BN305: Virtual Private Networks (VPN Technologies and Security Issues)
VerifiedAdded on 2023/06/04
|5
|3844
|470
Report
AI Summary
This report examines Virtual Private Networks (VPNs), crucial for secure remote access and data transmission. It explores the benefits, technologies, and architecture of VPNs, highlighting their role in cost reduction and enhanced productivity. The report delves into the security challenges associated with VPNs, emphasizing vulnerabilities like weak passwords and the need for robust authentication methods. It discusses encryption technologies, data integrity, and various authentication methods such as two-factor authentication, digital certificates, and biometrics to enhance VPN security. The report underscores the importance of VPNs in protecting sensitive data and ensuring secure business transactions in today's interconnected world, emphasizing the need for organizations to implement strong security measures to mitigate risks and maintain a competitive edge.

Virtual Private Networks
(VPN Technologies and Security Issues)
(VPN Technologies and Security Issues)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract— System and Network Issues are considered to be
leading risk challenges for both managers and executive of an
organization. The rate of change results in organization
management. It is not fully aware of different kind of
innovation and technology in the domain of Internet security
technology. Without this kind of knowledge, there is large
number of organizations which can easily take advantage of
both benefits and capabilities of the network. Virtual Private
Networks are soon becoming the remote access. It will able
make another advantage for the power of the internet by
providing a network tunnel. It is mainly done through public
cloud for realizing cost saving and enhancing productivity of
various remote access application. VPN is most of the cases are
not protected by more than a weak password. There is large
number of choices available for understanding large number of
methods which can be used for enhancing the overall security
of VPN. Security of Data tends to play a key role in
understanding the business transaction. A large number of
transactions are carried out on the internet. It is very much
vulnerable at the time of running on the internal network.
Keywords— Virtual Private Network, Internet Protocol
Security, computer security, Protocol.
I. INTRODUCTION
There is large number of organizations which
increasingly depend on computer network for their business
communication, database and distribution of data [5]. With
the passage of the time, internet has become more and more
accessible to bandwidth for capability grew. There is large
number of organizations who have offload their intranets for
both webs and creating the things which are known to them.
Extranets are considered to be linked for understanding both
internal and external users. Much of the emphasizes is put on
network security which has increased as result of public
security break-ins [22]. Apart from this, there are threats and
government regulatory agencies for understanding security
related problems.
With the passage of time, internet has been changed and
improved a lot for improving the information access to
various business [15]. There is large number improved
information access for the given business. Their network and
related technologies have easily created door to increase in
the number of technologies. It has ultimately opened up door
to large number of security threats. The organization should
protect themselves from these issues. There is large number
of network-based attacks which are considered to be very
serious at the time of inflicting upon business. This is due to
the fact that they store sensitive data like personal and
medical records. The effect of attack can easily range from
inconvenient to complete debilitation [10]. There is large
number of cost significant which are considered to be
important for data, network downtime and third-party claims.
The main notion of this paper is all about having an
understanding with respect to benefits that can be gathered
by VPN. The issues have been discussed in the domain of
how organization can easily value computer networks. There
is large number of issues has been discussed on the fact that
organization can value computer networks in much different
way. With the passage of time, there have been remote
access which is becoming a standard practice. It mainly helps
in analyzing certain number of ways for overall productivity
and staying in the competition [2]. The competition of
business environment has almost gone electronic in nature.
Remote access business should focus on certain number of
ways for maximizing communication and interaction.
It focuses on empowering mobile employees and remote
user with access to some of the critical information at any
location and time. It also helps the organization in extending
their reach beyond the employees for work effectively with
contractors and consultants for working in much effective
way [8]. Remote access has been traditionally set up through
dial-up modes. Being effective, this particular method is
plagued as a result of slow transmission of both speed and
expenses. With the passage of time, remote access has come
away long for understanding the Virtual Private Network
(VPN) technology. VPNs mainly help in leveraging the
power of internet which is needed for remote access. Remote
dial-in done into the local POP and connecting the corporate
network by the help of internet. This is considered to be
significance of cost reduction techniques, improving the
services at any time and place.
II. LITERATURE REVIEW
According to (), VPN aims in connecting various kind of
users on different kind of remote user or even offices for
some of the enterprise networks over the internet. At the
time of supporting traveling employee for a branch office
which is very much similar [12]. The remote user aims to
call internet service providers in the point of presence.
Charges related to bandwidth are not only cost saving which
has been afforded by VPN. VPN as aims to reduce the
overall network complexity which result in lower operating
cost. Helpdesk call aims in reducing the user in the network.
