code, so that only people
with access to a secret key (formally called a decryption key) or password can read it.
Encrypted data is commonly referred to as cipher text, while unencrypted data is called
plaintext. Currently, encryption is one of the most popular and effective data security
methods used by organizations. The purpose of “Data Encryption” is to protect digital data
confidentiality as it is stored on computer systems and transmitted using the internet or other
computer networks. The outdated data encryption standard (DES) has been replaced by
modern encryption algorithms that play a critical role in the security of IT systems and
communications. These algorithms provide confidentiality and drive key security initiatives
including authentication, integrity, and non-repudiation. Authentication allows for the
verification of a message’s origin, and integrity provides proof that a message’s contents have
not changed since it was sent.
12

Automatic Security Updates
Up-dates are part of every software and application to keep the tool to the latest
version. Now these update can be done manually whenever there is an update. Operating
Systems like Linux and Ubuntu files have regular updates and same should be done as soon
as possible. Here the “auto Update” feature will help a lot. During the installation process
itself, the facility i.e. “Install security updates automatically” should be used in all the
software’s so that even if we forget to update, the system will itself update on its own.
Improve your passwords
A strong “Password” provides essential protection from financial fraud and identity theft.
One of the most common ways that hackers break into computers is by guessing passwords.
Simple and commonly used passwords enable intruders to easily gain access and control of a
computing device. Long and complex passwords require more effort and time for a hacker to
guess. Passwords should contain at least ten characters and have a combination of characters
such as commas, percent signs, and parentheses, as well as upper-case and lower-case letters
and numbers.
SSH hardening
SSH or Secure Shell is the popular protocol for doing system administration on
Linux systems. It runs on most systems, often with its default configuration. As this service
opens up a potential gateway into the system, it is one of the steps to hardening a Linux
system. Run the SSH to perform SSH configuration Hardening before using the system.
Check for connections and external drives when the configuration is running.
Task 4 – Investigation Report and Details of the Security System
We shall be discussing about a Special Security Tool which is extensively used on
Linux Systems. It is “Lynis”. Lynis is an extensible security audit tool for computer systems
running Linux. It assists system administrators and security professionals with scanning a
system and its security defenses, with the final goal being system hardening. The tools can
run security scans on the system itself or even remotely. The primary goal of this tool is to
13
Up-dates are part of every software and application to keep the tool to the latest
version. Now these update can be done manually whenever there is an update. Operating
Systems like Linux and Ubuntu files have regular updates and same should be done as soon
as possible. Here the “auto Update” feature will help a lot. During the installation process
itself, the facility i.e. “Install security updates automatically” should be used in all the
software’s so that even if we forget to update, the system will itself update on its own.
Improve your passwords
A strong “Password” provides essential protection from financial fraud and identity theft.
One of the most common ways that hackers break into computers is by guessing passwords.
Simple and commonly used passwords enable intruders to easily gain access and control of a
computing device. Long and complex passwords require more effort and time for a hacker to
guess. Passwords should contain at least ten characters and have a combination of characters
such as commas, percent signs, and parentheses, as well as upper-case and lower-case letters
and numbers.
SSH hardening
SSH or Secure Shell is the popular protocol for doing system administration on
Linux systems. It runs on most systems, often with its default configuration. As this service
opens up a potential gateway into the system, it is one of the steps to hardening a Linux
system. Run the SSH to perform SSH configuration Hardening before using the system.
Check for connections and external drives when the configuration is running.
Task 4 – Investigation Report and Details of the Security System
We shall be discussing about a Special Security Tool which is extensively used on
Linux Systems. It is “Lynis”. Lynis is an extensible security audit tool for computer systems
running Linux. It assists system administrators and security professionals with scanning a
system and its security defenses, with the final goal being system hardening. The tools can
run security scans on the system itself or even remotely. The primary goal of this tool is to
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
test the configuration of a system and provide tips to harden security. The tool can also scan
for general information and vulnerable software packages and possible configurations flaws
in the system. Lynis is commonly used by the system administrators and security penetration
testers to perform audits and assess a system’s security. After running the tool on the System
or the Network, it shall display a number of helpful recommendations in hardening your
system. This tool is useful for auditors, network and system administrators, security
specialists and penetration testers (Gupta and Anand, 2017).
