Comprehensive Analysis of Security Vulnerabilities in Systems Report
VerifiedAdded on 2023/01/16
|21
|3691
|92
Report
AI Summary
This report provides a comprehensive analysis of system vulnerabilities across different security levels (medium, high, and critical). It examines three specific vulnerabilities: Spectre, Meltdown, and Eternal Blue, detailing their characteristics and potential impacts. The report utilizes the Common Vulnerability Scoring System (CVSS) to assess the severity of each vulnerability, including base score calculations and comparisons. It also explores potential mitigation strategies and delves into the exploitation of a high-risk vulnerability (CVE-2017-18330). The report aims to enhance the understanding of security vulnerabilities and promote effective risk management practices. Furthermore, the report highlights the importance of regular updates and proactive measures to safeguard systems against potential threats. The report is a valuable resource for students and professionals seeking to deepen their knowledge of cybersecurity.

Running head: VULNERABILITIES
VULNERABILITIES
Name of the Student:
Name of the University:
Author Note:
VULNERABILITIES
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VULNERABILITIES
Table of Contents
Introduction................................................................................................................................2
Three Vulnerabilities in the three level of security (Medium, High and Critical).................3
Base score calculation:...............................................................................................................5
Algorithm:..............................................................................................................................5
Calculations:...........................................................................................................................6
Comparison of the three Vulnerabilities (Spectre, Meltdown, Eternal Blue)......................10
CVSS Temporal and Environmental scores.........................................................................11
Potential Mitigation Strategies:............................................................................................15
Exploitation of High risk vulnerability CVE-2017-18330...................................................16
Conclusion:..............................................................................................................................17
References:...............................................................................................................................18
Table of Contents
Introduction................................................................................................................................2
Three Vulnerabilities in the three level of security (Medium, High and Critical).................3
Base score calculation:...............................................................................................................5
Algorithm:..............................................................................................................................5
Calculations:...........................................................................................................................6
Comparison of the three Vulnerabilities (Spectre, Meltdown, Eternal Blue)......................10
CVSS Temporal and Environmental scores.........................................................................11
Potential Mitigation Strategies:............................................................................................15
Exploitation of High risk vulnerability CVE-2017-18330...................................................16
Conclusion:..............................................................................................................................17
References:...............................................................................................................................18

2VULNERABILITIES
Introduction
The overall importance of vulnerabilities is completely based on various level of
security. The level of security goes from 1 the lowest to 5 the highest. Vulnerabilities can be
stated as the reliability to which they can be found as potential vulnerabilities. High
vulnerabilities are the one that comes up with security level of 4 or 5. Vulnerability of the
group is given to the attacker which come up with possibility for execution of code of target.
If the attacker comes up with unauthorized potential along with high privileges, then the code
can extract the required information. It can also result in tampering of data and deletion of
data of the user. The group of low or medium vulnerability is considered to be common one
which represents the attack vectors that more specific information about the given target.
There can be increase in overall degree of sensitivity that is from 1 to 3. In high vulnerability,
attacker can easily code on the target. While in medium and low vulnerability there is only
leakage of information. Medium level vulnerabilities are considered to be very less
complicated in nature as they depend on the given context. CVSS can be expanded as
common vulnerability scoring system that provides a framework that is open that comes up
with communicating characteristics. CVSS can create huge amount of impact on overall IT
vulnerabilities.
In the coming pages of the report, an idea has been provided with respect to three
vulnerabilities in the security level that is Medium, High and critical. After that, a derivation
has been done with respect to their CVSS score of 3.0 by making use of algorithm. All the
validation has been done by the help of proper calculation. All the possible similarities and
differences that are Spectre, Meltdown and Eternal blue have been done.
Introduction
The overall importance of vulnerabilities is completely based on various level of
security. The level of security goes from 1 the lowest to 5 the highest. Vulnerabilities can be
stated as the reliability to which they can be found as potential vulnerabilities. High
vulnerabilities are the one that comes up with security level of 4 or 5. Vulnerability of the
group is given to the attacker which come up with possibility for execution of code of target.
If the attacker comes up with unauthorized potential along with high privileges, then the code
can extract the required information. It can also result in tampering of data and deletion of
data of the user. The group of low or medium vulnerability is considered to be common one
which represents the attack vectors that more specific information about the given target.
There can be increase in overall degree of sensitivity that is from 1 to 3. In high vulnerability,
attacker can easily code on the target. While in medium and low vulnerability there is only
leakage of information. Medium level vulnerabilities are considered to be very less
complicated in nature as they depend on the given context. CVSS can be expanded as
common vulnerability scoring system that provides a framework that is open that comes up
with communicating characteristics. CVSS can create huge amount of impact on overall IT
vulnerabilities.
