Wireless Communication Advances Report - Energy Harvesting, Telestra
VerifiedAdded on 2020/03/28
|10
|1400
|94
Report
AI Summary
This report delves into various aspects of wireless communication, starting with an analysis of WiMax (IEEE 802.16) networks, comparing data encryption standards like 3DES, AES, and RSA. It then explores Wireless Personal Area Networks (WPANs), specifically Bluetooth and ZigBee, discussing their security challenges. The report further examines energy harvesting techniques for wireless sensor networks, highlighting their importance for sustainable and efficient operation, particularly in the context of the Internet of Things. Finally, it presents a case study of Telestra, a company implementing cellular digital cellular handsets to enhance field service operations, detailing the features and benefits of this technology over traditional notebook computers, including improved customer service, data loss reduction, and increased mobility for service technicians. The report is a valuable resource for understanding the latest trends and practical applications in wireless communication.

Running head: WIRELESS COMMUNICATION ADVANCES 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS COMMUNICATION ADVANCES 2
Task 1
WiMax (Worldwide Interoperability for Microwave Access) networks are wireless
communication standards established on IEEE 802.16 technologies that enable the transfer of
broadband wireless access (Kucharzewski & Kotulski, 2008). WiMax provides point to point
and point to multipoint applications enabling large area coverage compared to WiFi IEEE
802.11 standards. WiMAX uses strong encryption algorithms for data privacy and
confidentiality including Advanced Encryption Standard (AES), Triple DES (3DES), and
asymmetric Rivest, Shamir, Adleman (RSA) algorithms (Singh & Supriya, 2013). Table 1
below shows a summary of similarities and differences between these WiMax data
encryption standards.
Factors Triple DES (3DES) Advanced
Encryption
Standard (AES)
RSA
Algorithm Symmetric key Symmetric key Asymmetric key
Year of
Development
1978 2000 1978
Key Length 112, 118 bits 128, 192, 256 bits Varies depending
on number of bits in
the modulus n where
n=p*q
Type of Cipher Block cipher Block cipher Asymmetric block
cipher
Block Size 64 bits 128 bits Variable
Round 48 10,12, 14 1
Speed Slow Fast Slowest
Security Good security Exceptional security Low security
Table 1: Comparison between 3DES, AES and RSA Encryption Standards
Task 1
WiMax (Worldwide Interoperability for Microwave Access) networks are wireless
communication standards established on IEEE 802.16 technologies that enable the transfer of
broadband wireless access (Kucharzewski & Kotulski, 2008). WiMax provides point to point
and point to multipoint applications enabling large area coverage compared to WiFi IEEE
802.11 standards. WiMAX uses strong encryption algorithms for data privacy and
confidentiality including Advanced Encryption Standard (AES), Triple DES (3DES), and
asymmetric Rivest, Shamir, Adleman (RSA) algorithms (Singh & Supriya, 2013). Table 1
below shows a summary of similarities and differences between these WiMax data
encryption standards.
Factors Triple DES (3DES) Advanced
Encryption
Standard (AES)
RSA
Algorithm Symmetric key Symmetric key Asymmetric key
Year of
Development
1978 2000 1978
Key Length 112, 118 bits 128, 192, 256 bits Varies depending
on number of bits in
the modulus n where
n=p*q
Type of Cipher Block cipher Block cipher Asymmetric block
cipher
Block Size 64 bits 128 bits Variable
Round 48 10,12, 14 1
Speed Slow Fast Slowest
Security Good security Exceptional security Low security
Table 1: Comparison between 3DES, AES and RSA Encryption Standards
WIRELESS COMMUNICATION ADVANCES 3
Task 2
A wireless personal area network (WPAN) is a wireless communication standard that
connects devices in close proximity for data transfer. Two of the most widely WPAN
technologies include Bluetooth and ZigBee.
