IEEE Transactions on VPN Security Insufficiency: A Detailed Analysis
VerifiedAdded on 2020/03/04
|8
|3117
|62
Report
AI Summary
This report delves into the insufficiencies of Virtual Private Networks (VPNs) in providing robust internet and information security. It begins with an overview of VPNs, their history, and their purpose, which is to create a secure, encrypted connection for data sharing across public networks. The study examines the security protocols, including IP Sec, L2TP, and others, and evaluates their strengths and weaknesses. A significant portion of the report focuses on the literature review, highlighting vulnerabilities such as IPv6 leakage, DNS hijacking, and insecure SSL certificates. The report also presents user satisfaction data from a review of several VPN providers. The report covers the working mechanisms of VPNs, including tunneling and encryption, and concludes by emphasizing the importance of reviewing VPN services and understanding their limitations. This report underscores the need to critically assess VPN security and the potential risks associated with their use, offering insights into how these protocols can be improved and alternative solutions.

IEEE TRANSACTIONS ON VPN SECURITY INSUFFICIENCY
VPN Security insufficiency
Abstract— Virtual Private Networks have of late been trusted to provide the best internet security.
Apparently, VPNs might still not keep you in guarantee of security. Cases such as IPv6 leakage are
some of the vulnerabilities that can expose user information to prying eyes. Passive monitoring and
DNS hijacking are some methods which have been used to attack and collect unencrypted information
or redirecting a user on internet to a fake popular site and viewed by the undesignated user without
much difficulty. This is sad for all the users who adopt VPNs plainly for improving their internet
security. Much that the VPNs do is to obfuscate user’s internet traffic. It is therefore important to review
the VPN services and the choice of whether to use them or not.
—————————— ——————————
INTRODUCTION
History and background of the topic
A virtual Private Network (VPN) is a private
network that spans a public network allowing
users to share data across the shared network just
like they are connected to the private network.
This is accomplished by creation of a secure and
encrypted connection which behaves like a tunnel
between the connected computer and the server.
The apparent tunnel is controlled by the Virtual
Private Network service. The VPN will therefore
allow users to access an intranet even when they
are located outside the office.it therefore turns out
to be possible to connect securely to
geographically disconnected offices of a given
organization.
VPNs transmit data by tunneling which
encapsulates with a header, every packet before it
is transmitted. The header will provide routing
information to enable the data packet transverse a
shared network or a public network. After the data
packet reaches the destination, it is decapsulated
and taken to its final destination. The only thing
that is considered is the power to support the
tunneling protocol used for both the end points.
The tunneling protocols are operated at the Data
Link Layer of the Open System Interconnection or
the network later of the Transmission Control
Protocol (TCP/IP) model.
They are mainly popular for securing sensitive
data when connecting remote data centers. This is
because after generation of P2P connections, a
user may be able to illegally acquire access to data
but be unable to access it on account of
encryption. The same has made virtual private
networks more common even to individuals in
pursuit of confidentiality and hope that data sent is
VPN Security insufficiency
Abstract— Virtual Private Networks have of late been trusted to provide the best internet security.
Apparently, VPNs might still not keep you in guarantee of security. Cases such as IPv6 leakage are
some of the vulnerabilities that can expose user information to prying eyes. Passive monitoring and
DNS hijacking are some methods which have been used to attack and collect unencrypted information
or redirecting a user on internet to a fake popular site and viewed by the undesignated user without
much difficulty. This is sad for all the users who adopt VPNs plainly for improving their internet
security. Much that the VPNs do is to obfuscate user’s internet traffic. It is therefore important to review
the VPN services and the choice of whether to use them or not.
—————————— ——————————
INTRODUCTION
History and background of the topic
A virtual Private Network (VPN) is a private
network that spans a public network allowing
users to share data across the shared network just
like they are connected to the private network.
This is accomplished by creation of a secure and
encrypted connection which behaves like a tunnel
between the connected computer and the server.
The apparent tunnel is controlled by the Virtual
Private Network service. The VPN will therefore
allow users to access an intranet even when they
are located outside the office.it therefore turns out
to be possible to connect securely to
geographically disconnected offices of a given
organization.
VPNs transmit data by tunneling which
encapsulates with a header, every packet before it
is transmitted. The header will provide routing
information to enable the data packet transverse a
shared network or a public network. After the data
packet reaches the destination, it is decapsulated
and taken to its final destination. The only thing
that is considered is the power to support the
tunneling protocol used for both the end points.
The tunneling protocols are operated at the Data
Link Layer of the Open System Interconnection or
the network later of the Transmission Control
Protocol (TCP/IP) model.