In the coming pages of the report, an idea has been provided with respect to three
vulnerabilities in the security level that is Medium, High and critical. After that, a derivation
has been done with respect to their CVSS score of 3.0 by making use of algorithm. All the
validation has been done by the help of proper calculation. All the possible similarities and
differences that are Spectre, Meltdown and Eternal blue have been done.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VULNERABILITIES
Three Vulnerabilities in the three level of security (Medium, High and Critical)
Software, Hardware and firmware vulnerability can result in huge amount of risk of
an organization by making use of computer system. Common Vulnerability Scoring System
(CVSS) aims to provide the best way by which they have characteristics of any vulnerability.
It aims to provide a numerical value along with representing in text of the score. The
collected numerical value of score can be used for translating it into critical, medium and
high. It will ultimately help the organization to give priority for the whole vulnerability
management process. CVSS aims to provide mainly three kinds of benefits like
It aims to provide proper standardization based on the vulnerability scores. There are
many instances when the organization makes use of common vulnerability in all the
IT platforms. This will result in single policy of vulnerability management which
provides maximum time for validation.
CVSS aims to provide framework where user is completely confused at the time of
validation and remediation of vulnerability. By the help of CVSS, the individual
characteristics can be used for driving the score which is transparent.
CVSS helps in prioritizing of the given risk at the instance of computing the
environmental score. Vulnerability can become textual to any organization. It
ultimately helps to provide a much better idea of risk which is posed by the
vulnerability to this organization.
In medium security level, vulnerabilities (CVE-2018-20650) which can score in the
medium range. It usually comes up with list of characteristics like
The affect system does not have any validation or even incorrect validation the input
which can affect overall control flow of data or even flow of diagram.
When the software does not validate the input properly for attacker which can draft
the input form which is not expected for the remaining portion of application.
Three Vulnerabilities in the three level of security (Medium, High and Critical)
Software, Hardware and firmware vulnerability can result in huge amount of risk of
an organization by making use of computer system. Common Vulnerability Scoring System
(CVSS) aims to provide the best way by which they have characteristics of any vulnerability.
It aims to provide a numerical value along with representing in text of the score. The
collected numerical value of score can be used for translating it into critical, medium and
high. It will ultimately help the organization to give priority for the whole vulnerability
management process. CVSS aims to provide mainly three kinds of benefits like
It aims to provide proper standardization based on the vulnerability scores. There are
many instances when the organization makes use of common vulnerability in all the
IT platforms. This will result in single policy of vulnerability management which
provides maximum time for validation.
CVSS aims to provide framework where user is completely confused at the time of
validation and remediation of vulnerability. By the help of CVSS, the individual
characteristics can be used for driving the score which is transparent.
CVSS helps in prioritizing of the given risk at the instance of computing the
environmental score. Vulnerability can become textual to any organization. It
ultimately helps to provide a much better idea of risk which is posed by the
vulnerability to this organization.
In medium security level, vulnerabilities (CVE-2018-20650) which can score in the
medium range. It usually comes up with list of characteristics like
The affect system does not have any validation or even incorrect validation the input
which can affect overall control flow of data or even flow of diagram.
When the software does not validate the input properly for attacker which can draft
the input form which is not expected for the remaining portion of application.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VULNERABILITIES
It will ultimately to different part of the application at the instance of receiving any
kind of input. This will result in control flow in altered and improper control of the
resources.
Vulnerabilities which require the attacker to make manipulation of the individual
victim through engineering tactics.
Vulnerabilities with respect to denial of service vulnerability can be considered to be
very much set up.
There are exploits which require an attacker to completely reside in the same local
network as the victim.
There are some instances vulnerabilities where the exploitation aims to provide
limited access.
There is large number of vulnerabilities that require the privilege of exploitation in
successful way.
In critical security level, vulnerabilities (CVE-2018-20718) that can score the critical
range which comes up with list of characteristics.
Software comes up with data and control in the given way that comprises of data and
control in proper way. It generally lacks any kind of vulnerability for user control that
results in injection issues.
In general, exploitation is considered to be very much straightforward in nature. It
merely the attackers do not require any particular kind of authentication. A list of
authentication credential and knowledge about the victim is produced. It does not
require to peruse the given target user. Social engineering can be considered to be as
one of the methods of performing any of the given special function.
