Using OpenSSL to Generate Digital Certificates
VerifiedAdded on 2024/06/04
|18
|5004
|246
AI Summary
This report delves into the use of OpenSSL for generating digital certificates, exploring its functionalities and significance in securing online communication. It covers the core concepts of OpenSSL, its role in TLS and SSL protocols, and the process of creating digital certificates. The report also examines the importance of digital certificates in ensuring data privacy, authenticity, and integrity, highlighting their role in protecting sensitive information during online transactions and communication. The report concludes by discussing the future scope of digital certificates and their potential for enhancing online security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Using OpenSSL to generate Digital Certificates
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction...........................................................................................................................................2
Literature review...................................................................................................................................4
Methodologies......................................................................................................................................7
Experiment Analysis with identify Cryptography technique (for security)..........................................10
Future scope........................................................................................................................................14
Conclusion...........................................................................................................................................15
References...........................................................................................................................................16
1
Introduction...........................................................................................................................................2
Literature review...................................................................................................................................4
Methodologies......................................................................................................................................7
Experiment Analysis with identify Cryptography technique (for security)..........................................10
Future scope........................................................................................................................................14
Conclusion...........................................................................................................................................15
References...........................................................................................................................................16
1

Introduction
The report is all about discussing usage of OpenSSL for generating digital certificates in brief. The
report will briefly cover the parts of OpenSSL used in making digital certificates. OpenSSL is a tool
which consisting of qualities such as overwhelming, finish ensured, Endeavour audit which is used in
conditions like transport layer security (TLS) and Secure socket layer (SSL). It can also be used for
performing cryptography. It works as a software library for various applications that can be used to
provide a secured communication in a computer network. It can also be used to identify the parties
that are taking part I the communication. Due to its various features, it is widely used in internet
webs servers and provides its features to them. It is open source software and can be used for TLS
and SSL protocols. Its core library is written in C language and can be used to implement
cryptographic functions which in turn can provide various securities based utility functions. Due to
its wrapping facility, it can be used with various computer languages available (Liu, 2015).
OpenSSL has an apache style license which means it is free to use whether it is commercial or non-
commercial. This is due to its simple conditions which allow the user to use the service considering
no worry. Now discussing its versions it started in 1998 when the product was launched and the first
version was 1.0. In April 2014 a bug came in its TLS heartbeat extension which released up to 64 KB
memory per memory. This was named as Heartbleed bug an attacked half million web users on the
internet the current version of the OpenSSL is named as 1.0.1G and is the improvement of the bug
named Heartbleed. It can be used with public key infrastructure and HTTPS also (HTTP and TLs).
Since OpenSSL is used in TLS and SSL one should have known about both of them. TLS can be said as
a successor to Secure sockets layer protocol (SSL). It is used to provide a secure and reliable end to
end communication. It is used in popular services like email, internet faxing, and various services
using data transfer. The TLS 1.0 is same as SSL 3.0 because of having same protocol. TLS operates in
the application layer of the OSI model. TLS generates a handshake protocol which is used to
determine client and server at both the ends. Also, it ensures to begin a cryptographic algorithm
through which client and server can share their messages securely. So before data exchange, the
communication is established using handshake protocol which ensures that client and server are
connected to each other in a network. This provides authenticity to the network and the client-
server identify each other. In between communication, TLS ensures that no third party user can
access any data in between the communication. It protects the external users from attacking the
network. TLS's main goal is to provide security and integrity. TLS version 1.0 is used in RFC
documentary (Liu, 2015).
2
The report is all about discussing usage of OpenSSL for generating digital certificates in brief. The
report will briefly cover the parts of OpenSSL used in making digital certificates. OpenSSL is a tool
which consisting of qualities such as overwhelming, finish ensured, Endeavour audit which is used in
conditions like transport layer security (TLS) and Secure socket layer (SSL). It can also be used for
performing cryptography. It works as a software library for various applications that can be used to
provide a secured communication in a computer network. It can also be used to identify the parties
that are taking part I the communication. Due to its various features, it is widely used in internet
webs servers and provides its features to them. It is open source software and can be used for TLS
and SSL protocols. Its core library is written in C language and can be used to implement
cryptographic functions which in turn can provide various securities based utility functions. Due to
its wrapping facility, it can be used with various computer languages available (Liu, 2015).
OpenSSL has an apache style license which means it is free to use whether it is commercial or non-
commercial. This is due to its simple conditions which allow the user to use the service considering
no worry. Now discussing its versions it started in 1998 when the product was launched and the first
version was 1.0. In April 2014 a bug came in its TLS heartbeat extension which released up to 64 KB
memory per memory. This was named as Heartbleed bug an attacked half million web users on the
internet the current version of the OpenSSL is named as 1.0.1G and is the improvement of the bug
named Heartbleed. It can be used with public key infrastructure and HTTPS also (HTTP and TLs).
Since OpenSSL is used in TLS and SSL one should have known about both of them. TLS can be said as
a successor to Secure sockets layer protocol (SSL). It is used to provide a secure and reliable end to
end communication. It is used in popular services like email, internet faxing, and various services
using data transfer. The TLS 1.0 is same as SSL 3.0 because of having same protocol. TLS operates in
the application layer of the OSI model. TLS generates a handshake protocol which is used to
determine client and server at both the ends. Also, it ensures to begin a cryptographic algorithm
through which client and server can share their messages securely. So before data exchange, the
communication is established using handshake protocol which ensures that client and server are
connected to each other in a network. This provides authenticity to the network and the client-
server identify each other. In between communication, TLS ensures that no third party user can
access any data in between the communication. It protects the external users from attacking the
network. TLS's main goal is to provide security and integrity. TLS version 1.0 is used in RFC
documentary (Liu, 2015).
2

When communicating online SSL creates encrypted links between client and server so as to provide
a secure and better communication between them. When using SSL it is to be sure that the data
transmitted will be encrypted at its best level. For establishing an SSL connection it is necessary to
generate SSL certificate. There are two cryptographic keys which are used: a private key and public
key. An SSL certificate consists of the domain name, company name, and other details. Forgetting a
certificate, a certificate signing request should be created. Now the CSR file is then sent to SSL
certificate that creates public and private keys for the server. The certification Authority and CSR
data are used for making public and private keys (Arthur, 2015).