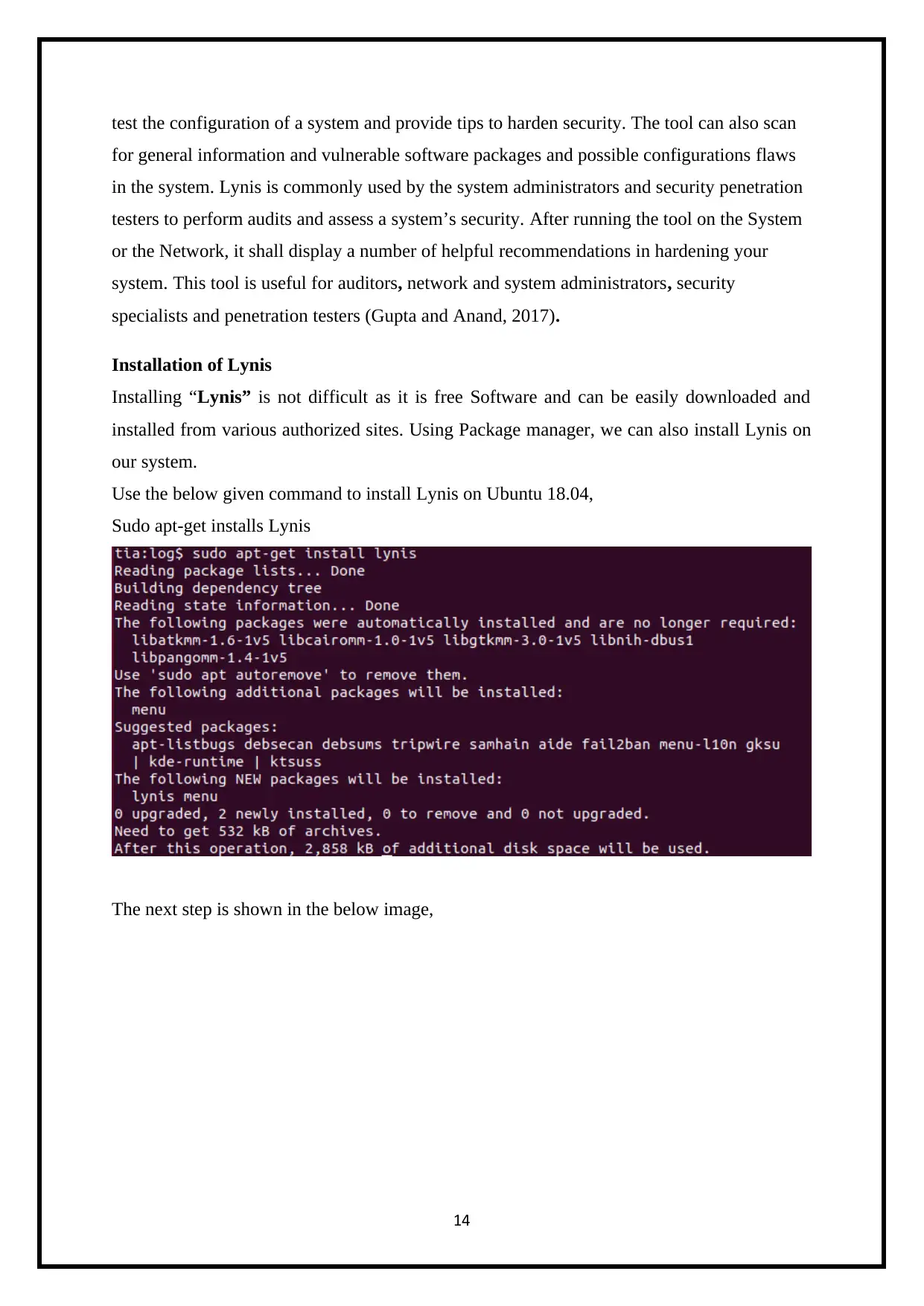
Installation of Lynis
Installing “Lynis” is not difficult as it is free Software and can be easily downloaded and
installed from various authorized sites. Using Package manager, we can also install Lynis on
our system.