Exploitation of the given vulnerability can easily result in root –level of both server
and infrastructure based devices.
It will ultimately to different part of the application at the instance of receiving any
kind of input. This will result in control flow in altered and improper control of the
resources.
Vulnerabilities which require the attacker to make manipulation of the individual
victim through engineering tactics.
Vulnerabilities with respect to denial of service vulnerability can be considered to be
very much set up.
There are exploits which require an attacker to completely reside in the same local
network as the victim.
There are some instances vulnerabilities where the exploitation aims to provide
limited access.
There is large number of vulnerabilities that require the privilege of exploitation in
successful way.
In critical security level, vulnerabilities (CVE-2018-20718) that can score the critical
range which comes up with list of characteristics.
Software comes up with data and control in the given way that comprises of data and
control in proper way. It generally lacks any kind of vulnerability for user control that
results in injection issues.
In general, exploitation is considered to be very much straightforward in nature. It
merely the attackers do not require any particular kind of authentication. A list of
authentication credential and knowledge about the victim is produced. It does not
require to peruse the given target user. Social engineering can be considered to be as
one of the methods of performing any of the given special function.
Exploitation of the given vulnerability can easily result in root –level of both server
and infrastructure based devices.

5VULNERABILITIES
In the cases of critical vulnerabilities, the best choice to upgrade the given patch
quickly. It needs to have another kind of mitigation measures for detection of attack.
A proper mitigation factor needs to be installed which is not accessible from the
internet.
In high-security level, there are some vulnerabilities (CVE-2017-18330) that can
score in the given high range that comes up with huge number of characteristics like
There is some instance of buffer overflow in AES- CCM encryption which is done
through initialization vector in Snapdragon mobile.