Digital certificate can be said as an electronic password that can be used to secure a connection
using public key cryptography. Digital certificates are used in information security systems and are
the main part of RSA algorithm. RSA uses public key cryptography method in which it resides. The
main aim of digital certificate is to provide privacy of data to client and server. It is also knows as
public key certificate and identity certificate. It is issued by a trusted authority named certification
authority. They are used in message encryption. It works as:
The certification authority provides a digital certificate to sender with sender's public key. The
sender has its public key and public key of CA with him at the time of sending message. When the
message is being send the sender collects the essentials like its public key, CA's public key, data to be
send and many more. Now these essentials are sent as a whole message to the receiver. At the
receiver's end it is provided with the public key of sender through which it can identify the sender
and decrypt the message. So the receiver identifies sender with help of digital certificate and thus
decrypts the message and receives it. IT also sends the sender an acknowledgement type message
that he has received his message securely. The information which is provided to sender is for
example name, serial number, date of expiration with digital certificate. This ensures the privacy of
message Digital certificate is one of the popular techniques used for security in internet. They assure
that the data communicated between sender and receiver gets contained with them only. There are
various cryptographic techniques available but with use of digital certificate one can trust with the
network. Digital certificates assure authenticity and legitimacy. The web servers that do not use or
that use fake digital certificates are not trusted one and they might not help in securing user's data.
The most used digital certificate is X509 (Shiakorn, 2017).
3
a secure and better communication between them. When using SSL it is to be sure that the data
transmitted will be encrypted at its best level. For establishing an SSL connection it is necessary to
generate SSL certificate. There are two cryptographic keys which are used: a private key and public
key. An SSL certificate consists of the domain name, company name, and other details. Forgetting a
certificate, a certificate signing request should be created. Now the CSR file is then sent to SSL
certificate that creates public and private keys for the server. The certification Authority and CSR
data are used for making public and private keys (Arthur, 2015).
Digital certificate can be said as an electronic password that can be used to secure a connection
using public key cryptography. Digital certificates are used in information security systems and are
the main part of RSA algorithm. RSA uses public key cryptography method in which it resides. The
main aim of digital certificate is to provide privacy of data to client and server. It is also knows as
public key certificate and identity certificate. It is issued by a trusted authority named certification
authority. They are used in message encryption. It works as:
The certification authority provides a digital certificate to sender with sender's public key. The
sender has its public key and public key of CA with him at the time of sending message. When the
message is being send the sender collects the essentials like its public key, CA's public key, data to be
send and many more. Now these essentials are sent as a whole message to the receiver. At the
receiver's end it is provided with the public key of sender through which it can identify the sender
and decrypt the message. So the receiver identifies sender with help of digital certificate and thus
decrypts the message and receives it. IT also sends the sender an acknowledgement type message
that he has received his message securely. The information which is provided to sender is for
example name, serial number, date of expiration with digital certificate. This ensures the privacy of
message Digital certificate is one of the popular techniques used for security in internet. They assure
that the data communicated between sender and receiver gets contained with them only. There are
various cryptographic techniques available but with use of digital certificate one can trust with the
network. Digital certificates assure authenticity and legitimacy. The web servers that do not use or
that use fake digital certificates are not trusted one and they might not help in securing user's data.
The most used digital certificate is X509 (Shiakorn, 2017).
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Literature review
As stated in (Kaur &anwar, 2016) the security is one of the most crucial tasks for any network. It is
considered that most of the assaults rely on wrong setup design but actually, it is due to the
imperfection of patron. Programming can arise additionally and rapidly. With the use of OpenSSL,
suites can be determined and measured with help of some special programs.To ensure security
there is a need for method/s which can be used for the purpose specified. It means whenever there
is a communication between the sender and a receiver there must be something that can protect
the message sharing between the two. These can be some passwords, login ids, and many more
(Airasvirta, 2016).
These methods used for security purposes are known as cryptographic methods. The first method
becomes is called SSL (comfortable connection layer) and the other method is called TLS (transport
layer protection). These methods are used in various protocols such as POP3S, SMTPS, IMPAS,
HTTPS, and AND STAMPS. These methods are used from the OpenSSL libraries to pass on the
customer. There are various techniques used in case of different encryption algorithms. For example
in case of AES a mass encryption computation is used, in case of SHA message affirmation code is
used to hide the messages with help of public and private keys. There can be various features of
cryptography which are used to utilize testimony, and characterizing the symmetric key, and
checking the message check code (MAC). For permitting every technique an association should
present it in a right manner. After permitting the association takes the responsibility of installing the
cryptography technique and authorizes it. Also, a complete relationship should be there between
client and server. For example, the web server uses TCP protocol but the client is a new one and
does not know much about security and protocols. So to know about all this the client asks for server
about it. Operate this customer sends a hello message to the server with 5 elements: self assertive
number, a consultation ID, a discern suite and a weighting methodology, higher type of SSL which
can be used. The self assertive number is used to check the condition and status of server.
Consultation id is for parameter exchanging, weighting methodology is used orchestrated once over
with discern suite (Arthur, 2015).
4
As stated in (Kaur &anwar, 2016) the security is one of the most crucial tasks for any network. It is
considered that most of the assaults rely on wrong setup design but actually, it is due to the
imperfection of patron. Programming can arise additionally and rapidly. With the use of OpenSSL,
suites can be determined and measured with help of some special programs.To ensure security
there is a need for method/s which can be used for the purpose specified. It means whenever there
is a communication between the sender and a receiver there must be something that can protect
the message sharing between the two. These can be some passwords, login ids, and many more
(Airasvirta, 2016).
These methods used for security purposes are known as cryptographic methods. The first method
becomes is called SSL (comfortable connection layer) and the other method is called TLS (transport
layer protection). These methods are used in various protocols such as POP3S, SMTPS, IMPAS,
HTTPS, and AND STAMPS. These methods are used from the OpenSSL libraries to pass on the
customer. There are various techniques used in case of different encryption algorithms. For example
in case of AES a mass encryption computation is used, in case of SHA message affirmation code is
used to hide the messages with help of public and private keys. There can be various features of
cryptography which are used to utilize testimony, and characterizing the symmetric key, and
checking the message check code (MAC). For permitting every technique an association should
present it in a right manner. After permitting the association takes the responsibility of installing the
cryptography technique and authorizes it. Also, a complete relationship should be there between
client and server. For example, the web server uses TCP protocol but the client is a new one and
does not know much about security and protocols. So to know about all this the client asks for server
about it. Operate this customer sends a hello message to the server with 5 elements: self assertive
number, a consultation ID, a discern suite and a weighting methodology, higher type of SSL which
can be used. The self assertive number is used to check the condition and status of server.
Consultation id is for parameter exchanging, weighting methodology is used orchestrated once over
with discern suite (Arthur, 2015).
