Comprehensive Evaluation of WAN Security Issues and Performance
VerifiedAdded on 2019/12/03
|13
|4149
|230
Report
AI Summary
This report provides an in-depth evaluation of Wide Area Network (WAN) security issues and performance, focusing on technologies like Dynamic Multipoint Virtual Private Network (DMVPN). The study aims to understand WAN concepts, identify security challenges such as unauthorized access and data theft, and explore strategies to mitigate these risks. The research methodology includes both primary data collection from IT employees at organizations like HP, Defcon, and Cisco, and secondary data analysis through literature review. The report examines various WAN technologies, including DMVPN, MPLS, VPN, and Frame Relay, and uses tools like PRTG Monitoring to measure network performance. The findings highlight the importance of establishing robust security systems and developing effective security strategies to balance WAN security and performance, ensuring data protection and efficient network operations. The report also includes a case study of Blue Ridge Networks to illustrate practical applications of WAN security principles.

Evaluation of the WAN security issues and
performance
performance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
1. ABSTRACT.................................................................................................................................1
2. INTRODUCTION.......................................................................................................................1
Background of the study..............................................................................................................2
3. AIM AND OBJECTIVES............................................................................................................3
4. TECHNOLOGIES AND STRATEGIES FOR SECURING WIDE AREA NETWORKS.........4
5. METHOD AND WORK PLAN..................................................................................................6
Milestone.....................................................................................................................................7
Prototype approach:.....................................................................................................................7
Research ethics............................................................................................................................8
Significance of the research.........................................................................................................9
Limitations...................................................................................................................................9
REFERENCES..............................................................................................................................10
1. ABSTRACT.................................................................................................................................1
2. INTRODUCTION.......................................................................................................................1
Background of the study..............................................................................................................2
3. AIM AND OBJECTIVES............................................................................................................3
4. TECHNOLOGIES AND STRATEGIES FOR SECURING WIDE AREA NETWORKS.........4
5. METHOD AND WORK PLAN..................................................................................................6
Milestone.....................................................................................................................................7
Prototype approach:.....................................................................................................................7
Research ethics............................................................................................................................8
Significance of the research.........................................................................................................9
Limitations...................................................................................................................................9
REFERENCES..............................................................................................................................10

1. ABSTRACT
Wide Area Network (WAN) plays an important role in terms of providing support to a
wide range of applications within wide geographical area. However, along with several
advantages some security and performance related issues are also associated with the
implementation and used of WAN technologies such as, Dynamic Multipoint Virtual Private
Network (DMVN). The main aim of the research proposal is to explore the wide area network
security issues and policies to overcome those issues effectively. In the context of carrying out
the present study, researcher will need both primary and secondary data collection techniques.
Primary data will be collected from 100 IT employees of HP, Defcon and Cisco organizations in
order to know their perceptions about wide area network security issues and ways through which
such kinds of issues can be controlled and overcome in an appropriate manner.
On the other side, for collecting secondary data, researcher can be conducted review of
literature method in which studies done by similar topic can be considered to better understand
WAN concept and principles of its implementation. Along with this, prototyping model can be
employed to break down the entire project into smaller tasks and sub-tasks so that each and
activity of present project will be executed in stipulated time. At the end of the proposal,
researcher will be able to identify security and performance measurement associates with DMVN
technology and its implementation at workplace. Along with this, investigator would be able to
measure impact of security factor on organizations and users who are using WAN technologies in
their day to day business operations.
Keywords: Dynamic Multipoint Virtual Private Network (DMVN), WAN, security and
performance measures.
2. INTRODUCTION
In the modern era, most of the organizations are emphasizing on using wide area network
for communicating large geographically area. This network may be privately owned or rented
but generally it is used with public (shared user) networks. Today’s many employees are working
outside from remote locations or different branches throughout the world. They are using WAN
because it provides facility of easy access of data and applications resources to a large corporate
user population in an appropriate manner (Alizadeh and et.al., 2015). However, along with
several advantages several security issues such as unauthorized use, information theft, and
malicious damage to files etc. are also associated with its use. These kinds of network
1
Wide Area Network (WAN) plays an important role in terms of providing support to a
wide range of applications within wide geographical area. However, along with several
advantages some security and performance related issues are also associated with the
implementation and used of WAN technologies such as, Dynamic Multipoint Virtual Private
Network (DMVN). The main aim of the research proposal is to explore the wide area network
security issues and policies to overcome those issues effectively. In the context of carrying out
the present study, researcher will need both primary and secondary data collection techniques.
Primary data will be collected from 100 IT employees of HP, Defcon and Cisco organizations in
order to know their perceptions about wide area network security issues and ways through which
such kinds of issues can be controlled and overcome in an appropriate manner.
On the other side, for collecting secondary data, researcher can be conducted review of
literature method in which studies done by similar topic can be considered to better understand
WAN concept and principles of its implementation. Along with this, prototyping model can be
employed to break down the entire project into smaller tasks and sub-tasks so that each and
activity of present project will be executed in stipulated time. At the end of the proposal,
researcher will be able to identify security and performance measurement associates with DMVN
technology and its implementation at workplace. Along with this, investigator would be able to
measure impact of security factor on organizations and users who are using WAN technologies in
their day to day business operations.
Keywords: Dynamic Multipoint Virtual Private Network (DMVN), WAN, security and
performance measures.
