CSCI 3301: Developing Secure Web Applications with PHP and MySQL
VerifiedAdded on 2023/06/14
|9
|1493
|176
Project
AI Summary
This project report details the development of a secure web application using PHP and MySQL, addressing common security vulnerabilities. Part I presents a technical essay explaining five security issues associated with PHP applications: SQL injection, Cross-Site Scripting (XSS), Session Hijacking, Directory Traversal, and Remote File Inclusion, referencing external articles. Part II involves creating an HTML form and storing the data in both a file and a MySQL database, including an SQL script to generate 500 contact details. The report also explains the security measures taken, such as input validation using HTML5, prevention of SQL injection using PDO parameterized queries, and avoidance of remote file inclusion by using server-based file systems. Concrete examples are provided to demonstrate how these security measures block potential attacks.

Part I – Technical Essay
Introduction
All sorts of conservative web applications are built by human and it is quite natural that humans
are prone to commit mistakes. The concept of complete security would remain an unfulfilled dream
since all applications are prone to the risk of being vulnerable. Hence it becomes the profession of
programmers to confirm that the risk is reduced by all means. Defending web application may either be
a simple task or an extremely time consuming task. To overcome any sort of risk faced in web
applications, we have to discuss the few ways of attacking a web application in PHP
SQL Injection
One of the code injection techniques which is involved in attacking data-driven applications is
SQL injection, in which nefarious SQL statements are added into an entry field for implementation. If the
web developers fail to construct data validation or any checking functionality for the ranges of the
website where data from the outside sources can be injected into the website, there is possibility of the
occurrence of attack by hackers. There are chances for the attacker to insert his designed SQL queries in
vulnerable that use data posted by the user to look-up rather in the database (Sharma, 2014).
Cross Site Scripting (XSS)
Sometimes, an attack may get injected the script into the webpage through html form or using
an anchor link tag. This may lead to redirecting us to a phishing page that gathers sensitive information.
The hackers may steal our session identifier so that they might impersonate us and access the web
application. This sort of attack from the hacker is mostly a kind of script injection that is made possible
by mistakenly validating user data. The injected code may be any malicious client-side code. The injected
code is highly valuable to stay away from damaging informations on the web server or execute a
malicious process in the client browser (Fekete, 2013).
Introduction
All sorts of conservative web applications are built by human and it is quite natural that humans
are prone to commit mistakes. The concept of complete security would remain an unfulfilled dream
since all applications are prone to the risk of being vulnerable. Hence it becomes the profession of
programmers to confirm that the risk is reduced by all means. Defending web application may either be
a simple task or an extremely time consuming task. To overcome any sort of risk faced in web
applications, we have to discuss the few ways of attacking a web application in PHP
SQL Injection
One of the code injection techniques which is involved in attacking data-driven applications is
SQL injection, in which nefarious SQL statements are added into an entry field for implementation. If the
web developers fail to construct data validation or any checking functionality for the ranges of the
website where data from the outside sources can be injected into the website, there is possibility of the
occurrence of attack by hackers. There are chances for the attacker to insert his designed SQL queries in
vulnerable that use data posted by the user to look-up rather in the database (Sharma, 2014).
Cross Site Scripting (XSS)
Sometimes, an attack may get injected the script into the webpage through html form or using
an anchor link tag. This may lead to redirecting us to a phishing page that gathers sensitive information.
The hackers may steal our session identifier so that they might impersonate us and access the web
application. This sort of attack from the hacker is mostly a kind of script injection that is made possible
by mistakenly validating user data. The injected code may be any malicious client-side code. The injected
code is highly valuable to stay away from damaging informations on the web server or execute a
malicious process in the client browser (Fekete, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Session Hijacking
Usually, Session IDs are stolen via a XSS attack. Thereby preventing such thefts is doubly
beneficial to us. It is impossible for the Session and cookies to exploit the information which is in the
database server but it may affect the client login data. A session may get started when the user gets into
contact with the Web server. Each session information is stored in Web Server, but Web developer may
store this session information in a cookie for faster retrieval or validation (Shirey, 2013). It may lead to
hacking. These information saved on the server could be availed by transfer the ID with the page
request (Qureshi, 2015). It is advisable to update the session information often or use encrypted session
id
Directory Traversal
Directory Traversal generally denotes the attack in which an authenticated or unauthenticated
user can request and view or execute files that reside external the root directory of a web application, or
outside a directory in which they should be restricted to. The root directory and access other parts of
the file system can take advantage of this vulnerability by an attacker (Prodromou, 2016). This usually
gives the attacker the ability to view controlled files, or run the commands on the server which may lead
to give full rights of the system
Remote File Inclusion
Remote File inclusion is an attack wherein an attacker may add the scripting file into web server.
