Virtual Networking
VerifiedAdded on 2023/04/21
|11
|3019
|90
AI Summary
This report discusses the creation of a medium-sized enterprise for connecting each department of an organization. It covers the scope, limitations, requirements, solution design, network topology, IP addressing, security features, redundancy and failover plans, and implementation of VPN service.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: VIRTUAL NETWORKING
Virtual Networking
[Name of the Student]
[Name of the University]
[Author note]
Virtual Networking
[Name of the Student]
[Name of the University]
[Author note]
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1VIRTUAL NETWORKING
Table of Contents
Introduction:...................................................................................................................2
Scopes and Limitations:.................................................................................................2
Requirements:................................................................................................................3
Solution Design..............................................................................................................4
a. Logical Design.......................................................................................................4
b. Physical Design......................................................................................................4
c. Network Topology:................................................................................................4
d. IP Addressing.........................................................................................................5
e. Security features and Policies:...............................................................................6
f. redundancy and the Failover Plans:........................................................................6
g. Implementation of the VPN service:......................................................................6
Confidentiality of the data:...........................................................................7
Data integrity:...............................................................................................7
Authentication of the data origin:.................................................................7
Data tunneling:..............................................................................................7
Conclusion:....................................................................................................................8
Table of Contents
Introduction:...................................................................................................................2
Scopes and Limitations:.................................................................................................2
Requirements:................................................................................................................3
Solution Design..............................................................................................................4
a. Logical Design.......................................................................................................4
b. Physical Design......................................................................................................4
c. Network Topology:................................................................................................4
d. IP Addressing.........................................................................................................5
e. Security features and Policies:...............................................................................6
f. redundancy and the Failover Plans:........................................................................6
g. Implementation of the VPN service:......................................................................6
Confidentiality of the data:...........................................................................7
Data integrity:...............................................................................................7
Authentication of the data origin:.................................................................7
Data tunneling:..............................................................................................7
Conclusion:....................................................................................................................8

2VIRTUAL NETWORKING
Introduction:
This report has been mainly associated with discussing the creation of a medium-sized
enterprise for the purpose of connecting each and every department of an organization so as to
improve the current capacity of the organization so as to accommodate the future growth. The
report documents all the technologies which can be applied so as to develop the new solution. The
report also consists of the scope as well as the limitations of the network along with the
requirements like the software and the hardware which are to be used for the purpose of
developing the network. Besides this, the logical design along with the physical design and the
network topologies has also been developed along with an IP address which has been created for
each of the department [1]. The security measures are deployed so as to increase eth security of the
network and to implement the VPN service so as to allow the users in getting themselves connected
to the resources in the network.
Scopes and Limitations:
The major scopes which have identified so as to develop the project include the following:
The existing network that the organization is having is to be integrated with the new devices
and the equipment which are to be used so as to reduce the network cost
The network services along with the routing devices are to be configured in accordance with
the requirements of the organization.
The existing servers are to be upgraded along with the enabling of the virtualization of the
servers so as to handle the increased number of requests by the users [2].
Installation of the wireless access points so as to secure the network from any kind of
unauthorized access.
The redundancy of the network is to be increased so as to remove the failover points and for
increasing the availability of the network resources.
Some of the major limitations of the project include the following:
The range of compatibility of the newly installed network devices with the existing
networking devices
Getting the budget and finance approved by the organization which has been assigned for
the new proposed solution.
High-security threats are to be eliminated along with the removal of the flaws that exist in
the system which in turn would be helping in increasing the work quality.
Introduction:
This report has been mainly associated with discussing the creation of a medium-sized
enterprise for the purpose of connecting each and every department of an organization so as to
improve the current capacity of the organization so as to accommodate the future growth. The
report documents all the technologies which can be applied so as to develop the new solution. The
report also consists of the scope as well as the limitations of the network along with the
requirements like the software and the hardware which are to be used for the purpose of
developing the network. Besides this, the logical design along with the physical design and the
network topologies has also been developed along with an IP address which has been created for
each of the department [1]. The security measures are deployed so as to increase eth security of the
network and to implement the VPN service so as to allow the users in getting themselves connected
to the resources in the network.
Scopes and Limitations:
The major scopes which have identified so as to develop the project include the following:
The existing network that the organization is having is to be integrated with the new devices
and the equipment which are to be used so as to reduce the network cost
The network services along with the routing devices are to be configured in accordance with
the requirements of the organization.
