Manage Network and Data Integrity
VerifiedAdded on 2023/03/31
|62
|2549
|302
AI Summary
This document provides a comprehensive guide on how to manage network and data integrity. It covers topics such as creating an effective antivirus security policy, installing antivirus software, configuring security on the router/modem, and more. The document also includes step-by-step instructions and screenshots for easy understanding.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

University
Semester
ICTNWK403 Manage Network and
Data Integrity
Student ID
Student Name
Submission Date
1
Semester
ICTNWK403 Manage Network and
Data Integrity
Student ID
Student Name
Submission Date
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1. Project Description........................................................................................................................4
2. Create an effective antivirus security policy..................................................................................4
3. Install antivirus software on all appropriate systems.....................................................................6
4. Develop information security awareness training........................................................................19
5. Configure Security on the Router / modem..................................................................................21
6. Configure security on the switch.................................................................................................23
7. Configure GPO............................................................................................................................26
8. Install suitable security software no.............................................................................................27
9. Establish security policy..............................................................................................................33
10. Configure user permissions / authenticate users......................................................................35
11. Configure file and folder access permissions...........................................................................37
12. Develop and configure inventory system.................................................................................42
13. Configure firewall....................................................................................................................43
14. Configure VPN........................................................................................................................44
15. Configure DHCP.....................................................................................................................45
16. Configure DNS........................................................................................................................46
17. Configure Certificates..............................................................................................................47
18. Create backup solution.............................................................................................................47
19. Check integrity of your data....................................................................................................48
20. Monitor logon events to the domain........................................................................................49
21. Create DMZ.............................................................................................................................49
22. Create VLANS........................................................................................................................50
23. Set VPN between sites.............................................................................................................51
24. Display warning message before user loges in.........................................................................52
25. Enforce password policy..........................................................................................................52
26. Enforce physical and environmental security...........................................................................53
27. Install network performance tools............................................................................................54
28. Generate network reports.........................................................................................................54
29. Audit and record security access..............................................................................................54
30. Determine threats / identify risks.............................................................................................55
31. Make recommendations...........................................................................................................55
32. Create baseline.........................................................................................................................56
2
1. Project Description........................................................................................................................4
2. Create an effective antivirus security policy..................................................................................4
3. Install antivirus software on all appropriate systems.....................................................................6
4. Develop information security awareness training........................................................................19
5. Configure Security on the Router / modem..................................................................................21
6. Configure security on the switch.................................................................................................23
7. Configure GPO............................................................................................................................26
8. Install suitable security software no.............................................................................................27
9. Establish security policy..............................................................................................................33
10. Configure user permissions / authenticate users......................................................................35
11. Configure file and folder access permissions...........................................................................37
12. Develop and configure inventory system.................................................................................42
13. Configure firewall....................................................................................................................43
14. Configure VPN........................................................................................................................44
15. Configure DHCP.....................................................................................................................45
16. Configure DNS........................................................................................................................46
17. Configure Certificates..............................................................................................................47
18. Create backup solution.............................................................................................................47
19. Check integrity of your data....................................................................................................48
20. Monitor logon events to the domain........................................................................................49
21. Create DMZ.............................................................................................................................49
22. Create VLANS........................................................................................................................50
23. Set VPN between sites.............................................................................................................51
24. Display warning message before user loges in.........................................................................52
25. Enforce password policy..........................................................................................................52
26. Enforce physical and environmental security...........................................................................53
27. Install network performance tools............................................................................................54
