ICT380: WA Oil & Gas Inc. Information Security Report
VerifiedAdded on 2021/08/16
|32
|8533
|112
Report
AI Summary
This report presents a comprehensive information security analysis and governance plan for WA Oil and Gas Inc. It begins with an overview of the company, its objectives, vision, and mission statement, followed by an introduction of the team and their roles. The core of the report focuses on risk management, including a detailed risk analysis identifying vulnerabilities in technical, human, physical, and policy areas. The report then provides a risk assessment, ranking information assets and conducting a cost-benefit analysis to justify control strategies. A security controls implementation plan and an incident response plan are also provided. The report aligns with industry standards like CIS controls and includes a toolkit with infographics and references. The analysis covers data leakage, service outages, PCI DSS compliance, and vulnerabilities in various systems, emphasizing the need for secure protocols, redundant infrastructure, and updated systems. Human risks like weak access controls and lack of security awareness are also addressed, along with physical security concerns such as access controls. The report recommends specific remediation strategies to mitigate identified risks, improve the overall information security structure, and protect the company's assets.

WA OIL AND GAS INC.
ICT380 Information Security Policy and Governance
CONTENTS
1. INTRODUCTION...................................................................................................................................4
1.1 OVERVIEW...................................................................................................................................4
1.2 OBJECTIVE....................................................................................................................................4
1.3 VISION..........................................................................................................................................4
1.4 MISSION STATEMENT..................................................................................................................4
2. TEAM INTRODUCTION........................................................................................................................5
2.1 AREAS OF INTEREST AND SKILLS..............................................................................................5
2.2 ROLES AND RESPONSIBILITIES.................................................................................................5
3. RISK MANAGEMENT...........................................................................................................................6
3.1 RISK ANALYSIS.............................................................................................................................6
3.2 RISK ANALYSIS SUMMARY........................................................................................................10
3.3 RISK ASSESSMENT.....................................................................................................................11
3.3.1 INFORMATION ASSETS...........................................................................................................11
3.3.2 INFORMATION ASSETS RANKING...........................................................................................11
3.4 RISK ASSESSMENT SUMMARY..................................................................................................12
3.5 COST BENEFIT ANALYSIS...........................................................................................................13
3.6 CONTROL STRATEGY.................................................................................................................14
3.7 ALIGNMENT WITH STANDARDS................................................................................................15
4. TOOLKIT.............................................................................................................................................16
4.1 INTRODUCTION.........................................................................................................................16
4.2 SCOPE........................................................................................................................................16
4.3 SECURITY CONTROLS IMPLEMENTATION PLAN.......................................................................16
4.3.1 CREATING AN INCIDENT RESPONSE CAPABILITY................................................................17
4.4 INCIDENT RESPONSE WEEKEND PLAN......................................................................................19
4.4.1 PREPARATION....................................................................................................................19
4.4.2 IDENTIFICATION.................................................................................................................20
4.4.3 CONTAINMENT..................................................................................................................21
ICT380 Information Security Policy and Governance
CONTENTS
1. INTRODUCTION...................................................................................................................................4
1.1 OVERVIEW...................................................................................................................................4