The existing servers are to be upgraded along with the enabling of the virtualization of the
servers so as to handle the increased number of requests by the users [2].
Installation of the wireless access points so as to secure the network from any kind of
unauthorized access.
The redundancy of the network is to be increased so as to remove the failover points and for
increasing the availability of the network resources.
Some of the major limitations of the project include the following:
The range of compatibility of the newly installed network devices with the existing
networking devices
Getting the budget and finance approved by the organization which has been assigned for
the new proposed solution.
High-security threats are to be eliminated along with the removal of the flaws that exist in
the system which in turn would be helping in increasing the work quality.

3VIRTUAL NETWORKING
There should exist efficient skills and knowledge in the network administrator so as to
configure the network devices in accordance with the organizational needs [3].
Requirements:
Below are some of the requirements of the new network which is to be developed and this
network requirements includes the product requirements, service requirements, network
requirements, security requirements and lastly the hardware requirements.
Creation of the proposed network should be done in accordance with the quality standards
for each of the devices that are to be used in the new network
In order to reduce the response time which, the system would be having it is essential to
divide the traffics of the intranet and the internet. Besides this, it would also be helping in
showing the ease of managing the processes [4].
In order to secure the servers from any kind of unauthorized physical access, it is essential to
store them in a separate locked room.
In order to balance the loads in the network and for handling the number of requests at a
time it is essential to apply the concept of virtualization.
It is essential to make sure that the existing network is being covered along with being
extended so as to include the current components of the network in the process of
developing the new network solution.
An addressing plan is to be created which should be proper and would be associated with
the allocation of the IP address to different VLAN along with differentiating the numerous
subnets so as to save the space for the address [5].
The server is to be configured with the DHCP so as t allocate the IP address for the PC that is
to be connected to the network in an automatic way.
A firewall is to be installed at the entry as well as at the exit point of the network so as to
help in securing the network traffic as well as for securing the network from any kind of
unauthorized access.
The communication channels are to be encrypted so as to secure the network from the
various kind of attacks.
Encryption along with passwords are to be used for the wireless access points so as to
reduce the risks related to unauthorized or illegal access.
Proper cabling is to be used so as to connect the devices which are installed in various
locations of the network.
There should exist efficient skills and knowledge in the network administrator so as to
configure the network devices in accordance with the organizational needs [3].
Requirements:
Below are some of the requirements of the new network which is to be developed and this
network requirements includes the product requirements, service requirements, network
requirements, security requirements and lastly the hardware requirements.
Creation of the proposed network should be done in accordance with the quality standards
for each of the devices that are to be used in the new network
In order to reduce the response time which, the system would be having it is essential to
divide the traffics of the intranet and the internet. Besides this, it would also be helping in
showing the ease of managing the processes [4].
In order to secure the servers from any kind of unauthorized physical access, it is essential to
store them in a separate locked room.
In order to balance the loads in the network and for handling the number of requests at a
time it is essential to apply the concept of virtualization.
It is essential to make sure that the existing network is being covered along with being
extended so as to include the current components of the network in the process of
developing the new network solution.
An addressing plan is to be created which should be proper and would be associated with
the allocation of the IP address to different VLAN along with differentiating the numerous
subnets so as to save the space for the address [5].
The server is to be configured with the DHCP so as t allocate the IP address for the PC that is
to be connected to the network in an automatic way.
A firewall is to be installed at the entry as well as at the exit point of the network so as to
help in securing the network traffic as well as for securing the network from any kind of
unauthorized access.
The communication channels are to be encrypted so as to secure the network from the
various kind of attacks.
Encryption along with passwords are to be used for the wireless access points so as to
reduce the risks related to unauthorized or illegal access.