28. Generate network reports.........................................................................................................54
29. Audit and record security access..............................................................................................54
30. Determine threats / identify risks.............................................................................................55
31. Make recommendations...........................................................................................................55
32. Create baseline.........................................................................................................................56
2

33. Modify system if required........................................................................................................56
34. Document your system............................................................................................................56
35. Review logs for possible intrusions.........................................................................................57
36. Carry out spot checks / document possible breaches...............................................................58
References...........................................................................................................................................60
3
34. Document your system............................................................................................................56
35. Review logs for possible intrusions.........................................................................................57
36. Carry out spot checks / document possible breaches...............................................................58
References...........................................................................................................................................60
3

1. Project Description
The main aim of this project is to implement, install and configure the network security and
to use it for data production. The process of analysis and systems is to create policies, enforce
technologies to minimize risk and make them more secure for the structure on the network
configuration. The main objective of the project is to use it for the development and manage
the antivirus system for the workstation, email filtering and server of the networking system.
The selected firm has 20 desktop and 20 laptop computers. The identification of the virus is
done by analysing it by two methods that are denoted as, Viruses and Malicious code on the
network. Disaster Recovery and Business management planning on the network security will
be investigated.
2. Create an effective antivirus security policy
Creating of the antivirus security software should mainly be specified for
the detection of the viruses on the computer and laptop. Analysis of each laptop and computer
for malicious threats shall be carried out for the pc so as to keep them in good condition. The
advanced security of the Comoro antivirus can be used for the detection of the virus and to
identify the same on each computer for any malicious attacks, to protect all the computers,
remove any malicious file and only access given for the important data of the computer
security. The Comoro antivirus features are given below (Gollmann, 2011),
Detects suspicious files immediately
Offers intelligent definition technique
Real time protection
Instant and quick update on the latest virus definition.
Access scanning.
4
The main aim of this project is to implement, install and configure the network security and
to use it for data production. The process of analysis and systems is to create policies, enforce
technologies to minimize risk and make them more secure for the structure on the network
configuration. The main objective of the project is to use it for the development and manage
the antivirus system for the workstation, email filtering and server of the networking system.
The selected firm has 20 desktop and 20 laptop computers. The identification of the virus is
done by analysing it by two methods that are denoted as, Viruses and Malicious code on the
network. Disaster Recovery and Business management planning on the network security will
be investigated.
2. Create an effective antivirus security policy
Creating of the antivirus security software should mainly be specified for
the detection of the viruses on the computer and laptop. Analysis of each laptop and computer
for malicious threats shall be carried out for the pc so as to keep them in good condition. The
advanced security of the Comoro antivirus can be used for the detection of the virus and to
identify the same on each computer for any malicious attacks, to protect all the computers,
remove any malicious file and only access given for the important data of the computer
security. The Comoro antivirus features are given below (Gollmann, 2011),
Detects suspicious files immediately
Offers intelligent definition technique
Real time protection
Instant and quick update on the latest virus definition.
Access scanning.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
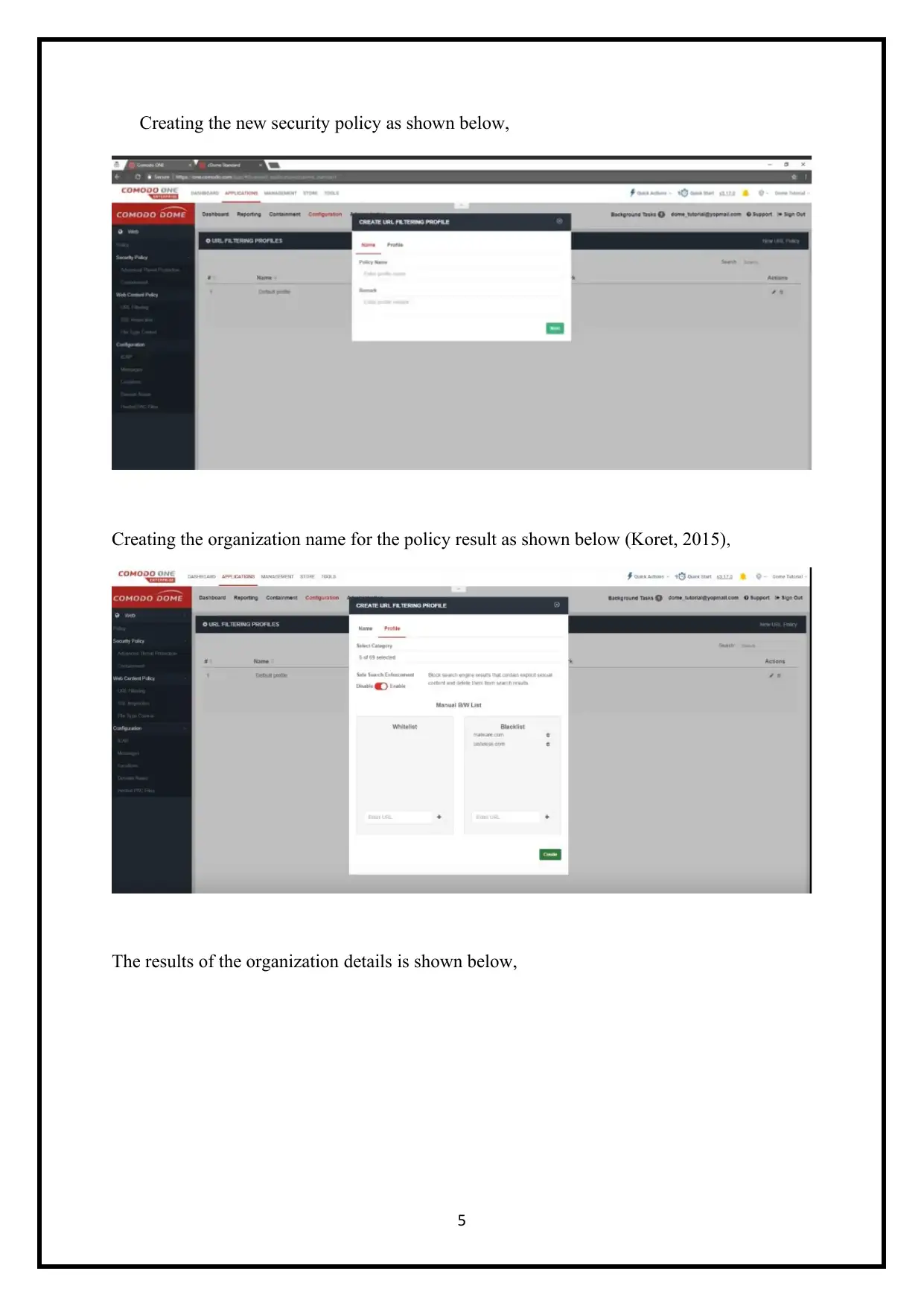
Creating the new security policy as shown below,
Creating the organization name for the policy result as shown below (Koret, 2015),
The results of the organization details is shown below,
5
Creating the organization name for the policy result as shown below (Koret, 2015),
The results of the organization details is shown below,
5
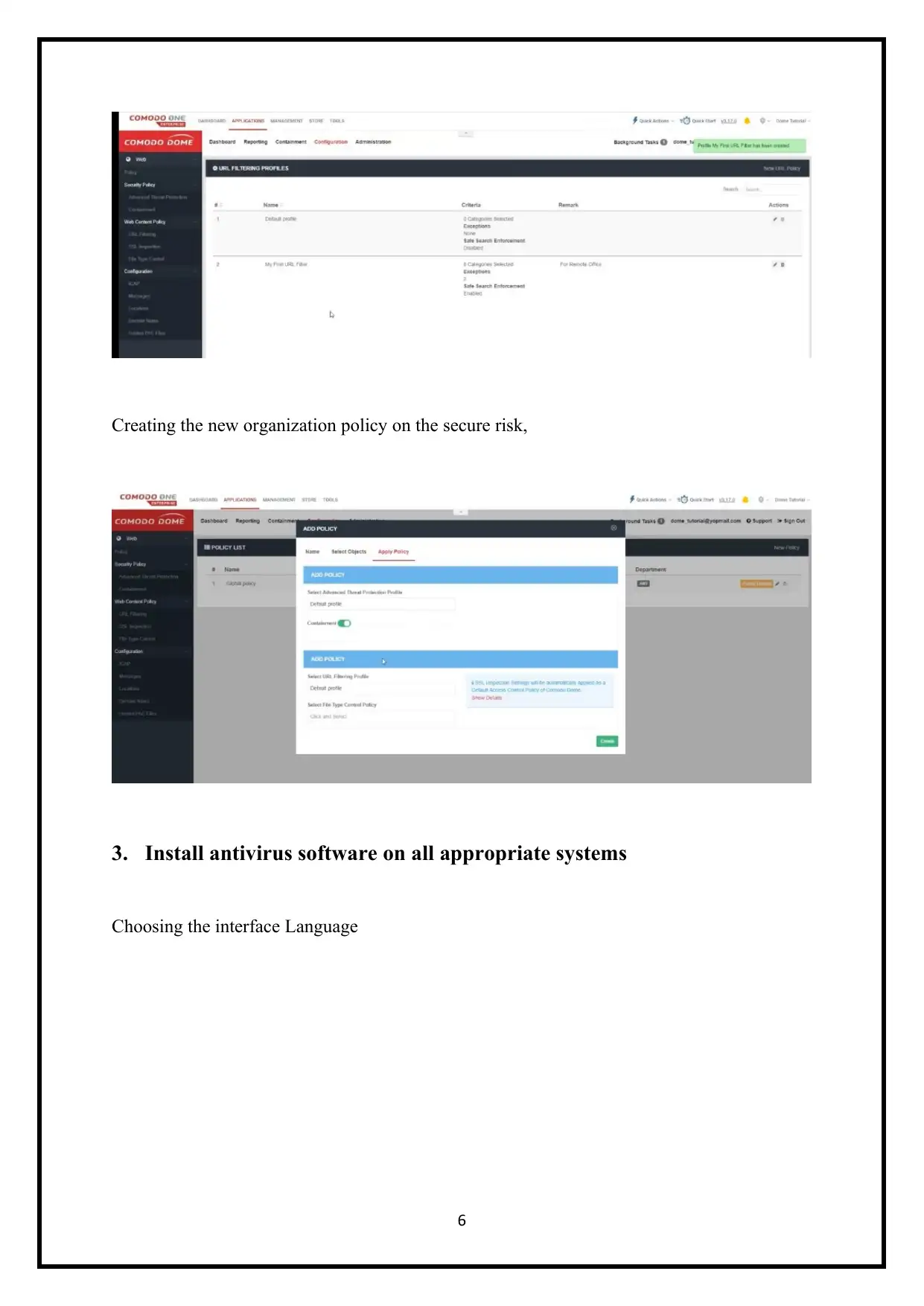
Creating the new organization policy on the secure risk,
3. Install antivirus software on all appropriate systems
Choosing the interface Language
6
3. Install antivirus software on all appropriate systems
Choosing the interface Language
6
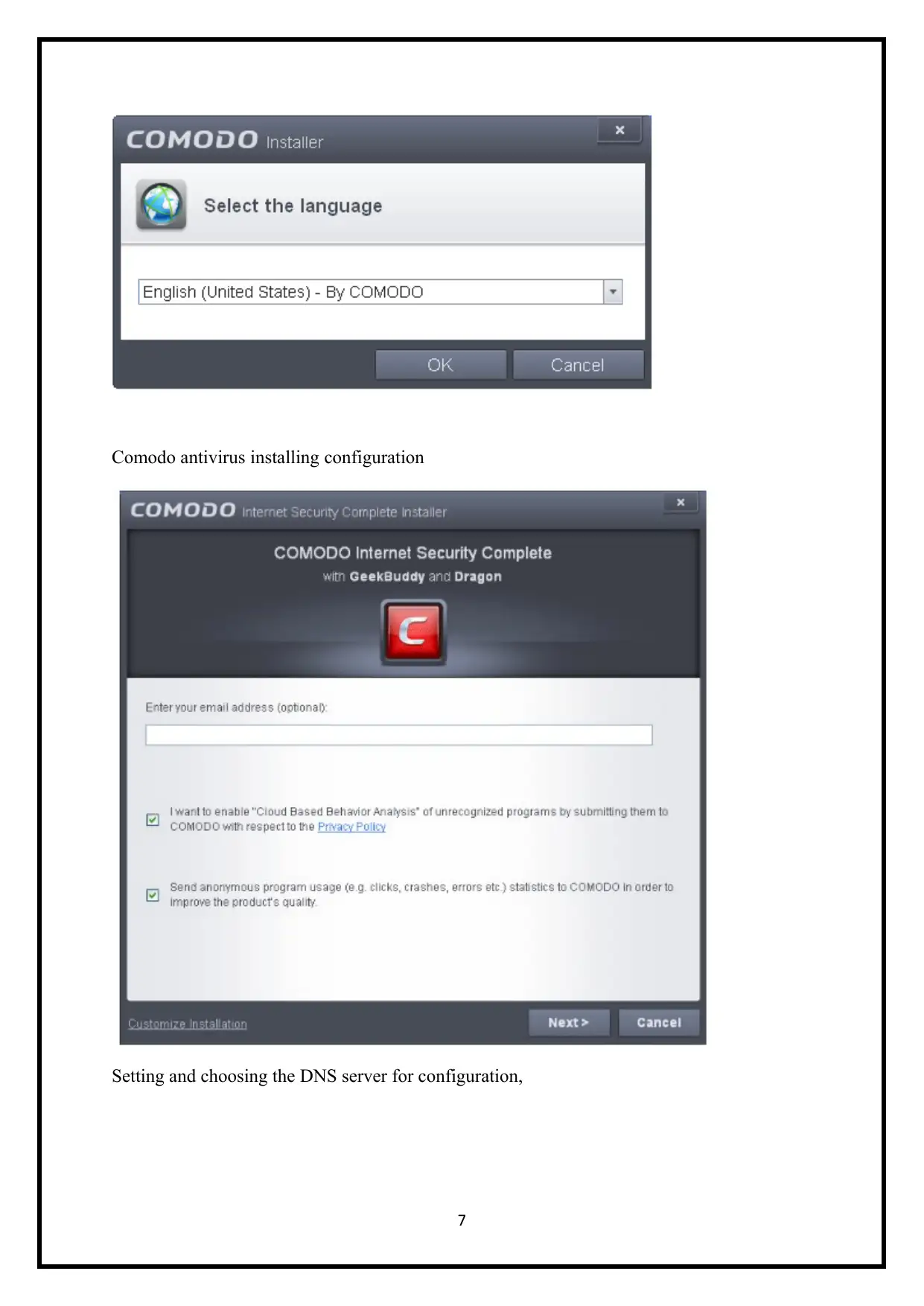
Comodo antivirus installing configuration
Setting and choosing the DNS server for configuration,
7
Setting and choosing the DNS server for configuration,
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
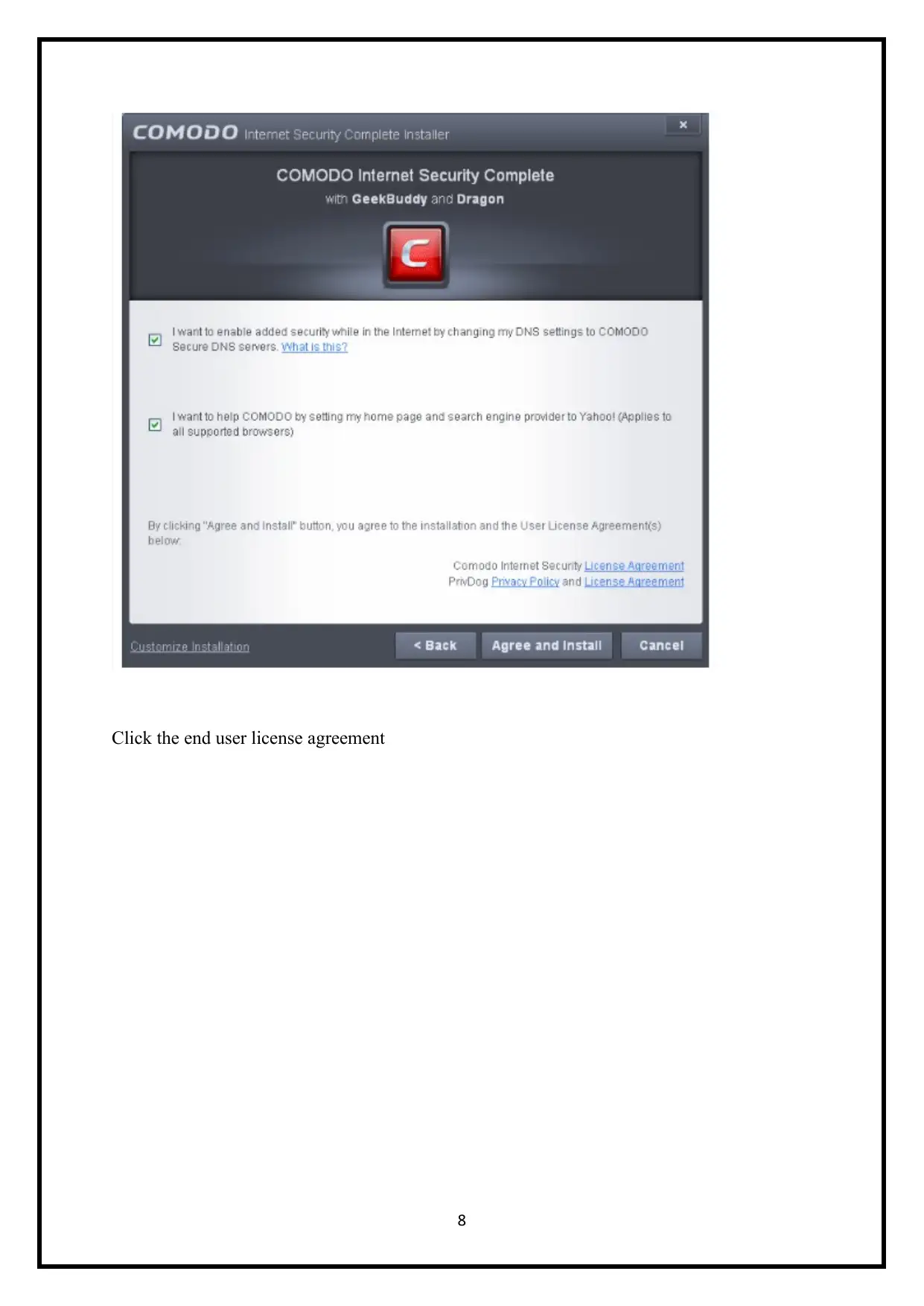
Click the end user license agreement
8
8
Customize the initialization,
9
9
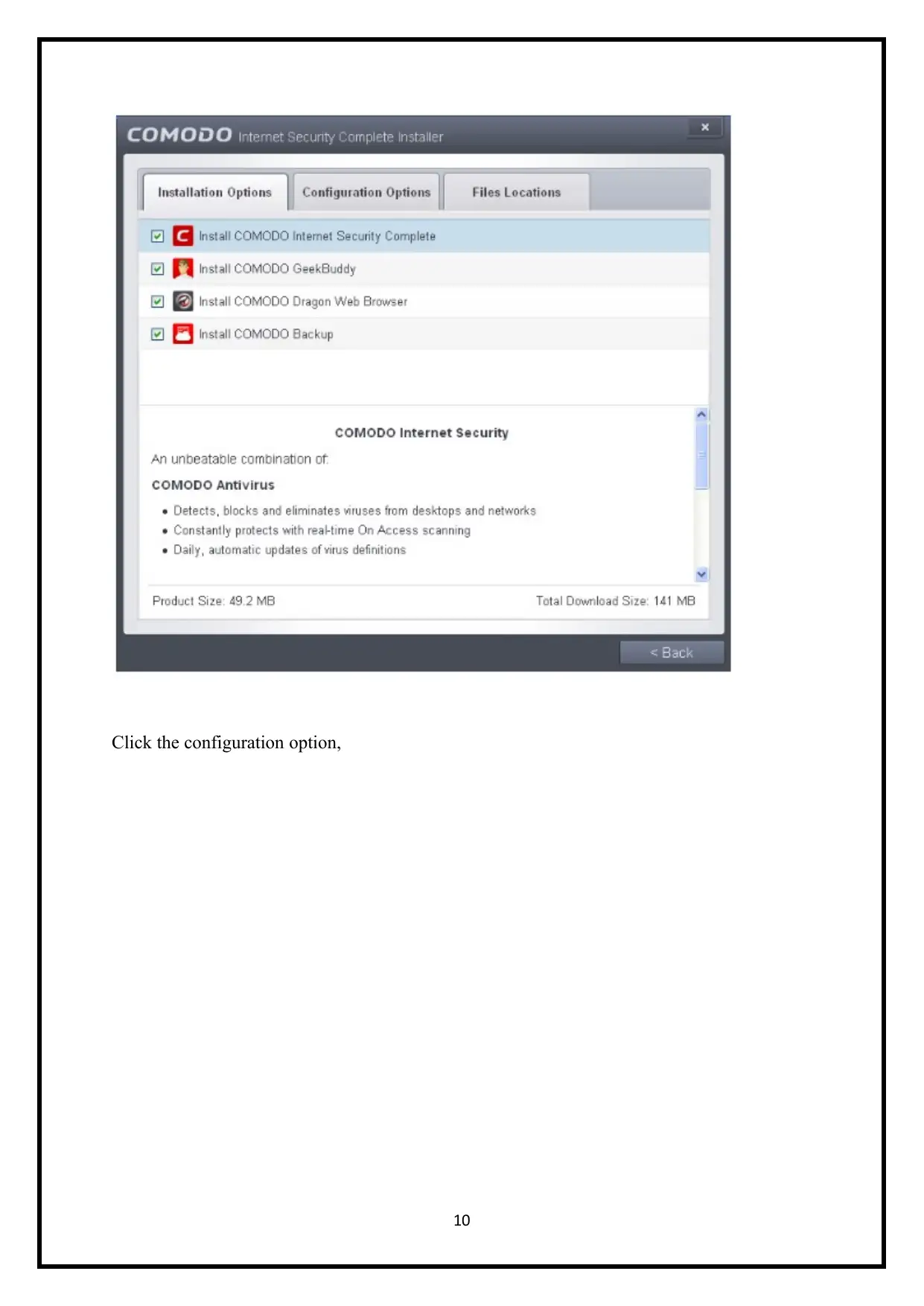
Click the configuration option,
10
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Select the installation location,
11
11
Comodo antiviruses’ installation is in progress as displayed in the below image,
12
12
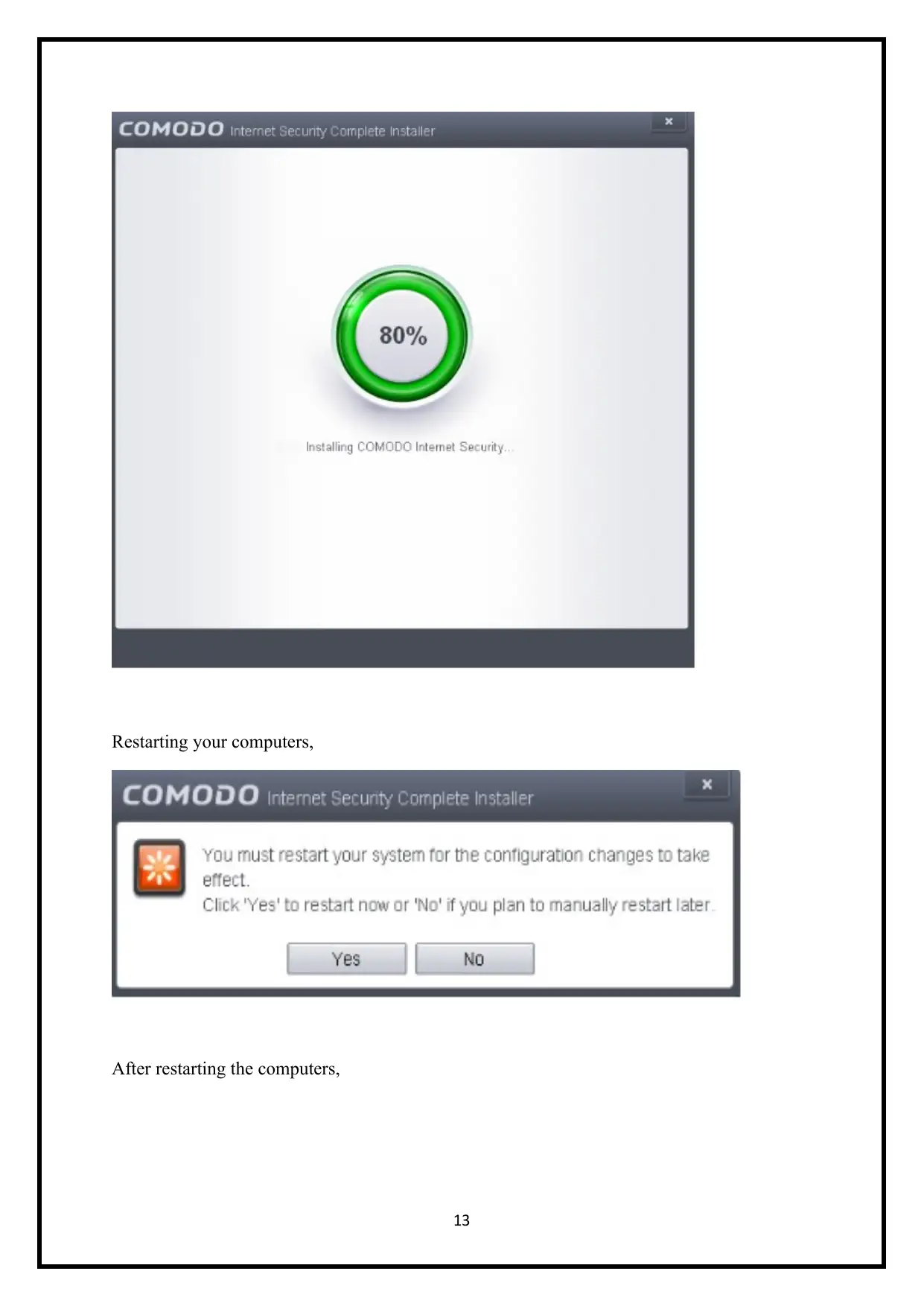
Restarting your computers,
After restarting the computers,
13
After restarting the computers,
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
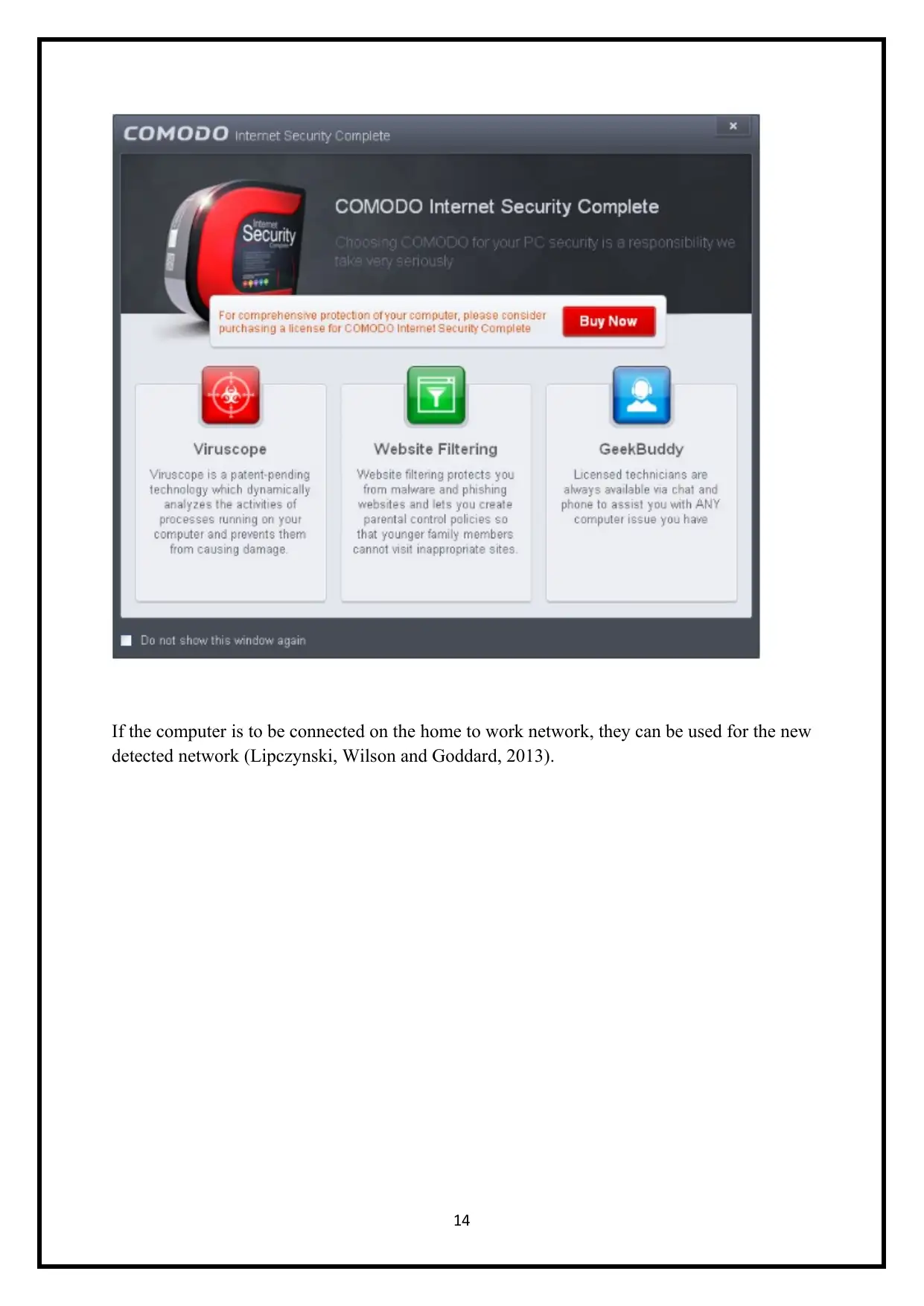
If the computer is to be connected on the home to work network, they can be used for the new
detected network (Lipczynski, Wilson and Goddard, 2013).
14
detected network (Lipczynski, Wilson and Goddard, 2013).
14
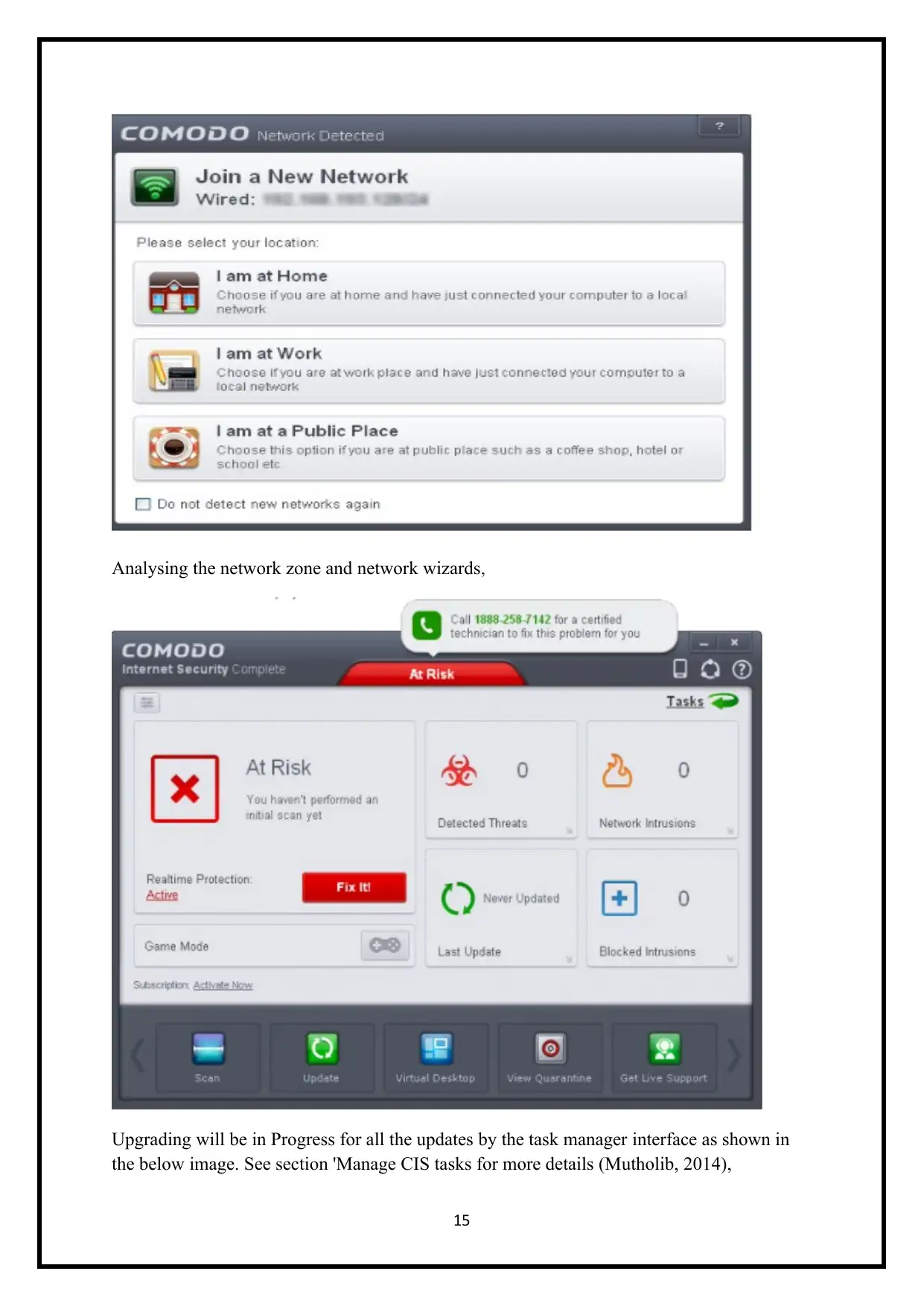
Analysing the network zone and network wizards,
Upgrading will be in Progress for all the updates by the task manager interface as shown in
the below image. See section 'Manage CIS tasks for more details (Mutholib, 2014),
15
Upgrading will be in Progress for all the updates by the task manager interface as shown in
the below image. See section 'Manage CIS tasks for more details (Mutholib, 2014),
15
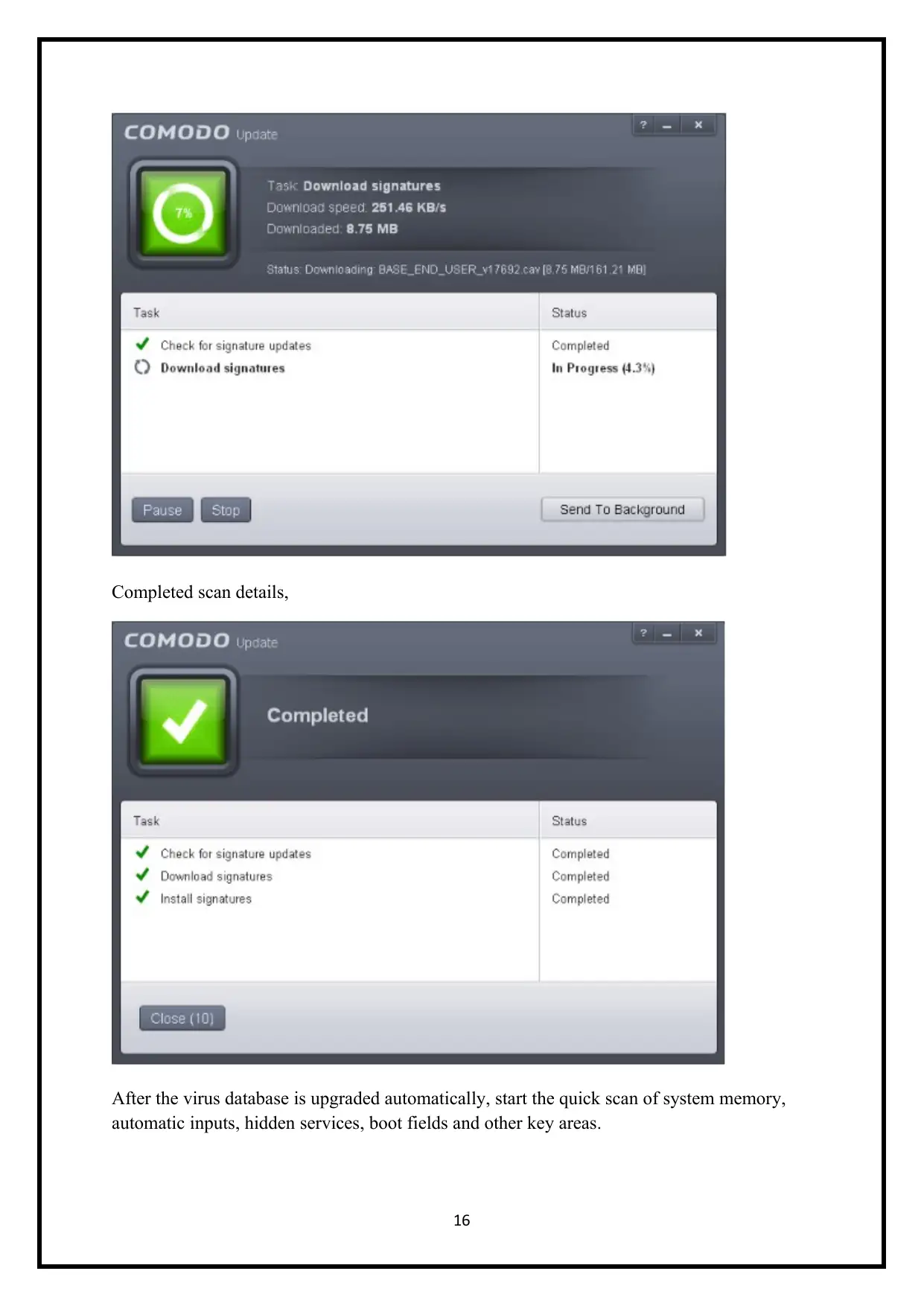
Completed scan details,
After the virus database is upgraded automatically, start the quick scan of system memory,
automatic inputs, hidden services, boot fields and other key areas.
16
After the virus database is upgraded automatically, start the quick scan of system memory,
automatic inputs, hidden services, boot fields and other key areas.
16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
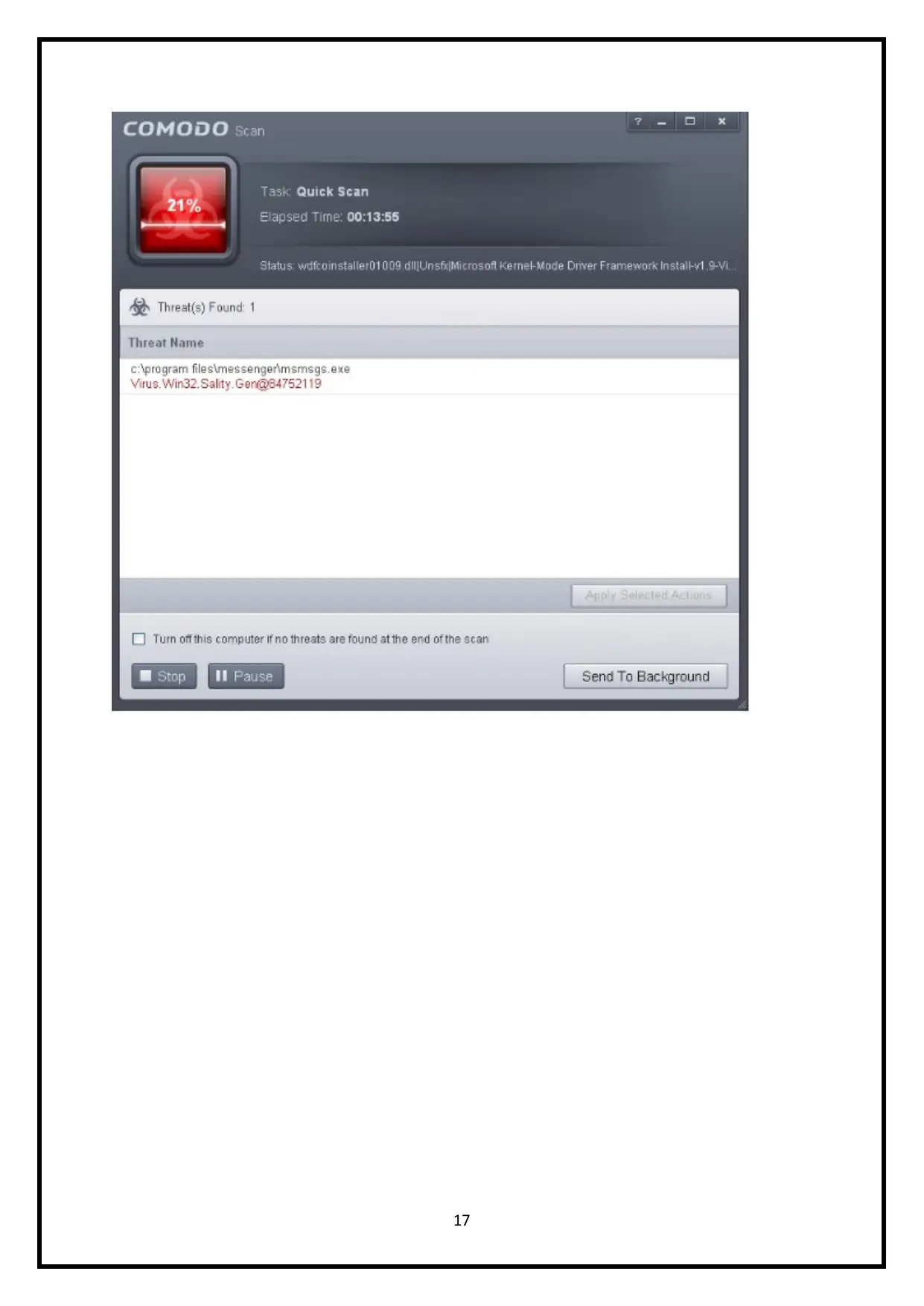
17
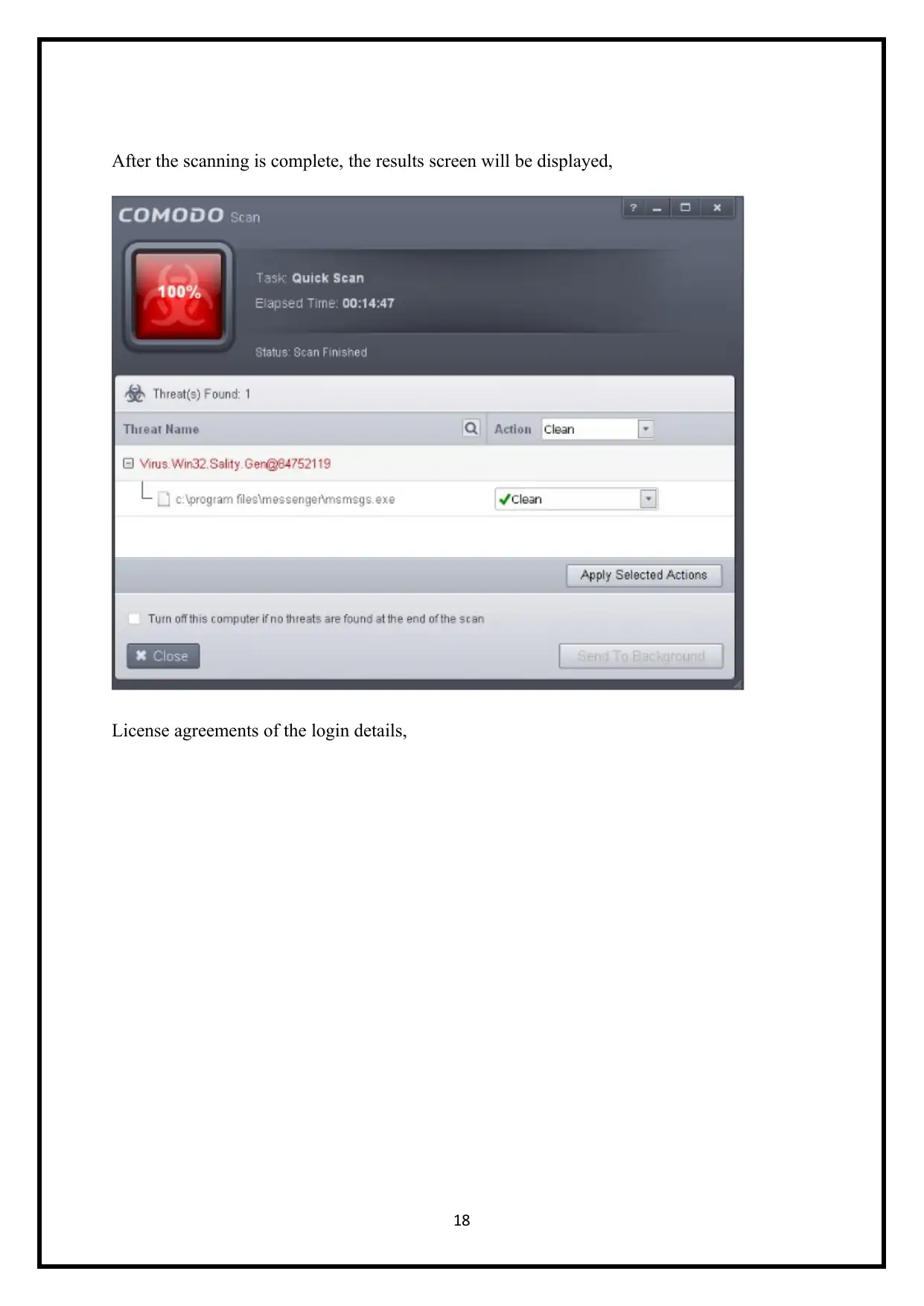
After the scanning is complete, the results screen will be displayed,
License agreements of the login details,
18
License agreements of the login details,
18
4. Develop information security awareness training
The building up of the antivirus for the data security, they can utilize the HIPS conduct of the
setting and determine on the ceaselessly screen the usefulness of the framework. It empowers
the procedures just as the pragmatic wellbeing principles are implemented. They can
pursueall those means that are incorporated for the normal client. Comodo Internet Safety
Ships are the default HIPS rules, which work for the largest amount of insurance with no
client mediation. For instance, HIPS consequently secures the PC complex records,
organizes, and transfers the keys to forestall unapproved changes by vindictive projects.
