Comprehensive Report on Web Application Penetration Testing Techniques
VerifiedAdded on 2021/06/22
|13
|3328
|55
Report
AI Summary
This report provides a detailed analysis of web application penetration testing, encompassing various aspects such as methodologies, vulnerability assessments, and security recommendations. The report begins by outlining the process of penetration testing, including scoping, permission forms, and the role of skilled security experts. It delves into specific vulnerabilities like misconfigurations, cross-site scripting, injection attacks (SQL, NoSQL, LDAP, OS), and vulnerable components. The report further explores testing methodologies, differentiating between intrusive and non-intrusive techniques, and the use of vulnerability scanners like Nessus. It also discusses techniques for host and service discovery, including ICMP packets and DNS zone transfers. The report highlights the importance of tools like Bandit for Python security and the overall goal of automated vulnerability assessment. The report concludes with a discussion on the CVSS metric and its importance in vulnerability reporting, providing a comprehensive overview of web application security testing. The report also includes figures illustrating the vulnerable software versions and the issues of web penetrations.

WEB APPLICATION PENETRATION TESTING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1.........................................................................................................................................3
Task 2.........................................................................................................................................4
Task 3.........................................................................................................................................5
References list............................................................................................................................8
2
Task 1.........................................................................................................................................3
Task 2.........................................................................................................................................4
Task 3.........................................................................................................................................5
References list............................................................................................................................8
2

Task 1
It will work with you on a detailed understanding of your needs. However, for more
sophisticated setups we will require you to finish a scoping form, usually we can do a pretty
easy penetration test mostly on device. Once the breadth of your evaluation is established, our
strategy, work and prices will be outlined. We commit to provide the task and reserve it on
our calendar when you are delighted and financially authorized. Before testing we will need
to fill out and submit a Trial Permission Form also known as the Letter of Permission, which
will be officially authorized by your corporate representatives. Safety evaluation is both a
scientific and a collaborative activity (Alhassan et al, 2018). Our experts are all inventive,
skilled manual safety testing agents with a record of detecting the twig in the defence of a
program. This is supplemented by our solid rock safety tests performed, which are matched
with OWASP Secure Coding Guide, PERS, OWASP ASVS and OWASP Unified
Communications Manuals. A formal process assures constant assurance for all tasks and staff
members, while physical information security enables the analysts to behave like its an
adversary and to identify the defects that an ethical hacker could not possibly perform. It
classifies all the results throughout the appraisal meeting to make it simpler for our
consumers to pinpoint the fundamental cause and focus on their primary problem solution.
Well you will find 10, or twenty, or more if you identify one Sql injection inside a software.
The main problem might not be 20 distinct bugs, but a singular fault in one ORM component.
It helps our advisors, by grouping related information, to provide significant
recommendations on how to deal with problems. The report will be provided as a PDF by
email attachment based on the internal QA procedure. Methodology framework if you want
this analysis in other formats (Seng et al, 2017).
Possible risks linked with security vulnerabilities, listed according to each vulnerability's
NVD/CVSS base score. Under PCI DSS, an ASV and the hazards classified in the CVSS
outside security testing must take place. Skilled staff and risks classified in line with the risk
rating of the company as described in PCI DSS Condition 6.1 may do local penetration tests.
An external vulnerability scan from elsewhere in the targeted community is performed.
Within the target organisation, an internal safety is undertaken. The web page development
needs the process of making a good testing facility for user activity. Explanation of each
validated weakness and/or detected potential problem. Additional particular hazards,
3
It will work with you on a detailed understanding of your needs. However, for more
sophisticated setups we will require you to finish a scoping form, usually we can do a pretty
easy penetration test mostly on device. Once the breadth of your evaluation is established, our
strategy, work and prices will be outlined. We commit to provide the task and reserve it on
our calendar when you are delighted and financially authorized. Before testing we will need
to fill out and submit a Trial Permission Form also known as the Letter of Permission, which
will be officially authorized by your corporate representatives. Safety evaluation is both a
scientific and a collaborative activity (Alhassan et al, 2018). Our experts are all inventive,
skilled manual safety testing agents with a record of detecting the twig in the defence of a
program. This is supplemented by our solid rock safety tests performed, which are matched
with OWASP Secure Coding Guide, PERS, OWASP ASVS and OWASP Unified
Communications Manuals. A formal process assures constant assurance for all tasks and staff
members, while physical information security enables the analysts to behave like its an
adversary and to identify the defects that an ethical hacker could not possibly perform. It
classifies all the results throughout the appraisal meeting to make it simpler for our
consumers to pinpoint the fundamental cause and focus on their primary problem solution.
Well you will find 10, or twenty, or more if you identify one Sql injection inside a software.
The main problem might not be 20 distinct bugs, but a singular fault in one ORM component.
It helps our advisors, by grouping related information, to provide significant
recommendations on how to deal with problems. The report will be provided as a PDF by
email attachment based on the internal QA procedure. Methodology framework if you want
this analysis in other formats (Seng et al, 2017).
Possible risks linked with security vulnerabilities, listed according to each vulnerability's
NVD/CVSS base score. Under PCI DSS, an ASV and the hazards classified in the CVSS
outside security testing must take place. Skilled staff and risks classified in line with the risk
rating of the company as described in PCI DSS Condition 6.1 may do local penetration tests.
An external vulnerability scan from elsewhere in the targeted community is performed.