2. INTRODUCTION
In the modern era, most of the organizations are emphasizing on using wide area network
for communicating large geographically area. This network may be privately owned or rented
but generally it is used with public (shared user) networks. Today’s many employees are working
outside from remote locations or different branches throughout the world. They are using WAN
because it provides facility of easy access of data and applications resources to a large corporate
user population in an appropriate manner (Alizadeh and et.al., 2015). However, along with
several advantages several security issues such as unauthorized use, information theft, and
malicious damage to files etc. are also associated with its use. These kinds of network
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

optimization and security threats are creating challenges for organizations across the world. In
such kind of critical situation, it is essential for network department of any firm to make right
balance between WAN security and performance issues by using adequate security measures and
strategies. In this regard, companies must establish a good security system and develop a security
strategy to overcome these types of security problems in a proper manner. Retailers spent a
significant ($25 million+) amount of money every year for the purpose of security their Wide
area network. Along with this, cost of the WAN circuits, operational costs, centralized
administration and traffic handling for different applications kinds of costs and challenges are
associated with the implementation of wide area network for different applications. For the
purpose of dynamic creation of virtual Private IP tunnels, enterprises are using Dynamic
Multipoint Virtual Private Network (Iskander, Trainor and Chrysanthis, 2014). For the storage of
their data in a quick, secure and distributed manner, management of companies is emphasizing
on use DMVN technology. For the purpose of attaining aim and objectives, researcher can
collect secondary data related to understand development and implementation of WAN security
measures. In this regard, study conducted by different authors will be considered (Liang, Qin and
Wan, 2014). By considering convergence duration, traffic sent, throughput and queuing factors,
performance of DMVN which is one type of WAN technology can be considered.
Background of the study
WAN has a capability to capture multiple distance areas and multiple smaller networks.
In addition, by using this network companies can grow as needed to cover multiple cities. Using
packet switching and circuit switching technologies, a set of switches and routers are
interconnected to form a WAN to share resources among different branches of companies at
different locations effectively. Besides that, it provides facility of share application software
resources (files, printers and modem) and allows electronic communication among users.
In digital era, most of company's proprietary information traverses wide area network but
most of enterprises wrongly assumed that they do not need to address security and network
management issues in order to protect their network. In the context of protecting information, it
is necessary for companies to establish strong security system before an intruder or any kinds of
security threats occur (Iskander, Trainor and Chrysanthis, 2014). For the purpose of
understanding WAN security threats and performance measurements, present study has been
conducted by the researcher.
2
such kind of critical situation, it is essential for network department of any firm to make right
balance between WAN security and performance issues by using adequate security measures and
strategies. In this regard, companies must establish a good security system and develop a security
strategy to overcome these types of security problems in a proper manner. Retailers spent a
significant ($25 million+) amount of money every year for the purpose of security their Wide
area network. Along with this, cost of the WAN circuits, operational costs, centralized
administration and traffic handling for different applications kinds of costs and challenges are
associated with the implementation of wide area network for different applications. For the
purpose of dynamic creation of virtual Private IP tunnels, enterprises are using Dynamic
Multipoint Virtual Private Network (Iskander, Trainor and Chrysanthis, 2014). For the storage of
their data in a quick, secure and distributed manner, management of companies is emphasizing
on use DMVN technology. For the purpose of attaining aim and objectives, researcher can
collect secondary data related to understand development and implementation of WAN security
measures. In this regard, study conducted by different authors will be considered (Liang, Qin and
Wan, 2014). By considering convergence duration, traffic sent, throughput and queuing factors,
performance of DMVN which is one type of WAN technology can be considered.
Background of the study
WAN has a capability to capture multiple distance areas and multiple smaller networks.
In addition, by using this network companies can grow as needed to cover multiple cities. Using
packet switching and circuit switching technologies, a set of switches and routers are
interconnected to form a WAN to share resources among different branches of companies at
different locations effectively. Besides that, it provides facility of share application software
resources (files, printers and modem) and allows electronic communication among users.
In digital era, most of company's proprietary information traverses wide area network but
most of enterprises wrongly assumed that they do not need to address security and network
management issues in order to protect their network. In the context of protecting information, it
is necessary for companies to establish strong security system before an intruder or any kinds of
security threats occur (Iskander, Trainor and Chrysanthis, 2014). For the purpose of
understanding WAN security threats and performance measurements, present study has been
conducted by the researcher.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The present topic is beneficial from stakeholder’s perspectives because it ensures that
their personal information and resources sharing process are secured while using wide area
network. However, stakeholder’s views and their acceptance regarding to conduct this proposal
can create issue to complete this project within the stipulated time. But after clearly understand
them about WAN security principles and network security policies and guidelines to overcome
security related issues, they will also support present project (Pei, Chen and Wan, 2014). The
present research is related to previous studies which are done by other researchers regarding to
measure performance of WAN.
Retail companies are tending increasingly to use Dynamic Multipoint Virtual Private
Network kind of wide area network technology in order to establish fast moving of digital
communications among different branches to communicate with each other securely through a
public shared infrastructure. It provides a full meshed connection between multiple sites and no
extra configuration is required for this (Anees and Zeilinger, 2014). By selecting this topic for
the research, investigator would be able to assess risks and implement effective security
measures to enhance security of Wide area network. In order to better understand the WAN
related security issues, case study of Blue Ridge Networks will be taken. Enterprise offers fast,
secure, high performing WAN services to its customers and government authorities at reasonable
price. Most of the retailers are using services of this company to carry out different business
activities such as data from special pricing or inventory sites, human resources and share
application software etc.