Propelled clients who are hoping to take an alluring handle of their security pointer rapidly
utilize the ground-breaking rules interface training system.
19
The building up of the antivirus for the data security, they can utilize the HIPS conduct of the
setting and determine on the ceaselessly screen the usefulness of the framework. It empowers
the procedures just as the pragmatic wellbeing principles are implemented. They can
pursueall those means that are incorporated for the normal client. Comodo Internet Safety
Ships are the default HIPS rules, which work for the largest amount of insurance with no
client mediation. For instance, HIPS consequently secures the PC complex records,
organizes, and transfers the keys to forestall unapproved changes by vindictive projects.
Propelled clients who are hoping to take an alluring handle of their security pointer rapidly
utilize the ground-breaking rules interface training system.
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
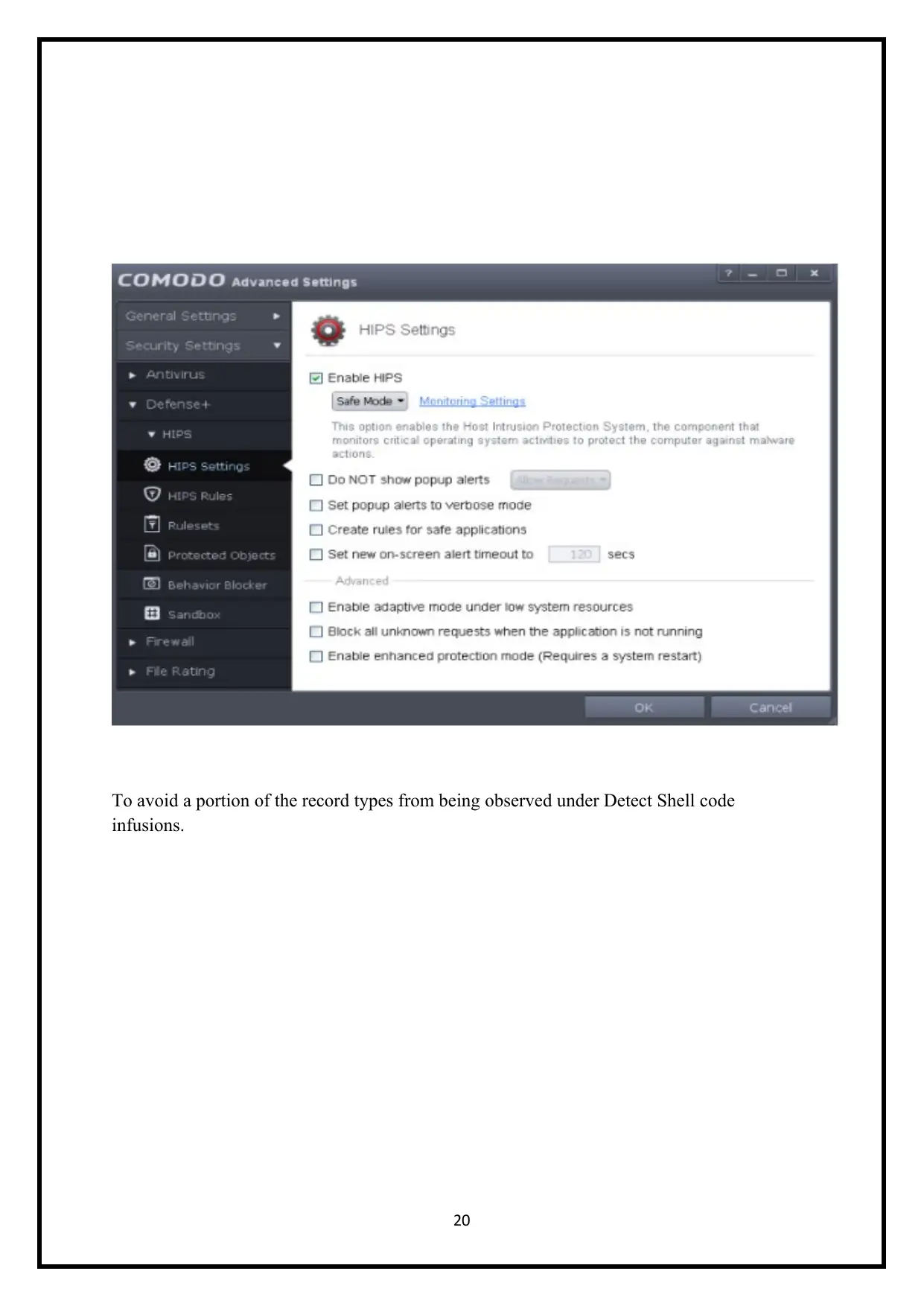
To avoid a portion of the record types from being observed under Detect Shell code
infusions.
20
infusions.
20
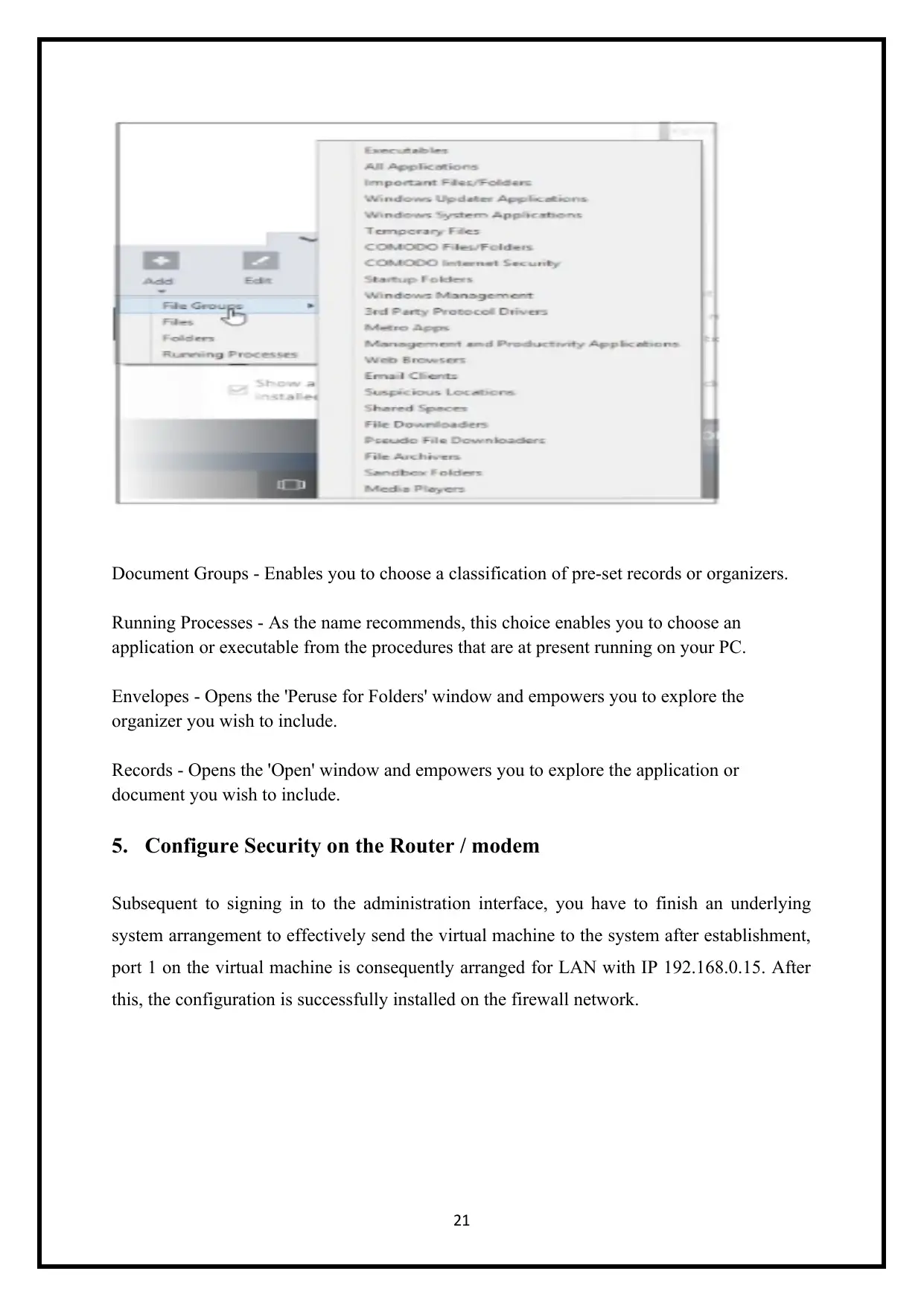
Document Groups - Enables you to choose a classification of pre-set records or organizers.
Running Processes - As the name recommends, this choice enables you to choose an
application or executable from the procedures that are at present running on your PC.
Envelopes - Opens the 'Peruse for Folders' window and empowers you to explore the
organizer you wish to include.
Records - Opens the 'Open' window and empowers you to explore the application or
document you wish to include.
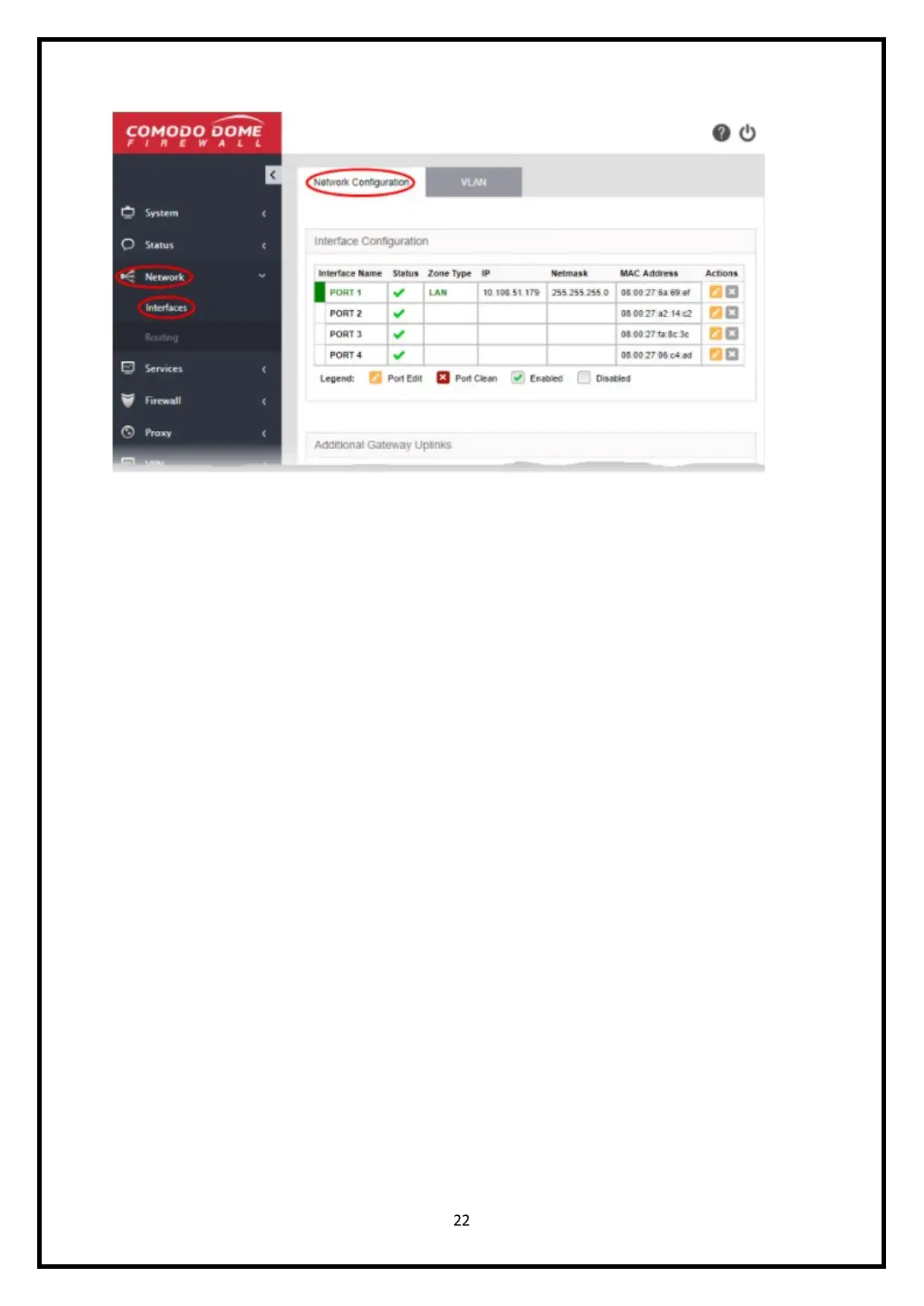
5. Configure Security on the Router / modem
Subsequent to signing in to the administration interface, you have to finish an underlying
system arrangement to effectively send the virtual machine to the system after establishment,
port 1 on the virtual machine is consequently arranged for LAN with IP 192.168.0.15. After
this, the configuration is successfully installed on the firewall network.
21
Running Processes - As the name recommends, this choice enables you to choose an
application or executable from the procedures that are at present running on your PC.
Envelopes - Opens the 'Peruse for Folders' window and empowers you to explore the
organizer you wish to include.
Records - Opens the 'Open' window and empowers you to explore the application or
document you wish to include.
5. Configure Security on the Router / modem
Subsequent to signing in to the administration interface, you have to finish an underlying
system arrangement to effectively send the virtual machine to the system after establishment,
port 1 on the virtual machine is consequently arranged for LAN with IP 192.168.0.15. After
this, the configuration is successfully installed on the firewall network.
21
22
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
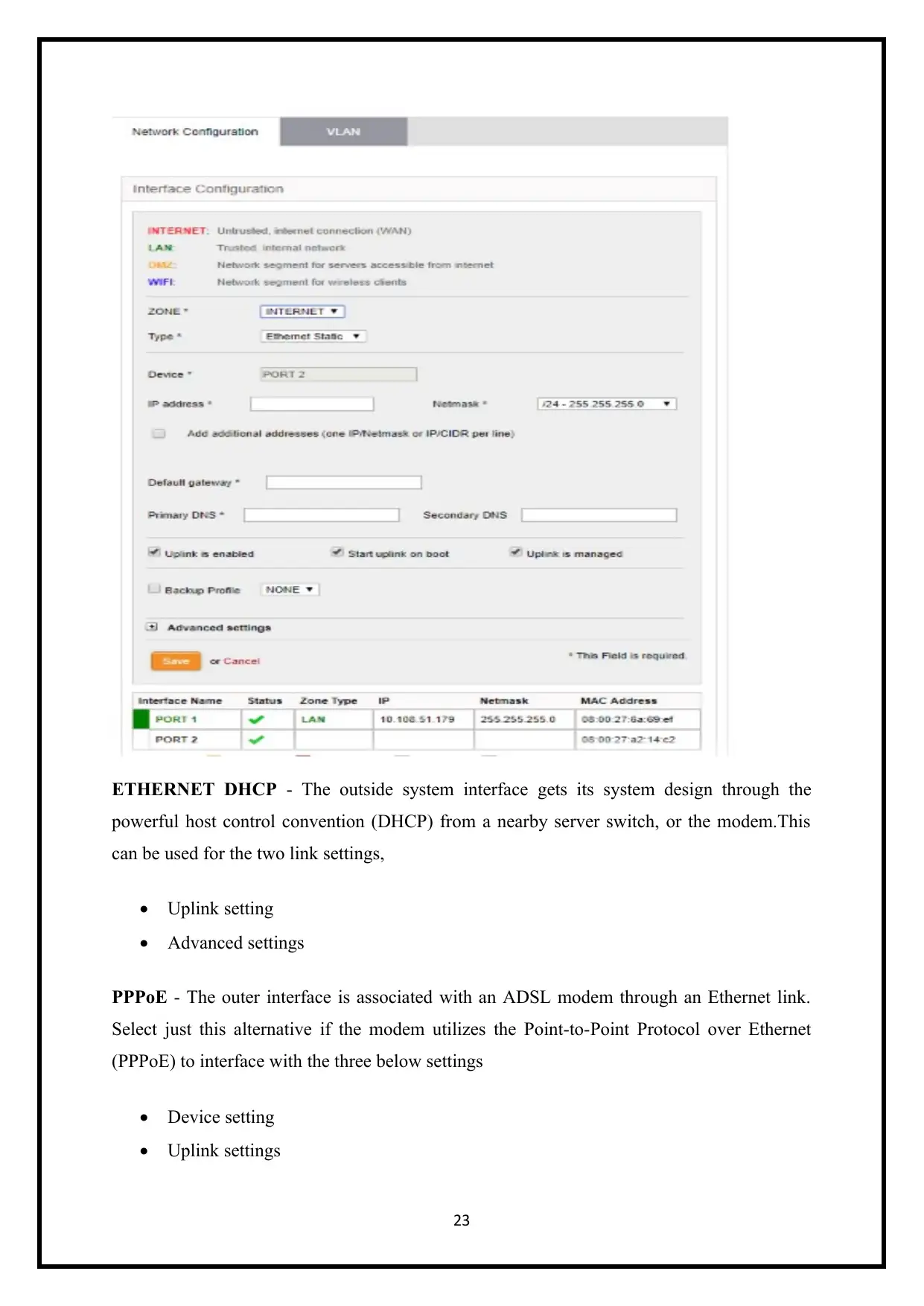
ETHERNET DHCP - The outside system interface gets its system design through the
powerful host control convention (DHCP) from a nearby server switch, or the modem.This
can be used for the two link settings,
Uplink setting
Advanced settings
PPPoE - The outer interface is associated with an ADSL modem through an Ethernet link.
Select just this alternative if the modem utilizes the Point-to-Point Protocol over Ethernet
(PPPoE) to interface with the three below settings
Device setting
Uplink settings
23
powerful host control convention (DHCP) from a nearby server switch, or the modem.This
can be used for the two link settings,
Uplink setting
Advanced settings
PPPoE - The outer interface is associated with an ADSL modem through an Ethernet link.
Select just this alternative if the modem utilizes the Point-to-Point Protocol over Ethernet
(PPPoE) to interface with the three below settings
Device setting
Uplink settings
23
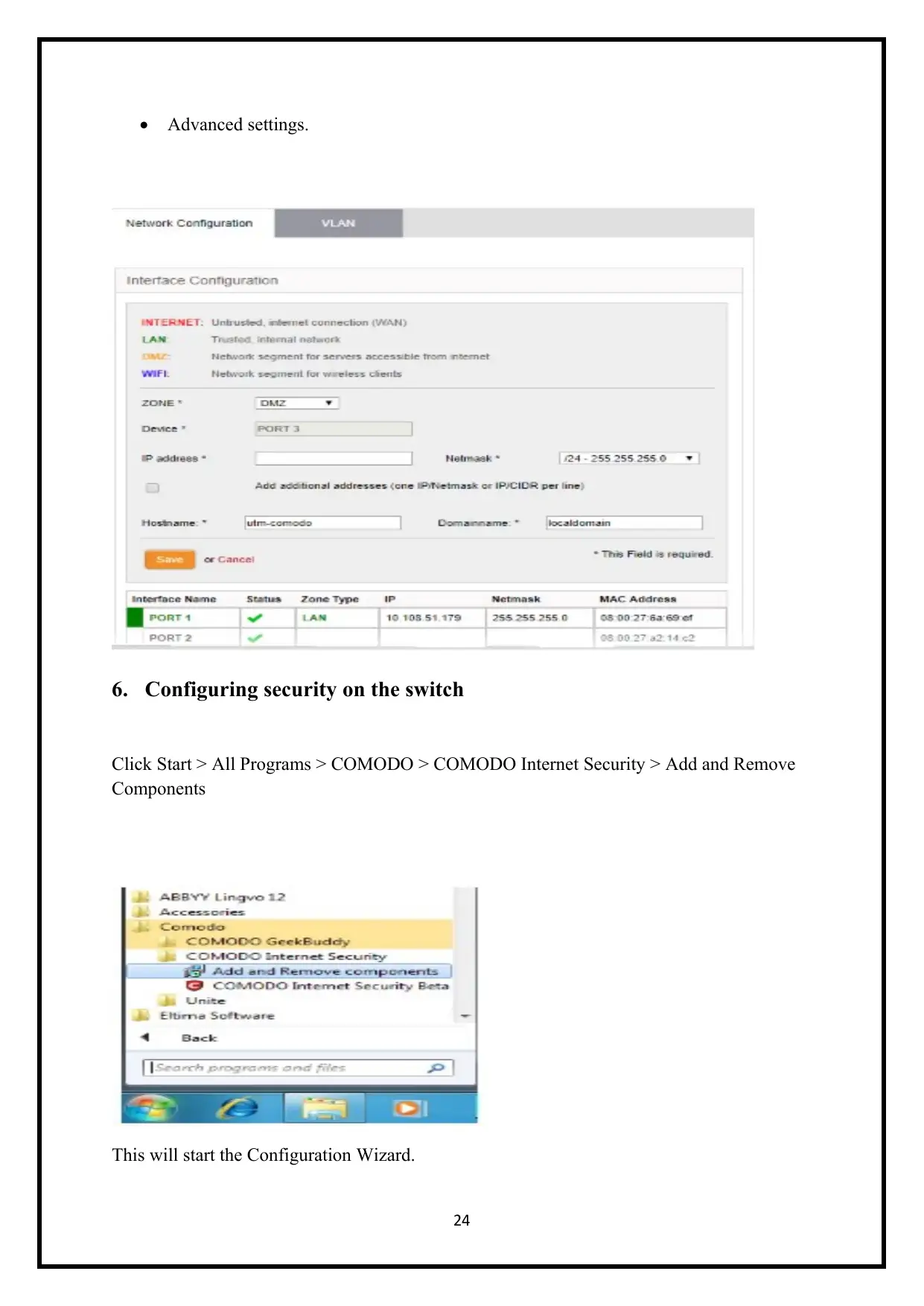
Advanced settings.
6. Configuring security on the switch
Click Start > All Programs > COMODO > COMODO Internet Security > Add and Remove
Components
This will start the Configuration Wizard.
24
6. Configuring security on the switch
Click Start > All Programs > COMODO > COMODO Internet Security > Add and Remove
Components
This will start the Configuration Wizard.
24
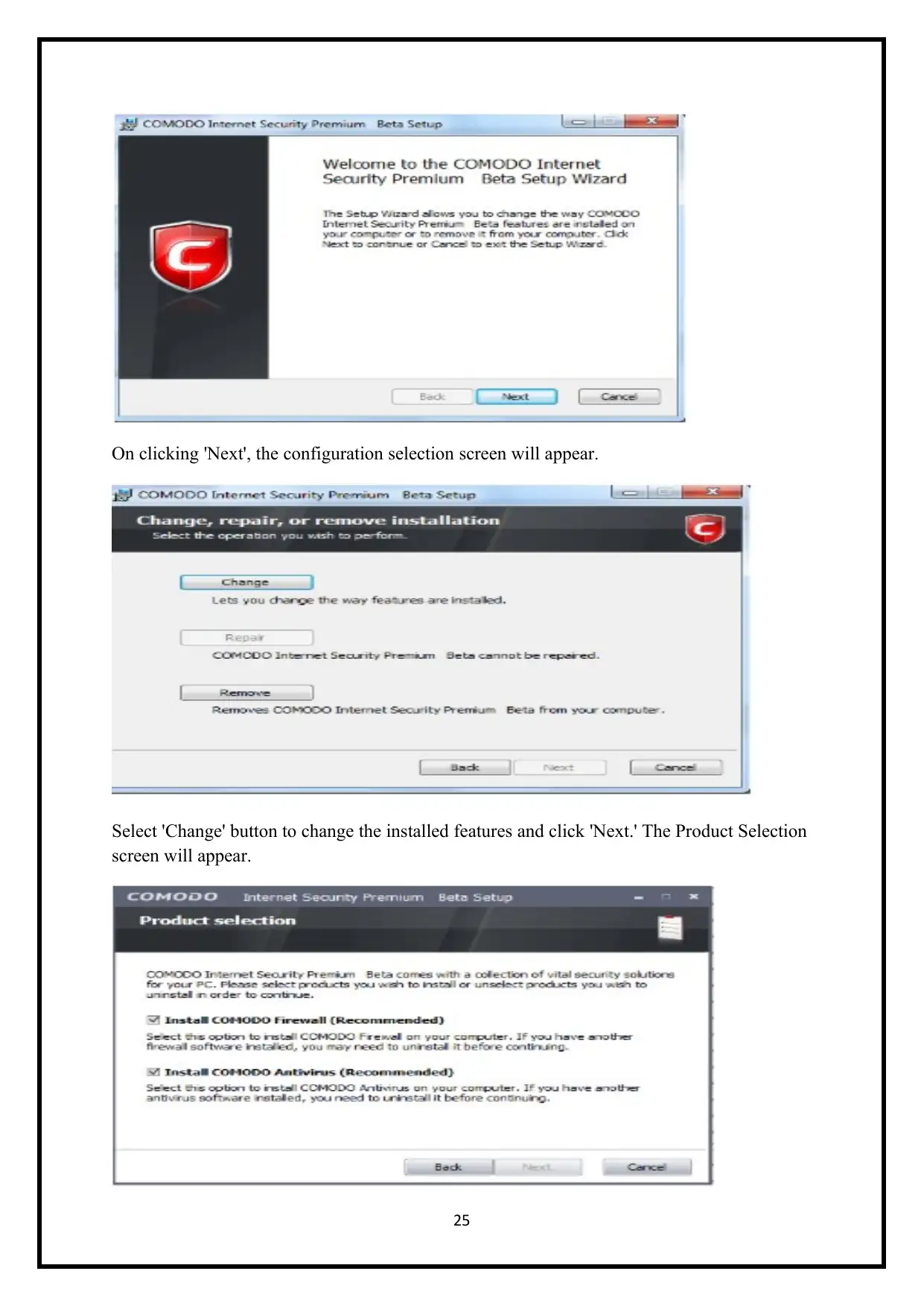
On clicking 'Next', the configuration selection screen will appear.