Use the below given command to install Lynis on Ubuntu 18.04,
Sudo apt-get installs Lynis
The next step is shown in the below image,
14
for general information and vulnerable software packages and possible configurations flaws
in the system. Lynis is commonly used by the system administrators and security penetration
testers to perform audits and assess a system’s security. After running the tool on the System
or the Network, it shall display a number of helpful recommendations in hardening your
system. This tool is useful for auditors, network and system administrators, security
specialists and penetration testers (Gupta and Anand, 2017).
Installation of Lynis
Installing “Lynis” is not difficult as it is free Software and can be easily downloaded and
installed from various authorized sites. Using Package manager, we can also install Lynis on
our system.
Use the below given command to install Lynis on Ubuntu 18.04,
Sudo apt-get installs Lynis
The next step is shown in the below image,
14
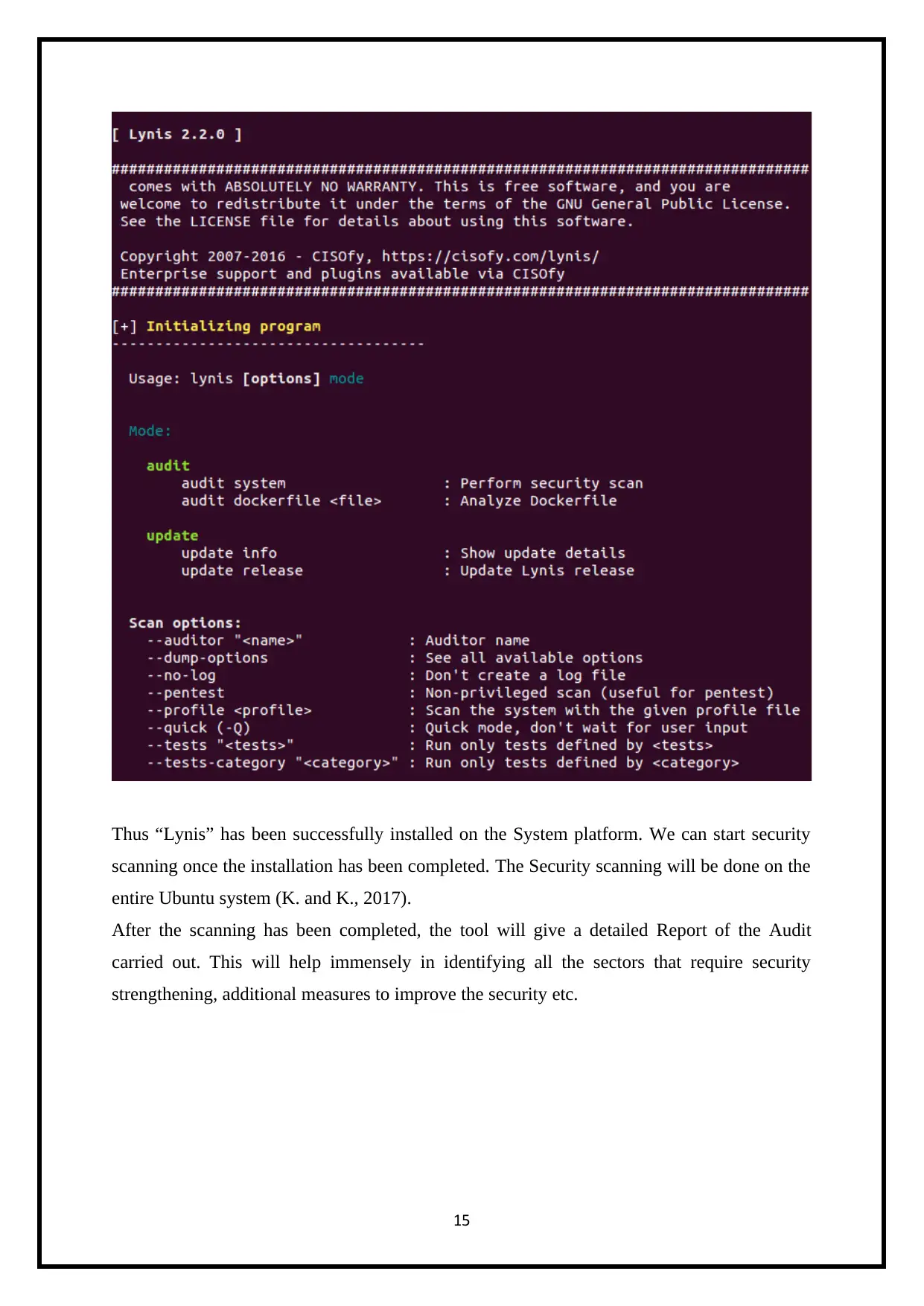
Thus “Lynis” has been successfully installed on the System platform. We can start security
scanning once the installation has been completed. The Security scanning will be done on the
entire Ubuntu system (K. and K., 2017).