Access control broadband internet access, cloud-based security and VPN are the
techniques which are offered by Blue Ridge Networks to its client companies. Moreover, high-
speed, secure support of multiple environments, protection of POS devices, managed WAN
services and so on are the major characteristics of services which are provided by company.
However, when enterprise went online then centralized firewall whitelisting, security threats and
network intrusion kinds of challenges were raised (Wan, Wang and Shi, 2014). But after
following WAN technologies implementation principles, management of the company was able
to solve security and performance related issues faced by the organization.
3. AIM AND OBJECTIVES
Aim: The main aim of the study is to evaluate WAN security issues and performance.
Objectives:
3
their personal information and resources sharing process are secured while using wide area
network. However, stakeholder’s views and their acceptance regarding to conduct this proposal
can create issue to complete this project within the stipulated time. But after clearly understand
them about WAN security principles and network security policies and guidelines to overcome
security related issues, they will also support present project (Pei, Chen and Wan, 2014). The
present research is related to previous studies which are done by other researchers regarding to
measure performance of WAN.
Retail companies are tending increasingly to use Dynamic Multipoint Virtual Private
Network kind of wide area network technology in order to establish fast moving of digital
communications among different branches to communicate with each other securely through a
public shared infrastructure. It provides a full meshed connection between multiple sites and no
extra configuration is required for this (Anees and Zeilinger, 2014). By selecting this topic for
the research, investigator would be able to assess risks and implement effective security
measures to enhance security of Wide area network. In order to better understand the WAN
related security issues, case study of Blue Ridge Networks will be taken. Enterprise offers fast,
secure, high performing WAN services to its customers and government authorities at reasonable
price. Most of the retailers are using services of this company to carry out different business
activities such as data from special pricing or inventory sites, human resources and share
application software etc.
Access control broadband internet access, cloud-based security and VPN are the
techniques which are offered by Blue Ridge Networks to its client companies. Moreover, high-
speed, secure support of multiple environments, protection of POS devices, managed WAN
services and so on are the major characteristics of services which are provided by company.
However, when enterprise went online then centralized firewall whitelisting, security threats and
network intrusion kinds of challenges were raised (Wan, Wang and Shi, 2014). But after
following WAN technologies implementation principles, management of the company was able
to solve security and performance related issues faced by the organization.
3. AIM AND OBJECTIVES
Aim: The main aim of the study is to evaluate WAN security issues and performance.
Objectives:
3

To understand WAN concept and principles of its implementation
To explore the wide area network security issues and policies to overcome security
related issues
To develop and implement WAN security strategy with considering effective security
measure
To evaluate the ways and strategies in order to overcome WAN security issues
Research questions
What is WAN concept and basic terminology of wide area network regarding its
implementation at large geographical area?
How wide area network security policies and guidelines can help companies in reducing
security related issues?
How WAN security strategies can be implemented for effective security measure of
network?
What are the main strategies and ways through which wide area network related issues
can be solved in a proper manner?
For completing the aim and objectives of current research proposal, researcher will be
required 7 months’ time period. The objectives which are framed by investigator are specific and
realistic. These are measurable in terms of producing outcomes and solutions to overcome
network security related issues. In the context of attaining research objectives, researcher can use
secondary data collection methods or literature review method. In this regard, books, journals,
research papers and online published articles can be used (Tzang, Chang and Tzang, 2015).
Besides that, primary data can be collected from different organizations to understand their
perspectives about implementation of wide area network security policies and guidelines to
overcome security related issues in a significant manner.
4. TECHNOLOGIES AND STRATEGIES FOR SECURING WIDE AREA
NETWORKS
Technologies used in WAN are based on the international standard organization (ISO)
model network architecture. Network administrator can evaluate all shared resources which can
be accessed through the network on the basis of access controls and developing a WAN security
strategy based on current or future products or technology. The main reason behind selecting
technique is to determine what needs to be secured, and from whom (Wan, Canedo and Faruque,
4
To explore the wide area network security issues and policies to overcome security
related issues
To develop and implement WAN security strategy with considering effective security
measure
To evaluate the ways and strategies in order to overcome WAN security issues
Research questions
What is WAN concept and basic terminology of wide area network regarding its
implementation at large geographical area?
How wide area network security policies and guidelines can help companies in reducing
security related issues?
How WAN security strategies can be implemented for effective security measure of
network?
What are the main strategies and ways through which wide area network related issues
can be solved in a proper manner?
For completing the aim and objectives of current research proposal, researcher will be
required 7 months’ time period. The objectives which are framed by investigator are specific and
realistic. These are measurable in terms of producing outcomes and solutions to overcome
network security related issues. In the context of attaining research objectives, researcher can use
secondary data collection methods or literature review method. In this regard, books, journals,
research papers and online published articles can be used (Tzang, Chang and Tzang, 2015).
Besides that, primary data can be collected from different organizations to understand their
perspectives about implementation of wide area network security policies and guidelines to
overcome security related issues in a significant manner.
4. TECHNOLOGIES AND STRATEGIES FOR SECURING WIDE AREA
NETWORKS
Technologies used in WAN are based on the international standard organization (ISO)
model network architecture. Network administrator can evaluate all shared resources which can
be accessed through the network on the basis of access controls and developing a WAN security
strategy based on current or future products or technology. The main reason behind selecting
technique is to determine what needs to be secured, and from whom (Wan, Canedo and Faruque,
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2015). Data will come from both primary and secondary sources to attain aim and objectives of
present study in a proper manner.