Select 'Change' button to change the installed features and click 'Next.' The Product Selection
screen will appear.
25
Select 'Change' button to change the installed features and click 'Next.' The Product Selection
screen will appear.
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
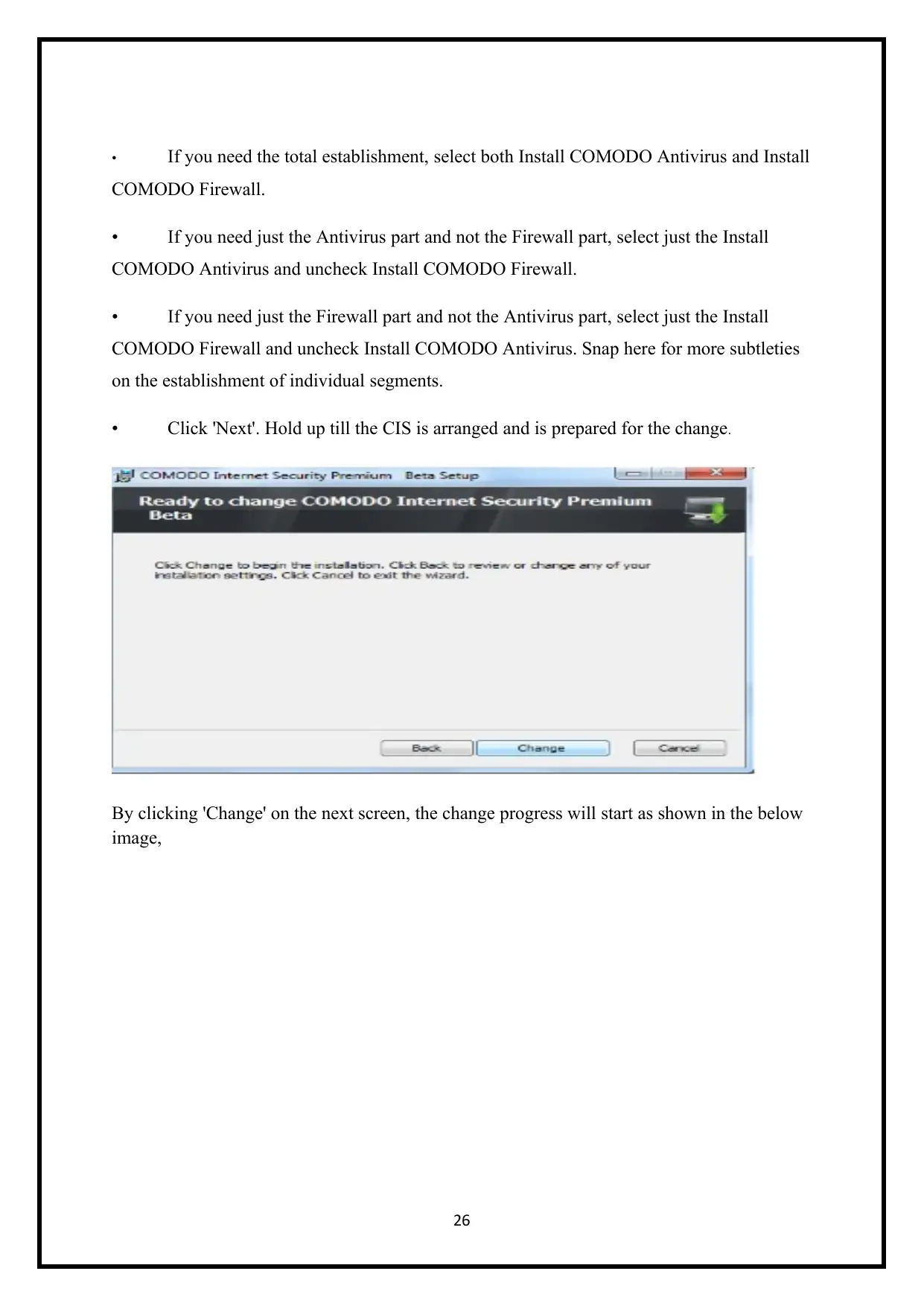
• If you need the total establishment, select both Install COMODO Antivirus and Install
COMODO Firewall.
• If you need just the Antivirus part and not the Firewall part, select just the Install
COMODO Antivirus and uncheck Install COMODO Firewall.
• If you need just the Firewall part and not the Antivirus part, select just the Install
COMODO Firewall and uncheck Install COMODO Antivirus. Snap here for more subtleties
on the establishment of individual segments.
• Click 'Next'. Hold up till the CIS is arranged and is prepared for the change.
By clicking 'Change' on the next screen, the change progress will start as shown in the below
image,
26
COMODO Firewall.
• If you need just the Antivirus part and not the Firewall part, select just the Install
COMODO Antivirus and uncheck Install COMODO Firewall.
• If you need just the Firewall part and not the Antivirus part, select just the Install
COMODO Firewall and uncheck Install COMODO Antivirus. Snap here for more subtleties
on the establishment of individual segments.
• Click 'Next'. Hold up till the CIS is arranged and is prepared for the change.
By clicking 'Change' on the next screen, the change progress will start as shown in the below
image,
26
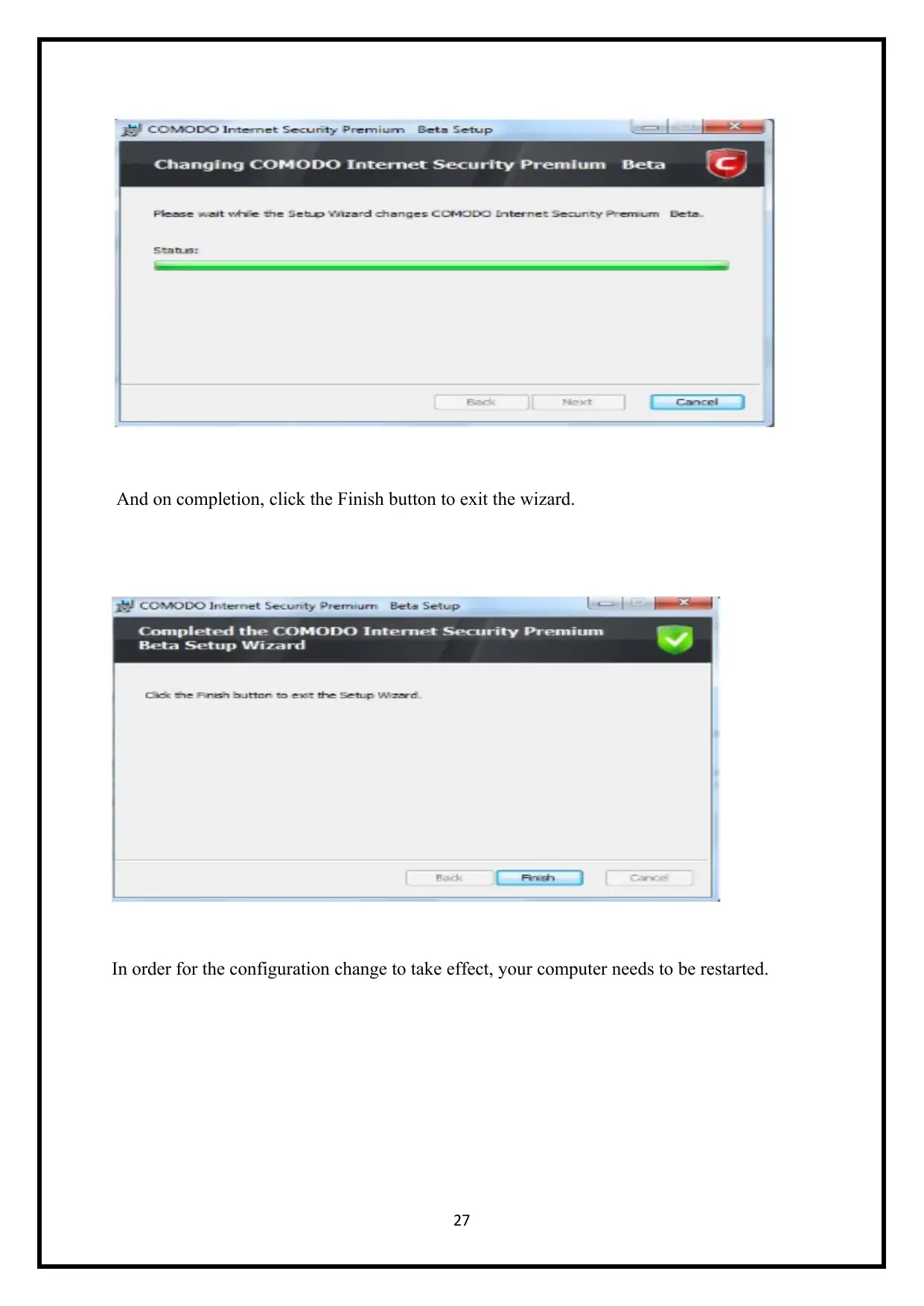
And on completion, click the Finish button to exit the wizard.
In order for the configuration change to take effect, your computer needs to be restarted.
27
In order for the configuration change to take effect, your computer needs to be restarted.
27
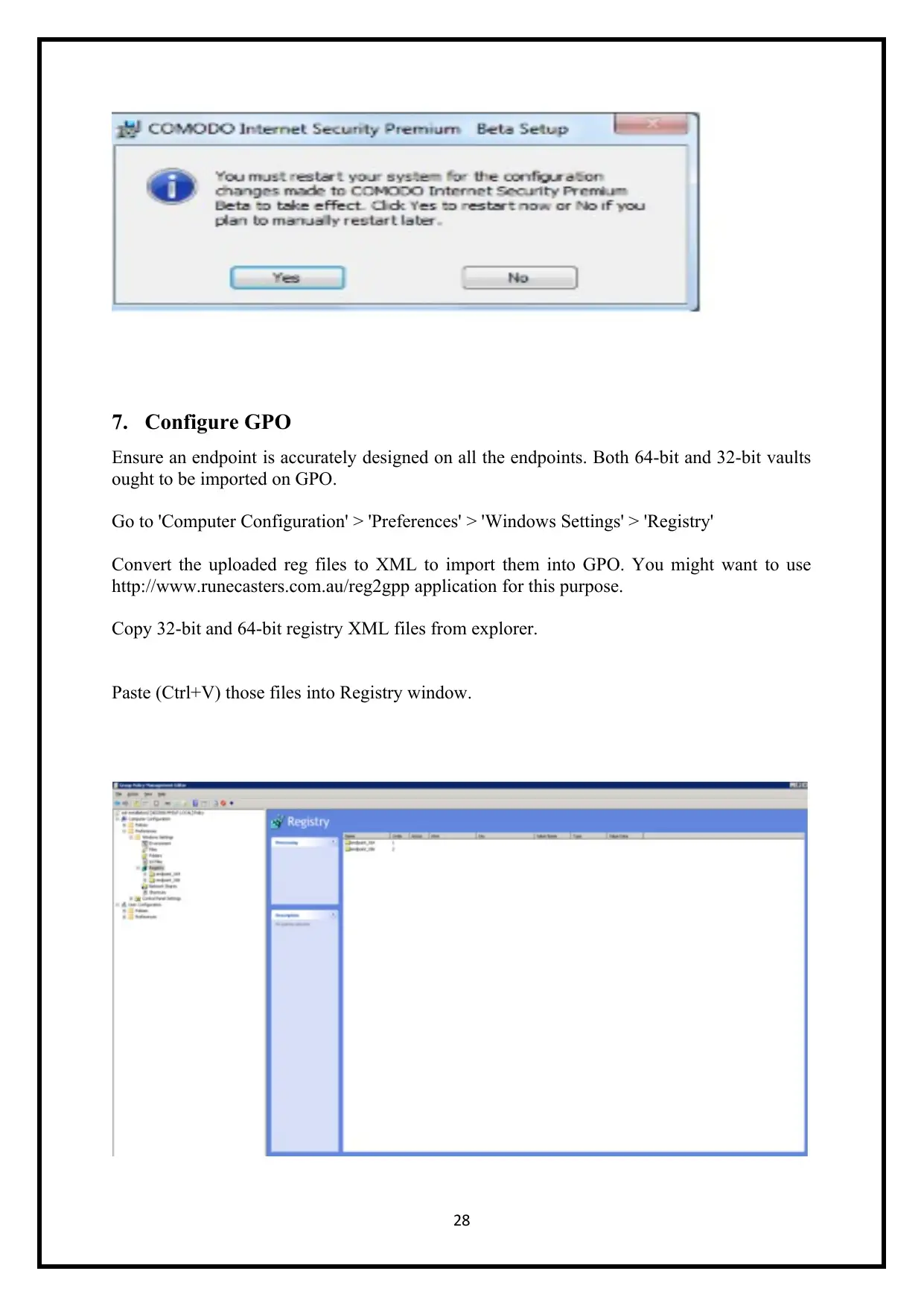
7. Configure GPO
Ensure an endpoint is accurately designed on all the endpoints. Both 64-bit and 32-bit vaults
ought to be imported on GPO.
Go to 'Computer Configuration' > 'Preferences' > 'Windows Settings' > 'Registry'
Convert the uploaded reg files to XML to import them into GPO. You might want to use
http://www.runecasters.com.au/reg2gpp application for this purpose.
Copy 32-bit and 64-bit registry XML files from explorer.
Paste (Ctrl+V) those files into Registry window.
28
Ensure an endpoint is accurately designed on all the endpoints. Both 64-bit and 32-bit vaults
ought to be imported on GPO.
Go to 'Computer Configuration' > 'Preferences' > 'Windows Settings' > 'Registry'
Convert the uploaded reg files to XML to import them into GPO. You might want to use