Within the target organisation, an internal safety is undertaken. The web page development
needs the process of making a good testing facility for user activity. Explanation of each
validated weakness and/or detected potential problem. Additional particular hazards,
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
particularly specific techniques of exploitation, may be presented by vulnerability. E.g.,
injections of SQL, privilege escalation, cross-site scripting or outdated are interfaces.
Instances of vulnerabilities comprise Depending on the severity of the experiment and the
environmental scale to be examined, commitments may span days or weeks. When attempts
find more breadth, assessments might rise in duration and complication. The security
management system and development of web page design will help to intricate the
application configuration system. The process of making good technological development
will help the process of systems (Nagpure, S. and Kurkure, S., 2017).
The exterior boundary of the CDE and also the important higher prevalence to or available to
public internet facilities is an exposing outside testing process. Any distinct connectivity from
corporate networks, especially programs is that has connectivity to single dedicated IP
addresses, should be assessed. Network architecture and physical network evaluations must
be included in the Assessment. Further testing for outside penetrations includes remote
management routes like telephone and VPN connectivity. The external security system will
make progress and develop connectivity to the system. The process of connecting the system
will help to develop a stable system in route management (Huang et al, 2017).
The range is the inner periphery of the CDE and important devices from an inner program's
view. Network architecture and network layer evaluations must be included in the Test
results. In which there is no inner CDE boundary and the CDE is perhaps the only inside
connection, the focus of the test is usually concentrated on key systems. For instance,
screening efforts may involve trying to defeat security processes of accessibility aimed at
preventing illegal access or usage by non-authorized processing and storing, handling or
sending CHD.
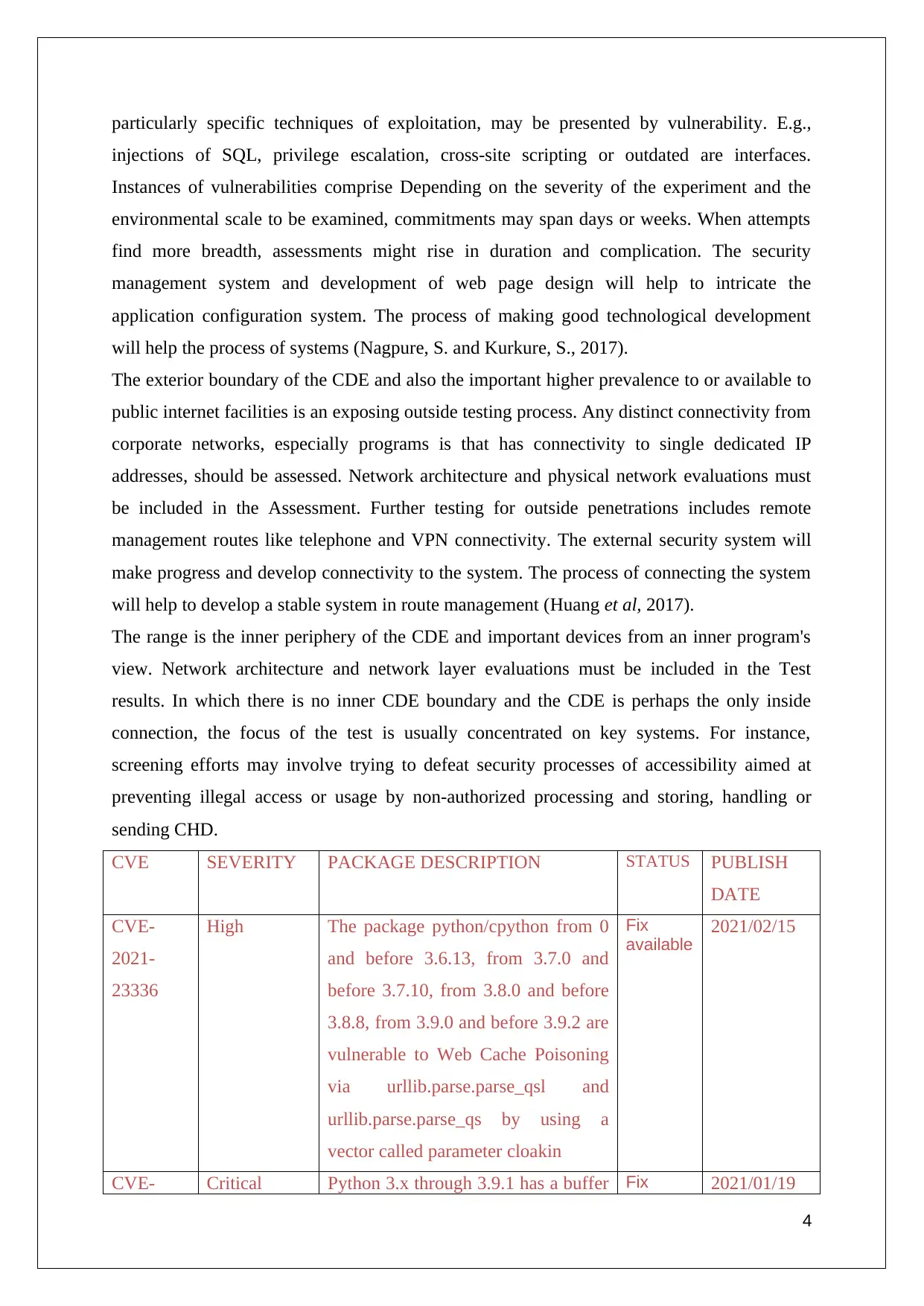
CVE SEVERITY PACKAGE DESCRIPTION STATUS PUBLISH
DATE
CVE-
2021-
23336
High The package python/cpython from 0
and before 3.6.13, from 3.7.0 and
before 3.7.10, from 3.8.0 and before
3.8.8, from 3.9.0 and before 3.9.2 are
vulnerable to Web Cache Poisoning
via urllib.parse.parse_qsl and
urllib.parse.parse_qs by using a
vector called parameter cloakin
Fix
available
2021/02/15
CVE- Critical Python 3.x through 3.9.1 has a buffer Fix 2021/01/19
4
injections of SQL, privilege escalation, cross-site scripting or outdated are interfaces.