Secondary data: As per the present study, technologies will be selected on the basis of comfort
levels and perceived threats to status. It is the responsibility to network administrator to consider
time factor and contentious activity in implementing a security policy at workplace. WAN
technologies including Dynamic Multipoint Virtual Private Network (DMVPN), Multiprotocol
Label Switching (MPLS), VPN and Frame Relay are the generally used by organizations to share
information to wide geographical area. For creating VPNs in a very easy manner, DMVPN wide
area network technology can be used (Kostiuk and Shunfenthal, 2015). As per the present case,
Dynamic Multipoint Virtual Private Network which is one type of WAN technology will be used
to describe security, and performance factors associated with it implementation. In order to
measure performance of this network, hub and spoke topology will be required.
For the purpose of measuring time, PRTG Monitoring tool can be used because it will
help researcher to measure minimum, maximum and convergence time of packet. In addition,
performance of this network will be measured in term of faster convergence protocols used in
network designed. Besides that, for securing the IP traffic from one site to other site, DMVPN
will use IPsec. The main reasons behind selecting this tool for measuring security and
performance are end to end security with encryption and hashing. In addition, for hashing
purpose Advance Encryption Standard (AES) and Secure Hash algorithm -1(SHA-1) can be
used. As per the given case scenario, in order to measure secondary data collection method can
be collected regarding to measure security and performance of Dynamic Multipoint Virtual
Private Network (DMVPN) in a significant manner (Xia, Kantarcioglu and Malin, 2015).
Primary data: In the context of conducting present research, researcher will need different types
of technologies and resources such as secondary sources (books, journals, online published
articles and research papers related to similar area) and primary data collection from respondents
of HP, Defcon and Cisco organizations. In this regard, data can be collected from 100
respondents on the basis of their availability and interest. In order to analyze the primary data
collected from respondents, statistical software package for social science (SPSS) can be used.
Besides that, purposive or judgment sampling technique can be employed in the context of
selecting sample size from large population regarding to attain aim and objectives of present
research in a proper manner.
5
present study in a proper manner.
Secondary data: As per the present study, technologies will be selected on the basis of comfort
levels and perceived threats to status. It is the responsibility to network administrator to consider
time factor and contentious activity in implementing a security policy at workplace. WAN
technologies including Dynamic Multipoint Virtual Private Network (DMVPN), Multiprotocol
Label Switching (MPLS), VPN and Frame Relay are the generally used by organizations to share
information to wide geographical area. For creating VPNs in a very easy manner, DMVPN wide
area network technology can be used (Kostiuk and Shunfenthal, 2015). As per the present case,
Dynamic Multipoint Virtual Private Network which is one type of WAN technology will be used
to describe security, and performance factors associated with it implementation. In order to
measure performance of this network, hub and spoke topology will be required.
For the purpose of measuring time, PRTG Monitoring tool can be used because it will
help researcher to measure minimum, maximum and convergence time of packet. In addition,
performance of this network will be measured in term of faster convergence protocols used in
network designed. Besides that, for securing the IP traffic from one site to other site, DMVPN
will use IPsec. The main reasons behind selecting this tool for measuring security and
performance are end to end security with encryption and hashing. In addition, for hashing
purpose Advance Encryption Standard (AES) and Secure Hash algorithm -1(SHA-1) can be
used. As per the given case scenario, in order to measure secondary data collection method can
be collected regarding to measure security and performance of Dynamic Multipoint Virtual
Private Network (DMVPN) in a significant manner (Xia, Kantarcioglu and Malin, 2015).
Primary data: In the context of conducting present research, researcher will need different types
of technologies and resources such as secondary sources (books, journals, online published
articles and research papers related to similar area) and primary data collection from respondents
of HP, Defcon and Cisco organizations. In this regard, data can be collected from 100
respondents on the basis of their availability and interest. In order to analyze the primary data
collected from respondents, statistical software package for social science (SPSS) can be used.