http://www.runecasters.com.au/reg2gpp application for this purpose.
Copy 32-bit and 64-bit registry XML files from explorer.
Paste (Ctrl+V) those files into Registry window.
28
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
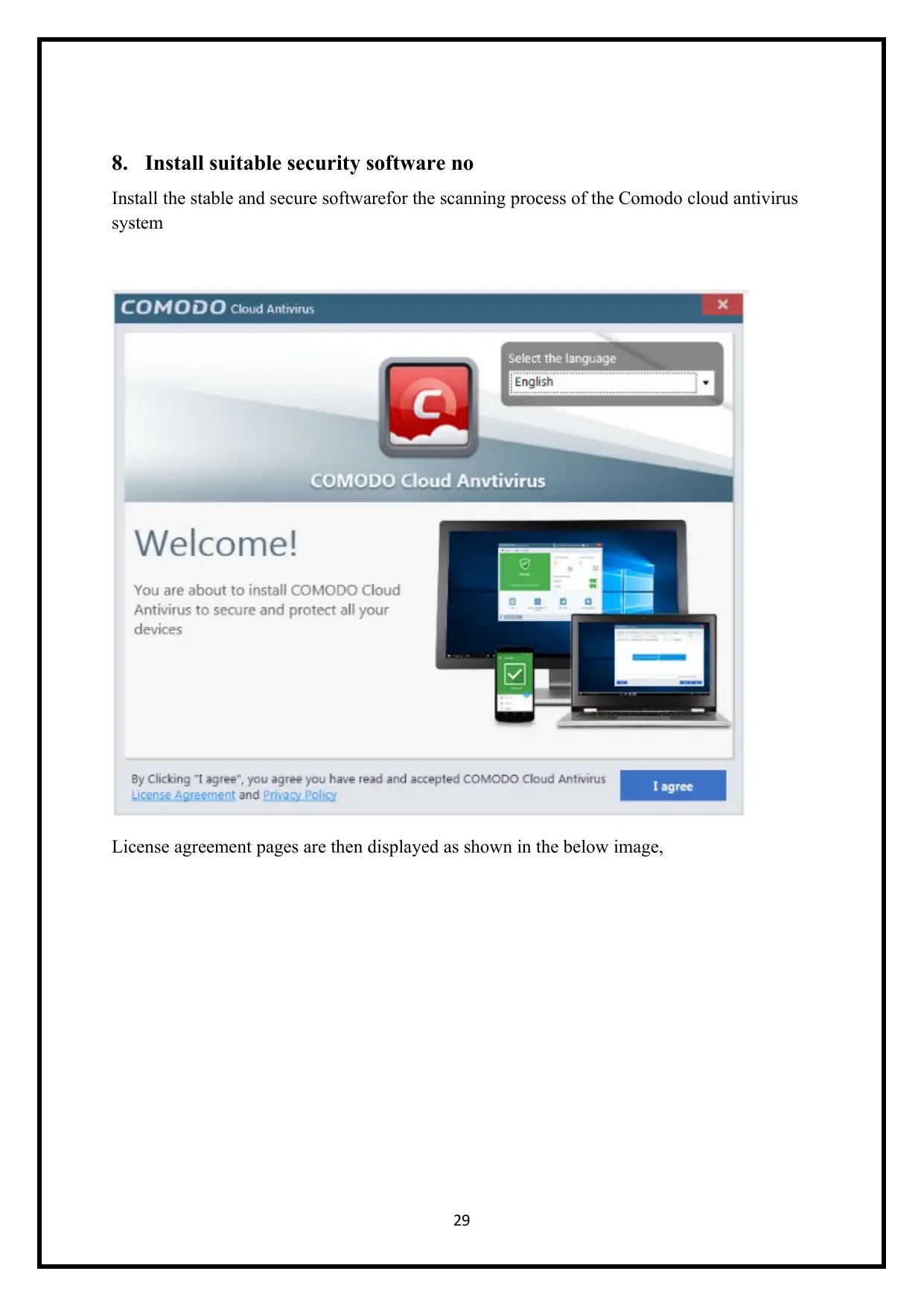
8. Install suitable security software no
Install the stable and secure softwarefor the scanning process of the Comodo cloud antivirus
system
License agreement pages are then displayed as shown in the below image,
29
Install the stable and secure softwarefor the scanning process of the Comodo cloud antivirus
system
License agreement pages are then displayed as shown in the below image,
29
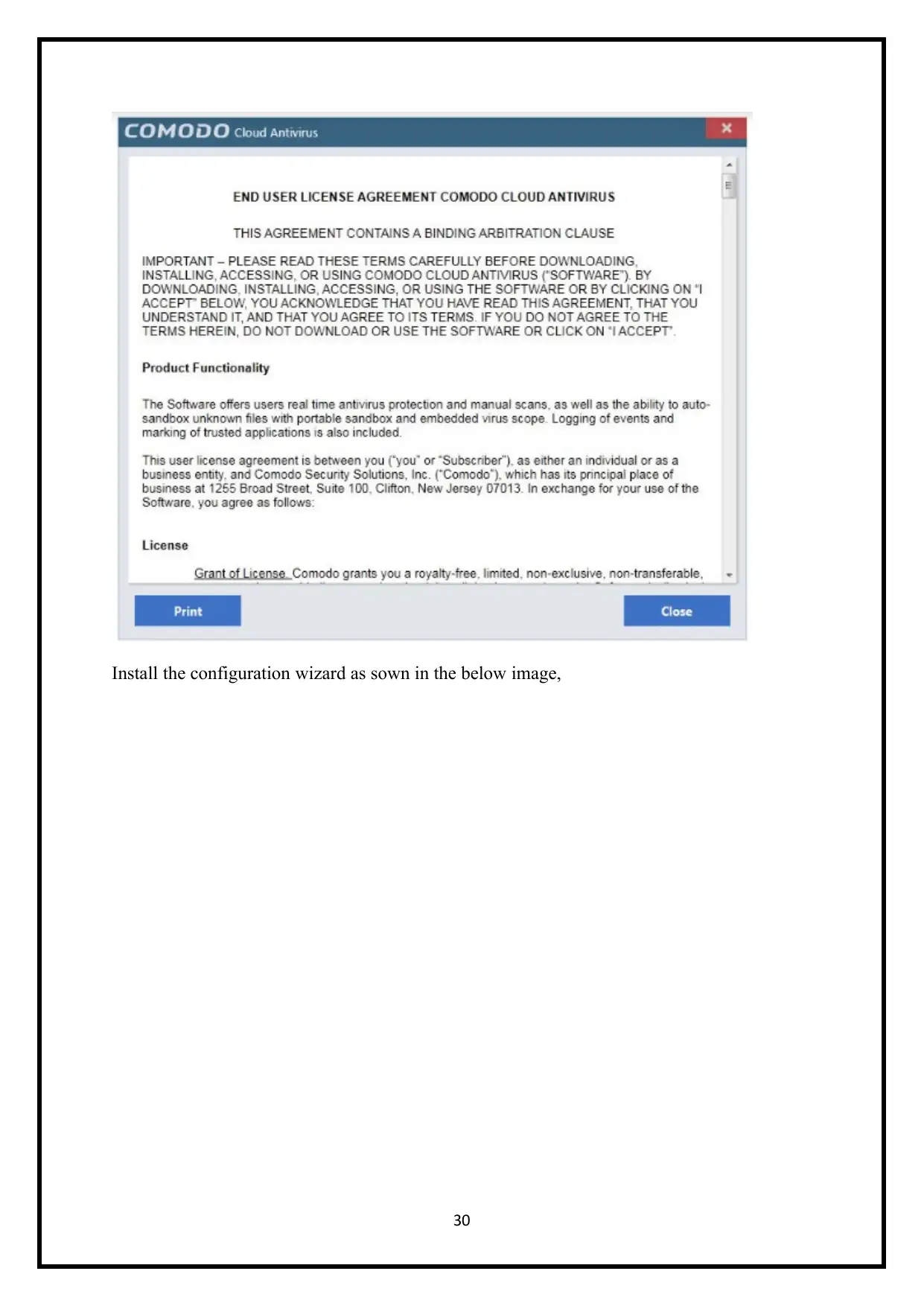
Install the configuration wizard as sown in the below image,
30
30
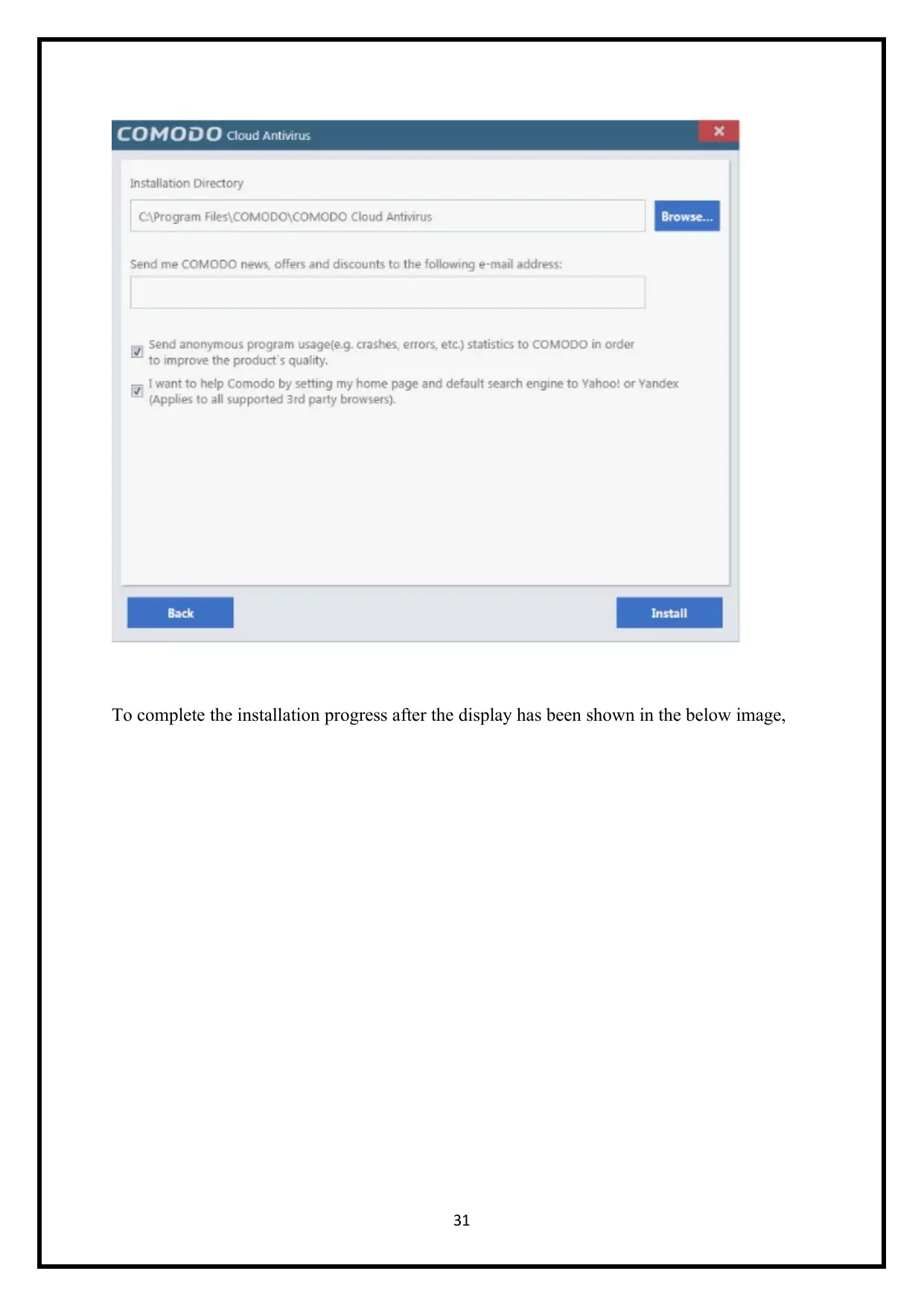
To complete the installation progress after the display has been shown in the below image,
31
31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Display all the successful messages,
32
32
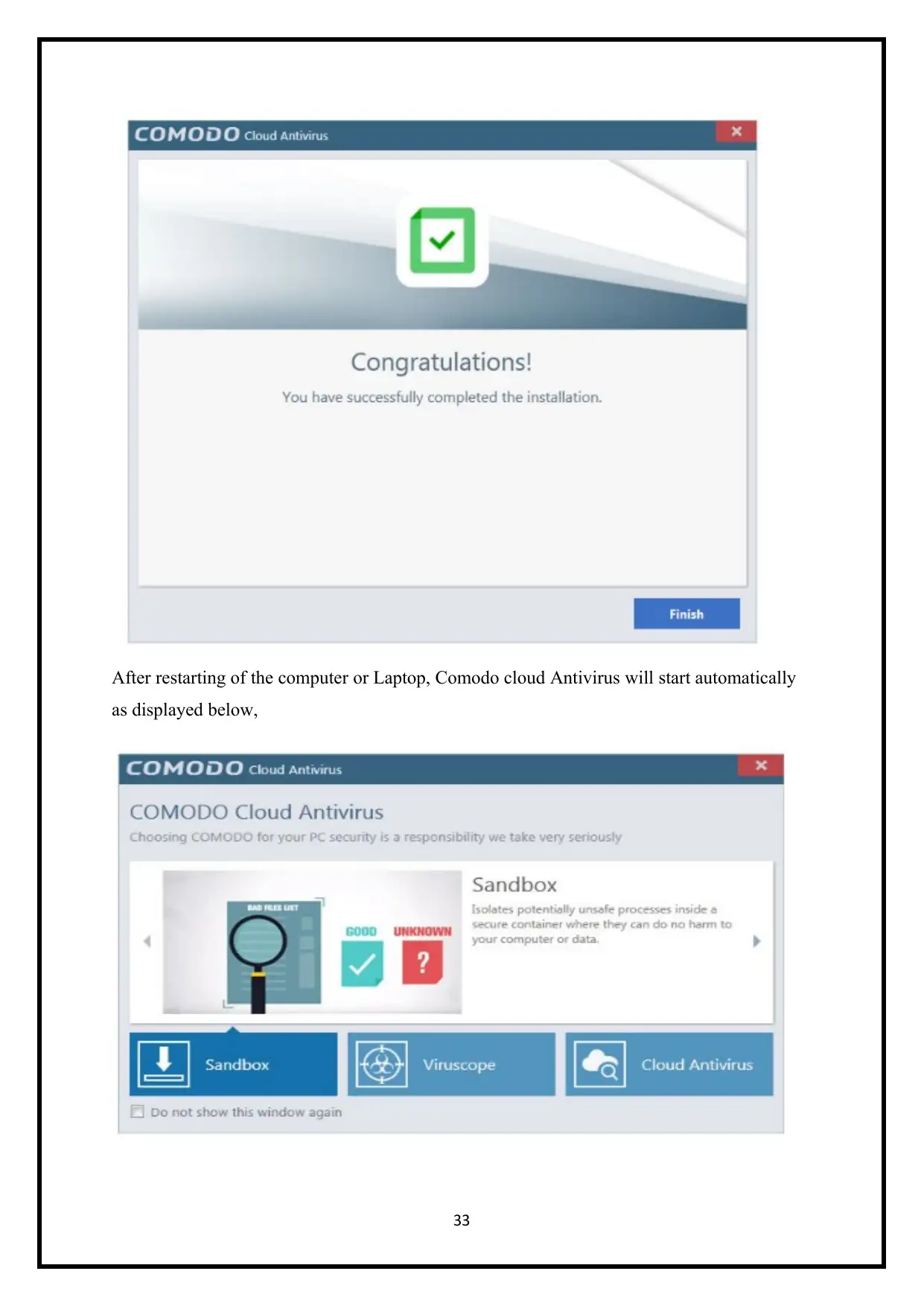
After restarting of the computer or Laptop, Comodo cloud Antivirus will start automatically
as displayed below,
33
as displayed below,
33
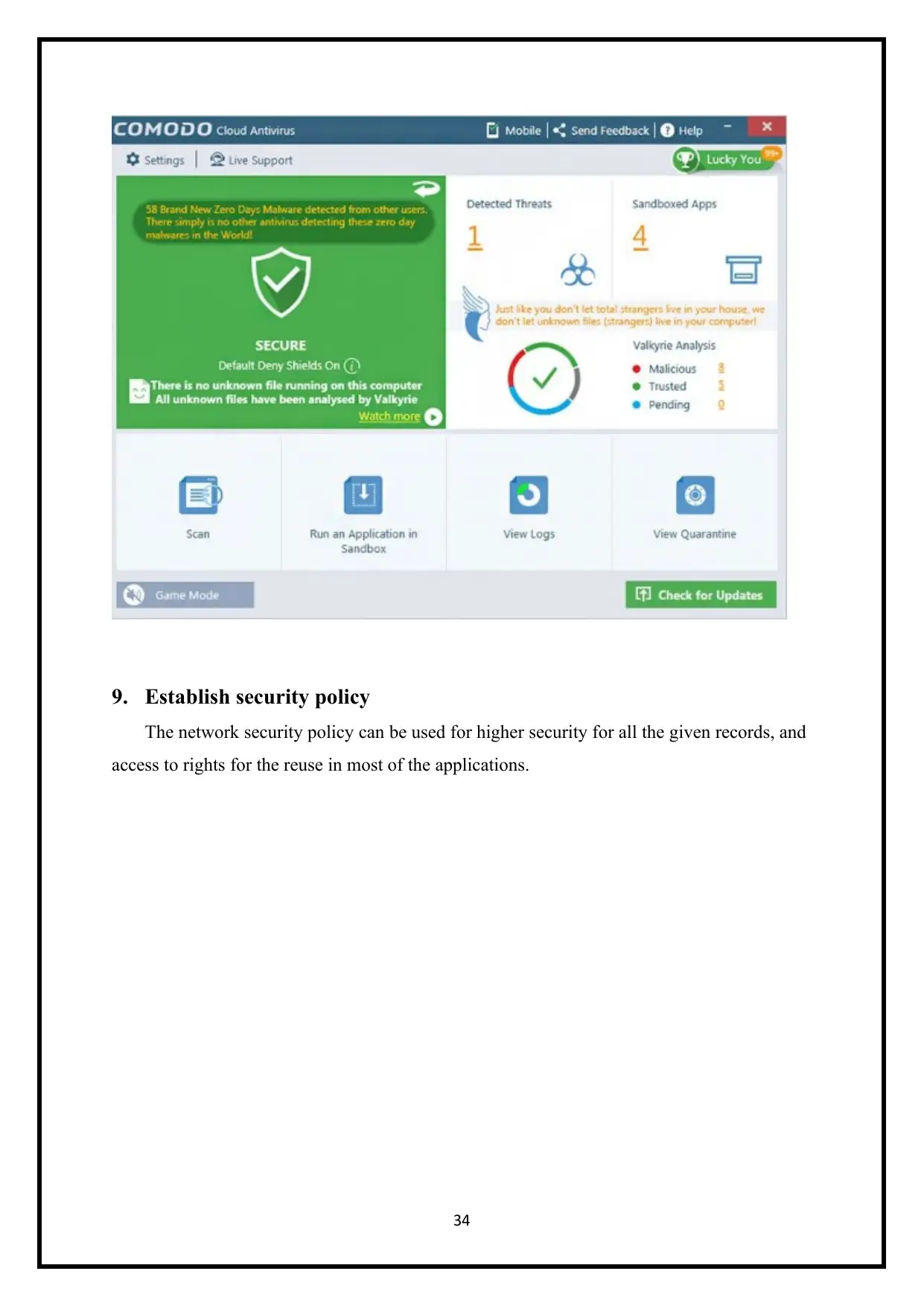
9. Establish security policy
The network security policy can be used for higher security for all the given records, and
access to rights for the reuse in most of the applications.
34
The network security policy can be used for higher security for all the given records, and
access to rights for the reuse in most of the applications.
34
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
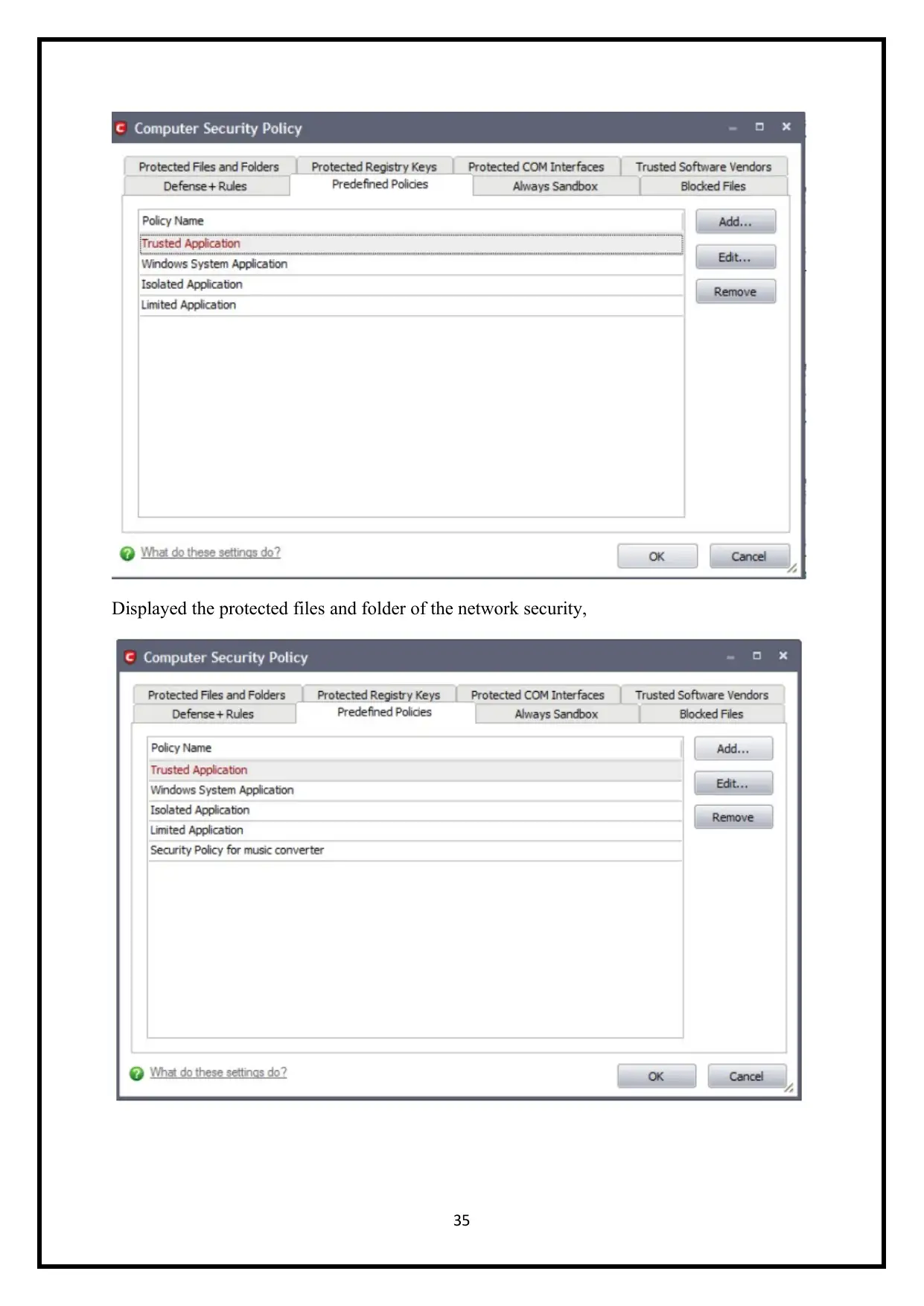
Displayed the protected files and folder of the network security,
35
35
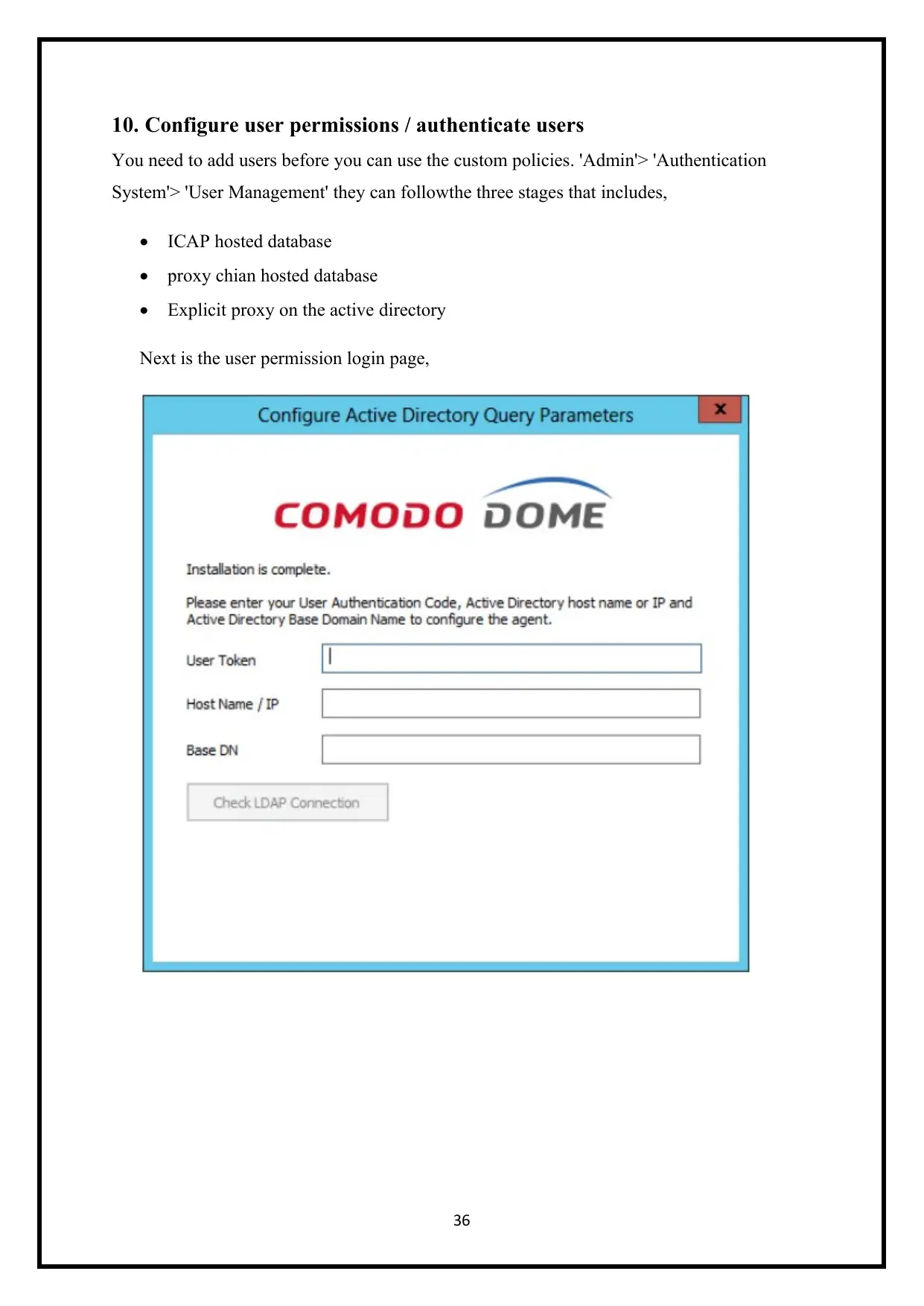
10. Configure user permissions / authenticate users
You need to add users before you can use the custom policies. 'Admin'> 'Authentication
System'> 'User Management' they can followthe three stages that includes,
ICAP hosted database
proxy chian hosted database
Explicit proxy on the active directory
Next is the user permission login page,
36
You need to add users before you can use the custom policies. 'Admin'> 'Authentication
System'> 'User Management' they can followthe three stages that includes,
ICAP hosted database
proxy chian hosted database
Explicit proxy on the active directory
Next is the user permission login page,
36
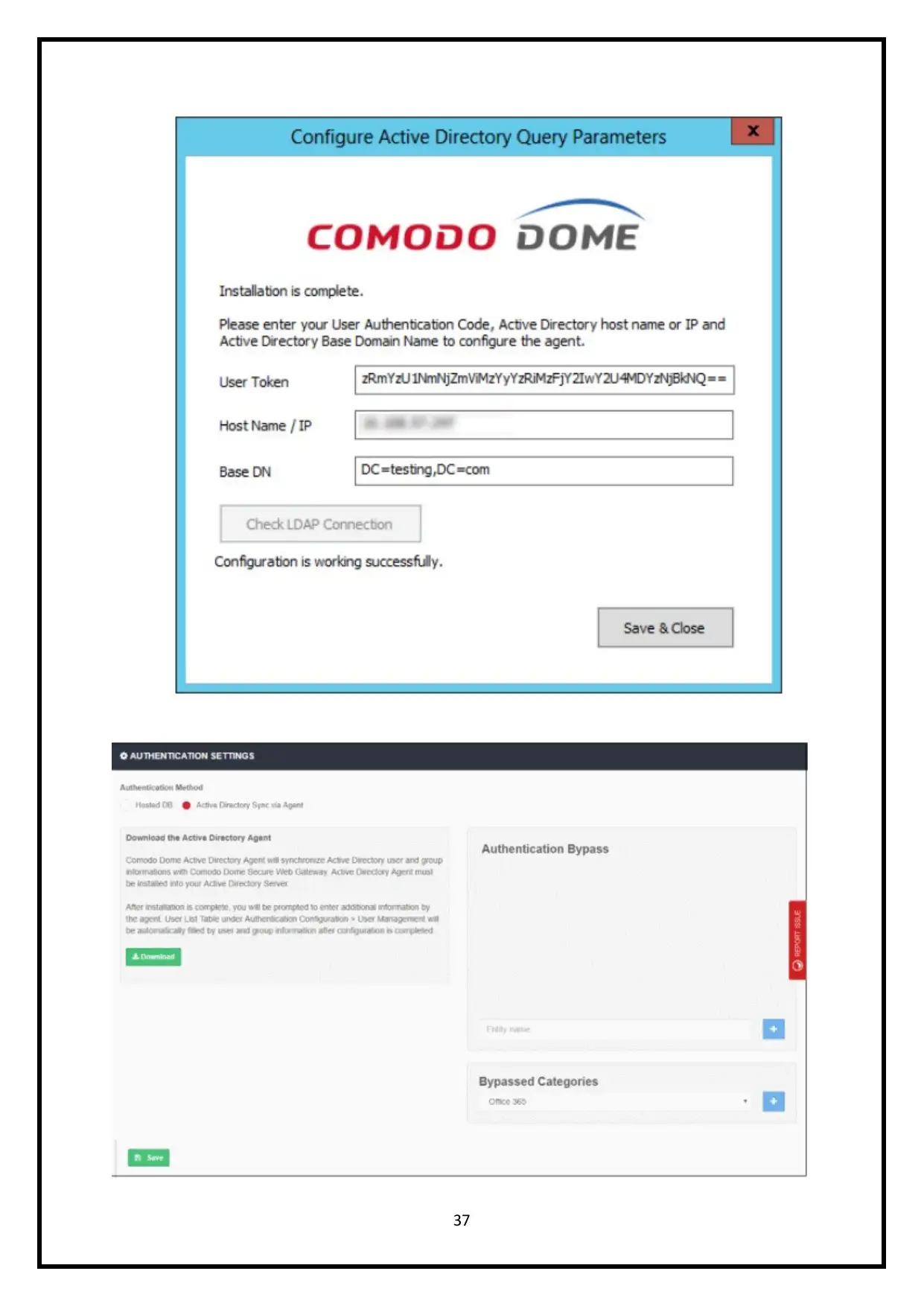
37
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
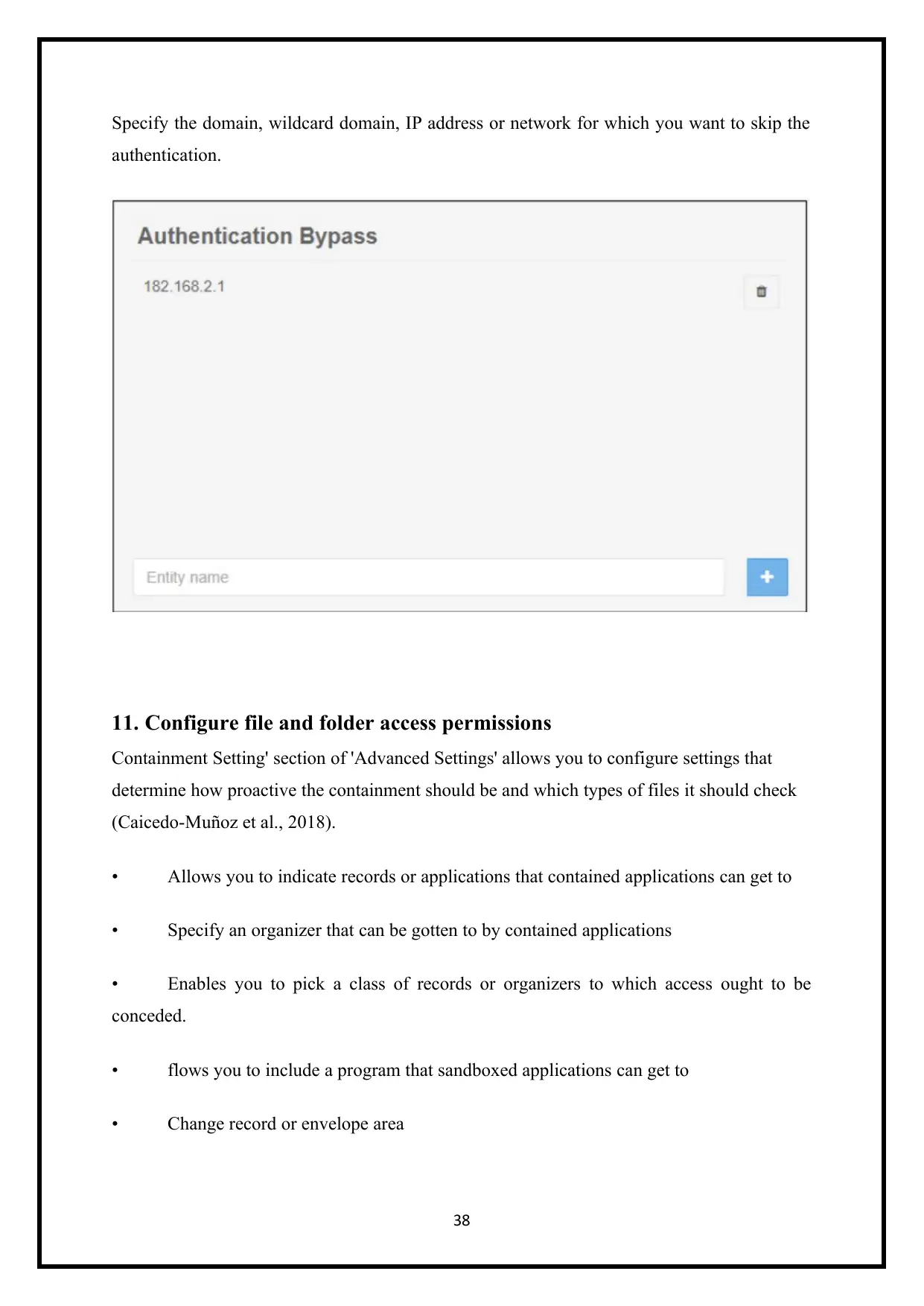
Specify the domain, wildcard domain, IP address or network for which you want to skip the
authentication.
