Cybersecurity for Victorian Public Sector
VerifiedAdded on 2020/03/02
|12
|3080
|34
AI Summary
This assignment delves into the Victorian Protective Data Security Framework (VPDSF) and its implications for cybersecurity within the Victorian Public Sector. It examines the framework's key components, including its focus on preemptive security measures through information analytics and risk management strategies. The analysis also considers the role of the VPDSF in mitigating unintentional insider threats and bolstering overall data security across public sector units.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

VIC Government
Security Risks and Concerns
8/25/2017
Security Risks and Concerns
8/25/2017
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VIC Government
Table of Contents
Introduction.................................................................................................................................................3
Diagram - Explanation................................................................................................................................3
Exposure of the Risk - High....................................................................................................................3
Exposure of the Risk - Medium...............................................................................................................3
Exposure of the Risk - Medium-Low......................................................................................................4
Exposure of the Risk - Low.....................................................................................................................4
Deliberate v/s Accidental Threats................................................................................................................4
Security/Risk Management Execution – Possible Challenges and Issues....................................................6
Comparison of Risks and Uncertainties.......................................................................................................7
Risk Control and Mitigation........................................................................................................................8
Administrative Methodology...................................................................................................................8
Technical Approach.................................................................................................................................8
Physical Security Approach.....................................................................................................................9
Recommendations & Conclusion................................................................................................................9
References.................................................................................................................................................11
2
Table of Contents
Introduction.................................................................................................................................................3
Diagram - Explanation................................................................................................................................3
Exposure of the Risk - High....................................................................................................................3
Exposure of the Risk - Medium...............................................................................................................3
Exposure of the Risk - Medium-Low......................................................................................................4
Exposure of the Risk - Low.....................................................................................................................4
Deliberate v/s Accidental Threats................................................................................................................4
Security/Risk Management Execution – Possible Challenges and Issues....................................................6