Besides that, purposive or judgment sampling technique can be employed in the context of
selecting sample size from large population regarding to attain aim and objectives of present
research in a proper manner.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
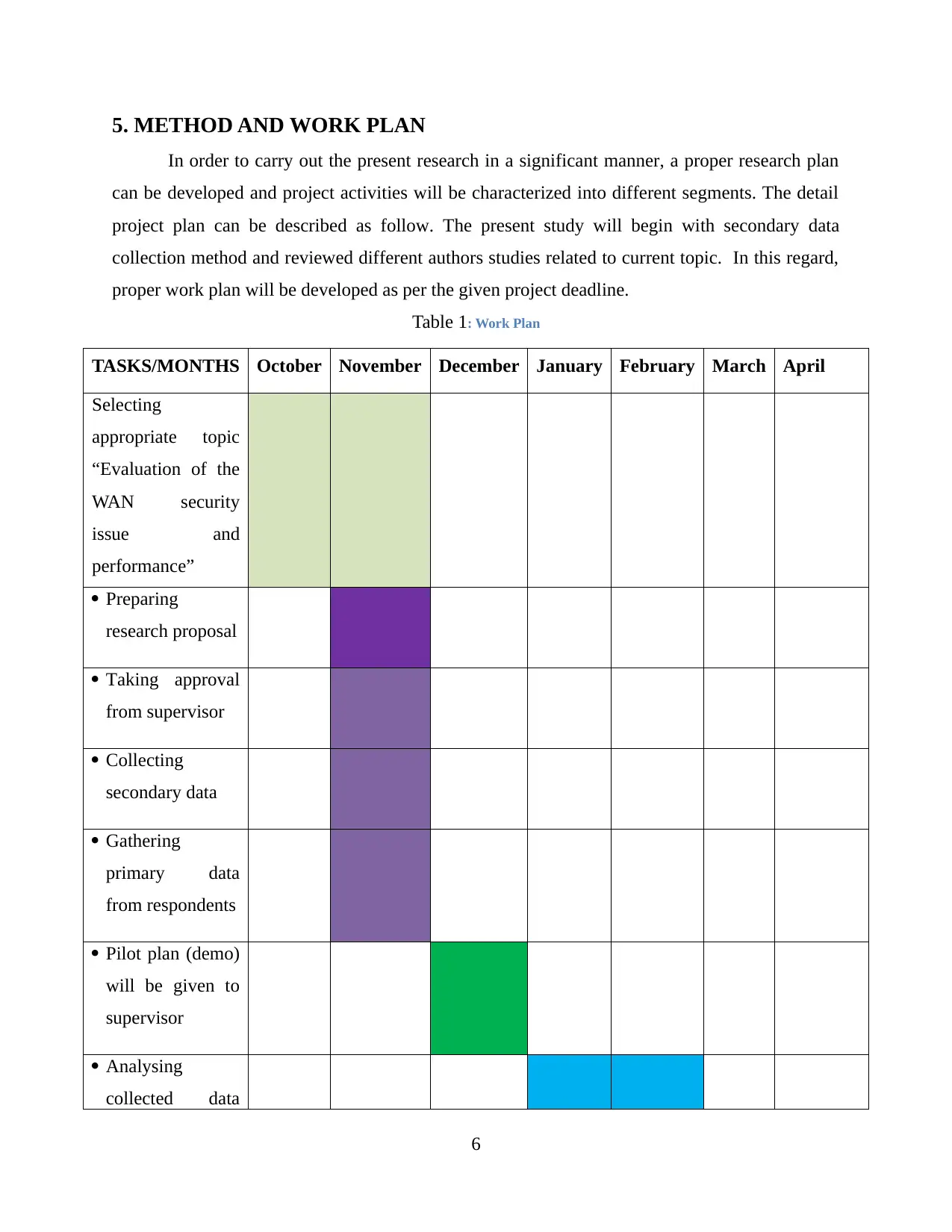
5. METHOD AND WORK PLAN
In order to carry out the present research in a significant manner, a proper research plan
can be developed and project activities will be characterized into different segments. The detail
project plan can be described as follow. The present study will begin with secondary data
collection method and reviewed different authors studies related to current topic. In this regard,
proper work plan will be developed as per the given project deadline.
Table 1: Work Plan
TASKS/MONTHS October November December January February March April
Selecting
appropriate topic
“Evaluation of the
WAN security
issue and
performance”
Preparing
research proposal
Taking approval
from supervisor
Collecting
secondary data
Gathering
primary data
from respondents
Pilot plan (demo)
will be given to
supervisor
Analysing
collected data
6
In order to carry out the present research in a significant manner, a proper research plan
can be developed and project activities will be characterized into different segments. The detail
project plan can be described as follow. The present study will begin with secondary data
collection method and reviewed different authors studies related to current topic. In this regard,
proper work plan will be developed as per the given project deadline.
Table 1: Work Plan
TASKS/MONTHS October November December January February March April
Selecting
appropriate topic
“Evaluation of the
WAN security
issue and
performance”
Preparing
research proposal
Taking approval
from supervisor
Collecting
secondary data
Gathering
primary data
from respondents
Pilot plan (demo)
will be given to
supervisor
Analysing
collected data
6
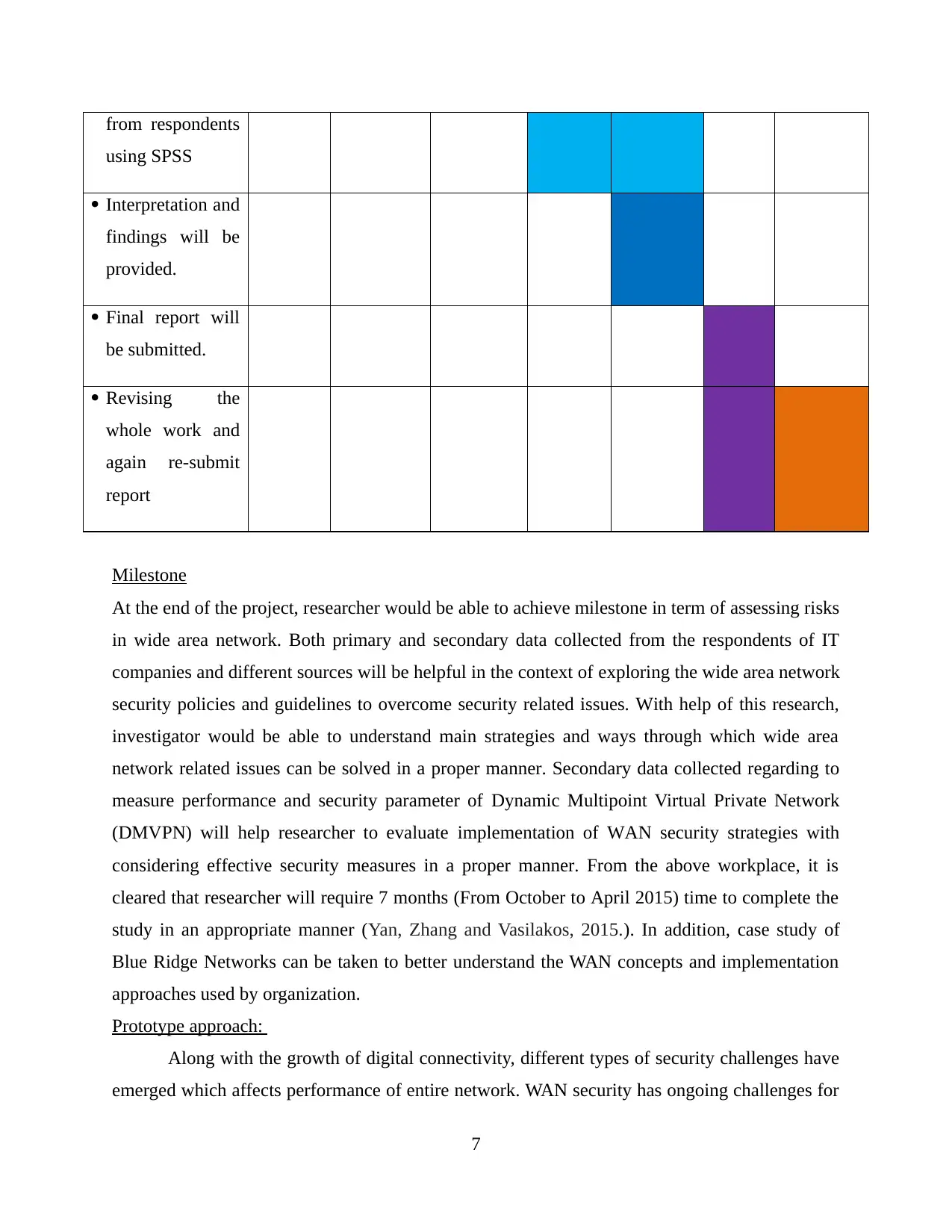
from respondents
using SPSS
Interpretation and
findings will be
provided.
Final report will
be submitted.
Revising the
whole work and
again re-submit
report
Milestone
At the end of the project, researcher would be able to achieve milestone in term of assessing risks
in wide area network. Both primary and secondary data collected from the respondents of IT
companies and different sources will be helpful in the context of exploring the wide area network
security policies and guidelines to overcome security related issues. With help of this research,
investigator would be able to understand main strategies and ways through which wide area
network related issues can be solved in a proper manner. Secondary data collected regarding to
measure performance and security parameter of Dynamic Multipoint Virtual Private Network
(DMVPN) will help researcher to evaluate implementation of WAN security strategies with
considering effective security measures in a proper manner. From the above workplace, it is
cleared that researcher will require 7 months (From October to April 2015) time to complete the
study in an appropriate manner (Yan, Zhang and Vasilakos, 2015.). In addition, case study of