1.2 OBJECTIVE....................................................................................................................................4
1.3 VISION..........................................................................................................................................4
1.4 MISSION STATEMENT..................................................................................................................4
2. TEAM INTRODUCTION........................................................................................................................5
2.1 AREAS OF INTEREST AND SKILLS..............................................................................................5
2.2 ROLES AND RESPONSIBILITIES.................................................................................................5
3. RISK MANAGEMENT...........................................................................................................................6
3.1 RISK ANALYSIS.............................................................................................................................6
3.2 RISK ANALYSIS SUMMARY........................................................................................................10
3.3 RISK ASSESSMENT.....................................................................................................................11
3.3.1 INFORMATION ASSETS...........................................................................................................11
3.3.2 INFORMATION ASSETS RANKING...........................................................................................11
3.4 RISK ASSESSMENT SUMMARY..................................................................................................12
3.5 COST BENEFIT ANALYSIS...........................................................................................................13
3.6 CONTROL STRATEGY.................................................................................................................14
3.7 ALIGNMENT WITH STANDARDS................................................................................................15
4. TOOLKIT.............................................................................................................................................16
4.1 INTRODUCTION.........................................................................................................................16
4.2 SCOPE........................................................................................................................................16
4.3 SECURITY CONTROLS IMPLEMENTATION PLAN.......................................................................16
4.3.1 CREATING AN INCIDENT RESPONSE CAPABILITY................................................................17
4.4 INCIDENT RESPONSE WEEKEND PLAN......................................................................................19
4.4.1 PREPARATION....................................................................................................................19
4.4.2 IDENTIFICATION.................................................................................................................20
4.4.3 CONTAINMENT..................................................................................................................21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4.4.4 ERADICATION.....................................................................................................................22
4.4.5 RECOVERY..........................................................................................................................23
4.4.6 LESSONS LEARNED.............................................................................................................23
4.5 INFOGRAPHICS..........................................................................................................................24
4.6 REFERENCES..............................................................................................................................26
4.4.5 RECOVERY..........................................................................................................................23
4.4.6 LESSONS LEARNED.............................................................................................................23
4.5 INFOGRAPHICS..........................................................................................................................24
4.6 REFERENCES..............................................................................................................................26
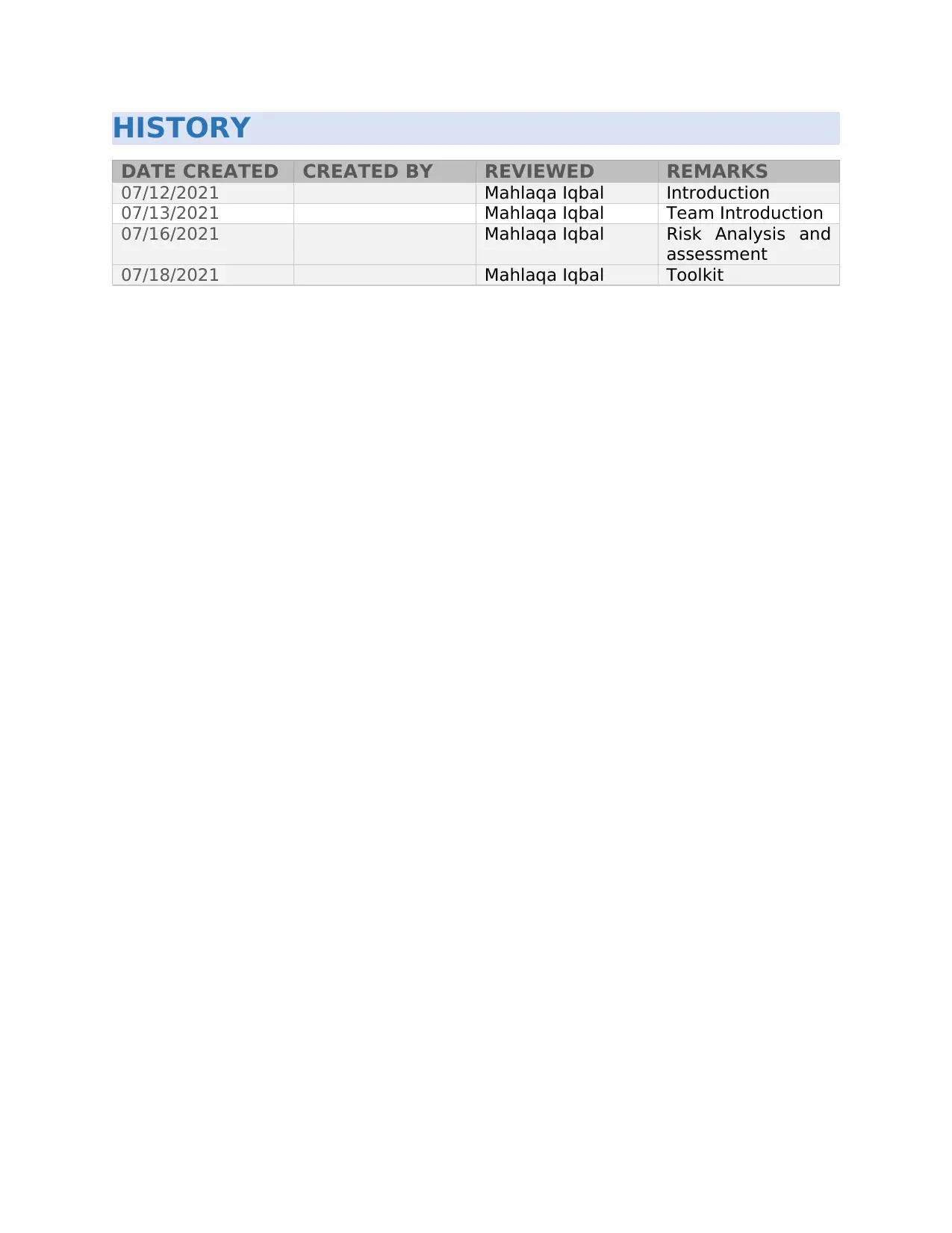
HISTORY
DATE CREATED CREATED BY REVIEWED REMARKS
07/12/2021 Mahlaqa Iqbal Introduction
07/13/2021 Mahlaqa Iqbal Team Introduction
07/16/2021 Mahlaqa Iqbal Risk Analysis and
assessment
07/18/2021 Mahlaqa Iqbal Toolkit
DATE CREATED CREATED BY REVIEWED REMARKS
07/12/2021 Mahlaqa Iqbal Introduction
07/13/2021 Mahlaqa Iqbal Team Introduction
07/16/2021 Mahlaqa Iqbal Risk Analysis and
assessment
07/18/2021 Mahlaqa Iqbal Toolkit
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.INTRODUCTION
1.1 OVERVIEW
WA Oil and Gas Inc. is a full spectrum analytical, software and hardware solution
company specializing in analysis, simulation, monitoring, control, optimization, and