They are mainly popular for securing sensitive
data when connecting remote data centers. This is
because after generation of P2P connections, a
user may be able to illegally acquire access to data
but be unable to access it on account of
encryption. The same has made virtual private
networks more common even to individuals in
pursuit of confidentiality and hope that data sent is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2 IEEE TRANSACTIONS ON XXXXXXXXXXXXXXXXXXXX, VOL. #, NO. #, MMMMMMMM 1996
only accessed by the destined receiver.
Purpose of the study
The purpose of the study was to examine the
importance of VPNs in providing internet and
information security. As the demand for security
in many organizations increase, it is important to
review the internet security provided by virtual
private networks and their sufficiency in their use.
Most users adopt VPNs at a desperate level of
need for the security of information they
encapsulate using the VPNs. It is therefore needful
that we examine the sufficiency of VPNs in
providing the designated services.
Scope of the study
The study focuses on security protocols developed
as Virtual Private Networks and the levels of
security features they offer. Their most and best
instances of use. Their weaknesses and hitches
expected upon using them. Their most common
leakages and vulnerabilities.
Our study also focuses on the creation of VPNs
and the needs for a local machine that need to be
met in order for it to support virtual private
network, the security issues related to our
discussed security protocols and how they can be
made better and possible alternatives to them. The
study also evaluates each security protocol and
reviews its best instances of use and best
recommendations on each based on their
vulnerabilities. Some of the discussed security
protocols discussed include Internet Protocol
Security (IP Sec), Layer 2 Tunneling protocol
(L2TP) and P2P tunneling protocol.
Literature review
The register records ninety percent of the Virtual
Private Networks as hopelessly insecure. After a
large scale research done by High-Tech Bridge on
most live and publicly accessible SSL Virtual
Private Network servers, a lot of problems were
found to be associated with them. Three quarter of
the tested SSL VPNs were found to be still in the
use of obsolete SSLv3 protocol which was come
up with in 1996. Another bunch were found to
have SSLv2 which is even older than the SSLv3.
This increases the vulnerability levels of the SSLs
and security provided by them is therefore
compromised.
The same tested VPNs were found to be using
untrusted SSL certificates and this creates a hole
for man in the middle attacks. Lack of the SSL
certificate makes it possible for a hacker to stand
in the middle and set up a counterfeit server to be
used for impersonation and then they can be able
to harvest data sent over the Virtual Private
Network. According to High Tech Bridge, most
users have a tendency of using corporates of
default preinstalled certificates from vendors
which is the main reason why untrusted
certificates have found way easily.
Another three quarter was found to have insecure
SHA-1 signatures and using old MD5 technology.
As technology keeps growing, many browsers
have plans underway to stop accepting SHA-1
signed certificates while some have already
stopped. This is because old technology is with
only accessed by the destined receiver.
Purpose of the study
The purpose of the study was to examine the
importance of VPNs in providing internet and
information security. As the demand for security
in many organizations increase, it is important to
review the internet security provided by virtual
private networks and their sufficiency in their use.
Most users adopt VPNs at a desperate level of
need for the security of information they
encapsulate using the VPNs. It is therefore needful
that we examine the sufficiency of VPNs in
providing the designated services.
Scope of the study
The study focuses on security protocols developed
as Virtual Private Networks and the levels of
security features they offer. Their most and best
instances of use. Their weaknesses and hitches
expected upon using them. Their most common
leakages and vulnerabilities.
Our study also focuses on the creation of VPNs
and the needs for a local machine that need to be
met in order for it to support virtual private
network, the security issues related to our
discussed security protocols and how they can be
made better and possible alternatives to them. The
study also evaluates each security protocol and
reviews its best instances of use and best
recommendations on each based on their
vulnerabilities. Some of the discussed security
protocols discussed include Internet Protocol
Security (IP Sec), Layer 2 Tunneling protocol
(L2TP) and P2P tunneling protocol.
Literature review
The register records ninety percent of the Virtual
Private Networks as hopelessly insecure. After a
large scale research done by High-Tech Bridge on
most live and publicly accessible SSL Virtual
Private Network servers, a lot of problems were
found to be associated with them. Three quarter of
the tested SSL VPNs were found to be still in the
use of obsolete SSLv3 protocol which was come
up with in 1996. Another bunch were found to
have SSLv2 which is even older than the SSLv3.
This increases the vulnerability levels of the SSLs
and security provided by them is therefore
compromised.
The same tested VPNs were found to be using
untrusted SSL certificates and this creates a hole
for man in the middle attacks. Lack of the SSL
certificate makes it possible for a hacker to stand
in the middle and set up a counterfeit server to be
used for impersonation and then they can be able
to harvest data sent over the Virtual Private
Network. According to High Tech Bridge, most
users have a tendency of using corporates of
default preinstalled certificates from vendors
which is the main reason why untrusted
certificates have found way easily.
Another three quarter was found to have insecure
SHA-1 signatures and using old MD5 technology.