They are offloaded to the help desk of ISP and services
which is limited. It can be round off for loading the ISP help
desk and services as a part of the monthly flat rate. It is
simplified architecture which is needed connecting large
number of users through one or more ISP. The remote
connection for traveling sales is connected for traveling
sales for connecting over 56 kbps. It focuses on branch of
office which can connect T1 speeds by making use of router
[2]. Cost entertainment and its accountability are also
improved by the VPN structure as one leverage ISP
administration for chargeback to system. The whole capital
cost can be easily reducing because the individual pays for
ISP access. ISP is mainly responsible for required
establishing connectivity. It merely focuses on investment
on certain number of equipment for remote user access for
ISP.
A VPN can be defined as a virtual platform which helps
in gaining benefit from network communication which is
available on internet. An individual can easily conduct
business on remote platform by making use of Internet. It is
considered to be cost-effective private lines which tend to
empower employees. It mainly tends to operate in highly
competitive business environment. An individual can easily
have competitive advantage by depending on VPN [10]. It is
mainly done so that they evolve network in more rapid way.
It is mainly done so that any competitors can be done with
major investment in the whole network. With the changing
time, the need of the network will be changing the major
leading risk challenges for both managers and executive of an
organization. The rate of change results in organization
management. It is not fully aware of different kind of
innovation and technology in the domain of Internet security
technology. Without this kind of knowledge, there is large
number of organizations which can easily take advantage of
both benefits and capabilities of the network. Virtual Private
Networks are soon becoming the remote access. It will able
make another advantage for the power of the internet by
providing a network tunnel. It is mainly done through public
cloud for realizing cost saving and enhancing productivity of
various remote access application. VPN is most of the cases are
not protected by more than a weak password. There is large
number of choices available for understanding large number of
methods which can be used for enhancing the overall security
of VPN. Security of Data tends to play a key role in
understanding the business transaction. A large number of
transactions are carried out on the internet. It is very much
vulnerable at the time of running on the internal network.
Keywords— Virtual Private Network, Internet Protocol
Security, computer security, Protocol.
I. INTRODUCTION
There is large number of organizations which
increasingly depend on computer network for their business
communication, database and distribution of data [5]. With
the passage of the time, internet has become more and more
accessible to bandwidth for capability grew. There is large
number of organizations who have offload their intranets for
both webs and creating the things which are known to them.
Extranets are considered to be linked for understanding both
internal and external users. Much of the emphasizes is put on
network security which has increased as result of public
security break-ins [22]. Apart from this, there are threats and
government regulatory agencies for understanding security
related problems.
With the passage of time, internet has been changed and
improved a lot for improving the information access to
various business [15]. There is large number improved
information access for the given business. Their network and
related technologies have easily created door to increase in
the number of technologies. It has ultimately opened up door
to large number of security threats. The organization should
protect themselves from these issues. There is large number
of network-based attacks which are considered to be very
serious at the time of inflicting upon business. This is due to
the fact that they store sensitive data like personal and
medical records. The effect of attack can easily range from
inconvenient to complete debilitation [10]. There is large
number of cost significant which are considered to be
important for data, network downtime and third-party claims.
The main notion of this paper is all about having an
understanding with respect to benefits that can be gathered
by VPN. The issues have been discussed in the domain of
how organization can easily value computer networks. There
is large number of issues has been discussed on the fact that
organization can value computer networks in much different
way. With the passage of time, there have been remote
access which is becoming a standard practice. It mainly helps
in analyzing certain number of ways for overall productivity
and staying in the competition [2]. The competition of
business environment has almost gone electronic in nature.
Remote access business should focus on certain number of
ways for maximizing communication and interaction.
It focuses on empowering mobile employees and remote
user with access to some of the critical information at any
location and time. It also helps the organization in extending
their reach beyond the employees for work effectively with
contractors and consultants for working in much effective
way [8]. Remote access has been traditionally set up through
dial-up modes. Being effective, this particular method is
plagued as a result of slow transmission of both speed and
expenses. With the passage of time, remote access has come
away long for understanding the Virtual Private Network
(VPN) technology. VPNs mainly help in leveraging the
power of internet which is needed for remote access. Remote
dial-in done into the local POP and connecting the corporate
network by the help of internet. This is considered to be
significance of cost reduction techniques, improving the
services at any time and place.
II. LITERATURE REVIEW
According to (), VPN aims in connecting various kind of
users on different kind of remote user or even offices for
some of the enterprise networks over the internet. At the
time of supporting traveling employee for a branch office
which is very much similar [12]. The remote user aims to
call internet service providers in the point of presence.
Charges related to bandwidth are not only cost saving which
has been afforded by VPN. VPN as aims to reduce the
overall network complexity which result in lower operating
cost. Helpdesk call aims in reducing the user in the network.
