Virtual Memory: Architecture, Management, and Performance
VerifiedAdded on 2022/09/11
|6
|3752
|50
Report
AI Summary
This report delves into the intricacies of virtual memory within computer architecture. It begins with an introduction to the concept, explaining how virtual memory allows computers to execute multiple programs by utilizing a combination of RAM and disk storage, addressing the limitations of physical memory. The report traces the historical evolution of virtual memory, from its early implementations to its integration in modern processors like the Intel 80286 and 80386. It then explains the background, detailing how virtual addresses are translated into physical memory locations through paging and segmentation. The report further explores memory management procedures, including the allocation of hard drive space and the impact of insufficient virtual memory. It describes the working principles of virtual memory, illustrating how the operating system and the virtual memory manager (VMM) work together to swap data between RAM and the paging file on the hard drive. The report also covers data structures and potential performance issues, such as disk thrashing, and offers suggestions for optimization. The report concludes by emphasizing the importance of virtual memory in enhancing system performance and enabling efficient multitasking.

Virtual memory in computer architecture
[Authors Name]
[Authors Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Abstract— Current technological improvements in
computer architectures and software constructions command a
revision of the virtual memory controlling upkeep delivered
by an OS. Previous virtual memory structures have not
reasonably addressed the difficulties modeled by
multiprocessor structures and the movability concerns
elevated by the massive diversity of memory management
components accessible. A computer with virtual memory
deviously manipulates the conflicting requests of several
programs within a secure quantity of physical memory. A
computer that's low on memory can execute similar programs
as one with sufficient RAM, while more gradually. In this
paper are described the fundamental concepts of virtual
memory, which can be essential for computer architecture.
I. INTRODUCTION
Modern computer structures are implementing many
different programs at a time, and most are to possess the OS
functioning and safe. The user then adds on to that the
essentials of the operator and the logics they will expose and
close. These create memory management even more
significant. The necessities of memory management are
address relocation and mapping, defense and sharing,
application organization, and lastly, virtual memory
organization. The term "Virtual memory" is a characteristic of
the OS that permits a computer to be capable of paying a lack
of physical memory by shifting data pages from RAM to disk
storage. This method is done provisionally [1]. It is calculated
to work as a mixture of RAM and area on the hard disk. This
denotes that when random memory runs low, virtual memory
can transfer documents from it to an area named a paging file.
This procedure permits for RAM to be unbound so
that a computer can finish the task. Sometimes an operator
might be displayed a statement that denotes the virtual
memory is working low, and this defines that either more
random memory wants to be added, or the dimension of the
paging file wants to be enlarged. Virtual Memory is a storing
allocation arrangement in which subordinate memory can be
located as though it were the measure of main memory. The
addresses a command may apply to reference memory are
differentiated from the locations the memory system applies to
classify physical storage positions, and program created
addresses are interpreted routinely to the logical machine
addresses.
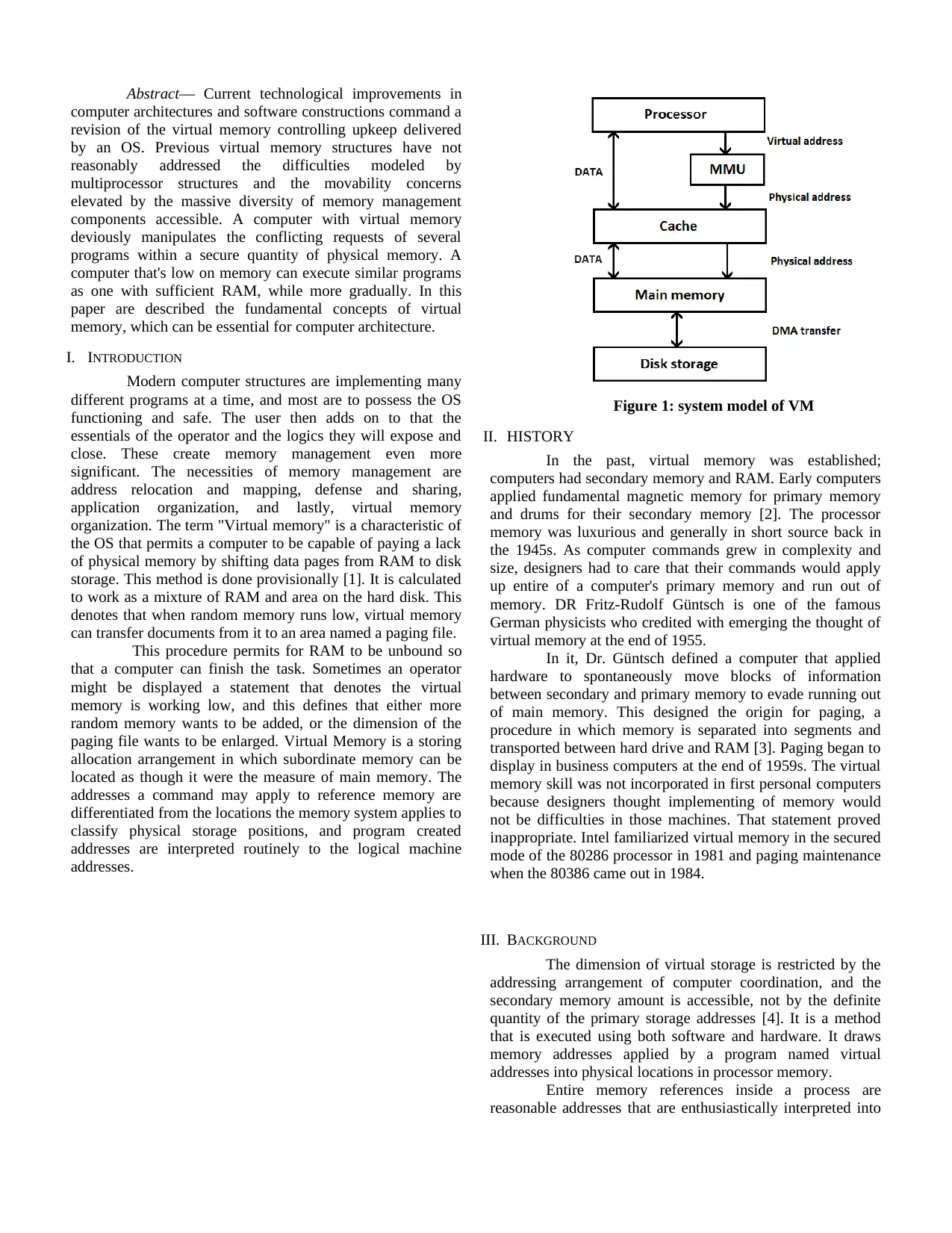
Figure 1: system model of VM
II. HISTORY
In the past, virtual memory was established;
computers had secondary memory and RAM. Early computers
applied fundamental magnetic memory for primary memory
and drums for their secondary memory [2]. The processor
memory was luxurious and generally in short source back in
the 1945s. As computer commands grew in complexity and
size, designers had to care that their commands would apply
up entire of a computer's primary memory and run out of
memory. DR Fritz-Rudolf Güntsch is one of the famous
German physicists who credited with emerging the thought of
virtual memory at the end of 1955.
In it, Dr. Güntsch defined a computer that applied
hardware to spontaneously move blocks of information
between secondary and primary memory to evade running out
of main memory. This designed the origin for paging, a