As technology keeps growing, many browsers
have plans underway to stop accepting SHA-1
signed certificates while some have already
stopped. This is because old technology is with
AUTHOR: TITLE
time getting weaker and not capable of
withstanding potential attacks. When this SSL
certificates are signed using these old
technologies, it is evident that as transition occurs
in our browsers, most Virtual Private Networks
will remain unsigned and thus hackers will have a
very easy way getting through.
Forty percent of the examined Virtual Private
Network servers were found to be using the
insecure 1024 bit keys for RSA certificates. RSA
key lengths should be more than 2048 since they
are responsible for authentication and encryption
key exchange. The less the key size, the easier it
becomes for a hacker to do code breaking and
crypto analysis which will definitely make our
Virtual Private Network insecure.
A tenth of the SSL Virtual Private Network servers
were also found to rely on Open SSL such as
Fortinet which are vulnerable to Heartbleed. After
the discovery of Heartbleed vulnerability, all
products using open SSL were found to be
creating a straightforward way for third parties
whose intention may be to extract sensitive
information such as encryption keys and more
since the systems get unmatched.
Another study by Vasile C. Perta, Marco V.
Barbera and Hammed Hadadi of Queen Mary
University saw most vendors’ privacy and security
promises as fake and putting users at risk.
Majority of Virtual Private Networks were found
to suffer from IPv6 traffic leakage on mildly
adversarial environments. Their research revealed
that most Virtual Private Network tunneling
technologies rely on old technologies like the
PPTP with MS-CHAPv2 which can be easily
broken into using methods such as brute-force
attacks. Many Virtual Private Networks were also
found to leak data exposing significant amounts of
user information which can be easy to access by
the hackers contrary to vendor claims.
It was also evident that all the DNS configurations
most Virtual Private Networks use are easily
overcome by DNS hijacking attackers.
Users’satisfaction
Although many users have heard the need for
VPNs, a review shows that only few manage to
get their required VPN service. The table below
represents our review
VPN vendor Users
review
ed
Users
satisfied
Users
not sure
Express VPN 13 4 3
HotSpot Shield 8 3 1
Pure VPN 6 4 1
Safer VPN 12 7 4
The review was conducted on the four VPNs and
the results show that only few users get satisfied
on a given VPN they choose.
Working of a VPN
A Virtual Private Network is similar to a home or
work private network. It is supposed to work in a
way that nobody outside the network can share or
time getting weaker and not capable of
withstanding potential attacks. When this SSL
certificates are signed using these old
technologies, it is evident that as transition occurs
in our browsers, most Virtual Private Networks
will remain unsigned and thus hackers will have a
very easy way getting through.
Forty percent of the examined Virtual Private
Network servers were found to be using the
insecure 1024 bit keys for RSA certificates. RSA
key lengths should be more than 2048 since they
are responsible for authentication and encryption
key exchange. The less the key size, the easier it
becomes for a hacker to do code breaking and
crypto analysis which will definitely make our
Virtual Private Network insecure.
A tenth of the SSL Virtual Private Network servers
were also found to rely on Open SSL such as
Fortinet which are vulnerable to Heartbleed. After
the discovery of Heartbleed vulnerability, all
products using open SSL were found to be
creating a straightforward way for third parties
whose intention may be to extract sensitive
information such as encryption keys and more
since the systems get unmatched.
Another study by Vasile C. Perta, Marco V.
Barbera and Hammed Hadadi of Queen Mary
University saw most vendors’ privacy and security
promises as fake and putting users at risk.
Majority of Virtual Private Networks were found
to suffer from IPv6 traffic leakage on mildly
adversarial environments. Their research revealed
that most Virtual Private Network tunneling
technologies rely on old technologies like the
PPTP with MS-CHAPv2 which can be easily
broken into using methods such as brute-force
attacks. Many Virtual Private Networks were also
found to leak data exposing significant amounts of
user information which can be easy to access by
the hackers contrary to vendor claims.
It was also evident that all the DNS configurations
most Virtual Private Networks use are easily
overcome by DNS hijacking attackers.
Users’satisfaction
Although many users have heard the need for
VPNs, a review shows that only few manage to
get their required VPN service. The table below
represents our review
VPN vendor Users
review
ed
Users
satisfied
Users
not sure
Express VPN 13 4 3
HotSpot Shield 8 3 1
Pure VPN 6 4 1
Safer VPN 12 7 4
The review was conducted on the four VPNs and
the results show that only few users get satisfied
on a given VPN they choose.
Working of a VPN
A Virtual Private Network is similar to a home or
work private network. It is supposed to work in a
way that nobody outside the network can share or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4 IEEE TRANSACTIONS ON XXXXXXXXXXXXXXXXXXXX, VOL. #, NO. #, MMMMMMMM 1996
read data from inside. The difference between a
Virtual Private Network and a home or business
network is that in a home network, you don’t
necessarily need the internet to access files from
another machine in the network or share a printer
like you will do on a VPN. The security of a home
network is guaranteed since if none of the devices
is connected to the internet, then no hacker can
gain access to any of the connected devices. For a
Virtual Private Network, you need the internet to
access any file on device connected to.it.