4
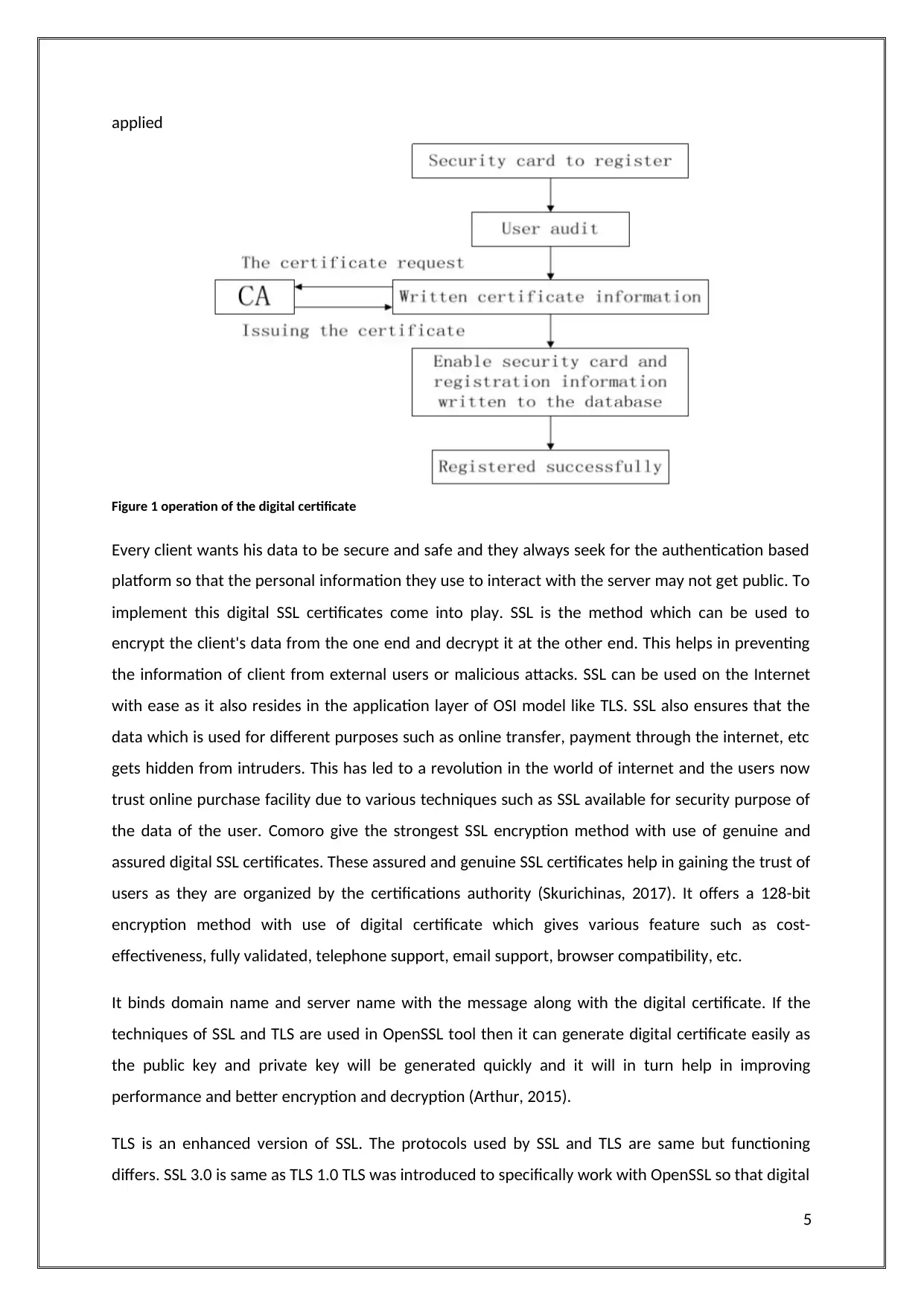
applied
Figure 1 operation of the digital certificate
Every client wants his data to be secure and safe and they always seek for the authentication based
platform so that the personal information they use to interact with the server may not get public. To
implement this digital SSL certificates come into play. SSL is the method which can be used to
encrypt the client's data from the one end and decrypt it at the other end. This helps in preventing
the information of client from external users or malicious attacks. SSL can be used on the Internet
with ease as it also resides in the application layer of OSI model like TLS. SSL also ensures that the
data which is used for different purposes such as online transfer, payment through the internet, etc
gets hidden from intruders. This has led to a revolution in the world of internet and the users now
trust online purchase facility due to various techniques such as SSL available for security purpose of
the data of the user. Comoro give the strongest SSL encryption method with use of genuine and
assured digital SSL certificates. These assured and genuine SSL certificates help in gaining the trust of
users as they are organized by the certifications authority (Skurichinas, 2017). It offers a 128-bit
encryption method with use of digital certificate which gives various feature such as cost-
effectiveness, fully validated, telephone support, email support, browser compatibility, etc.
It binds domain name and server name with the message along with the digital certificate. If the
techniques of SSL and TLS are used in OpenSSL tool then it can generate digital certificate easily as
the public key and private key will be generated quickly and it will in turn help in improving
performance and better encryption and decryption (Arthur, 2015).
TLS is an enhanced version of SSL. The protocols used by SSL and TLS are same but functioning
differs. SSL 3.0 is same as TLS 1.0 TLS was introduced to specifically work with OpenSSL so that digital
5
Figure 1 operation of the digital certificate
Every client wants his data to be secure and safe and they always seek for the authentication based
platform so that the personal information they use to interact with the server may not get public. To
implement this digital SSL certificates come into play. SSL is the method which can be used to
encrypt the client's data from the one end and decrypt it at the other end. This helps in preventing
the information of client from external users or malicious attacks. SSL can be used on the Internet
with ease as it also resides in the application layer of OSI model like TLS. SSL also ensures that the
data which is used for different purposes such as online transfer, payment through the internet, etc
gets hidden from intruders. This has led to a revolution in the world of internet and the users now
trust online purchase facility due to various techniques such as SSL available for security purpose of
the data of the user. Comoro give the strongest SSL encryption method with use of genuine and
assured digital SSL certificates. These assured and genuine SSL certificates help in gaining the trust of
users as they are organized by the certifications authority (Skurichinas, 2017). It offers a 128-bit
encryption method with use of digital certificate which gives various feature such as cost-
effectiveness, fully validated, telephone support, email support, browser compatibility, etc.
It binds domain name and server name with the message along with the digital certificate. If the
techniques of SSL and TLS are used in OpenSSL tool then it can generate digital certificate easily as
the public key and private key will be generated quickly and it will in turn help in improving
performance and better encryption and decryption (Arthur, 2015).