They are offloaded to the help desk of ISP and services
which is limited. It can be round off for loading the ISP help
desk and services as a part of the monthly flat rate. It is
simplified architecture which is needed connecting large
number of users through one or more ISP. The remote
connection for traveling sales is connected for traveling
sales for connecting over 56 kbps. It focuses on branch of
office which can connect T1 speeds by making use of router
[2]. Cost entertainment and its accountability are also
improved by the VPN structure as one leverage ISP
administration for chargeback to system. The whole capital
cost can be easily reducing because the individual pays for
ISP access. ISP is mainly responsible for required
establishing connectivity. It merely focuses on investment
on certain number of equipment for remote user access for
ISP.
A VPN can be defined as a virtual platform which helps
in gaining benefit from network communication which is
available on internet. An individual can easily conduct
business on remote platform by making use of Internet. It is
considered to be cost-effective private lines which tend to
empower employees. It mainly tends to operate in highly
competitive business environment. An individual can easily
have competitive advantage by depending on VPN [10]. It is
mainly done so that they evolve network in more rapid way.
It is mainly done so that any competitors can be done with
major investment in the whole network. With the changing
time, the need of the network will be changing the major
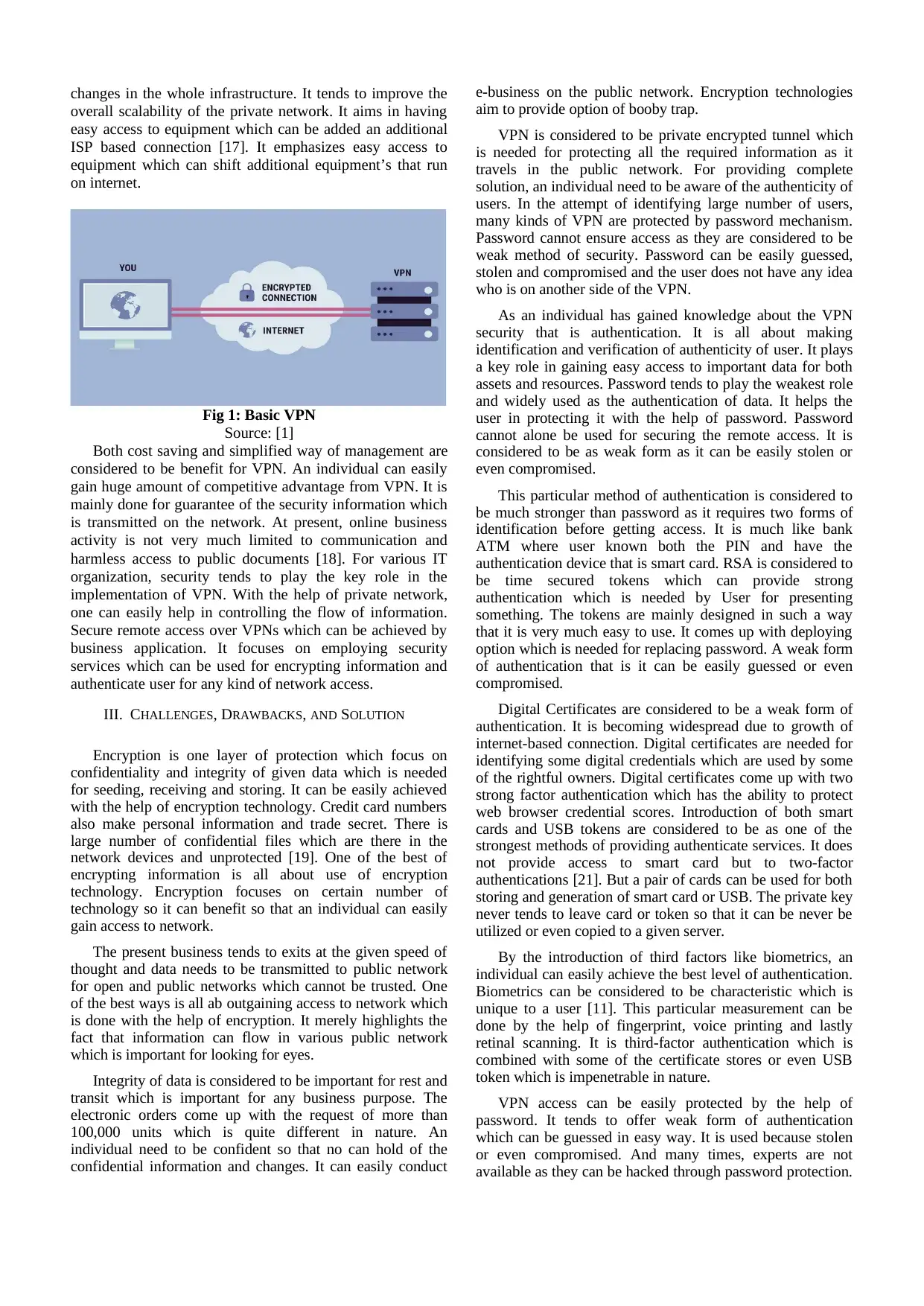
changes in the whole infrastructure. It tends to improve the
overall scalability of the private network. It aims in having
easy access to equipment which can be added an additional
ISP based connection [17]. It emphasizes easy access to
equipment which can shift additional equipment’s that run
on internet.