After the scanning has been completed, the tool will give a detailed Report of the Audit
carried out. This will help immensely in identifying all the sectors that require security
strengthening, additional measures to improve the security etc.
15
scanning once the installation has been completed. The Security scanning will be done on the
entire Ubuntu system (K. and K., 2017).
After the scanning has been completed, the tool will give a detailed Report of the Audit
carried out. This will help immensely in identifying all the sectors that require security
strengthening, additional measures to improve the security etc.
15
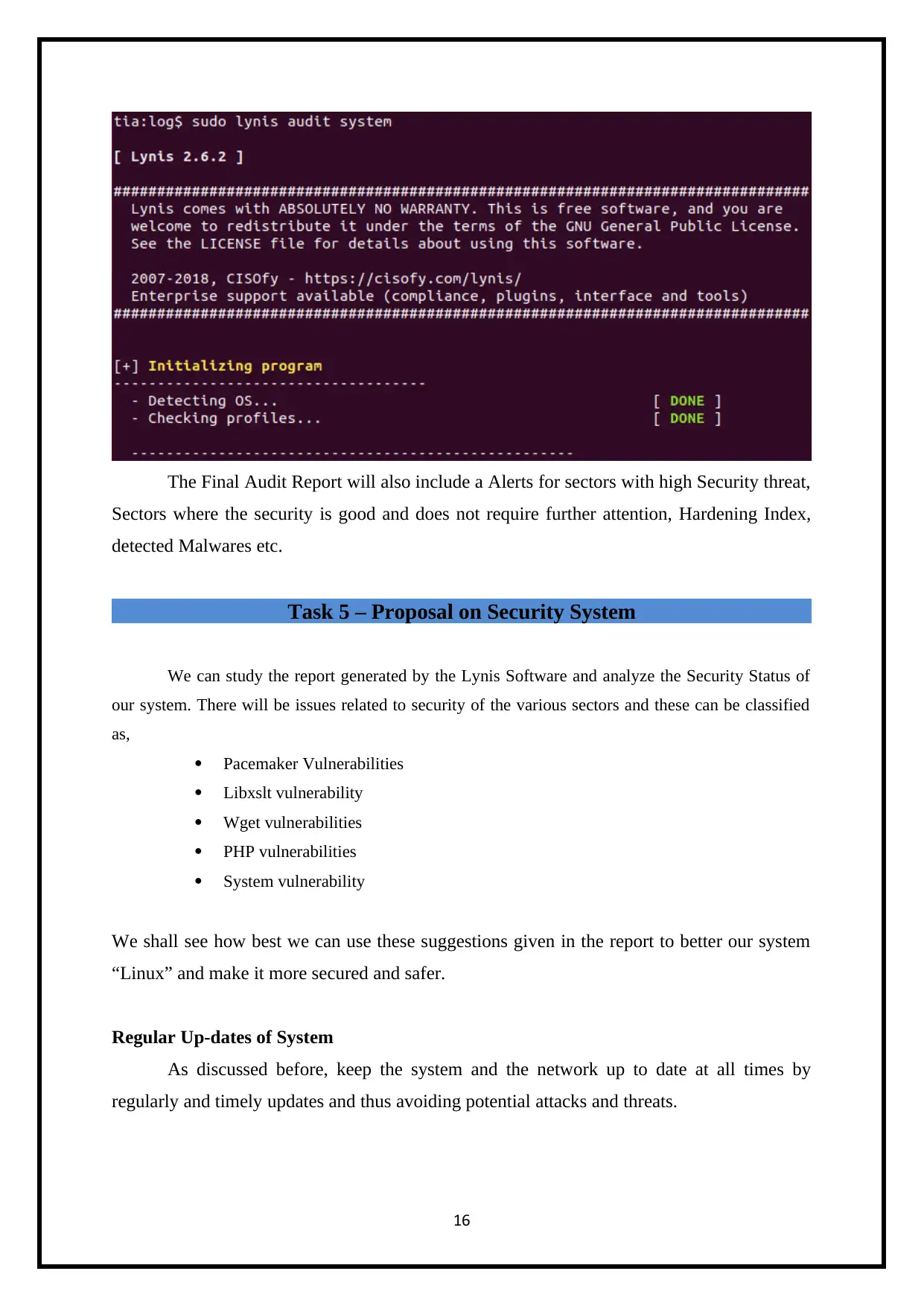
The Final Audit Report will also include a Alerts for sectors with high Security threat,
Sectors where the security is good and does not require further attention, Hardening Index,
detected Malwares etc.
Task 5 – Proposal on Security System
We can study the report generated by the Lynis Software and analyze the Security Status of
our system. There will be issues related to security of the various sectors and these can be classified
as,
Pacemaker Vulnerabilities
Libxslt vulnerability
Wget vulnerabilities
PHP vulnerabilities
System vulnerability
We shall see how best we can use these suggestions given in the report to better our system
“Linux” and make it more secured and safer.
Regular Up-dates of System
As discussed before, keep the system and the network up to date at all times by
regularly and timely updates and thus avoiding potential attacks and threats.
16
Sectors where the security is good and does not require further attention, Hardening Index,
detected Malwares etc.
Task 5 – Proposal on Security System
We can study the report generated by the Lynis Software and analyze the Security Status of
our system. There will be issues related to security of the various sectors and these can be classified
as,
Pacemaker Vulnerabilities
Libxslt vulnerability
Wget vulnerabilities
PHP vulnerabilities
System vulnerability
We shall see how best we can use these suggestions given in the report to better our system