Any kind of exploitation can result in elevation of privileges.
Exploitation of the data in the system and network can result in huge amount of
system downtime.
Base score calculation:
Algorithm:
The Base Score is a function of the Impact and Exploitability sub score equations. Where the
Base score is defined as,
If (Impact sub score <= 0) 0 else,
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(𝐼𝑚𝑝𝑎𝑐𝑡 + 𝐸𝑥𝑝𝑙𝑜𝑖𝑡𝑎𝑏𝑖𝑙𝑖𝑡𝑦), 10])
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (𝐼𝑚𝑝𝑎𝑐𝑡 +
𝐸𝑥𝑝𝑙𝑜𝑖𝑡𝑎𝑏𝑖𝑙𝑖𝑡𝑦), 10])
and the Impact sub score (ISC) is defined as,
In the cases of critical vulnerabilities, the best choice to upgrade the given patch
quickly. It needs to have another kind of mitigation measures for detection of attack.
A proper mitigation factor needs to be installed which is not accessible from the
internet.
In high-security level, there are some vulnerabilities (CVE-2017-18330) that can
score in the given high range that comes up with huge number of characteristics like
There is some instance of buffer overflow in AES- CCM encryption which is done
through initialization vector in Snapdragon mobile.
Any kind of exploitation can result in elevation of privileges.
Exploitation of the data in the system and network can result in huge amount of
system downtime.
Base score calculation:
Algorithm:
The Base Score is a function of the Impact and Exploitability sub score equations. Where the
Base score is defined as,
If (Impact sub score <= 0) 0 else,
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(𝐼𝑚𝑝𝑎𝑐𝑡 + 𝐸𝑥𝑝𝑙𝑜𝑖𝑡𝑎𝑏𝑖𝑙𝑖𝑡𝑦), 10])
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (𝐼𝑚𝑝𝑎𝑐𝑡 +
𝐸𝑥𝑝𝑙𝑜𝑖𝑡𝑎𝑏𝑖𝑙𝑖𝑡𝑦), 10])
and the Impact sub score (ISC) is defined as,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6VULNERABILITIES
Scope Unchanged 6.42 × 𝐼𝑆𝐶Base
Scope Changed 7.52 × [𝐼𝑆𝐶𝐵𝑎𝑠𝑒 − 0.029] − 3.25 × [𝐼𝑆𝐶𝐵𝑎𝑠𝑒 − 0.02]15
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 − 𝐼𝑚𝑝𝑎𝑐𝑡𝐶𝑜𝑛𝑓) × (1 − 𝐼𝑚𝑝𝑎𝑐𝑡𝐼𝑛𝑡𝑒𝑔) × (1 −
𝐼𝑚𝑝𝑎𝑐𝑡𝐴𝑣𝑎𝑖𝑙)]
And the Exploitability sub score is,
8.22 × 𝐴𝑡𝑡𝑎𝑐𝑘𝑉𝑒𝑐𝑡𝑜𝑟 × 𝐴𝑡𝑡𝑎𝑐𝑘𝐶𝑜𝑚𝑝𝑙𝑒𝑥𝑖𝑡𝑦 × 𝑃𝑟𝑖𝑣𝑖𝑙𝑒𝑔𝑒𝑅𝑒𝑞𝑢𝑖𝑟𝑒𝑑 ×
𝑈𝑠𝑒𝑟𝐼𝑛𝑡𝑒𝑟𝑎𝑐𝑡𝑖𝑜𝑛
Calculations:
1. CVE-2018-20718 - Risk Critical
Impact sub score (ISC) is defined as,
Scope Unchanged 6.42 × 0.914816= 5.87311872
Scope Changed 7.52 × [0.914816 − 0.029] − 3.25 × [0.914816 − 0.02]15
= 7.52 x 0.885816 – 3.25 x 0.1888 = 6.6613 – 0.6136 = 6.0477