11. Configure file and folder access permissions
Containment Setting' section of 'Advanced Settings' allows you to configure settings that
determine how proactive the containment should be and which types of files it should check
(Caicedo-Muñoz et al., 2018).
• Allows you to indicate records or applications that contained applications can get to
• Specify an organizer that can be gotten to by contained applications
• Enables you to pick a class of records or organizers to which access ought to be
conceded.
• flows you to include a program that sandboxed applications can get to
• Change record or envelope area
38
authentication.
11. Configure file and folder access permissions
Containment Setting' section of 'Advanced Settings' allows you to configure settings that
determine how proactive the containment should be and which types of files it should check
(Caicedo-Muñoz et al., 2018).
• Allows you to indicate records or applications that contained applications can get to
• Specify an organizer that can be gotten to by contained applications
• Enables you to pick a class of records or organizers to which access ought to be
conceded.
• flows you to include a program that sandboxed applications can get to
• Change record or envelope area
38
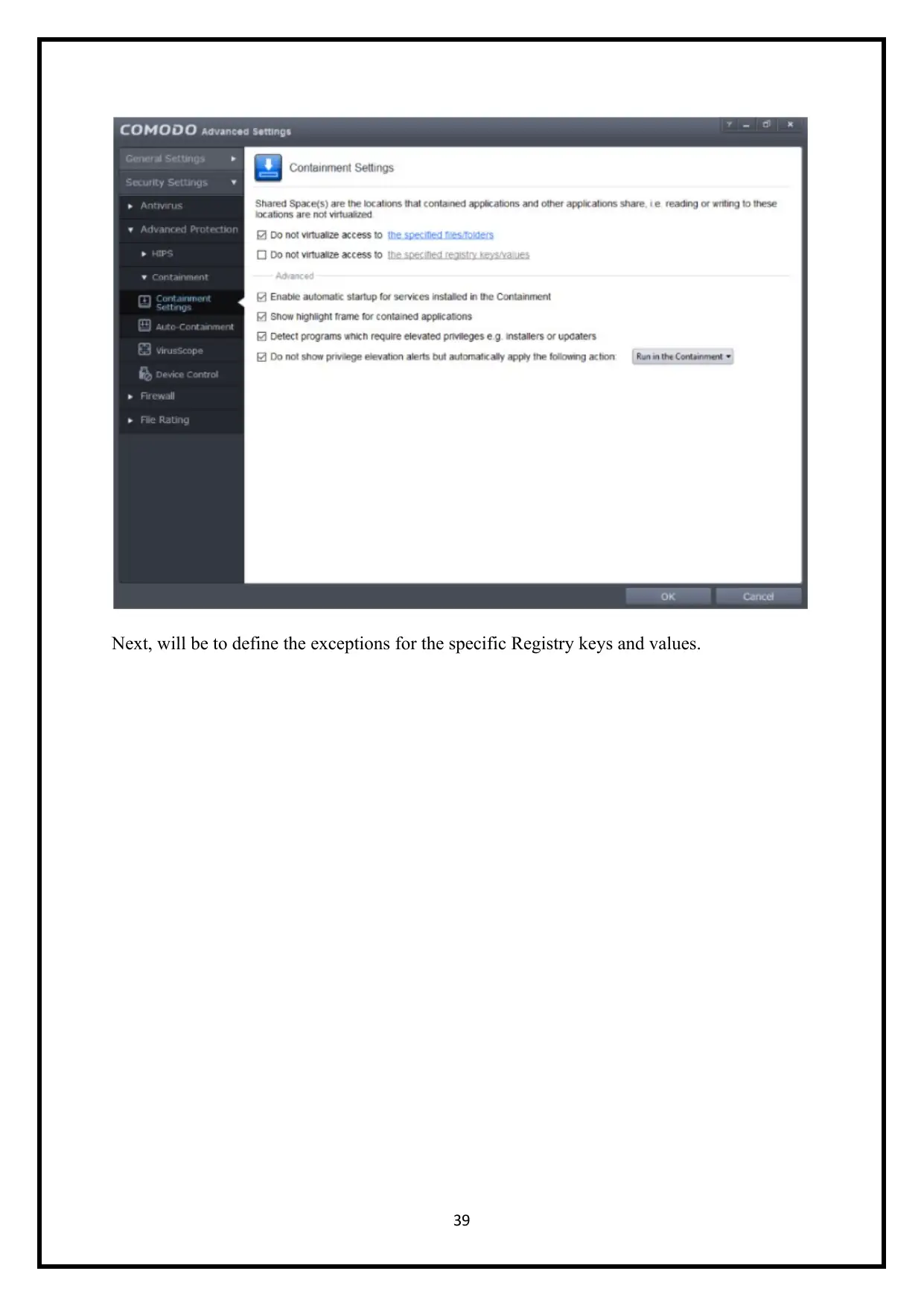
Next, will be to define the exceptions for the specific Registry keys and values.
39
39
Search the files or folder sandbox,
40
40
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
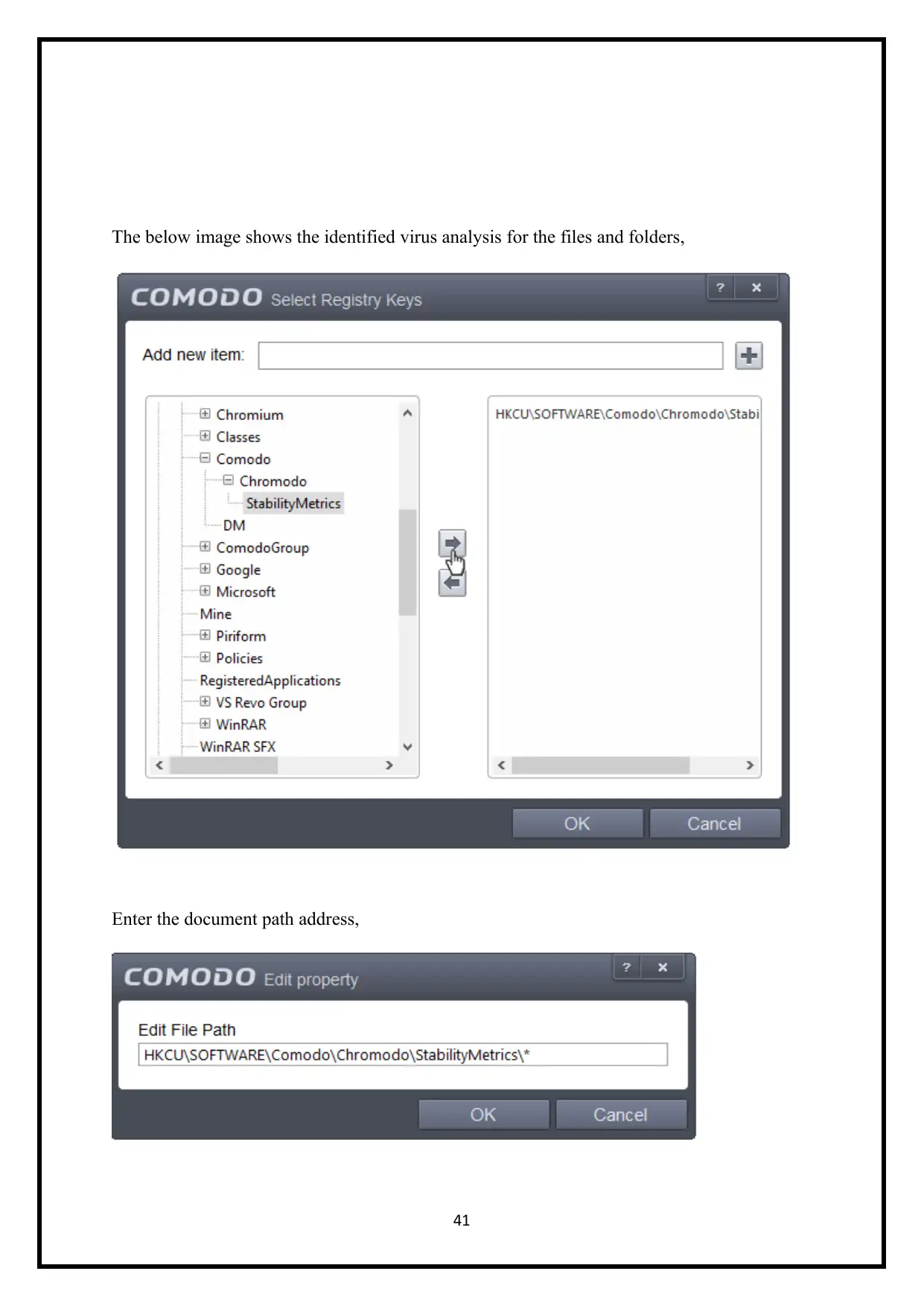
The below image shows the identified virus analysis for the files and folders,
Enter the document path address,
41
Enter the document path address,
41
Display the reports,
Analysing and displaying the virus issues,
42
Analysing and displaying the virus issues,
42
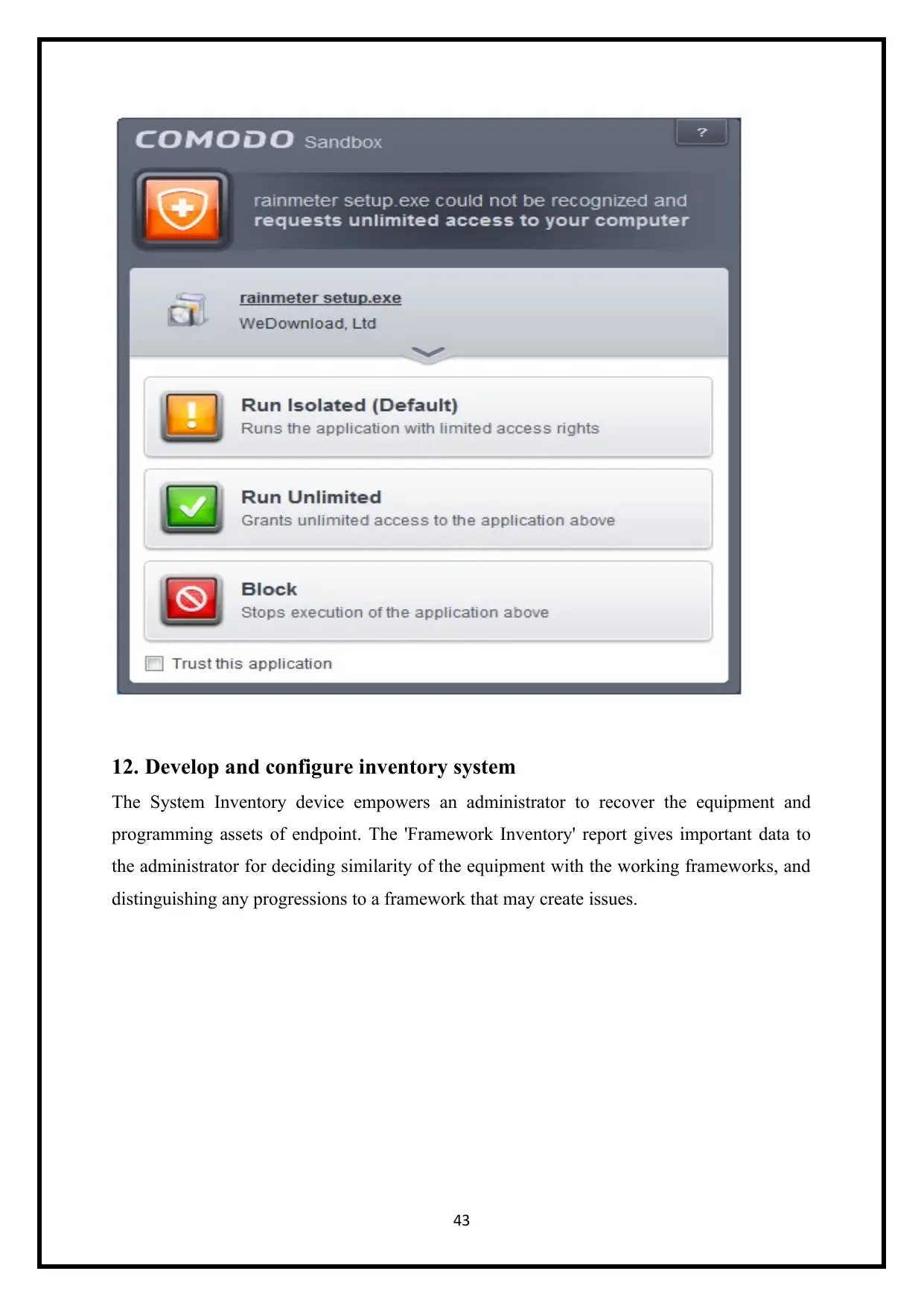
12. Develop and configure inventory system
The System Inventory device empowers an administrator to recover the equipment and
programming assets of endpoint. The 'Framework Inventory' report gives important data to
the administrator for deciding similarity of the equipment with the working frameworks, and
distinguishing any progressions to a framework that may create issues.
43
The System Inventory device empowers an administrator to recover the equipment and
programming assets of endpoint. The 'Framework Inventory' report gives important data to
the administrator for deciding similarity of the equipment with the working frameworks, and
distinguishing any progressions to a framework that may create issues.
43
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
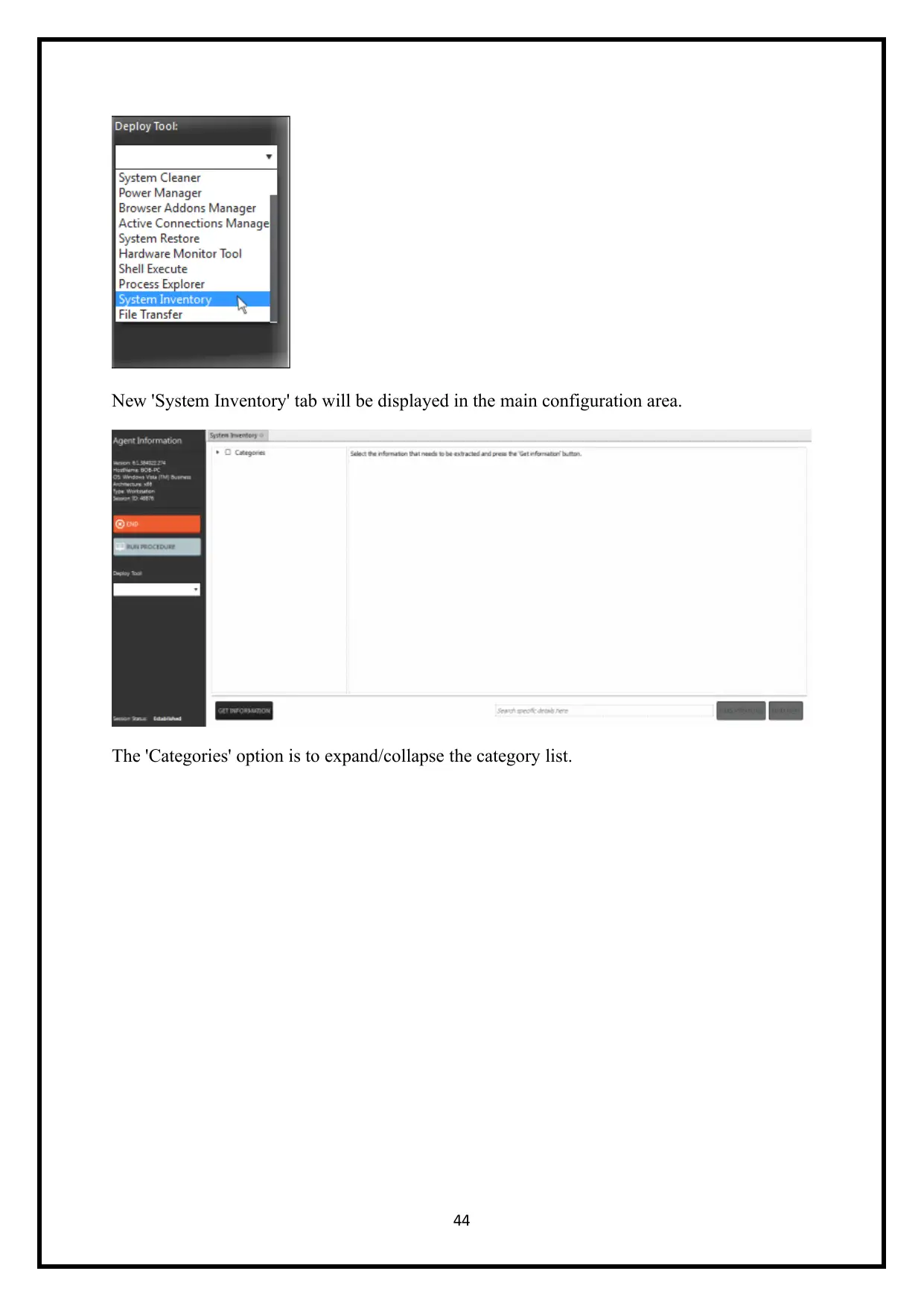
New 'System Inventory' tab will be displayed in the main configuration area.
The 'Categories' option is to expand/collapse the category list.
44
The 'Categories' option is to expand/collapse the category list.
44
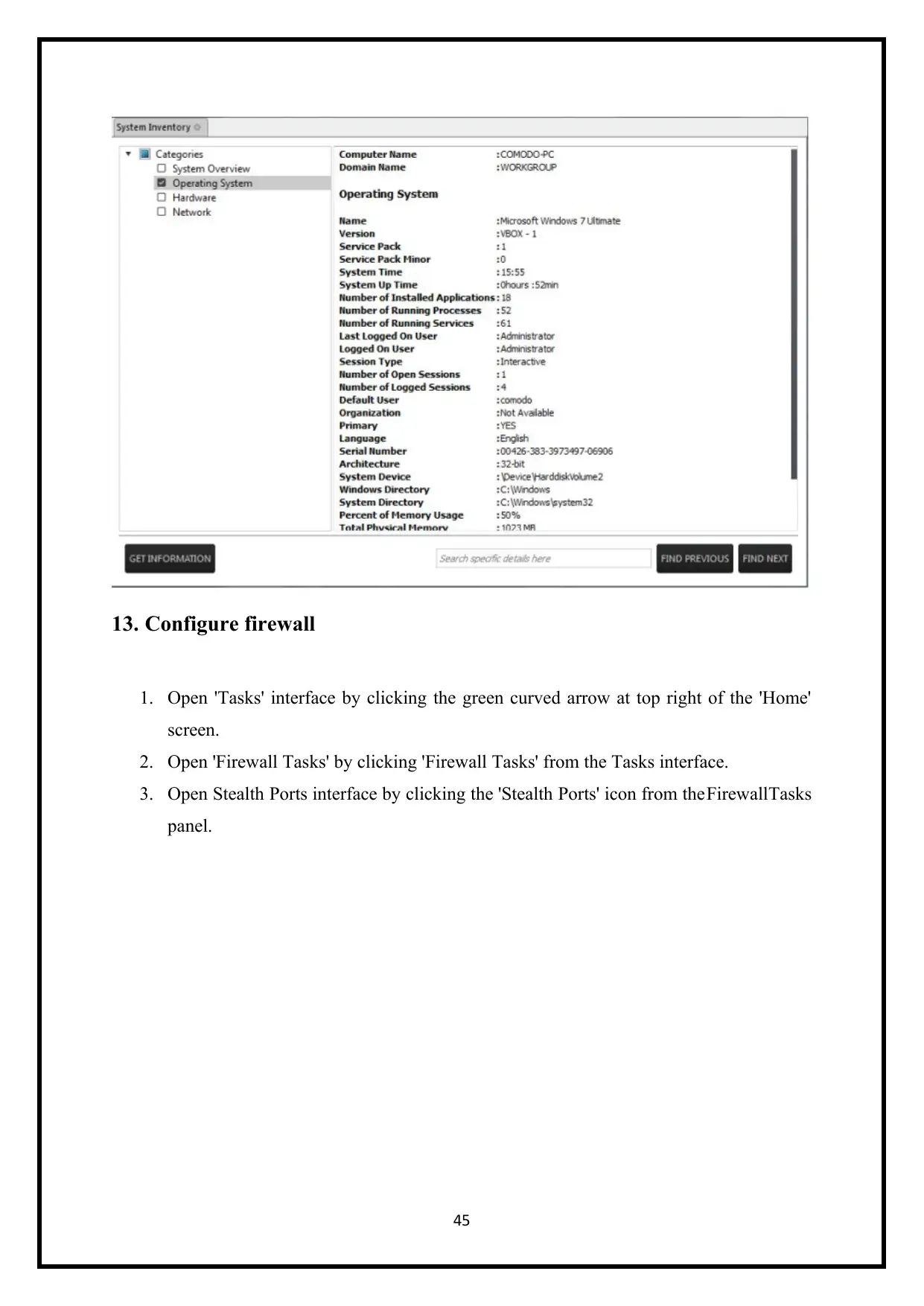
13. Configure firewall
1. Open 'Tasks' interface by clicking the green curved arrow at top right of the 'Home'
screen.
2. Open 'Firewall Tasks' by clicking 'Firewall Tasks' from the Tasks interface.
3. Open Stealth Ports interface by clicking the 'Stealth Ports' icon from theFirewallTasks
panel.
45
1. Open 'Tasks' interface by clicking the green curved arrow at top right of the 'Home'
screen.
2. Open 'Firewall Tasks' by clicking 'Firewall Tasks' from the Tasks interface.
3. Open Stealth Ports interface by clicking the 'Stealth Ports' icon from theFirewallTasks
panel.
45
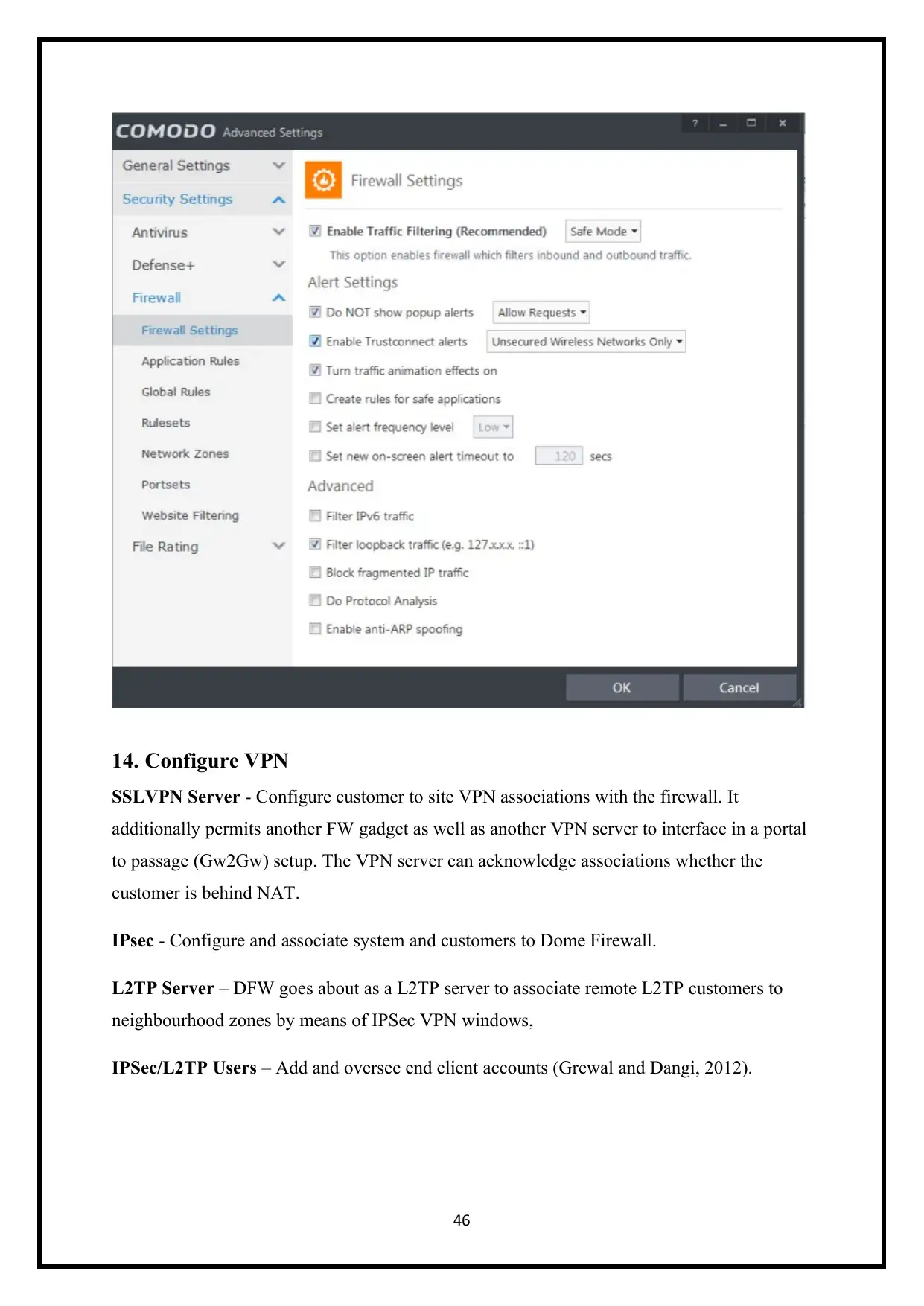
14. Configure VPN
SSLVPN Server - Configure customer to site VPN associations with the firewall. It
additionally permits another FW gadget as well as another VPN server to interface in a portal
to passage (Gw2Gw) setup. The VPN server can acknowledge associations whether the
customer is behind NAT.