procedure in which memory is separated into segments and
transported between hard drive and RAM [3]. Paging began to
display in business computers at the end of 1959s. The virtual
memory skill was not incorporated in first personal computers
because designers thought implementing of memory would
not be difficulties in those machines. That statement proved
inappropriate. Intel familiarized virtual memory in the secured
mode of the 80286 processor in 1981 and paging maintenance
when the 80386 came out in 1984.
III. BACKGROUND
The dimension of virtual storage is restricted by the
addressing arrangement of computer coordination, and the
secondary memory amount is accessible, not by the definite
quantity of the primary storage addresses [4]. It is a method
that is executed using both software and hardware. It draws
memory addresses applied by a program named virtual
addresses into physical locations in processor memory.
Entire memory references inside a process are
reasonable addresses that are enthusiastically interpreted into
computer architectures and software constructions command a
revision of the virtual memory controlling upkeep delivered
by an OS. Previous virtual memory structures have not
reasonably addressed the difficulties modeled by
multiprocessor structures and the movability concerns
elevated by the massive diversity of memory management
components accessible. A computer with virtual memory
deviously manipulates the conflicting requests of several
programs within a secure quantity of physical memory. A
computer that's low on memory can execute similar programs
as one with sufficient RAM, while more gradually. In this
paper are described the fundamental concepts of virtual
memory, which can be essential for computer architecture.
I. INTRODUCTION
Modern computer structures are implementing many
different programs at a time, and most are to possess the OS
functioning and safe. The user then adds on to that the
essentials of the operator and the logics they will expose and
close. These create memory management even more
significant. The necessities of memory management are
address relocation and mapping, defense and sharing,
application organization, and lastly, virtual memory
organization. The term "Virtual memory" is a characteristic of
the OS that permits a computer to be capable of paying a lack
of physical memory by shifting data pages from RAM to disk
storage. This method is done provisionally [1]. It is calculated
to work as a mixture of RAM and area on the hard disk. This
denotes that when random memory runs low, virtual memory
can transfer documents from it to an area named a paging file.
This procedure permits for RAM to be unbound so
that a computer can finish the task. Sometimes an operator
might be displayed a statement that denotes the virtual
memory is working low, and this defines that either more
random memory wants to be added, or the dimension of the
paging file wants to be enlarged. Virtual Memory is a storing
allocation arrangement in which subordinate memory can be
located as though it were the measure of main memory. The
addresses a command may apply to reference memory are
differentiated from the locations the memory system applies to
classify physical storage positions, and program created
addresses are interpreted routinely to the logical machine
addresses.
Figure 1: system model of VM
II. HISTORY
In the past, virtual memory was established;
computers had secondary memory and RAM. Early computers
applied fundamental magnetic memory for primary memory
and drums for their secondary memory [2]. The processor
memory was luxurious and generally in short source back in
the 1945s. As computer commands grew in complexity and
size, designers had to care that their commands would apply
up entire of a computer's primary memory and run out of
memory. DR Fritz-Rudolf Güntsch is one of the famous
German physicists who credited with emerging the thought of
virtual memory at the end of 1955.
In it, Dr. Güntsch defined a computer that applied
hardware to spontaneously move blocks of information
between secondary and primary memory to evade running out
of main memory. This designed the origin for paging, a
procedure in which memory is separated into segments and
transported between hard drive and RAM [3]. Paging began to
display in business computers at the end of 1959s. The virtual
memory skill was not incorporated in first personal computers
because designers thought implementing of memory would
not be difficulties in those machines. That statement proved
inappropriate. Intel familiarized virtual memory in the secured
mode of the 80286 processor in 1981 and paging maintenance
when the 80386 came out in 1984.
