AgriDigital Network Infrastructure and VPN Services Design Report
VerifiedAdded on 2023/03/31
|16
|2044
|391
Report
AI Summary
This report provides a comprehensive analysis of the network requirements for AgriDigital, focusing on the design and implementation of VPN services. It outlines the project scope, limitations, and a summary of network and VPN service requirements. The solution design section details both the logical and physical network designs, accompanied by diagrams, and discusses the network topologies used, including physical star and ring topologies for redundancy. Furthermore, the report includes a detailed IP address allocation scheme using CIDR, security policies and features such as VPN implementation, firewall configuration, and WPA2 encryption, as well as redundancy and failover plans. It concludes with the implementation of VPN services across different connections to secure the network infrastructure for AgriDigital, ensuring secure access for both organizational members and end-users.

Running head: VIIRTUAL PRIVATE NETWORK
Virtual Private Network
Name of the Student
Name of the University
Author Note
Virtual Private Network
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VIRTUAL PRIVATE NETWORK
Summary
The purpose of this report is to analyse the requirements of the network and identify the VPN
service parts being used in the existing network infrastructure of AgriDigital and discusses about the
scope and limitations of the project. First the report talks about the project scope after which the
limitations of the network is described. Following this the report goes on to provide the summary of
requirements related to the network and the VPN services being used. After that the report enters
the solution design section where the logical network design and the physical network design is
provided and discussed along with diagrams. Then the report speaks about the networking
topologies that were used to implement the network and VPN solution. Thereafter the IP address
allocation is detailed with relevant IPs of sub networks given in tabular format. After giving the IP
address allocation and listing explaining the method the security features and policies get discussed
followed by the redundancy and failover plans. Then after talking about implementation of VPN
services the report ends with concluding notes.
Summary
The purpose of this report is to analyse the requirements of the network and identify the VPN
service parts being used in the existing network infrastructure of AgriDigital and discusses about the
scope and limitations of the project. First the report talks about the project scope after which the
limitations of the network is described. Following this the report goes on to provide the summary of
requirements related to the network and the VPN services being used. After that the report enters
the solution design section where the logical network design and the physical network design is
provided and discussed along with diagrams. Then the report speaks about the networking
topologies that were used to implement the network and VPN solution. Thereafter the IP address
allocation is detailed with relevant IPs of sub networks given in tabular format. After giving the IP
address allocation and listing explaining the method the security features and policies get discussed
followed by the redundancy and failover plans. Then after talking about implementation of VPN
services the report ends with concluding notes.

2VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction...............................................................................................................................3
Scope of Project..........................................................................................................................3
Limitations..................................................................................................................................4
Requirements Summary.............................................................................................................4
Solutions Design.........................................................................................................................4
Logical Network Design..........................................................................................................4
Physical Network Design........................................................................................................4
Network Topologies...............................................................................................................4
IP Address Allocation..............................................................................................................5
Security Policy and features...................................................................................................5
Redundancy and Failover Plan...............................................................................................5
Implementation of VPN services............................................................................................5
Conclusion..................................................................................................................................5
References..................................................................................................................................6
Table of Contents
Introduction...............................................................................................................................3
Scope of Project..........................................................................................................................3
Limitations..................................................................................................................................4
Requirements Summary.............................................................................................................4
Solutions Design.........................................................................................................................4
Logical Network Design..........................................................................................................4
Physical Network Design........................................................................................................4
Network Topologies...............................................................................................................4
IP Address Allocation..............................................................................................................5
Security Policy and features...................................................................................................5
Redundancy and Failover Plan...............................................................................................5
Implementation of VPN services............................................................................................5
Conclusion..................................................................................................................................5
References..................................................................................................................................6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VIRTUAL PRIVATE NETWORK
Introduction
The following report analyses the network based requirements of the company AgriDigital
and proceeds to identify also the VPN service parts and discusses about the scope and limitations of
the project. This report begins by talking about the project scope after which the limitations of the
network is described. Following this the report goes on to provide the summary of requirements
related to the network and the VPN services being used. After that the report enters the solution
design section where the logical network design and the physical network design is provided and
discussed along with diagrams [4]. Then the report speaks about the networking topologies that
were used to implement the network and VPN solution. Thereafter the IP address allocation is
detailed with relevant IPs of sub networks given in tabular format. After giving the IP address
allocation and listing explaining the method the security features and policies get discussed followed
by the redundancy and failover plans. Then after talking about implementation of VPN services the
report ends with concluding notes.
