Data Hiding, Steganography, and Anonymity: Techniques and Analysis
VerifiedAdded on 2023/04/23
|13
|709
|121
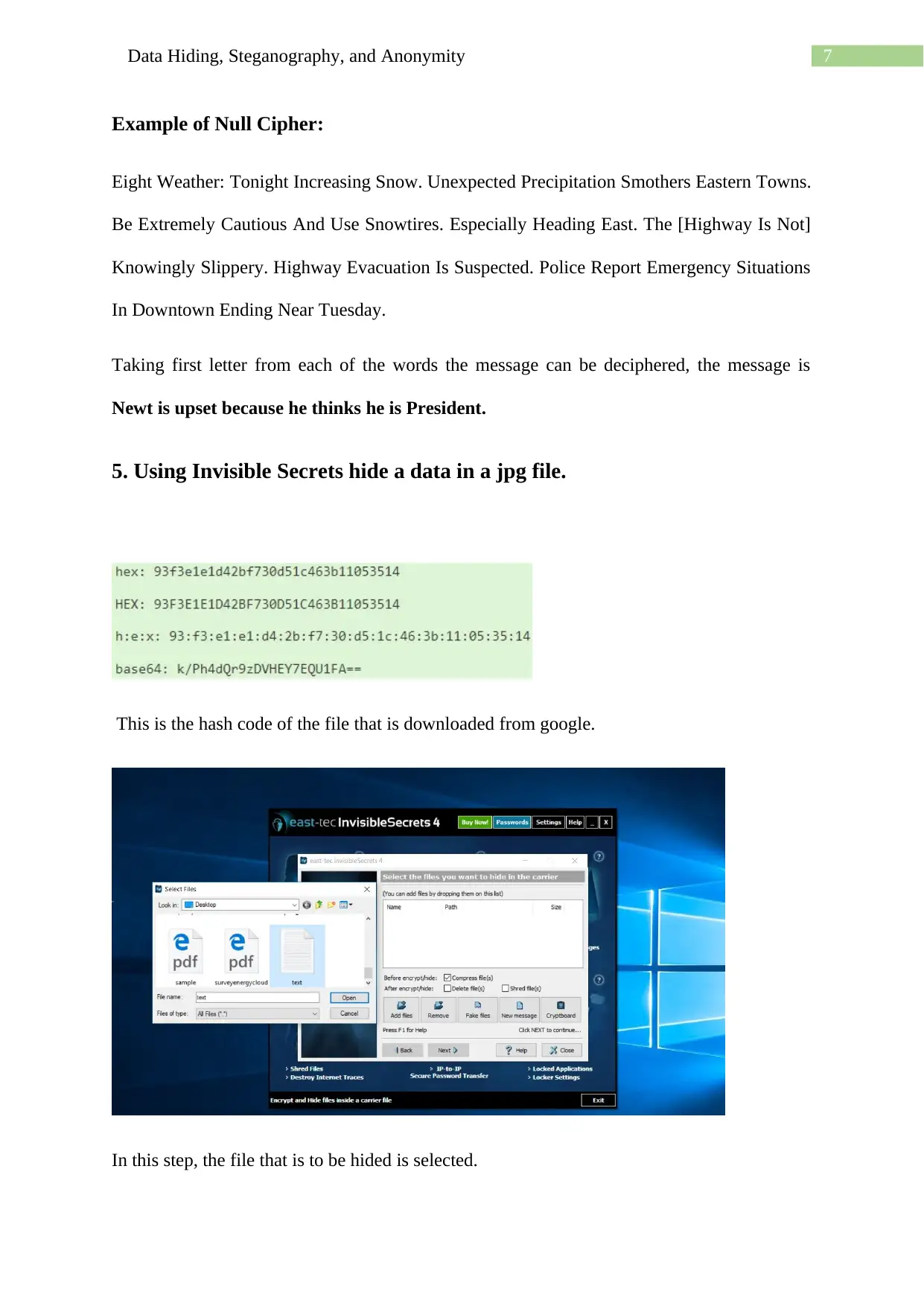