III. BACKGROUND
The dimension of virtual storage is restricted by the
addressing arrangement of computer coordination, and the
secondary memory amount is accessible, not by the definite
quantity of the primary storage addresses [4]. It is a method
that is executed using both software and hardware. It draws
memory addresses applied by a program named virtual
addresses into physical locations in processor memory.
Entire memory references inside a process are
reasonable addresses that are enthusiastically interpreted into

physical locations at execution time. This denotes that a
procedure can be exchanged in and out of main memory like
that it conquers diverse spaces in main memory at different
times throughout the sequence of execution. On the other
hand, a procedure may be damaged into the number of bits,
and these bits want not to be incessantly positioned in the
main memory throughout execution. The arrangement of
vigorous run-time statement translation and routine of
segment or page table certifies this.
Figure 2:- Disk address allocation
If these features exist then, not every segment does
not have to be existing in the main memory throughout
execution. This defines that the compulsory pages want to be
positioned into memory when mandatory. As everybody
knows, the structure itself is applying a share of RAM. If the
user runs many applications, every application will also get its
portion of RAM. At that time operator won’t be capable of
opening any supplemental application [5]. When the
processors require more memory, it plots selected of its
memory locations out of disk drive. That denotes that users
can implement many applications than they have installed
RAM. If typical user-run several applications, at one point,
they will execute out of RAM. At that time, the CPU is
concerned there is adequate memory to accommodate entire
applications. That additional memory doesn’t primarily
happen in RAM. It’s the storage area on the hard disk drive.
IV. MANGEMENT PROCEDURES
OS has default backgrounds that regulate the quantity
of hard drive space to assign for virtual memory. That
background will work for maximum processes and
applications [6]. However, there may be intervals when it's
essential to physically reset the quantity of hard drive space
allotted to virtual memory, like with applications that trust on
fast reaction times or when the process computer has several
disk drives. When physically rearranging virtual memory, the
maximum and minimum extent of hard drive area to be
applied for virtual memory must be identified. Distributing too
little disk drive space for virtual memory can affect a
processor running out of RAM. If a structure always wants
more virtual memory location, it may be sensible to reflect
adding RAM.
Figure 3:- computer memory to secondary
memory
Virtual memory aims to increase the address space,
the background of addresses a command can utilize. For
instance, it might cover twice as several addresses as primary
memory. A logic command applying every virtual memory,
consequently, must not be capable of setting in primary
memory at once. However, the processor (computer) could
implement such a command by copying into primary memory
those parts of the program wanted at any prearranged point
throughout execution [7]. To simplify copying virtual memory
into actual memory, the OS distributes virtual memory into
pages, every of which covers a static address number. Every
page is kept on a disk drive until it is desired. When the page
is desirable, the OS copies it from disk drive to primary
memory, interpreting the virtual addresses into valid
addresses.
V. WORKING PRINCIPAL AND CONFIGUARATION
Maximum computers currently have roughly like 32
or 64 mb of RAM manageable for the processing unit to
apply. Unluckily, that amount of RAM is not enough to run
each of the programs that most operators imagine to
implement at once. With these process, the processors can do
is express at random memory for spaces that have not been
applied newly and copy them onto the disk drive. This opens
up an area in RAM to install another application. Because this
replication occurs automatically, the user doesn't even
distinguish it is occurring, and it creates the computer sense
like the open RAM space even though it only has 32
megabytes launched. Because space of hard disk is so much
inexpensive than RAM chips, it also has an excellent financial
benefit. The write or read hard drive speed is much lesser than
RAM, and the architecture of a hard drive is not geared in the
direction of accessing little data pieces at a time [8]. If the user
structure has to trust too severely on virtual memory, the user
will observe a vital performance drop. The key is to have
sufficient RAM to grip everything users tend to work on
simultaneously.
procedure can be exchanged in and out of main memory like
that it conquers diverse spaces in main memory at different
times throughout the sequence of execution. On the other
hand, a procedure may be damaged into the number of bits,
and these bits want not to be incessantly positioned in the
main memory throughout execution. The arrangement of
vigorous run-time statement translation and routine of
segment or page table certifies this.
Figure 2:- Disk address allocation
If these features exist then, not every segment does
not have to be existing in the main memory throughout
execution. This defines that the compulsory pages want to be
positioned into memory when mandatory. As everybody
knows, the structure itself is applying a share of RAM. If the
user runs many applications, every application will also get its
portion of RAM. At that time operator won’t be capable of
opening any supplemental application [5]. When the
processors require more memory, it plots selected of its
memory locations out of disk drive. That denotes that users
can implement many applications than they have installed
RAM. If typical user-run several applications, at one point,
they will execute out of RAM. At that time, the CPU is
concerned there is adequate memory to accommodate entire
applications. That additional memory doesn’t primarily
happen in RAM. It’s the storage area on the hard disk drive.