TLS is an enhanced version of SSL. The protocols used by SSL and TLS are same but functioning
differs. SSL 3.0 is same as TLS 1.0 TLS was introduced to specifically work with OpenSSL so that digital
5

certificates can be generated quickly. TLS comes as an advantage of SSL limitations. OpenSSL has a
library which includes various techniques that are to be used with the TLS technique for securing
user's data. The OpenSSL tool can be implemented with various techniques that is why it is mostly
used for generating certificates. The digital certificates ensure trust between client and server by
keeping the data safe between the servers. It also improves the business conversion rates as the
most used tool will require various updates and terminologies (Kabtoul, 2017).
6
library which includes various techniques that are to be used with the TLS technique for securing
user's data. The OpenSSL tool can be implemented with various techniques that is why it is mostly
used for generating certificates. The digital certificates ensure trust between client and server by
keeping the data safe between the servers. It also improves the business conversion rates as the
most used tool will require various updates and terminologies (Kabtoul, 2017).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Methodologies
To ensure the best security the encryption standard used should be up to mark. There can be various
methods that can be used with OpenSSL to generate the certificates and keys but the best standard
encryption should be used for high performance and efficiency. Therefore SAS defines high
encryption standards for securing deployment
There are various steps which are to be followed to generate a certificate:
Step 1: Generating a new RSA private key and CSR:
1. create an openssl.conf file or if an existing file is there then edit that file
2. Select the directory of OpenSSL
3. Initialize OpenSSL using $openssl
4. For requesting digital certificate appropriate command should be issued
5. After requesting commands the information message is displayed and any other additional
information is also displayed on the screen. Press the enter key to accept the value. For
editing, a default value types the information and then presses enter (Pancholli, 2016).
Step 2: Generate a public certificate from an existing certificate:
1. for generating public certificate enter the specific command with help of certificate signing
request
2. International messages are displayed on the screen and additional information is prompted
accordingly. For accepting the default value enter is used and for editing, some kind of
editing option is required.
3. after generation of the public certificate, a discriminated name is acquired
Step 3: Secure your private key file:
1. The password is used to restrict the external user from accessing the information.
2. Passwords are made by using various special characters and numbers to make it strong and
unbreakable
3. Passwords can be made during generation of the private key or they can be made afterward
Step 4: Check digital certificate using OpenSSL:
To check, enter the following command:
7
To ensure the best security the encryption standard used should be up to mark. There can be various
methods that can be used with OpenSSL to generate the certificates and keys but the best standard
encryption should be used for high performance and efficiency. Therefore SAS defines high
encryption standards for securing deployment
There are various steps which are to be followed to generate a certificate:
Step 1: Generating a new RSA private key and CSR:
1. create an openssl.conf file or if an existing file is there then edit that file
2. Select the directory of OpenSSL
3. Initialize OpenSSL using $openssl
4. For requesting digital certificate appropriate command should be issued
5. After requesting commands the information message is displayed and any other additional
information is also displayed on the screen. Press the enter key to accept the value. For
editing, a default value types the information and then presses enter (Pancholli, 2016).
Step 2: Generate a public certificate from an existing certificate:
1. for generating public certificate enter the specific command with help of certificate signing
request
2. International messages are displayed on the screen and additional information is prompted
accordingly. For accepting the default value enter is used and for editing, some kind of
editing option is required.
3. after generation of the public certificate, a discriminated name is acquired
Step 3: Secure your private key file:
1. The password is used to restrict the external user from accessing the information.
2. Passwords are made by using various special characters and numbers to make it strong and
unbreakable
3. Passwords can be made during generation of the private key or they can be made afterward
Step 4: Check digital certificate using OpenSSL:
To check, enter the following command:
7

openssl> x509 - text -in filename.pm (Keller,2017)
Step 5: After generation of the digital certificate, identifying client and server the OpenSSL is
identified. It means the library; current version and many more elements of it are identified.
Step 6: Verify certificates in trust chain using OpenSSL:
Client and server verify each other's digital certificates in this step. All of the certificates used in a
procedure form like a chain and they are verified one by one. The command used for verification is:
openssl verify -verbose -CA file <your CA-file>.pem<your-server-cert>.pem.
Ok, message is displayed if the local OpenSSL verifies all the certificates successfully.
Step 7: End OpenSSL:
To exit OpenSSL, press on quit button.
Digital certificates are used for security purpose of the network and client-server architecture. It is a
cryptographic technique and is mostly used in internet facility. The main aim is to achieve
authenticity which means that the sender and receiver know about each other and the message they
receive is from a trusted one. Various encryption techniques are used to provide authenticity. The
sender is issued with its private key from the certifications authority and a public key of the sender is
also issued. The sender sends his message along with a digital certificate and private key of the
sender in an encrypted form. The receiver receives the message and performs verification with help
of digital certificate. If verified the receiver uses the public key of the sender to decrypt the message
and sends an acknowledgment type message in reply (Martin, 2016).
There are various types of Digital Certificates, these are;
1. Secure Socket Layer Certificate
2. Programming Signing
3. Client Certificate
Secure Socket Layer
Secure Socket Layer server Certificates provide their services in the web server. Mainly used in email,
the mail server regularly checks for the requirements which are needed to perform the operation. It
uses the automated delivery system and authentication system to make the procedure automatic.
8
Step 5: After generation of the digital certificate, identifying client and server the OpenSSL is
identified. It means the library; current version and many more elements of it are identified.
Step 6: Verify certificates in trust chain using OpenSSL:
Client and server verify each other's digital certificates in this step. All of the certificates used in a
procedure form like a chain and they are verified one by one. The command used for verification is:
openssl verify -verbose -CA file <your CA-file>.pem<your-server-cert>.pem.
Ok, message is displayed if the local OpenSSL verifies all the certificates successfully.
Step 7: End OpenSSL:
To exit OpenSSL, press on quit button.
Digital certificates are used for security purpose of the network and client-server architecture. It is a
cryptographic technique and is mostly used in internet facility. The main aim is to achieve
authenticity which means that the sender and receiver know about each other and the message they
receive is from a trusted one. Various encryption techniques are used to provide authenticity. The
sender is issued with its private key from the certifications authority and a public key of the sender is
also issued. The sender sends his message along with a digital certificate and private key of the
sender in an encrypted form. The receiver receives the message and performs verification with help
of digital certificate. If verified the receiver uses the public key of the sender to decrypt the message
and sends an acknowledgment type message in reply (Martin, 2016).
There are various types of Digital Certificates, these are;
1. Secure Socket Layer Certificate
2. Programming Signing
3. Client Certificate
Secure Socket Layer
Secure Socket Layer server Certificates provide their services in the web server. Mainly used in email,
the mail server regularly checks for the requirements which are needed to perform the operation. It
uses the automated delivery system and authentication system to make the procedure automatic.
8

Now the mail can be transferred by using encryption-decryption methods and digital certificates in
an automated fashion (Reddy, 2018).