automation for Oil and Gas Sector. Their services offer the most comprehensive
suite of integrated system enterprise solutions. WA Oil and Gas Inc. not only hold a
40% market share for providing tailored services in oil and gas monitoring systems
but their market base makes them recommendable for a consistent upgradation
makes them different for a long term relationship with their clients.
1.2 OBJECTIVE
The main objective of this report is to provide recommendations of security
measures with respect to the current security posture of WA Oil and Gas Inc. It will
also provide a detailed risk assessment to improve security structure thereafter.
1.3 VISION
WA Oil and Gas Inc.'s vision is to provide unmatched services of monitored and
automated seismic data in oil and gas industry with the latest technology in the
market.
1.4 MISSION STATEMENT
The aim of this risk assessment is to improve the overall Information Security
Structure of the company.
1.1 OVERVIEW
WA Oil and Gas Inc. is a full spectrum analytical, software and hardware solution
company specializing in analysis, simulation, monitoring, control, optimization, and
automation for Oil and Gas Sector. Their services offer the most comprehensive
suite of integrated system enterprise solutions. WA Oil and Gas Inc. not only hold a
40% market share for providing tailored services in oil and gas monitoring systems
but their market base makes them recommendable for a consistent upgradation
makes them different for a long term relationship with their clients.
1.2 OBJECTIVE
The main objective of this report is to provide recommendations of security
measures with respect to the current security posture of WA Oil and Gas Inc. It will
also provide a detailed risk assessment to improve security structure thereafter.
1.3 VISION
WA Oil and Gas Inc.'s vision is to provide unmatched services of monitored and
automated seismic data in oil and gas industry with the latest technology in the
market.
1.4 MISSION STATEMENT
The aim of this risk assessment is to improve the overall Information Security
Structure of the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
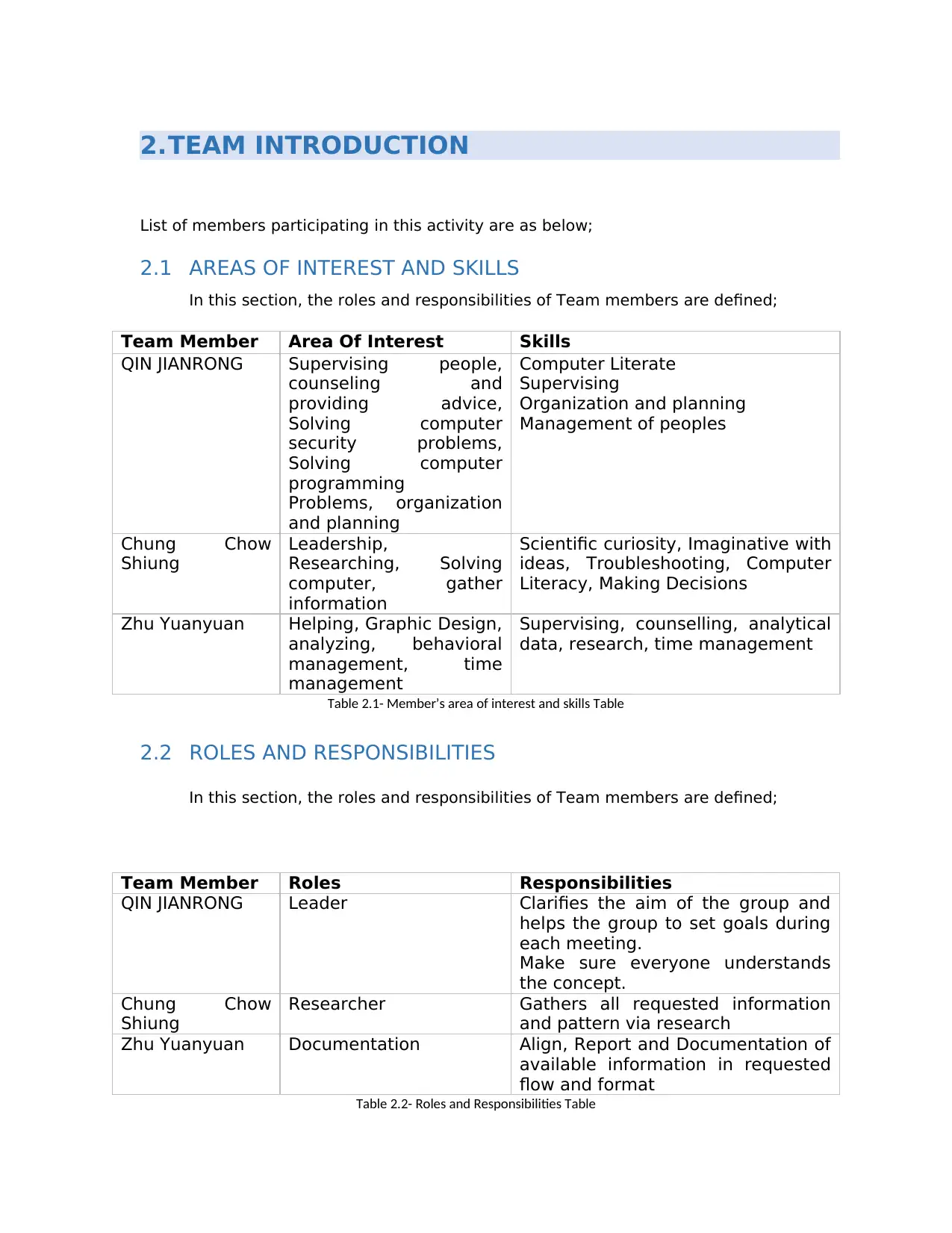
2.TEAM INTRODUCTION
List of members participating in this activity are as below;
2.1 AREAS OF INTEREST AND SKILLS
In this section, the roles and responsibilities of Team members are defined;
Team Member Area Of Interest Skills
QIN JIANRONG Supervising people,
counseling and
providing advice,
Solving computer
security problems,
Solving computer
programming
Problems, organization
and planning
Computer Literate
Supervising
Organization and planning
Management of peoples
Chung Chow
Shiung
Leadership,
Researching, Solving
computer, gather
information
Scientific curiosity, Imaginative with
ideas, Troubleshooting, Computer
Literacy, Making Decisions
Zhu Yuanyuan Helping, Graphic Design,
analyzing, behavioral
management, time
management
Supervising, counselling, analytical
data, research, time management
Table 2.1- Member’s area of interest and skills Table
2.2 ROLES AND RESPONSIBILITIES
In this section, the roles and responsibilities of Team members are defined;
Team Member Roles Responsibilities
QIN JIANRONG Leader Clarifies the aim of the group and
helps the group to set goals during
each meeting.
Make sure everyone understands
the concept.
Chung Chow
Shiung
Researcher Gathers all requested information
and pattern via research
Zhu Yuanyuan Documentation Align, Report and Documentation of
available information in requested
flow and format
Table 2.2- Roles and Responsibilities Table
List of members participating in this activity are as below;
2.1 AREAS OF INTEREST AND SKILLS
In this section, the roles and responsibilities of Team members are defined;
Team Member Area Of Interest Skills
QIN JIANRONG Supervising people,
counseling and
providing advice,
Solving computer
security problems,
Solving computer
programming
Problems, organization
and planning
Computer Literate
Supervising
Organization and planning
Management of peoples
Chung Chow
Shiung
Leadership,
Researching, Solving
computer, gather
information
Scientific curiosity, Imaginative with
ideas, Troubleshooting, Computer
Literacy, Making Decisions
Zhu Yuanyuan Helping, Graphic Design,
analyzing, behavioral
management, time
management
Supervising, counselling, analytical
data, research, time management
Table 2.1- Member’s area of interest and skills Table
2.2 ROLES AND RESPONSIBILITIES
In this section, the roles and responsibilities of Team members are defined;
Team Member Roles Responsibilities
QIN JIANRONG Leader Clarifies the aim of the group and
helps the group to set goals during
each meeting.
Make sure everyone understands
the concept.
Chung Chow
Shiung
Researcher Gathers all requested information
and pattern via research
Zhu Yuanyuan Documentation Align, Report and Documentation of
available information in requested
flow and format
Table 2.2- Roles and Responsibilities Table

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
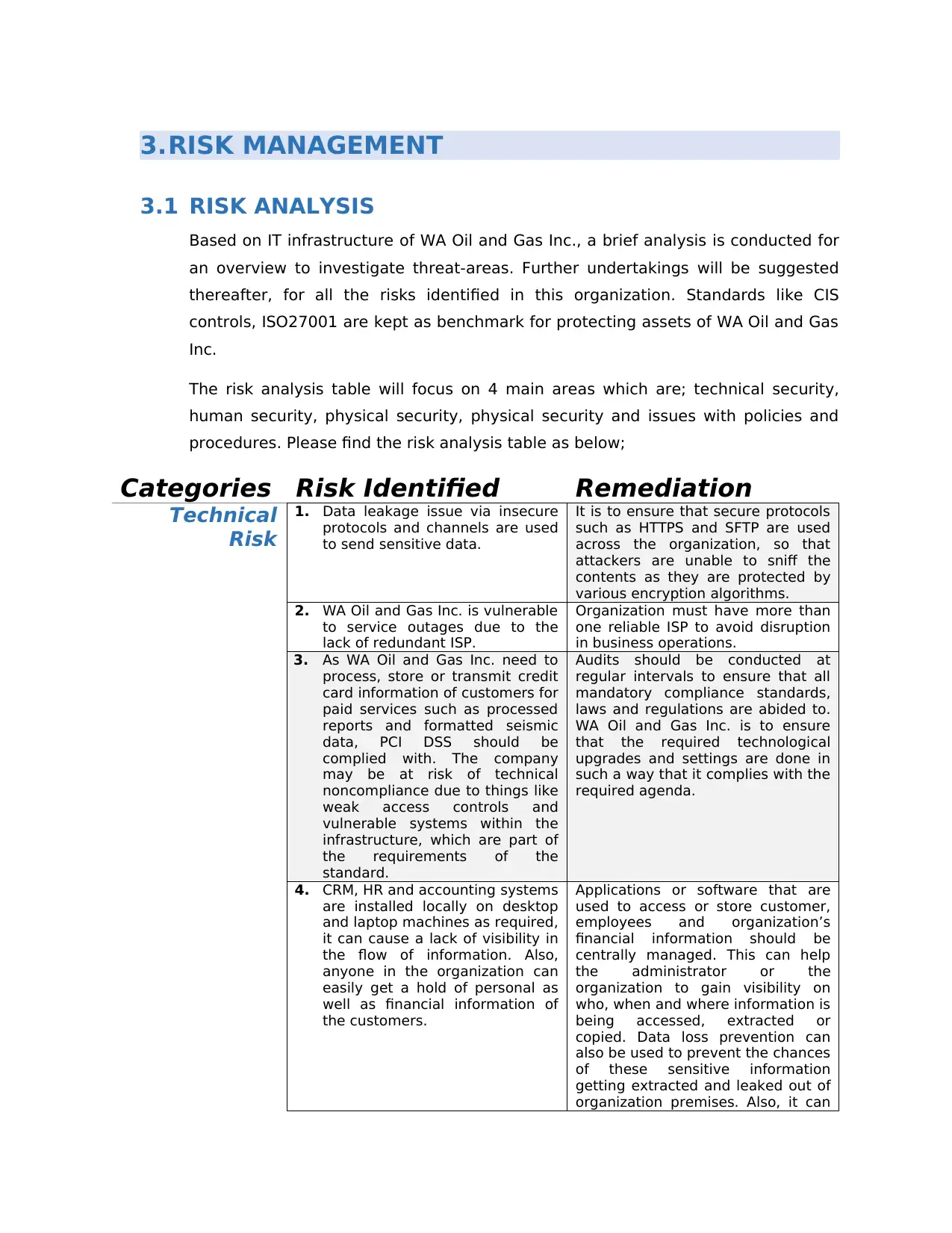
3.RISK MANAGEMENT
3.1 RISK ANALYSIS
Based on IT infrastructure of WA Oil and Gas Inc., a brief analysis is conducted for
an overview to investigate threat-areas. Further undertakings will be suggested
thereafter, for all the risks identified in this organization. Standards like CIS
controls, ISO27001 are kept as benchmark for protecting assets of WA Oil and Gas
Inc.