Scope of Project
The project aims to improve the existing network infrastructure of AgriDigital while keeping
in mind long term network performance evolution so as to optimize the present capability and
capacity of the network. The purpose this process is about accommodating organizational expansion
and ability to support more modern and complex methods of communication through the network
for the intended users.
To perform the above task, acquiring and implementation of new networking equipment is
required. These equipment should then be installed, build as per requirements for configuring a new
network which needs to be integrated to existing network.
The resulting network should include both layer 2 as also layer 3 services. The
implementation and configuration of the network must involve internet and intranet related
services.
Security for the network needs to be ensured by maintaining a server farm which is to
include Web servers, FTP Servers, Email servers and the several DNS servers.
Wireless Local Area Network or WLAN services needs to be set up to support the portable
devices that need to be connected to the network [9]. The security mechanism for such network
connection also needs to be configured.
Introduction
The following report analyses the network based requirements of the company AgriDigital
and proceeds to identify also the VPN service parts and discusses about the scope and limitations of
the project. This report begins by talking about the project scope after which the limitations of the
network is described. Following this the report goes on to provide the summary of requirements
related to the network and the VPN services being used. After that the report enters the solution
design section where the logical network design and the physical network design is provided and
discussed along with diagrams [4]. Then the report speaks about the networking topologies that
were used to implement the network and VPN solution. Thereafter the IP address allocation is
detailed with relevant IPs of sub networks given in tabular format. After giving the IP address
allocation and listing explaining the method the security features and policies get discussed followed
by the redundancy and failover plans. Then after talking about implementation of VPN services the
report ends with concluding notes.
Scope of Project
The project aims to improve the existing network infrastructure of AgriDigital while keeping
in mind long term network performance evolution so as to optimize the present capability and
capacity of the network. The purpose this process is about accommodating organizational expansion
and ability to support more modern and complex methods of communication through the network
for the intended users.
To perform the above task, acquiring and implementation of new networking equipment is
required. These equipment should then be installed, build as per requirements for configuring a new
network which needs to be integrated to existing network.
The resulting network should include both layer 2 as also layer 3 services. The
implementation and configuration of the network must involve internet and intranet related
services.
Security for the network needs to be ensured by maintaining a server farm which is to
include Web servers, FTP Servers, Email servers and the several DNS servers.
Wireless Local Area Network or WLAN services needs to be set up to support the portable
devices that need to be connected to the network [9]. The security mechanism for such network
connection also needs to be configured.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VIRTUAL PRIVATE NETWORK
Different types of cabling may be required for different parts of the network. Such cabling
and their connectivity with devices needs to be justified as per requirements for correct optimization
of the network.
Implementing security within the network requires installation of firewalls, core layer
switches and as well a wireless access points. Implementing wired LAN connections is important for
connecting the workstations in newly set up building [7]. Capability for remote access needs to be
ensured using IPsec based Virtual Private Networks or VPNs. Other than that redundancy needs to
present for finance section.
Limitations
Redundancy must be ensured for firewall, routers, switches access points and servers.
Redundancy of firewalls is necessary in securing both endpoints of VPN solutions [3]. VPN solutions
as good as they are in hiding the network from hackers, also make it difficult for even organizational
members to access the company network from public Wi-Fi regions or other areas.
Requirements Summary
Assumptions
Two branches Branch 1 and Branch 2 have recently been set up. Branch 1 is to have
twice the IP requirements of Branch 2. Networks of both these branches are connected to
overall network of the office by integrating the networks into the network of the headquarters
through the firewalls.
IP addresses are required for the edge router installed in headquarters. Also IPs are
required for the interfaces to connect with the branch networks.