Proper cabling is to be used so as to connect the devices which are installed in various
locations of the network.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
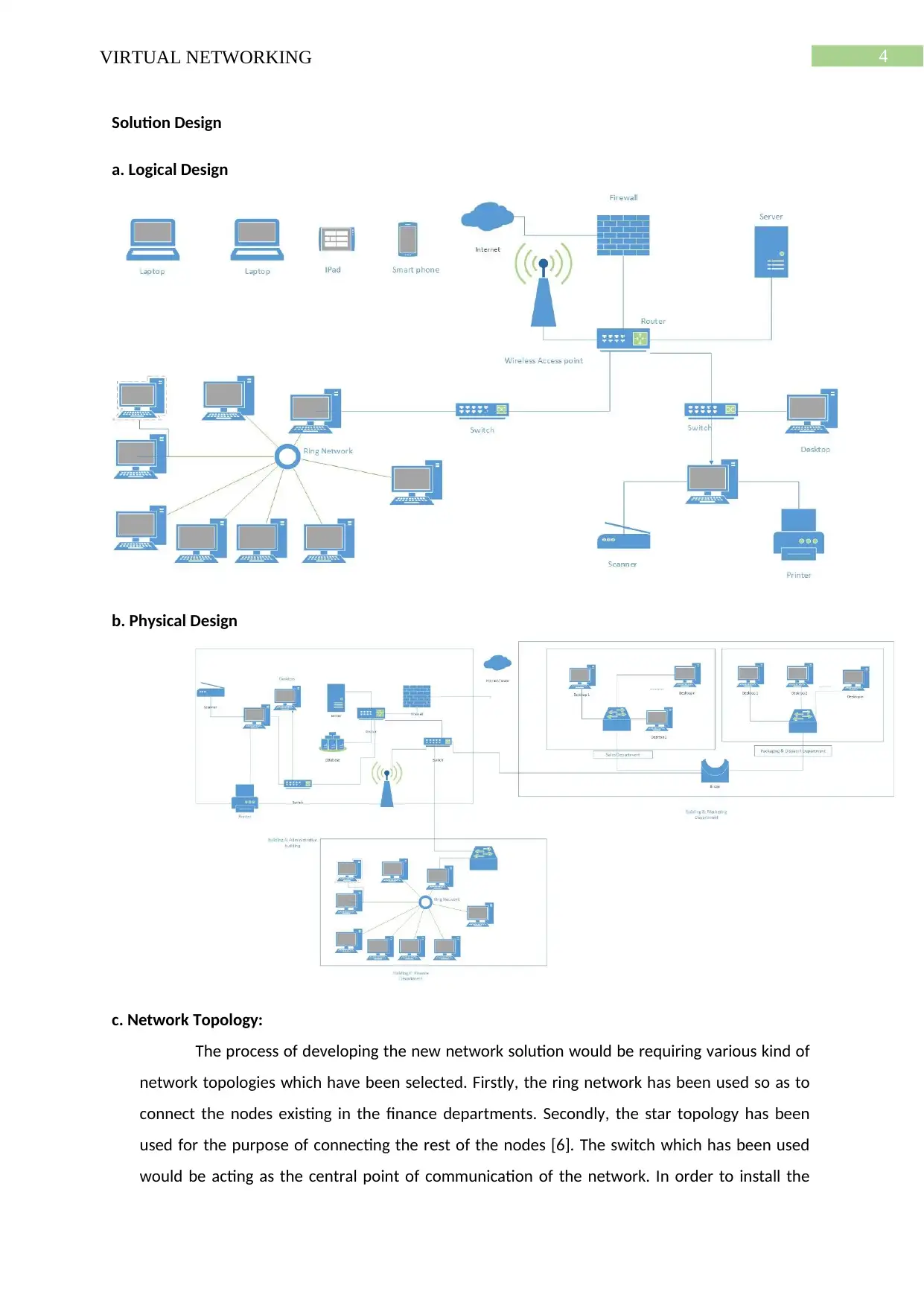
4VIRTUAL NETWORKING
Solution Design
a. Logical Design
b. Physical Design
c. Network Topology:
The process of developing the new network solution would be requiring various kind of
network topologies which have been selected. Firstly, the ring network has been used so as to
connect the nodes existing in the finance departments. Secondly, the star topology has been
used for the purpose of connecting the rest of the nodes [6]. The switch which has been used
would be acting as the central point of communication of the network. In order to install the
Solution Design
a. Logical Design
b. Physical Design
c. Network Topology:
The process of developing the new network solution would be requiring various kind of
network topologies which have been selected. Firstly, the ring network has been used so as to
connect the nodes existing in the finance departments. Secondly, the star topology has been
used for the purpose of connecting the rest of the nodes [6]. The switch which has been used
would be acting as the central point of communication of the network. In order to install the
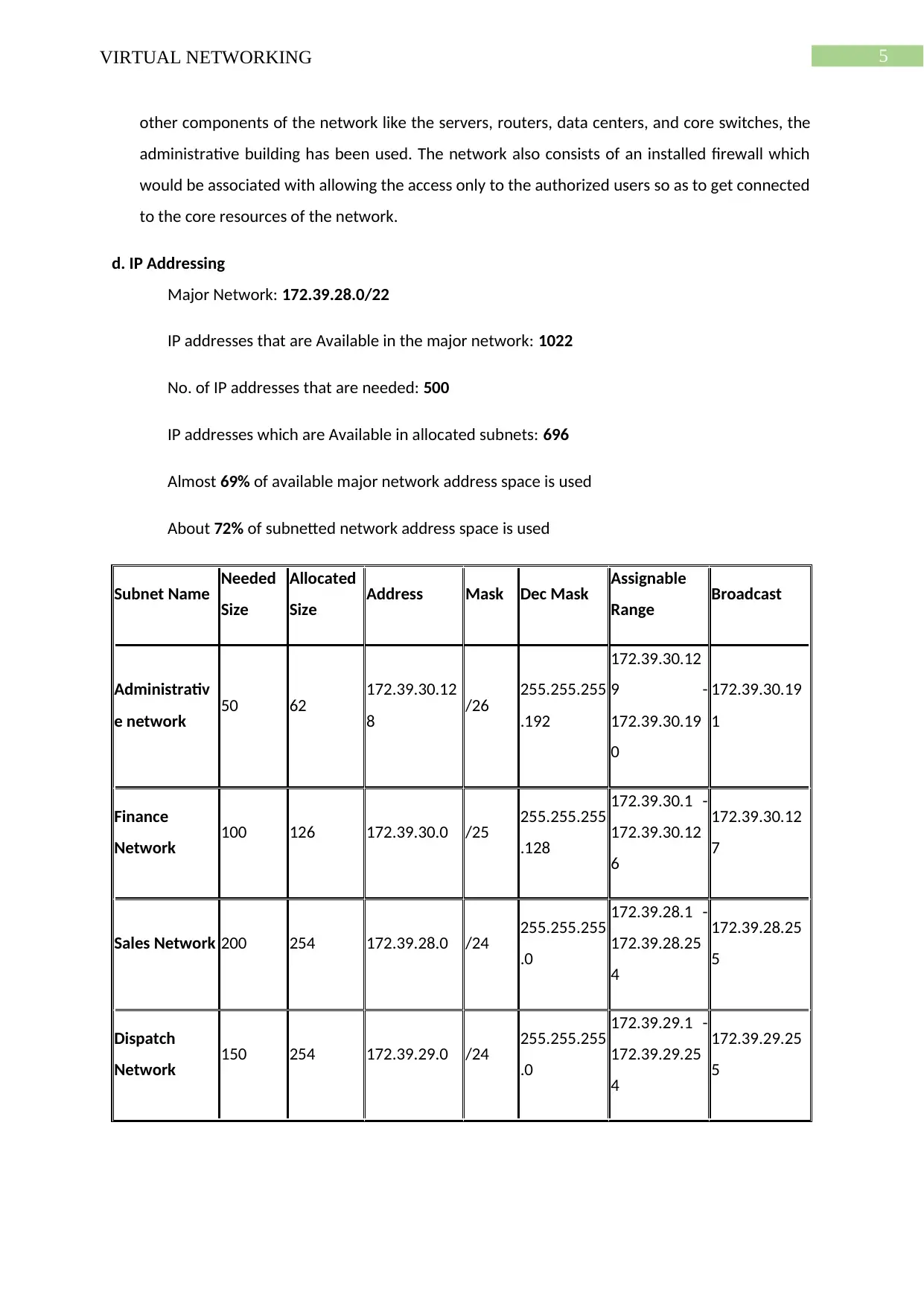
5VIRTUAL NETWORKING
other components of the network like the servers, routers, data centers, and core switches, the
administrative building has been used. The network also consists of an installed firewall which
would be associated with allowing the access only to the authorized users so as to get connected
to the core resources of the network.