Comparison of Risks and Uncertainties.......................................................................................................7
Risk Control and Mitigation........................................................................................................................8
Administrative Methodology...................................................................................................................8
Technical Approach.................................................................................................................................8
Physical Security Approach.....................................................................................................................9
Recommendations & Conclusion................................................................................................................9
References.................................................................................................................................................11
2
VIC Government
Introduction
Victorian Protective Data Security Framework (VPDSF) is the security scheme that has been
prepared by the Victorian Government. The aim of the framework is the management of security
risks and concerns that are identified in the operations and activities associated with the public
sector units. There are three elements to security that are present in VPDSF that is security
standards & protocols, assurance model along with the supporting references and guides. The
framework that has been defined for the Victorian Government addresses these security risks. A
clear picture of the probable security events is required for the development of the measures to
prevent and control the risks.
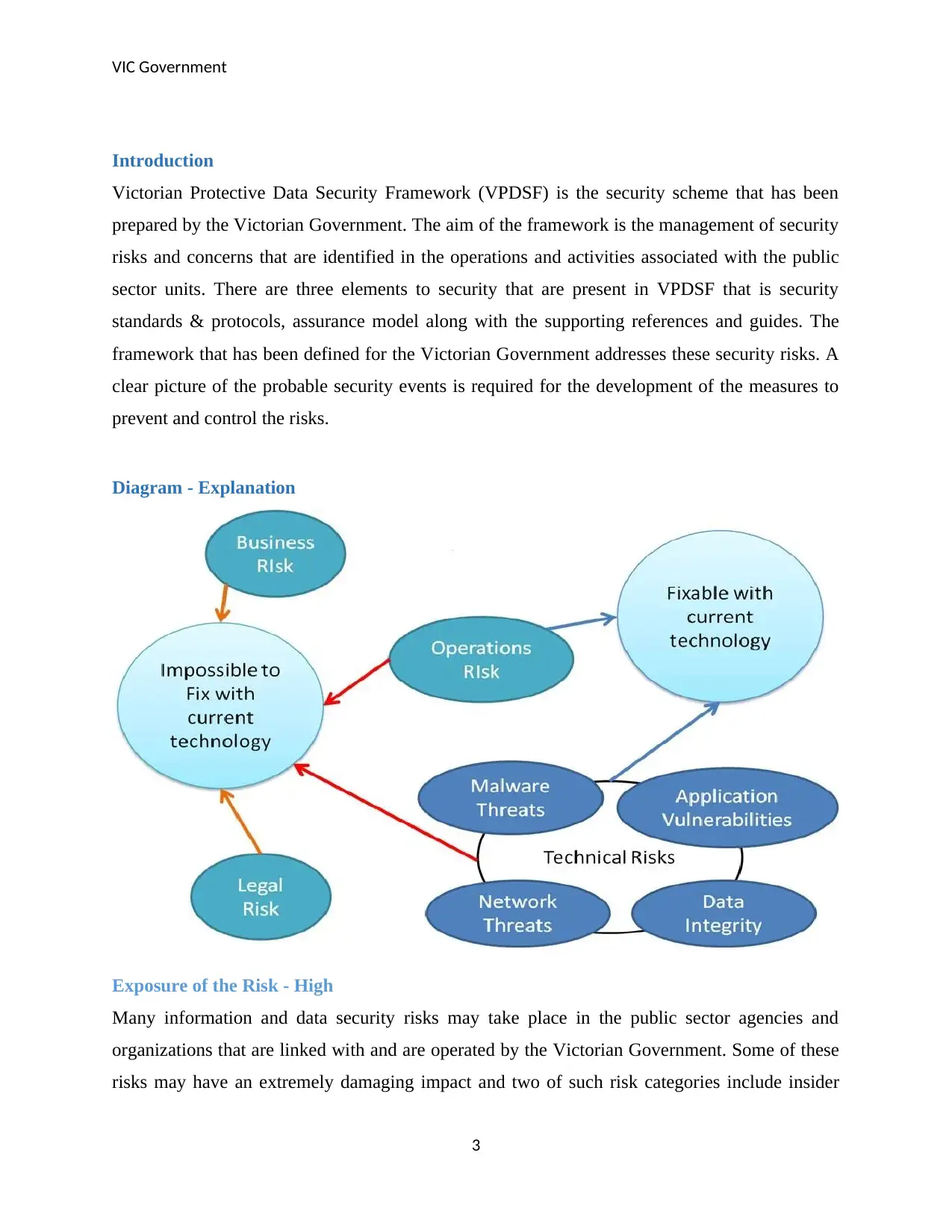
Diagram - Explanation
Exposure of the Risk - High
Many information and data security risks may take place in the public sector agencies and
organizations that are linked with and are operated by the Victorian Government. Some of these
risks may have an extremely damaging impact and two of such risk categories include insider
3
Introduction
Victorian Protective Data Security Framework (VPDSF) is the security scheme that has been
prepared by the Victorian Government. The aim of the framework is the management of security
risks and concerns that are identified in the operations and activities associated with the public
sector units. There are three elements to security that are present in VPDSF that is security
standards & protocols, assurance model along with the supporting references and guides. The
framework that has been defined for the Victorian Government addresses these security risks. A
clear picture of the probable security events is required for the development of the measures to
prevent and control the risks.
Diagram - Explanation
Exposure of the Risk - High
Many information and data security risks may take place in the public sector agencies and
organizations that are linked with and are operated by the Victorian Government. Some of these
risks may have an extremely damaging impact and two of such risk categories include insider
3

VIC Government
attacks and availability attacks. The members and employees of the public sector units will have
added privileges to access the public and personal information of the agencies and organizations.
These privileges may be used in a malicious manner to expose the information to the
unauthorized entities to gain personal advantage. Also, the malevolent entities may flood the
system with unwanted network traffic to disrupt the continuity of the applications and the
services (Cpdp, 2016).
Exposure of the Risk - Medium
Information breaches and leakage of the information may occur in association with the data and
information sets. There may also be violation of the information integrity by altering the
destination address or the contents of the information sets. These attacks will include the network
access points as the threat agent. These attacks may occur in association with the information in-
motion.