The risk analysis table will focus on 4 main areas which are; technical security,
human security, physical security, physical security and issues with policies and
procedures. Please find the risk analysis table as below;
Categories Risk Identified Remediation
Technical
Risk
1. Data leakage issue via insecure
protocols and channels are used
to send sensitive data.
It is to ensure that secure protocols
such as HTTPS and SFTP are used
across the organization, so that
attackers are unable to sniff the
contents as they are protected by
various encryption algorithms.
2. WA Oil and Gas Inc. is vulnerable
to service outages due to the
lack of redundant ISP.
Organization must have more than
one reliable ISP to avoid disruption
in business operations.
3. As WA Oil and Gas Inc. need to
process, store or transmit credit
card information of customers for
paid services such as processed
reports and formatted seismic
data, PCI DSS should be
complied with. The company
may be at risk of technical
noncompliance due to things like
weak access controls and
vulnerable systems within the
infrastructure, which are part of
the requirements of the
standard.
Audits should be conducted at
regular intervals to ensure that all
mandatory compliance standards,
laws and regulations are abided to.
WA Oil and Gas Inc. is to ensure
that the required technological
upgrades and settings are done in
such a way that it complies with the
required agenda.
4. CRM, HR and accounting systems
are installed locally on desktop
and laptop machines as required,
it can cause a lack of visibility in
the flow of information. Also,
anyone in the organization can
easily get a hold of personal as
well as financial information of
the customers.
Applications or software that are
used to access or store customer,
employees and organization’s
financial information should be
centrally managed. This can help
the administrator or the
organization to gain visibility on
who, when and where information is
being accessed, extracted or
copied. Data loss prevention can
also be used to prevent the chances
of these sensitive information
getting extracted and leaked out of
organization premises. Also, it can
3.1 RISK ANALYSIS
Based on IT infrastructure of WA Oil and Gas Inc., a brief analysis is conducted for
an overview to investigate threat-areas. Further undertakings will be suggested
thereafter, for all the risks identified in this organization. Standards like CIS
controls, ISO27001 are kept as benchmark for protecting assets of WA Oil and Gas
Inc.
The risk analysis table will focus on 4 main areas which are; technical security,
human security, physical security, physical security and issues with policies and
procedures. Please find the risk analysis table as below;
Categories Risk Identified Remediation
Technical
Risk
1. Data leakage issue via insecure
protocols and channels are used
to send sensitive data.
It is to ensure that secure protocols
such as HTTPS and SFTP are used
across the organization, so that
attackers are unable to sniff the
contents as they are protected by
various encryption algorithms.
2. WA Oil and Gas Inc. is vulnerable
to service outages due to the
lack of redundant ISP.
Organization must have more than
one reliable ISP to avoid disruption
in business operations.
3. As WA Oil and Gas Inc. need to
process, store or transmit credit
card information of customers for
paid services such as processed
reports and formatted seismic
data, PCI DSS should be
complied with. The company
may be at risk of technical
noncompliance due to things like
weak access controls and
vulnerable systems within the
infrastructure, which are part of
the requirements of the
standard.
Audits should be conducted at
regular intervals to ensure that all
mandatory compliance standards,
laws and regulations are abided to.
WA Oil and Gas Inc. is to ensure
that the required technological
upgrades and settings are done in
such a way that it complies with the
required agenda.
4. CRM, HR and accounting systems
are installed locally on desktop
and laptop machines as required,
it can cause a lack of visibility in
the flow of information. Also,
anyone in the organization can
easily get a hold of personal as
well as financial information of
the customers.
Applications or software that are
used to access or store customer,
employees and organization’s
financial information should be
centrally managed. This can help
the administrator or the
organization to gain visibility on
who, when and where information is
being accessed, extracted or
copied. Data loss prevention can
also be used to prevent the chances
of these sensitive information
getting extracted and leaked out of
organization premises. Also, it can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
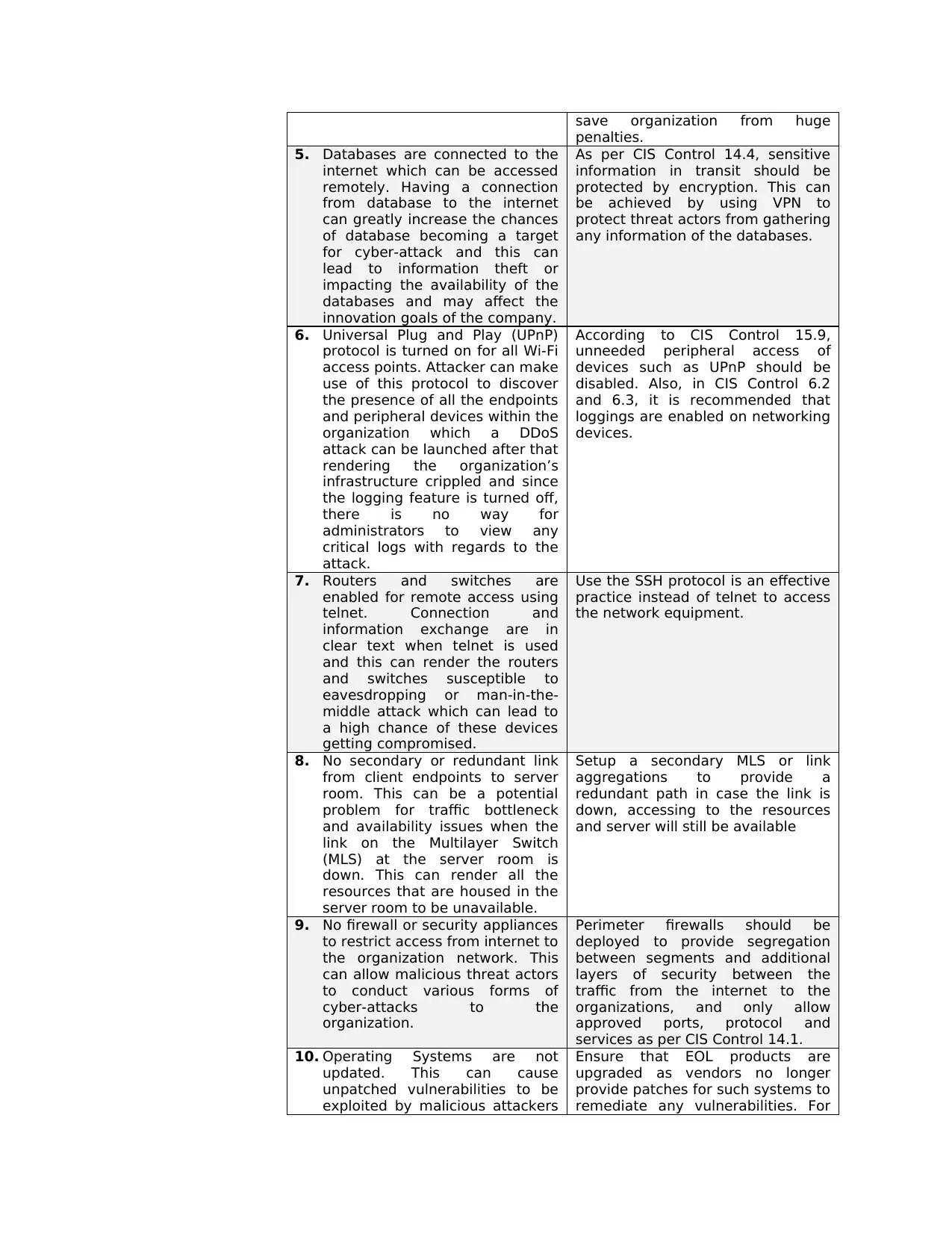
save organization from huge
penalties.