Scope Unchanged 6.42 × 𝐼𝑆𝐶Base
Scope Changed 7.52 × [𝐼𝑆𝐶𝐵𝑎𝑠𝑒 − 0.029] − 3.25 × [𝐼𝑆𝐶𝐵𝑎𝑠𝑒 − 0.02]15
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 − 𝐼𝑚𝑝𝑎𝑐𝑡𝐶𝑜𝑛𝑓) × (1 − 𝐼𝑚𝑝𝑎𝑐𝑡𝐼𝑛𝑡𝑒𝑔) × (1 −
𝐼𝑚𝑝𝑎𝑐𝑡𝐴𝑣𝑎𝑖𝑙)]
And the Exploitability sub score is,
8.22 × 𝐴𝑡𝑡𝑎𝑐𝑘𝑉𝑒𝑐𝑡𝑜𝑟 × 𝐴𝑡𝑡𝑎𝑐𝑘𝐶𝑜𝑚𝑝𝑙𝑒𝑥𝑖𝑡𝑦 × 𝑃𝑟𝑖𝑣𝑖𝑙𝑒𝑔𝑒𝑅𝑒𝑞𝑢𝑖𝑟𝑒𝑑 ×
𝑈𝑠𝑒𝑟𝐼𝑛𝑡𝑒𝑟𝑎𝑐𝑡𝑖𝑜𝑛
Calculations:
1. CVE-2018-20718 - Risk Critical
Impact sub score (ISC) is defined as,
Scope Unchanged 6.42 × 0.914816= 5.87311872
Scope Changed 7.52 × [0.914816 − 0.029] − 3.25 × [0.914816 − 0.02]15
= 7.52 x 0.885816 – 3.25 x 0.1888 = 6.6613 – 0.6136 = 6.0477
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7VULNERABILITIES
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 – 0.56) × (1 – 0.56) × (1 – 0.56)] = 1-0.085184=0.914816
And the Exploitability sub score is,
8.22 × 0.77 × 0.85 × 0.85 × 0.85 = 3.88704278
Base score is defined as,
If (Impact sub score <= 0) 0 else,
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(5.9 + 3.9), 10]) = 9.8
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (6 + 3.9), 10]) = 10
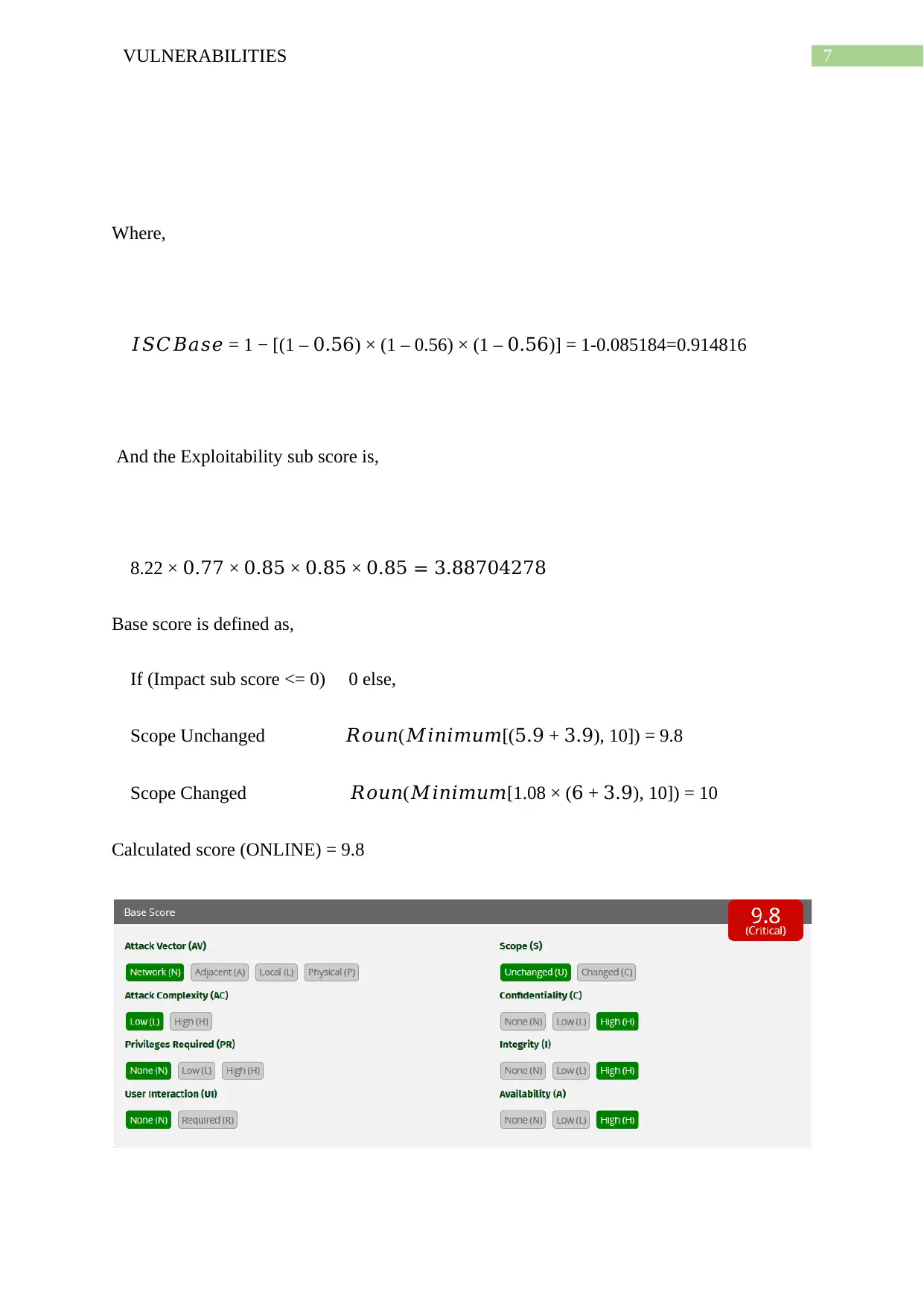
Calculated score (ONLINE) = 9.8
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 – 0.56) × (1 – 0.56) × (1 – 0.56)] = 1-0.085184=0.914816
And the Exploitability sub score is,
8.22 × 0.77 × 0.85 × 0.85 × 0.85 = 3.88704278
Base score is defined as,
If (Impact sub score <= 0) 0 else,
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(5.9 + 3.9), 10]) = 9.8
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (6 + 3.9), 10]) = 10
Calculated score (ONLINE) = 9.8

8VULNERABILITIES
As can be seen from above, both the manual and online calculated scores match each other.
Hence, the result is validated.
2. CVE-2018-20650 –Risk Medium
Impact sub score (ISC) is defined as,
Scope Unchanged 6.42 × 0.56= 3.595
Scope Changed 7.52 × [0.56 − 0.029] − 3.25 × [0.56 − 0.02]15
= 7.52 x 0.531 – 3.25 x 9.68x10^-5 = 3.99312 – 0.0003146 = 3.9928054
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 – 0) × (1 – 0) × (1 – 0.56)] = 1-0.44= 0.56
And the Exploitability sub score is,
8.22 × 0.85 × 0.77 × 0.85 × 0.62 = 2.835
Base score is defined as,
If (Impact sub score <= 0) 0 else,
As can be seen from above, both the manual and online calculated scores match each other.
Hence, the result is validated.