Blue Ridge Networks can be taken to better understand the WAN concepts and implementation
approaches used by organization.
Prototype approach:
Along with the growth of digital connectivity, different types of security challenges have
emerged which affects performance of entire network. WAN security has ongoing challenges for
7
using SPSS
Interpretation and
findings will be
provided.
Final report will
be submitted.
Revising the
whole work and
again re-submit
report
Milestone
At the end of the project, researcher would be able to achieve milestone in term of assessing risks
in wide area network. Both primary and secondary data collected from the respondents of IT
companies and different sources will be helpful in the context of exploring the wide area network
security policies and guidelines to overcome security related issues. With help of this research,
investigator would be able to understand main strategies and ways through which wide area
network related issues can be solved in a proper manner. Secondary data collected regarding to
measure performance and security parameter of Dynamic Multipoint Virtual Private Network
(DMVPN) will help researcher to evaluate implementation of WAN security strategies with
considering effective security measures in a proper manner. From the above workplace, it is
cleared that researcher will require 7 months (From October to April 2015) time to complete the
study in an appropriate manner (Yan, Zhang and Vasilakos, 2015.). In addition, case study of
Blue Ridge Networks can be taken to better understand the WAN concepts and implementation
approaches used by organization.
Prototype approach:
Along with the growth of digital connectivity, different types of security challenges have
emerged which affects performance of entire network. WAN security has ongoing challenges for
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

service providers and users because fear of infringement of personal data for criminal activities is
associated with the use of taking services while using wide area network (Trubiani, Koziolek
and Happe, 2015.). As per the present case concern, prototyping approach can be used. This
approach will be taken because it provides opportunity to researcher to break project into smaller
tasks to see realistic-looking results long before the final project completion. Prototype model
will begin with secondary data collection method in which studies conducted by WAN
technologies and security measures will be taken. After this step, researcher will prepare
questionnaire to reach IT respondents in order to know their perceptions about wide area network
terminologies and techniques such as Dynamic Multipoint Virtual Private Network and security
issues associated with it (Bahnasse and Kamoun, 2015). Further, different security measures such
as storage controls, data encryption, callback systems, public- and private-key security and
network operating systems with built-in security features will be discussed. At the end, wide area
network security policies have been considered to establish a secure WAN environment for all
connected departments, offices and individuals.