d. IP Addressing
Major Network: 172.39.28.0/22
IP addresses that are Available in the major network: 1022
No. of IP addresses that are needed: 500
IP addresses which are Available in allocated subnets: 696
Almost 69% of available major network address space is used
About 72% of subnetted network address space is used
Subnet Name Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
Administrativ
e network 50 62 172.39.30.12
8 /26 255.255.255
.192
172.39.30.12
9 -
172.39.30.19
0
172.39.30.19
1
Finance
Network 100 126 172.39.30.0 /25 255.255.255
.128
172.39.30.1 -
172.39.30.12
6
172.39.30.12
7
Sales Network 200 254 172.39.28.0 /24 255.255.255
.0
172.39.28.1 -
172.39.28.25
4
172.39.28.25
5
Dispatch
Network 150 254 172.39.29.0 /24 255.255.255
.0
172.39.29.1 -
172.39.29.25
4
172.39.29.25
5
other components of the network like the servers, routers, data centers, and core switches, the
administrative building has been used. The network also consists of an installed firewall which
would be associated with allowing the access only to the authorized users so as to get connected
to the core resources of the network.
d. IP Addressing
Major Network: 172.39.28.0/22
IP addresses that are Available in the major network: 1022
No. of IP addresses that are needed: 500
IP addresses which are Available in allocated subnets: 696
Almost 69% of available major network address space is used
About 72% of subnetted network address space is used
Subnet Name Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
Administrativ
e network 50 62 172.39.30.12
8 /26 255.255.255
.192
172.39.30.12
9 -
172.39.30.19
0
172.39.30.19
1
Finance
Network 100 126 172.39.30.0 /25 255.255.255
.128
172.39.30.1 -
172.39.30.12
6
172.39.30.12
7
Sales Network 200 254 172.39.28.0 /24 255.255.255
.0
172.39.28.1 -
172.39.28.25
4
172.39.28.25
5
Dispatch
Network 150 254 172.39.29.0 /24 255.255.255
.0
172.39.29.1 -
172.39.29.25
4
172.39.29.25
5

6VIRTUAL NETWORKING
e. Security features and Policies:
There is a need of deploying a multilayer security design into the new network so as to
have a secured network solution. Besides this, there is also a need of creating a backup
mechanism for each of the devices that are installed in the network along with a dedicated
hardware device which is to be installed as well so as to limit the access of the core network
resources to all the users who would be connected to the network [7]. Besides this, it is also
essential to make sure that the network is being divided into modules which would be including
the internet access, remote access or the VPN, management of the network and services, and
lastly the wireless network and the user services. Security features like the packet filtering,
authentication, audit logs along with devices for physical security like the firewall, IPS can be
used in order to have secure internet access [8]. In order to secure the servers, they should be
installed in the DMZ zone and besides this, the servers should also be configured in such a way
so as to run only the services which are required for protecting the servers from any kind of
intrusion attacks.
The three remote access and the VPN are also essential to be secured by making use of
the authentication and authorization mechanisms [9]. Besides this, the point to point which is
established between the remote users and the remote routers must make use of the CHAP
authentication as well as the Radius server so as to centralize the process of data management
and for authentication the dial and dial-out services.
f. redundancy and the Failover Plans:
in case if any one of the links fails then there would exist a backup link which would be
used for the purpose of reaching the destination node which is connected to the network. The
core network must consist of a reductant link along with dual channel so as to establish a
connection between the source port and the destination [10]. In order to manage the business
traffic, a load balancing mechanism is to be used so as to increase the reliance upon the
network. Besides this, there is a need for creating a reliable data communication so as to
increase the availability of the resources and for increasing the availability of the VPN
connection.
g. Implementation of the VPN service:
there is a need for selecting a VPN software so as to establish a VPN tunnel between the
user and the organizational network in order to have secure communication with the
components of the network [11]. The internet would be used for the purpose of establishing a
e. Security features and Policies:
There is a need of deploying a multilayer security design into the new network so as to
have a secured network solution. Besides this, there is also a need of creating a backup
mechanism for each of the devices that are installed in the network along with a dedicated
hardware device which is to be installed as well so as to limit the access of the core network
resources to all the users who would be connected to the network [7]. Besides this, it is also
essential to make sure that the network is being divided into modules which would be including
the internet access, remote access or the VPN, management of the network and services, and
lastly the wireless network and the user services. Security features like the packet filtering,
authentication, audit logs along with devices for physical security like the firewall, IPS can be
used in order to have secure internet access [8]. In order to secure the servers, they should be
installed in the DMZ zone and besides this, the servers should also be configured in such a way
so as to run only the services which are required for protecting the servers from any kind of
intrusion attacks.