1. Bluetooth
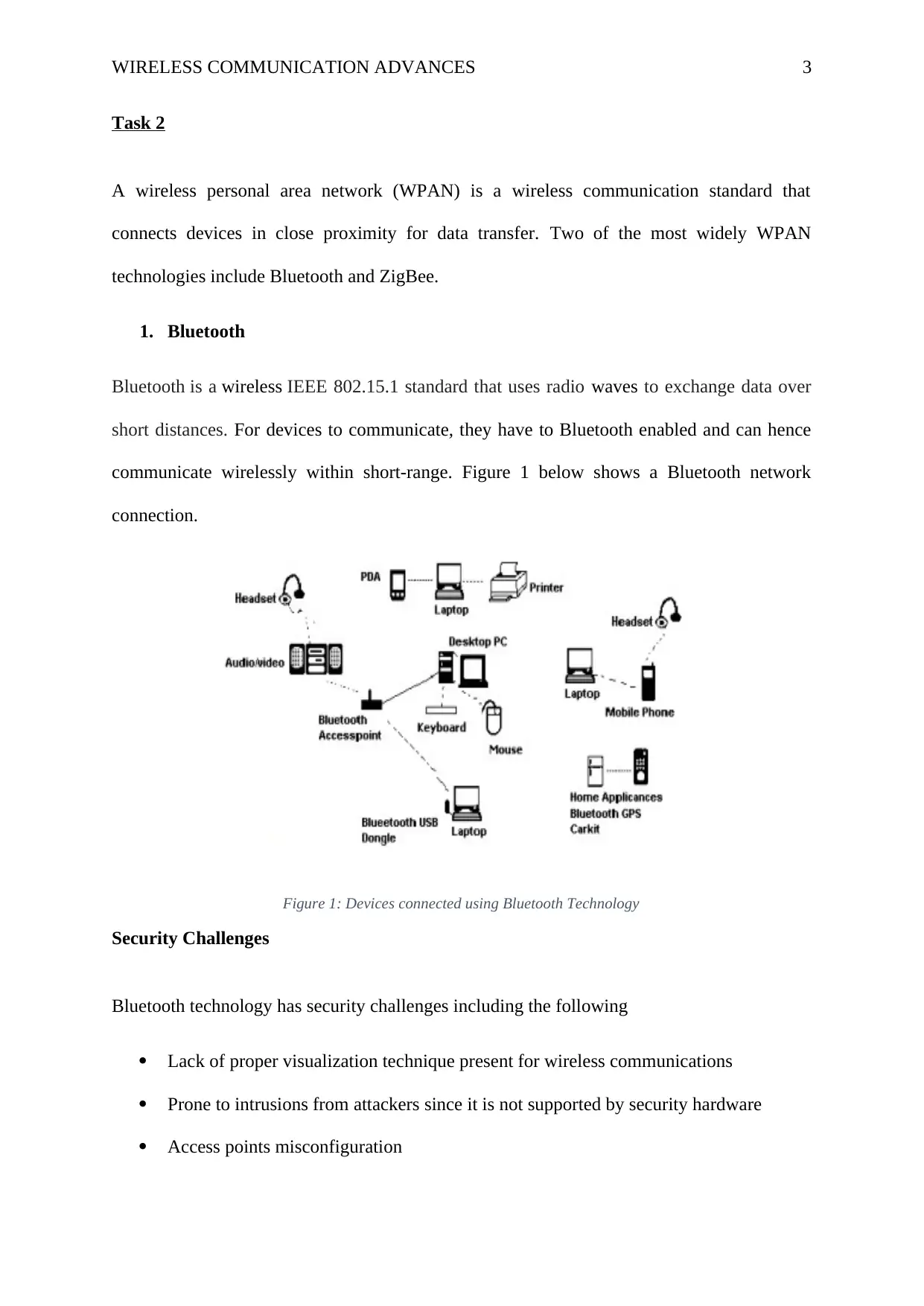
Bluetooth is a wireless IEEE 802.15.1 standard that uses radio waves to exchange data over
short distances. For devices to communicate, they have to Bluetooth enabled and can hence
communicate wirelessly within short-range. Figure 1 below shows a Bluetooth network
connection.