Code Signing Certificate
Code signing certificates are used to add an assurance layer that indicates users the software they
are using is up to mark and trusted. Also, it specifies that it does not come via malware. It allows the
developers to sign their software in a digital manner before it is available for use to the users on the
internet. The certificate is of 32 bit or 64 bit and assures that there are no modifications in the data
used.
Features: Trusted outlet, improved software downloads high customer confidence, strong integrity,
high compatibility, content authenticity, verified identity (Chuchra, 2017).
Client Certificate
What when a client wants to access data from the server and it wishes to perform an authentication
check on the data to be used. For that purpose, client certificates are used. It is a type of digital
certificates which is used by the client to ensure that the request for data from the client to server
remains to be secured by means of authentication. To install the certificate you must take it from a
certified user like Comodo. The certificate consists of public-private key infrastructure which is highly
secured. It is like SSL certificate instead the client keeps the private key throughout the procedure.
To provide a better authentication and confidentiality SSL certificates are used. These are used to
ensure that the data used in exchange is not from an external one (Ma, 2017).
The SSL certificate is issued by a Certification authority which itself is a trusted organization for
providing certificates. The certification authority checks those areas where the use of certificates is
needed. With CA in the backend the certificate becomes to be a trusted one and the user easily
accepts that. There is a program which is generated by CA which tells the user that the website or
web server user is using is a trusted one and can be used for exchanging information (both public
and private). Due to this the user feels secure and uses that server for his work accordingly.
9
an automated fashion (Reddy, 2018).
Code Signing Certificate
Code signing certificates are used to add an assurance layer that indicates users the software they
are using is up to mark and trusted. Also, it specifies that it does not come via malware. It allows the
developers to sign their software in a digital manner before it is available for use to the users on the
internet. The certificate is of 32 bit or 64 bit and assures that there are no modifications in the data
used.
Features: Trusted outlet, improved software downloads high customer confidence, strong integrity,
high compatibility, content authenticity, verified identity (Chuchra, 2017).
Client Certificate
What when a client wants to access data from the server and it wishes to perform an authentication
check on the data to be used. For that purpose, client certificates are used. It is a type of digital
certificates which is used by the client to ensure that the request for data from the client to server
remains to be secured by means of authentication. To install the certificate you must take it from a
certified user like Comodo. The certificate consists of public-private key infrastructure which is highly
secured. It is like SSL certificate instead the client keeps the private key throughout the procedure.
To provide a better authentication and confidentiality SSL certificates are used. These are used to
ensure that the data used in exchange is not from an external one (Ma, 2017).
The SSL certificate is issued by a Certification authority which itself is a trusted organization for
providing certificates. The certification authority checks those areas where the use of certificates is
needed. With CA in the backend the certificate becomes to be a trusted one and the user easily
accepts that. There is a program which is generated by CA which tells the user that the website or
web server user is using is a trusted one and can be used for exchanging information (both public
and private). Due to this the user feels secure and uses that server for his work accordingly.
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
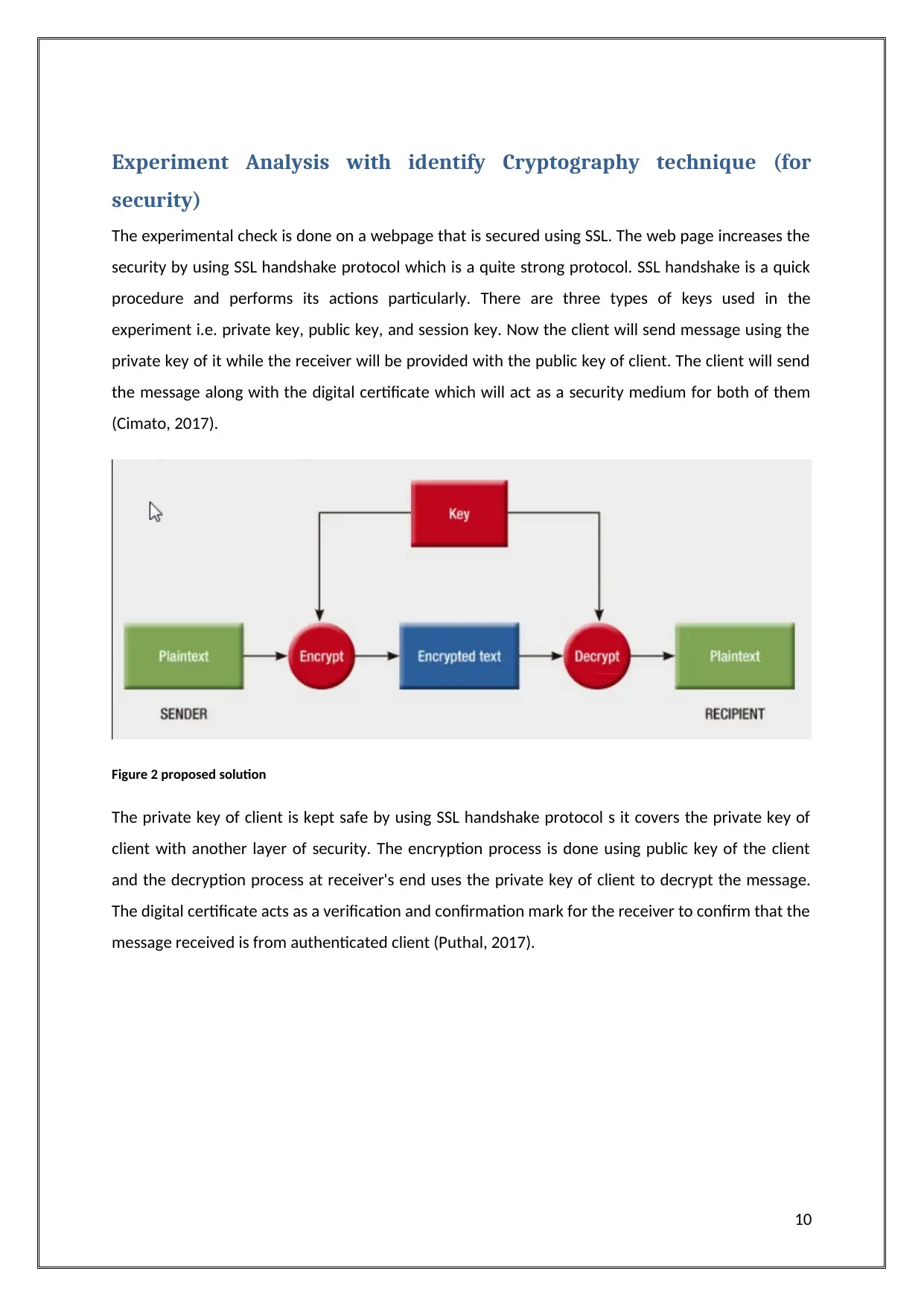
Experiment Analysis with identify Cryptography technique (for
security)
The experimental check is done on a webpage that is secured using SSL. The web page increases the
security by using SSL handshake protocol which is a quite strong protocol. SSL handshake is a quick
procedure and performs its actions particularly. There are three types of keys used in the
experiment i.e. private key, public key, and session key. Now the client will send message using the
private key of it while the receiver will be provided with the public key of client. The client will send
the message along with the digital certificate which will act as a security medium for both of them
(Cimato, 2017).