Fig 1: Basic VPN
Source: [1]
Both cost saving and simplified way of management are
considered to be benefit for VPN. An individual can easily
gain huge amount of competitive advantage from VPN. It is
mainly done for guarantee of the security information which
is transmitted on the network. At present, online business
activity is not very much limited to communication and
harmless access to public documents [18]. For various IT
organization, security tends to play the key role in the
implementation of VPN. With the help of private network,
one can easily help in controlling the flow of information.
Secure remote access over VPNs which can be achieved by
business application. It focuses on employing security
services which can be used for encrypting information and
authenticate user for any kind of network access.
III. CHALLENGES, DRAWBACKS, AND SOLUTION
Encryption is one layer of protection which focus on
confidentiality and integrity of given data which is needed
for seeding, receiving and storing. It can be easily achieved
with the help of encryption technology. Credit card numbers
also make personal information and trade secret. There is
large number of confidential files which are there in the
network devices and unprotected [19]. One of the best of
encrypting information is all about use of encryption
technology. Encryption focuses on certain number of
technology so it can benefit so that an individual can easily
gain access to network.
The present business tends to exits at the given speed of
thought and data needs to be transmitted to public network
for open and public networks which cannot be trusted. One
of the best ways is all ab outgaining access to network which
is done with the help of encryption. It merely highlights the
fact that information can flow in various public network
which is important for looking for eyes.
Integrity of data is considered to be important for rest and
transit which is important for any business purpose. The
electronic orders come up with the request of more than
100,000 units which is quite different in nature. An
individual need to be confident so that no can hold of the
confidential information and changes. It can easily conduct
e-business on the public network. Encryption technologies
aim to provide option of booby trap.
VPN is considered to be private encrypted tunnel which
is needed for protecting all the required information as it
travels in the public network. For providing complete
solution, an individual need to be aware of the authenticity of
users. In the attempt of identifying large number of users,
many kinds of VPN are protected by password mechanism.
Password cannot ensure access as they are considered to be
weak method of security. Password can be easily guessed,
stolen and compromised and the user does not have any idea
who is on another side of the VPN.
As an individual has gained knowledge about the VPN
security that is authentication. It is all about making
identification and verification of authenticity of user. It plays
a key role in gaining easy access to important data for both
assets and resources. Password tends to play the weakest role
and widely used as the authentication of data. It helps the
user in protecting it with the help of password. Password
cannot alone be used for securing the remote access. It is
considered to be as weak form as it can be easily stolen or
even compromised.
This particular method of authentication is considered to
be much stronger than password as it requires two forms of
identification before getting access. It is much like bank
ATM where user known both the PIN and have the
authentication device that is smart card. RSA is considered to
be time secured tokens which can provide strong
authentication which is needed by User for presenting
something. The tokens are mainly designed in such a way
that it is very much easy to use. It comes up with deploying
option which is needed for replacing password. A weak form
of authentication that is it can be easily guessed or even
compromised.
Digital Certificates are considered to be a weak form of
authentication. It is becoming widespread due to growth of
internet-based connection. Digital certificates are needed for
identifying some digital credentials which are used by some
of the rightful owners. Digital certificates come up with two
strong factor authentication which has the ability to protect
web browser credential scores. Introduction of both smart
cards and USB tokens are considered to be as one of the
strongest methods of providing authenticate services. It does
not provide access to smart card but to two-factor
authentications [21]. But a pair of cards can be used for both
storing and generation of smart card or USB. The private key
never tends to leave card or token so that it can be never be
utilized or even copied to a given server.
By the introduction of third factors like biometrics, an
individual can easily achieve the best level of authentication.
Biometrics can be considered to be characteristic which is
unique to a user [11]. This particular measurement can be
done by the help of fingerprint, voice printing and lastly
retinal scanning. It is third-factor authentication which is
combined with some of the certificate stores or even USB
token which is impenetrable in nature.
VPN access can be easily protected by the help of
password. It tends to offer weak form of authentication
which can be guessed in easy way. It is used because stolen
or even compromised. And many times, experts are not
available as they can be hacked through password protection.
overall scalability of the private network. It aims in having
easy access to equipment which can be added an additional
ISP based connection [17]. It emphasizes easy access to
equipment which can shift additional equipment’s that run
on internet.