Instances of vulnerabilities comprise Depending on the severity of the experiment and the
environmental scale to be examined, commitments may span days or weeks. When attempts
find more breadth, assessments might rise in duration and complication. The security
management system and development of web page design will help to intricate the
application configuration system. The process of making good technological development
will help the process of systems (Nagpure, S. and Kurkure, S., 2017).
The exterior boundary of the CDE and also the important higher prevalence to or available to
public internet facilities is an exposing outside testing process. Any distinct connectivity from
corporate networks, especially programs is that has connectivity to single dedicated IP
addresses, should be assessed. Network architecture and physical network evaluations must
be included in the Assessment. Further testing for outside penetrations includes remote
management routes like telephone and VPN connectivity. The external security system will
make progress and develop connectivity to the system. The process of connecting the system
will help to develop a stable system in route management (Huang et al, 2017).
The range is the inner periphery of the CDE and important devices from an inner program's
view. Network architecture and network layer evaluations must be included in the Test
results. In which there is no inner CDE boundary and the CDE is perhaps the only inside
connection, the focus of the test is usually concentrated on key systems. For instance,
screening efforts may involve trying to defeat security processes of accessibility aimed at
preventing illegal access or usage by non-authorized processing and storing, handling or
sending CHD.
CVE SEVERITY PACKAGE DESCRIPTION STATUS PUBLISH
DATE
CVE-
2021-
23336
High The package python/cpython from 0
and before 3.6.13, from 3.7.0 and
before 3.7.10, from 3.8.0 and before
3.8.8, from 3.9.0 and before 3.9.2 are
vulnerable to Web Cache Poisoning
via urllib.parse.parse_qsl and
urllib.parse.parse_qs by using a
vector called parameter cloakin
Fix
available
2021/02/15
CVE- Critical Python 3.x through 3.9.1 has a buffer Fix 2021/01/19
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
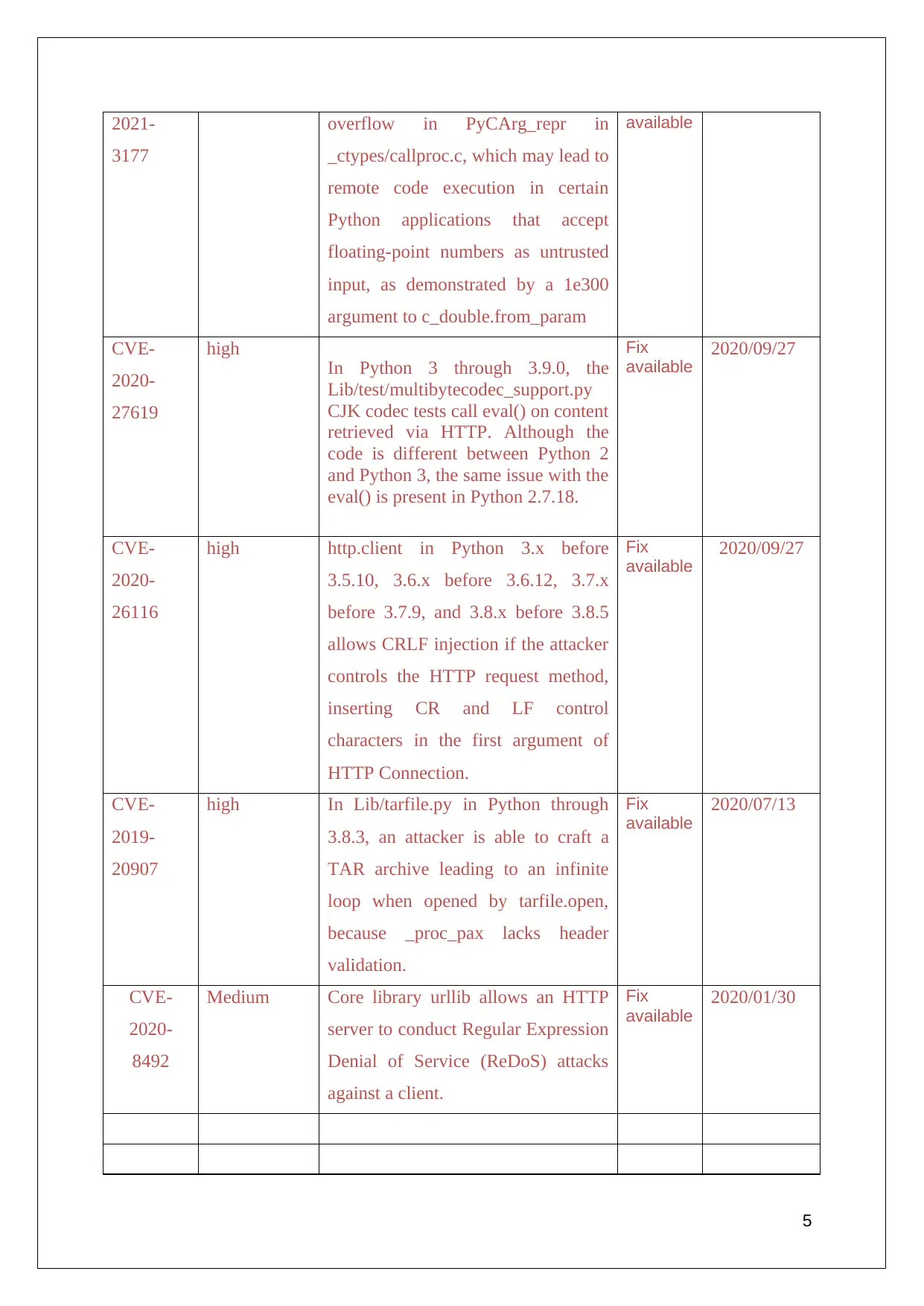
2021-
3177
overflow in PyCArg_repr in
_ctypes/callproc.c, which may lead to
remote code execution in certain