IV. MANGEMENT PROCEDURES
OS has default backgrounds that regulate the quantity
of hard drive space to assign for virtual memory. That
background will work for maximum processes and
applications [6]. However, there may be intervals when it's
essential to physically reset the quantity of hard drive space
allotted to virtual memory, like with applications that trust on
fast reaction times or when the process computer has several
disk drives. When physically rearranging virtual memory, the
maximum and minimum extent of hard drive area to be
applied for virtual memory must be identified. Distributing too
little disk drive space for virtual memory can affect a
processor running out of RAM. If a structure always wants
more virtual memory location, it may be sensible to reflect
adding RAM.
Figure 3:- computer memory to secondary
memory
Virtual memory aims to increase the address space,
the background of addresses a command can utilize. For
instance, it might cover twice as several addresses as primary
memory. A logic command applying every virtual memory,
consequently, must not be capable of setting in primary
memory at once. However, the processor (computer) could
implement such a command by copying into primary memory
those parts of the program wanted at any prearranged point
throughout execution [7]. To simplify copying virtual memory
into actual memory, the OS distributes virtual memory into
pages, every of which covers a static address number. Every
page is kept on a disk drive until it is desired. When the page
is desirable, the OS copies it from disk drive to primary
memory, interpreting the virtual addresses into valid
addresses.
V. WORKING PRINCIPAL AND CONFIGUARATION
Maximum computers currently have roughly like 32
or 64 mb of RAM manageable for the processing unit to
apply. Unluckily, that amount of RAM is not enough to run
each of the programs that most operators imagine to
implement at once. With these process, the processors can do
is express at random memory for spaces that have not been
applied newly and copy them onto the disk drive. This opens
up an area in RAM to install another application. Because this
replication occurs automatically, the user doesn't even
distinguish it is occurring, and it creates the computer sense
like the open RAM space even though it only has 32
megabytes launched. Because space of hard disk is so much
inexpensive than RAM chips, it also has an excellent financial
benefit. The write or read hard drive speed is much lesser than
RAM, and the architecture of a hard drive is not geared in the
direction of accessing little data pieces at a time [8]. If the user
structure has to trust too severely on virtual memory, the user
will observe a vital performance drop. The key is to have
sufficient RAM to grip everything users tend to work on
simultaneously.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 4:- Processor to Disk memory data transfer process
Windows 98 is an instance of a usual OS that has
virtual memory. This has an intellectual virtual memory
manager that applies a default set to assist Windows to
distribute the hard disk area for virtual memory as wanted. For
excellent conditions, this must meet user requirements.
However, the user may want to physically construct virtual
memory, specifically if they have more than one physical
HDD or speed-critical applications.
Let’s assume that an OS wants 200 MB of memory to
grip every running program. But there's only 40 MB of
accessible physical memory kept on the RAM chips. The
operating system will then set up 200 MB of VM & will apply
a program named the VMM to cope with that 200 MB. These
will generate disk drive file that is 160 MB (200 – 40) in
dimension to account for the additional memory that’s desired.
The operating will now keep addressing l as if there were
necessarily 200 MB of actual memory kept in the RAM.
However, there's only 40 MB [9]. It is the accountability of
the VMM to contract with the circumstance that there is only
40 MB of actual memory.
VMM generates a file on the disk drive that holds the
additional memory which desirable by the OS, which in this
case, is 160 MB in size. This file named a paging file & plays
an imperative role in the work of virtual memory. The paging
file shared with the RAM accounts for every of the memory.
Each time the OS wants a memory block that’s not in the main
access memory, the VMM receipts a block from the actual
memory that hasn’t applied newly, writes it to the paging file
& then declaims the memory block that the OS needs from the
paging file. The VMM then receipts the memory block from
the paging file & changes it into the leading memory – in
place of the longstanding block. This procedure is named
swapping & the memory blocks that are exchanged, named
pages. There are more than a few algorithms for this
procedure, called “Page Replacement Algorithms." The pages
group that presently happens in RAM & that is dedicated to an
exact process is identified as the working background for that
method.
Figure 5:- Physical memory to Disk drive
Virtual memory characteristics are excellent, but it is
thinkable overdoing it. This can occur if the user runs several
applications, or if structures that they run want vast quantities
of memory. The difficulties are not unavoidably with the page
file themself. Meanwhile, the user can create it massively. The
operator generally takes an immense hard drive, so they can
apply a considerable space on that disk for virtual memory.
The concern is the detail that the exchanging has to happen
very commonly [10]. If the user runs several applications and
uses huge memory, as contrasting to the physical memory
implemented, then the exchanging occurs too frequently.
Currently, disk thrashing occurs less frequently, but it still can
particularly if they are applying applications that want massive
memory amounts. If the user is having difficulties with disk
thrashing, they can try and stop specific applications and
procedures. The other mechanism user can do to launch more
system memory. The procedure of taking an application from
the RAM and placing it in the page file is named paging out.
The procedure of transferring the application from the page
file back into random physical memory is named paging in.
Disk thrashing happens when the physical memory amount is
too less. In that circumstance, the information must
continuously be relocated from RAM to disk.
VI. DATA STRUCTURE
Some rudimentary memory management information
structures are applied in computers. The resident a table
applied to save monitor of evidence about free machine pages.
2) The memory unit of helping storing achieved by an
operator task, 3) the map linked list of records, every of which
defines a mapping from an addresses range to a memory
object area. Not unpredictably, these data arrangements agree
roughly to software or hardware perceptions. The local page
table agrees to a machine’s physical memory [11]. A location
record resembles a task or a procedure (in UNIX). The
memory object agrees to resource for paging. In conclusion, a
p-map agrees to a hardware’s demonstration of an address
area.