The three remote access and the VPN are also essential to be secured by making use of
the authentication and authorization mechanisms [9]. Besides this, the point to point which is
established between the remote users and the remote routers must make use of the CHAP
authentication as well as the Radius server so as to centralize the process of data management
and for authentication the dial and dial-out services.
f. redundancy and the Failover Plans:
in case if any one of the links fails then there would exist a backup link which would be
used for the purpose of reaching the destination node which is connected to the network. The
core network must consist of a reductant link along with dual channel so as to establish a
connection between the source port and the destination [10]. In order to manage the business
traffic, a load balancing mechanism is to be used so as to increase the reliance upon the
network. Besides this, there is a need for creating a reliable data communication so as to
increase the availability of the resources and for increasing the availability of the VPN
connection.
g. Implementation of the VPN service:
there is a need for selecting a VPN software so as to establish a VPN tunnel between the
user and the organizational network in order to have secure communication with the
components of the network [11]. The internet would be used for the purpose of establishing a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7VIRTUAL NETWORKING
connection between the remote users and the network. Some of the major benefits that are
likely to be gained after the implementation of the VPN service have been listed below:
The geographical connectivity would be extended
The operational cost would be reduced
Reduction of the time that is taken for the transmission by the remote users
The network topology would be simplified.
Productivity improvements
The method which is to be used so as to secure the data connection of the VPN have been
listed below:
Confidentiality of the data:
The data is to be encrypted before it is sent to the users who are connected to the network
and this is to be done via the VPN. The major reason lying behind this is that the data is to be sent in
a public network where it can be accessed by any third-party users in an illegal way.
o IPsec: This is to be applied so as to increase the levels of security and by making use
of a strong encryption algorithm along with comprehensive authentication
mechanism so as to secure the network. For this reason, two-mode tunneling is to
be used along with transportation, in which the tunnel model would be acting as the
header of the data packet which would be encrypted whereas in the transportation
mode the payload would be encrypted [12]. In order to have the application IPsec,
the system needs to be compliant with the protocol along with setting the same
policy in the network.
o PPTP or the MPPE: Multi protocols are used in the PPTP by utilization of the multiple
points to point protocol. Besides this, the 40 bits and 128 bits encryption are used so
as to encrypt the communication channel.
Data integrity:
It is very much essential to check the data which has been deceived by the other end so as to
make sure that the data is consisting of all the information and has not been tampered.
Authentication of the data origin:
It is important to identify the source of the data and besides this authentication should be
applied in order to make sure that the data is protected from any kind of attacks.
connection between the remote users and the network. Some of the major benefits that are
likely to be gained after the implementation of the VPN service have been listed below:
The geographical connectivity would be extended
The operational cost would be reduced
Reduction of the time that is taken for the transmission by the remote users
The network topology would be simplified.
Productivity improvements
The method which is to be used so as to secure the data connection of the VPN have been
listed below:
Confidentiality of the data:
The data is to be encrypted before it is sent to the users who are connected to the network
and this is to be done via the VPN. The major reason lying behind this is that the data is to be sent in
a public network where it can be accessed by any third-party users in an illegal way.
o IPsec: This is to be applied so as to increase the levels of security and by making use
of a strong encryption algorithm along with comprehensive authentication
mechanism so as to secure the network. For this reason, two-mode tunneling is to
be used along with transportation, in which the tunnel model would be acting as the
header of the data packet which would be encrypted whereas in the transportation
mode the payload would be encrypted [12]. In order to have the application IPsec,
the system needs to be compliant with the protocol along with setting the same
policy in the network.
o PPTP or the MPPE: Multi protocols are used in the PPTP by utilization of the multiple
points to point protocol. Besides this, the 40 bits and 128 bits encryption are used so
as to encrypt the communication channel.
Data integrity:
It is very much essential to check the data which has been deceived by the other end so as to
make sure that the data is consisting of all the information and has not been tampered.
Authentication of the data origin:
It is important to identify the source of the data and besides this authentication should be
applied in order to make sure that the data is protected from any kind of attacks.