Figure 1: Devices connected using Bluetooth Technology
Security Challenges
Bluetooth technology has security challenges including the following
Lack of proper visualization technique present for wireless communications
Prone to intrusions from attackers since it is not supported by security hardware
Access points misconfiguration
Task 2
A wireless personal area network (WPAN) is a wireless communication standard that
connects devices in close proximity for data transfer. Two of the most widely WPAN
technologies include Bluetooth and ZigBee.
1. Bluetooth
Bluetooth is a wireless IEEE 802.15.1 standard that uses radio waves to exchange data over
short distances. For devices to communicate, they have to Bluetooth enabled and can hence
communicate wirelessly within short-range. Figure 1 below shows a Bluetooth network
connection.
Figure 1: Devices connected using Bluetooth Technology
Security Challenges
Bluetooth technology has security challenges including the following
Lack of proper visualization technique present for wireless communications
Prone to intrusions from attackers since it is not supported by security hardware
Access points misconfiguration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS COMMUNICATION ADVANCES 4
Lack of network management because of mobility
Implementation of weak encryption standards
2. ZigBee
ZigBee approach is an IEEE 802.15.4 wireless standard for creating personal area network
connections that do not require a lot of power and bandwidth consumption. Applications
include devices for medical data collection, wireless light switches, home energy device
monitors, traffic systems, and other network devices that only require short distance wireless
data transmission. Figure 2 shows devices connected using ZigBee technology.
Figure 2: Devices connected with Zigbee Technology
Security Challenges
Some of the security issues facing Wireless Personal Area Networks according to (Kashif,
2011) include
ZigBee is an emerging technology and therefore security mechanisms are not well
implemented
Lack of network management because of mobility
Implementation of weak encryption standards
2. ZigBee
ZigBee approach is an IEEE 802.15.4 wireless standard for creating personal area network
connections that do not require a lot of power and bandwidth consumption. Applications
include devices for medical data collection, wireless light switches, home energy device
monitors, traffic systems, and other network devices that only require short distance wireless
data transmission. Figure 2 shows devices connected using ZigBee technology.
Figure 2: Devices connected with Zigbee Technology
Security Challenges
Some of the security issues facing Wireless Personal Area Networks according to (Kashif,
2011) include
ZigBee is an emerging technology and therefore security mechanisms are not well
implemented
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS COMMUNICATION ADVANCES 5
ZigBee networks that don’t use proper encryption standards are prone to network
sniffing where attackers can collect sensitive network information
Denial of service attacks can easily affect ZigBee network performance
Easy to tamper with ZigBee network devices since they are not supported by
hardware infrastructure
Task 3
Energy harvesting is a technique used to generate energy for wireless sensor networks either,
from their ambient sources and external source in order to provide an interruptible power
supply for the network or some of its nodes. With technology advancing daily including the
Internet of Things, energy harvesting is therefore very essential. The Internet of Things
technology requires that connected devices be in a constant supply of power for sustainability
and efficiency. It is easy to maintain and supply indoor wireless sensor networks with power,
however it is not easy to guarantee constant power supply for outdoor sensor networks. They
are limited in terms of sensor node power supply which lead to their breakdown. It is
therefore important to harvest energy for their sustainability and perpetual operation.
Firstly, wireless sensor networks are projected to greatly advance in the coming years. This is
because of the advancing technologies that need to use their infrastructure like previously
mentioned. For such technologies to be effective, they will be required to be continuously
efficient. For this to happen, they need constant power supply and hence the importance of
harvesting energy from the surrounding.
