ITC571 Project: Mobile Security Enhancement via Face Detection
VerifiedAdded on 2024/06/25
|4
|1092
|124
Project
AI Summary
This project proposal focuses on enhancing mobile security through the application of the Viola-Jones face detection algorithm and image logging techniques. It addresses the vulnerabilities in current mobile security systems, particularly those related to image errors and illumination issues affecting biometric identification. The proposal outlines a research methodology involving data gathering, analysis of existing solutions, and the development of a novel approach using the Viola-Jones framework for improved face detection and security. Expected outcomes include effective recognition of normal and abnormal faces, enhanced mobile security through integrated face detection logging, and potential exploration of brain signal patterns for high-level biometric verification. The project aims to contribute to a more robust and efficient mobile security system by leveraging advanced image processing and face detection technologies. The document is available on Desklib, a platform offering a range of study tools and solved assignments for students.
Writing Proposal Sample for ITC571
Student Name and ID
Project area Security
Project name Use of Viola-Jones face detection algorithm and image logging to enhance mobile security
Keywords Video Frame-based face detection, Lib face detection, Deep learning, Gaussian Mixture Model
Research Type Theoretical and Practical
1. Introduction Background
Information,
Issues, and
Current Solutions
1. Mobile security is the protection of portable computing device from threats and vulnerabilities to
minimize the level of frauds. It is known that image recording is a type of artificial intelligence
technology which emerges as a crucial tool in day to day life. The demand for uncovering and
identification is higher accuracy and advanced speed for the mobile security. The mobile security
faces attacks due to poor coding which creates loopholes. Communication network attacks and OS
attacks which create vulnerabilities. Basically, here an abnormal face defines that which is partly
obstructed by certain irrelevant objects as face cover or others. As it can also bring us some potential
risks, particularly in the mobile security area. Current technologies include lip-based, iris biometric
identification, and smart video frame based detection system is intended for developing a good safety
protection in identifying the ordinary and irregular face in the domain of enhancing mobile security.
Shortcomings/
limitations in the
current /existing
solutions
2. The existing solution includes biometric identification related to face detection which manages
mobile vulnerabilities. But it faces issues related to image error which impact the identification of
the face to maintain security. Illumination issue in an image which impacts identification due to
change in lightface appears differently and pose variation impacts recognition.
The problem of humiliation will occur when the complexity of the neural network will increase. This
technology basically does not predict the user effectively as any of the customers can make a fake
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
Student Name and ID
Project area Security
Project name Use of Viola-Jones face detection algorithm and image logging to enhance mobile security
Keywords Video Frame-based face detection, Lib face detection, Deep learning, Gaussian Mixture Model
Research Type Theoretical and Practical
1. Introduction Background
Information,
Issues, and
Current Solutions
1. Mobile security is the protection of portable computing device from threats and vulnerabilities to
minimize the level of frauds. It is known that image recording is a type of artificial intelligence
technology which emerges as a crucial tool in day to day life. The demand for uncovering and
identification is higher accuracy and advanced speed for the mobile security. The mobile security
faces attacks due to poor coding which creates loopholes. Communication network attacks and OS
attacks which create vulnerabilities. Basically, here an abnormal face defines that which is partly
obstructed by certain irrelevant objects as face cover or others. As it can also bring us some potential
risks, particularly in the mobile security area. Current technologies include lip-based, iris biometric
identification, and smart video frame based detection system is intended for developing a good safety
protection in identifying the ordinary and irregular face in the domain of enhancing mobile security.
Shortcomings/
limitations in the
current /existing
solutions
2. The existing solution includes biometric identification related to face detection which manages
mobile vulnerabilities. But it faces issues related to image error which impact the identification of
the face to maintain security. Illumination issue in an image which impacts identification due to
change in lightface appears differently and pose variation impacts recognition.
The problem of humiliation will occur when the complexity of the neural network will increase. This
technology basically does not predict the user effectively as any of the customers can make a fake
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
image to unlock the mobile phone.
Importance of
solving this
problem
3. With the presence of Viola face detection algorithm in image logging, early face recognition can
be done. As this will assist in managing the mobile security effectively and efficiently. For this Open
CV can be used for detecting whether the image contains faces which include Harr classifier based
on the Viola-Jones framework. The image logging technique is used for providing high image
resolution with the Borehole image logs, optical image, and KGS- geological image logging. This
face detection outline can easily be used for the mobile security.
2. The Main aims of
this research
1. Aims and purposes of this research project are listed below:
To design an image logging system using the Viola-Jones face detection algorithm for maintaining security
To analyze the mobile characteristic for predicting its security issues effectively and efficiently.
To propose Viola Jones detection algorithm and techniques for improving the mobile security.
3. A Brief Description
of Your Proposal
In this research project, the effective and efficient application of the Viola-Jones faces detection framework for evaluating
the security issues in the mobile phone will be proposed. The role and application of Viola-Jones framework will be
discussed in an effective way. In the basic framework for detection gray-scale processing is used in the image, the lib face
detection will be performed for the face detection.