5. Databases are connected to the
internet which can be accessed
remotely. Having a connection
from database to the internet
can greatly increase the chances
of database becoming a target
for cyber-attack and this can
lead to information theft or
impacting the availability of the
databases and may affect the
innovation goals of the company.
As per CIS Control 14.4, sensitive
information in transit should be
protected by encryption. This can
be achieved by using VPN to
protect threat actors from gathering
any information of the databases.
6. Universal Plug and Play (UPnP)
protocol is turned on for all Wi-Fi
access points. Attacker can make
use of this protocol to discover
the presence of all the endpoints
and peripheral devices within the
organization which a DDoS
attack can be launched after that
rendering the organization’s
infrastructure crippled and since
the logging feature is turned off,
there is no way for
administrators to view any
critical logs with regards to the
attack.
According to CIS Control 15.9,
unneeded peripheral access of
devices such as UPnP should be
disabled. Also, in CIS Control 6.2
and 6.3, it is recommended that
loggings are enabled on networking
devices.
7. Routers and switches are
enabled for remote access using
telnet. Connection and
information exchange are in
clear text when telnet is used
and this can render the routers
and switches susceptible to
eavesdropping or man-in-the-
middle attack which can lead to
a high chance of these devices
getting compromised.
Use the SSH protocol is an effective
practice instead of telnet to access
the network equipment.
8. No secondary or redundant link
from client endpoints to server
room. This can be a potential
problem for traffic bottleneck
and availability issues when the
link on the Multilayer Switch
(MLS) at the server room is
down. This can render all the
resources that are housed in the
server room to be unavailable.
Setup a secondary MLS or link
aggregations to provide a
redundant path in case the link is
down, accessing to the resources
and server will still be available
9. No firewall or security appliances
to restrict access from internet to
the organization network. This
can allow malicious threat actors
to conduct various forms of
cyber-attacks to the
organization.
Perimeter firewalls should be
deployed to provide segregation
between segments and additional
layers of security between the
traffic from the internet to the
organizations, and only allow
approved ports, protocol and
services as per CIS Control 14.1.
10. Operating Systems are not
updated. This can cause
unpatched vulnerabilities to be
exploited by malicious attackers
Ensure that EOL products are
upgraded as vendors no longer
provide patches for such systems to
remediate any vulnerabilities. For
penalties.
5. Databases are connected to the
internet which can be accessed
remotely. Having a connection
from database to the internet
can greatly increase the chances
of database becoming a target
for cyber-attack and this can
lead to information theft or
impacting the availability of the
databases and may affect the
innovation goals of the company.
As per CIS Control 14.4, sensitive
information in transit should be
protected by encryption. This can
be achieved by using VPN to
protect threat actors from gathering
any information of the databases.
6. Universal Plug and Play (UPnP)
protocol is turned on for all Wi-Fi
access points. Attacker can make
use of this protocol to discover
the presence of all the endpoints
and peripheral devices within the
organization which a DDoS
attack can be launched after that
rendering the organization’s
infrastructure crippled and since
the logging feature is turned off,
there is no way for
administrators to view any
critical logs with regards to the
attack.
According to CIS Control 15.9,
unneeded peripheral access of
devices such as UPnP should be
disabled. Also, in CIS Control 6.2
and 6.3, it is recommended that
loggings are enabled on networking
devices.
7. Routers and switches are
enabled for remote access using
telnet. Connection and
information exchange are in
clear text when telnet is used
and this can render the routers
and switches susceptible to
eavesdropping or man-in-the-
middle attack which can lead to
a high chance of these devices
getting compromised.
Use the SSH protocol is an effective
practice instead of telnet to access
the network equipment.
8. No secondary or redundant link
from client endpoints to server
room. This can be a potential
problem for traffic bottleneck
and availability issues when the
link on the Multilayer Switch
(MLS) at the server room is
down. This can render all the
resources that are housed in the
server room to be unavailable.
Setup a secondary MLS or link
aggregations to provide a
redundant path in case the link is
down, accessing to the resources
and server will still be available
9. No firewall or security appliances
to restrict access from internet to
the organization network. This
can allow malicious threat actors
to conduct various forms of
cyber-attacks to the
organization.
Perimeter firewalls should be
deployed to provide segregation
between segments and additional
layers of security between the
traffic from the internet to the
organizations, and only allow
approved ports, protocol and
services as per CIS Control 14.1.
10. Operating Systems are not
updated. This can cause
unpatched vulnerabilities to be
exploited by malicious attackers
Ensure that EOL products are
upgraded as vendors no longer
provide patches for such systems to
remediate any vulnerabilities. For

and cause a variety of
confidentiality, integrity and
availability issues. Such OS
includes Windows 2008 R2 OS
and IBM blade Linux OS.
the Linux OS, it should still be
updated regularly to address
possible vulnerabilities. To prevent
stability issues, it should be full
tested in a staging environment or
VM before being updated.
Human Risk 1. Allowing temporary staff to have
the same access as permanent
staff is a weak security culture.
These human risks can allow the
company to be susceptible to
multiple malicious attack
vectors.
Regular mandatory security
awareness training or related talks,
instill leadership-driven
governance, motivating through
rewards, and improving existing
security policies and making sure
employees are aware and
acknowledge such policies. This
recommendation is in accordance
with CIS Control 17.
2. Hiring temporary staff from a
recruitment firm may become
dangerous. It is not known
whether a recruiting firm is
conducting a background check
or not.
Organizations should do a
background check on the
employment agency with regards to
the reputation, reliability and
credibility. Organization should also
conduct Background checks on the
candidate provided by the
employment agency and conduct
individual interviews to ensure that
temporary or contracted staff met
the requirement of the
organization.