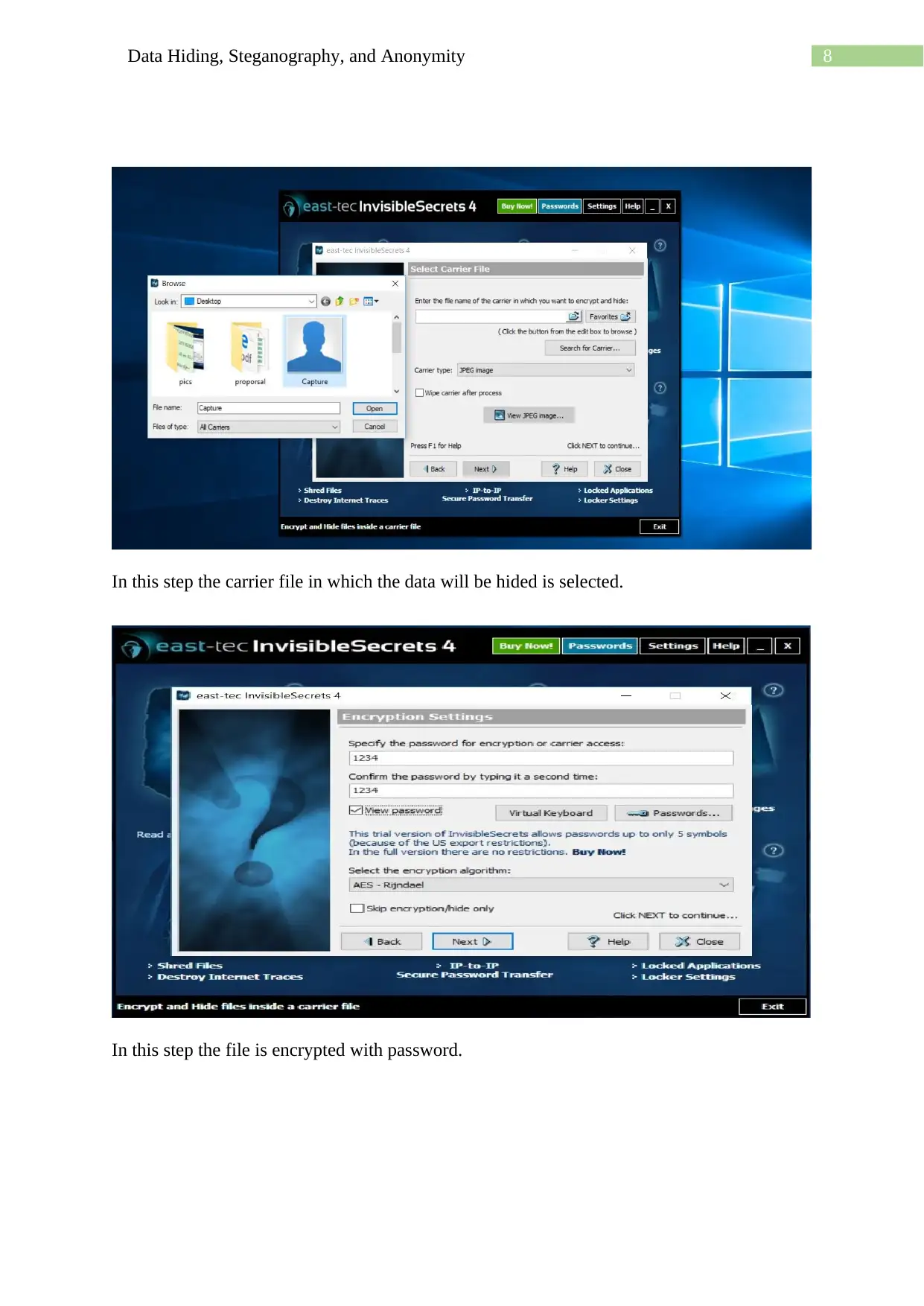
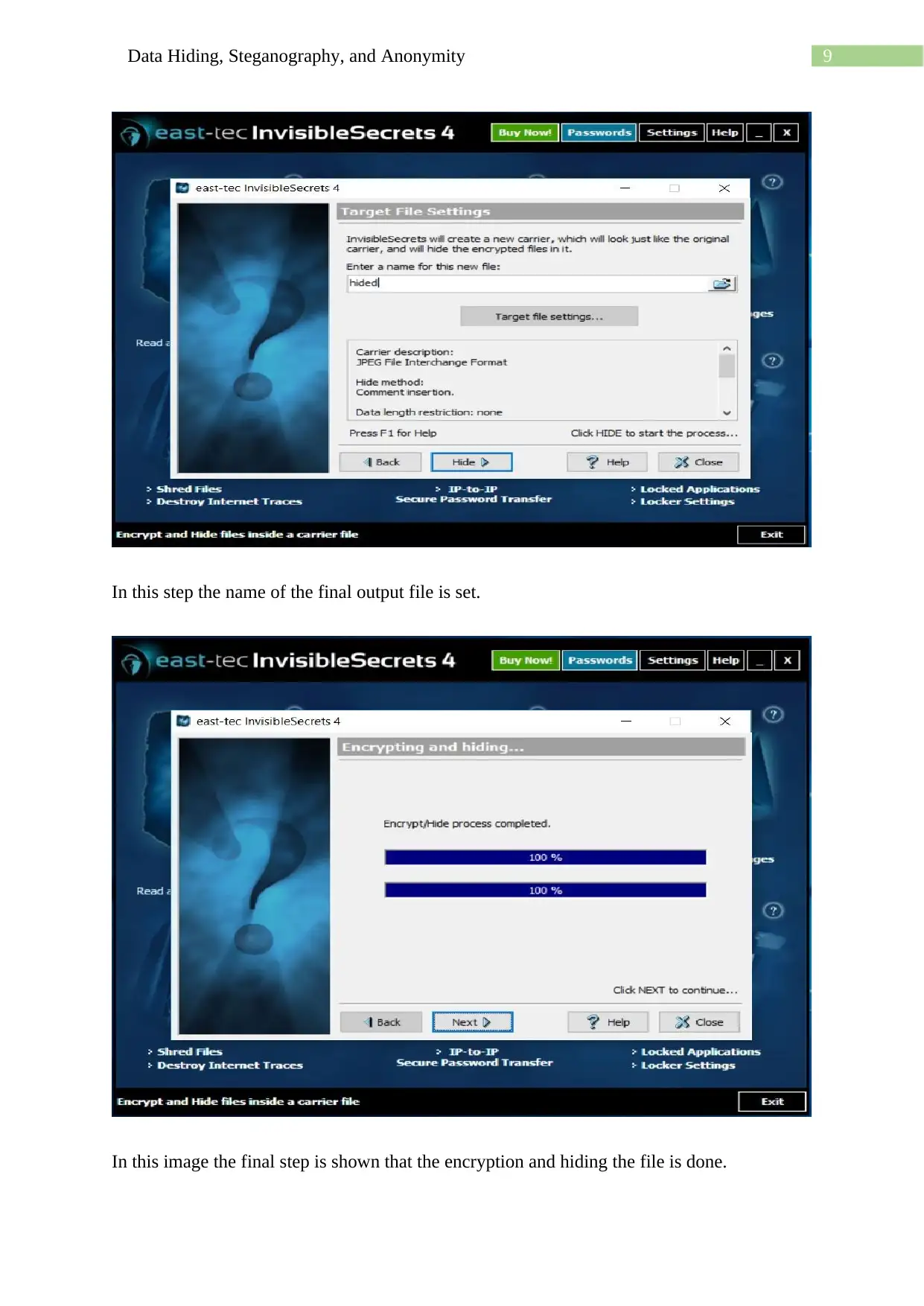
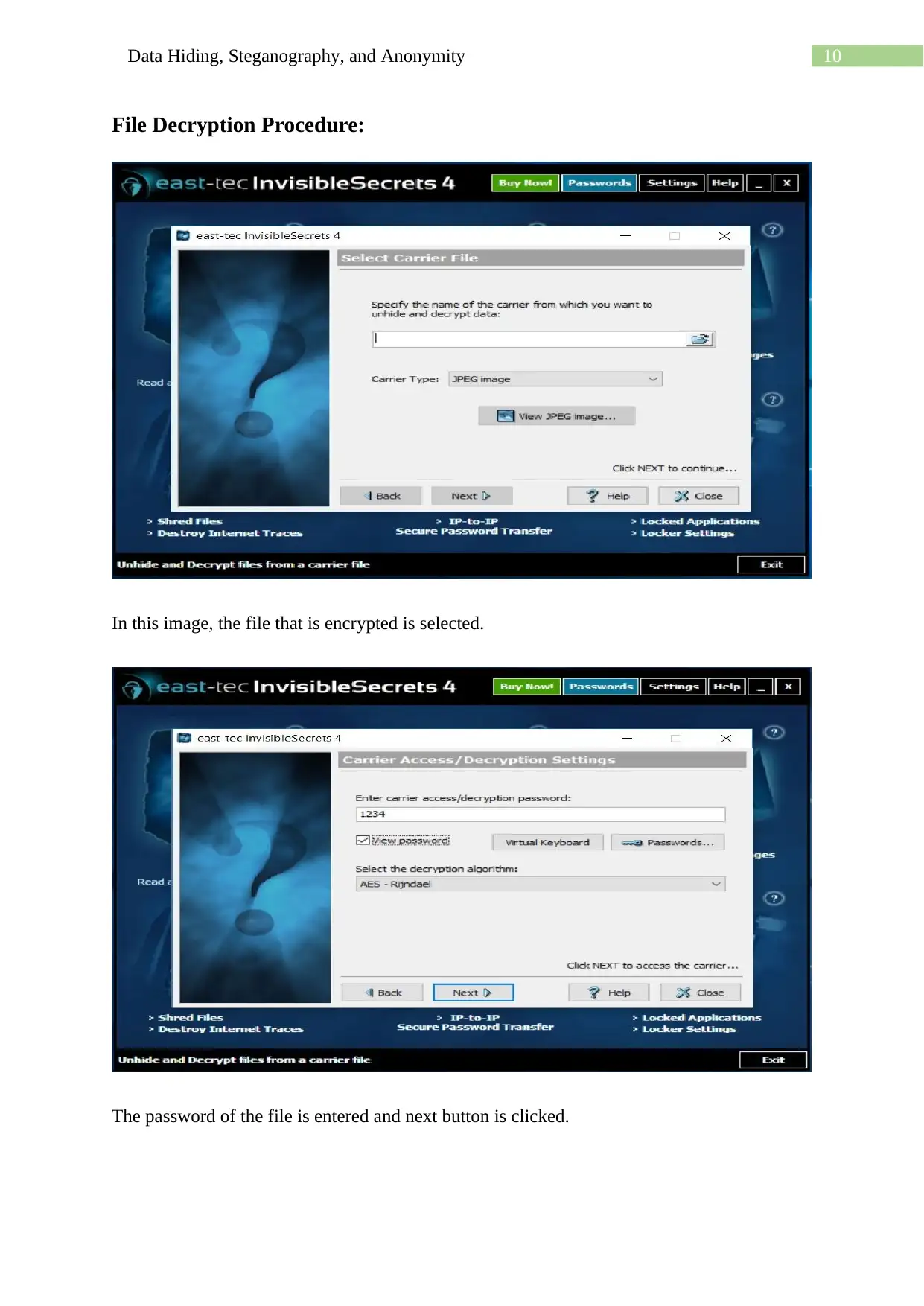
Homework Assignment
AI Summary
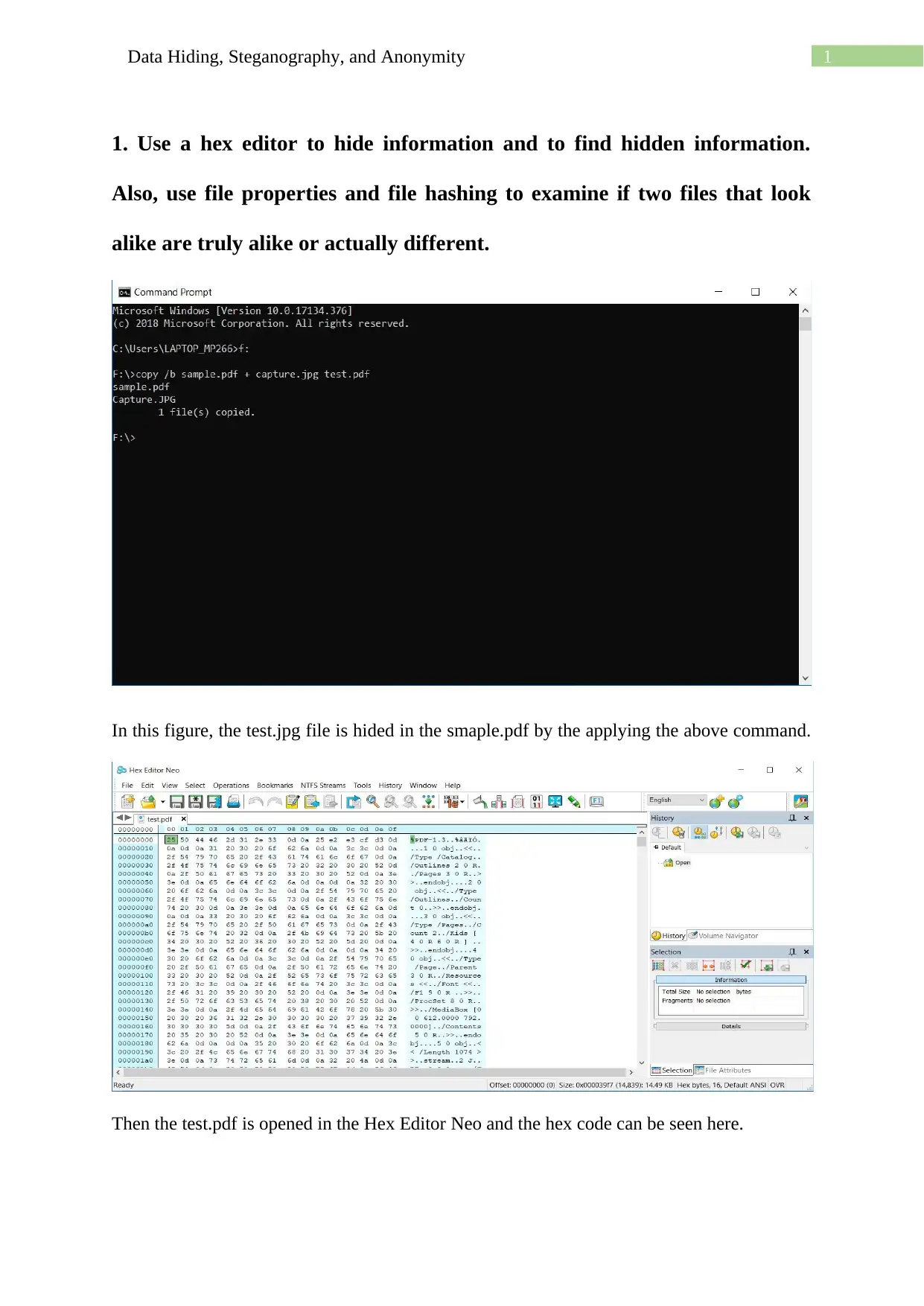