4. The Processor
Methodology of Your
Project
1) Data gathering and analysis
Identification of security issues in mobile device
The stated topic will be analyzed for identification of issues and problems faced due to the mobile security
issues
Understanding of project methodologies for predicting mobile security issue
2) Data collection and analysis
A literature review will be presented for the current best solution for the identification of the issue
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
Importance of
solving this
problem
3. With the presence of Viola face detection algorithm in image logging, early face recognition can
be done. As this will assist in managing the mobile security effectively and efficiently. For this Open
CV can be used for detecting whether the image contains faces which include Harr classifier based
on the Viola-Jones framework. The image logging technique is used for providing high image
resolution with the Borehole image logs, optical image, and KGS- geological image logging. This
face detection outline can easily be used for the mobile security.
2. The Main aims of
this research
1. Aims and purposes of this research project are listed below:
To design an image logging system using the Viola-Jones face detection algorithm for maintaining security
To analyze the mobile characteristic for predicting its security issues effectively and efficiently.
To propose Viola Jones detection algorithm and techniques for improving the mobile security.
3. A Brief Description
of Your Proposal
In this research project, the effective and efficient application of the Viola-Jones faces detection framework for evaluating
the security issues in the mobile phone will be proposed. The role and application of Viola-Jones framework will be
discussed in an effective way. In the basic framework for detection gray-scale processing is used in the image, the lib face
detection will be performed for the face detection.
4. The Processor
Methodology of Your
Project
1) Data gathering and analysis
Identification of security issues in mobile device
The stated topic will be analyzed for identification of issues and problems faced due to the mobile security
issues
Understanding of project methodologies for predicting mobile security issue
2) Data collection and analysis
A literature review will be presented for the current best solution for the identification of the issue
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre

Determining the current best solution
Resources will be collected for evaluating the process
3) Proposal makeup
Analysing the pros and cons of the existing solution
To propose a current best solution for the identification of the issue
Justification and recommendation for the possible outcomes.
5. Expected Outcomes The expected outcomes of the research project are underneath:
1. Recognition of normal and abnormal face effectively
2. Explored the role of Viola Face detection framework in the mobile security system
3. Enhance the mobile security system with the integration of face detection logging system in mobile
4. Proposing brain signal patterns for biometric identification to enhance high-level security through a verification
system
Reference list Niu, G., and Chen, Q. (2018). Learning a Video Frame-based face detection system for security fields. Journal of
Visual Communication and Image Representation. Retrieved from: https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/S1047320318301561
Arceda, V. M., Fabián, K. F., Laura, P. L., Tito, J. R., &Cáceres, J. G. (2016). Fast face detection in violent video
scenes. Electronic Notes in Theoretical Computer Science, 329, 5-26. Retrieved from: https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/S1571066116301050
Chaudhry, S., & Chandra, R. (2017). Face detection and recognition in an unconstrained environment for the
mobile visual assistive system. Applied Soft Computing, 53, 168-180. Retrieved from: https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/S1568494616306603
Singh, M., &Arora, A. S. (2017). A robust anti-spoofing technique for face liveness detection with morphological
operations. Optik-International Journal for Light and Electron Optics, 139, 347-354. Retrieved from: https://www-
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
Resources will be collected for evaluating the process
3) Proposal makeup
Analysing the pros and cons of the existing solution
To propose a current best solution for the identification of the issue
Justification and recommendation for the possible outcomes.