Different types of cabling may be required for different parts of the network. Such cabling
and their connectivity with devices needs to be justified as per requirements for correct optimization
of the network.
Implementing security within the network requires installation of firewalls, core layer
switches and as well a wireless access points. Implementing wired LAN connections is important for
connecting the workstations in newly set up building [7]. Capability for remote access needs to be
ensured using IPsec based Virtual Private Networks or VPNs. Other than that redundancy needs to
present for finance section.
Limitations
Redundancy must be ensured for firewall, routers, switches access points and servers.
Redundancy of firewalls is necessary in securing both endpoints of VPN solutions [3]. VPN solutions
as good as they are in hiding the network from hackers, also make it difficult for even organizational
members to access the company network from public Wi-Fi regions or other areas.
Requirements Summary
Assumptions
Two branches Branch 1 and Branch 2 have recently been set up. Branch 1 is to have
twice the IP requirements of Branch 2. Networks of both these branches are connected to
overall network of the office by integrating the networks into the network of the headquarters
through the firewalls.
IP addresses are required for the edge router installed in headquarters. Also IPs are
required for the interfaces to connect with the branch networks.
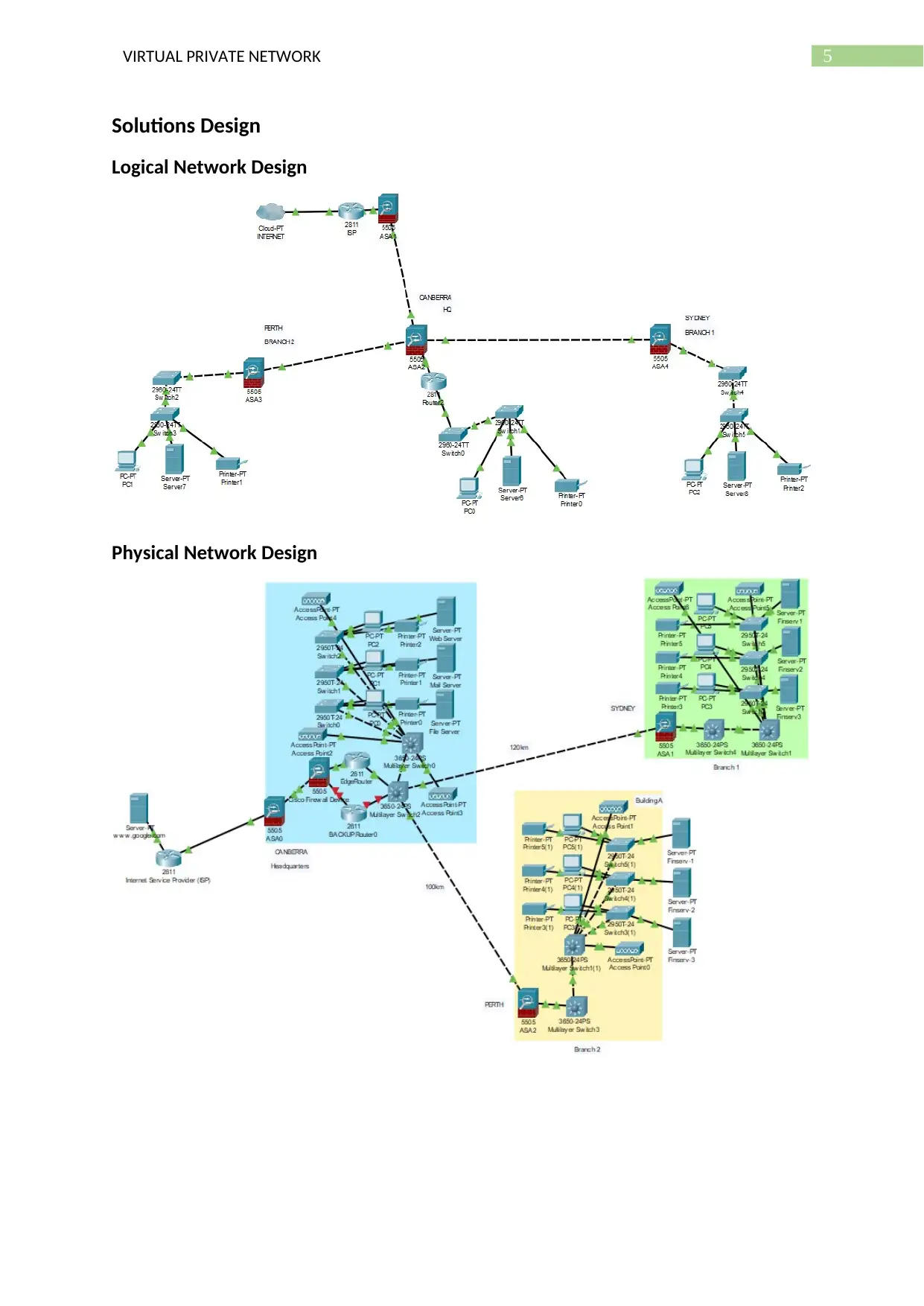
5VIRTUAL PRIVATE NETWORK
Solutions Design
Logical Network Design
Physical Network Design
Solutions Design
Logical Network Design
Physical Network Design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
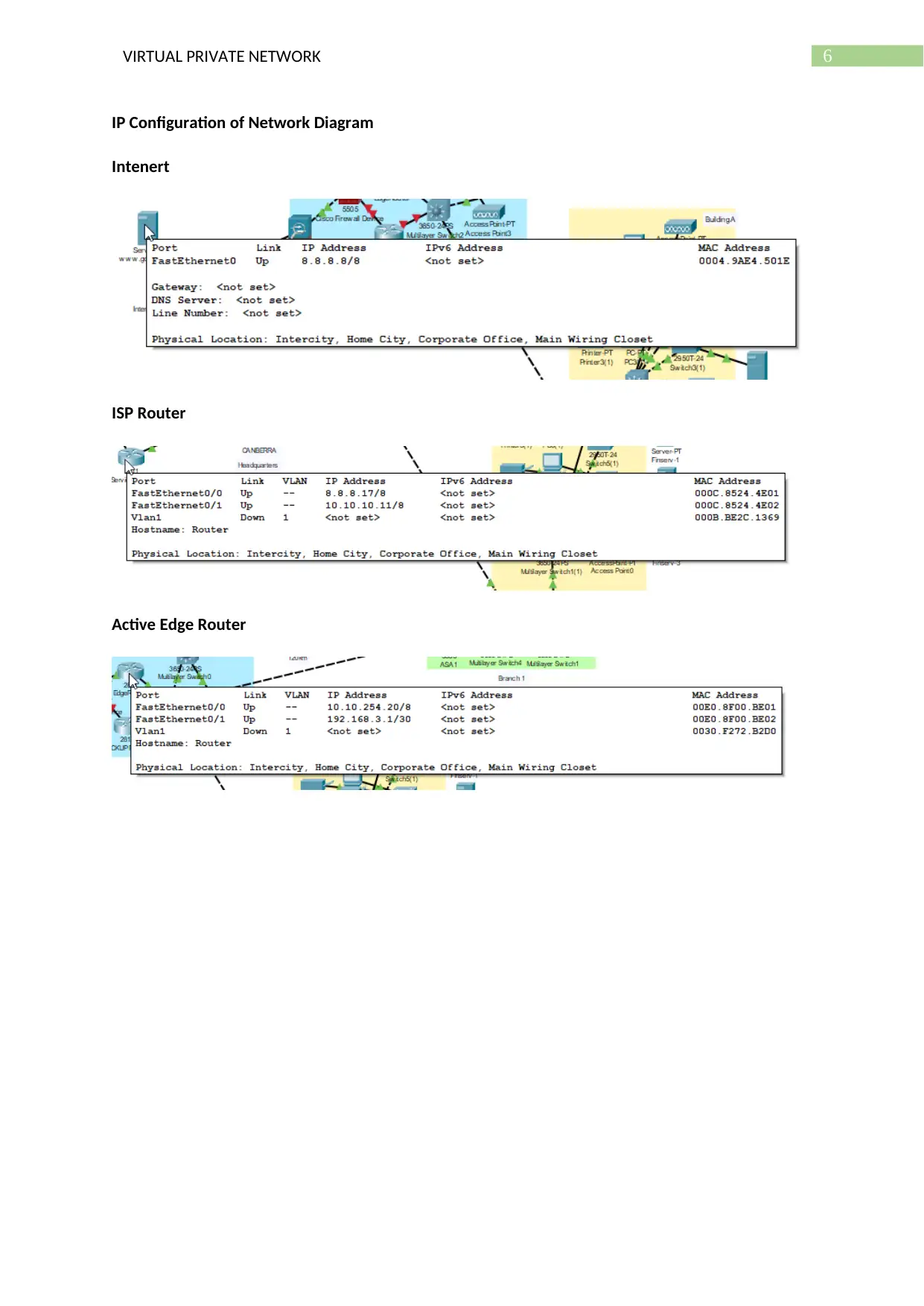
6VIRTUAL PRIVATE NETWORK
IP Configuration of Network Diagram
Intenert
ISP Router
Active Edge Router
IP Configuration of Network Diagram
Intenert
ISP Router
Active Edge Router
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
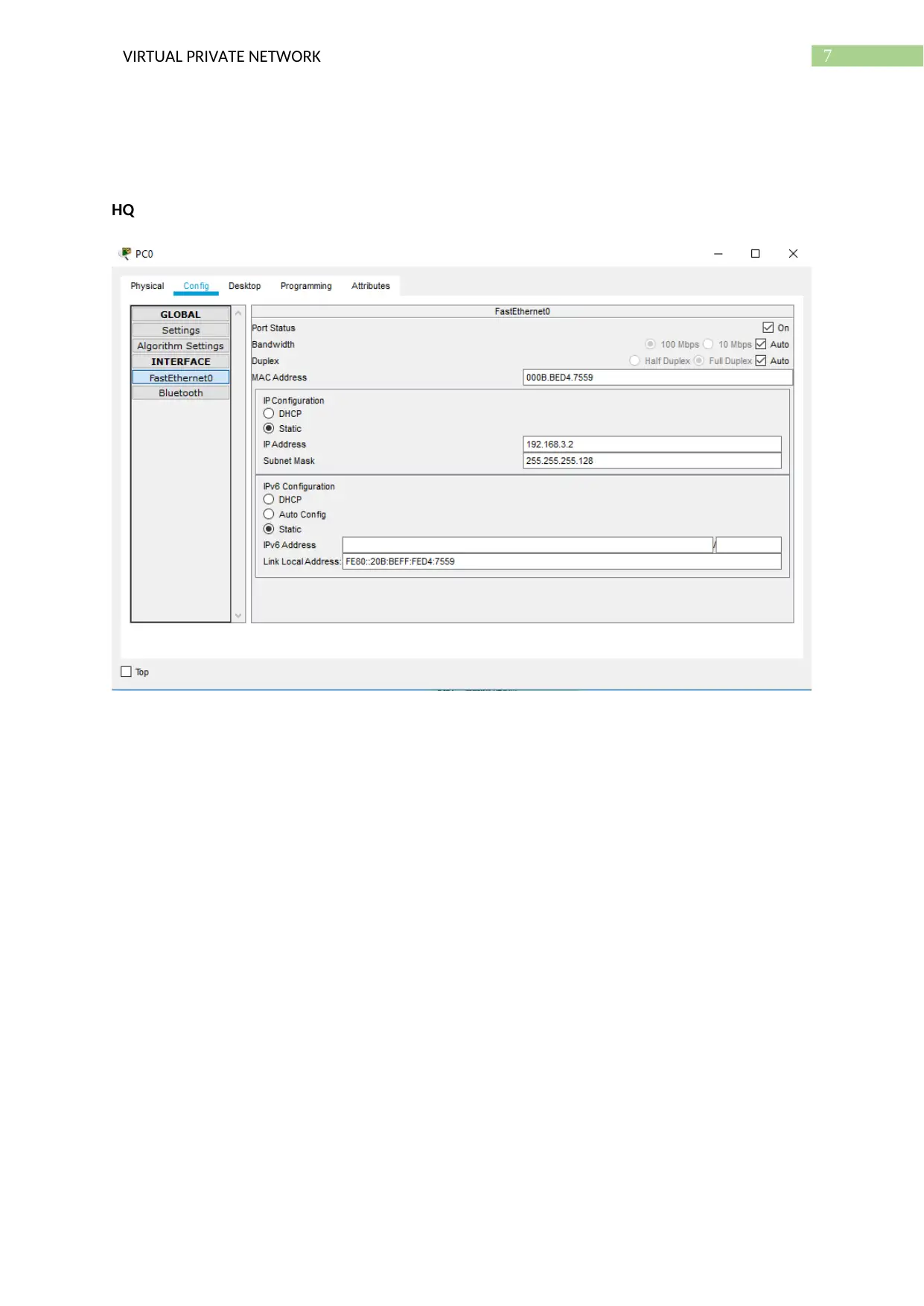
7VIRTUAL PRIVATE NETWORK
HQ
HQ
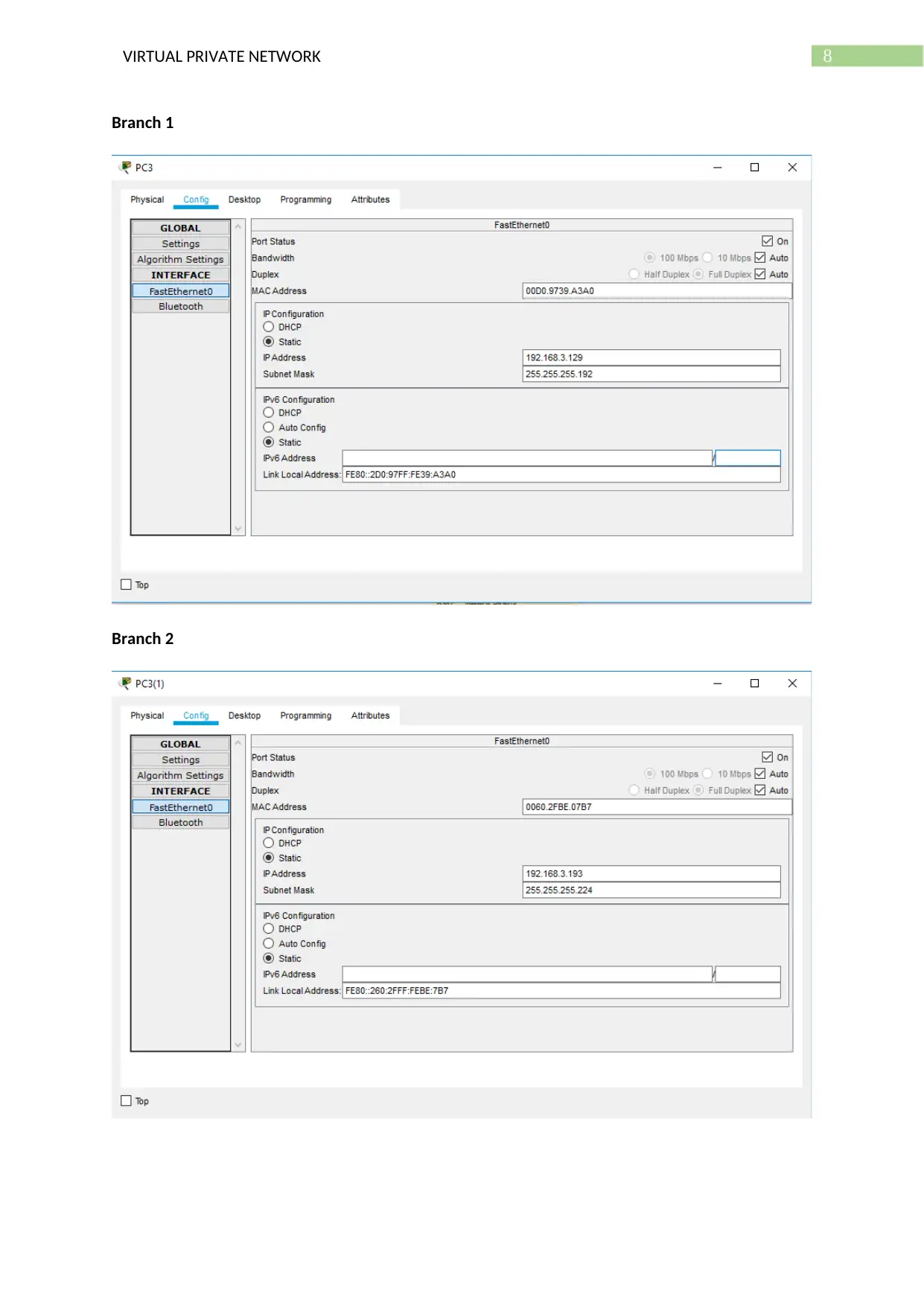
8VIRTUAL PRIVATE NETWORK
Branch 1
Branch 2
Branch 1
Branch 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9VIRTUAL PRIVATE NETWORK
Network Topologies