Python applications that accept
floating-point numbers as untrusted
input, as demonstrated by a 1e300
argument to c_double.from_param
available
CVE-
2020-
27619
high
In Python 3 through 3.9.0, the
Lib/test/multibytecodec_support.py
CJK codec tests call eval() on content
retrieved via HTTP. Although the
code is different between Python 2
and Python 3, the same issue with the
eval() is present in Python 2.7.18.
Fix
available
2020/09/27
CVE-
2020-
26116
high http.client in Python 3.x before
3.5.10, 3.6.x before 3.6.12, 3.7.x
before 3.7.9, and 3.8.x before 3.8.5
allows CRLF injection if the attacker
controls the HTTP request method,
inserting CR and LF control
characters in the first argument of
HTTP Connection.
Fix
available
2020/09/27
CVE-
2019-
20907
high In Lib/tarfile.py in Python through
3.8.3, an attacker is able to craft a
TAR archive leading to an infinite
loop when opened by tarfile.open,
because _proc_pax lacks header
validation.
Fix
available
2020/07/13
CVE-
2020-
8492
Medium Core library urllib allows an HTTP
server to conduct Regular Expression
Denial of Service (ReDoS) attacks
against a client.
Fix
available
2020/01/30
5
3177
overflow in PyCArg_repr in
_ctypes/callproc.c, which may lead to
remote code execution in certain
Python applications that accept
floating-point numbers as untrusted
input, as demonstrated by a 1e300
argument to c_double.from_param
available
CVE-
2020-
27619
high
In Python 3 through 3.9.0, the
Lib/test/multibytecodec_support.py
CJK codec tests call eval() on content
retrieved via HTTP. Although the
code is different between Python 2
and Python 3, the same issue with the
eval() is present in Python 2.7.18.
Fix
available
2020/09/27
CVE-
2020-
26116
high http.client in Python 3.x before
3.5.10, 3.6.x before 3.6.12, 3.7.x
before 3.7.9, and 3.8.x before 3.8.5
allows CRLF injection if the attacker
controls the HTTP request method,
inserting CR and LF control
characters in the first argument of
HTTP Connection.
Fix
available
2020/09/27
CVE-
2019-
20907
high In Lib/tarfile.py in Python through
3.8.3, an attacker is able to craft a
TAR archive leading to an infinite
loop when opened by tarfile.open,
because _proc_pax lacks header
validation.
Fix
available
2020/07/13
CVE-
2020-
8492
Medium Core library urllib allows an HTTP
server to conduct Regular Expression
Denial of Service (ReDoS) attacks
against a client.