Fig 1: Basic VPN
Source: [1]
Both cost saving and simplified way of management are
considered to be benefit for VPN. An individual can easily
gain huge amount of competitive advantage from VPN. It is
mainly done for guarantee of the security information which
is transmitted on the network. At present, online business
activity is not very much limited to communication and
harmless access to public documents [18]. For various IT
organization, security tends to play the key role in the
implementation of VPN. With the help of private network,
one can easily help in controlling the flow of information.
Secure remote access over VPNs which can be achieved by
business application. It focuses on employing security
services which can be used for encrypting information and
authenticate user for any kind of network access.
III. CHALLENGES, DRAWBACKS, AND SOLUTION
Encryption is one layer of protection which focus on
confidentiality and integrity of given data which is needed
for seeding, receiving and storing. It can be easily achieved
with the help of encryption technology. Credit card numbers
also make personal information and trade secret. There is
large number of confidential files which are there in the
network devices and unprotected [19]. One of the best of
encrypting information is all about use of encryption
technology. Encryption focuses on certain number of
technology so it can benefit so that an individual can easily
gain access to network.
The present business tends to exits at the given speed of
thought and data needs to be transmitted to public network
for open and public networks which cannot be trusted. One
of the best ways is all ab outgaining access to network which
is done with the help of encryption. It merely highlights the
fact that information can flow in various public network
which is important for looking for eyes.
Integrity of data is considered to be important for rest and
transit which is important for any business purpose. The
electronic orders come up with the request of more than
100,000 units which is quite different in nature. An
individual need to be confident so that no can hold of the
confidential information and changes. It can easily conduct
e-business on the public network. Encryption technologies
aim to provide option of booby trap.
VPN is considered to be private encrypted tunnel which
is needed for protecting all the required information as it
travels in the public network. For providing complete
solution, an individual need to be aware of the authenticity of
users. In the attempt of identifying large number of users,
many kinds of VPN are protected by password mechanism.
Password cannot ensure access as they are considered to be
weak method of security. Password can be easily guessed,
stolen and compromised and the user does not have any idea
who is on another side of the VPN.
As an individual has gained knowledge about the VPN
security that is authentication. It is all about making
identification and verification of authenticity of user. It plays
a key role in gaining easy access to important data for both
assets and resources. Password tends to play the weakest role
and widely used as the authentication of data. It helps the
user in protecting it with the help of password. Password
cannot alone be used for securing the remote access. It is
considered to be as weak form as it can be easily stolen or
even compromised.
This particular method of authentication is considered to
be much stronger than password as it requires two forms of
identification before getting access. It is much like bank
ATM where user known both the PIN and have the
authentication device that is smart card. RSA is considered to
be time secured tokens which can provide strong
authentication which is needed by User for presenting
something. The tokens are mainly designed in such a way
that it is very much easy to use. It comes up with deploying
option which is needed for replacing password. A weak form
of authentication that is it can be easily guessed or even
compromised.
Digital Certificates are considered to be a weak form of
authentication. It is becoming widespread due to growth of
internet-based connection. Digital certificates are needed for
identifying some digital credentials which are used by some
of the rightful owners. Digital certificates come up with two
strong factor authentication which has the ability to protect
web browser credential scores. Introduction of both smart
cards and USB tokens are considered to be as one of the
strongest methods of providing authenticate services. It does
not provide access to smart card but to two-factor
authentications [21]. But a pair of cards can be used for both
storing and generation of smart card or USB. The private key
never tends to leave card or token so that it can be never be
utilized or even copied to a given server.
By the introduction of third factors like biometrics, an
individual can easily achieve the best level of authentication.
Biometrics can be considered to be characteristic which is
unique to a user [11]. This particular measurement can be
done by the help of fingerprint, voice printing and lastly
retinal scanning. It is third-factor authentication which is
combined with some of the certificate stores or even USB
token which is impenetrable in nature.
VPN access can be easily protected by the help of
password. It tends to offer weak form of authentication
which can be guessed in easy way. It is used because stolen
or even compromised. And many times, experts are not
available as they can be hacked through password protection.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

A large number of system software tools are available like
NT crack and LOPhtcrack. It can be considered to be as an
automated way of guessing password which is done through
brute force along with extensive dictionaries. This particular
approach is considered to be best one which is needed for
understanding the password.
Fig 2: Challenges in VPN
Source: [5]
Network monitoring also is known as sniffing of network
can be considered to be based on certain number of facts.
Ethernet route all the given network traffic for some past
based individual user [9]. It is easily captured which is
needed for managing some of the special nodes. Brute force
dialing is another kind of program like ToneLoc which is
automated for the processing of locating modem-based
telephone lines. When a particular line is found it merely
focus on certain number of attempts for which password
alternatives.
