Vulnerability Assessment and Risk Management - Course Name
VerifiedAdded on 2022/09/24
|4
|286
|22
Report
AI Summary
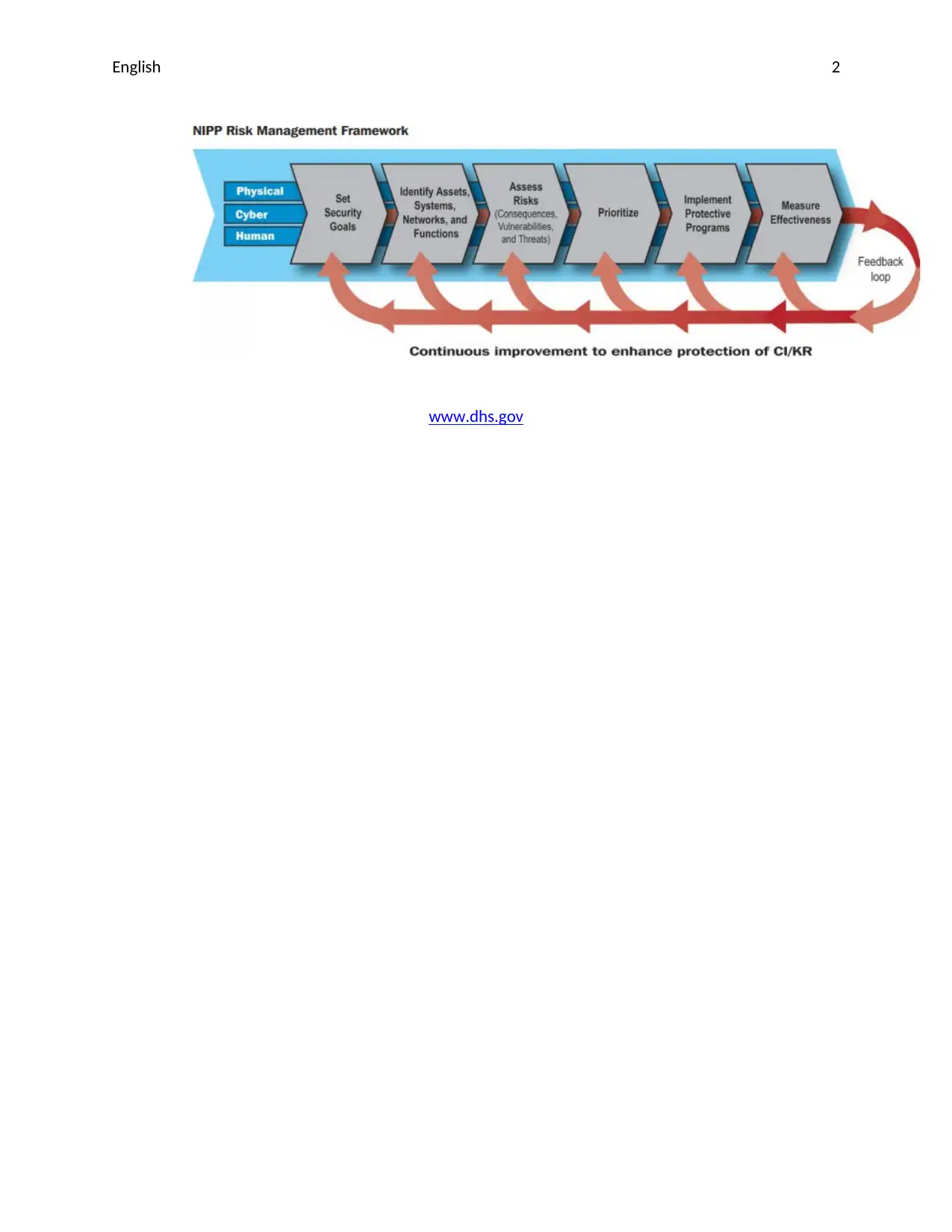
This report provides an overview of vulnerability assessment and risk management. It discusses the importance of evaluating potential hazards and risks in various systems, including information technology, energy supply, and water management networks. The report highlights the role of the National Infrastructure Protection Plan (NIPP) in establishing priorities and objectives for protecting critical infrastructure and key resources. It emphasizes the need for a comprehensive approach that considers physical, cyber, and human aspects. The report also explores the practical implications of risk evaluation, including the identification of potential dangers, assessment of their likelihood and severity, and the implementation of measures to mitigate or eliminate the identified risks. This assignment is a valuable resource for students looking to understand the principles of risk management and the protection of critical infrastructure.
1 out of 4









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)