Fix
available
2020/01/30
5
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

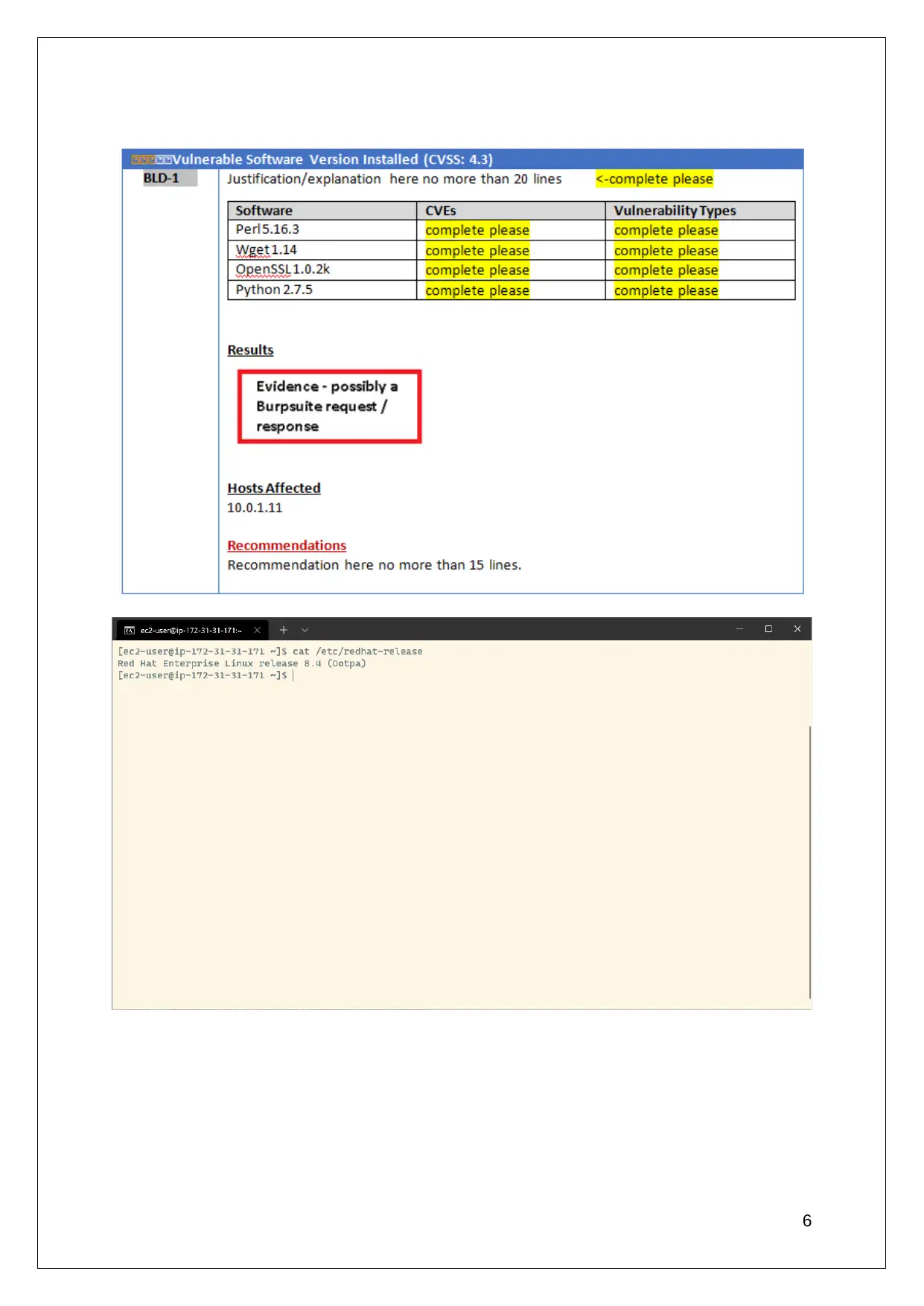
Figure 1: Vulnerable software version
(Source: Self-made)
Task 2
Misconfiguration of security:
This weakness is the most common online software that attacks field names and URLs.
Designers who cannot properly separate a web software's security settings and devices make
it sensitive for unauthorised access by malevolent users. The security system will help the
user to make proper connectivity to the system (Malekar, V. and Ghode, 2017).
Cross site scripting :
This fault occurs so each time something new official website includes untrustworthy data or
new features an existing user-driven home page through internet explorer APIs that allow
JavaScript or HTML to be generated. These issue scripts can be misused by threat hackers to
undertake such exercises as trying to hijack cookie sessions, disfacing sites, or rediriging
unsuspecting victories. The markup language is making the progress and connecting the
website development and home page settings (Kachhwaha, R. and Purohit, R., 2019).
Injection attack
The SQL, NoSQL, LDAP and OS objectives are. A problem develops if untrustworthy data
are forwarded as parts of a search or order to a translator. Cybercriminals can modify the
SQL declaration in the backend of an application and handle it in order to execute queries
that provide unauthorised data access. Another version is XML External Entities Injection
7
(Source: Self-made)
Task 2
Misconfiguration of security:
This weakness is the most common online software that attacks field names and URLs.
Designers who cannot properly separate a web software's security settings and devices make
it sensitive for unauthorised access by malevolent users. The security system will help the
user to make proper connectivity to the system (Malekar, V. and Ghode, 2017).
Cross site scripting :
This fault occurs so each time something new official website includes untrustworthy data or
new features an existing user-driven home page through internet explorer APIs that allow
JavaScript or HTML to be generated. These issue scripts can be misused by threat hackers to
undertake such exercises as trying to hijack cookie sessions, disfacing sites, or rediriging
unsuspecting victories. The markup language is making the progress and connecting the
website development and home page settings (Kachhwaha, R. and Purohit, R., 2019).
Injection attack
The SQL, NoSQL, LDAP and OS objectives are. A problem develops if untrustworthy data
are forwarded as parts of a search or order to a translator. Cybercriminals can modify the
SQL declaration in the backend of an application and handle it in order to execute queries
that provide unauthorised data access. Another version is XML External Entities Injection
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(XXE), which allows malicious actors to interrupt the management of XML data by a
Software system. You may then view the server's assets and log on to back technologies on
which the webpage is based. Script development and database management systems will
perform the activity of data protections and identify the unauthorized activity of the network
system (Sandhya et al, 2017).
Vulnerable Components:
This happens when programmers use obsolete, deprecated elements that are vulnerable to
online assaults. These susceptible elements enable hackers to hide the computer or plunder
important information of an organisation. For important data protection, most APIs and
online apps are unsuitable. Attackers may hijack or change the insufficiently guarded
information to conduct data theft, bankruptcy or other associated breaches. Your critical
information might be jeopardized without further information security.