Exposure of the Risk - Medium-Low
There are some of the extremely severe impacts that may result with the occurrence of a security
attack. These impacts may give rise to the other forms of the risks and threats that may be
required to be dealt with. Some of the data security risks may result in legal obligations or the
risks revolving around non-compliance of the regulatory policies. The likelihood of such events
is not very high and these have been therefore been put in this category.
Exposure of the Risk - Low
Many of the data security risks may come up due to the operational error or a technical fault
resulted due to the negligence or mistake of the operator or the employee. These events may lead
to the exposure of information in front of the unauthorized entities. There may also be
occurrences wherein the damage may not be reversible in nature. The likelihood and the degree
of impact associated with these issues are low (Moreau, 2001).
Deliberate v/s Accidental Threats
The data and information security risks that may occur in the VIC Government and the public
sector units governed by the Government are abundant in number. The nature of these risks may
differ from one another that will determine the degree of impact that will be caused by the
occurrence of the risk.
4
attacks and availability attacks. The members and employees of the public sector units will have
added privileges to access the public and personal information of the agencies and organizations.
These privileges may be used in a malicious manner to expose the information to the
unauthorized entities to gain personal advantage. Also, the malevolent entities may flood the
system with unwanted network traffic to disrupt the continuity of the applications and the
services (Cpdp, 2016).
Exposure of the Risk - Medium
Information breaches and leakage of the information may occur in association with the data and
information sets. There may also be violation of the information integrity by altering the
destination address or the contents of the information sets. These attacks will include the network
access points as the threat agent. These attacks may occur in association with the information in-
motion.
Exposure of the Risk - Medium-Low
There are some of the extremely severe impacts that may result with the occurrence of a security
attack. These impacts may give rise to the other forms of the risks and threats that may be
required to be dealt with. Some of the data security risks may result in legal obligations or the
risks revolving around non-compliance of the regulatory policies. The likelihood of such events
is not very high and these have been therefore been put in this category.
Exposure of the Risk - Low
Many of the data security risks may come up due to the operational error or a technical fault
resulted due to the negligence or mistake of the operator or the employee. These events may lead
to the exposure of information in front of the unauthorized entities. There may also be
occurrences wherein the damage may not be reversible in nature. The likelihood and the degree
of impact associated with these issues are low (Moreau, 2001).
Deliberate v/s Accidental Threats
The data and information security risks that may occur in the VIC Government and the public
sector units governed by the Government are abundant in number. The nature of these risks may
differ from one another that will determine the degree of impact that will be caused by the
occurrence of the risk.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VIC Government
These risks can be categorized in two different categories on the basis of the motive that is
involved behind the same.
Deliberate Threats Accidental Threats
The motive of the attacker that is involved
behind the execution of these threats and
attacks is completely malicious in order to
cause negative impact on the party attacked.
The motive of the attacker is not negative or
selfish in this case as these are the forms of the
threats that are caused without any malicious
intent. These are primarily a result of the
unintended move that may cause damage.
These threats may have a vanishing damage
as the primary motive of the attacker in this
case is to cause damage.
The impact in this case may vary. These can
have low, medium, high or critical impact
which is usually negative (Kadam, 2007).
Attackers plan these threats in advance and
there are specific time-intervals that are
determined to trigger these attacks
These are not planned in advance and can
occur at any time or at any moment.
Threats on the availability of the
information and services are usually
deliberate in nature. These may include all
form of flooding attacks.
Threats carried out with network as the
threat agent are included in this category
Malware attacks
Leakage of the information due to the exposure
of authorized information in front of the
unauthorized users due to an error or a mistake.
Breaching of information or the loss of data
There is one form of attack that may be
deliberate as well as accidental in nature
depending upon the situation.
Insider threats are the attacks that are
carried out with employees of an
organization as the threat agents. These
employees may cause a threat due to selfish
motives.
Insider threats are the attacks that are carried
out with employees of an organization as the
threat agents. These employees may cause a
threat due to an error or a mistake that may not
be known in advance.