Secondly, certain situations and circumstances necessitate the setting up of wireless sensor
networks for example, networks to monitor and sense forest fires or networks to monitor
flooded areas as well as networks that need to be set in remote areas that have no
ZigBee networks that don’t use proper encryption standards are prone to network
sniffing where attackers can collect sensitive network information
Denial of service attacks can easily affect ZigBee network performance
Easy to tamper with ZigBee network devices since they are not supported by
hardware infrastructure
Task 3
Energy harvesting is a technique used to generate energy for wireless sensor networks either,
from their ambient sources and external source in order to provide an interruptible power
supply for the network or some of its nodes. With technology advancing daily including the
Internet of Things, energy harvesting is therefore very essential. The Internet of Things
technology requires that connected devices be in a constant supply of power for sustainability
and efficiency. It is easy to maintain and supply indoor wireless sensor networks with power,
however it is not easy to guarantee constant power supply for outdoor sensor networks. They
are limited in terms of sensor node power supply which lead to their breakdown. It is
therefore important to harvest energy for their sustainability and perpetual operation.
Firstly, wireless sensor networks are projected to greatly advance in the coming years. This is
because of the advancing technologies that need to use their infrastructure like previously
mentioned. For such technologies to be effective, they will be required to be continuously
efficient. For this to happen, they need constant power supply and hence the importance of
harvesting energy from the surrounding.
Secondly, certain situations and circumstances necessitate the setting up of wireless sensor
networks for example, networks to monitor and sense forest fires or networks to monitor
flooded areas as well as networks that need to be set in remote areas that have no

WIRELESS COMMUNICATION ADVANCES 6
infrastructure. It is important to ensure that in such cases, network efficiency is maintained.
Energy harvesting would also ensure that emergency networks can be set to solve issues and
not fail by lacking energy or power to sustain.
Finally, applications that require to survive for long require constant energy. Such energy
cannot be provided by low-level battery set up in such networks. Energy harvesting then is
very crucial to help the sustainability of such systems. Most WSN have low-powered
batteries which survives only for a short time. Constant power supply is therefore needed for
them.
With technologies such as Internet of Things evolving every day, energy harvesting is
expected to significantly increase in the future. Some situations require sensor networks to be
resolved. Further some applications in wireless sensor networks require constant energy
which can only be obtained through energy harvesting. It is important to determine how to
effectively harvest energy for each case. In conclusion, for efficiency and perpetual operation
of wireless sensor networks, energy harvesting is crucial.
Task 4
Background Information
Telestra is a licensed company to provide wired telecommunication services in Australia. The
company needs to implement of a new field service system that will require service
technicians to access company network remotely. Accessing the company network wirelessly
will eliminate the need for staff to carry books and drawings while on the filed particularly
while servicing underground equipment or when climbing. Company service technicians will
be in position to access and bring up-to-date the records for company equipment, thus
evading paperwork, errors and omissions. To achieve this, the company wants to implement
infrastructure. It is important to ensure that in such cases, network efficiency is maintained.
Energy harvesting would also ensure that emergency networks can be set to solve issues and
not fail by lacking energy or power to sustain.
Finally, applications that require to survive for long require constant energy. Such energy
cannot be provided by low-level battery set up in such networks. Energy harvesting then is
very crucial to help the sustainability of such systems. Most WSN have low-powered
batteries which survives only for a short time. Constant power supply is therefore needed for
them.
With technologies such as Internet of Things evolving every day, energy harvesting is
expected to significantly increase in the future. Some situations require sensor networks to be
resolved. Further some applications in wireless sensor networks require constant energy
which can only be obtained through energy harvesting. It is important to determine how to
effectively harvest energy for each case. In conclusion, for efficiency and perpetual operation
of wireless sensor networks, energy harvesting is crucial.