Task 3
Check vulnerability is the search for known faults in known items. The transmitted traffic is
particularly targeted, requiring a lot of traffic alteration. Intrusive or non - intrusive tests can
be performed by a vulnerability scanner. An invasive test attempts to use the bug to destroy
or to modify the external target (Hasan et al, 2017). A non-intrusive examination attempts not
to damage the objective. The test normally involves verifying or verifying if weak settings
are activated. The distant edition of the application is typically, intrusive testing is far more
precise, but can clearly not be carried out in a production context. The way a vulnerability
scanner including Nessus attacks weaknesses varies from a penetrating program. A scanning
makes sure the fault is there, and does not compromise the system that is susceptible. An
invasive test, not a purpose, is a breakdown or deterioration of the services. Internet domains
can be discovered using ICMP packets to determine if particular hosts are supplied to the
system. Answers are received when ICMP capabilities are activated and barriers are not
disabled. The biggest problem with this strategy is that ping screening is unique to detect all
the hosts on the network. A different way of identifying host availability on the network
depends on accessible data such as DNS and tra c algorithms. DNS servers offer zoneffi
transfer capabilities to This is generally done between several DNS servers for the
transmission of Email account and user accounts Iist. For the threat detection technique, data
transmission might convey crucial facts. Include Interface, version and more characteristics
8
Software system. You may then view the server's assets and log on to back technologies on
which the webpage is based. Script development and database management systems will
perform the activity of data protections and identify the unauthorized activity of the network
system (Sandhya et al, 2017).
Vulnerable Components:
This happens when programmers use obsolete, deprecated elements that are vulnerable to
online assaults. These susceptible elements enable hackers to hide the computer or plunder
important information of an organisation. For important data protection, most APIs and
online apps are unsuitable. Attackers may hijack or change the insufficiently guarded
information to conduct data theft, bankruptcy or other associated breaches. Your critical
information might be jeopardized without further information security.
Task 3
Check vulnerability is the search for known faults in known items. The transmitted traffic is
particularly targeted, requiring a lot of traffic alteration. Intrusive or non - intrusive tests can
be performed by a vulnerability scanner. An invasive test attempts to use the bug to destroy
or to modify the external target (Hasan et al, 2017). A non-intrusive examination attempts not
to damage the objective. The test normally involves verifying or verifying if weak settings
are activated. The distant edition of the application is typically, intrusive testing is far more
precise, but can clearly not be carried out in a production context. The way a vulnerability
scanner including Nessus attacks weaknesses varies from a penetrating program. A scanning
makes sure the fault is there, and does not compromise the system that is susceptible. An
invasive test, not a purpose, is a breakdown or deterioration of the services. Internet domains
can be discovered using ICMP packets to determine if particular hosts are supplied to the
system. Answers are received when ICMP capabilities are activated and barriers are not
disabled. The biggest problem with this strategy is that ping screening is unique to detect all
the hosts on the network. A different way of identifying host availability on the network
depends on accessible data such as DNS and tra c algorithms. DNS servers offer zoneffi
transfer capabilities to This is generally done between several DNS servers for the
transmission of Email account and user accounts Iist. For the threat detection technique, data
transmission might convey crucial facts. Include Interface, version and more characteristics
8

from which even the computer system may be extrapolated in network layer and data (Casola
et al, 2018).
The usage of connected devices, particularly active monitoring approaches, does not involve
contact with a runtime environment. Nevertheless, there are various more issues that need to
be appropriately addressed. For example, it is vital to detect malware for the most potential
web servers from the sample location in the organization.
A scan using Bandit is an easy approach to identify security issues and to evaluate your
Python security position of your own Python code. Bandit is a project open source accessible
in the Python Packaging Index (PyPI). Bandit is a Python security tool that analyses and
creates a relevant abstract syntax tree for each .py file (AST). Bandit then runs many AST
plugins to identify typical security issues with software. For instance, a plugin may find out
whether you are running Flask with a True debug option.
Eventually, the objective of the technology described is to facilitate automated vulnerability
evaluation and weakness chains development. Possible assault roads are built on the basis of
knowledge collected in the previous rounds. Researchers take the vulnerability, requirements
and suggest alternatives into consideration in understanding the major business network
targets.
The building of vulnerable networks also creates substantial problems since before the
numbers of operating systems, e.g. several thousand hosts, may be quite high. In these cases,
due to the large number of potential combinations, the method might be confronted with a
phase implosion (Muñoz et al, 20158). Cross-Site Scripting, CSRF and several other issues
are accepted.
9
et al, 2018).
The usage of connected devices, particularly active monitoring approaches, does not involve
contact with a runtime environment. Nevertheless, there are various more issues that need to
be appropriately addressed. For example, it is vital to detect malware for the most potential
web servers from the sample location in the organization.
A scan using Bandit is an easy approach to identify security issues and to evaluate your
Python security position of your own Python code. Bandit is a project open source accessible
in the Python Packaging Index (PyPI). Bandit is a Python security tool that analyses and
creates a relevant abstract syntax tree for each .py file (AST). Bandit then runs many AST
plugins to identify typical security issues with software. For instance, a plugin may find out
whether you are running Flask with a True debug option.
Eventually, the objective of the technology described is to facilitate automated vulnerability
evaluation and weakness chains development. Possible assault roads are built on the basis of
knowledge collected in the previous rounds. Researchers take the vulnerability, requirements
and suggest alternatives into consideration in understanding the major business network
targets.