5
These risks can be categorized in two different categories on the basis of the motive that is
involved behind the same.
Deliberate Threats Accidental Threats
The motive of the attacker that is involved
behind the execution of these threats and
attacks is completely malicious in order to
cause negative impact on the party attacked.
The motive of the attacker is not negative or
selfish in this case as these are the forms of the
threats that are caused without any malicious
intent. These are primarily a result of the
unintended move that may cause damage.
These threats may have a vanishing damage
as the primary motive of the attacker in this
case is to cause damage.
The impact in this case may vary. These can
have low, medium, high or critical impact
which is usually negative (Kadam, 2007).
Attackers plan these threats in advance and
there are specific time-intervals that are
determined to trigger these attacks
These are not planned in advance and can
occur at any time or at any moment.
Threats on the availability of the
information and services are usually
deliberate in nature. These may include all
form of flooding attacks.
Threats carried out with network as the
threat agent are included in this category
Malware attacks
Leakage of the information due to the exposure
of authorized information in front of the
unauthorized users due to an error or a mistake.
Breaching of information or the loss of data
There is one form of attack that may be
deliberate as well as accidental in nature
depending upon the situation.
Insider threats are the attacks that are
carried out with employees of an
organization as the threat agents. These
employees may cause a threat due to selfish
motives.
Insider threats are the attacks that are carried
out with employees of an organization as the
threat agents. These employees may cause a
threat due to an error or a mistake that may not
be known in advance.
5

VIC Government
Organizations and business units have developed and implemented the security standards and
policies to ensure that the deliberate and accidental threats are targeted. There are also measures
that VIC Government may use and apply to put a check on both forms of the attacks.
Department of Homeland security made an analysis of the possible deliberate and accidental
threat events that may occur. The mitigation strategies and associated decisions were taken to
target and deal with both of these threat categories. The nature of impact and the degree of
damage was found to be more severe in case of deliberate threats in comparison with the
accidental events to security. The first step that the department carried out was risk and threat
analysis and the account of the organizational practices. There were many gaps and loopholes
that were discovered. There were many automated tools and applications that were implemented
to fight against the attacks. The human resources were also provided with the skills and trainings
to put a check on the deliberate attacks. VIC Government can also refer to the same approach
and take a phased approach to prevent and mitigate the deliberate and accidental threats to
security (Sei, 2013).
Security/Risk Management Execution – Possible Challenges and Issues
There are various methodologies and processes that may be adopted by VIC Government to deal
with the security risks and attacks. The process of strategy implementation and decision making
in terms of design and development of the methods may be done internally or externally.
The internal method may involve the in-house development of the security protocols and
processes which shall then be implemented across the entire infrastructure. The process will be
extremely cost-effective in nature as the resource utilization that will be done will be on an
internal basis. There might a few challenges that VIC Government may have to face in
association with the internal methods as suggested above.
The internal employees may not have an adequate combination of the necessary skills
and knowledge to accurately develop the necessary tools.
The process of design and development of the mechanisms internally will provide the
internal employees with a complete knowledge of the security processes. This may be
used in a malevolent manner.
6
Organizations and business units have developed and implemented the security standards and
policies to ensure that the deliberate and accidental threats are targeted. There are also measures
that VIC Government may use and apply to put a check on both forms of the attacks.
Department of Homeland security made an analysis of the possible deliberate and accidental
threat events that may occur. The mitigation strategies and associated decisions were taken to
target and deal with both of these threat categories. The nature of impact and the degree of
damage was found to be more severe in case of deliberate threats in comparison with the
accidental events to security. The first step that the department carried out was risk and threat
analysis and the account of the organizational practices. There were many gaps and loopholes
that were discovered. There were many automated tools and applications that were implemented
to fight against the attacks. The human resources were also provided with the skills and trainings
to put a check on the deliberate attacks. VIC Government can also refer to the same approach
and take a phased approach to prevent and mitigate the deliberate and accidental threats to
security (Sei, 2013).