3. Allowing sales staff to work at
any location and have immediate
access to client’s data or
resources can be a potential risk
as sales staff can connect to any
Wi-Fi without knowing if the SSID
that they are connected to is a
legitimate one. This can cause
them to be susceptible to Man-
in-the-Middle attacks and
increase the chances of
information theft.
According to CIS Control 14.4, all
sensitive information in transit
should be protected by encryption.
This can be achieved by deploying
VPN clients to client PCs to allow a
private connection to a VPN
controller in the organization’s
network.
4. Issuing an additional computer to
certain group of staff can have
the following risks increased:
Staff might misplace it, store it in
an improper way or place if they
deem that they do not need the
additional computer.
Additional computers might be
misused by the staff for non-
work related purposes.
Organization should not issue a
second or additional computer to
these groups of staff. Instead if the
staff have the needs for an
additional computer due to work
requirements, they should file a
request to the Desktop support
team or raise a request up to their
direct superior. All terminals should
also have disk-level encryption so
that when terminals are misplaced,
information at rest is still protected.
5. Contracted and temporary staff
have the same access rights as
permanent staff. There are
higher chance where anyone
from the staff, intentionally or
unintentionally modified the
information and company
records may be manipulated.
Access to information within
organizations should be restricted
for this group of staff since they will
be either with the company for a
short period of time or they are only
providing ad-hoc services. Access
given should only be restricted to
what is needed to perform the
duties. Other than that, encryption
confidentiality, integrity and
availability issues. Such OS
includes Windows 2008 R2 OS
and IBM blade Linux OS.
the Linux OS, it should still be
updated regularly to address
possible vulnerabilities. To prevent
stability issues, it should be full
tested in a staging environment or
VM before being updated.
Human Risk 1. Allowing temporary staff to have
the same access as permanent
staff is a weak security culture.
These human risks can allow the
company to be susceptible to
multiple malicious attack
vectors.
Regular mandatory security
awareness training or related talks,
instill leadership-driven
governance, motivating through
rewards, and improving existing
security policies and making sure
employees are aware and
acknowledge such policies. This
recommendation is in accordance
with CIS Control 17.
2. Hiring temporary staff from a
recruitment firm may become
dangerous. It is not known
whether a recruiting firm is
conducting a background check
or not.
Organizations should do a
background check on the
employment agency with regards to
the reputation, reliability and
credibility. Organization should also
conduct Background checks on the
candidate provided by the
employment agency and conduct
individual interviews to ensure that
temporary or contracted staff met
the requirement of the
organization.
3. Allowing sales staff to work at
any location and have immediate
access to client’s data or
resources can be a potential risk
as sales staff can connect to any
Wi-Fi without knowing if the SSID
that they are connected to is a
legitimate one. This can cause
them to be susceptible to Man-
in-the-Middle attacks and
increase the chances of
information theft.
According to CIS Control 14.4, all
sensitive information in transit
should be protected by encryption.
This can be achieved by deploying
VPN clients to client PCs to allow a
private connection to a VPN
controller in the organization’s
network.
4. Issuing an additional computer to
certain group of staff can have
the following risks increased:
Staff might misplace it, store it in
an improper way or place if they
deem that they do not need the
additional computer.
Additional computers might be
misused by the staff for non-
work related purposes.
Organization should not issue a
second or additional computer to
these groups of staff. Instead if the
staff have the needs for an
additional computer due to work
requirements, they should file a
request to the Desktop support
team or raise a request up to their
direct superior. All terminals should
also have disk-level encryption so
that when terminals are misplaced,
information at rest is still protected.
5. Contracted and temporary staff
have the same access rights as
permanent staff. There are
higher chance where anyone
from the staff, intentionally or
unintentionally modified the
information and company
records may be manipulated.
Access to information within
organizations should be restricted
for this group of staff since they will
be either with the company for a
short period of time or they are only
providing ad-hoc services. Access
given should only be restricted to
what is needed to perform the
duties. Other than that, encryption
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

or Privileged Access Management
(PAM) can be used as an additional
layer of security to protect these
data or documents.
6. Higher management has their
own office and are not allowed to
bring their laptop home. Since
it's an open-plan layout, their
offices can be breached via
cleaners after working hours if
they do not lock their office.
Enforce a policy to ensure all
employees lock their offices before
leaving work. Employ security
officers to go for hourly rounds and
make sure places that should be
locked, are locked.
Physical Risk 1. Access controls within the
company are weak, such as
unlock doors and unescorted
personnel. This may allow
potential threat actors to have
physical access to places where
they should not be allowed to.
Confidentiality, integrity and
availability of systems can be
compromised by such threat
vectors and can cripple the
company’s day-to-day
operations.
Ensure warning signboards and
adequate monitoring devices such
as CCTVs are placed in strategic
locations to act as a deterrence for
threat actors. Additionally, locations
in the office can be classified to
indicate which areas are restricted
areas. Access controls of sensitive
areas shall be improved with
technological enhancement like
automatic door locks and MFA. A
“clean desk” policy should also be
enforced so that all information is
kept out of sight.
2. The door access to the IT office
area is not locked during office
hours and during weekly
scheduled maintenance, the
office area is vacant at the
period from 4am to 6am. This
can be a risk due to the following
factor:
During office hours, anyone can
enter the IT office area and since
the server room is not locked.
Information assets stored in
these unprotected areas are
susceptible to problems such as
theft.
During the weekly schedule
maintenance period, there will
be no one in the office and any
other person with ill intention
can access the office area to
perform malicious acts.
The door access to the IT office
area should be locked at all times.
Staff working in this area must be
made known on the importance of
locking up these doors to prevent
unauthorized access when no one is
around during the scheduled
maintenance period. Digital access
locks can also be implemented on
the door access to the office area
which serve as an additional
security to prevent unauthorized
access and also this can mitigate
the issue of staff forgetting to lock
up the door when no one is around.
3. Server room not locked and
depends on IT staff to lock. This
may lead to give access to
unauthorized people at any point
during the office hours.
All doors to locations where critical
information assets are housed
should have physical security
controls such as digital security
locks to prevent unauthorized
personnel from accessing these
areas.
4. Backup tapes which contain
client data are housed on open
racks. Although the data
processing room is locked and
only authorized personnel are
allowed into the room, the risk of
leakage of client data still exists
since the backup tape can be
According to CIS Control 10,
backups which contain client data
should be stored at a physically
protected and secure location.
Encryption can also be used to
protect these backup tapes.
Additionally, these tapes should be
kept tagged to indicate the backup
(PAM) can be used as an additional
layer of security to protect these
data or documents.
6. Higher management has their
own office and are not allowed to
bring their laptop home. Since
it's an open-plan layout, their
offices can be breached via
cleaners after working hours if
they do not lock their office.
Enforce a policy to ensure all
employees lock their offices before
leaving work. Employ security
officers to go for hourly rounds and
make sure places that should be
locked, are locked.