8VIRTUAL NETWORKING
Data tunneling:
This the process which includes the encapsulation of the data packets into some other
packets so as have the transmission in the network [13]. This is generally used for the purpose of
hiding the identity of the users and for the purpose of protecting the source from where the
data packet has been generated.
Conclusion:
The above report helps in concluding to the fact that there is a need of preparing a network
solution only after the analysis of the requirements is done. In order to develop the new network all,
the internet security policies can be applied so as to increase the network security and this is to be
done by aligning of the business requirements. Besides this, a list of needed equipment is to be
created so as respond in accordance to the needs of emergency conditions and for the purpose of
mitigating the various kind of risks that are associated with the process of developing the new
network solution. Additionally, the creation of separate VLANs for each of the departments and
groups is one major component of the new network and this would also be helping in the creation of
separate communication channels along with helping in reducing the network congestion.
Data tunneling:
This the process which includes the encapsulation of the data packets into some other
packets so as have the transmission in the network [13]. This is generally used for the purpose of
hiding the identity of the users and for the purpose of protecting the source from where the
data packet has been generated.
Conclusion:
The above report helps in concluding to the fact that there is a need of preparing a network
solution only after the analysis of the requirements is done. In order to develop the new network all,
the internet security policies can be applied so as to increase the network security and this is to be
done by aligning of the business requirements. Besides this, a list of needed equipment is to be
created so as respond in accordance to the needs of emergency conditions and for the purpose of
mitigating the various kind of risks that are associated with the process of developing the new
network solution. Additionally, the creation of separate VLANs for each of the departments and
groups is one major component of the new network and this would also be helping in the creation of
separate communication channels along with helping in reducing the network congestion.

9VIRTUAL NETWORKING
References:
[1.] D. Choffnes, "A case for personal virtual networks." In Proceedings of the 15th ACM
Workshop on Hot Topics in Networks, pp. 8-14. ACM, 2016.
[2.] R. Moreno-Vozmediano, R. S. Montero, E. Huedo, and M. I. Llorente, "Cross-site virtual
network in cloud and fog computing." IEEE Cloud Computing 2 (2017): 46-53.
[3.] R. Munoz, R. Vilalta, R. Casellas, R. Martínez, T. Szyrkowiec, A. Autenrieth, V. López, and
D. López, "SDN/NFV orchestration for dynamic deployment of virtual SDN controllers as
VNF for multi-tenant optical networks." In Optical Fiber Communications Conference and
Exhibition (OFC), 2015, pp. 1-3. IEEE, 2015.
[4.] Sadasivarao, D. Naik, C. Liou, S. Syed, and A. Sharma, "Demystifying SDN for optical
transport networks: real-world deployments and insights." In Global Communications
Conference (GLOBECOM), 2016 IEEE, pp. 1-7. IEEE, 2016.
[5.] Vogel, D. Griebler, C. A. Maron, C. Schepke, and L. G. Fernandes, "Private IaaS clouds: a
comparative analysis of OpenNebula, CloudStack and OpenStack." In Parallel,
Distributed, and Network-Based Processing (PDP), 2016 24th Euromicro International
Conference on, pp. 672-679. IEEE, 2016.
[6.] J. T. Harmening, "Virtual private networks." In Computer and Information Security
Handbook (Third Edition), pp. 843-856. 2017.
[7.] G. Lospoto, M. Rimondini, B. G. Vignoli, and G. Di Battista, "Rethinking virtual private
networks in the software-defined era." In Integrated Network Management (IM), 2015
IFIP/IEEE International Symposium on, pp. 379-387. IEEE, 2015.
[8.] P. Massonet, S. Dupont, A. Michot, A. Levin, and M. Villari, "Enforcement of global
security policies in federated cloud networks with virtual network functions."
References:
[1.] D. Choffnes, "A case for personal virtual networks." In Proceedings of the 15th ACM
Workshop on Hot Topics in Networks, pp. 8-14. ACM, 2016.
[2.] R. Moreno-Vozmediano, R. S. Montero, E. Huedo, and M. I. Llorente, "Cross-site virtual
network in cloud and fog computing." IEEE Cloud Computing 2 (2017): 46-53.