Security/Risk Management Execution – Possible Challenges and Issues
There are various methodologies and processes that may be adopted by VIC Government to deal
with the security risks and attacks. The process of strategy implementation and decision making
in terms of design and development of the methods may be done internally or externally.
The internal method may involve the in-house development of the security protocols and
processes which shall then be implemented across the entire infrastructure. The process will be
extremely cost-effective in nature as the resource utilization that will be done will be on an
internal basis. There might a few challenges that VIC Government may have to face in
association with the internal methods as suggested above.
The internal employees may not have an adequate combination of the necessary skills
and knowledge to accurately develop the necessary tools.
The process of design and development of the mechanisms internally will provide the
internal employees with a complete knowledge of the security processes. This may be
used in a malevolent manner.
6

VIC Government
There may be technical issues and operational challenges that may be observed in the
process of migration.
The second method that may be used and applied may be outsourcing of the development
activities and processes. This method will be external to the VIC Government and there will the
third-parties that will be assigned with the tasks of development and design processes. This
method will have its own set of challenges and issues.
In terms of cost, this process will score higher than the internal method explained earlier
(Taylor, 2015).
The end-result may not be in complete adherence with the requirements and
specifications.
The third-parties may demand access to the production data for the execution of the
testing activities. It will put the privacy of the data at risk.
There will be many changes that will be introduced in any of the two processes. These changes
will be a challenge in itself. The entities associated with the public sector units under the VIC
Government will have to manage and understand all of these changes. Adaptability to these
changes will be necessary to make sure that the smooth functioning of the operations is
maintained.
Comparison of Risks and Uncertainties
Risk is defined as an occurrence that can be predicted and controlled and is usually associated
with the negative impacts and outcomes for the parties that are targeted. In case of the VIC
Government, the primary risks that are present are in the form of information security risks.
These risks may impact the availability, integrity and confidentiality of the information.
The impact that may result out from the risks on the VIC Government may be low, medium, high
or critical in nature. Some of these risks may have an extremely damaging impact and two of
such risk categories include insider attacks and availability attacks. The members and employees
of the public sector units will have added privileges to access the public and personal
information of the agencies and organizations. These privileges may be used in a malicious
manner to expose the information to the unauthorized entities to gain personal advantage. There
7
There may be technical issues and operational challenges that may be observed in the
process of migration.
The second method that may be used and applied may be outsourcing of the development
activities and processes. This method will be external to the VIC Government and there will the
third-parties that will be assigned with the tasks of development and design processes. This
method will have its own set of challenges and issues.
In terms of cost, this process will score higher than the internal method explained earlier
(Taylor, 2015).
The end-result may not be in complete adherence with the requirements and
specifications.
The third-parties may demand access to the production data for the execution of the
testing activities. It will put the privacy of the data at risk.
There will be many changes that will be introduced in any of the two processes. These changes
will be a challenge in itself. The entities associated with the public sector units under the VIC
Government will have to manage and understand all of these changes. Adaptability to these
changes will be necessary to make sure that the smooth functioning of the operations is
maintained.
Comparison of Risks and Uncertainties
Risk is defined as an occurrence that can be predicted and controlled and is usually associated
with the negative impacts and outcomes for the parties that are targeted. In case of the VIC
Government, the primary risks that are present are in the form of information security risks.
These risks may impact the availability, integrity and confidentiality of the information.
The impact that may result out from the risks on the VIC Government may be low, medium, high
or critical in nature. Some of these risks may have an extremely damaging impact and two of
such risk categories include insider attacks and availability attacks. The members and employees
of the public sector units will have added privileges to access the public and personal
information of the agencies and organizations. These privileges may be used in a malicious
manner to expose the information to the unauthorized entities to gain personal advantage. There
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VIC Government
may also be violation of the information integrity by altering the destination address or the
contents of the information sets. Some of the data security risks may result in legal obligations or
the risks revolving around non-compliance of the regulatory policies. These events may lead to
the exposure of information in front of the unauthorized entities. There may also be occurrences
wherein the damage may not be reversible in nature. The likelihood and the degree of impact
associated with these issues are low (Kumar, 2013).