5. Expected Outcomes The expected outcomes of the research project are underneath:
1. Recognition of normal and abnormal face effectively
2. Explored the role of Viola Face detection framework in the mobile security system
3. Enhance the mobile security system with the integration of face detection logging system in mobile
4. Proposing brain signal patterns for biometric identification to enhance high-level security through a verification
system
Reference list Niu, G., and Chen, Q. (2018). Learning a Video Frame-based face detection system for security fields. Journal of
Visual Communication and Image Representation. Retrieved from: https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/S1047320318301561
Arceda, V. M., Fabián, K. F., Laura, P. L., Tito, J. R., &Cáceres, J. G. (2016). Fast face detection in violent video
scenes. Electronic Notes in Theoretical Computer Science, 329, 5-26. Retrieved from: https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/S1571066116301050
Chaudhry, S., & Chandra, R. (2017). Face detection and recognition in an unconstrained environment for the
mobile visual assistive system. Applied Soft Computing, 53, 168-180. Retrieved from: https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/S1568494616306603
Singh, M., &Arora, A. S. (2017). A robust anti-spoofing technique for face liveness detection with morphological
operations. Optik-International Journal for Light and Electron Optics, 139, 347-354. Retrieved from: https://www-
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
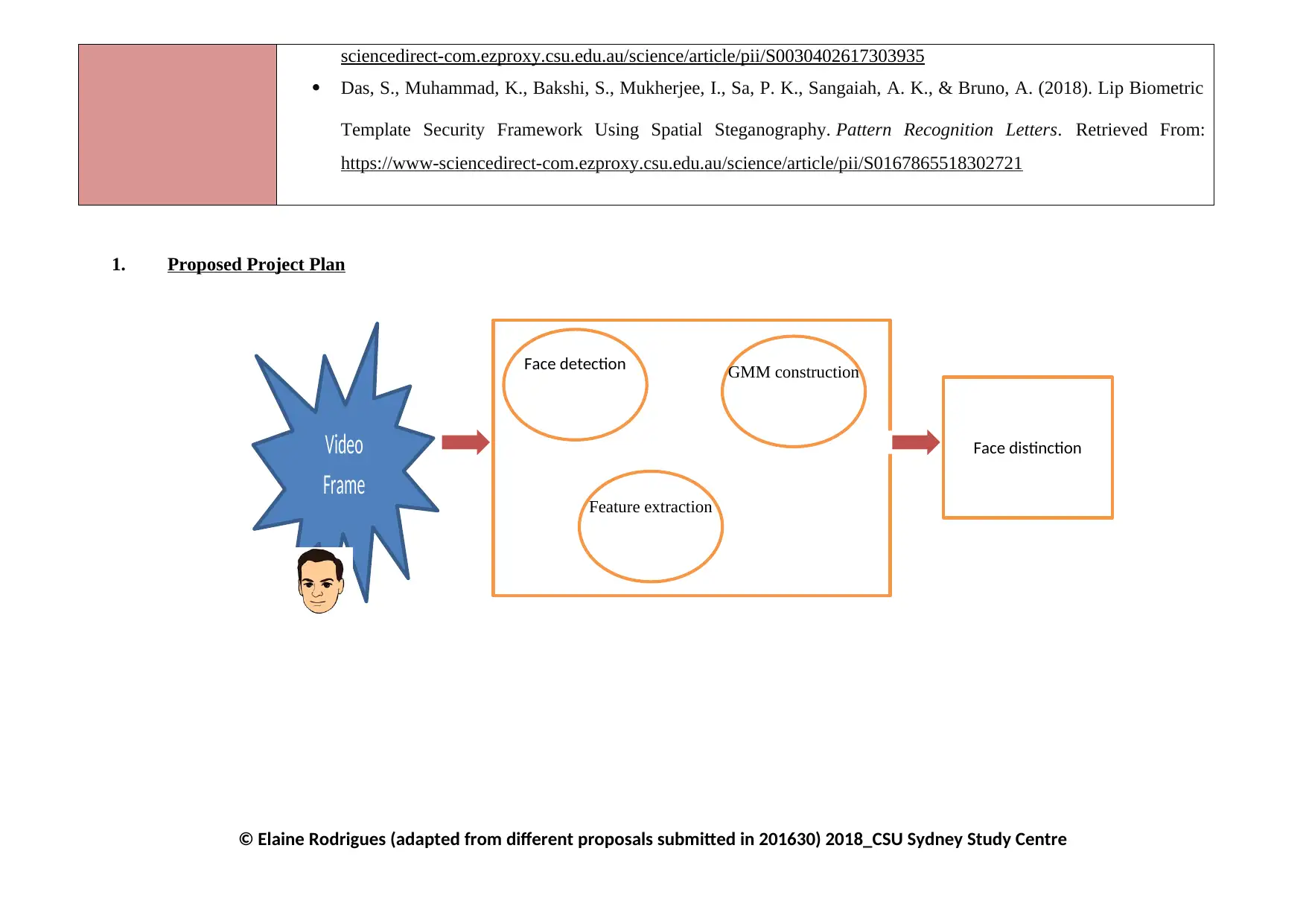
Video
Frame
Face detection
Feature extraction
GMM construction
Face distinction
sciencedirect-com.ezproxy.csu.edu.au/science/article/pii/S0030402617303935
Das, S., Muhammad, K., Bakshi, S., Mukherjee, I., Sa, P. K., Sangaiah, A. K., & Bruno, A. (2018). Lip Biometric
Template Security Framework Using Spatial Steganography. Pattern Recognition Letters. Retrieved From:
https://www-sciencedirect-com.ezproxy.csu.edu.au/science/article/pii/S0167865518302721
1. Proposed Project Plan
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
Frame
Face detection
Feature extraction
GMM construction
Face distinction
sciencedirect-com.ezproxy.csu.edu.au/science/article/pii/S0030402617303935
Das, S., Muhammad, K., Bakshi, S., Mukherjee, I., Sa, P. K., Sangaiah, A. K., & Bruno, A. (2018). Lip Biometric
Template Security Framework Using Spatial Steganography. Pattern Recognition Letters. Retrieved From:
https://www-sciencedirect-com.ezproxy.csu.edu.au/science/article/pii/S0167865518302721
1. Proposed Project Plan
© Elaine Rodrigues (adapted from different proposals submitted in 201630) 2018_CSU Sydney Study Centre
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