2. CVE-2018-20650 –Risk Medium
Impact sub score (ISC) is defined as,
Scope Unchanged 6.42 × 0.56= 3.595
Scope Changed 7.52 × [0.56 − 0.029] − 3.25 × [0.56 − 0.02]15
= 7.52 x 0.531 – 3.25 x 9.68x10^-5 = 3.99312 – 0.0003146 = 3.9928054
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 – 0) × (1 – 0) × (1 – 0.56)] = 1-0.44= 0.56
And the Exploitability sub score is,
8.22 × 0.85 × 0.77 × 0.85 × 0.62 = 2.835
Base score is defined as,
If (Impact sub score <= 0) 0 else,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9VULNERABILITIES
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(3.595 + 2.835), 10]) = 6.5
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (3.99 + 2.835), 10]) = 7.4
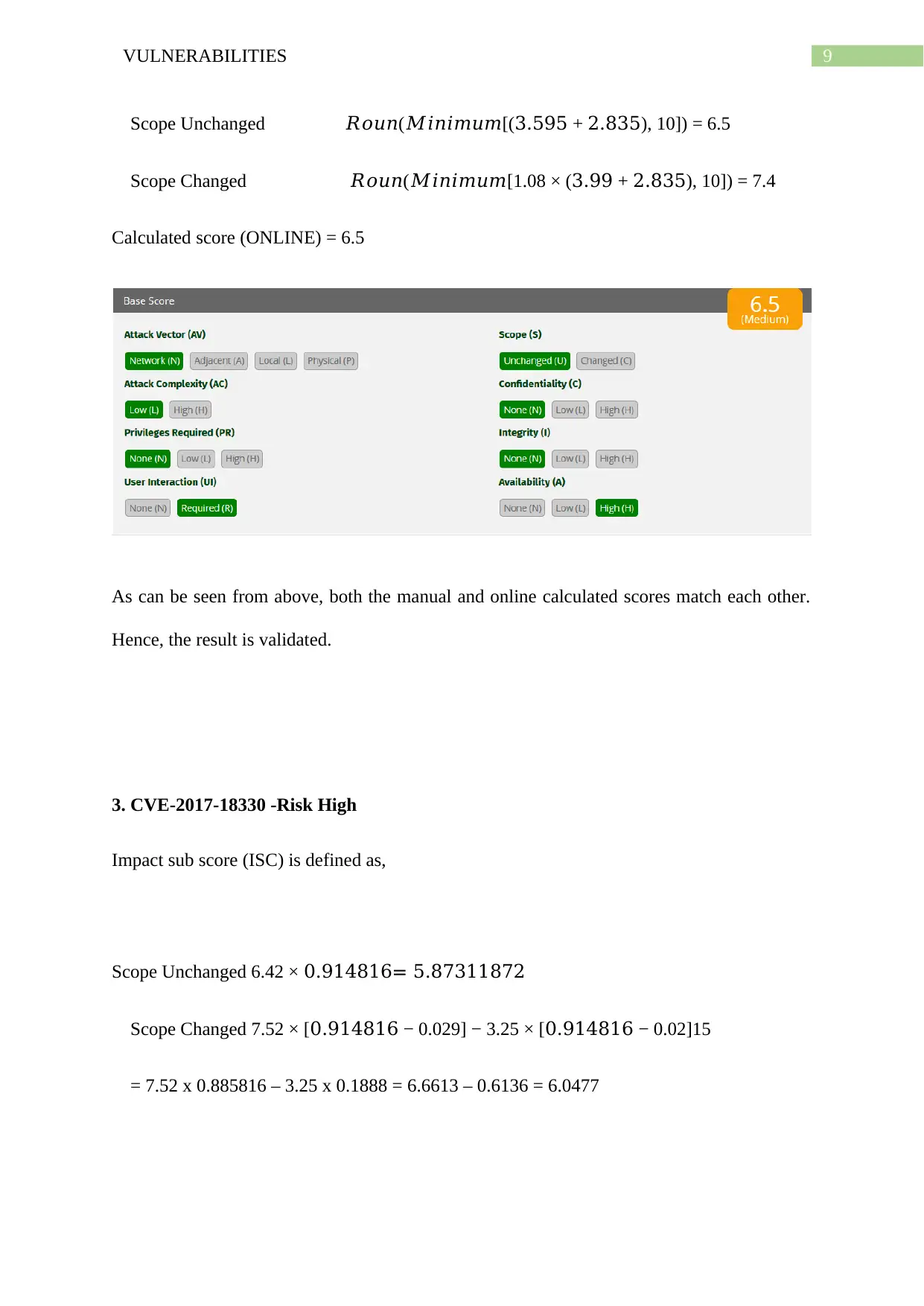
Calculated score (ONLINE) = 6.5
As can be seen from above, both the manual and online calculated scores match each other.
Hence, the result is validated.