Based on the currently known requirements and data available regarding to WAN security
measure, prototype will be developed. This model will help investigator to better understand the
WAN concept and basic terminology of wide area network regarding to its implementation at
large geographical area. In order to implement this approach, researcher will follow different
stages such as requirement gathering, quick design, build prototype, evaluate respondents
perspectives about security concerns and refine projects as per the responses provided by
respondents and secondary data available related to same topic. Due to limited time period, this
model will be used (Kaur and Gurm, 2015). It will provide facility of identifying missing
information quickly and errors can be detected much earlier. Planning will be done before start
the project. In this regard, feasibility study and basic requirement to measure WAN security
measures will be considered. The main reason behind using this process is to ensure clients that
the end users constantly work with the system.
Research ethics
In term of maintaining reliability and validity of entire research, prior permission from
ethical committee and supervisor can be considered. Besides that, prior permission from
Faculty's Research Ethics Committee will be taken in order to conduct research in a significant
manner. In addition, quality and security issues and their impact on organizations which are
8
associated with the use of taking services while using wide area network (Trubiani, Koziolek
and Happe, 2015.). As per the present case concern, prototyping approach can be used. This
approach will be taken because it provides opportunity to researcher to break project into smaller
tasks to see realistic-looking results long before the final project completion. Prototype model
will begin with secondary data collection method in which studies conducted by WAN
technologies and security measures will be taken. After this step, researcher will prepare
questionnaire to reach IT respondents in order to know their perceptions about wide area network
terminologies and techniques such as Dynamic Multipoint Virtual Private Network and security
issues associated with it (Bahnasse and Kamoun, 2015). Further, different security measures such
as storage controls, data encryption, callback systems, public- and private-key security and
network operating systems with built-in security features will be discussed. At the end, wide area
network security policies have been considered to establish a secure WAN environment for all
connected departments, offices and individuals.
Based on the currently known requirements and data available regarding to WAN security
measure, prototype will be developed. This model will help investigator to better understand the
WAN concept and basic terminology of wide area network regarding to its implementation at
large geographical area. In order to implement this approach, researcher will follow different
stages such as requirement gathering, quick design, build prototype, evaluate respondents
perspectives about security concerns and refine projects as per the responses provided by
respondents and secondary data available related to same topic. Due to limited time period, this
model will be used (Kaur and Gurm, 2015). It will provide facility of identifying missing
information quickly and errors can be detected much earlier. Planning will be done before start
the project. In this regard, feasibility study and basic requirement to measure WAN security
measures will be considered. The main reason behind using this process is to ensure clients that
the end users constantly work with the system.
Research ethics
In term of maintaining reliability and validity of entire research, prior permission from
ethical committee and supervisor can be considered. Besides that, prior permission from
Faculty's Research Ethics Committee will be taken in order to conduct research in a significant
manner. In addition, quality and security issues and their impact on organizations which are
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

facing security and performance related issues in their wide area network will be considered to
conduct the research project in a significant manner (Wide Area Network Security Policy, n.d).
Along with taking permission from Faculty's Research Ethics Committee, prior permission from
IT companies’ respondents will also be taken in order to know their availability and interest to
give answer of research questions in a proper manner. In the context of measuring reliability of
data, SPSS tool can be employed by researcher (Powell, 2011). Despite of that, all guidelines
framed by university and plagiarism criteria will be followed to reduce chance of ambiguity,
reliability and quality related issues in a significant manner.
Significance of the research
The present research proposal will be beneficial for organizations in terms of
understanding WAN technologies and principles of wide area network implementation in
dynamic changing era. Through conducting this study, researcher will be able to develop WAN
security framework to reduce security and other kinds of challenges associated with the
implementation of this large geographic network (Zhang, 2009). Students and scholars would be
able to better understand the concept of WAN and strategies required for reducing issues
associated with the use of wide area network technologies at different locations in a significant
manner.
Limitations
Time and cost are the major constraints that are associated with the evaluation of the
WAN security issues and performance. In order to carry out the present study, researcher mainly
focuses on secondary data collection method in which results and findings of other authors
related to similar area will be included in the present research. Besides that, due to high cost of
technologies used in WAN security measures and performance, researcher will consider
secondary data collection or review literature method for measuring security and performance of
WAN technologies such as Dynamic Multipoint Virtual Private Network. On the other side,
primary data will be collected from IT companies’ employees and this task will take time. Hence,
these are the major limitations of the present study.
9
conduct the research project in a significant manner (Wide Area Network Security Policy, n.d).
Along with taking permission from Faculty's Research Ethics Committee, prior permission from
IT companies’ respondents will also be taken in order to know their availability and interest to
give answer of research questions in a proper manner. In the context of measuring reliability of
data, SPSS tool can be employed by researcher (Powell, 2011). Despite of that, all guidelines
framed by university and plagiarism criteria will be followed to reduce chance of ambiguity,
reliability and quality related issues in a significant manner.
Significance of the research
The present research proposal will be beneficial for organizations in terms of
understanding WAN technologies and principles of wide area network implementation in
dynamic changing era. Through conducting this study, researcher will be able to develop WAN
security framework to reduce security and other kinds of challenges associated with the
implementation of this large geographic network (Zhang, 2009). Students and scholars would be
able to better understand the concept of WAN and strategies required for reducing issues
associated with the use of wide area network technologies at different locations in a significant
manner.