The building of vulnerable networks also creates substantial problems since before the
numbers of operating systems, e.g. several thousand hosts, may be quite high. In these cases,
due to the large number of potential combinations, the method might be confronted with a
phase implosion (Muñoz et al, 20158). Cross-Site Scripting, CSRF and several other issues
are accepted.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 2: Issue of Web penetrations
(Sources: Self-made)
It is currently one of the most prevalent vulnerabilities in online applications. We do not save
the PII, just the blurred screensaver following verification of the problem when notifying the
GDPR PII disclosure. The correct test method is innocuous and cannot destroy a webpage,
application, system or associated equipment (Al Shebli et al, 2018). We do not allow vulners
that damage a website, its data or the infrastructure layer or that are meant to damage it. Open
bug bounty forbids the publishing by system vulnerabilities and other automatic tooling of
bugs that have been found. The actual metric contained in the Standard Consider Factors
System is a crucial component of any vulnerability report (CVSS). This is a measuring
component of vulnerability that our technique uses in the evaluation of the vulnerability on
the system level.
The evaluation got the knowledge of a comparison between two and computing a method
vulnerability score based on the data given with the Shodan tool and special vulnerabilities.
For each service reported, Shodan provides Common Programme Enumerations (CPE). The
element is often used as identification if it provides complete data. In the next sections we
will test the execution of the strategy so that its effectiveness and probable shortcomings may
be assessed. We will next carry out a range of experiments to see how applicable the safety of
global computing devices today is to be improved. Preliminary findings for the development
of prototypes are shown in Fig. I. It can be observed that because of the capacity of Shodan to
10
(Sources: Self-made)
It is currently one of the most prevalent vulnerabilities in online applications. We do not save
the PII, just the blurred screensaver following verification of the problem when notifying the
GDPR PII disclosure. The correct test method is innocuous and cannot destroy a webpage,
application, system or associated equipment (Al Shebli et al, 2018). We do not allow vulners
that damage a website, its data or the infrastructure layer or that are meant to damage it. Open
bug bounty forbids the publishing by system vulnerabilities and other automatic tooling of
bugs that have been found. The actual metric contained in the Standard Consider Factors
System is a crucial component of any vulnerability report (CVSS). This is a measuring
component of vulnerability that our technique uses in the evaluation of the vulnerability on
the system level.
The evaluation got the knowledge of a comparison between two and computing a method
vulnerability score based on the data given with the Shodan tool and special vulnerabilities.
For each service reported, Shodan provides Common Programme Enumerations (CPE). The
element is often used as identification if it provides complete data. In the next sections we
will test the execution of the strategy so that its effectiveness and probable shortcomings may
be assessed. We will next carry out a range of experiments to see how applicable the safety of
global computing devices today is to be improved. Preliminary findings for the development
of prototypes are shown in Fig. I. It can be observed that because of the capacity of Shodan to
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

produce past data, old CPE names for distinct services may be automatically reconstructed.
We provided data for many FTP HTTPS and SNMP providers in this specific situation.
Organisation, for the purpose of protecting IT infrastructures, depended primarily on secure
socket security measures, such as barriers and network security. However, as many assaults
are directed at security defects of marketing and web programs, such as injection holes, the
traditional technique to defend online and user interface and users may not be effective. Ten
safety issues were also regarded as the main safety issues related with online applications
through the Project Management Body of Knowledge. These are frequent sorts of assaults
known to take place. To offer an assessment of the respective years of practise and expertise
is in present and historical vulnerabilities of websites and online applications. Vulnerability
of knowledge of users on the website and online program are all the aforementioned cyber
weaknesses were verified on the complainant's awareness. It's been overlooked 95% of 19 of
20 respondents examined had medium injection fault understanding and 60% represented 12
hard understanding respondents Verification broken down and administration of sessions
(Caraguay, 2021).
Safety malfunction got 90%, 18 out of 20 answers; it turned out that over 95% of these 18
persons had a concern with such weakness in one way or another. Of 20 respondents, 75
percent are susceptible to unauthorized access yet 16 of 20 being concerned about the lack of
level network management (Qasaimeh et al, 2018). Private data availability is also known in
16 of 20. Overturned and forward-looking redirects, Credential stuffing and Insecure Direct
Verses were among the 20 respondents, employing weaknesses such as forgeries for
command injection application (CSRF), employing modules with common problems. The
penetration testing revealed instructions on bloggers and IT specialists' levels of expertise on
contemporary and existing website/web program security fears. The vulnerabilities were
beneficial. It is necessary to be aware of these security challenges in order to enable answers
to acquire skills and knowledge the ways for combating these risks to security. The poll
found 47 percent of respondents on aggregate do not know much or no about at least one or
more weaknesses or the current website.
11
We provided data for many FTP HTTPS and SNMP providers in this specific situation.
Organisation, for the purpose of protecting IT infrastructures, depended primarily on secure
socket security measures, such as barriers and network security. However, as many assaults
are directed at security defects of marketing and web programs, such as injection holes, the
traditional technique to defend online and user interface and users may not be effective. Ten
safety issues were also regarded as the main safety issues related with online applications
through the Project Management Body of Knowledge. These are frequent sorts of assaults
known to take place. To offer an assessment of the respective years of practise and expertise
is in present and historical vulnerabilities of websites and online applications. Vulnerability
of knowledge of users on the website and online program are all the aforementioned cyber
weaknesses were verified on the complainant's awareness. It's been overlooked 95% of 19 of
20 respondents examined had medium injection fault understanding and 60% represented 12
hard understanding respondents Verification broken down and administration of sessions
(Caraguay, 2021).