3. CVE-2017-18330 -Risk High
Impact sub score (ISC) is defined as,
Scope Unchanged 6.42 × 0.914816= 5.87311872
Scope Changed 7.52 × [0.914816 − 0.029] − 3.25 × [0.914816 − 0.02]15
= 7.52 x 0.885816 – 3.25 x 0.1888 = 6.6613 – 0.6136 = 6.0477
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(3.595 + 2.835), 10]) = 6.5
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (3.99 + 2.835), 10]) = 7.4
Calculated score (ONLINE) = 6.5
As can be seen from above, both the manual and online calculated scores match each other.
Hence, the result is validated.
3. CVE-2017-18330 -Risk High
Impact sub score (ISC) is defined as,
Scope Unchanged 6.42 × 0.914816= 5.87311872
Scope Changed 7.52 × [0.914816 − 0.029] − 3.25 × [0.914816 − 0.02]15
= 7.52 x 0.885816 – 3.25 x 0.1888 = 6.6613 – 0.6136 = 6.0477
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10VULNERABILITIES
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 – 0.56) × (1 – 0.56) × (1 – 0.56)] = 0.914816
And the Exploitability sub score is,
Changed scope= 8.22 × 0.2 × 0.77 × 0.68 × 0.85 = 1.796
Unchanged scope= 8.22 × 0.2 × 0.77 × 0.62 × 0.85 = 0.667
Base score is defined as,
If (Impact sub score <= 0) 0 else,
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(5.9 + 1.8), 10]) = 7.8
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (6.04 + 0.667), 10]) = 7.2
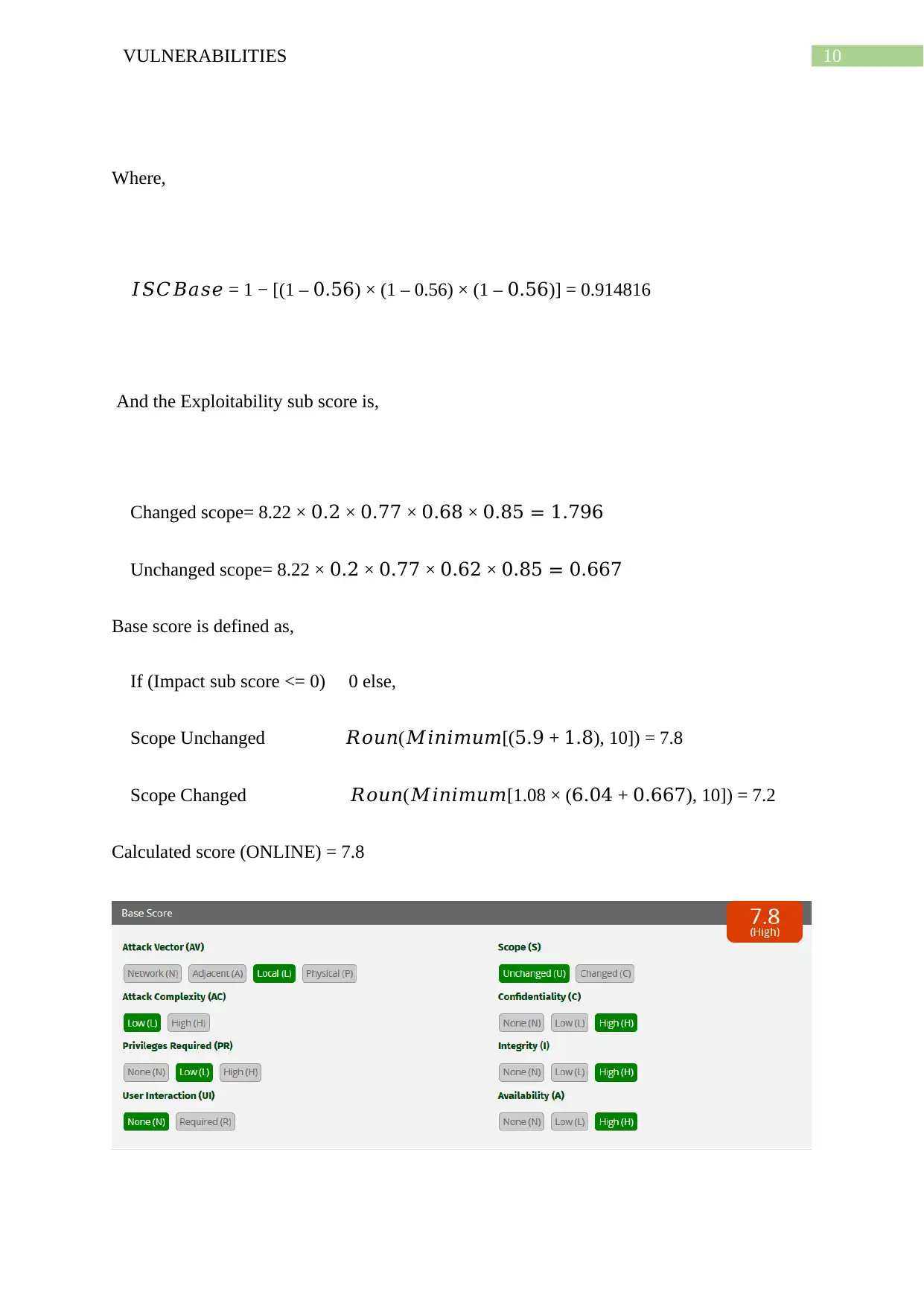
Calculated score (ONLINE) = 7.8
Where,
𝐼𝑆𝐶𝐵𝑎𝑠𝑒 = 1 − [(1 – 0.56) × (1 – 0.56) × (1 – 0.56)] = 0.914816
And the Exploitability sub score is,
Changed scope= 8.22 × 0.2 × 0.77 × 0.68 × 0.85 = 1.796
Unchanged scope= 8.22 × 0.2 × 0.77 × 0.62 × 0.85 = 0.667
Base score is defined as,
If (Impact sub score <= 0) 0 else,
Scope Unchanged 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[(5.9 + 1.8), 10]) = 7.8
Scope Changed 𝑅𝑜𝑢𝑛(𝑀𝑖𝑛𝑖𝑚𝑢𝑚[1.08 × (6.04 + 0.667), 10]) = 7.2
Calculated score (ONLINE) = 7.8

11VULNERABILITIES
As can be seen from above, both the manual and online calculated scores match each other.
Hence, the result is validated.
Comparison of the three Vulnerabilities (Spectre, Meltdown, Eternal Blue)
In CVE-2018-20718, there can be improper neutralization of some of the elements is
given as Output by the downstream components. Injection issues consist of huge
number of problems that have wide range of issues. All of these can be mitigated in
various ways and makes an attempt for making an alteration of control flow in the
whole process.
In Spectre attack, there comes up a popped on online platform on everyday basis. In
the earlier days, Spectre based attacks can be working section in CPU cannot be
investigated until now. Spectre aims to break the given isolation in different
application. It allows the attacker to provide error-free programs. It aims to follow