In conducting the physical implementation of the network of the firm AgriDigital, two key
physical networking topologies have been used. These are the physical star topology and the
physical ring topology [2]. Their use in the network of AgriDigital has been explained below.
Physical Star Topology
Physical star topology refers to the physical networking topology where direct connections
are provided to the individual devices from switches, hubs and access points [6]. In AgriDigital’s
network devices like workstations, printers, servers as well as switches and access points are
connected with other networking equipment by using this topology. Because of being connected
directly, effective network connectivity, ping and bandwidth are experienced by the users.
Physical Ring Topology
Redundancy is a key aspect of the network of AgriDigital. As a result several redundancy
among several components of the network is ensured. These components can include firewalls,
routers or even switches. The edge router is responsible for enabling network for the entire firm so a
backup is kept in case the current edge router starts showing problems [10]. Both the current and
the backup edge router acquires connection from the firewall and provides it to the core layer
switches thereby forming a physical ring topology [11].
IP Address Allocation
The IP addressing scheme used for allocating IP addresses to the newly set up buildings is
conducted through the CIDR or Classless Inter Domain Routing IP addressing scheme. This is
preferred over traditional classful IP addressing as CIDR helps in smoother transitions between sub
networks. The major IP network used for allocating IPs to the several groups is 192.16.3.0/24.
Office
subnetwo
rk
IPs
require
d
IPs
allocate
d
Network
Addresses CIDR Subnet
Mask
Range of
IPs
Broadcast
Addresses
Headquar
ters 91 126 192.168.3.0 /25 255.255.2
55.128
192.168.3.1
-
192.168.3.1
26
192.168.3.1
27
Branch 1 60 62 192.168.3.1
28
/26 255.255.2
55.192
192.168.3.1
29 -
192.168.3.1
192.168.3.1
91
Network Topologies
In conducting the physical implementation of the network of the firm AgriDigital, two key
physical networking topologies have been used. These are the physical star topology and the
physical ring topology [2]. Their use in the network of AgriDigital has been explained below.
Physical Star Topology
Physical star topology refers to the physical networking topology where direct connections
are provided to the individual devices from switches, hubs and access points [6]. In AgriDigital’s
network devices like workstations, printers, servers as well as switches and access points are
connected with other networking equipment by using this topology. Because of being connected
directly, effective network connectivity, ping and bandwidth are experienced by the users.
Physical Ring Topology
Redundancy is a key aspect of the network of AgriDigital. As a result several redundancy
among several components of the network is ensured. These components can include firewalls,
routers or even switches. The edge router is responsible for enabling network for the entire firm so a
backup is kept in case the current edge router starts showing problems [10]. Both the current and
the backup edge router acquires connection from the firewall and provides it to the core layer
switches thereby forming a physical ring topology [11].