These script may lead to create/delete/modify the data or file in the web server dynamically. In the
latest version of PHP, we can configure the allow_url_include set to off which is used to restrict the
server file from remote accessing or inclusion of file from the hacker system to the web server (Muscat,
2017).
Usually, Session IDs are stolen via a XSS attack. Thereby preventing such thefts is doubly
beneficial to us. It is impossible for the Session and cookies to exploit the information which is in the
database server but it may affect the client login data. A session may get started when the user gets into
contact with the Web server. Each session information is stored in Web Server, but Web developer may
store this session information in a cookie for faster retrieval or validation (Shirey, 2013). It may lead to
hacking. These information saved on the server could be availed by transfer the ID with the page
request (Qureshi, 2015). It is advisable to update the session information often or use encrypted session
id
Directory Traversal
Directory Traversal generally denotes the attack in which an authenticated or unauthenticated
user can request and view or execute files that reside external the root directory of a web application, or
outside a directory in which they should be restricted to. The root directory and access other parts of
the file system can take advantage of this vulnerability by an attacker (Prodromou, 2016). This usually
gives the attacker the ability to view controlled files, or run the commands on the server which may lead
to give full rights of the system
Remote File Inclusion
Remote File inclusion is an attack wherein an attacker may add the scripting file into web server.
These script may lead to create/delete/modify the data or file in the web server dynamically. In the
latest version of PHP, we can configure the allow_url_include set to off which is used to restrict the
server file from remote accessing or inclusion of file from the hacker system to the web server (Muscat,
2017).

Part II – PHP, MySQL, Web-Based Security
Create the following HTML form and
a) Store the information from the form in a file
b) Store the information from the form in a MySQL table
Ref: code.zip
SQL Query to generate 500 contact details using Loop
PHP Code:
<?php
include 'dbconnect.php';
$i=1;
while($i<=500)
{
$fname1='First'.$i;
$lname1='Last'.$i;
$addr1='Addr '.$i;
$state1='FA';
$zip1=45872+$i;
$phone='8989483'.(999-$i);
$email1='xyz@tt.co'.$i;
$sql="insert into contact (FirstName,LastName,Address,State,Zip,Phone,Email) values
(:fname,:lname,:addr,:state,:zip,:phone,:email)";
Create the following HTML form and
a) Store the information from the form in a file
b) Store the information from the form in a MySQL table
Ref: code.zip
SQL Query to generate 500 contact details using Loop
PHP Code:
<?php
include 'dbconnect.php';
$i=1;
while($i<=500)
{
$fname1='First'.$i;
$lname1='Last'.$i;
$addr1='Addr '.$i;
$state1='FA';
$zip1=45872+$i;
$phone='8989483'.(999-$i);
$email1='xyz@tt.co'.$i;
$sql="insert into contact (FirstName,LastName,Address,State,Zip,Phone,Email) values