some of the best practices that are leakage of the secrets.
In Meltdown, there is breakdown of fundamental isolation between the application of
user and operating system. It will allow the attacker program to gain easy access to
the memory. Apart from this, it also aims to share secret of other associated programs
and operating system.
Eternal blue is the name of the vulnerability that is given to the vulnerability of
software in Microsoft Windows OS. This particular tech giant is known to have called
EternalBlue MS17-010. It will provide security updates on flaw on the 14th March.
This particular patch was released prior to WannaCry ransomware that spread around
the whole world. It focusses on update on regular basis.
Eternal blue vulnerability aims to work by complete exploitation of Microsoft Server
Block number 1.0. SMB can be defined as a networking file which shares protocol
As can be seen from above, both the manual and online calculated scores match each other.
Hence, the result is validated.
Comparison of the three Vulnerabilities (Spectre, Meltdown, Eternal Blue)
In CVE-2018-20718, there can be improper neutralization of some of the elements is
given as Output by the downstream components. Injection issues consist of huge
number of problems that have wide range of issues. All of these can be mitigated in
various ways and makes an attempt for making an alteration of control flow in the
whole process.
In Spectre attack, there comes up a popped on online platform on everyday basis. In
the earlier days, Spectre based attacks can be working section in CPU cannot be
investigated until now. Spectre aims to break the given isolation in different
application. It allows the attacker to provide error-free programs. It aims to follow
some of the best practices that are leakage of the secrets.
In Meltdown, there is breakdown of fundamental isolation between the application of
user and operating system. It will allow the attacker program to gain easy access to
the memory. Apart from this, it also aims to share secret of other associated programs
and operating system.
Eternal blue is the name of the vulnerability that is given to the vulnerability of
software in Microsoft Windows OS. This particular tech giant is known to have called
EternalBlue MS17-010. It will provide security updates on flaw on the 14th March.
This particular patch was released prior to WannaCry ransomware that spread around
the whole world. It focusses on update on regular basis.
Eternal blue vulnerability aims to work by complete exploitation of Microsoft Server
Block number 1.0. SMB can be defined as a networking file which shares protocol
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