VII. TYPES
Two types of virtual memory are applicable in
computer architecture. Virtual memory can be coped with a
figure of diverse ways by a structure's operating system, and
the two most usual methods are segmentation and paging.
Segmentation:-
Segmentation is an unconventional method to
memory management, whereas an alternative of pages of
static size, procedures are assigned segments of opposing
length to accurately fulfill their necessities. That means that
dissimilar in a paged structure, and no memory is misused in a
segment. Segmentation also permits applications to
differentiate into reasonably autonomous address locations,
which can create them more straightforward to distribute, and
more protected [12]. But a difficulty with segmentation is that
since every segment is a different length, it can prime to
memory "destruction." This denotes that as segments are
distributed and de-allocated, small memory chunks can be
Windows 98 is an instance of a usual OS that has
virtual memory. This has an intellectual virtual memory
manager that applies a default set to assist Windows to
distribute the hard disk area for virtual memory as wanted. For
excellent conditions, this must meet user requirements.
However, the user may want to physically construct virtual
memory, specifically if they have more than one physical
HDD or speed-critical applications.
Let’s assume that an OS wants 200 MB of memory to
grip every running program. But there's only 40 MB of
accessible physical memory kept on the RAM chips. The
operating system will then set up 200 MB of VM & will apply
a program named the VMM to cope with that 200 MB. These
will generate disk drive file that is 160 MB (200 – 40) in
dimension to account for the additional memory that’s desired.
The operating will now keep addressing l as if there were
necessarily 200 MB of actual memory kept in the RAM.
However, there's only 40 MB [9]. It is the accountability of
the VMM to contract with the circumstance that there is only
40 MB of actual memory.
VMM generates a file on the disk drive that holds the
additional memory which desirable by the OS, which in this
case, is 160 MB in size. This file named a paging file & plays
an imperative role in the work of virtual memory. The paging
file shared with the RAM accounts for every of the memory.
Each time the OS wants a memory block that’s not in the main
access memory, the VMM receipts a block from the actual
memory that hasn’t applied newly, writes it to the paging file
& then declaims the memory block that the OS needs from the
paging file. The VMM then receipts the memory block from
the paging file & changes it into the leading memory – in
place of the longstanding block. This procedure is named
swapping & the memory blocks that are exchanged, named
pages. There are more than a few algorithms for this
procedure, called “Page Replacement Algorithms." The pages
group that presently happens in RAM & that is dedicated to an
exact process is identified as the working background for that
method.
Figure 5:- Physical memory to Disk drive
Virtual memory characteristics are excellent, but it is
thinkable overdoing it. This can occur if the user runs several
applications, or if structures that they run want vast quantities
of memory. The difficulties are not unavoidably with the page
file themself. Meanwhile, the user can create it massively. The
operator generally takes an immense hard drive, so they can
apply a considerable space on that disk for virtual memory.
The concern is the detail that the exchanging has to happen
very commonly [10]. If the user runs several applications and
uses huge memory, as contrasting to the physical memory
implemented, then the exchanging occurs too frequently.
Currently, disk thrashing occurs less frequently, but it still can
particularly if they are applying applications that want massive
memory amounts. If the user is having difficulties with disk
thrashing, they can try and stop specific applications and
procedures. The other mechanism user can do to launch more
system memory. The procedure of taking an application from
the RAM and placing it in the page file is named paging out.
The procedure of transferring the application from the page
file back into random physical memory is named paging in.
Disk thrashing happens when the physical memory amount is
too less. In that circumstance, the information must
continuously be relocated from RAM to disk.
VI. DATA STRUCTURE
Some rudimentary memory management information
structures are applied in computers. The resident a table
applied to save monitor of evidence about free machine pages.
2) The memory unit of helping storing achieved by an
operator task, 3) the map linked list of records, every of which
defines a mapping from an addresses range to a memory
object area. Not unpredictably, these data arrangements agree
roughly to software or hardware perceptions. The local page
table agrees to a machine’s physical memory [11]. A location
record resembles a task or a procedure (in UNIX). The
memory object agrees to resource for paging. In conclusion, a
p-map agrees to a hardware’s demonstration of an address
area.
VII. TYPES
Two types of virtual memory are applicable in
computer architecture. Virtual memory can be coped with a
figure of diverse ways by a structure's operating system, and
the two most usual methods are segmentation and paging.
Segmentation:-
Segmentation is an unconventional method to
memory management, whereas an alternative of pages of
static size, procedures are assigned segments of opposing
length to accurately fulfill their necessities. That means that
dissimilar in a paged structure, and no memory is misused in a
segment. Segmentation also permits applications to
differentiate into reasonably autonomous address locations,
which can create them more straightforward to distribute, and
more protected [12]. But a difficulty with segmentation is that
since every segment is a different length, it can prime to
memory "destruction." This denotes that as segments are
distributed and de-allocated, small memory chunks can be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
missing distributed nearby, which are too trivial to be
beneficial.