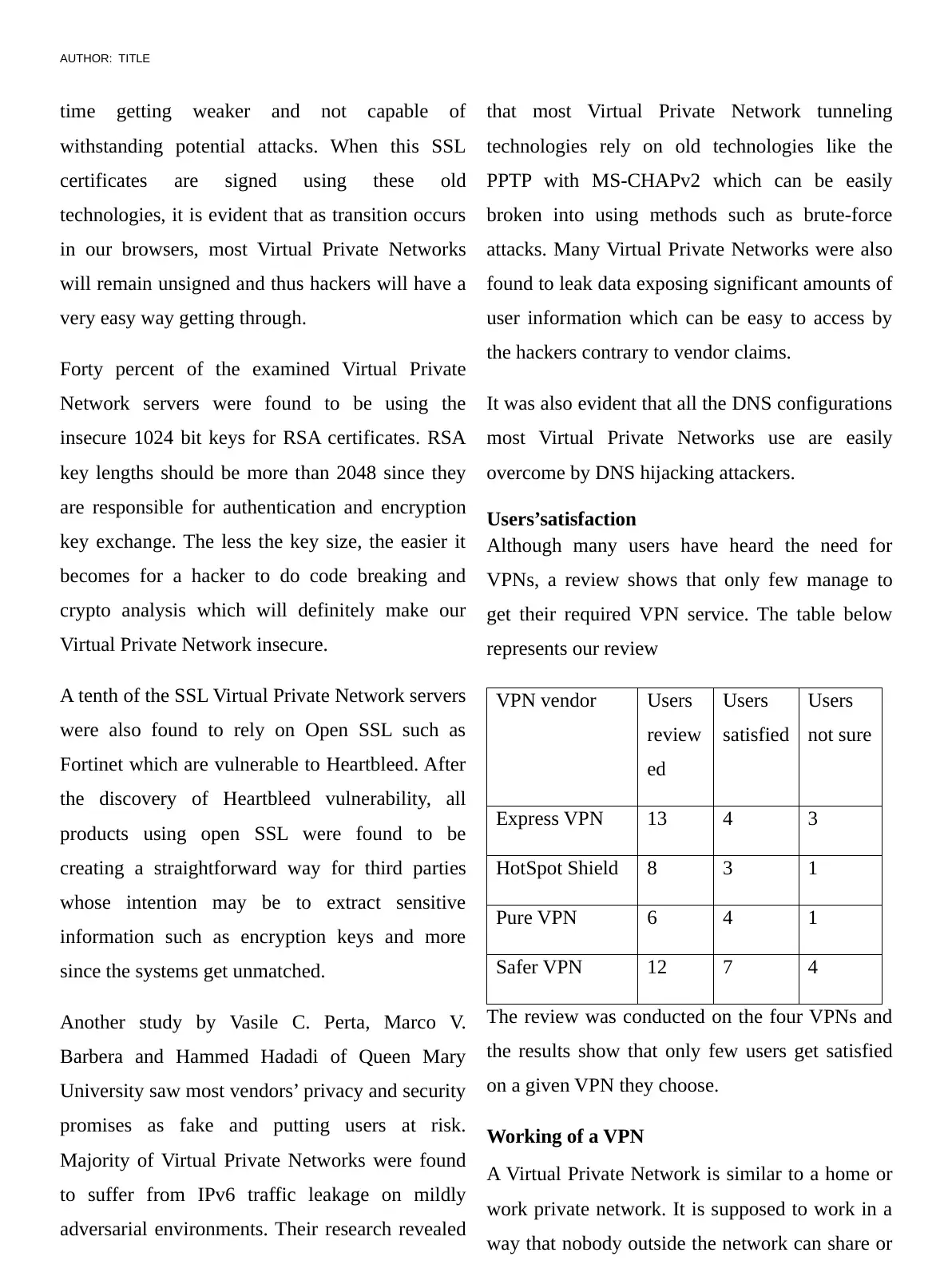
Connecting
For a successful connect to a Virtual Private
Network, we need the network server and the
client to have a dedicated software. The VPN
provider (Acting as server) has a different
software from the computer in need of the Virtual
Private Network (acting as the client). The Virtual
Private Network will have several layers of
security to be used during authentication. The
Virtual Private Network provider will have a
remote access server. The client machine connects
to the server while connected to the Virtual Private
Network. The server will require that the client
machine provides valid credentials using any of
the authentication methods it recognizes.