Uncertainties are defined as the events that cannot be predicted and therefore it is difficult to
develop the control measures for these events. The uncertainties that are associated with the VIC
Government can include the modification on the regulatory and legal policies that are put in
action by the Government. The policies around data privacy, Intellectual property and
information security may be updated by the Victorian Government. There are also many of the
security models and security standards that have been developed to make sure that the security of
the information is maintained in the organizations. However, with such unpredictable scenarios,
these models and standards will turn invalid. There will be transformations that will be required
to be made so that the new sets of policies and controls may be applied.
Risk Control and Mitigation
Many different approaches can be put in to action to prevent, detect, control and mitigate the
security risks and concerns.
Administrative Methodology
The overall structure of security can be put in to action if it is backed by a strong administrative
control. There are developments that are required to be made in this area at regular intervals to
ensure that the security risks and attacks do not take place. These administrative controls must
match with the latest security strategies and the enforcement of the same shall be monitored.
In case of the VIC Government, the approach will determine the correctness and validity of the
security policies that are applied across the agencies and organizations under the public sector. It
shall be ensured that the team of reviewers, auditors and inspectors are provided with the set of
latest tools and equipment for easier execution of the processes.
8
may also be violation of the information integrity by altering the destination address or the
contents of the information sets. Some of the data security risks may result in legal obligations or
the risks revolving around non-compliance of the regulatory policies. These events may lead to
the exposure of information in front of the unauthorized entities. There may also be occurrences
wherein the damage may not be reversible in nature. The likelihood and the degree of impact
associated with these issues are low (Kumar, 2013).
Uncertainties are defined as the events that cannot be predicted and therefore it is difficult to
develop the control measures for these events. The uncertainties that are associated with the VIC
Government can include the modification on the regulatory and legal policies that are put in
action by the Government. The policies around data privacy, Intellectual property and
information security may be updated by the Victorian Government. There are also many of the
security models and security standards that have been developed to make sure that the security of
the information is maintained in the organizations. However, with such unpredictable scenarios,
these models and standards will turn invalid. There will be transformations that will be required
to be made so that the new sets of policies and controls may be applied.
Risk Control and Mitigation
Many different approaches can be put in to action to prevent, detect, control and mitigate the
security risks and concerns.
Administrative Methodology
The overall structure of security can be put in to action if it is backed by a strong administrative
control. There are developments that are required to be made in this area at regular intervals to
ensure that the security risks and attacks do not take place. These administrative controls must
match with the latest security strategies and the enforcement of the same shall be monitored.
In case of the VIC Government, the approach will determine the correctness and validity of the
security policies that are applied across the agencies and organizations under the public sector. It
shall be ensured that the team of reviewers, auditors and inspectors are provided with the set of
latest tools and equipment for easier execution of the processes.
8

VIC Government
Technical Approach
There are also technical steps that the VIC Government may take for the improvements in the
security status and the management of the overall security infrastructure.
There are many technical applications and tools that are available in the market that can be
purchases and installed in the organizations across the entire public sector. These tools may also
be outsourced for development as per the specific policies of the organizations and agencies. The
information categories such as public data and private data will be protected with this approach.
Also, the trust and engagement of the customers will also improve. There are many flooding and
malware attacks that are on the higher side of the probability which will be reduced with the aid
of the technical methods (Rashvand, 2010).
The development in the technical framework will also cause the enhancement of the security
architecture and the integration of all the units with each other.
Physical Security Approach
There are various units that are associated with the public sector agencies and organizations that
need to be safeguarded. Such units include the data centres, databases, server rooms,
workstations etc.
The administrative and technical approach towards security can add to the advanced methods to
protect and safeguard the overall security of the information. However, the basic step towards
security will be provided only with the aid of the physical security measures. The physical
security approach will provide the required control and mitigation in association with the risks
and attacks. The entry and exit doors of all the units shall be equipped with physical security
measures for keeping a track of the people making the access and intruders (Godlove, 2012).