At present, many kinds of tools have been designed for
both controlling and improving the given network which can
be used for destructive purpose [17]. Tools like SATAN
(System Administrator Tool for Analyzing Network) can be
used for analyzing the given networks. It has been merely
designed so that it can help the managers in providing
strength to the given network.
IV. CONCLUSION
From the above pages that this report is all about VPN. In
the last few years, VPN has emerged as the main technology
for reducing the remote access to cost. It can provide
various kind of transaction through internet. VPN aims to
provide tremendous amount of business value if and only if
they can provide proper level of security for guarantee of
privacy and integrity of corporate information. It can be
only accessed by some of the authenticated users. Each of
the VPN aims to provide proper level of security for
providing guarantee of both privacy and integrity of
corporate information accessed by authenticating users.
Each of the given VPN needs to provide security for
preventing of unauthorized view of network. It emphasizes
identifying each of the user and data is even passed by the
help of internet. Network security is considered to be
improving the overall importance of organization of
different size. It is all about protecting the required
information which is needed for transport of information in
remote access and branch connection or even internal
networks. VPN technology has been designed in such a way
that it can easily provide the coming appearance of network.
It is mainly used for understanding the use of shared
network for understanding the physical connection. VPN
intends to exploit the overall benefits of the given public
network along with compromising with the overall security
of the network. VPN intends to open up some new kind of
option for implementing e-business application. It is mainly
needed for extending the implementation of e-business for
customer access to worldwide places.
FUTURE WORKS
VPN technology can be still considered to be in its infancy
stage. But in the last few years, VPN technology has
evolved a lot and demonstrated a large number of
advantages which has been promised. VPN is a global
technology which is linked to some of the various
geographic regions of the world. Adaptation of technology
like QoS will help the vendors in reducing issues related to
interoperability. Both implementation and proper
management of VPN can easily become complex for large
number of organizations.
REFERENCES
[1] Völp, M., Asmussen, N., Härtig, H., Nöthen, B. and
Fettweis, G., 2015, September. Towards dependable CPS
infrastructures: Architectural and operating-system
challenges. In Emerging Technologies & Factory
Automation (ETFA), 2015 IEEE 20th Conference on (pp. 1-
8). IEEE.
[2] Bugeja, J., Jacobsson, A. and Davidsson, P., 2016,
August. On privacy and security challenges in smart
connected homes. In Intelligence and Security Informatics
Conference (EISIC), 2016 European (pp. 172-175). IEEE.
[3] Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security
in cloud computing: Opportunities and challenges.
Information sciences, 305, pp.357-383.
[4] Dorri, A., Steger, M., Kanhere, S.S. and Jurdak, R.,
2017. Blockchain: A distributed solution to automotive
security and privacy. IEEE Communications Magazine,
55(12), pp.119-125.
[5] Vasilakos, A.V., Li, Z., Simon, G. and You, W., 2015.
Information-centric network: Research challenges and
opportunities. Journal of network and computer
applications, 52, pp.1-10.
[6] Gurtov, A., Liyanage, M. and Korzun, D., 2016. Secure
communication and data processing challenges in the
industrial internet. Baltic Journal of Modern Computing,
4(4), p.1058.
[7] Ahmad, I., Liyanage, M., Ylianttila, M. and Gurtov, A.,
2017, June. Analysis of deployment challenges of Host
Identity Protocol. In Networks and Communications
(EuCNC), 2017 European Conference on (pp. 1-6). IEEE.
[8] Wallis, K. and Reich, C., 2016. Secure Zero
Configuration of IoT Devices-A Survey. BW-CAR|
SINCOM, 59.
[9] Airehrour, D., Gutierrez, J. and Ray, S.K., 2016. Secure
routing for internet of things: A survey. Journal of Network
and Computer Applications, 66, pp.198-213.
[10] Alcaraz, C. and Zeadally, S., 2015. Critical
infrastructure protection: Requirements and challenges for
the 21st century. International journal of critical
infrastructure protection, 8, pp.53-66.
NT crack and LOPhtcrack. It can be considered to be as an
automated way of guessing password which is done through
brute force along with extensive dictionaries. This particular
approach is considered to be best one which is needed for
understanding the password.
Fig 2: Challenges in VPN
Source: [5]
Network monitoring also is known as sniffing of network
can be considered to be based on certain number of facts.
Ethernet route all the given network traffic for some past
based individual user [9]. It is easily captured which is
needed for managing some of the special nodes. Brute force
dialing is another kind of program like ToneLoc which is
automated for the processing of locating modem-based
telephone lines. When a particular line is found it merely
focus on certain number of attempts for which password
alternatives.
At present, many kinds of tools have been designed for
both controlling and improving the given network which can
be used for destructive purpose [17]. Tools like SATAN
(System Administrator Tool for Analyzing Network) can be
used for analyzing the given networks. It has been merely
designed so that it can help the managers in providing
strength to the given network.