Task 4
Background Information
Telestra is a licensed company to provide wired telecommunication services in Australia. The
company needs to implement of a new field service system that will require service
technicians to access company network remotely. Accessing the company network wirelessly
will eliminate the need for staff to carry books and drawings while on the filed particularly
while servicing underground equipment or when climbing. Company service technicians will
be in position to access and bring up-to-date the records for company equipment, thus
evading paperwork, errors and omissions. To achieve this, the company wants to implement
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS COMMUNICATION ADVANCES 7
cellular digital cellular handsets technology to enable their technicians’ access company
network wirelessly. Cellular handsets are mobile electronic devices that provides services to
users including cellular telephony, managing address book, calendar scheduling, documents
access, accessing internet and email and more. Handsets include smartphones and PDAs
Features of using cellular handsets
Using cellular phone technology for Telestra will provide the following capabilities
(BusinessInformation, 2017)
• Handset applications mirror those of computers such as word processors, PDF
readers, web browsing
• Enhanced portability, smaller size, light weight – easy to carry and carry around than
a notebook
• Phone call capabilities
• Wireless internet access capabilities
• Mobile accessibility – easy to use in underground tunnels where it would be difficult
to use notebooks
• High rate power retention supply unlike notebooks, mobile handsets keep power for a
relatively longer periods of time
• Mobile apps installation of word processors such as word, excel and pdf applications
• Can access email and other work related notifications
• Relatively cheaper
Benefits of using cellular handsets over notebook computers for Telestra
cellular digital cellular handsets technology to enable their technicians’ access company
network wirelessly. Cellular handsets are mobile electronic devices that provides services to
users including cellular telephony, managing address book, calendar scheduling, documents
access, accessing internet and email and more. Handsets include smartphones and PDAs
Features of using cellular handsets
Using cellular phone technology for Telestra will provide the following capabilities
(BusinessInformation, 2017)
• Handset applications mirror those of computers such as word processors, PDF
readers, web browsing
• Enhanced portability, smaller size, light weight – easy to carry and carry around than
a notebook
• Phone call capabilities
• Wireless internet access capabilities
• Mobile accessibility – easy to use in underground tunnels where it would be difficult
to use notebooks
• High rate power retention supply unlike notebooks, mobile handsets keep power for a
relatively longer periods of time
• Mobile apps installation of word processors such as word, excel and pdf applications
• Can access email and other work related notifications
• Relatively cheaper
Benefits of using cellular handsets over notebook computers for Telestra
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS COMMUNICATION ADVANCES 8
• Enhanced customer service
• Flexible engagement between company stakeholders with the office, customers and
suppliers
• Data loss reduction
• Reduced data mismatch since handsets can be used to send data to the company
database
• Increase mobility
• Increase productivity
• Will allow service technicians to work quickly in any setting
• Enhanced customer service
• Flexible engagement between company stakeholders with the office, customers and
suppliers
• Data loss reduction
• Reduced data mismatch since handsets can be used to send data to the company
database
• Increase mobility
• Increase productivity
• Will allow service technicians to work quickly in any setting

WIRELESS COMMUNICATION ADVANCES 9
References
BusinessInformation. (2017). niBusinessInfo.co.uk. Retrieved from Business phone systems:
https://www.nibusinessinfo.co.uk/content/advantages-and-disadvantages-mobile-
phones-business
Kashif, L. (2011). Security Challenges & Prevention in Wireless Communications.
International Journal of Scientific and Engineering Research .
Kucharzewski, Ł., & Kotulski, Z. (2008). WiMAX Networks – architecture and data security.
Retrieved from http://www.ippt.pan.pl/Repository/o320.pdf
Singh, G., & Supriya. (2013). A Study of Encryption Algorithms (RSA, DES, 3DES and
AES) for Information Security. International Journal of Computer Applications
(0975 – 8887).
References
BusinessInformation. (2017). niBusinessInfo.co.uk. Retrieved from Business phone systems:
https://www.nibusinessinfo.co.uk/content/advantages-and-disadvantages-mobile-
phones-business
Kashif, L. (2011). Security Challenges & Prevention in Wireless Communications.
International Journal of Scientific and Engineering Research .
Kucharzewski, Ł., & Kotulski, Z. (2008). WiMAX Networks – architecture and data security.
Retrieved from http://www.ippt.pan.pl/Repository/o320.pdf
Singh, G., & Supriya. (2013). A Study of Encryption Algorithms (RSA, DES, 3DES and
AES) for Information Security. International Journal of Computer Applications
(0975 – 8887).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS COMMUNICATION ADVANCES 10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