(:fname,:lname,:addr,:state,:zip,:phone,:email)";
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

$q=$dbconn->prepare($sql);
$res=$q->execute(array(':fname'=>$fname1, ':lname'=>$lname1, ':addr'=>$addr1,
':state'=>$state1, ':zip'=>$zip1, ':phone'=>$phone1, ':email'=>$email1));
$i++;
}
echo '<p><b>500 Sample records are created</b></p>';
?>
Table Creation/ Description of the table
SQL Code:
CREATE TABLE Contact (ContactID INT NOT NULL AUTO_INCREMENT, FirstName VARCHAR(25)
NOT NULL, LastName VARCHAR(25) NOT NULL, Address VARCHAR(60) NOT NULL, State
VARCHAR(3) NOT NULL, Zip INT(5) NOT NULL, Phone VARCHAR(10) NOT NULL, Email
VARCHAR(45) NOT NULL, PRIMARY KEY (ContactID));
ContactID - Contact ID
FirstName - First Name of the person
LastName - Last Name of the person
Address - Address of the person
State - State Code of the person
Zip - Zip Code (5 digit number)
Phone - Phone Number (10 digit number)
Email - Email Address (@ symbol)
Here ContactID is the Primary key
$res=$q->execute(array(':fname'=>$fname1, ':lname'=>$lname1, ':addr'=>$addr1,
':state'=>$state1, ':zip'=>$zip1, ':phone'=>$phone1, ':email'=>$email1));
$i++;
}
echo '<p><b>500 Sample records are created</b></p>';
?>
Table Creation/ Description of the table
SQL Code:
CREATE TABLE Contact (ContactID INT NOT NULL AUTO_INCREMENT, FirstName VARCHAR(25)
NOT NULL, LastName VARCHAR(25) NOT NULL, Address VARCHAR(60) NOT NULL, State
VARCHAR(3) NOT NULL, Zip INT(5) NOT NULL, Phone VARCHAR(10) NOT NULL, Email
VARCHAR(45) NOT NULL, PRIMARY KEY (ContactID));
ContactID - Contact ID
FirstName - First Name of the person
LastName - Last Name of the person
Address - Address of the person
State - State Code of the person
Zip - Zip Code (5 digit number)
Phone - Phone Number (10 digit number)
Email - Email Address (@ symbol)
Here ContactID is the Primary key
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


Explain in detail the security measures you took to secure the web-based application
Input Validation
I used HTML5 form. It is used to validate the input data. It prevents unnecessary data to enter
into the file or database
Avoid SQL injection using PDO
PDO data object is used to execute the query using parameterized query. It avoids/prevent the
SQL injection from input (textbox)
Avoid File Inclusion
In file handling, I have used server based file system without any referencing path. So that It is
used to restrict the remote file inclusion
Input Validation
I used HTML5 form. It is used to validate the input data. It prevents unnecessary data to enter
into the file or database
Avoid SQL injection using PDO
PDO data object is used to execute the query using parameterized query. It avoids/prevent the
SQL injection from input (textbox)
Avoid File Inclusion
In file handling, I have used server based file system without any referencing path. So that It is
used to restrict the remote file inclusion
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
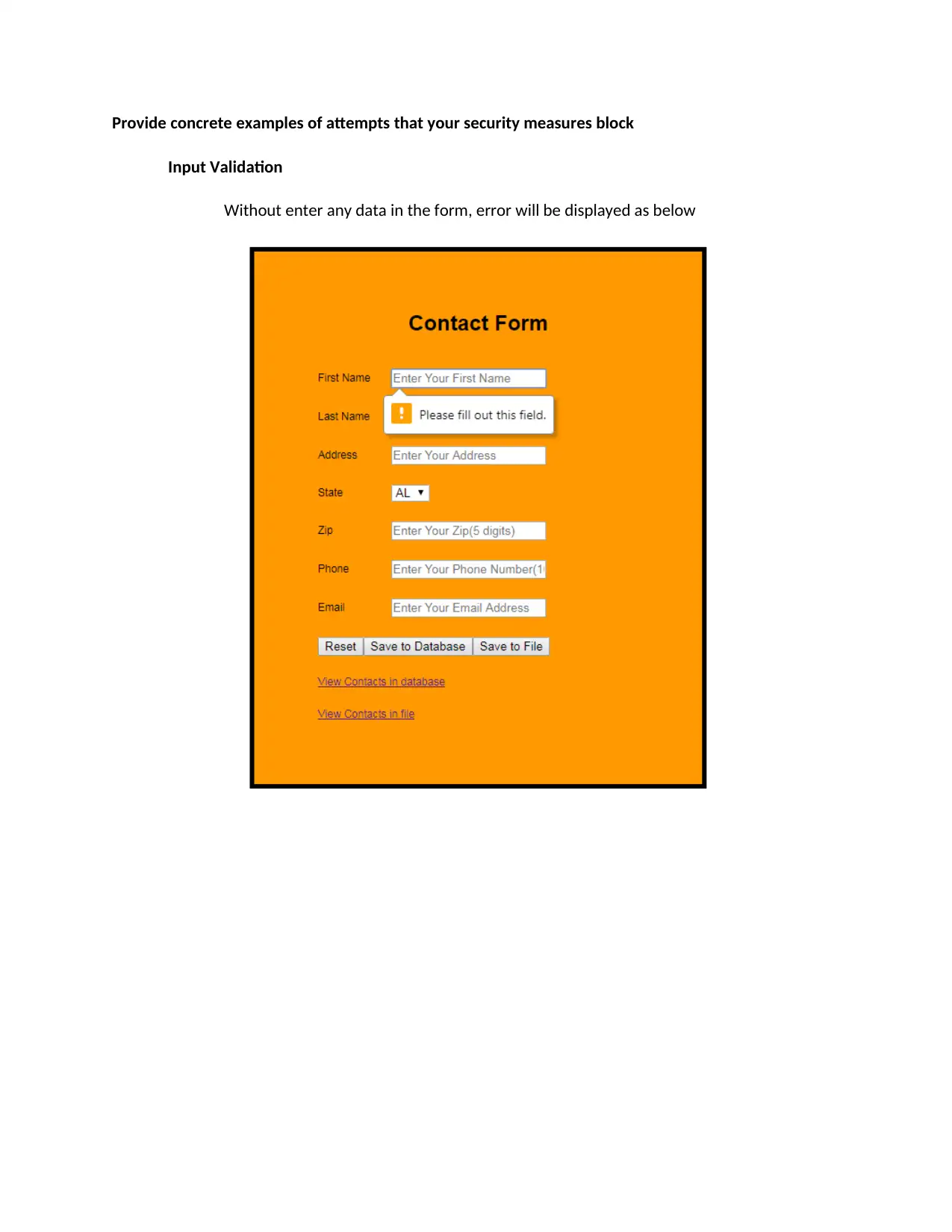
Provide concrete examples of attempts that your security measures block
Input Validation
Without enter any data in the form, error will be displayed as below
Input Validation