Figure 2 proposed solution
The private key of client is kept safe by using SSL handshake protocol s it covers the private key of
client with another layer of security. The encryption process is done using public key of the client
and the decryption process at receiver's end uses the private key of client to decrypt the message.
The digital certificate acts as a verification and confirmation mark for the receiver to confirm that the
message received is from authenticated client (Puthal, 2017).
10
security)
The experimental check is done on a webpage that is secured using SSL. The web page increases the
security by using SSL handshake protocol which is a quite strong protocol. SSL handshake is a quick
procedure and performs its actions particularly. There are three types of keys used in the
experiment i.e. private key, public key, and session key. Now the client will send message using the
private key of it while the receiver will be provided with the public key of client. The client will send
the message along with the digital certificate which will act as a security medium for both of them
(Cimato, 2017).
Figure 2 proposed solution
The private key of client is kept safe by using SSL handshake protocol s it covers the private key of
client with another layer of security. The encryption process is done using public key of the client
and the decryption process at receiver's end uses the private key of client to decrypt the message.
The digital certificate acts as a verification and confirmation mark for the receiver to confirm that the
message received is from authenticated client (Puthal, 2017).
10
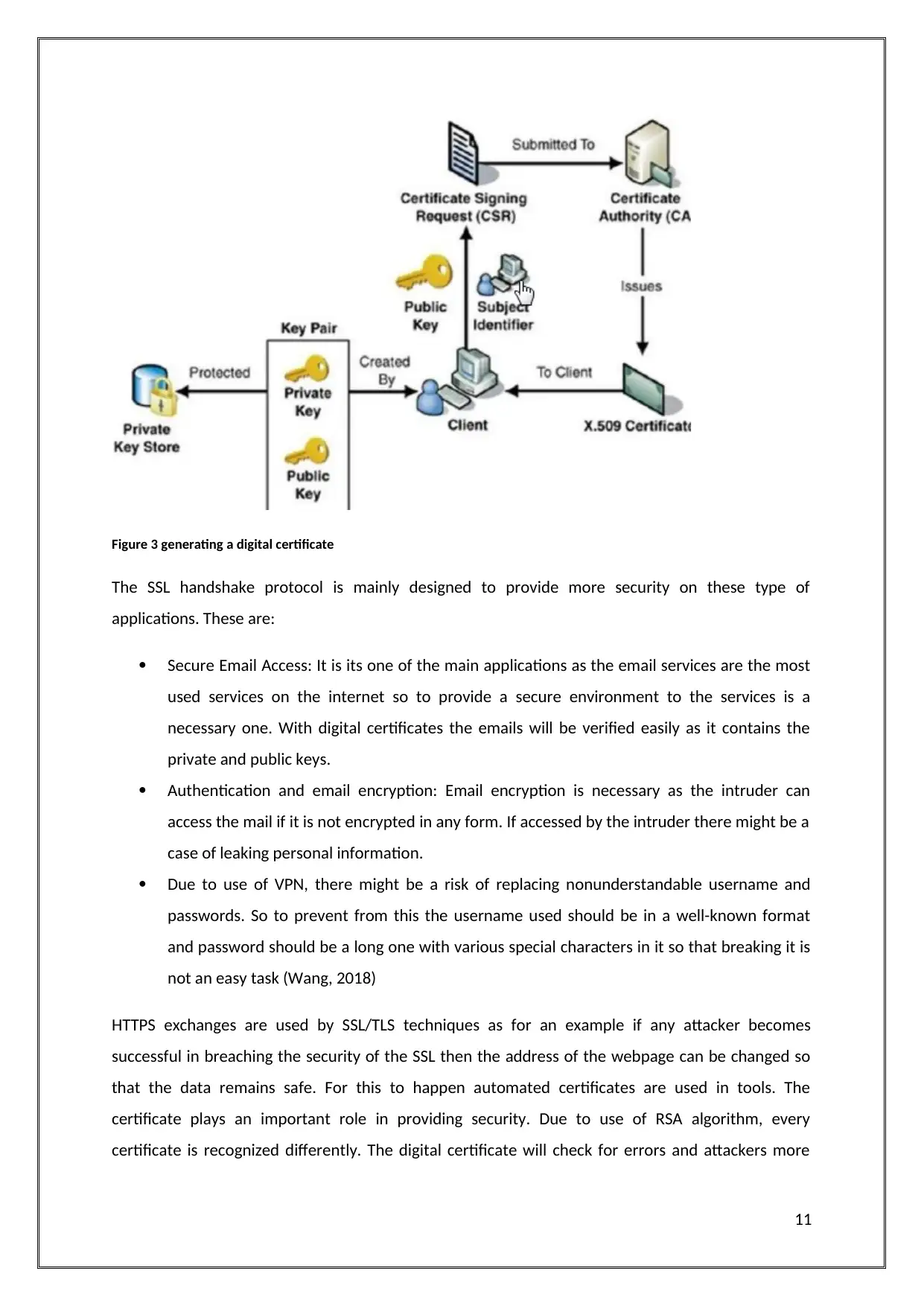
Figure 3 generating a digital certificate
The SSL handshake protocol is mainly designed to provide more security on these type of
applications. These are:
Secure Email Access: It is its one of the main applications as the email services are the most
used services on the internet so to provide a secure environment to the services is a
necessary one. With digital certificates the emails will be verified easily as it contains the
private and public keys.
Authentication and email encryption: Email encryption is necessary as the intruder can
access the mail if it is not encrypted in any form. If accessed by the intruder there might be a
case of leaking personal information.
Due to use of VPN, there might be a risk of replacing nonunderstandable username and
passwords. So to prevent from this the username used should be in a well-known format
and password should be a long one with various special characters in it so that breaking it is
not an easy task (Wang, 2018)
HTTPS exchanges are used by SSL/TLS techniques as for an example if any attacker becomes
successful in breaching the security of the SSL then the address of the webpage can be changed so
that the data remains safe. For this to happen automated certificates are used in tools. The
certificate plays an important role in providing security. Due to use of RSA algorithm, every
certificate is recognized differently. The digital certificate will check for errors and attackers more
11
The SSL handshake protocol is mainly designed to provide more security on these type of
applications. These are:
Secure Email Access: It is its one of the main applications as the email services are the most
used services on the internet so to provide a secure environment to the services is a
necessary one. With digital certificates the emails will be verified easily as it contains the
private and public keys.