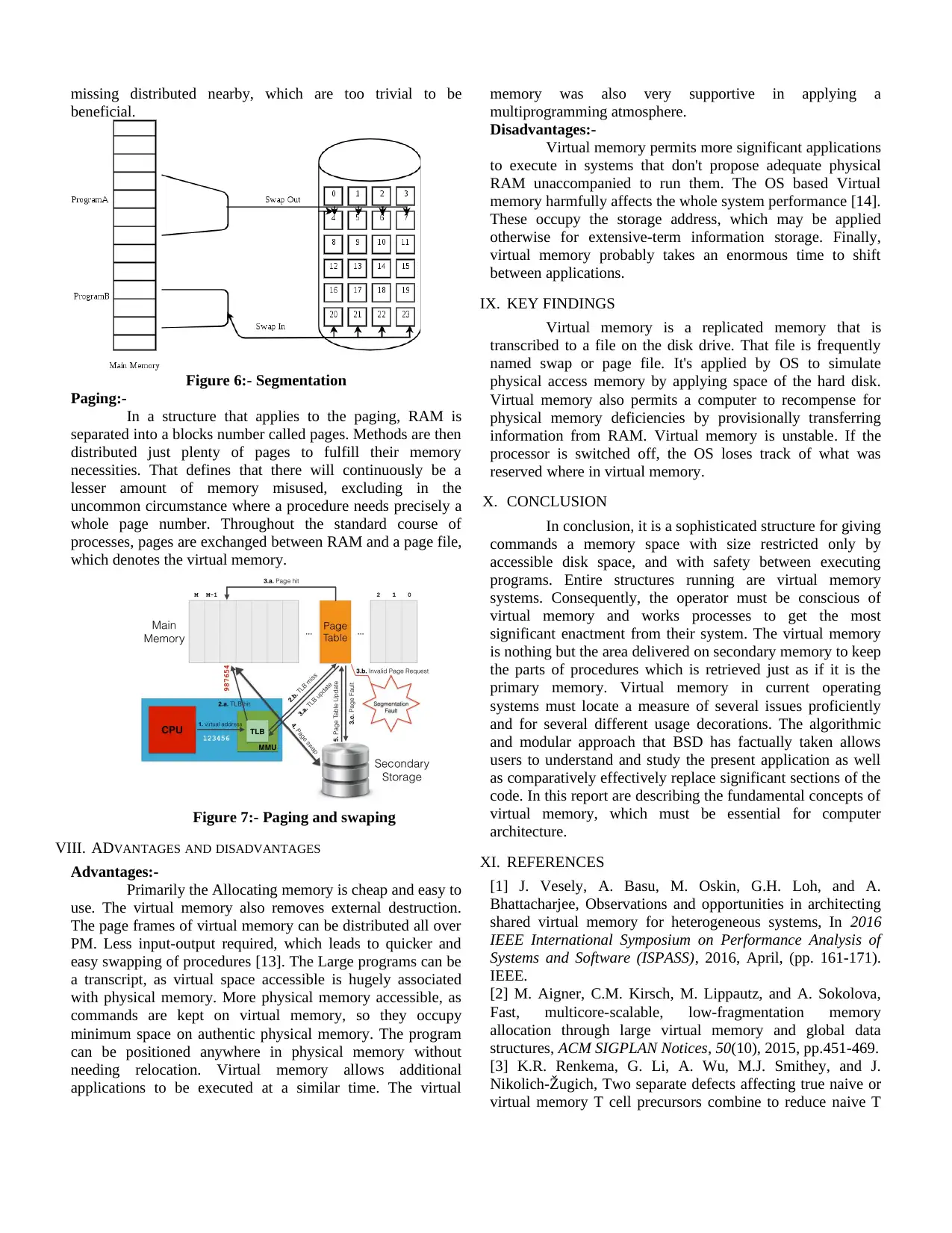
Figure 6:- Segmentation
Paging:-
In a structure that applies to the paging, RAM is
separated into a blocks number called pages. Methods are then
distributed just plenty of pages to fulfill their memory
necessities. That defines that there will continuously be a
lesser amount of memory misused, excluding in the
uncommon circumstance where a procedure needs precisely a
whole page number. Throughout the standard course of
processes, pages are exchanged between RAM and a page file,
which denotes the virtual memory.
Figure 7:- Paging and swaping
VIII. ADVANTAGES AND DISADVANTAGES
Advantages:-
Primarily the Allocating memory is cheap and easy to
use. The virtual memory also removes external destruction.
The page frames of virtual memory can be distributed all over
PM. Less input-output required, which leads to quicker and
easy swapping of procedures [13]. The Large programs can be
a transcript, as virtual space accessible is hugely associated
with physical memory. More physical memory accessible, as
commands are kept on virtual memory, so they occupy
minimum space on authentic physical memory. The program
can be positioned anywhere in physical memory without
needing relocation. Virtual memory allows additional
applications to be executed at a similar time. The virtual
memory was also very supportive in applying a
multiprogramming atmosphere.
Disadvantages:-
Virtual memory permits more significant applications
to execute in systems that don't propose adequate physical
RAM unaccompanied to run them. The OS based Virtual
memory harmfully affects the whole system performance [14].
These occupy the storage address, which may be applied
otherwise for extensive-term information storage. Finally,
virtual memory probably takes an enormous time to shift
between applications.
IX. KEY FINDINGS
Virtual memory is a replicated memory that is
transcribed to a file on the disk drive. That file is frequently
named swap or page file. It's applied by OS to simulate
physical access memory by applying space of the hard disk.
Virtual memory also permits a computer to recompense for
physical memory deficiencies by provisionally transferring
information from RAM. Virtual memory is unstable. If the
processor is switched off, the OS loses track of what was
reserved where in virtual memory.