Without enter any data in the form, error will be displayed as below
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SQL injection using PDO
In our code, we used to insert the record using PDO based query execution. It does not execute
any injected query
Query:
$sql="insert into contact (FirstName,LastName,Address,State,Zip,Phone,Email) values
(:fname,:lname,:addr,:state,:zip,:phone,:email)";
$q=$dbconn->prepare($sql);
$res=$q-
>execute(array(':fname'=>$fname1,':lname'=>$lname1,':addr'=>$addr1,':state'=>$state1,':zip'=>
$zip1,':phone'=>$phone1,':email'=>$email1));
In our code, we used to insert the record using PDO based query execution. It does not execute
any injected query
Query:
$sql="insert into contact (FirstName,LastName,Address,State,Zip,Phone,Email) values
(:fname,:lname,:addr,:state,:zip,:phone,:email)";
$q=$dbconn->prepare($sql);
$res=$q-
>execute(array(':fname'=>$fname1,':lname'=>$lname1,':addr'=>$addr1,':state'=>$state1,':zip'=>
$zip1,':phone'=>$phone1,':email'=>$email1));

References
1. Prodromou, A. (2017, December 26). PHP Security Part 2: Directory Traversal & Code Injection.
Retrieved from https://www.acunetix.com/blog/articles/php-security-part-2-directory-traversal-
code-injection/
2. Fekete, G. (2013, October 29). Cross-Site Scripting Attacks (XSS). Retrieved from
https://www.sitepoint.com/php-security-cross-site-scripting-attacks-xss/
3. Shirey, D. (2013, August 20). PHP Master | Top 10 PHP Security Vulnerabilities. Retrieved from
https://www.sitepoint.com/top-10-php-security-vulnerabilities/
4. Qureshi, A. S. (2015, December 22). 6 Common PHP Security Issues And Their Remedies.
Retrieved from https://www.phpclasses.org/blog/post/338-6-Common-PHP-Security-Issues-
And-Their-Remedies.html
5. Sharma, S. (2014, May 08). 5 PHP Security Issues and What You Can do About Them? Retrieved
from https://www.templatemonster.com/blog/php-security-issues/
6. Muscat, I. (2017, April 24). What is Remote File Inclusion (RFI)? Retrieved from
https://www.acunetix.com/blog/articles/remote-file-inclusion-rfi/
1. Prodromou, A. (2017, December 26). PHP Security Part 2: Directory Traversal & Code Injection.
Retrieved from https://www.acunetix.com/blog/articles/php-security-part-2-directory-traversal-
code-injection/
2. Fekete, G. (2013, October 29). Cross-Site Scripting Attacks (XSS). Retrieved from
https://www.sitepoint.com/php-security-cross-site-scripting-attacks-xss/
3. Shirey, D. (2013, August 20). PHP Master | Top 10 PHP Security Vulnerabilities. Retrieved from
https://www.sitepoint.com/top-10-php-security-vulnerabilities/
4. Qureshi, A. S. (2015, December 22). 6 Common PHP Security Issues And Their Remedies.
Retrieved from https://www.phpclasses.org/blog/post/338-6-Common-PHP-Security-Issues-
And-Their-Remedies.html
5. Sharma, S. (2014, May 08). 5 PHP Security Issues and What You Can do About Them? Retrieved
from https://www.templatemonster.com/blog/php-security-issues/
6. Muscat, I. (2017, April 24). What is Remote File Inclusion (RFI)? Retrieved from
https://www.acunetix.com/blog/articles/remote-file-inclusion-rfi/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