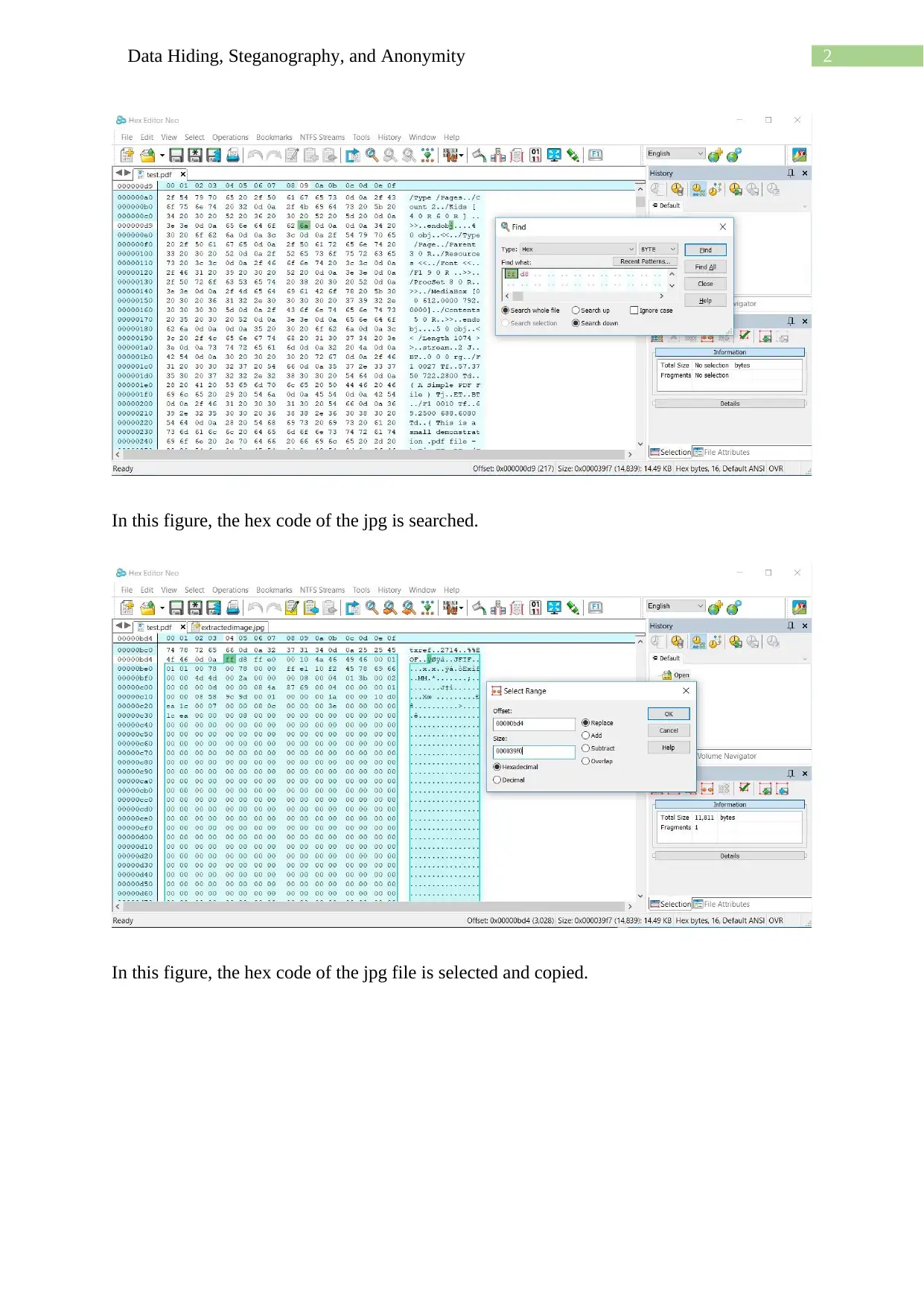
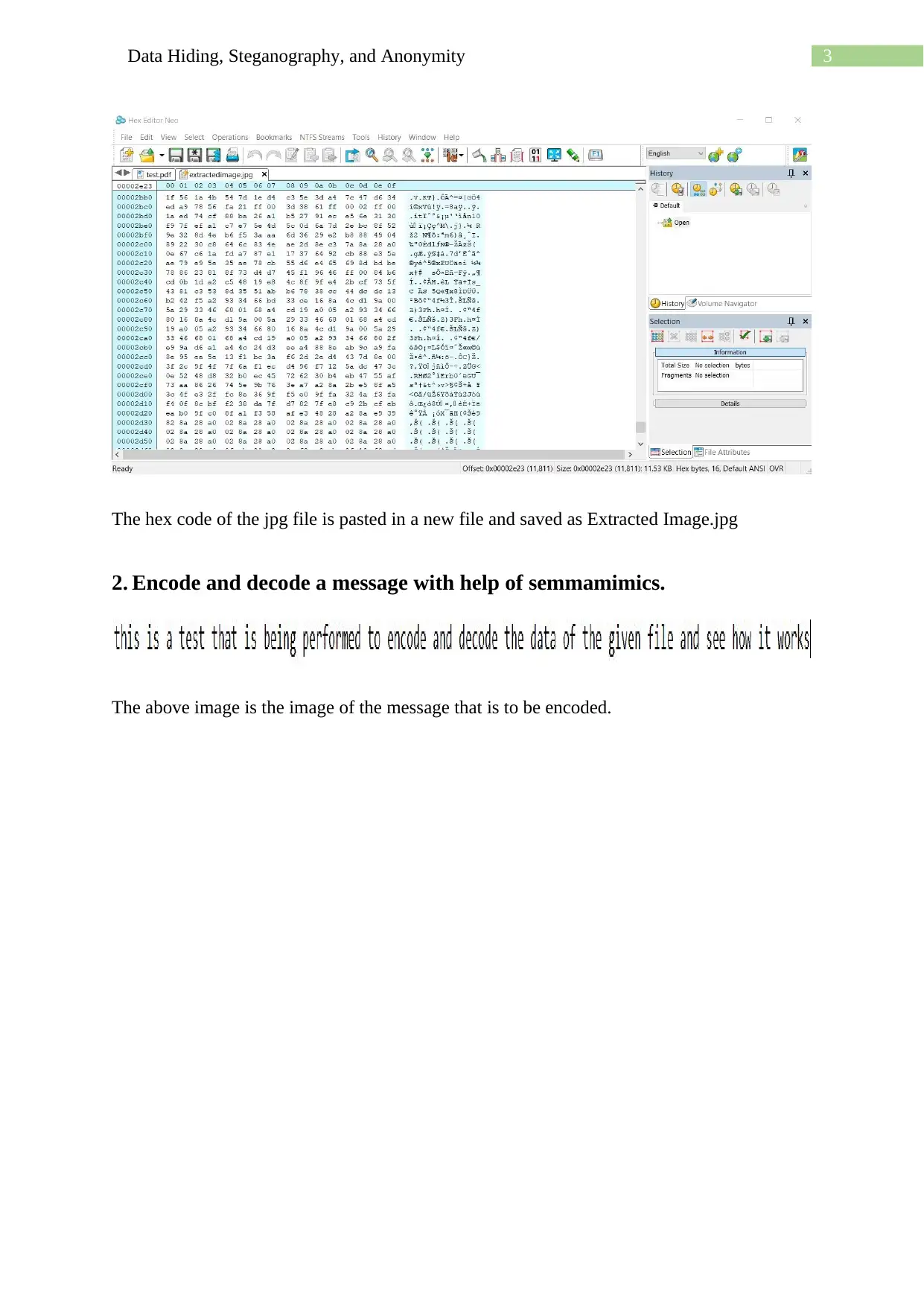
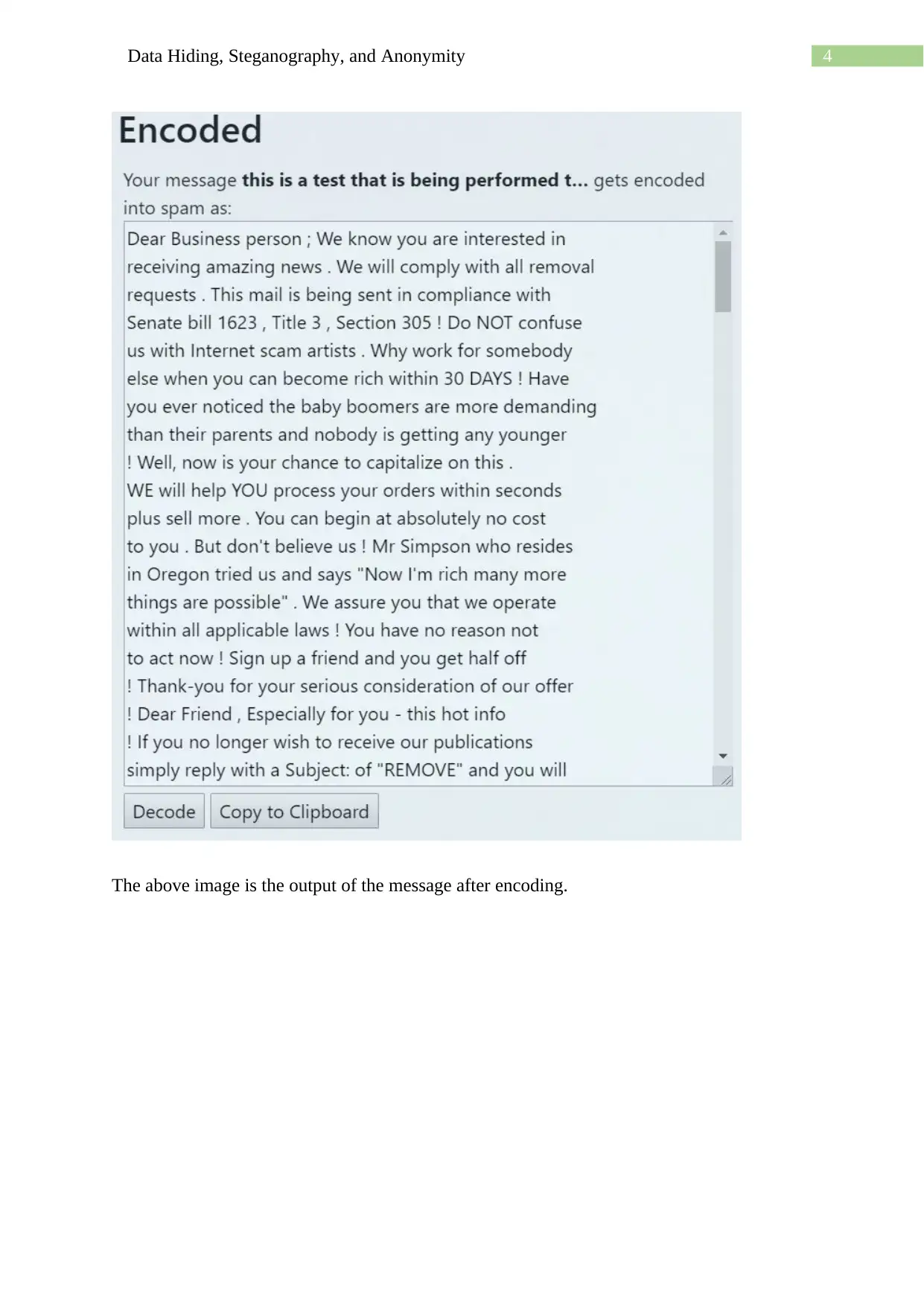
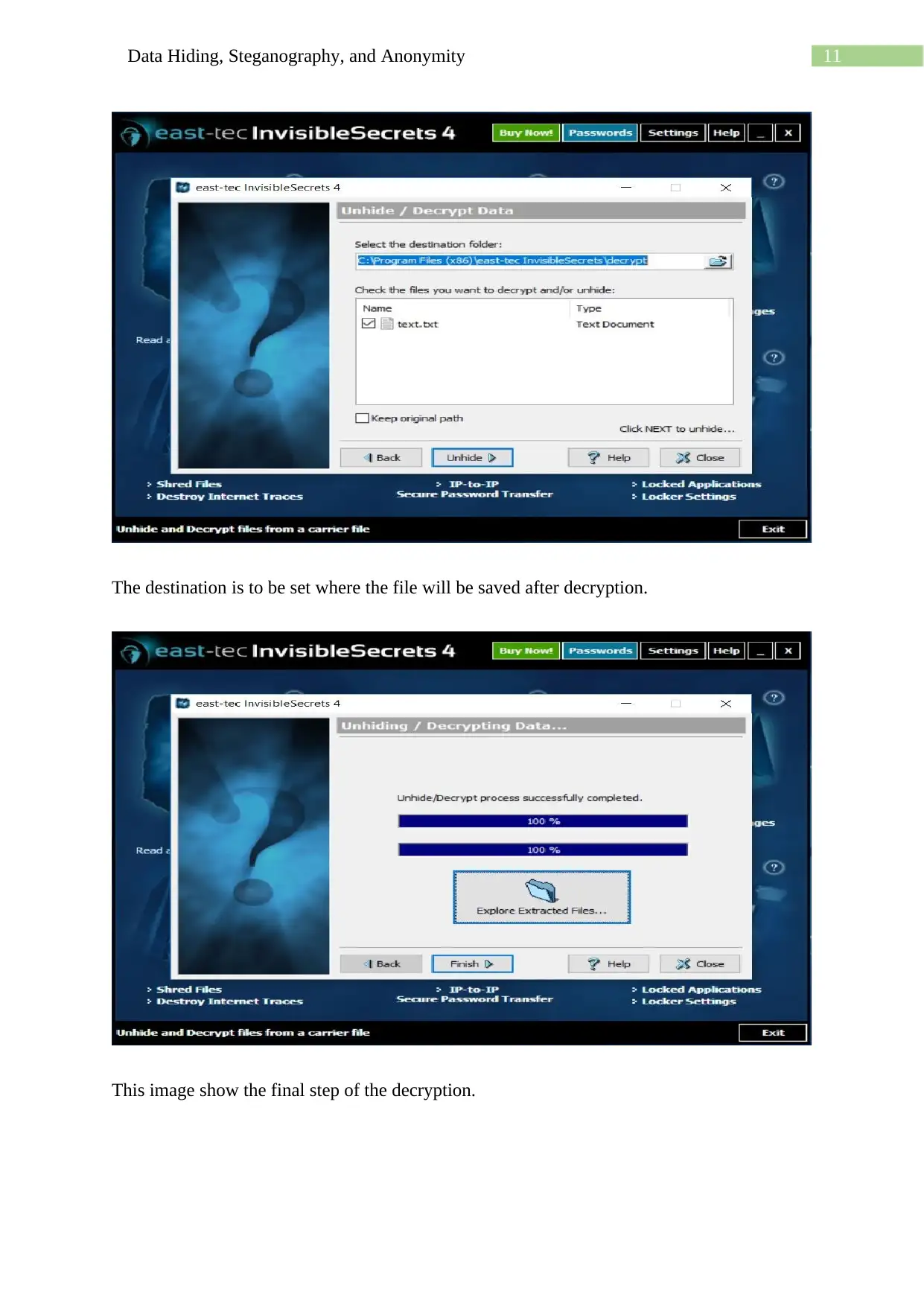
This assignment delves into the techniques of data hiding, steganography, and anonymity, showcasing practical applications using various methods. It begins with using a hex editor to hide and find information within files, along with examining file properties and hashing to differentiate similar-looking files. The assignment then explores message encoding and decoding using semmamimics, followed by decoding hidden messages using methods like Null Cipher. Finally, it demonstrates data hiding within a JPG file using Invisible Secrets, including the encryption and decryption procedures, complete with file hashing and password protection. The assignment provides a comprehensive overview of different approaches to concealing data and ensuring anonymity.
1 out of 13





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)