X. CONCLUSION
In conclusion, it is a sophisticated structure for giving
commands a memory space with size restricted only by
accessible disk space, and with safety between executing
programs. Entire structures running are virtual memory
systems. Consequently, the operator must be conscious of
virtual memory and works processes to get the most
significant enactment from their system. The virtual memory
is nothing but the area delivered on secondary memory to keep
the parts of procedures which is retrieved just as if it is the
primary memory. Virtual memory in current operating
systems must locate a measure of several issues proficiently
and for several different usage decorations. The algorithmic
and modular approach that BSD has factually taken allows
users to understand and study the present application as well
as comparatively effectively replace significant sections of the
code. In this report are describing the fundamental concepts of
virtual memory, which must be essential for computer
architecture.
XI. REFERENCES
[1] J. Vesely, A. Basu, M. Oskin, G.H. Loh, and A.
Bhattacharjee, Observations and opportunities in architecting
shared virtual memory for heterogeneous systems, In 2016
IEEE International Symposium on Performance Analysis of
Systems and Software (ISPASS), 2016, April, (pp. 161-171).
IEEE.
[2] M. Aigner, C.M. Kirsch, M. Lippautz, and A. Sokolova,
Fast, multicore-scalable, low-fragmentation memory
allocation through large virtual memory and global data
structures, ACM SIGPLAN Notices, 50(10), 2015, pp.451-469.
[3] K.R. Renkema, G. Li, A. Wu, M.J. Smithey, and J.
Nikolich-Žugich, Two separate defects affecting true naive or
virtual memory T cell precursors combine to reduce naive T
beneficial.
Figure 6:- Segmentation
Paging:-
In a structure that applies to the paging, RAM is
separated into a blocks number called pages. Methods are then
distributed just plenty of pages to fulfill their memory
necessities. That defines that there will continuously be a
lesser amount of memory misused, excluding in the
uncommon circumstance where a procedure needs precisely a
whole page number. Throughout the standard course of
processes, pages are exchanged between RAM and a page file,
which denotes the virtual memory.
Figure 7:- Paging and swaping
VIII. ADVANTAGES AND DISADVANTAGES
Advantages:-
Primarily the Allocating memory is cheap and easy to
use. The virtual memory also removes external destruction.
The page frames of virtual memory can be distributed all over
PM. Less input-output required, which leads to quicker and
easy swapping of procedures [13]. The Large programs can be
a transcript, as virtual space accessible is hugely associated
with physical memory. More physical memory accessible, as
commands are kept on virtual memory, so they occupy
minimum space on authentic physical memory. The program
can be positioned anywhere in physical memory without
needing relocation. Virtual memory allows additional
applications to be executed at a similar time. The virtual
memory was also very supportive in applying a
multiprogramming atmosphere.
Disadvantages:-
Virtual memory permits more significant applications
to execute in systems that don't propose adequate physical
RAM unaccompanied to run them. The OS based Virtual
memory harmfully affects the whole system performance [14].
These occupy the storage address, which may be applied
otherwise for extensive-term information storage. Finally,
virtual memory probably takes an enormous time to shift
between applications.
IX. KEY FINDINGS
Virtual memory is a replicated memory that is
transcribed to a file on the disk drive. That file is frequently
named swap or page file. It's applied by OS to simulate
physical access memory by applying space of the hard disk.
Virtual memory also permits a computer to recompense for
physical memory deficiencies by provisionally transferring
information from RAM. Virtual memory is unstable. If the
processor is switched off, the OS loses track of what was
reserved where in virtual memory.
X. CONCLUSION
In conclusion, it is a sophisticated structure for giving
commands a memory space with size restricted only by
accessible disk space, and with safety between executing
programs. Entire structures running are virtual memory
systems. Consequently, the operator must be conscious of
virtual memory and works processes to get the most
significant enactment from their system. The virtual memory
is nothing but the area delivered on secondary memory to keep
the parts of procedures which is retrieved just as if it is the
primary memory. Virtual memory in current operating
systems must locate a measure of several issues proficiently
and for several different usage decorations. The algorithmic
and modular approach that BSD has factually taken allows
users to understand and study the present application as well
as comparatively effectively replace significant sections of the
code. In this report are describing the fundamental concepts of
virtual memory, which must be essential for computer
architecture.
XI. REFERENCES
[1] J. Vesely, A. Basu, M. Oskin, G.H. Loh, and A.
Bhattacharjee, Observations and opportunities in architecting
shared virtual memory for heterogeneous systems, In 2016
IEEE International Symposium on Performance Analysis of
Systems and Software (ISPASS), 2016, April, (pp. 161-171).
IEEE.
[2] M. Aigner, C.M. Kirsch, M. Lippautz, and A. Sokolova,
Fast, multicore-scalable, low-fragmentation memory
allocation through large virtual memory and global data
structures, ACM SIGPLAN Notices, 50(10), 2015, pp.451-469.
[3] K.R. Renkema, G. Li, A. Wu, M.J. Smithey, and J.
Nikolich-Žugich, Two separate defects affecting true naive or
virtual memory T cell precursors combine to reduce naive T

cell responses with aging. The Journal of Immunology, 192(1),
2014, pp.151-159.
[4] J. Gandhi, V. Karakostas, F. Ayar, A. Cristal, M.D. Hill,
K.S. McKinley, M. Nemirovsky, M.M Swift, and O.S. Ünsal,
Range translations for fast virtual memory. IEEE Micro,
36(3), 2016, pp.118-126.