The security approach that is recommended to be used for risk mitigation in the VIC
Government is the implementation of the technical approach amalgamated with the physical and
administrative approach.
Recommendations & Conclusion
VIC Government is an entity that is composed of numerous components and entities. These
components include the agencies and organizations along with their specific data bases, data
9
Technical Approach
There are also technical steps that the VIC Government may take for the improvements in the
security status and the management of the overall security infrastructure.
There are many technical applications and tools that are available in the market that can be
purchases and installed in the organizations across the entire public sector. These tools may also
be outsourced for development as per the specific policies of the organizations and agencies. The
information categories such as public data and private data will be protected with this approach.
Also, the trust and engagement of the customers will also improve. There are many flooding and
malware attacks that are on the higher side of the probability which will be reduced with the aid
of the technical methods (Rashvand, 2010).
The development in the technical framework will also cause the enhancement of the security
architecture and the integration of all the units with each other.
Physical Security Approach
There are various units that are associated with the public sector agencies and organizations that
need to be safeguarded. Such units include the data centres, databases, server rooms,
workstations etc.
The administrative and technical approach towards security can add to the advanced methods to
protect and safeguard the overall security of the information. However, the basic step towards
security will be provided only with the aid of the physical security measures. The physical
security approach will provide the required control and mitigation in association with the risks
and attacks. The entry and exit doors of all the units shall be equipped with physical security
measures for keeping a track of the people making the access and intruders (Godlove, 2012).
The security approach that is recommended to be used for risk mitigation in the VIC
Government is the implementation of the technical approach amalgamated with the physical and
administrative approach.
Recommendations & Conclusion
VIC Government is an entity that is composed of numerous components and entities. These
components include the agencies and organizations along with their specific data bases, data
9

VIC Government
centres, workstations, server rooms, warehouses etc. Every such unit has a lot of information and
data associated with it. Also, the information sets that are associated with a specific agency are
also huge in number. There are information and data related security risks that may take place in
relation with the public sector units under the VIC Government. It is of utmost importance to
make sure that there are countermeasures and mitigation strategies developed and implemented
for the avoidance and prevention of the security risks and issues (Leszczyna, 2011).
The approach that has been recommended for the purpose is the implementation of the technical
approach. However, it shall be combined along with the physical security and administrative
controls. There are various elements of technology that may be used and applied to deal with the
security risks and attacks. One of such elements is the Big Data tools for security. These tools
have the capability to perform the analytics on the risks and security occurrences that have taken
place in the past. This will provide the strategies and mechanisms to develop for the avoidance
and control of the risks (Early, 2015). Also, these tools will efficiently manage the information
and data sets that will be associated with the public sector units under the VIC Government. In
such a manner, the overall state of security will be strengthened and there will be lesser
occurrences of data security risks and attacks.
10
centres, workstations, server rooms, warehouses etc. Every such unit has a lot of information and
data associated with it. Also, the information sets that are associated with a specific agency are
also huge in number. There are information and data related security risks that may take place in
relation with the public sector units under the VIC Government. It is of utmost importance to
make sure that there are countermeasures and mitigation strategies developed and implemented
for the avoidance and prevention of the security risks and issues (Leszczyna, 2011).
The approach that has been recommended for the purpose is the implementation of the technical
approach. However, it shall be combined along with the physical security and administrative
controls. There are various elements of technology that may be used and applied to deal with the
security risks and attacks. One of such elements is the Big Data tools for security. These tools
have the capability to perform the analytics on the risks and security occurrences that have taken
place in the past. This will provide the strategies and mechanisms to develop for the avoidance
and control of the risks (Early, 2015). Also, these tools will efficiently manage the information
and data sets that will be associated with the public sector units under the VIC Government. In
such a manner, the overall state of security will be strengthened and there will be lesser
occurrences of data security risks and attacks.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VIC Government
References
Cpdp. (2016). Victorian Protective Data Security Framework. Retrieved 25 August 2017, from
https://www.cpdp.vic.gov.au/images/content/pdf/data_security/20160628%20VPDSF
%20Framework%20June%202016%20v1.0.pdf
Early, G. (2015). Preemptive Security Through Information Analytics. Information Security
Journal: A Global Perspective, 24(1-3), 48-56.