Physical Risk 1. Access controls within the
company are weak, such as
unlock doors and unescorted
personnel. This may allow
potential threat actors to have
physical access to places where
they should not be allowed to.
Confidentiality, integrity and
availability of systems can be
compromised by such threat
vectors and can cripple the
company’s day-to-day
operations.
Ensure warning signboards and
adequate monitoring devices such
as CCTVs are placed in strategic
locations to act as a deterrence for
threat actors. Additionally, locations
in the office can be classified to
indicate which areas are restricted
areas. Access controls of sensitive
areas shall be improved with
technological enhancement like
automatic door locks and MFA. A
“clean desk” policy should also be
enforced so that all information is
kept out of sight.
2. The door access to the IT office
area is not locked during office
hours and during weekly
scheduled maintenance, the
office area is vacant at the
period from 4am to 6am. This
can be a risk due to the following
factor:
During office hours, anyone can
enter the IT office area and since
the server room is not locked.
Information assets stored in
these unprotected areas are
susceptible to problems such as
theft.
During the weekly schedule
maintenance period, there will
be no one in the office and any
other person with ill intention
can access the office area to
perform malicious acts.
The door access to the IT office
area should be locked at all times.
Staff working in this area must be
made known on the importance of
locking up these doors to prevent
unauthorized access when no one is
around during the scheduled
maintenance period. Digital access
locks can also be implemented on
the door access to the office area
which serve as an additional
security to prevent unauthorized
access and also this can mitigate
the issue of staff forgetting to lock
up the door when no one is around.
3. Server room not locked and
depends on IT staff to lock. This
may lead to give access to
unauthorized people at any point
during the office hours.
All doors to locations where critical
information assets are housed
should have physical security
controls such as digital security
locks to prevent unauthorized
personnel from accessing these
areas.
4. Backup tapes which contain
client data are housed on open
racks. Although the data
processing room is locked and
only authorized personnel are
allowed into the room, the risk of
leakage of client data still exists
since the backup tape can be
According to CIS Control 10,
backups which contain client data
should be stored at a physically
protected and secure location.
Encryption can also be used to
protect these backup tapes.
Additionally, these tapes should be
kept tagged to indicate the backup
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
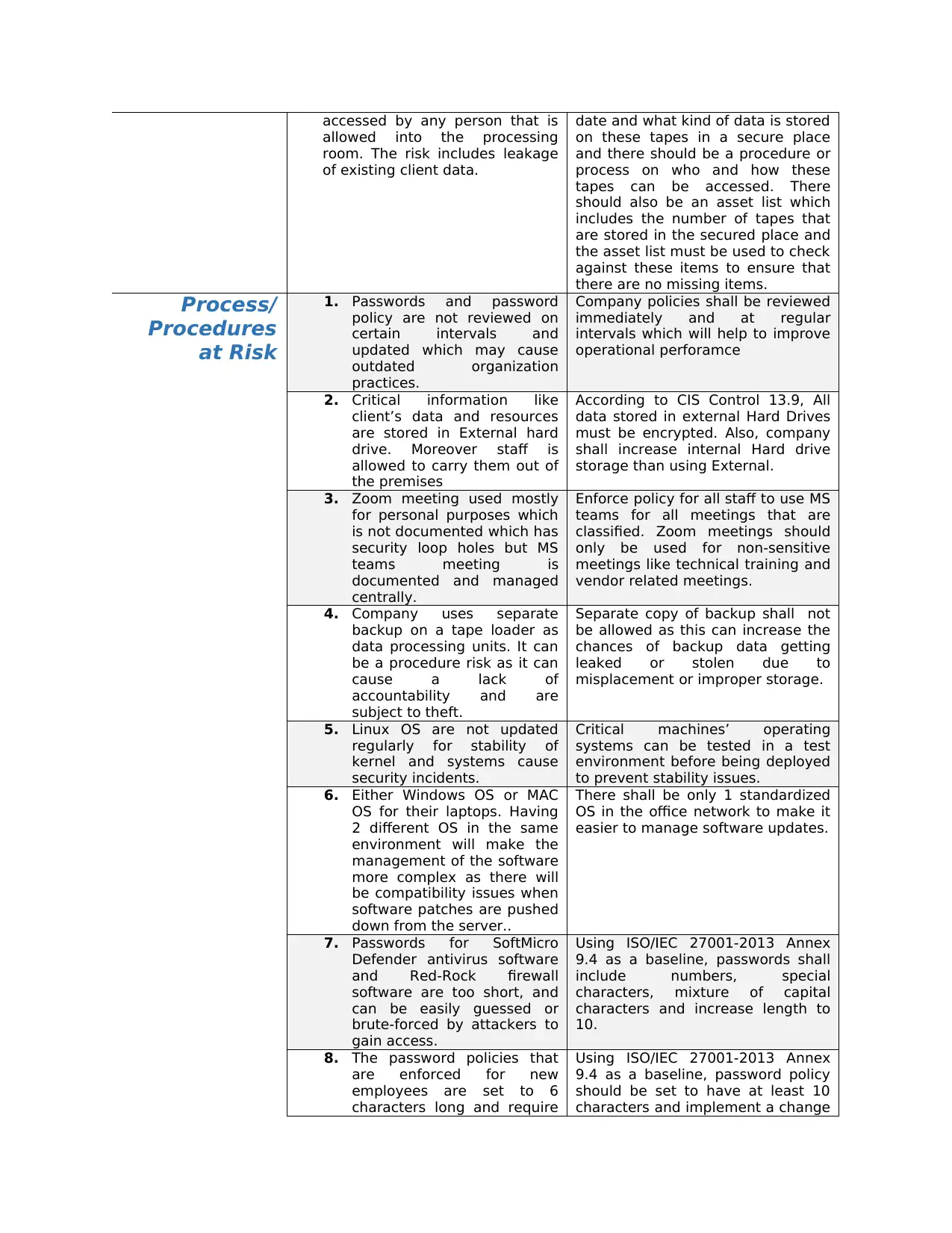
accessed by any person that is
allowed into the processing
room. The risk includes leakage
of existing client data.
date and what kind of data is stored
on these tapes in a secure place
and there should be a procedure or
process on who and how these
tapes can be accessed. There
should also be an asset list which
includes the number of tapes that
are stored in the secured place and
the asset list must be used to check
against these items to ensure that
there are no missing items.
Process/
Procedures
at Risk
1. Passwords and password
policy are not reviewed on
certain intervals and
updated which may cause
outdated organization
practices.
Company policies shall be reviewed
immediately and at regular
intervals which will help to improve
operational perforamce
2. Critical information like
client’s data and resources
are stored in External hard
drive. Moreover staff is
allowed to carry them out of
the premises
According to CIS Control 13.9, All
data stored in external Hard Drives
must be encrypted. Also, company
shall increase internal Hard drive
storage than using External.
3. Zoom meeting used mostly
for personal purposes which
is not documented which has
security loop holes but MS
teams meeting is
documented and managed
centrally.
Enforce policy for all staff to use MS
teams for all meetings that are
classified. Zoom meetings should
only be used for non-sensitive
meetings like technical training and
vendor related meetings.