The client machine will therefore use the client
dedicated software to establish a connection and
maintain it to the Virtual Private Network. It is the
client dedicated software that establishes and sets
up the tunneled connection with the remote access
server and manages the encryption that maintains
the connection.
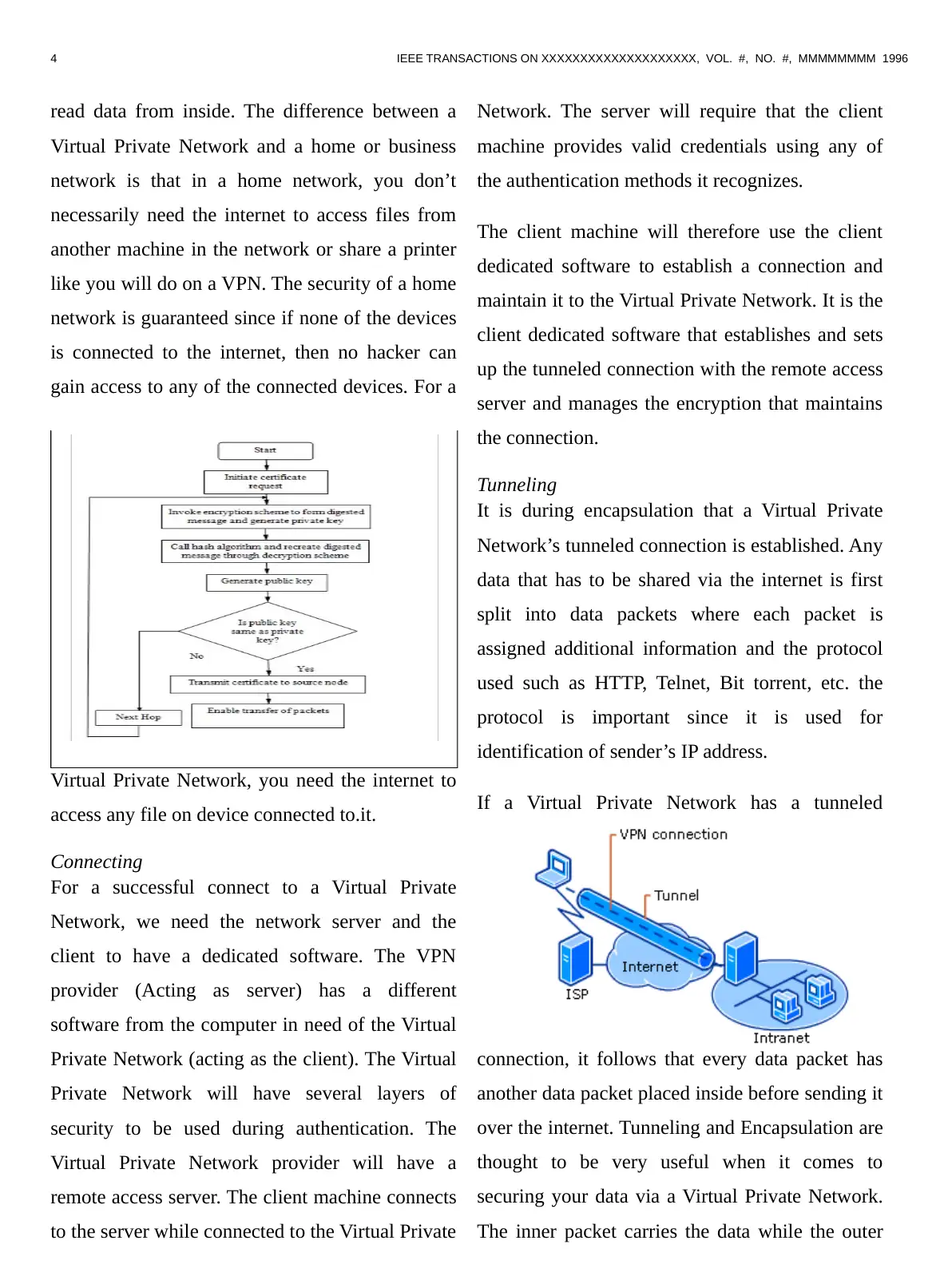
Tunneling
It is during encapsulation that a Virtual Private
Network’s tunneled connection is established. Any
data that has to be shared via the internet is first
split into data packets where each packet is
assigned additional information and the protocol
used such as HTTP, Telnet, Bit torrent, etc. the
protocol is important since it is used for
identification of sender’s IP address.
If a Virtual Private Network has a tunneled
connection, it follows that every data packet has
another data packet placed inside before sending it
over the internet. Tunneling and Encapsulation are
thought to be very useful when it comes to
securing your data via a Virtual Private Network.