IPsec - Configure and associate system and customers to Dome Firewall.
L2TP Server – DFW goes about as a L2TP server to associate remote L2TP customers to
neighbourhood zones by means of IPSec VPN windows,
IPSec/L2TP Users – Add and oversee end client accounts (Grewal and Dangi, 2012).
46
SSLVPN Server - Configure customer to site VPN associations with the firewall. It
additionally permits another FW gadget as well as another VPN server to interface in a portal
to passage (Gw2Gw) setup. The VPN server can acknowledge associations whether the
customer is behind NAT.
IPsec - Configure and associate system and customers to Dome Firewall.
L2TP Server – DFW goes about as a L2TP server to associate remote L2TP customers to
neighbourhood zones by means of IPSec VPN windows,
IPSec/L2TP Users – Add and oversee end client accounts (Grewal and Dangi, 2012).
46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
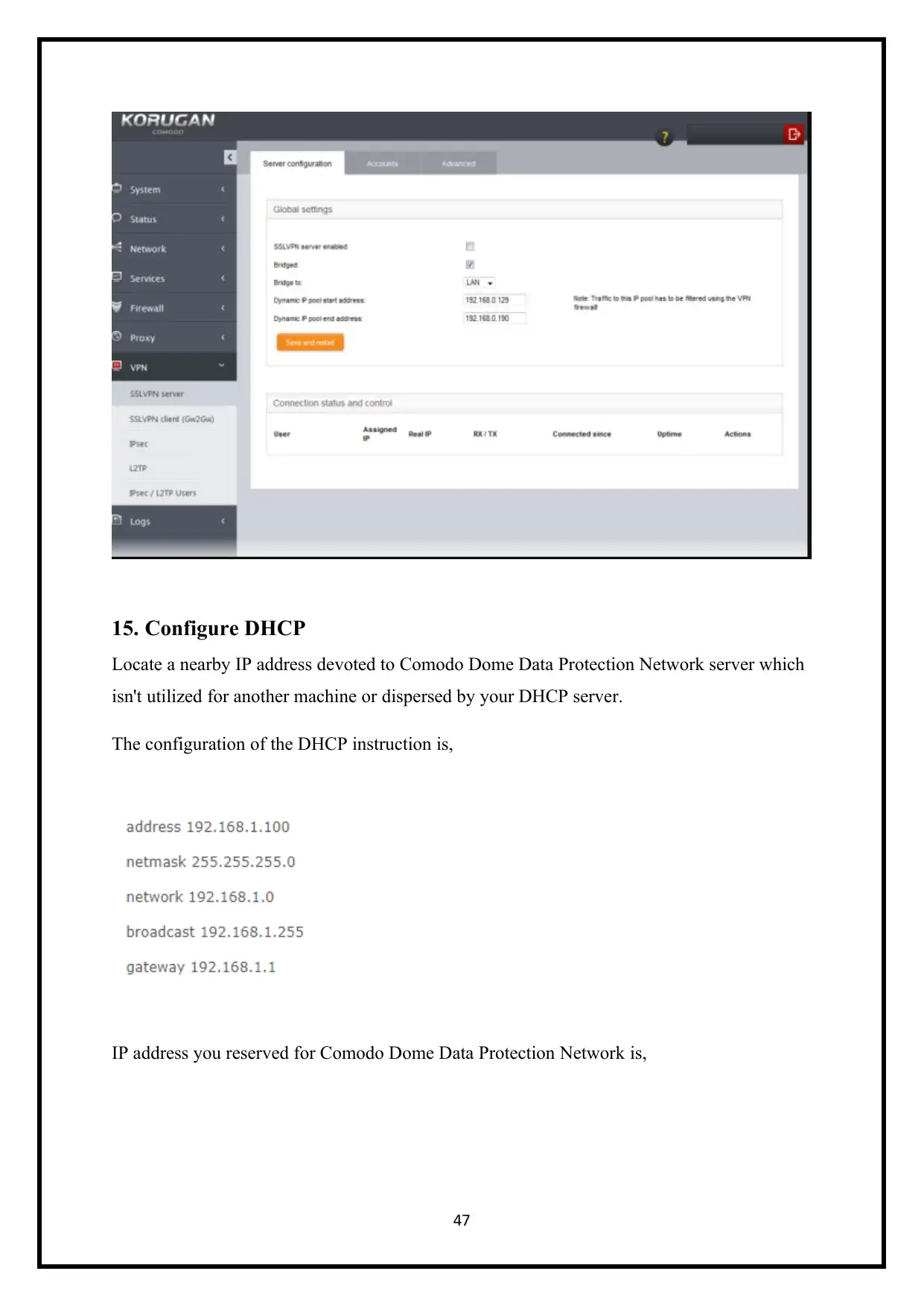
15. Configure DHCP
Locate a nearby IP address devoted to Comodo Dome Data Protection Network server which
isn't utilized for another machine or dispersed by your DHCP server.
The configuration of the DHCP instruction is,
IP address you reserved for Comodo Dome Data Protection Network is,
47
Locate a nearby IP address devoted to Comodo Dome Data Protection Network server which
isn't utilized for another machine or dispersed by your DHCP server.
The configuration of the DHCP instruction is,
IP address you reserved for Comodo Dome Data Protection Network is,
47
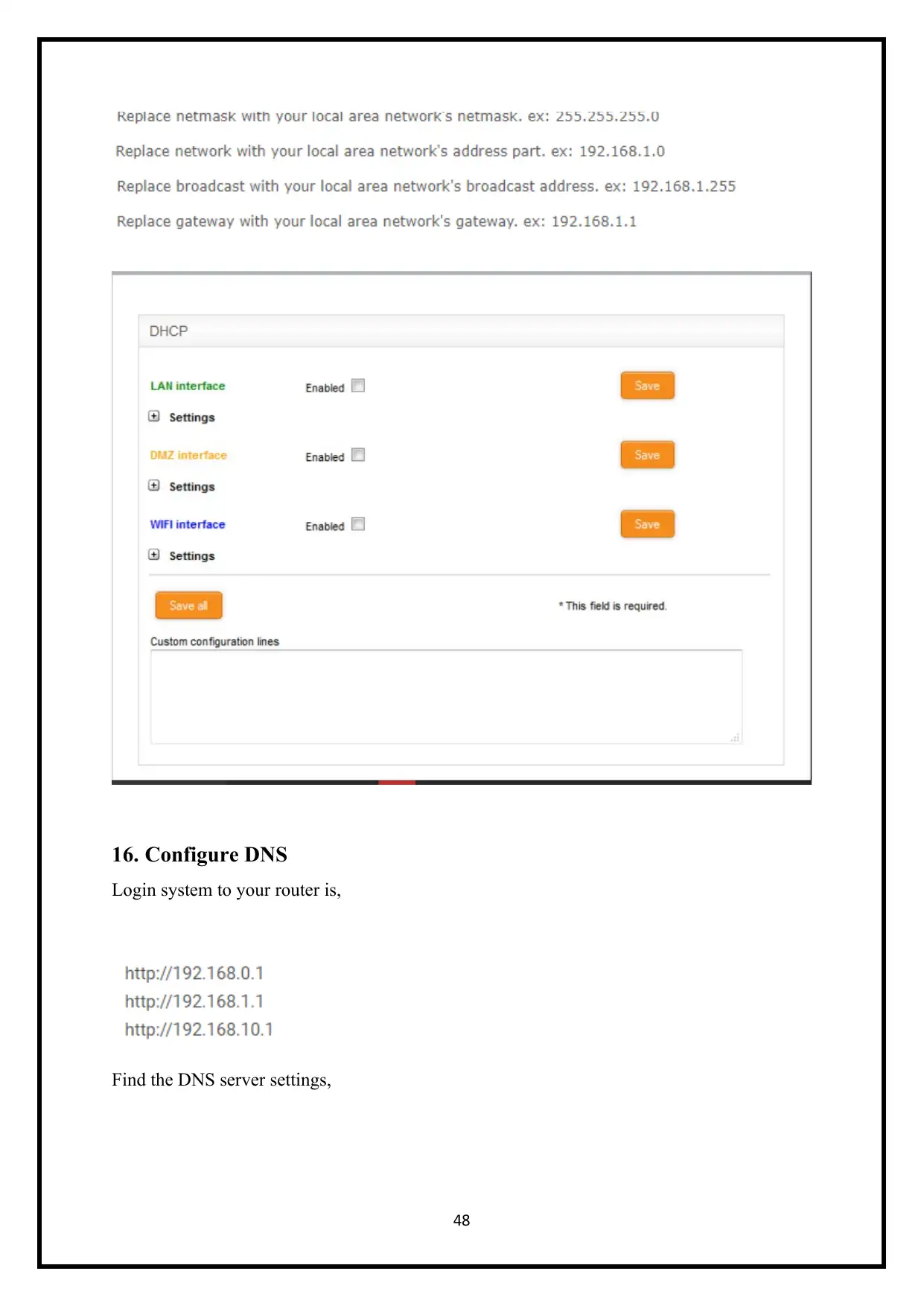
16. Configure DNS
Login system to your router is,
Find the DNS server settings,
48
Login system to your router is,
Find the DNS server settings,
48
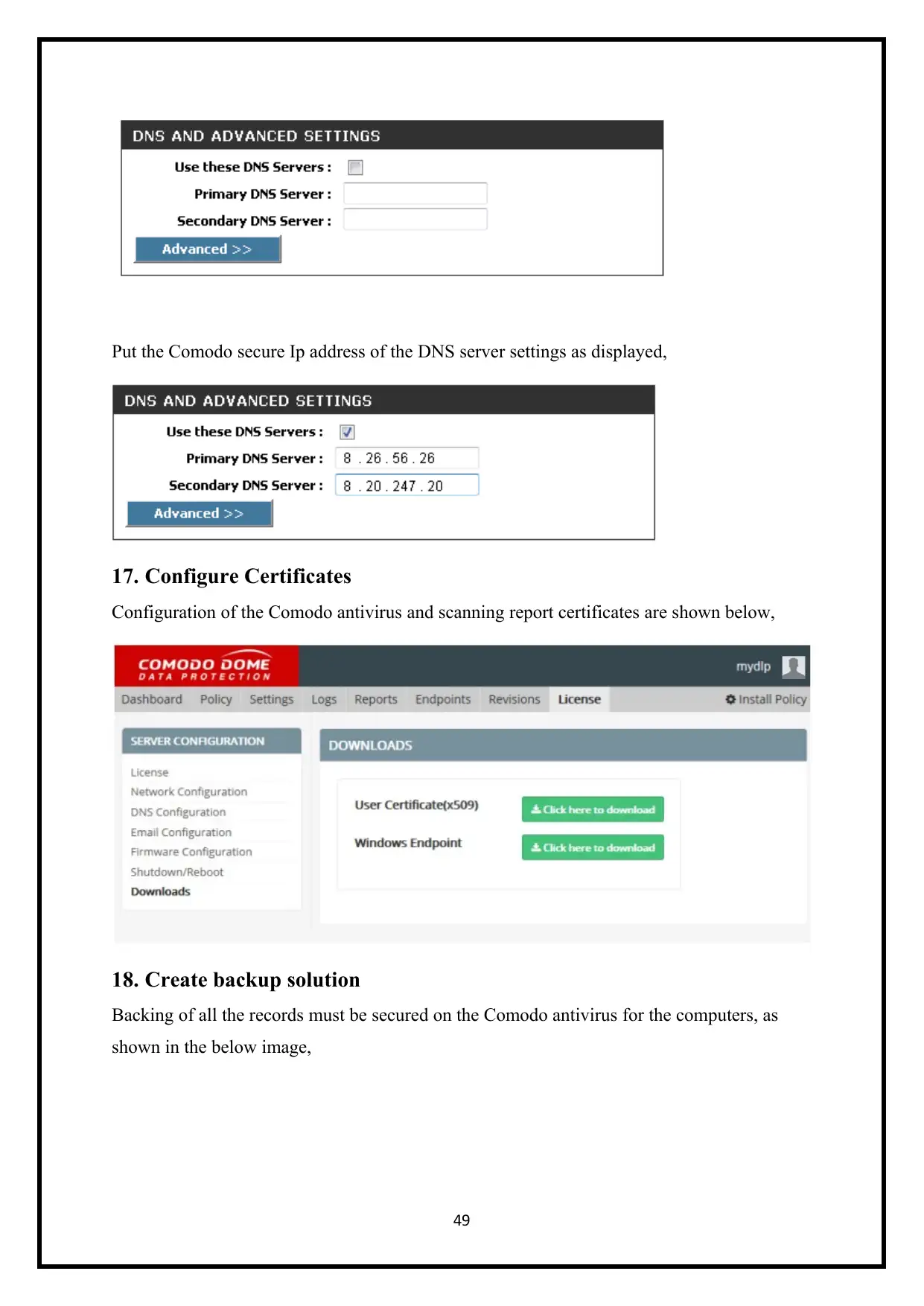
Put the Comodo secure Ip address of the DNS server settings as displayed,
17. Configure Certificates
Configuration of the Comodo antivirus and scanning report certificates are shown below,
18. Create backup solution
Backing of all the records must be secured on the Comodo antivirus for the computers, as
shown in the below image,
49
17. Configure Certificates
Configuration of the Comodo antivirus and scanning report certificates are shown below,
18. Create backup solution
Backing of all the records must be secured on the Comodo antivirus for the computers, as
shown in the below image,
49
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
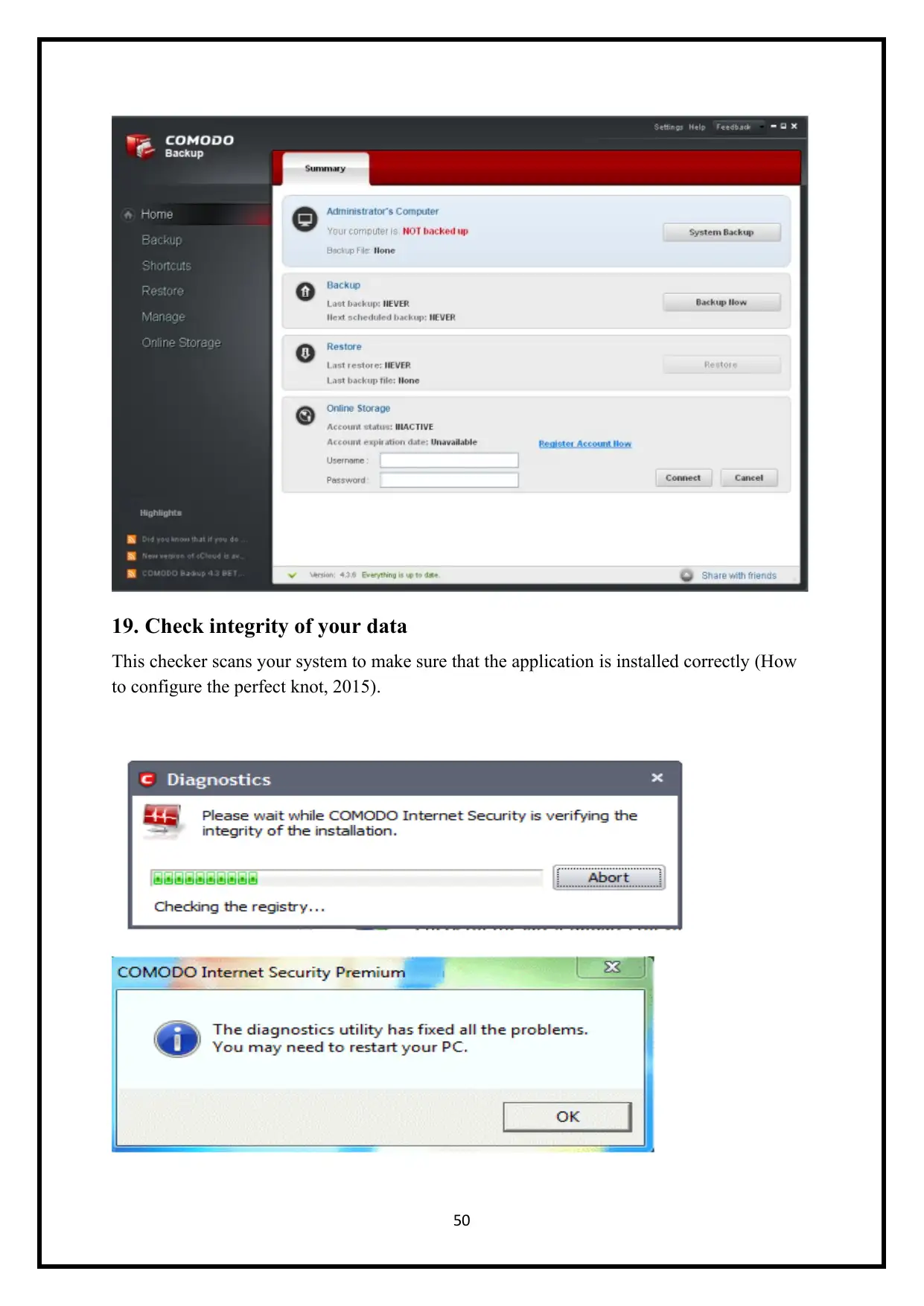
19. Check integrity of your data
This checker scans your system to make sure that the application is installed correctly (How
to configure the perfect knot, 2015).
50
This checker scans your system to make sure that the application is installed correctly (How
to configure the perfect knot, 2015).
50
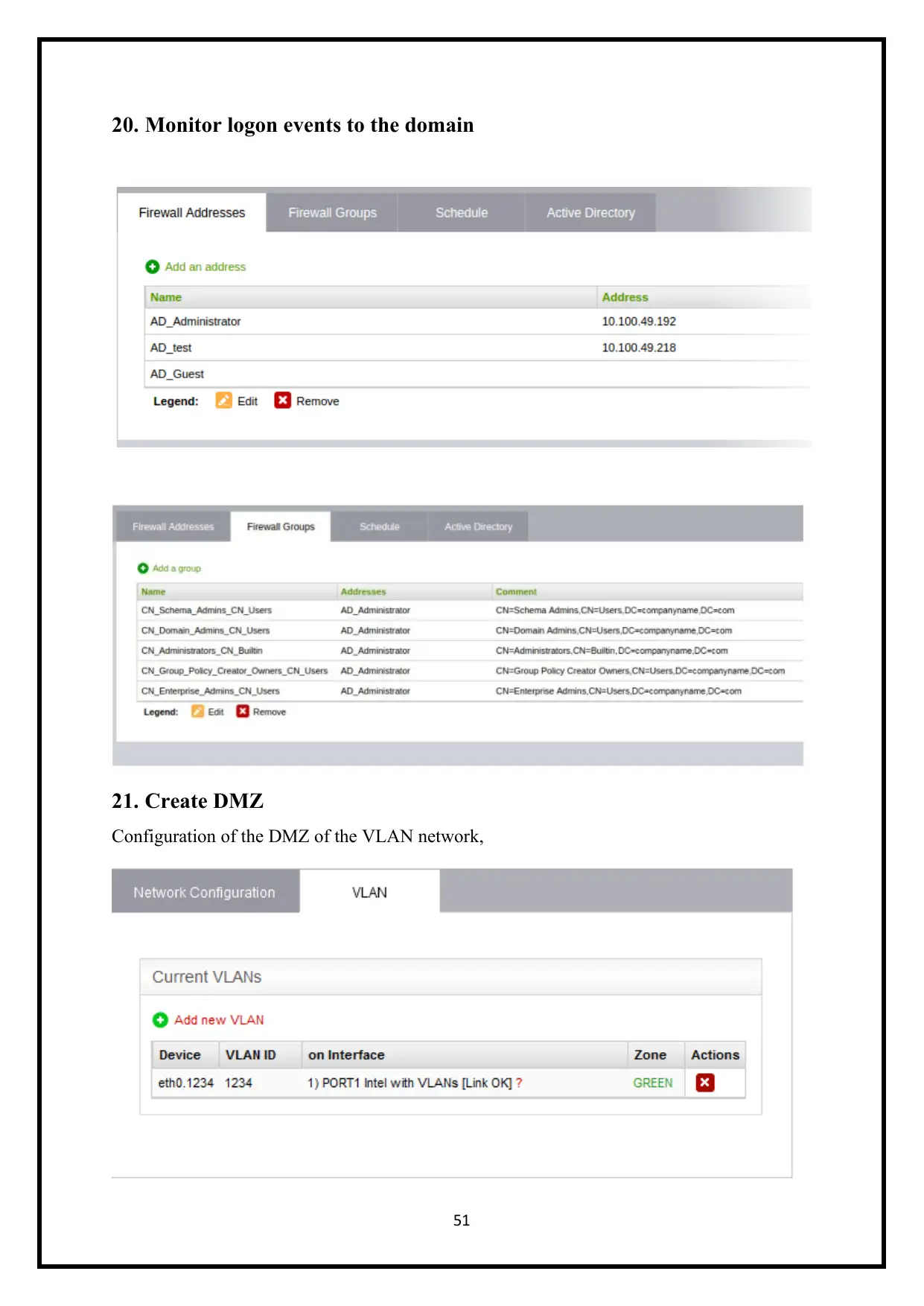
20. Monitor logon events to the domain
21. Create DMZ
Configuration of the DMZ of the VLAN network,
51
21. Create DMZ
Configuration of the DMZ of the VLAN network,
51
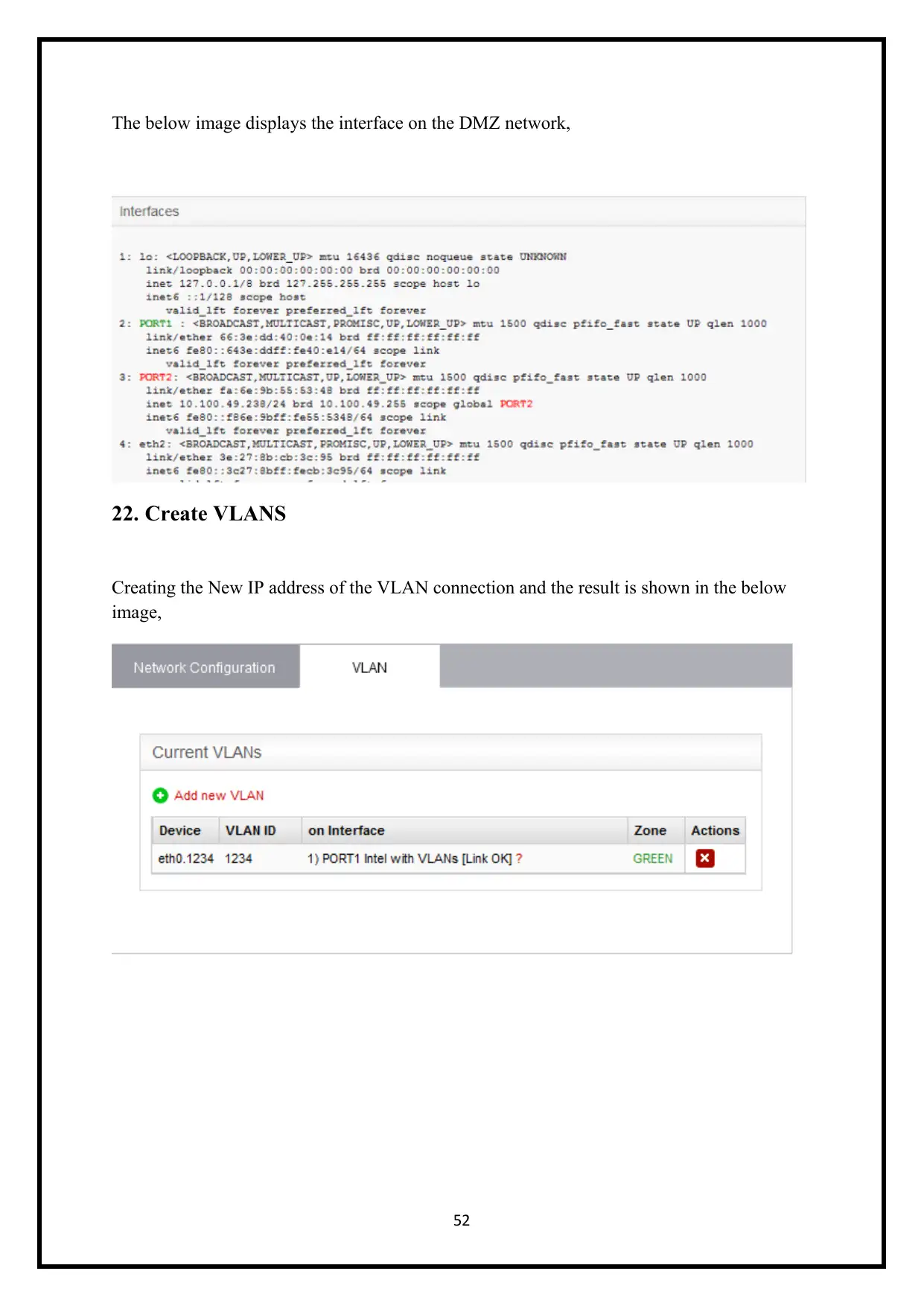
The below image displays the interface on the DMZ network,
22. Create VLANS
Creating the New IP address of the VLAN connection and the result is shown in the below
image,
52
22. Create VLANS
Creating the New IP address of the VLAN connection and the result is shown in the below
image,
52
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
.