IP Address Allocation
The IP addressing scheme used for allocating IP addresses to the newly set up buildings is
conducted through the CIDR or Classless Inter Domain Routing IP addressing scheme. This is
preferred over traditional classful IP addressing as CIDR helps in smoother transitions between sub
networks. The major IP network used for allocating IPs to the several groups is 192.16.3.0/24.
Office
subnetwo
rk
IPs
require
d
IPs
allocate
d
Network
Addresses CIDR Subnet
Mask
Range of
IPs
Broadcast
Addresses
Headquar
ters 91 126 192.168.3.0 /25 255.255.2
55.128
192.168.3.1
-
192.168.3.1
26
192.168.3.1
27
Branch 1 60 62 192.168.3.1
28
/26 255.255.2
55.192
192.168.3.1
29 -
192.168.3.1
192.168.3.1
91
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10VIRTUAL PRIVATE NETWORK
90
Branch 2 31 62 192.168.3.1
92 /26 255.255.2
55.192
192.168.3.1
93 -
192.168.3.2
54
192.168.3.2
55
ER-CS 2 2 192.168.3.1
92
/30 255.255.2
55.252
192.168.3.1
93 -
192.168.3.1
94
192.168.3.1
95
Security Policy and features
The security policies and features incorporated in securing the network are the following:
Implementing VPN: Virtual Private Networks (VPNs) are essential in the sense they can hide the
network from the view of external threats like hackers [1]. VPNs also conduct user account
verification.
Installing and configuring firewall: For medium sized businesses or small medium enterprises,
firewalls are extremely important. The ideal firewall solution can be the physical firewall device
which can also perform authentication.
WPA2 Encryption for wireless connectivity: This refers to the Wi-Fi Protected access used to
generate unique keys for each device that are to connect the network using wireless access [8].
Redundancy and Failover Plan
In most sections redundancy is noticed on firewalls. These firewalls are used to secure both
endpoints of the VPN tunnels as just having a VPN is not enough to secure the network from cyber-
attacks. A backup router is kept to ensure total network outage can be prevented if the edge router
fails. Another critical area of redundancy is observed with wireless access points [5]. This is mitigate
signal issues in wireless networks.
Implementation of VPN services
VPNs or Virtual Private networks are implanted among three connections. These are the
connection between Branch 1 and HQ, between Branch 2 and HQ and between HQ and the ISP
network. In addition to securing the branches through VPN, having a VPN channel between the ISP
and the HQ ensures that the web portal being hosted by thee network is also secured for both
organizational members and end users.
90
Branch 2 31 62 192.168.3.1
92 /26 255.255.2
55.192
192.168.3.1
93 -
192.168.3.2
54
192.168.3.2
55
ER-CS 2 2 192.168.3.1
92
/30 255.255.2
55.252
192.168.3.1
93 -
192.168.3.1
94
192.168.3.1
95
Security Policy and features
The security policies and features incorporated in securing the network are the following:
Implementing VPN: Virtual Private Networks (VPNs) are essential in the sense they can hide the
network from the view of external threats like hackers [1]. VPNs also conduct user account
verification.
Installing and configuring firewall: For medium sized businesses or small medium enterprises,
firewalls are extremely important. The ideal firewall solution can be the physical firewall device
which can also perform authentication.
WPA2 Encryption for wireless connectivity: This refers to the Wi-Fi Protected access used to
generate unique keys for each device that are to connect the network using wireless access [8].
Redundancy and Failover Plan
In most sections redundancy is noticed on firewalls. These firewalls are used to secure both
endpoints of the VPN tunnels as just having a VPN is not enough to secure the network from cyber-
attacks. A backup router is kept to ensure total network outage can be prevented if the edge router
fails. Another critical area of redundancy is observed with wireless access points [5]. This is mitigate
signal issues in wireless networks.
Implementation of VPN services
VPNs or Virtual Private networks are implanted among three connections. These are the
connection between Branch 1 and HQ, between Branch 2 and HQ and between HQ and the ISP
network. In addition to securing the branches through VPN, having a VPN channel between the ISP
and the HQ ensures that the web portal being hosted by thee network is also secured for both
organizational members and end users.
11VIRTUAL PRIVATE NETWORK
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