The inner packet carries the data while the outer
read data from inside. The difference between a
Virtual Private Network and a home or business
network is that in a home network, you don’t
necessarily need the internet to access files from
another machine in the network or share a printer
like you will do on a VPN. The security of a home
network is guaranteed since if none of the devices
is connected to the internet, then no hacker can
gain access to any of the connected devices. For a
Virtual Private Network, you need the internet to
access any file on device connected to.it.
Connecting
For a successful connect to a Virtual Private
Network, we need the network server and the
client to have a dedicated software. The VPN
provider (Acting as server) has a different
software from the computer in need of the Virtual
Private Network (acting as the client). The Virtual
Private Network will have several layers of
security to be used during authentication. The
Virtual Private Network provider will have a
remote access server. The client machine connects
to the server while connected to the Virtual Private
Network. The server will require that the client
machine provides valid credentials using any of
the authentication methods it recognizes.
The client machine will therefore use the client
dedicated software to establish a connection and
maintain it to the Virtual Private Network. It is the
client dedicated software that establishes and sets
up the tunneled connection with the remote access
server and manages the encryption that maintains
the connection.
Tunneling
It is during encapsulation that a Virtual Private
Network’s tunneled connection is established. Any
data that has to be shared via the internet is first
split into data packets where each packet is
assigned additional information and the protocol
used such as HTTP, Telnet, Bit torrent, etc. the
protocol is important since it is used for
identification of sender’s IP address.
If a Virtual Private Network has a tunneled
connection, it follows that every data packet has
another data packet placed inside before sending it
over the internet. Tunneling and Encapsulation are
thought to be very useful when it comes to
securing your data via a Virtual Private Network.
The inner packet carries the data while the outer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AUTHOR: TITLE
packet is the one responsible for keeping the data
safe from public view.
Tunnel end points need to be authenticated first
before establishing VPN Network tunnels.
Passwords and biometrics among other other
methods may be used when the remote access
Virtual Private Network is user created. Network
to network tunnels use passwords and digital
certificates. A key which needs permanent storing
is permanently stored first so that a tunnel can
establish automatically without the need for an
administrator to intervene.
Encryption
Data sent over a Virtual Private Network is not
sufficiently secure just by tunneling. It is then that
data encryption appears important. The data is
normally encoded in a way that only the Virtual
Private Network client and the Virtual Private
Network server will read. They are both assumed
to be connected securely at this stage. The most
common methods of security protocols used by
the Virtual Private Networks to encrypt data are IP
Sec, Open VPN and Layer 2 Tunneling protocol
(L2TP). Point to point tunneling protocol and
secure shell are other security protocols in use
thought they are not as common as IP Sec and
Open VPN, which is one reason why most VPNs
turn insufficient. The later methods are better
protocols than open VPN.
The security protocols work by first encrypting
each data packet with a key which is known and
shared only by the Virtual Private Network’s
server and the Virtual Private Network’s client.
This ensures no third party can access the
encapsulated data and if they do, the will not be
able to decapsulate the data and therefore it will
not be usable.
They also use a sub-protocol called Encapsulation
Header which is used to hide certain packet
information such as sender’s identity during
transmission. The data thus stands private since
any hacker who manages to gain access will not
be able to know whether the source of the data
packets is their intended source. It will also be
impossible to get other data packets that were
hidden hence the data acquired will be incomplete
and probably not usable.
Mobile VPNs
When the endpoint of a Virtual Private Network is
not fitted to an Internet Protocol address or WAP,
Mobile Virtual Private Networks appear to be the
best. They are mostly used for safety by police
officers where they may be given access to
applications that control mission while travelling
between different subnets of a mobile network.
Mobile Virtual Private Networks can be best when
there is need to roam across wireless networks in
and out of wireless coverage areas without
necessarily losing application sessions or dropping
the secure Virtual Private Network connection.
When using a conventional Virtual Private
Network, the network tunnel is normally disrupted
causing application disconnects, timeouts, fails or
even crashing of the computer in use.
packet is the one responsible for keeping the data
safe from public view.
Tunnel end points need to be authenticated first
before establishing VPN Network tunnels.
Passwords and biometrics among other other
methods may be used when the remote access
Virtual Private Network is user created. Network
to network tunnels use passwords and digital
certificates. A key which needs permanent storing
is permanently stored first so that a tunnel can
establish automatically without the need for an
administrator to intervene.
Encryption
Data sent over a Virtual Private Network is not
sufficiently secure just by tunneling. It is then that
data encryption appears important. The data is
normally encoded in a way that only the Virtual
Private Network client and the Virtual Private
Network server will read. They are both assumed
to be connected securely at this stage. The most
common methods of security protocols used by
the Virtual Private Networks to encrypt data are IP
Sec, Open VPN and Layer 2 Tunneling protocol
(L2TP). Point to point tunneling protocol and
secure shell are other security protocols in use
thought they are not as common as IP Sec and
Open VPN, which is one reason why most VPNs
turn insufficient. The later methods are better
protocols than open VPN.