Authentication and email encryption: Email encryption is necessary as the intruder can
access the mail if it is not encrypted in any form. If accessed by the intruder there might be a
case of leaking personal information.
Due to use of VPN, there might be a risk of replacing nonunderstandable username and
passwords. So to prevent from this the username used should be in a well-known format
and password should be a long one with various special characters in it so that breaking it is
not an easy task (Wang, 2018)
HTTPS exchanges are used by SSL/TLS techniques as for an example if any attacker becomes
successful in breaching the security of the SSL then the address of the webpage can be changed so
that the data remains safe. For this to happen automated certificates are used in tools. The
certificate plays an important role in providing security. Due to use of RSA algorithm, every
certificate is recognized differently. The digital certificate will check for errors and attackers more
11
deeply which will lead to better security. Also, an email will be encrypted in a new fashion so the
attacker has to begin from zero level again to breach the security level of the system
Use of OpenSSL digital certificates
It is used for generating web pages in HTTPS format.
Ensures safe data transfer between client and server
It provides trust and authentication with use of the certificate
The digital certificates provide security to user's private information with help of
authentication
It is used to eliminate warnings and alerts
These type of certificates increase trust on certification authority and improve their
reputation.
Figure 4 use of a digital certificate
There are many advantages of using SSL certificates but there are some cases where SSL certificates
might not perform up to mark. There are some issues related to the digital certificates such as SSL
and TLS certificates. These certificates are vulnerable to malware.
One of the examples of these malware is the Heartbleed virus that came in OpenSSL library which
gathered and deleted the data of half million users. At that time the certificates were not able to
provide proper security as that virus contained some features that were new for the OpenSSL
library. Therefore the virus destroyed the whole library and the authenticity and confidentiality of
the company came in trouble. Although after some time the virus was studied and then a new
12
attacker has to begin from zero level again to breach the security level of the system
Use of OpenSSL digital certificates
It is used for generating web pages in HTTPS format.
Ensures safe data transfer between client and server
It provides trust and authentication with use of the certificate
The digital certificates provide security to user's private information with help of
authentication
It is used to eliminate warnings and alerts
These type of certificates increase trust on certification authority and improve their
reputation.
Figure 4 use of a digital certificate
There are many advantages of using SSL certificates but there are some cases where SSL certificates
might not perform up to mark. There are some issues related to the digital certificates such as SSL
and TLS certificates. These certificates are vulnerable to malware.
One of the examples of these malware is the Heartbleed virus that came in OpenSSL library which
gathered and deleted the data of half million users. At that time the certificates were not able to
provide proper security as that virus contained some features that were new for the OpenSSL
library. Therefore the virus destroyed the whole library and the authenticity and confidentiality of
the company came in trouble. Although after some time the virus was studied and then a new
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

version of OpenSSL named 1.0.G was introduced which included a solution of that malware. Another
problem regarding these certificates is that they show many warnings and errors irrelevant to the
security (Pouliot, 2016).
13
problem regarding these certificates is that they show many warnings and errors irrelevant to the
security (Pouliot, 2016).
13

Future scope
The increasing demand of internet has increased the scope of digital certificates as the more
internet one use the more secure environment should be provided. Also, digital certificates are the
new way of encryption and can be updated as you need in future. It uses 128-bit encryption method
so to improve its confidentiality the organization certification authority can improve the digital
certificate by using 64 or 256-bit encryption keys. Digital certificates are in high demand over the
internet and thus are used by most trusted organizations. It helps in securing data over the internet
by using public key and private key combination. They are also used for solving issues like denial of
service. If the sender sends the message using digital certificate then he cannot deny at the other
end about not sending it. It means that digital certificate assures the authenticity of the user.
Though digital certificates might come with some problems in future as nothing is unbreakable but
the digital certificate imposes a property of self-updating which can help in getting rid of these
problems. The future study on digital certificates is like how to get a more secure environment
between client and server using latest certificates and various possible updates in the digital
certificate.
14
The increasing demand of internet has increased the scope of digital certificates as the more
internet one use the more secure environment should be provided. Also, digital certificates are the
new way of encryption and can be updated as you need in future. It uses 128-bit encryption method
so to improve its confidentiality the organization certification authority can improve the digital
certificate by using 64 or 256-bit encryption keys. Digital certificates are in high demand over the
internet and thus are used by most trusted organizations. It helps in securing data over the internet
by using public key and private key combination. They are also used for solving issues like denial of
service. If the sender sends the message using digital certificate then he cannot deny at the other
end about not sending it. It means that digital certificate assures the authenticity of the user.
Though digital certificates might come with some problems in future as nothing is unbreakable but
the digital certificate imposes a property of self-updating which can help in getting rid of these
problems. The future study on digital certificates is like how to get a more secure environment
between client and server using latest certificates and various possible updates in the digital
certificate.
14

Conclusion
The research report consists of various methodologies used for generating methods using OpenSSL.
The introduction part contains the brief introduction about tool OpenSSL which describes its libraries
and versions. OpenSSL can be used with TLS and SSL certificates to operate. Introduction part also
gives an introductory about SSL and TLS certificates and their operational areas. The literature
review contains review of different papers about generating digital certificates. It describes various
ways through which digital certificates can be generated with various algorithms involved in it.
Different algorithms can have different complexities so algorithms such as RSA use different
technique and SHA algorithm uses different for generation of digital certificates. Security is the main
concern of digital certificates as we know and SSL and TLs certificates can help in performing the way
it must be implemented. We have analyzed various research papers to write literature review and it
thus has helped us in gaining vast knowledge about digital certificate and its use. The method to
generate digital certificate using OpenSSL is shown in the next section which describe various ways
like SSL, code signing, and client certificates. These certificates can be used according to the amount
of security needed as per the instructions. The section also describes a procedure to generate
certificate using OpenSSL which gives a step by step procedure that is easy to understand and
implement. In the experimental section a test case is performed showing the implementation
process of generating the certificate using certification authority's encryption and decryption
method. It also describes various uses of SSL certificates with their advantages. In the future the
certificates be improved by using different key combinations and different algorithms. Digital
certificates are easy to update so they provide a long functioning system.
15
The research report consists of various methodologies used for generating methods using OpenSSL.
The introduction part contains the brief introduction about tool OpenSSL which describes its libraries
and versions. OpenSSL can be used with TLS and SSL certificates to operate. Introduction part also
gives an introductory about SSL and TLS certificates and their operational areas. The literature
review contains review of different papers about generating digital certificates. It describes various
ways through which digital certificates can be generated with various algorithms involved in it.