Limitations
Time and cost are the major constraints that are associated with the evaluation of the
WAN security issues and performance. In order to carry out the present study, researcher mainly
focuses on secondary data collection method in which results and findings of other authors
related to similar area will be included in the present research. Besides that, due to high cost of
technologies used in WAN security measures and performance, researcher will consider
secondary data collection or review literature method for measuring security and performance of
WAN technologies such as Dynamic Multipoint Virtual Private Network. On the other side,
primary data will be collected from IT companies’ employees and this task will take time. Hence,
these are the major limitations of the present study.
9

REFERENCES
Books and Journals
Alizadeh, M. and et.al., 2015. Security and Privacy Criteria to Evaluate Authentication
Mechanisms in Proxy Mobile IPv6. Jurnal Teknologi.72(5).
Anees, T. and Zeilinger, H., 2014. Performance evaluation of a service availability model. IEEE.
pp. 115-120
Hossain, M., Fotouhi, M. and Hasan, R., 2015. Towards an Analysis of Security Issues,
Challenges, and Open Problems in the Internet of Things. IEEE. pp. 21-28.
Ijemaru, G. K., and et.al., 2015. Evaluating the Challenging Issues in the Security of Wireless
Communication Networks in Nigeria.
Iskander, M. K., Trainor, T. and Chrysanthis, P. K., 2014. Balancing Performance, Accuracy, and
Precision for Secure Cloud Transactions. Parallel and Distributed Systems, IEEE
Transactions on. 25(2).pp. 417-426.
Kostiuk, P. F. and Shunfenthal, M., 2015. Architecture Development for Shadow Mode
Assessments of Air Traffic Management Technologies. In AIAA Modeling and Simulation
Technologies Conference. pp. 2797.
Liang, X., Qin, J. and Wan, J., 2014. An Effective and Secure Epidemic Routing for Disruption-
Tolerant Networks. IEEE. pp. 329-333.
Pei, B., Chen, C.and Wan, C., 2014. Key management for outsourced data security. Wuhan
University Journal of Natural Sciences. 19(5).pp. 449-454.
Trubiani, C., Koziolek, A. and Happe, L. , 2015. Exploiting Software Performance Engineering
Techniques to Optimise the Quality of Smart Grid Environments. pp. 199-202.
Tzang, Y. J., Chang, H. Y. and Tzang, C. H., 2015. Enhancing the performance and security
against media‐access‐control table overflow vulnerability attacks. Security and
Communication Networks. 8(9). Pp.1780-1793.
Wan, J., Canedo, A. and Faruque, M. A. A., 2015. Security-Aware Functional Modeling of
Cyber-Physical Systems. ETFA'15.
Wan, Z., Wang, G. and Shi, S., 2014. SKM: Scalable Key Management for Advanced Metering
Infrastructure in Smart Grids. Industrial Electronics, IEEE Transactions. 61(12).
pp.7055-7066.
Xia, W., Kantarcioglu, M. and Malin, B., 2015. Process-Driven Data Privacy. ACM. pp. 1021-
10
Books and Journals
Alizadeh, M. and et.al., 2015. Security and Privacy Criteria to Evaluate Authentication
Mechanisms in Proxy Mobile IPv6. Jurnal Teknologi.72(5).
Anees, T. and Zeilinger, H., 2014. Performance evaluation of a service availability model. IEEE.
pp. 115-120
Hossain, M., Fotouhi, M. and Hasan, R., 2015. Towards an Analysis of Security Issues,
Challenges, and Open Problems in the Internet of Things. IEEE. pp. 21-28.
Ijemaru, G. K., and et.al., 2015. Evaluating the Challenging Issues in the Security of Wireless
Communication Networks in Nigeria.
Iskander, M. K., Trainor, T. and Chrysanthis, P. K., 2014. Balancing Performance, Accuracy, and
Precision for Secure Cloud Transactions. Parallel and Distributed Systems, IEEE
Transactions on. 25(2).pp. 417-426.
Kostiuk, P. F. and Shunfenthal, M., 2015. Architecture Development for Shadow Mode
Assessments of Air Traffic Management Technologies. In AIAA Modeling and Simulation
Technologies Conference. pp. 2797.
Liang, X., Qin, J. and Wan, J., 2014. An Effective and Secure Epidemic Routing for Disruption-
Tolerant Networks. IEEE. pp. 329-333.
Pei, B., Chen, C.and Wan, C., 2014. Key management for outsourced data security. Wuhan
University Journal of Natural Sciences. 19(5).pp. 449-454.
Trubiani, C., Koziolek, A. and Happe, L. , 2015. Exploiting Software Performance Engineering
Techniques to Optimise the Quality of Smart Grid Environments. pp. 199-202.
Tzang, Y. J., Chang, H. Y. and Tzang, C. H., 2015. Enhancing the performance and security
against media‐access‐control table overflow vulnerability attacks. Security and
Communication Networks. 8(9). Pp.1780-1793.
Wan, J., Canedo, A. and Faruque, M. A. A., 2015. Security-Aware Functional Modeling of
Cyber-Physical Systems. ETFA'15.
Wan, Z., Wang, G. and Shi, S., 2014. SKM: Scalable Key Management for Advanced Metering
Infrastructure in Smart Grids. Industrial Electronics, IEEE Transactions. 61(12).
pp.7055-7066.
Xia, W., Kantarcioglu, M. and Malin, B., 2015. Process-Driven Data Privacy. ACM. pp. 1021-
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