The security protocols work by first encrypting
each data packet with a key which is known and
shared only by the Virtual Private Network’s
server and the Virtual Private Network’s client.
This ensures no third party can access the
encapsulated data and if they do, the will not be
able to decapsulate the data and therefore it will
not be usable.
They also use a sub-protocol called Encapsulation
Header which is used to hide certain packet
information such as sender’s identity during
transmission. The data thus stands private since
any hacker who manages to gain access will not
be able to know whether the source of the data
packets is their intended source. It will also be
impossible to get other data packets that were
hidden hence the data acquired will be incomplete
and probably not usable.
Mobile VPNs
When the endpoint of a Virtual Private Network is
not fitted to an Internet Protocol address or WAP,
Mobile Virtual Private Networks appear to be the
best. They are mostly used for safety by police
officers where they may be given access to
applications that control mission while travelling
between different subnets of a mobile network.
Mobile Virtual Private Networks can be best when
there is need to roam across wireless networks in
and out of wireless coverage areas without
necessarily losing application sessions or dropping
the secure Virtual Private Network connection.
When using a conventional Virtual Private
Network, the network tunnel is normally disrupted
causing application disconnects, timeouts, fails or
even crashing of the computer in use.

6 IEEE TRANSACTIONS ON XXXXXXXXXXXXXXXXXXXX, VOL. #, NO. #, MMMMMMMM 1996
Challenges and Drawbacks
Traditional Virtual Private Networks are
Point to Point and thus do not support
broadcast domains.
Connecting to the Virtual Private
Networks takes several steps which force
the user to wait for authentication. If the
organization confirms that the computer is
healthy before allowing the connection,
establishing the Virtual Private Network
connection will take even longer.
Some environments may filter Virtual
Private Network traffic and the connection
will be a problem.
If for a machine the intranet it is connected
to goes through a Virtual Private Network,
and the internet traffic too goes through the
same, the internet performance will be
very slow.
Loss of the internet connection means re-
connecting even to the Virtual Private
Network and therefore if the network is
unstable and a user keeps losing his
internet connection, the time taken for each
reconnection to the Virtual Private
Network will be too much.
Solutions to challenges
The best way to handle Virtual Private Network is
to make sure that they are only used when needed.
Their use being not a guarantee to total security,
they should not be used when the problem being
handled by the machine is time since their use
only adds more time loss during connection. They
should also be avoided when the network being
used is not much stable and reliable.
CONCLUSION
Virtual Private Networks can be good when the
security need can be handled by IP Sec and Open
VPN. However, their security is not sufficient for
most user needs. All vendors will promise very
much pertaining the capabilities of the Virtual
Private Network but the information may later
prove to be exaggerated since most of the VPNs in
use today don’t meet the expected security levels.
FUTURE WORKS
As need for security in information shared on
networks rises, the need to study information
security and how it can be enhanced inreases. Our
efforts therefore, to analyze and understand more
the Virtual Private networks in place today don’t
end here. There are plans to advance the research
to cover all the other ways of securing information
and their effectiveness compared to Virtual Private
Networks. There are other information security
systems in place that users may opt if their
security service is reriable than the VPNs. The
analysis therefore will cover the ability to handle
all the users’ need as they seek the systems.
Challenges and Drawbacks
Traditional Virtual Private Networks are
Point to Point and thus do not support
broadcast domains.
Connecting to the Virtual Private
Networks takes several steps which force
the user to wait for authentication. If the
organization confirms that the computer is
healthy before allowing the connection,
establishing the Virtual Private Network
connection will take even longer.
Some environments may filter Virtual
Private Network traffic and the connection
will be a problem.
If for a machine the intranet it is connected
to goes through a Virtual Private Network,
and the internet traffic too goes through the
same, the internet performance will be
very slow.
Loss of the internet connection means re-
connecting even to the Virtual Private
Network and therefore if the network is
unstable and a user keeps losing his
internet connection, the time taken for each
reconnection to the Virtual Private
Network will be too much.
Solutions to challenges
The best way to handle Virtual Private Network is
to make sure that they are only used when needed.
Their use being not a guarantee to total security,
they should not be used when the problem being
handled by the machine is time since their use
only adds more time loss during connection. They
should also be avoided when the network being
used is not much stable and reliable.
CONCLUSION
Virtual Private Networks can be good when the
security need can be handled by IP Sec and Open
VPN. However, their security is not sufficient for
most user needs. All vendors will promise very
much pertaining the capabilities of the Virtual
Private Network but the information may later
prove to be exaggerated since most of the VPNs in
use today don’t meet the expected security levels.