[3.] R. Munoz, R. Vilalta, R. Casellas, R. Martínez, T. Szyrkowiec, A. Autenrieth, V. López, and
D. López, "SDN/NFV orchestration for dynamic deployment of virtual SDN controllers as
VNF for multi-tenant optical networks." In Optical Fiber Communications Conference and
Exhibition (OFC), 2015, pp. 1-3. IEEE, 2015.
[4.] Sadasivarao, D. Naik, C. Liou, S. Syed, and A. Sharma, "Demystifying SDN for optical
transport networks: real-world deployments and insights." In Global Communications
Conference (GLOBECOM), 2016 IEEE, pp. 1-7. IEEE, 2016.
[5.] Vogel, D. Griebler, C. A. Maron, C. Schepke, and L. G. Fernandes, "Private IaaS clouds: a
comparative analysis of OpenNebula, CloudStack and OpenStack." In Parallel,
Distributed, and Network-Based Processing (PDP), 2016 24th Euromicro International
Conference on, pp. 672-679. IEEE, 2016.
[6.] J. T. Harmening, "Virtual private networks." In Computer and Information Security
Handbook (Third Edition), pp. 843-856. 2017.
[7.] G. Lospoto, M. Rimondini, B. G. Vignoli, and G. Di Battista, "Rethinking virtual private
networks in the software-defined era." In Integrated Network Management (IM), 2015
IFIP/IEEE International Symposium on, pp. 379-387. IEEE, 2015.
[8.] P. Massonet, S. Dupont, A. Michot, A. Levin, and M. Villari, "Enforcement of global
security policies in federated cloud networks with virtual network functions."
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10VIRTUAL NETWORKING
In Network Computing and Applications (NCA), 2016 IEEE 15th International Symposium
on, pp. 81-84. IEEE, 2016.
[9.] BAHNASSE and N. ELKAMOUN, "Study and evaluation of the high availability of a
Dynamic Multipoint Virtual Private Network." Revue MéDiterranéEnne Des
TéLéCommunications 5, no. 2 (2015).
[10.] M. Liyanage, J. Okwuibe, M. Ylianttila, and A. Gurtov. "Secure Virtual Private LAN
Services: An Overview with Performance Evaluation." In Communication Workshop
(ICCW), 2015 IEEE International Conference on, pp. 2231-2237. IEEE, 2015.
[11.] Fajjari, N. Aitsaadi, B. Dab, and G. Pujolle, "Novel adaptive virtual network
embedding algorithm for cloud’s private backbone network." Computer
Communications 84 (2016): 12-24.
[12.] L. Bennacer, Y. Amirat, A. Chibani, A. Mellouk, and L. Ciavaglia, "Self-diagnosis
technique for virtual private networks combining Bayesian networks and case-based
reasoning." IEEE Transactions on Automation Science and Engineering 12, no. 1 (2015):
354-366.
[13.] R. Chandramouli, and R. Chandramouli, "Secure Virtual Network Configuration for
Virtual Machine (VM) Protection." NIST Special Publication 800 (2016): 125B.
In Network Computing and Applications (NCA), 2016 IEEE 15th International Symposium
on, pp. 81-84. IEEE, 2016.
[9.] BAHNASSE and N. ELKAMOUN, "Study and evaluation of the high availability of a
Dynamic Multipoint Virtual Private Network." Revue MéDiterranéEnne Des
TéLéCommunications 5, no. 2 (2015).
[10.] M. Liyanage, J. Okwuibe, M. Ylianttila, and A. Gurtov. "Secure Virtual Private LAN
Services: An Overview with Performance Evaluation." In Communication Workshop
(ICCW), 2015 IEEE International Conference on, pp. 2231-2237. IEEE, 2015.
[11.] Fajjari, N. Aitsaadi, B. Dab, and G. Pujolle, "Novel adaptive virtual network
embedding algorithm for cloud’s private backbone network." Computer
Communications 84 (2016): 12-24.
[12.] L. Bennacer, Y. Amirat, A. Chibani, A. Mellouk, and L. Ciavaglia, "Self-diagnosis
technique for virtual private networks combining Bayesian networks and case-based
reasoning." IEEE Transactions on Automation Science and Engineering 12, no. 1 (2015):
354-366.
[13.] R. Chandramouli, and R. Chandramouli, "Secure Virtual Network Configuration for
Virtual Machine (VM) Protection." NIST Special Publication 800 (2016): 125B.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