Safety malfunction got 90%, 18 out of 20 answers; it turned out that over 95% of these 18
persons had a concern with such weakness in one way or another. Of 20 respondents, 75
percent are susceptible to unauthorized access yet 16 of 20 being concerned about the lack of
level network management (Qasaimeh et al, 2018). Private data availability is also known in
16 of 20. Overturned and forward-looking redirects, Credential stuffing and Insecure Direct
Verses were among the 20 respondents, employing weaknesses such as forgeries for
command injection application (CSRF), employing modules with common problems. The
penetration testing revealed instructions on bloggers and IT specialists' levels of expertise on
contemporary and existing website/web program security fears. The vulnerabilities were
beneficial. It is necessary to be aware of these security challenges in order to enable answers
to acquire skills and knowledge the ways for combating these risks to security. The poll
found 47 percent of respondents on aggregate do not know much or no about at least one or
more weaknesses or the current website.
11

References list
Journals
Alhassan, J.K., Misra, S., Umar, A., Maskeliūnas, R., Damaševičius, R. and Adewumi, A.,
2018, January. A fuzzy classifier-based penetration testing for web applications.
In International Conference on Information Technology & Systems (pp. 95-104). Springer,
Cham.
Seng, L.K., Ithnin, N. and Said, S.Z.M., 2018. The approaches to quantify web application
security scanners quality: a review. International Journal of Advanced Computer
Research, 8(38), pp.285-312.
Nagpure, S. and Kurkure, S., 2017, August. Vulnerability assessment and penetration testing
of Web application. In 2017 International Conference on Computing, Communication,
Control and Automation (ICCUBEA) (pp. 1-6). IEEE.
Huang, H.C., Zhang, Z.K., Cheng, H.W. and Shieh, S.W., 2017. Web application security:
threats, countermeasures, and pitfalls. Computer, 50(6), pp.81-85.
Kachhwaha, R. and Purohit, R., 2019. Relating vulnerability and security service points for
web application through penetration testing. In Progress in Advanced Computing and
Intelligent Engineering (pp. 41-51). Springer, Singapore.
Sandhya, S., Purkayastha, S., Joshua, E. and Deep, A., 2017, January. Assessment of website
security by penetration testing using Wireshark. In 2017 4th International Conference on
Advanced Computing and Communication Systems (ICACCS) (pp. 1-4). IEEE.
Malekar, V. and Ghode, S., A Review on Vulnerability Assessment and Penetration Testing
Open Source Tools for Web Application Security.
Hasan, A.M., Meva, D.T., Roy, A.K. and Doshi, J., 2017, December. Perusal of web
application security approach. In 2017 International Conference on Intelligent
Communication and Computational Techniques (ICCT) (pp. 90-95). IEEE.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Muñoz, F.R., Vega, E.A.A. and Villalba, L.J.G., 2018. Analyzing the traffic of penetration
testing tools with an IDS. The Journal of Supercomputing, 74(12), pp.6454-6469.
12
Journals
Alhassan, J.K., Misra, S., Umar, A., Maskeliūnas, R., Damaševičius, R. and Adewumi, A.,
2018, January. A fuzzy classifier-based penetration testing for web applications.
In International Conference on Information Technology & Systems (pp. 95-104). Springer,
Cham.
Seng, L.K., Ithnin, N. and Said, S.Z.M., 2018. The approaches to quantify web application
security scanners quality: a review. International Journal of Advanced Computer
Research, 8(38), pp.285-312.
Nagpure, S. and Kurkure, S., 2017, August. Vulnerability assessment and penetration testing
of Web application. In 2017 International Conference on Computing, Communication,
Control and Automation (ICCUBEA) (pp. 1-6). IEEE.
Huang, H.C., Zhang, Z.K., Cheng, H.W. and Shieh, S.W., 2017. Web application security:
threats, countermeasures, and pitfalls. Computer, 50(6), pp.81-85.
Kachhwaha, R. and Purohit, R., 2019. Relating vulnerability and security service points for
web application through penetration testing. In Progress in Advanced Computing and
Intelligent Engineering (pp. 41-51). Springer, Singapore.
Sandhya, S., Purkayastha, S., Joshua, E. and Deep, A., 2017, January. Assessment of website
security by penetration testing using Wireshark. In 2017 4th International Conference on
Advanced Computing and Communication Systems (ICACCS) (pp. 1-4). IEEE.
Malekar, V. and Ghode, S., A Review on Vulnerability Assessment and Penetration Testing
Open Source Tools for Web Application Security.
Hasan, A.M., Meva, D.T., Roy, A.K. and Doshi, J., 2017, December. Perusal of web
application security approach. In 2017 International Conference on Intelligent
Communication and Computational Techniques (ICCT) (pp. 90-95). IEEE.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Muñoz, F.R., Vega, E.A.A. and Villalba, L.J.G., 2018. Analyzing the traffic of penetration
testing tools with an IDS. The Journal of Supercomputing, 74(12), pp.6454-6469.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