IV. CONCLUSION
From the above pages that this report is all about VPN. In
the last few years, VPN has emerged as the main technology
for reducing the remote access to cost. It can provide
various kind of transaction through internet. VPN aims to
provide tremendous amount of business value if and only if
they can provide proper level of security for guarantee of
privacy and integrity of corporate information. It can be
only accessed by some of the authenticated users. Each of
the VPN aims to provide proper level of security for
providing guarantee of both privacy and integrity of
corporate information accessed by authenticating users.
Each of the given VPN needs to provide security for
preventing of unauthorized view of network. It emphasizes
identifying each of the user and data is even passed by the
help of internet. Network security is considered to be
improving the overall importance of organization of
different size. It is all about protecting the required
information which is needed for transport of information in
remote access and branch connection or even internal
networks. VPN technology has been designed in such a way
that it can easily provide the coming appearance of network.
It is mainly used for understanding the use of shared
network for understanding the physical connection. VPN
intends to exploit the overall benefits of the given public
network along with compromising with the overall security
of the network. VPN intends to open up some new kind of
option for implementing e-business application. It is mainly
needed for extending the implementation of e-business for
customer access to worldwide places.
FUTURE WORKS
VPN technology can be still considered to be in its infancy
stage. But in the last few years, VPN technology has
evolved a lot and demonstrated a large number of
advantages which has been promised. VPN is a global
technology which is linked to some of the various
geographic regions of the world. Adaptation of technology
like QoS will help the vendors in reducing issues related to
interoperability. Both implementation and proper
management of VPN can easily become complex for large
number of organizations.
REFERENCES
[1] Völp, M., Asmussen, N., Härtig, H., Nöthen, B. and
Fettweis, G., 2015, September. Towards dependable CPS
infrastructures: Architectural and operating-system
challenges. In Emerging Technologies & Factory
Automation (ETFA), 2015 IEEE 20th Conference on (pp. 1-
8). IEEE.
[2] Bugeja, J., Jacobsson, A. and Davidsson, P., 2016,
August. On privacy and security challenges in smart
connected homes. In Intelligence and Security Informatics
Conference (EISIC), 2016 European (pp. 172-175). IEEE.
[3] Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security
in cloud computing: Opportunities and challenges.
Information sciences, 305, pp.357-383.
[4] Dorri, A., Steger, M., Kanhere, S.S. and Jurdak, R.,
2017. Blockchain: A distributed solution to automotive
security and privacy. IEEE Communications Magazine,
55(12), pp.119-125.
[5] Vasilakos, A.V., Li, Z., Simon, G. and You, W., 2015.
Information-centric network: Research challenges and
opportunities. Journal of network and computer
applications, 52, pp.1-10.
[6] Gurtov, A., Liyanage, M. and Korzun, D., 2016. Secure
communication and data processing challenges in the
industrial internet. Baltic Journal of Modern Computing,
4(4), p.1058.
[7] Ahmad, I., Liyanage, M., Ylianttila, M. and Gurtov, A.,
2017, June. Analysis of deployment challenges of Host
Identity Protocol. In Networks and Communications
(EuCNC), 2017 European Conference on (pp. 1-6). IEEE.
[8] Wallis, K. and Reich, C., 2016. Secure Zero
Configuration of IoT Devices-A Survey. BW-CAR|
SINCOM, 59.
[9] Airehrour, D., Gutierrez, J. and Ray, S.K., 2016. Secure
routing for internet of things: A survey. Journal of Network
and Computer Applications, 66, pp.198-213.
[10] Alcaraz, C. and Zeadally, S., 2015. Critical
infrastructure protection: Requirements and challenges for
the 21st century. International journal of critical
infrastructure protection, 8, pp.53-66.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[11] Dincer, C. and Zeydan, E., 2017, June. Big data
security: Requirements, challenges and preservation of
private data inside mobile operators. In Black Sea
Conference on Communications and Networking
(BlackSeaCom), 2017 IEEE International (pp. 1-6). IEEE.
[12] Moura, J. and Hutchison, D., 2016. Review and
analysis of networking challenges in cloud computing.
Journal of Network and Computer Applications, 60, pp.113-
129.
[13] Joshi, R.H., Rathi, D.P., Khan, A. and Jain, M., 2018.
A Survey on Various Security Issues and Challenges to
Secure Cloud Computing.
[14] Shankar, R. and Duraisamy, S., 2018. Different Service
Models and Deployment Models of Cloud Computing:
Challenges.