“Linux” and make it more secured and safer.
Regular Up-dates of System
As discussed before, keep the system and the network up to date at all times by
regularly and timely updates and thus avoiding potential attacks and threats.
16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Performing a security audit
As seen in the above discussion, using Auditing tools like Lynis helps a lot in identifying the
weak sectors, especially in relation to our Security concerns. This is like checking the health
status of our System to understand which organ (sector) needs our utmost attention. This will
also help once the Hardening of the system has been completed and when there are security
related issues in the system.
Some of the other popular Security Evaluation tools for Security Auditing available are Lynis
Nmap and OpenVas (Kali Linux – Assuring Security by Penetration Testing, 2014).
Lynis Audits
Lynis as we have mentioned before is an open software tool for Security Audits and Health
scans. Lynis reports are very detailed and gives a very good insight on all the sectors and how
best to improve the overall health of the system. It is also very fast and takes less memory
and processing power when in use.
Nmap and Security Scanning
Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and
network discovery. Network administrators use Nmap to identify what devices are running on
their systems, discovering hosts that are available and the services they offer, finding open
ports and detecting security risks. Nmap can be used to monitor single hosts as well as vast
networks that encompass hundreds of thousands of devices and multitudes of subnets. The
packets that Nmap sends out return with IP addresses and a wealth of other data, allowing
you to identify all sorts of network attributes, giving you a profile or map of the network and
allowing you to create a hardware and software inventory. Thus this will add to the security if
the overall Network. It works well on platforms like Linux, Ubuntu etc.