[5] V. Kurzweil, A. LaRoche, and P.M. Oliver, Increased
peripheral IL-4 leads to an expanded virtual memory CD8+
population, The Journal of Immunology, 192(12), 2014,
pp.5643-5651.
[6] L. Van Kaer, Innate and virtual memory T cells in man,
European journal of immunology, 45(7), 2015, pp.1916-1920.
[7] V. Medina, and J.M. García, A survey of migration
mechanisms of virtual machines, ACM Computing Surveys
(CSUR), 46(3), 2014, pp.1-33.
[8] P. Weisberg and Y. Wiseman, Virtual memory systems
should use larger pages, Advanced Science and Technology
Letters, 106, 2015. ,pp.1-4.
[9] P. Weisberg and Y. Wiseman, Virtual Memory Systems
Should Use Larger Pages rather than the Traditional 4KB
Pages, International Journal of Hybrid Information
Technology, 8(8), 2015, pp.57-68.
[10] Y. Soma, B. Gerofi, and Y. Ishikawa, Revisiting virtual
memory for high performance computing on manycore
architectures: a hybrid segmentation kernel approach. In
Proceedings of the 4th International Workshop on Runtime
and Operating Systems for Supercomputers, 2014, June, (pp.
1-8).
[11] A. Drobek, A. Moudra, D. Mueller, M. Huranova, V.
Horkova, M. Pribikova, R. Ivanek, S. Oberle, D. Zehn, K.D.
McCoy, and P. Draber, Strong homeostatic TCR signals
induce formation of self‐tolerant virtual memory CD8 T cells,
The EMBO journal, 37(14), 2018.
[12] P. Vogel, A. Kurth, J. Weinbuch, A. Marongiu, and L.
Benini, Efficient virtual memory sharing via on-accelerator
page table walking in heterogeneous embedded SoCs, ACM
Transactions on Embedded Computing Systems (TECS),
16(5s), 2017, pp.1-19.
[13] J. Ahn, S. Yoo, O. Mutlu, and K. Choi, PIM-enabled
instructions: a low-overhead, locality-aware processing-in-
memory architecture, In 2015 ACM/IEEE 42nd Annual
International Symposium on Computer Architecture (ISCA),
2015, June (pp. 336-348). IEEE.
[14] F. Winterstein, and G. Constantinides, December. Pass a
pointer: Exploring shared virtual memory abstractions in
OpenCL tools for FPGAs, In 2017 International Conference
on Field Programmable Technology (ICFPT), 2017, (pp. 104-
111). IEEE.
2014, pp.151-159.
[4] J. Gandhi, V. Karakostas, F. Ayar, A. Cristal, M.D. Hill,
K.S. McKinley, M. Nemirovsky, M.M Swift, and O.S. Ünsal,
Range translations for fast virtual memory. IEEE Micro,
36(3), 2016, pp.118-126.
[5] V. Kurzweil, A. LaRoche, and P.M. Oliver, Increased
peripheral IL-4 leads to an expanded virtual memory CD8+
population, The Journal of Immunology, 192(12), 2014,
pp.5643-5651.
[6] L. Van Kaer, Innate and virtual memory T cells in man,
European journal of immunology, 45(7), 2015, pp.1916-1920.
[7] V. Medina, and J.M. García, A survey of migration
mechanisms of virtual machines, ACM Computing Surveys
(CSUR), 46(3), 2014, pp.1-33.
[8] P. Weisberg and Y. Wiseman, Virtual memory systems
should use larger pages, Advanced Science and Technology
Letters, 106, 2015. ,pp.1-4.
[9] P. Weisberg and Y. Wiseman, Virtual Memory Systems
Should Use Larger Pages rather than the Traditional 4KB
Pages, International Journal of Hybrid Information
Technology, 8(8), 2015, pp.57-68.
[10] Y. Soma, B. Gerofi, and Y. Ishikawa, Revisiting virtual
memory for high performance computing on manycore
architectures: a hybrid segmentation kernel approach. In
Proceedings of the 4th International Workshop on Runtime
and Operating Systems for Supercomputers, 2014, June, (pp.
1-8).
[11] A. Drobek, A. Moudra, D. Mueller, M. Huranova, V.
Horkova, M. Pribikova, R. Ivanek, S. Oberle, D. Zehn, K.D.
McCoy, and P. Draber, Strong homeostatic TCR signals
induce formation of self‐tolerant virtual memory CD8 T cells,
The EMBO journal, 37(14), 2018.
[12] P. Vogel, A. Kurth, J. Weinbuch, A. Marongiu, and L.
Benini, Efficient virtual memory sharing via on-accelerator
page table walking in heterogeneous embedded SoCs, ACM
Transactions on Embedded Computing Systems (TECS),
16(5s), 2017, pp.1-19.
[13] J. Ahn, S. Yoo, O. Mutlu, and K. Choi, PIM-enabled
instructions: a low-overhead, locality-aware processing-in-
memory architecture, In 2015 ACM/IEEE 42nd Annual
International Symposium on Computer Architecture (ISCA),
2015, June (pp. 336-348). IEEE.
[14] F. Winterstein, and G. Constantinides, December. Pass a
pointer: Exploring shared virtual memory abstractions in
OpenCL tools for FPGAs, In 2017 International Conference
on Field Programmable Technology (ICFPT), 2017, (pp. 104-
111). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