http://dx.doi.org/10.1080/19393555.2015.1042600
Godlove, T. (2012). Examination of the Factors that Influence Teleworkers' Willingness to
Comply with Information Security Guidelines. Information Security Journal: A Global
Perspective, 21(4), 216-229. http://dx.doi.org/10.1080/19393555.2012.668747
Kadam, A. (2007). Information Security Policy Development and Implementation. Information
Systems Security, 16(5), 246-256. http://dx.doi.org/10.1080/10658980701744861
Kumar, M. (2013). An exploration of risk management in global industrial investment. Risk
Management, 15(4), 272-300. http://dx.doi.org/10.1057/rm.2013.8
Leszczyna, R. (2011). Approach to security assessment of critical infrastructures’
information systems. IET Information Security, 5(3), 135. http://dx.doi.org/10.1049/iet-
ifs.2010.0261
Moreau, F. (2001). Managing technological catastrophic risks. Risk Decision And Policy, 6(1),
17-32. http://dx.doi.org/10.1017/s1357530901000242
Rashvand, H. (2010). Editorial: Multi-agent & distributed information security. IET Information
Security, 4(4), 185. http://dx.doi.org/10.1049/iet-ifs.2010.9128
Sei. (2013). Unintentional Insider Threats: A Foundational Study. Retrieved 25 August 2017,
from https://www.sei.cmu.edu/reports/13tn022.pdf
Taylor, R. (2015). Potential Problems with Information Security Risk Assessments. Information
Security Journal: A Global Perspective, 24(4-6), 177-184.
http://dx.doi.org/10.1080/19393555.2015.1092620
11
References
Cpdp. (2016). Victorian Protective Data Security Framework. Retrieved 25 August 2017, from
https://www.cpdp.vic.gov.au/images/content/pdf/data_security/20160628%20VPDSF
%20Framework%20June%202016%20v1.0.pdf
Early, G. (2015). Preemptive Security Through Information Analytics. Information Security
Journal: A Global Perspective, 24(1-3), 48-56.
http://dx.doi.org/10.1080/19393555.2015.1042600
Godlove, T. (2012). Examination of the Factors that Influence Teleworkers' Willingness to
Comply with Information Security Guidelines. Information Security Journal: A Global
Perspective, 21(4), 216-229. http://dx.doi.org/10.1080/19393555.2012.668747
Kadam, A. (2007). Information Security Policy Development and Implementation. Information
Systems Security, 16(5), 246-256. http://dx.doi.org/10.1080/10658980701744861
Kumar, M. (2013). An exploration of risk management in global industrial investment. Risk
Management, 15(4), 272-300. http://dx.doi.org/10.1057/rm.2013.8
Leszczyna, R. (2011). Approach to security assessment of critical infrastructures’
information systems. IET Information Security, 5(3), 135. http://dx.doi.org/10.1049/iet-
ifs.2010.0261
Moreau, F. (2001). Managing technological catastrophic risks. Risk Decision And Policy, 6(1),
17-32. http://dx.doi.org/10.1017/s1357530901000242
Rashvand, H. (2010). Editorial: Multi-agent & distributed information security. IET Information
Security, 4(4), 185. http://dx.doi.org/10.1049/iet-ifs.2010.9128
Sei. (2013). Unintentional Insider Threats: A Foundational Study. Retrieved 25 August 2017,
from https://www.sei.cmu.edu/reports/13tn022.pdf
Taylor, R. (2015). Potential Problems with Information Security Risk Assessments. Information
Security Journal: A Global Perspective, 24(4-6), 177-184.
http://dx.doi.org/10.1080/19393555.2015.1092620
11

VIC Government
12
12
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