OpenVAS and Vulnerability scanning
The Open Vulnerability Assessment System (OpenVAS) is a vulnerability scanner
maintained and distributed by Greenbone Networks. It is intended to be an all-in-one
vulnerability scanner with a variety of built-in tests and a Web interface designed to make
setting up and running vulnerability scans fast and easy while providing a high level of user
17
As seen in the above discussion, using Auditing tools like Lynis helps a lot in identifying the
weak sectors, especially in relation to our Security concerns. This is like checking the health
status of our System to understand which organ (sector) needs our utmost attention. This will
also help once the Hardening of the system has been completed and when there are security
related issues in the system.
Some of the other popular Security Evaluation tools for Security Auditing available are Lynis
Nmap and OpenVas (Kali Linux – Assuring Security by Penetration Testing, 2014).
Lynis Audits
Lynis as we have mentioned before is an open software tool for Security Audits and Health
scans. Lynis reports are very detailed and gives a very good insight on all the sectors and how
best to improve the overall health of the system. It is also very fast and takes less memory
and processing power when in use.
Nmap and Security Scanning
Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and
network discovery. Network administrators use Nmap to identify what devices are running on
their systems, discovering hosts that are available and the services they offer, finding open
ports and detecting security risks. Nmap can be used to monitor single hosts as well as vast
networks that encompass hundreds of thousands of devices and multitudes of subnets. The
packets that Nmap sends out return with IP addresses and a wealth of other data, allowing
you to identify all sorts of network attributes, giving you a profile or map of the network and
allowing you to create a hardware and software inventory. Thus this will add to the security if
the overall Network. It works well on platforms like Linux, Ubuntu etc.
OpenVAS and Vulnerability scanning
The Open Vulnerability Assessment System (OpenVAS) is a vulnerability scanner
maintained and distributed by Greenbone Networks. It is intended to be an all-in-one
vulnerability scanner with a variety of built-in tests and a Web interface designed to make
setting up and running vulnerability scans fast and easy while providing a high level of user
17

configurability. OpenVAS is a vulnerability scanner designed to run in a Linux environment.
It can be installed either as a self-contained virtual machine or from source code.
Vulnerability scanning is a crucial phase of a penetration test and having an updated
vulnerability scanner in your security toolkit can often make a real difference by helping you
discover overlooked vulnerable items .It is an ideal choice for the independent penetration
tester or for Network admin’s who needs an inexpensive and intuitive option for identifying
potential security holes.
Firewall – UFW
UFW, or uncomplicated firewall, is a frontend for managing firewall rules in Arch Linux,
Debian or Ubuntu. UFW is used through the command line (although it has GUIs available),
and aims to make firewall configuration easy (or, uncomplicated).
The Uncomplicated Firewall (UFW) is a frontend for iptables and is particularly well-suited
for host-based firewalls. UFW provides a framework for managing net filter, as well as a
command-line interface for manipulating the firewall. UFW aims to provide an easy to use
interface for people unfamiliar with firewall concepts, while at the same time simplifies
complicated iptables commands to help an administrator who knows what he or she is
doing. UFW is an upstream for other distributions and graphical frontends.
The ufw application is capable of doing anything that iptables can do. This is achieved by
using several sets of rules files, which are nothing more than iptables-restore compatible text
files. This Firewall helps to control the data that is coming in and going out. It is the line of
defense for all information passing within the network and outside it. It is a major barrier in
keeping malicious elements from entering the system and to create problems within.
Problematic Sectors should be discarded.
Removal of areas within the System that are causing issues to the whole network or
even a part of it should be immediately isolated and removed. This will be good for the
overall performance of the system as the performance will improve. Less sectors means less
threats and attacks. Security will improve as there will be less exposed area of the Network.
Will include the following,
UDP and TCPwill be the running services as identified.
Identify the services which have to be discarded.
Discarding unwanted sectors, areas, services and programs.