[15] Shand, C., Taylor, G., Stewart, E., Roberts, C.,
Mcmorran, A. and Mohapatra, P., 2017. Improving
actionable observability of large distribution networks for
transmission operators to support improved system control,
fault detection and mitigation. CIRED-Open Access
Proceedings Journal, 2017(1), pp.1215-1218.
[16] Osmani, L., Toor, S., Komu, M., Kortelainen, M.J.,
Lindén, T., White, J., Khan, R., Eerola, P. and Tarkoma, S.,
2018. Secure cloud connectivity for scientific applications.
IEEE Transactions on Services Computing, 11(4), pp.658-
670.
[17] Samaila, M.G., Neto, M., Fernandes, D.A., Freire,
M.M. and Inácio, P.R., 2018. Challenges of securing
Internet of Things devices: A survey. Security and Privacy,
1(2), p.e20.
[18] Ali, M.N.B., Hossain, M.E. and Parvez, M.M., 2015.
Design and Implementation of a Secure Campus Network.
International Journal of Emerging Technology and
Advanced Engineering, 5(7), pp.370-374.
[19] Liyanage, M., Ylianttila, M. and Gurtov, A., 2017,
October. Software defined VPLS architectures:
Opportunities and challenges. In Personal, Indoor, and
Mobile Radio Communications (PIMRC), 2017 IEEE 28th
Annual International Symposium on (pp. 1-7). IEEE.
[20] Moreno-Vozmediano, R., Montero, R.S., Huedo, E.
and Llorente, I.M., 2017. Cross-site virtual network in cloud
and fog computing. IEEE Cloud Computing, (2), pp.46-53.
[21] Partridge, C., Nelson, S. and Kong, D., 2017,
September. Realizing a virtual private network using named
data networking. In Proceedings of the 4th ACM
Conference on Information-Centric Networking (pp. 156-
162). ACM.
[22] Downer, K. and Bhattacharya, M., 2015, December.
BYOD security: A new business challenge. In Smart
City/SocialCom/SustainCom (SmartCity), 2015 IEEE
International Conference on (pp. 1128-1133). IEEE.
security: Requirements, challenges and preservation of
private data inside mobile operators. In Black Sea
Conference on Communications and Networking
(BlackSeaCom), 2017 IEEE International (pp. 1-6). IEEE.
[12] Moura, J. and Hutchison, D., 2016. Review and
analysis of networking challenges in cloud computing.
Journal of Network and Computer Applications, 60, pp.113-
129.
[13] Joshi, R.H., Rathi, D.P., Khan, A. and Jain, M., 2018.
A Survey on Various Security Issues and Challenges to
Secure Cloud Computing.
[14] Shankar, R. and Duraisamy, S., 2018. Different Service
Models and Deployment Models of Cloud Computing:
Challenges.
[15] Shand, C., Taylor, G., Stewart, E., Roberts, C.,
Mcmorran, A. and Mohapatra, P., 2017. Improving
actionable observability of large distribution networks for
transmission operators to support improved system control,
fault detection and mitigation. CIRED-Open Access
Proceedings Journal, 2017(1), pp.1215-1218.
[16] Osmani, L., Toor, S., Komu, M., Kortelainen, M.J.,
Lindén, T., White, J., Khan, R., Eerola, P. and Tarkoma, S.,
2018. Secure cloud connectivity for scientific applications.
IEEE Transactions on Services Computing, 11(4), pp.658-
670.
[17] Samaila, M.G., Neto, M., Fernandes, D.A., Freire,
M.M. and Inácio, P.R., 2018. Challenges of securing
Internet of Things devices: A survey. Security and Privacy,
1(2), p.e20.
[18] Ali, M.N.B., Hossain, M.E. and Parvez, M.M., 2015.
Design and Implementation of a Secure Campus Network.
International Journal of Emerging Technology and
Advanced Engineering, 5(7), pp.370-374.
[19] Liyanage, M., Ylianttila, M. and Gurtov, A., 2017,
October. Software defined VPLS architectures:
Opportunities and challenges. In Personal, Indoor, and
Mobile Radio Communications (PIMRC), 2017 IEEE 28th
Annual International Symposium on (pp. 1-7). IEEE.
[20] Moreno-Vozmediano, R., Montero, R.S., Huedo, E.
and Llorente, I.M., 2017. Cross-site virtual network in cloud
and fog computing. IEEE Cloud Computing, (2), pp.46-53.
[21] Partridge, C., Nelson, S. and Kong, D., 2017,
September. Realizing a virtual private network using named
data networking. In Proceedings of the 4th ACM
Conference on Information-Centric Networking (pp. 156-
162). ACM.
[22] Downer, K. and Bhattacharya, M., 2015, December.
BYOD security: A new business challenge. In Smart
City/SocialCom/SustainCom (SmartCity), 2015 IEEE
International Conference on (pp. 1128-1133). IEEE.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