FUTURE WORKS
As need for security in information shared on
networks rises, the need to study information
security and how it can be enhanced inreases. Our
efforts therefore, to analyze and understand more
the Virtual Private networks in place today don’t
end here. There are plans to advance the research
to cover all the other ways of securing information
and their effectiveness compared to Virtual Private
Networks. There are other information security
systems in place that users may opt if their
security service is reriable than the VPNs. The
analysis therefore will cover the ability to handle
all the users’ need as they seek the systems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AUTHOR ET AL.: TITLE
ABBREVIATIONS AND ACRONYMS
DNS Domain Name System
IP Sec Internet Protocol security
IPv4 Internet Protocol Version 4
IPv6 Internet protocol version 6
L2TP Layer 2 tunneling protocol
MS-CHAPv2 Microsoft handshake authentication
Protocol version 2
PPTP Point to point tunneling protocol
RSA A data security technique where there is no
efficient way to factor very large numbers
SHA-1 Secure harsh algorithm 1
SSL Secure Sockets layer
TCP/IP Transmission control protocol IP
VPN Virtual private network.
REFERENCES
[1] Mason, Andrew G., Cisco secure VPN, CISCO
press, 2002
[2] Virtual Private Networking, Microsoft Technet.
[3] Lewis Mark, Comparing, Designing and and
deploying VPNs, 2006
[4] Queen Mary University “A glance through the
VPN looking glass”- IPv6bleakage and DNS
hijacking in commercial VPN clients,
[5] “90% of SSL VPNs ‘hopelessly insecure’”, -
The register, www.rtheegister.co.uk
[6] RFC 1702, Generic Routing Encapsulation
over IPv4 networks, October 1994.
[7] Layer Two Tunneling Protocol "L2TP", RFC
2661, IETF (1999)
[8] Internetworking Technologies Hand book.
Networking Technology Series (4 Ed.). Cisco
Systems, Inc. (2004).
[9] W. Townsley, Layer Two Tunneling
Protocol "L2TP”, RFC 2661, August 1999
[10] A. Valencia, IP Based Virtual Private
Networks, RFC 2341, May 1998
[11] K. Hamzeh., Point-to-Point Tunneling
Protocol (PPTP), RFC 2637, July1999
[12] "Mobile VPN: Closing the Gap”,
SearchMobileComputing.com, July16, 2006.
[13] Willett Andy, "Solving the Computing
Challenges of Mobile Officers",
www.officer.com, May, 2006.
[14] Cheng Roger, "Lost Connections", the
Wall Street Journal, December 11, 2007.
[15] "Encryption and Security Protocols in a
VPN", www.computer.howstuffworks.com,
2015-09-23.
ABBREVIATIONS AND ACRONYMS
DNS Domain Name System
IP Sec Internet Protocol security
IPv4 Internet Protocol Version 4
IPv6 Internet protocol version 6
L2TP Layer 2 tunneling protocol
MS-CHAPv2 Microsoft handshake authentication
Protocol version 2
PPTP Point to point tunneling protocol
RSA A data security technique where there is no
efficient way to factor very large numbers
SHA-1 Secure harsh algorithm 1
SSL Secure Sockets layer
TCP/IP Transmission control protocol IP
VPN Virtual private network.
REFERENCES
[1] Mason, Andrew G., Cisco secure VPN, CISCO
press, 2002
[2] Virtual Private Networking, Microsoft Technet.
[3] Lewis Mark, Comparing, Designing and and
deploying VPNs, 2006
[4] Queen Mary University “A glance through the
VPN looking glass”- IPv6bleakage and DNS
hijacking in commercial VPN clients,
[5] “90% of SSL VPNs ‘hopelessly insecure’”, -
The register, www.rtheegister.co.uk
[6] RFC 1702, Generic Routing Encapsulation
over IPv4 networks, October 1994.
[7] Layer Two Tunneling Protocol "L2TP", RFC
2661, IETF (1999)
[8] Internetworking Technologies Hand book.
Networking Technology Series (4 Ed.). Cisco
Systems, Inc. (2004).
[9] W. Townsley, Layer Two Tunneling
Protocol "L2TP”, RFC 2661, August 1999
[10] A. Valencia, IP Based Virtual Private
Networks, RFC 2341, May 1998
[11] K. Hamzeh., Point-to-Point Tunneling
Protocol (PPTP), RFC 2637, July1999
[12] "Mobile VPN: Closing the Gap”,
SearchMobileComputing.com, July16, 2006.
[13] Willett Andy, "Solving the Computing
Challenges of Mobile Officers",
www.officer.com, May, 2006.
[14] Cheng Roger, "Lost Connections", the
Wall Street Journal, December 11, 2007.
[15] "Encryption and Security Protocols in a
VPN", www.computer.howstuffworks.com,
2015-09-23.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8 IEEE TRANSACTIONS ON VPN SECURITY INSUFFICIENCY, 600281
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