18
It can be installed either as a self-contained virtual machine or from source code.
Vulnerability scanning is a crucial phase of a penetration test and having an updated
vulnerability scanner in your security toolkit can often make a real difference by helping you
discover overlooked vulnerable items .It is an ideal choice for the independent penetration
tester or for Network admin’s who needs an inexpensive and intuitive option for identifying
potential security holes.
Firewall – UFW
UFW, or uncomplicated firewall, is a frontend for managing firewall rules in Arch Linux,
Debian or Ubuntu. UFW is used through the command line (although it has GUIs available),
and aims to make firewall configuration easy (or, uncomplicated).
The Uncomplicated Firewall (UFW) is a frontend for iptables and is particularly well-suited
for host-based firewalls. UFW provides a framework for managing net filter, as well as a
command-line interface for manipulating the firewall. UFW aims to provide an easy to use
interface for people unfamiliar with firewall concepts, while at the same time simplifies
complicated iptables commands to help an administrator who knows what he or she is
doing. UFW is an upstream for other distributions and graphical frontends.
The ufw application is capable of doing anything that iptables can do. This is achieved by
using several sets of rules files, which are nothing more than iptables-restore compatible text
files. This Firewall helps to control the data that is coming in and going out. It is the line of
defense for all information passing within the network and outside it. It is a major barrier in
keeping malicious elements from entering the system and to create problems within.
Problematic Sectors should be discarded.
Removal of areas within the System that are causing issues to the whole network or
even a part of it should be immediately isolated and removed. This will be good for the
overall performance of the system as the performance will improve. Less sectors means less
threats and attacks. Security will improve as there will be less exposed area of the Network.
Will include the following,
UDP and TCPwill be the running services as identified.
Identify the services which have to be discarded.
Discarding unwanted sectors, areas, services and programs.
18

Finally we have finished our entire process of Security Evaluation and Analysis and thus
making our System (Ubuntu) Safe, Secured and working at its peak performance (Müller-
Török and Schäfer, 2013).
.
References
Gunawan, T., Kasim Lim, M., Kartiwi, M., Abdul Malik, N. and Ismail, N. (2018).
Penetration Testing using Kali Linux: SQL Injection, XSS, Wordpres, and WPA2
Attacks. Indonesian Journal of Electrical Engineering and Computer Science, 12(2),
p.729.
Gupta, A. and Anand, A. (2017). Ethical Hacking and Hacking Attacks. International
Journal Of Engineering And Computer Science.
K., A. and K., C. (2017). Analyzing the Bitmap Image File and Extracting Different Bit
Patterns for Compressing the Image File using Distinct Colour Codes. International
Journal of Computer Applications, 180(5), pp.17-20.
Kali Linux – Assuring Security by Penetration Testing. (2014). Network Security,
2014(8), p.4.
Müller-Török, R. and Schäfer, N. (2013). Hauptwohnort, Wahlrecht und steuerliche
Veranlagung. VM, pp.98-102.
19
making our System (Ubuntu) Safe, Secured and working at its peak performance (Müller-
Török and Schäfer, 2013).
.
References
Gunawan, T., Kasim Lim, M., Kartiwi, M., Abdul Malik, N. and Ismail, N. (2018).
Penetration Testing using Kali Linux: SQL Injection, XSS, Wordpres, and WPA2
Attacks. Indonesian Journal of Electrical Engineering and Computer Science, 12(2),
p.729.
Gupta, A. and Anand, A. (2017). Ethical Hacking and Hacking Attacks. International
Journal Of Engineering And Computer Science.
K., A. and K., C. (2017). Analyzing the Bitmap Image File and Extracting Different Bit
Patterns for Compressing the Image File using Distinct Colour Codes. International
Journal of Computer Applications, 180(5), pp.17-20.
Kali Linux – Assuring Security by Penetration Testing. (2014). Network Security,
2014(8), p.4.
Müller-Török, R. and Schäfer, N. (2013). Hauptwohnort, Wahlrecht und steuerliche
Veranlagung. VM, pp.98-102.
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
20
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





