Virtual Private Network: History, Challenges, Scope, and Future Research
VerifiedAdded on 2023/04/21
|14
|701
|165
Presentation
AI Summary
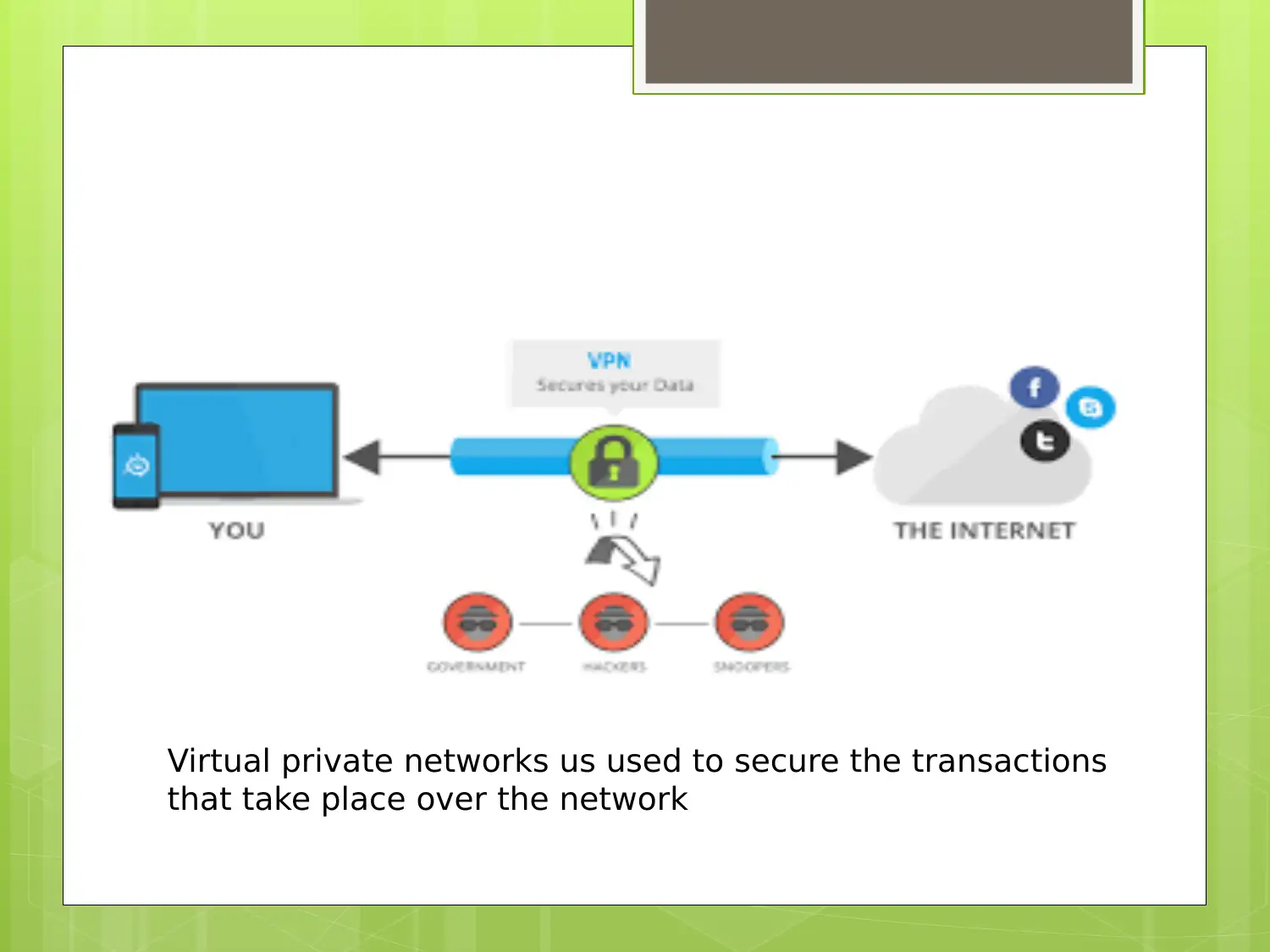
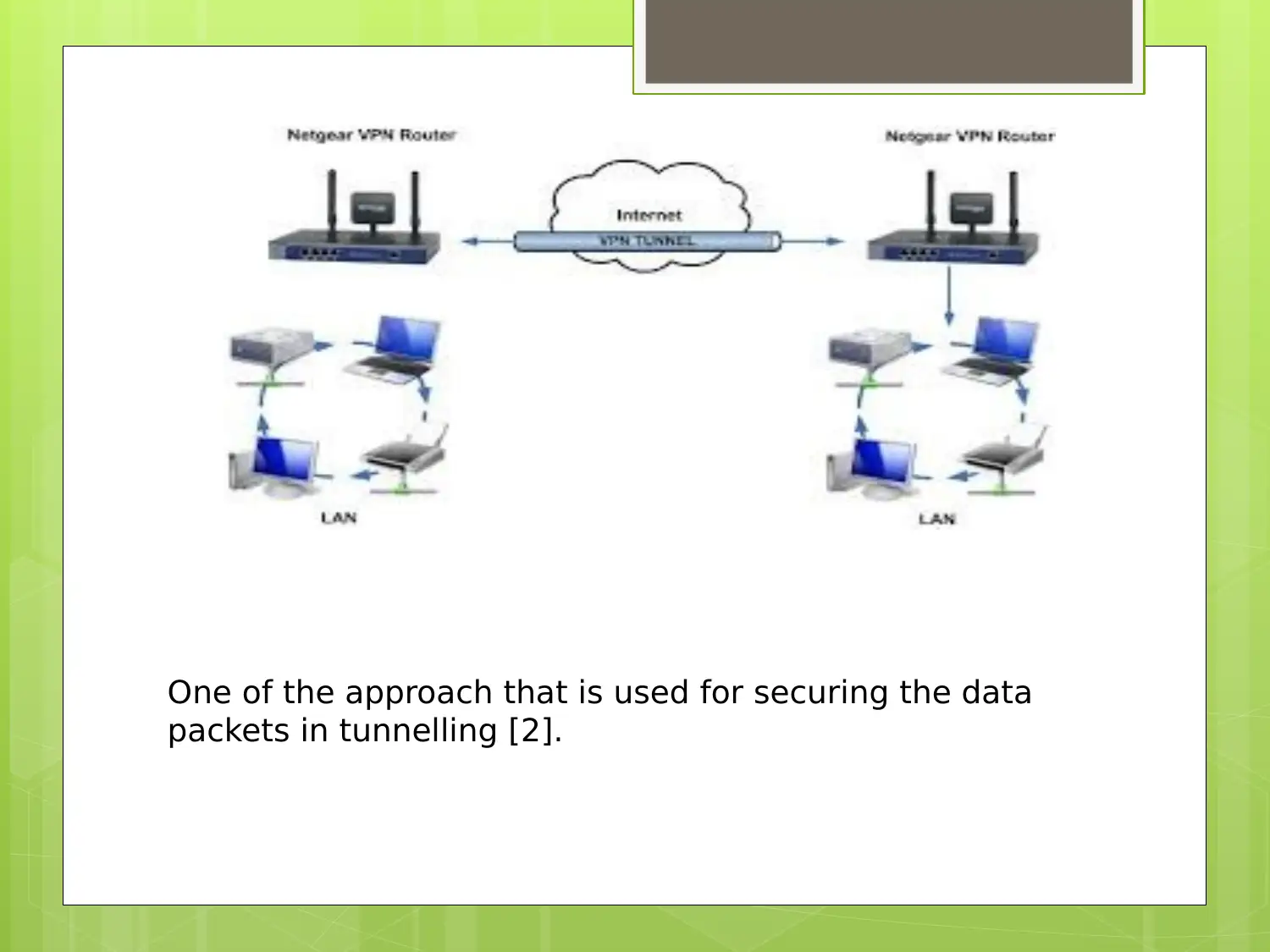
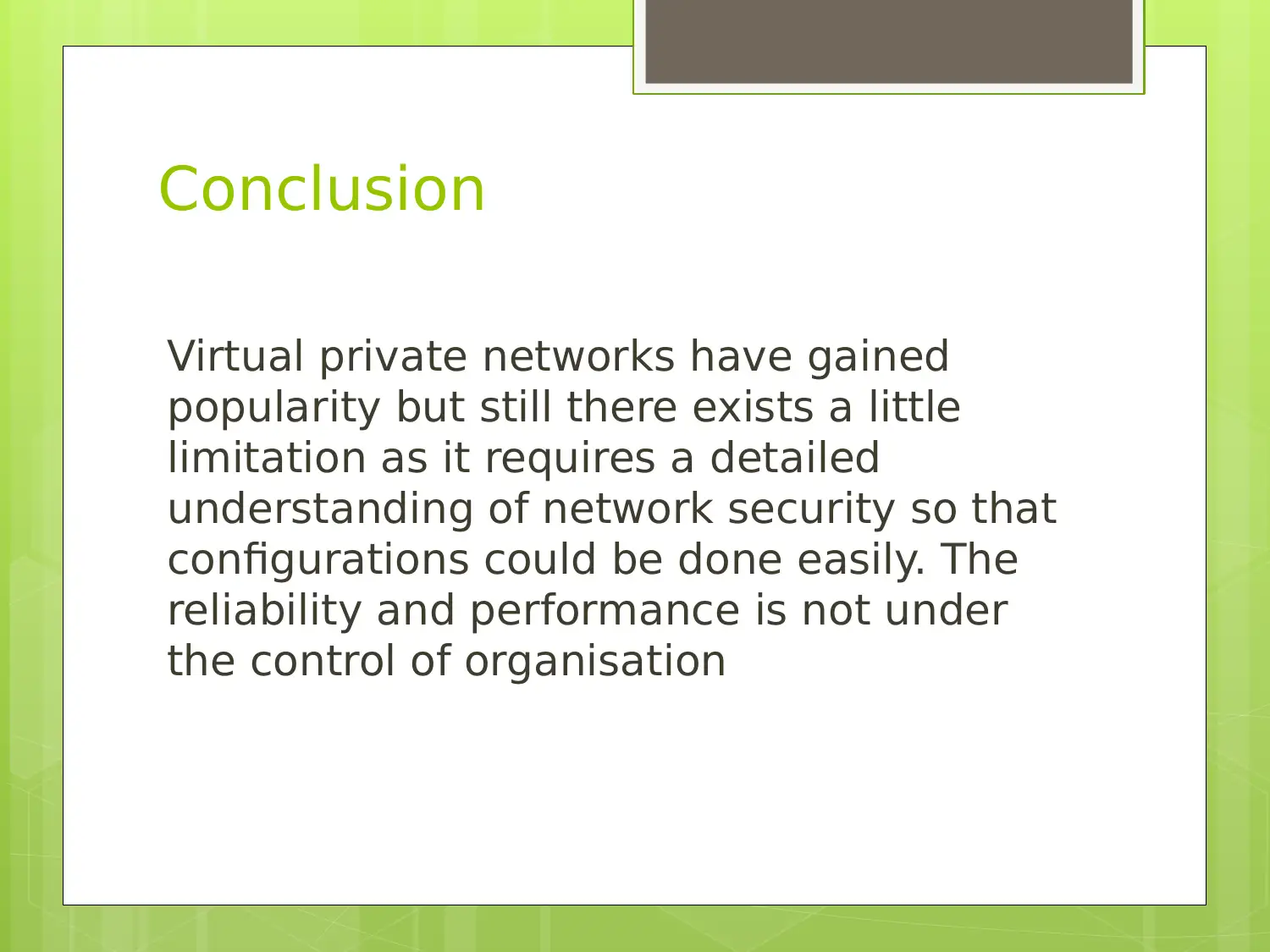
Learn about the history, challenges, scope, and future research areas of Virtual Private Networks (VPNs). Understand how VPNs provide secure transactions and prevent unauthorized access to internal networks. Explore the complexities and limitations of VPN implementation and the potential for future advancements in network security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
1 out of 14















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)