23. Set VPN between sites
Add any of the sites to the organization reports,
24. Display warning message before user loges in.
Comodo antivirus Login details give the warning message as displayed below,
53
23. Set VPN between sites
Add any of the sites to the organization reports,
24. Display warning message before user loges in.
Comodo antivirus Login details give the warning message as displayed below,
53
25. Enforce password policy
Comodo antivirus Login details of the password policy is displayed below,
26. Enforce physical and environmental security
Comodo security protection can be bought from the Comodo antivirus server as displayed
below (Liu et al., 2017),
54
Comodo antivirus Login details of the password policy is displayed below,
26. Enforce physical and environmental security
Comodo security protection can be bought from the Comodo antivirus server as displayed
below (Liu et al., 2017),
54
27. Install network performance tools
Below is the virus scanning performance report,
55
Below is the virus scanning performance report,
55
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
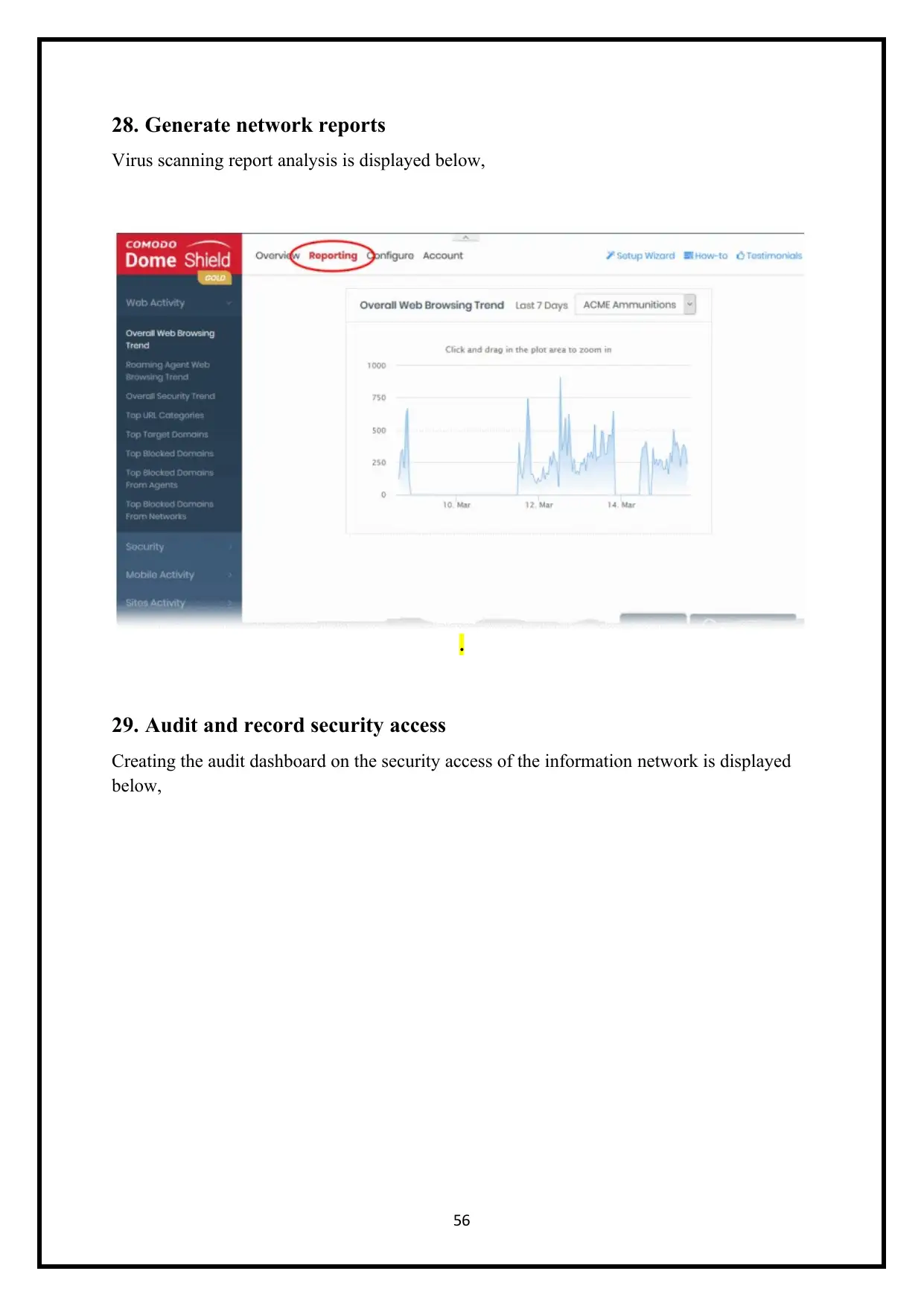
28. Generate network reports
Virus scanning report analysis is displayed below,
.
29. Audit and record security access
Creating the audit dashboard on the security access of the information network is displayed
below,
56
Virus scanning report analysis is displayed below,
.
29. Audit and record security access
Creating the audit dashboard on the security access of the information network is displayed
below,
56
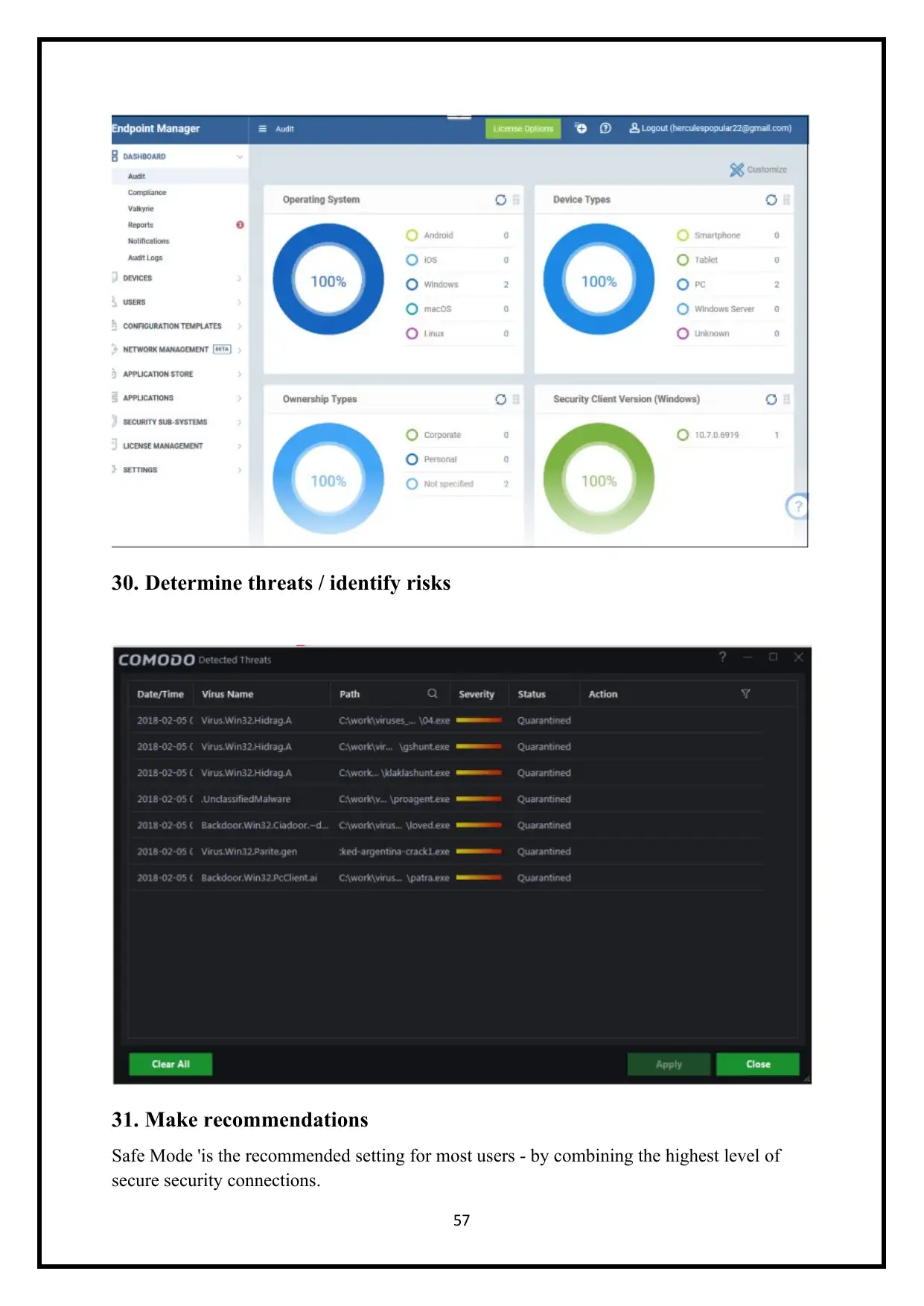
30. Determine threats / identify risks
31. Make recommendations
Safe Mode 'is the recommended setting for most users - by combining the highest level of
secure security connections.
57
31. Make recommendations
Safe Mode 'is the recommended setting for most users - by combining the highest level of
secure security connections.
57
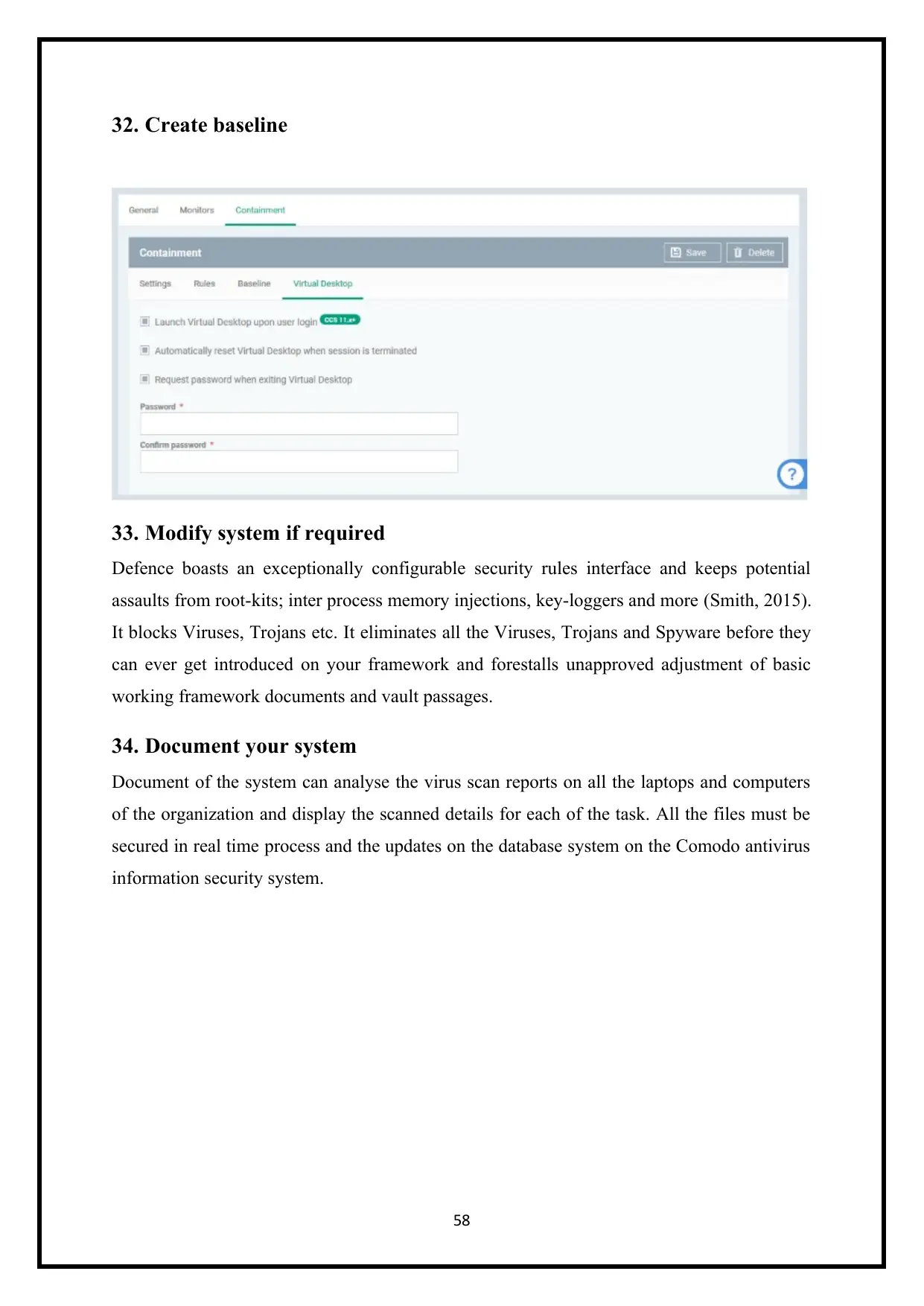
32. Create baseline
33. Modify system if required
Defence boasts an exceptionally configurable security rules interface and keeps potential
assaults from root-kits; inter process memory injections, key-loggers and more (Smith, 2015).
It blocks Viruses, Trojans etc. It eliminates all the Viruses, Trojans and Spyware before they
can ever get introduced on your framework and forestalls unapproved adjustment of basic
working framework documents and vault passages.
34. Document your system
Document of the system can analyse the virus scan reports on all the laptops and computers
of the organization and display the scanned details for each of the task. All the files must be
secured in real time process and the updates on the database system on the Comodo antivirus
information security system.
58
33. Modify system if required
Defence boasts an exceptionally configurable security rules interface and keeps potential
assaults from root-kits; inter process memory injections, key-loggers and more (Smith, 2015).
It blocks Viruses, Trojans etc. It eliminates all the Viruses, Trojans and Spyware before they
can ever get introduced on your framework and forestalls unapproved adjustment of basic
working framework documents and vault passages.
34. Document your system
Document of the system can analyse the virus scan reports on all the laptops and computers
of the organization and display the scanned details for each of the task. All the files must be
secured in real time process and the updates on the database system on the Comodo antivirus
information security system.
58
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
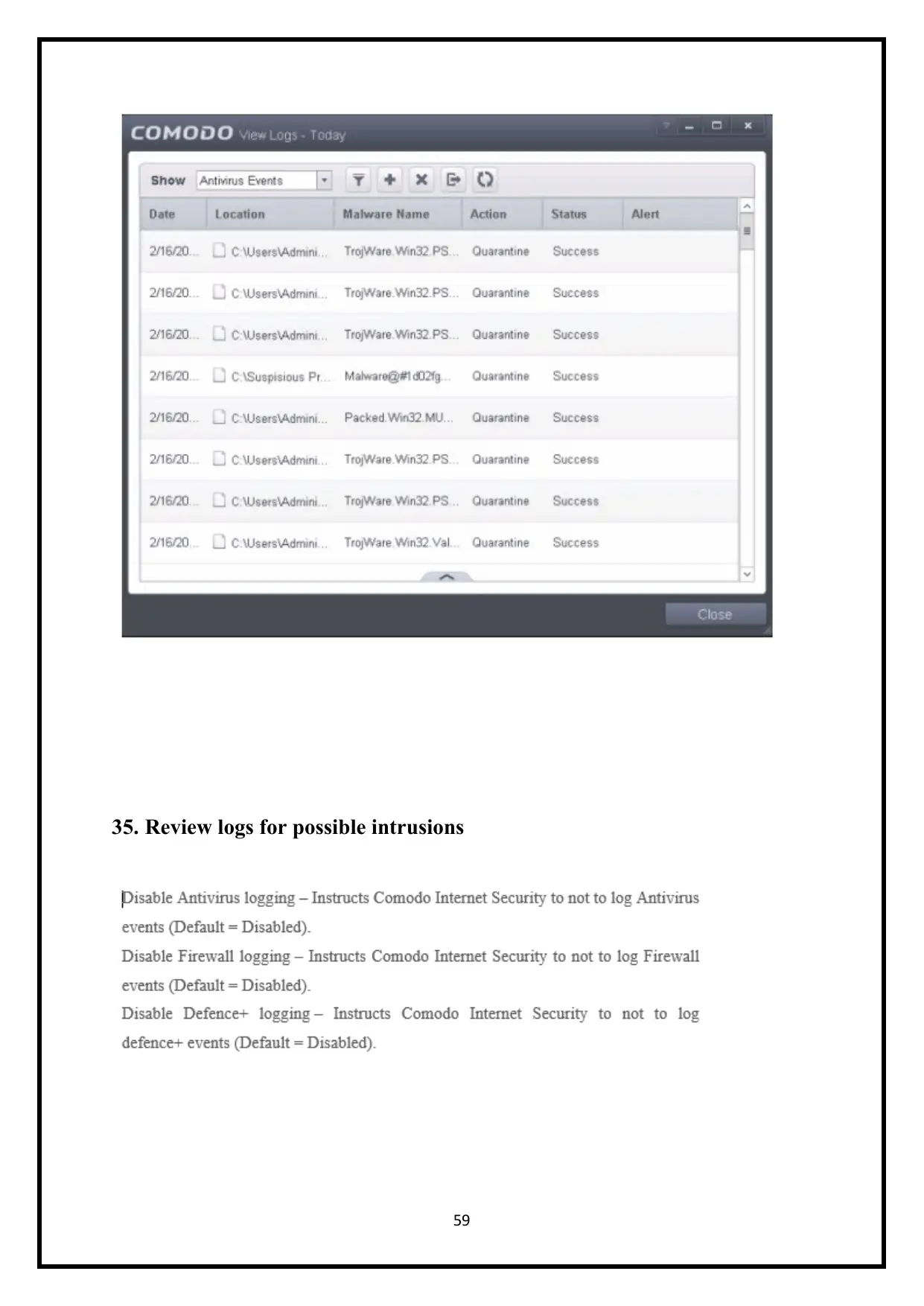
35. Review logs for possible intrusions
59
59
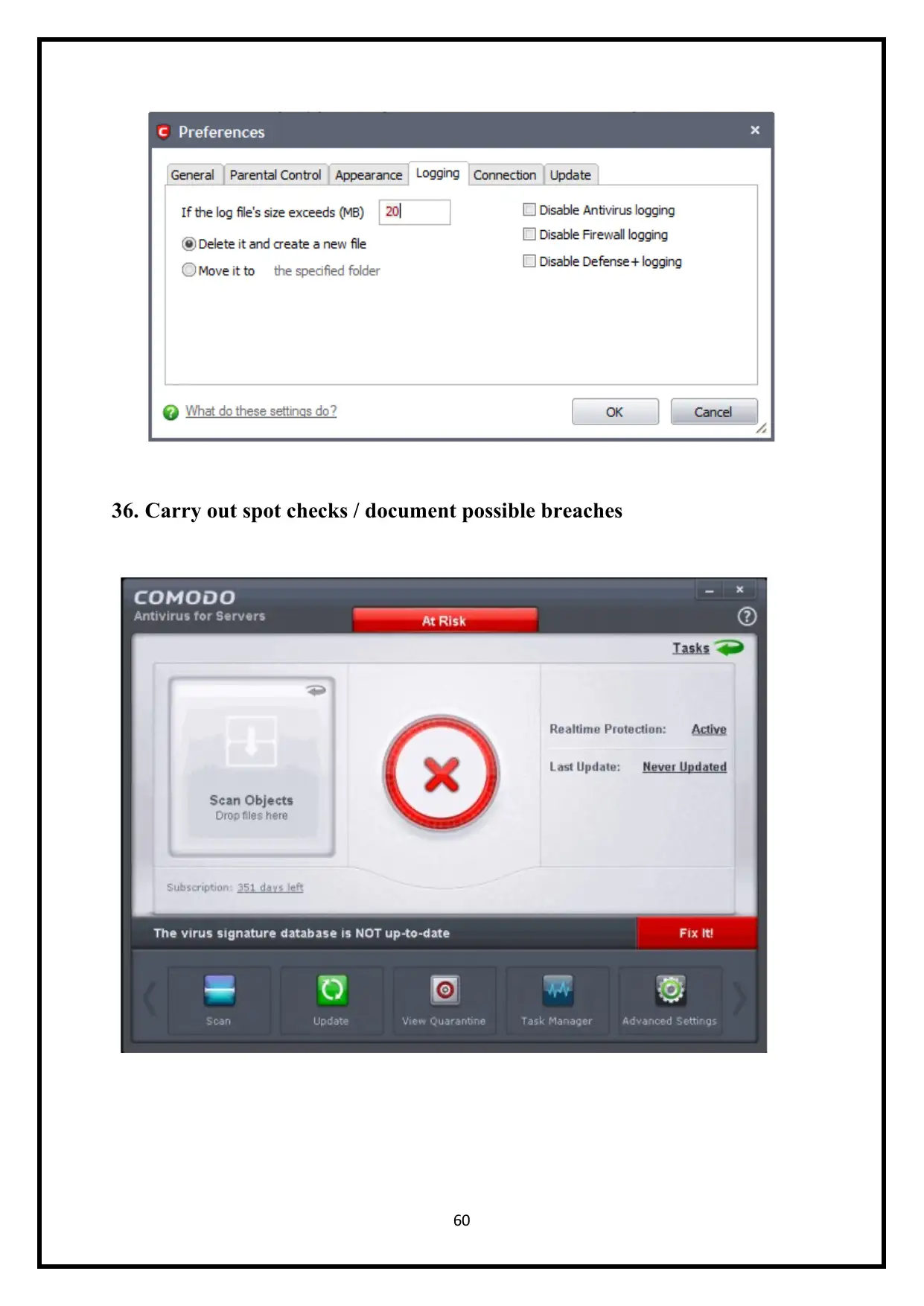
36. Carry out spot checks / document possible breaches
60
60
61
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Gellman, D. (2011). Computer Security. Hoboken: Wiley Textbooks.
Koret, J. (2015). Antivirus hacker's handbook. Hoboken: John Wiley & Sons.
Lipczynski, J., Wilson, J. and Goddard, J. (2013). Industrial organization. Harlow,
England: Pearson.
Mutholib, A. (2014). Development of automatic number plate recognition on computer
and laptop platforms. Kuala Lumpur: Kulliyyah of Engineering, International Islamic
University Malaysia.
Caicedo-Muñoz, J., Ledezma Espino, A., Corrales, J. and Rendón, A. (2018). QoS-
Classifier for VPN and Non-VPN traffic based on time-related features. Computer
Networks, 144, pp.271-279.
Grewal, K. and Dangi, R. (2012). Comparative Analysis of QoS VPN Provisioning
Algorithm on Traditional IP based VPN and MPLS VPN using NS-2. International
Journal of Computer Applications, 48(1), pp.43-46.
How to configure the perfect knot. (2015). Physics Today.
Liu, X., Yang, Y., Meng, M. and Rau, A. (2017). Impact of Different Bus Stop Designs
on Bus Operating Time Components. Journal of Public Transportation, 20(1), pp.104-
118.
Smith, N. (2015). Classic Project: GPO Telephone 706. Engineering & Technology,
10(11), pp.100-101.
62
Gellman, D. (2011). Computer Security. Hoboken: Wiley Textbooks.
Koret, J. (2015). Antivirus hacker's handbook. Hoboken: John Wiley & Sons.
Lipczynski, J., Wilson, J. and Goddard, J. (2013). Industrial organization. Harlow,
England: Pearson.
Mutholib, A. (2014). Development of automatic number plate recognition on computer
and laptop platforms. Kuala Lumpur: Kulliyyah of Engineering, International Islamic
University Malaysia.
Caicedo-Muñoz, J., Ledezma Espino, A., Corrales, J. and Rendón, A. (2018). QoS-
Classifier for VPN and Non-VPN traffic based on time-related features. Computer
Networks, 144, pp.271-279.
Grewal, K. and Dangi, R. (2012). Comparative Analysis of QoS VPN Provisioning
Algorithm on Traditional IP based VPN and MPLS VPN using NS-2. International
Journal of Computer Applications, 48(1), pp.43-46.
How to configure the perfect knot. (2015). Physics Today.
Liu, X., Yang, Y., Meng, M. and Rau, A. (2017). Impact of Different Bus Stop Designs
on Bus Operating Time Components. Journal of Public Transportation, 20(1), pp.104-
118.
Smith, N. (2015). Classic Project: GPO Telephone 706. Engineering & Technology,
10(11), pp.100-101.
62
1 out of 62
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