Different algorithms can have different complexities so algorithms such as RSA use different
technique and SHA algorithm uses different for generation of digital certificates. Security is the main
concern of digital certificates as we know and SSL and TLs certificates can help in performing the way
it must be implemented. We have analyzed various research papers to write literature review and it
thus has helped us in gaining vast knowledge about digital certificate and its use. The method to
generate digital certificate using OpenSSL is shown in the next section which describe various ways
like SSL, code signing, and client certificates. These certificates can be used according to the amount
of security needed as per the instructions. The section also describes a procedure to generate
certificate using OpenSSL which gives a step by step procedure that is easy to understand and
implement. In the experimental section a test case is performed showing the implementation
process of generating the certificate using certification authority's encryption and decryption
method. It also describes various uses of SSL certificates with their advantages. In the future the
certificates be improved by using different key combinations and different algorithms. Digital
certificates are easy to update so they provide a long functioning system.
15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Airasvirta, E.J., 2016. Versatile Authentication Methods for Web Applications.
Arthur, W. and Challener, D., 2015. A Practical Guide to TPM 2.0: Using the Trusted Platform
Module in the New Age of Security. Apress.
Chuchra, R. and Kaur, R., 2017. IMPLEMENTATION OF JSMEA (JOINT SELECTIVE MULTIMEDIA
ENCRYPTION ALGORITHM)-A PRIVACY ENHANCING STRATEGY. International Journal of
Advanced Research in Computer Science, 8(9), pp.266-269.
Cimato, S. and Yang, C.N. eds., 2017. Visual cryptography and secret image sharing. CRC
press.
Kabtoul, O., 2017. Last Mile Transfer: enabling local data transfers on the global WLCG
infrastructure.
Keller, M., Orsini, E., Rotaru, D., Scholl, P., Soria-Vazquez, E. and Vivek, S., 2017, July. Faster
secure multi-party computation of AES and DES using lookup tables. In International
Conference on Applied Cryptography and Network Security (pp. 229-249). Springer, Cham.
Liu, Y., Tome, W., Zhang, L., Choffnes, D., Levin, D., Maggs, B., Mislove, A., Schulman, A. and
Wilson, C., 2015, October. An end-to-end measurement of a certificate revocation in the
web's PKI. In Proceedings of the 2015 Internet Measurement Conference (pp. 183-196). ACM.
Ma, E.T.K., and Grider, S.N., Maxim Integrated Products Inc, 2017. Block encryption security
for integrated microcontroller and external memory system. U.S. Patent 9,773,431.
Martin, L.W., Spies, T. and Pauker, M.J., Voltage Security Inc, 2016. Format preserving
encryption methods for data strings with constraints. U.S. Patent 9,489,521.
Pancholi, V.R., and Patel, B.P., 2016. Enhancement of cloud computing security with secure
data storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), pp.18-21.
Pouliot, D. and Wright, C.V., 2016, October. The shadow nemesis: Inference attacks on
efficiently deployable, efficiently searchable encryption. In Proceedings of the 2016 ACM
SIGSAC Conference on Computer and Communications Security (pp. 1341-1352). ACM.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2017. A synchronized shared key generation
method for maintaining the end-to-end security of big data streams.
Reddy, K.R., and Rao, C.M., 2018, April. GUI implementation of image encryption and
decryption using Open CV-Python script on secured TFTP protocol. In AIP Conference
Proceedings (Vol. 1952, No. 1, p. 020074). AIP Publishing.
16
Airasvirta, E.J., 2016. Versatile Authentication Methods for Web Applications.
Arthur, W. and Challener, D., 2015. A Practical Guide to TPM 2.0: Using the Trusted Platform
Module in the New Age of Security. Apress.
Chuchra, R. and Kaur, R., 2017. IMPLEMENTATION OF JSMEA (JOINT SELECTIVE MULTIMEDIA
ENCRYPTION ALGORITHM)-A PRIVACY ENHANCING STRATEGY. International Journal of
Advanced Research in Computer Science, 8(9), pp.266-269.
Cimato, S. and Yang, C.N. eds., 2017. Visual cryptography and secret image sharing. CRC
press.
Kabtoul, O., 2017. Last Mile Transfer: enabling local data transfers on the global WLCG
infrastructure.
Keller, M., Orsini, E., Rotaru, D., Scholl, P., Soria-Vazquez, E. and Vivek, S., 2017, July. Faster
secure multi-party computation of AES and DES using lookup tables. In International
Conference on Applied Cryptography and Network Security (pp. 229-249). Springer, Cham.
Liu, Y., Tome, W., Zhang, L., Choffnes, D., Levin, D., Maggs, B., Mislove, A., Schulman, A. and
Wilson, C., 2015, October. An end-to-end measurement of a certificate revocation in the
web's PKI. In Proceedings of the 2015 Internet Measurement Conference (pp. 183-196). ACM.
Ma, E.T.K., and Grider, S.N., Maxim Integrated Products Inc, 2017. Block encryption security
for integrated microcontroller and external memory system. U.S. Patent 9,773,431.
Martin, L.W., Spies, T. and Pauker, M.J., Voltage Security Inc, 2016. Format preserving
encryption methods for data strings with constraints. U.S. Patent 9,489,521.
Pancholi, V.R., and Patel, B.P., 2016. Enhancement of cloud computing security with secure
data storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), pp.18-21.
Pouliot, D. and Wright, C.V., 2016, October. The shadow nemesis: Inference attacks on
efficiently deployable, efficiently searchable encryption. In Proceedings of the 2016 ACM
SIGSAC Conference on Computer and Communications Security (pp. 1341-1352). ACM.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2017. A synchronized shared key generation
method for maintaining the end-to-end security of big data streams.
Reddy, K.R., and Rao, C.M., 2018, April. GUI implementation of image encryption and
decryption using Open CV-Python script on secured TFTP protocol. In AIP Conference
Proceedings (Vol. 1952, No. 1, p. 020074). AIP Publishing.
16

Sivakorn, S., Argyros, G., Pei, K., Keromytis, A.D. and Jana, S., 2017, May. HVLearn:
Automated black-box analysis of hostname verification in SSL/TLS implementations.
In Security and Privacy (SP), 2017 IEEE Symposium on (pp. 521-538). IEEE.
Skurichinas, G., 2017. Public-Key Distribution and Acquisition services over SMS.
17
Automated black-box analysis of hostname verification in SSL/TLS implementations.
In Security and Privacy (SP), 2017 IEEE Symposium on (pp. 521-538). IEEE.
Skurichinas, G., 2017. Public-Key Distribution and Acquisition services over SMS.
17
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