4. Company uses separate
backup on a tape loader as
data processing units. It can
be a procedure risk as it can
cause a lack of
accountability and are
subject to theft.
Separate copy of backup shall not
be allowed as this can increase the
chances of backup data getting
leaked or stolen due to
misplacement or improper storage.
5. Linux OS are not updated
regularly for stability of
kernel and systems cause
security incidents.
Critical machines’ operating
systems can be tested in a test
environment before being deployed
to prevent stability issues.
6. Either Windows OS or MAC
OS for their laptops. Having
2 different OS in the same
environment will make the
management of the software
more complex as there will
be compatibility issues when
software patches are pushed
down from the server..
There shall be only 1 standardized
OS in the office network to make it
easier to manage software updates.
7. Passwords for SoftMicro
Defender antivirus software
and Red-Rock firewall
software are too short, and
can be easily guessed or
brute-forced by attackers to
gain access.
Using ISO/IEC 27001-2013 Annex
9.4 as a baseline, passwords shall
include numbers, special
characters, mixture of capital
characters and increase length to
10.
8. The password policies that
are enforced for new
employees are set to 6
characters long and require
Using ISO/IEC 27001-2013 Annex
9.4 as a baseline, password policy
should be set to have at least 10
characters and implement a change
allowed into the processing
room. The risk includes leakage
of existing client data.
date and what kind of data is stored
on these tapes in a secure place
and there should be a procedure or
process on who and how these
tapes can be accessed. There
should also be an asset list which
includes the number of tapes that
are stored in the secured place and
the asset list must be used to check
against these items to ensure that
there are no missing items.
Process/
Procedures
at Risk
1. Passwords and password
policy are not reviewed on
certain intervals and
updated which may cause
outdated organization
practices.
Company policies shall be reviewed
immediately and at regular
intervals which will help to improve
operational perforamce
2. Critical information like
client’s data and resources
are stored in External hard
drive. Moreover staff is
allowed to carry them out of
the premises
According to CIS Control 13.9, All
data stored in external Hard Drives
must be encrypted. Also, company
shall increase internal Hard drive
storage than using External.
3. Zoom meeting used mostly
for personal purposes which
is not documented which has
security loop holes but MS
teams meeting is
documented and managed
centrally.
Enforce policy for all staff to use MS
teams for all meetings that are
classified. Zoom meetings should
only be used for non-sensitive
meetings like technical training and
vendor related meetings.
4. Company uses separate
backup on a tape loader as
data processing units. It can
be a procedure risk as it can
cause a lack of
accountability and are
subject to theft.
Separate copy of backup shall not
be allowed as this can increase the
chances of backup data getting
leaked or stolen due to
misplacement or improper storage.
5. Linux OS are not updated
regularly for stability of
kernel and systems cause
security incidents.
Critical machines’ operating
systems can be tested in a test
environment before being deployed
to prevent stability issues.
6. Either Windows OS or MAC
OS for their laptops. Having
2 different OS in the same
environment will make the
management of the software
more complex as there will
be compatibility issues when
software patches are pushed
down from the server..
There shall be only 1 standardized
OS in the office network to make it
easier to manage software updates.
7. Passwords for SoftMicro
Defender antivirus software
and Red-Rock firewall
software are too short, and
can be easily guessed or
brute-forced by attackers to
gain access.
Using ISO/IEC 27001-2013 Annex
9.4 as a baseline, passwords shall
include numbers, special
characters, mixture of capital
characters and increase length to
10.
8. The password policies that
are enforced for new
employees are set to 6
characters long and require
Using ISO/IEC 27001-2013 Annex
9.4 as a baseline, password policy
should be set to have at least 10
characters and implement a change

to not change after 6
months. 6 character
passwords can be easily
guessed or brute-forced,
allowing attacker access to
the 2nd authentication
factor.
of password on a 3-monthly basis.
3.2 RISK ANALYSIS SUMMARY
According to the risks analysis, WA Oil and Risk Inc. found a few common patterns
to the cause of such risks. Firstly, most risks discovered in all risk tables involve
some form of bad security practices caused by employees. Secondly, there are
also weaknesses in basic security awareness, which could also be seen in all risks
tables. In this section, one risk from each of the risk tables listed in Section 3 will
be used to explain the common patterns found.
In Point 7 of Table 3.3.1, employees have a bad security practice of using
unsecure protocols like “telnet” to access networking devices. Engineers should
be technically sound to advise team leads or managers that such practice
contains the risks of allowing sensitive information to be compromised.
In Point 5 of Table 3.2, the organization allowed both contracted staff and
temporary staff to hold the same access rights as the permanent staff. This is also
considered a bad security practice as hiring managers should know that allowing
the same level of access rights as permanent staff can create security risks itself.
Table 3.3 contains the most bad security practices such as leaving places
unsecured and having inadequate security controls. It is common security
practice that sensitive locations within an organization should be secured by
locking and no unauthorized access should be allowed.
Point 5 of Table 3.4 accurately depicts the bad security practice caused by
engineers. Although it might be true that stability issues can occur during and
after any upgrade process, it should not be a reason to not update systems
altogether. System engineers should follow best practices to read the release
notes from vendors and advise on the need for the upgrade instead of avoiding
any patching.
In conclusion, a general direction for the risk flaws in WA Oil and Gas Inc. is that
they do not follow standard security policies and procedures in order to prevent
security risks. This also includes employees not being properly educated of such
risks and their consequences that follows the breach of security.
months. 6 character
passwords can be easily
guessed or brute-forced,
allowing attacker access to
the 2nd authentication
factor.
of password on a 3-monthly basis.
3.2 RISK ANALYSIS SUMMARY
According to the risks analysis, WA Oil and Risk Inc. found a few common patterns
to the cause of such risks. Firstly, most risks discovered in all risk tables involve
some form of bad security practices caused by employees. Secondly, there are
also weaknesses in basic security awareness, which could also be seen in all risks
tables. In this section, one risk from each of the risk tables listed in Section 3 will
be used to explain the common patterns found.
In Point 7 of Table 3.3.1, employees have a bad security practice of using
unsecure protocols like “telnet” to access networking devices. Engineers should
be technically sound to advise team leads or managers that such practice
contains the risks of allowing sensitive information to be compromised.
In Point 5 of Table 3.2, the organization allowed both contracted staff and
temporary staff to hold the same access rights as the permanent staff. This is also
considered a bad security practice as hiring managers should know that allowing
the same level of access rights as permanent staff can create security risks itself.
Table 3.3 contains the most bad security practices such as leaving places
unsecured and having inadequate security controls. It is common security
practice that sensitive locations within an organization should be secured by
locking and no unauthorized access should be allowed.
Point 5 of Table 3.4 accurately depicts the bad security practice caused by
engineers. Although it might be true that stability issues can occur during and
after any upgrade process, it should not be a reason to not update systems
altogether. System engineers should follow best practices to read the release
notes from vendors and advise on the need for the upgrade instead of avoiding
any patching.
In conclusion, a general direction for the risk flaws in WA Oil and Gas Inc. is that
they do not follow standard security policies and procedures in order to prevent
security risks. This also includes employees not being properly educated of such
risks and their consequences that follows the breach of security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.